#professional Twitter hacker
Explore tagged Tumblr posts
Text
Hire Professional Twitter Account Hackers
One can hire hacker to hack twitter through a number of online services. By using complex academic jargon, one can write about the many benefits of hiring a hacker for twitter. Hiring a hacker for twitter can help protect one’s account from being compromised. If you hire professional twitter hacker it can also help one gain access to exclusive information. And insights that are not available to the general public.
We provide a service that allows you to hire a hacker for twitter. By using our service, you can access the latest in hacking technology and techniques. in order to help you get the most out of your twitter account. We provide a variety of services, including password cracking, account takeover, and more. Our teams of experts are available 24/7 to help you get the most out of your twitter account.
Why Hire A Twitter Hacker From Us By You?
There are many reasons why hiring a Twitter hacker from us would be the best decision. First of all, our team is experienced and qualified in the field of social media hacking. We have the ability to provide our clients with the highest quality service possible. In addition, we are always up-to-date on the latest Twitter security vulnerabilities and how to exploit them. Our team is also available 24/7 to help you with any problems or questions you may have.
Our Twitter Hacker’s Skills
Our Twitter hacker is a highly skilled and experienced professional who can help you with all your Twitter hacking needs. He has years of experience in the field and is known for his expertise in this area. So he can help you hack into any Twitter account and access its data, and he can also help you protect your own account from being hacked. He is a reliable and trustworthy hacker who will always put your needs first. