#personal infosec
Explore tagged Tumblr posts
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
53 notes
·
View notes
Text

good to know there’s people who are more insane than me, by far. yikes
157 notes
·
View notes
Text
i signed up for national cyber league a few months ago, and the individual game starts today...
for those who don't know, national cyber league is a capture-the-flag style, cybersecurity skills competition. i participated at least once for the past three years, the first two years competing along with my school. it was fun and i learned lots. my favorite part is watching the leaderboard lol.
now i'm already a day late because im tired... but because im not affiliated with any university doing this, i already paid $30 to participate, so i feel some investment in at least giving the individual game a wholehearted attempt. (there is also a team game, and i got connected to a team through a friend. i will take that more seriously, or however seriously those people take it. idk ive never worked with them before.)
#from now on i should probably do the free stuff instead#this game gives you skill reports and learning videos and whatnot#its good for an entry level infosec job resume#but i don't need that anymore#bags personal postings#studyblr#codeblr
12 notes
·
View notes
Text

10 notes
·
View notes
Text
last night we have mounted adguard (alternative to pi-hole) via home-made server to block spying and ads across our entire network. This morning we turned on our LG smart tv and just staying in home screen, and later opening youtube, during 20 minutes netfix (??) sent more queries than google did through the entire night
what the hell
2 notes
·
View notes
Text
Staying Relevant: Balancing Learning and Life as an Ethical Hacker
Have you experienced burnout while trying to develop your skills and you just don't have the time to do everything? Finding balance is the key to improving your skills in a healthy way. In this article, I explore healthy habits to grow without burning out
You’ve heard it before – cybersecurity is a field that evolves at a blindingly fast pace. The tools, techniques, and technologies threatening networks transform rapidly. As an ethical hacker, your skills can become obsolete within months if you aren’t continuously upgrading your knowledge. Point #4 on our hacker roadmap deals with knowing the latest and greatest when it comes to the state of…

View On WordPress
#burnout#certifications#conference#continuous learning#Cyber Security#cybersecurity education#cybersecurity skills#Ethical Hacking#hacker skills#infosec community#leadership#learning plan#maintaining balance#microlearning#Penetration Testing#pentesting methodologies#personal development#podcast#red team operations#security news#security policies#security tools#time management#trends#vulnerability assessments#work-life balance
3 notes
·
View notes
Text
for a moment I was so confused like “why is spinelli beefing with Cody???” …girl the blackmail
#pentababbles#general hospital#I FORGOT I FORGOT COMPLETELY#I forgot that other people on this show can get blackmailed beside just nina 😅#I mean yea cody blackmailing spinelli to get a date with Britt so he could steal her family jewels was pretty fucked#but spinelli having the most terrifying infosec privacy nightmare embedded into his paid dating service seems a bit way worse#also in retrospect I only ever remember that Austin was blackmailing spinelli as well to try fixing his relationship with Maxie 🤷♂️#ultimately Cody’s a better person now. mostly. but since they didn’t mention the blackmail in the ep… maybe the writers forgot abt it too 🤭
6 notes
·
View notes
Note
i’m curious what your opinion is on the finer points of the case mentioned in the JSTOR post you reblogged earlier. the two sources in the post say that JSTOR didn’t press charges against him and had already settled with him by the time he killed himself. from what i read on wikipedia, the concern seems to be that JSTOR complied with a subpoena, which i don’t believe they have a choice to ignore? if anything it seems like the us government had reason to want him dead for wikileaks and public court records reasons, so they took a terms of use violation and blew it up into a dozen federal crimes.
is there more context i should be aware of? i have no particular affection or malice for JSTOR but the sources i found don’t exactly implicate the database or its employees in murder.
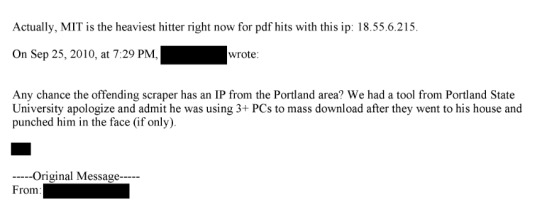


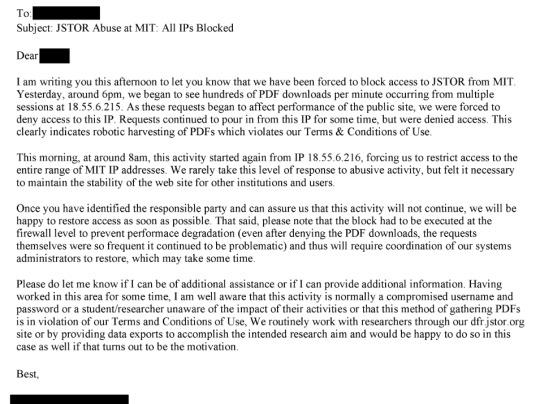
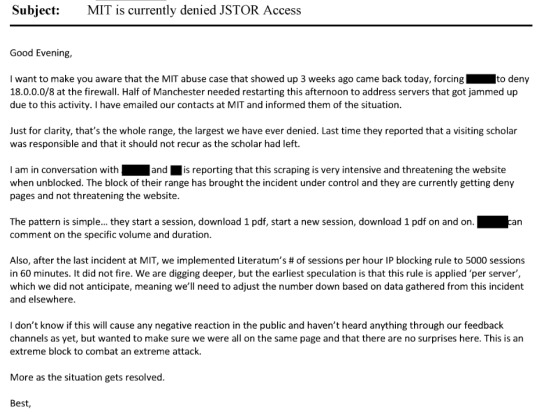
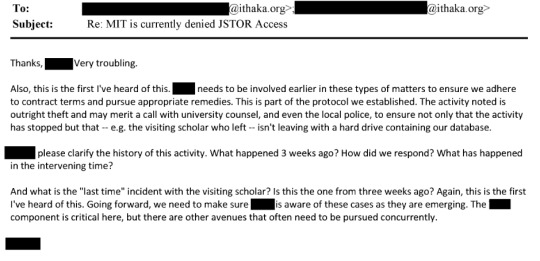
That's from page 175 of this document. This line: "The activity noted is outright theft and may merit a call with university counsel, and even the local police, to ensure not only that the activity has stopped but that - e.g. the visiting scholar who left - isn't leaving with a hard drive containing our database" is where I think the culpability starts.

If someone is downloading 1000s of articles (what seems like reasonable threshold for us to take action), what's wrong with us - or the university in collaboration with us - alerting the cyber-crimes division of law enforcement and initiating an investigation, having cop search dorm room and try to retrieve any hard drive that contains our content, etc. Our content is extraordinarily valuable and hard to replicate by the sweat of one's brow, but can be duplicated by savvy hackers and who knows what they want to do with the content?
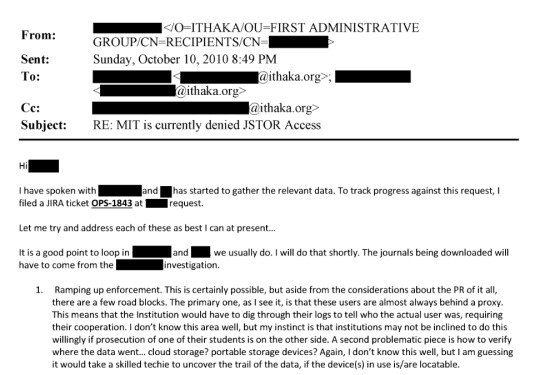


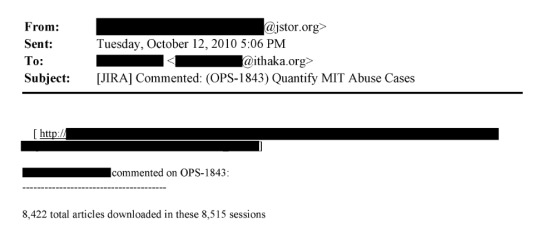
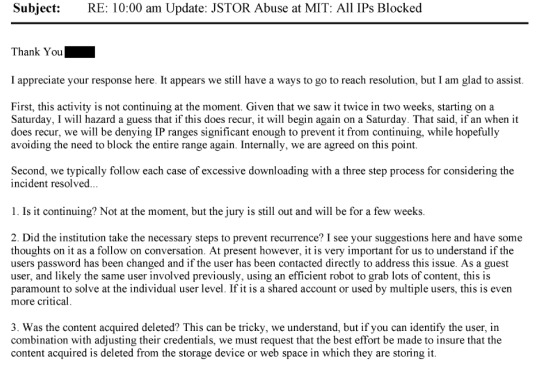
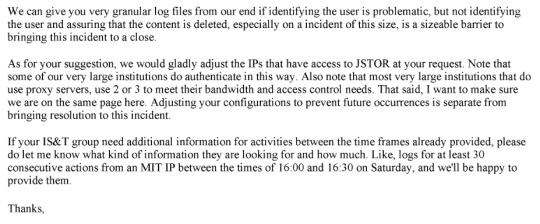
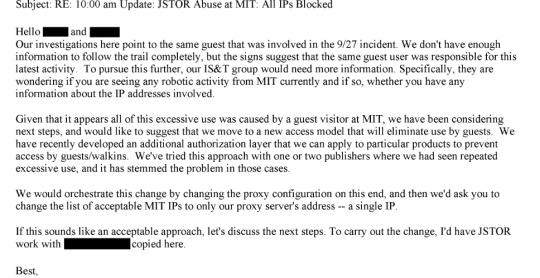
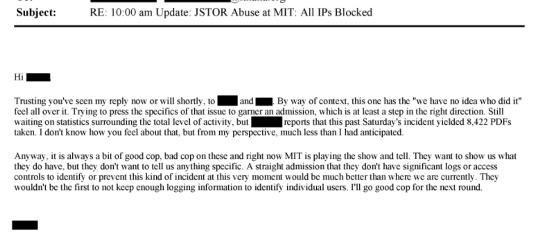


Page 379: "Does the university contact law enforcement? Would they be willing to do so in this instance?




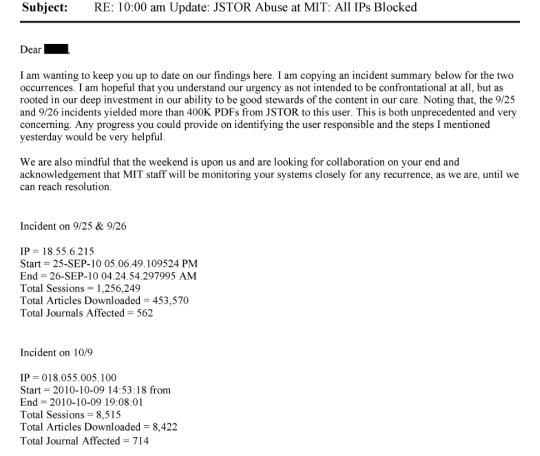
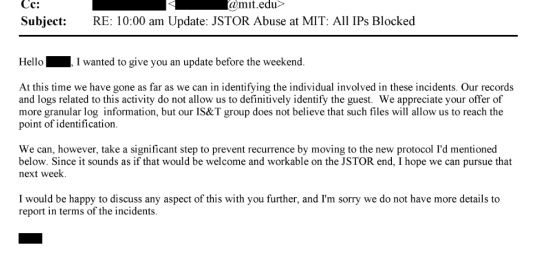



From page 1296:

I think the important thing to note here is that JSTOR had worked with MIT and had plans in place to prevent future similar downloads, but remained focused on identifying the person responsible for the downloads and ensuring that their data was deleted.

"I might just be irked because I am up dealing with this person on a Sunday night, but I am starting to feel like they need to get a hold of this situation right away or we need to offer to send them some help (read FBI).
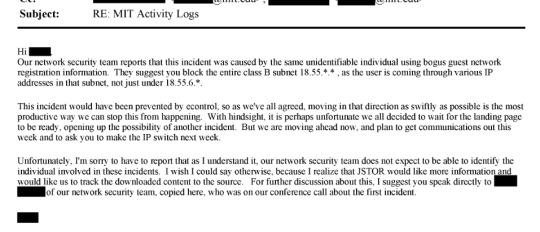
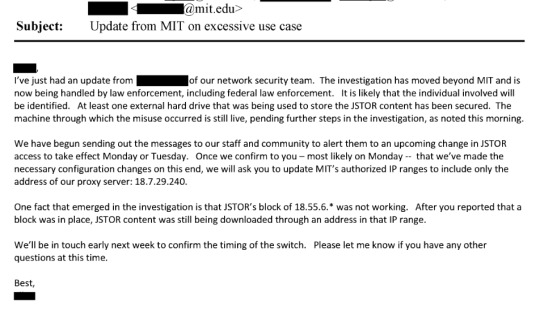
And there it is. Page 3093 of the document.
JSTOR can hem and haw about it all they want, but you can't un-call the cops.
MIT was working with JSTOR on preventing future incidents of pirating, but JSTOR repeatedly said that they weren't going to let it go, that it was unacceptable to drop the issue, that they were going to continue to pursue the pirate.
You can scroll through the document and see the JSTOR tech department and abuse team talking about Swartz as a script kiddie, and a hacker. You can see someone talking about how this was real theft - making the comparison to stealing books even while admitting that piracy doesn't close others out of access.
You can see the thread starts with a joke about punching someone in the face for hacking their system, and includes the tech team ominously considering whether they should threaten the MIT librarians with the FBI.
There's something really important to note here which I don't think that people who aren't PRETTY DEEP into hackery shit aren't aware of: US law enforcement is absolutely rabidly feral about prosecuting hackers. People may be more aware of this now because of Chelsea Manning and Edward Snowden (and perhaps a bit on tumblr because of maia arson crimew), but people who work in tech and who are in infosec - like the people joking about calling the FBI in these emails - would be aware of the bonkers disproportionate punishments faced by hackers. And knowing that, they kept pushing and pushing and pushing for identification of the hacker. They kept digging with MIT, they kept saying that simply preventing future incidents wasn't enough.
Early in the exchange someone from JSTOR asked "what's wrong with us - or the university in collaboration with us - alerting the cyber-crimes division of law enforcement and initiating an investigation, having cop search dorm room and try to retrieve any hard drive that contains our content, etc." and the answer is what happened to Aaron Swartz.
It is absolute bullshit for JSTOR to say "we arrived at a solution privately and didn't want to press charges" after law enforcement has gotten involved with a hacking case, especially one where they're talking about "real theft" and are attempting to quantify and emphasize the amount that was "stolen" from them.
The *public* may believe that private individuals or institutions are the ones who "press charges" but that's simply not the case. It's prosecutors who decide whether or not to go ahead with charges; they do it based on what cases they think they can win and what their office's perspective is on the crime. When you hear about people choosing to press charges it simply means that they decided to tell the prosecutor they wanted the case to go forward. It's up to the prosecutor whether or not that happens.
And the tech team at JSTOR had to know that law enforcement wasn't just going to wag a finger at an academic hacker.
There's a parallel here that happens sometimes when people have their identities stolen by their parents. If you mom takes out a credit card in your name, that's identity theft. That's fraud. That's illegal. If you reach the age of 25 and realize that your credit is ruined because your mom has been defaulting on cards in your name, you've got two choices to fix that: one is to accept the debt and pay it off and build up credit, and the other is to report the identity theft - which will end up with your mom in prison for a decade or so. Ruin your own personal finances, or your mom goes to jail for ruining your finances. So if you find out that your mom stole your identity you can't just call the cops to pressure her into transferring the debt to her name or something. That's not an option. The cops are not a threat to wave over people, they are not a way to get people to fall in line or act right. They aren't someone you can send to a college student's dorm room to retrieve a hard drive and have the matter drop.
When you call the cops on someone you are sending the full force of the law after them, and the full force of the law falls really heavily on hackers, and how heavy that blow can be is something that the JSTOR team must have been aware of when they were making snide comments about calling the FBI because they were frustrated with the noncommittal responses they were getting from librarians.
Ultimately it was the carceral state that killed Aaron Swartz, but they would not have been involved if JSTOR didn't think that what he did constituted theft.
Taking an *EVEN LARGER* step back from that, the idea that information can be owned and locked behind a paywall is what killed Aaron Swartz, someone who fought for information to be free.
Like. JSTOR is a licensing company. At the end of the day, cute social media posts and all, they're the same as the RIAA and ASCAB. They exist to extract a fee from people attempting to access information.
Aaron Swartz and all that he stood for are an existential threat to their core function.
Are JSTOR's hands as dirty as the federal prosecutors? Absolutely not. But they operate on a model that puts them in opposition to open information activists and it ended up with a hammer falling on Aaron Swartz that they dropped.
2K notes
·
View notes
Text
On Personal InfoSec
Been awhile since I've had one of these posts but I figure with all that's going on in the world it's time to make another one of these posts and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides.
Browsers:
There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out.
Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN:
Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Proton VPN: Has easily the most amount of countries serviced, can take cash payments, and does offer port forwarding.
Email Provider:
Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Outlook.com you'll need to pay.
Proton Mail: Secure, end-to-end encrypted, and fairly easy to setup and use. Offers a free option up to 1gb
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Email Client:
Thunderbird if you're on Windows or Linux
Apple Mail if you're on macOS
Cloud Storage:
Proton Drive: Encrypted cloud storage from the same people as Proton Mail.
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free, and open source.
Chat Clients:
Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode.
If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help.
I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#information security#infosec#computer security#computer infosec#personal infosec#browsers#internet browser#email#instant messaging#cloud storage#linux#pop os#linux mint#ubuntu#firefox#firefox extensions#long post
56 notes
·
View notes
Text
I think I have the perfect audience for this post.
If you're a
person who's mildly into software;
who doesn't have much or any experience with infosec;
and who likes puzzles,
you should try participating in a ctf (ctftime.org, picoctf). Challenges are usually different/abstract/weird enough to not feel like work (though web challenges are pretty much ruined for me now tbh) and you still get to hone your linux, forensic, pwn and other skills.
You really don't need any special skills to get started except for knowing how to search for things and the ability to not compare yourself to the top teams too much.
happy to answer any ctf related asks btw
#I solved a ~medium difficulty challenge today. first one in like 2 years. it felt SOOOO good#i pretty much stopped playing ctfs after getting my degree. which was a shame tbh
215 notes
·
View notes
Text
Friend you have landed on the literal reason this practice was passed onto me
You see, the scene I grew up in was "queer polyamorous fetishists who were alive and actively tryin to fuck back when it was still an enforced crime to be gay"
Several had sodomy or crossdressing convictions in their past. Many more had their lives ruined in some way or another when a landlord, employer, family member, etc found out they were gay. Every one of them had aliases they had been using SINCE THE 50S to cruise for super vanilla gay sex, let alone for like. Fetish-involved or non-monogamy or sex work or general sluttery.
It's the reason I do it too.
Known of you know my actual name unless you know me in person or MAYBE if you've sent me money. You DO all know my alias (in fact this is one of the first public spaces I used it in when I was an adult, because I had to transition away from the name I'd been using as a teen)
And meanwhile, Youtube Boy straight up doesn't know my name. I mean, he probably does by NOW because I am fully fucking aware he's had the opportunity to learn it even if I didn't tell him. But notably, we both have the plausible deniability of "I don't know who the fuck you'retalking about" if need be.
We have this for (shocker) reasons of queerphobia in our professions SPECIFICALLY. Because we both work in field that involve some combination of intensive background checks and steep public scrutiny.
If one of us gets "outed" we both specifically function under the "the exposure dies with me" policy to not hang the other out to dry. During the McCarthy era, the Hollywood blacklist depended on queer people, leftists, and others reporting on each other to save themselves. You can't do that if you don't have damning info to "give up".
I understand this isn't necessarily common practice for a lot of people now, but it wasn't that long ago (within my lifetime) that this stuff was simply How It Is Being Queer. The fact that my queerness never fully escaped that issue means I have never stopped living this way, and while even I was starting to loosen up about these things, I definitely won't be continuing that policy.
Because that's the thing right? Sex shouldn't be something that ruins your life! Nor should affection or love! These are blessings and gifts we all deserve to treasure, and we can do that best when WE get to decide who knows what about it.
While I'm on a kick of being really open about my sexuality, lets just start throwing shit out there and seeing how people interact with it
People who have followed me from the beginning will know that most of my partners get some quippy little nickname assigned to them in place of a name for the internet, and I want to name that this actually DOESN'T come from where might think (or rather it's still infosec, but it goes beyond "don't post the actual names of people you fuck online"
In the scene I have most cultural context for, people often came to group play sessions with an alias (I have one too lol, and it's the only name I ever introduce myself to partners as, mine has been static for going on a decade now). You would introduce yourselves to playmates under your alias, and often you would continue to use it as a marker of in-scene vs out-scene topics of conversation (e.g. sometimes people will talk about their aliases in third person as a whole entity with their own motivation, life, and power, my mom used to talk about "her friend [redacted 1]" if she ever needed to be able to reference a thing without naming explicitly that she and [redacted 1] were the same person, and there are friends of hers who still call her exclusively by that name in private because they have loved each other for going on 50 years now and [redacted 1] is still their partner and love even if mom isn't and vice versa).
So for example, on here, I will refer to any metamours by the plural-inclusive term The Metamour with very little discussion of which one or how many there are or whatever. But in person, I call one metamour [redacted 2] and another metamour [redacted 3] because they were introduced to me by their aliases first, and I genuinely DID NOT KNOW THEY'RE ACTUAL NAMES until after we had become real friends lol.
Anyway, Youtube Boy doesn't know that his nickname here is Youtube Boy, and that's not his alias in scene, nor his actual name, but critically these terms allow me to side step early uncertainties around terms like "boyfriend/girlfriend/datemate/etc" which may imply a degree of romantic entanglement I'm genuinely uncomfortable with. On occasion during this round of posting, I have gone "well it's CLEARER tho" and tried to type out "my boyfriend" about one of my current partners (partner does not carry this same issue for me, as I have always carried dual connotations of Romantic Oartner and Play Partner, so I feel no discomfort/cognitive dissonance with it's implications) and every time I do it I physically cringe away from the screen and delete it. Maybe he wouldn't feel the same way, and hell maybe I won't forever either! But I have almost never been willing to use a word like boyfriend without fairly explicit conversations about commitment, meaning to each other, and boundaries that just don't come up all the time in play partnerships for me you know?
Anyway, what I'm saying here is that sometimes the point of being a slut is to get to be every iteration of yourself that you love being independently from each other in a space that adequately facilitates that iteration of you. I like the people I play with to each get absolutely all of me that is available to them, and I **LIKE** that this often means I get to spend time as different important aspects of self, wholly and without self-doubt or minimization.
And hell, sometimes I even name the iteratioms and let them become something bigger than just a "version of me" and that can be fun too.
#and also yes i do enjoy being able to talk about the people i'm fucking and know people cannot actually connect that to#my stories that are ABOUT fucking those people#i have always been really comfortable sharing my non-vulnerable stuff about queerness and sexuality#but my non vulnerable isn't everybody's first of all#and second i actually AM really private about who is in my life#what we're doing? no. about who i am? eh infosec wise sure but i'm an open book personality wise#but who i'm doing that with?#that ain't all yalls fuckin business (said with love)
50 notes
·
View notes
Text
From a young age I have always been shocked by how incredibly trusting the average person seems to be, and I don't mean stuff like having poor infosec and the like but just how quickly people will tell me private information about themselves that I could use to seriously hurt them if I wanted to.
If anything that has become worse now that normies expect each other to put their real names and faces on the public internet.
35 notes
·
View notes
Text
I want to fight, I want to help information circulating but I don't know enough about politics to freely discuss things, so as a layman, let me say just this: I never once saw people speaking about one crucial thing about israel & usa. If you want to know - go to Darknet Diaries podcast
1 note
·
View note
Text
The surveillance advertising to financial fraud pipeline

Monday (October 2), I'll be in Boise to host an event with VE Schwab. On October 7–8, I'm in Milan to keynote Wired Nextfest.

Being watched sucks. Of all the parenting mistakes I've made, none haunt me more than the times my daughter caught me watching her while she was learning to do something, discovered she was being observed in a vulnerable moment, and abandoned her attempt:
https://www.theguardian.com/technology/blog/2014/may/09/cybersecurity-begins-with-integrity-not-surveillance
It's hard to be your authentic self while you're under surveillance. For that reason alone, the rise and rise of the surveillance industry – an unholy public-private partnership between cops, spooks, and ad-tech scum – is a plague on humanity and a scourge on the Earth:
https://pluralistic.net/2023/08/16/the-second-best-time-is-now/#the-point-of-a-system-is-what-it-does
But beyond the psychic damage surveillance metes out, there are immediate, concrete ways in which surveillance brings us to harm. Ad-tech follows us into abortion clinics and then sells the info to the cops back home in the forced birth states run by Handmaid's Tale LARPers:
https://pluralistic.net/2022/06/29/no-i-in-uter-us/#egged-on
And even if you have the good fortune to live in a state whose motto isn't "There's no 'I" in uter-US," ad-tech also lets anti-abortion propagandists trick you into visiting fake "clinics" who defraud you into giving birth by running out the clock on terminating your pregnancy:
https://pluralistic.net/2023/06/15/paid-medical-disinformation/#crisis-pregnancy-centers
The commercial surveillance industry fuels SWATting, where sociopaths who don't like your internet opinions or are steamed because you beat them at Call of Duty trick the cops into thinking that there's an "active shooter" at your house, provoking the kind of American policing autoimmune reaction that can get you killed:
https://www.cnn.com/2019/09/14/us/swatting-sentence-casey-viner/index.html
There's just a lot of ways that compiling deep, nonconsensual, population-scale surveillance dossiers can bring safety and financial harm to the unwilling subjects of our experiment in digital spying. The wave of "business email compromises" (the infosec term for impersonating your boss to you and tricking you into cleaning out the company bank accounts)? They start with spear phishing, a phishing attack that uses personal information – bought from commercial sources or ganked from leaks – to craft a virtual Big Store con:
https://www.fbi.gov/how-we-can-help-you/safety-resources/scams-and-safety/common-scams-and-crimes/business-email-compromise
It's not just spear-phishers. There are plenty of financial predators who run petty grifts – stock swindles, identity theft, and other petty cons. These scams depend on commercial surveillance, both to target victims (e.g. buying Facebook ads targeting people struggling with medical debt and worried about losing their homes) and to run the con itself (by getting the information needed to pull of a successful identity theft).
In "Consumer Surveillance and Financial Fraud," a new National Bureau of Academic Research paper, a trio of business-school profs – Bo Bian (UBC), Michaela Pagel (WUSTL) and Huan Tang (Wharton) quantify the commercial surveillance industry's relationship to finance crimes:
https://www.nber.org/papers/w31692
The authors take advantage of a time-series of ZIP-code-accurate fraud complaint data from the Consumer Finance Protection Board, supplemented by complaints from the FTC, along with Apple's rollout of App Tracking Transparency, a change to app-based tracking on Apple mobile devices that turned of third-party commercial surveillance unless users explicitly opted into being spied on. More than 96% of Apple users blocked spying:
https://arstechnica.com/gadgets/2021/05/96-of-us-users-opt-out-of-app-tracking-in-ios-14-5-analytics-find/
In other words, they were able to see, neighborhood by neighborhood, what happened to financial fraud when users were able to block commercial surveillance.
What happened is, fraud plunged. Deprived of the raw material for committing fraud, criminals were substantially hampered in their ability to steal from internet users.
While this is something that security professionals have understood for years, this study puts some empirical spine into the large corpus of qualitative accounts of the surveillance-to-fraud pipeline.
As the authors note in their conclusion, this analysis is timely. Google has just rolled out a new surveillance system, the deceptively named "Privacy Sandbox," that every Chrome user is being opted in to unless they find and untick three separate preference tickboxes. You should find and untick these boxes:
https://www.eff.org/deeplinks/2023/09/how-turn-googles-privacy-sandbox-ad-tracking-and-why-you-should
Google has spun, lied and bullied Privacy Sandbox into existence; whenever this program draws enough fire, they rename it (it used to be called FLoC). But as the Apple example showed, no one wants to be spied on – that's why Google makes you find and untick three boxes to opt out of this new form of surveillance.
There is no consensual basis for mass commercial surveillance. The story that "people don't mind ads so long as they're relevant" is a lie. But even if it was true, it wouldn't be enough, because beyond the harms to being our authentic selves that come from the knowledge that we're being observed, surveillance data is a crucial ingredient for all kinds of crime, harassment, and deception.
We can't rely on companies to spy on us responsibly. Apple may have blocked third-party app spying, but they effect nonconsensual, continuous surveillance of every Apple mobile device user, and lie about it:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
That's why we should ban commercial surveillance. We should outlaw surveillance advertising. Period:
https://www.eff.org/deeplinks/2022/03/ban-online-behavioral-advertising
Contrary to the claims of surveillance profiteers, this wouldn't reduce the income to ad-supported news and other media – it would increase their revenues, by letting them place ads without relying on the surveillance troves assembled by the Google/Meta ad-tech duopoly, who take the majority of ad-revenue:
https://www.eff.org/deeplinks/2023/05/save-news-we-must-ban-surveillance-advertising
We're 30 years into the commercial surveillance pandemic and Congress still hasn't passed a federal privacy law with a private right of action. But other agencies aren't waiting for Congress. The FTC and DoJ Antitrust Divsision have proposed new merger guidelines that allow regulators to consider privacy harms when companies merge:
https://www.regulations.gov/comment/FTC-2023-0043-1569
Think here of how Google devoured Fitbit and claimed massive troves of extremely personal data, much of which was collected because employers required workers to wear biometric trackers to get the best deal on health care:
https://www.eff.org/deeplinks/2020/04/google-fitbit-merger-would-cement-googles-data-empire
Companies can't be trusted to collect, retain or use our personal data wisely. The right "balance" here is to simply ban that collection, without an explicit opt-in. The way this should work is that companies can't collect private data unless users hunt down and untick three "don't spy on me" boxes. After all, that's the standard that Google has set.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/09/29/ban-surveillance-ads/#sucker-funnel

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#commercial surveillance#surveillance#surveillance advertising#ad-tech#behavioral advertising#ads#privacy#fraud#targeting#ad targeting#scams#scholarship#nber#merger guidelines#ftc#doj
285 notes
·
View notes
Text

A Beginner's Guide to Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
(Side note: this post is aimed towards the technical side of security, rather than the governance/management side, because the tech stuff is what I'm familiar with.)
Where do I start?
Cybersecurity is a specialization of general tech & therefore builds on some concepts that you'll need to know before you can dive deep into security. It's good to have a background in and understand:
how computers & operating systems work
how to use Linux
computer networking & basic protocols
If you're serious about learning cybersecurity, it can be helpful to look at certifications. Even if you don't want to get certified or take the exam (they can get expensive), they provide you with a list of topics that you can use to guide your self-study. And if you want to find a job, a certification is practically required for getting your foot in the door.
I personally recommend the CompTIA series of certifications, because they're well-recognized and I think they expose you to a good breadth and depth of material to get you started. Start with the A+ certification if you have zero tech background. Start with the Network+ certification if you've never taken a networking course. Once you get your basic computer and networking knowledge down, then you can jump into security. The Security+ is a good starting point.
Do I need to know how to code?
No, but it would be really really helpful. You don't have to be a skilled software engineer, but understanding the basics and being able to write small scripts will give you a solid foundation.
From Daniel Miessler's post How to Build a Cybersecurity Career:
You can get a job without being a programmer. You can even get a good job. And you can even get promoted to management. But you won’t ever hit the elite levels of infosec if you cannot build things. Websites. Tools. Proofs of concept. Etc. If you can’t code, you’ll always be dependent on those who can.
How do I gain skills?
Play Capture the Flag (CTF) games.
Stay up to date with security news via an RSS reader, podcasts, or whatever works for you. Research terms that you're unfamiliar with.
Watch conference talks that get uploaded to YouTube.
Spin up a VM to practice working with tools and experiment on your own computer.
There are lots of brilliant, generous people in cybersecurity who share their knowledge and advice for free. Find their blogs, podcasts, and YouTube channels. Look for local meetups in your area.
I'm still relatively new to the field, but I have a general knowledge of lots of different things, so feel free to send me an ask and I can probably help point you to some resources. We're all in this together!
Previous Cybersecurity Masterposts
An Introduction to Cybersecurity
Cybersecurity Book Masterpost
Free Cybersecurity Learning Resources Masterpost
Masterpost of Study Tips for Cybersecurity
Cybersecurity Tools Masterpost
Thank you so much to everyone who participated in the #StudyblrMasterpostJam this week! It was wonderful to see what other studyblr folks are passionate about. The jam technically ends today but there are no official rules, so if you've been thinking about writing a masterpost, this is your sign!
30 notes
·
View notes
Text
Modern Academic AU pt2
Originally started because Professor Raphael got stuck in my head and I had (foolishly) hoped if I wrote down some thoughts, that would be the end of it 🫠
Part 1 and Part 3 ------------------------------ Minthara - School of Law. Used to be a high profile defense lawyer but was barred from practice under questionable circumstances, so now she teaches courses on criminal procedure and domestic violence litigation. Male students are actively warned against taking any of her classes. Elminster - Liberal Arts Dean. Has been in the position forever and is something of a legend at this point. He's Gale's mentor and long time family friend, and he delights in showing up unannounced to Prof. Dekarios's lectures. The two of them have a longstanding tradition of leaving surprise pranks in each others offices. Rolan - English department. Newly upgraded from adjunct instructor to junior full time staff, he's been assigned the special hell of having to teach the general ed. introductory writing courses that none of the other faculty want to deal with. He hates it and thinks it's a complete waste of his talents, but is determined to stick through it long enough to get that research grant. Alfira - School of Theater & Music. Teaches vocal technique and musicality at every level. She's also the faculty coordinator for multiple on-campus performance groups, directs the university chorale and composes all their arrangements, is herself in a local acapella group, AND does community arts & outreach programs for kids.
Gortash - Newly appointed Dean of Information Studies. He's brilliant, he talks big about new frontiers in infosec and grand designs in the future potential of AI... and is already under investigation by the ethics board for misappropriation of university funds. Ketheric - VP of Alumni and he's been with the university longer than Elminster. Nobody knows why he hasn't just retired yet, despite how much he seems to hate his job. Orin - School of Fine Art. She "teaches" a course on performative art. It's weird and extremely uncomfortable for everyone involved, but for some reason people keep enrolling. Durge - Fine Art Dep't Chair. The deeply disturbing nature of his personal art aside, he's actually good at his job as both the chair and an instructor. Mostly teaches anatomy and live model studio courses. Ulder - VP of Public Affairs. He's a great public face for the university, everybody loves him... except the son he refuses to acknowledge after a falling out years ago. Mizora - Human resources admin. Loves her job because it gives her power over other people. Is more likely to be the source of an HR complaint than the one who actually solves the problem. Thaniel (as requested!) - Also HR. He's the one you hope gets assigned to whatever you need because he's great at it. Is also the only one who can reliably get in touch with Halsin; it's not well known that he can, so he'll usually agree to help those who figure out to ask him.
------------------------------
This started going long, so it looks like I'll be doing a third (and probably final?) installment to cover Dammon, Zevlor, Wulbren, Aylin & Isobel, and any other requests!
#bg3#baldurs gate 3#minthara#elminster#rolan#alfira#enver gortash#ketheric thorm#orin the red#durge#mizora#ulder ravengard#thaniel
56 notes
·
View notes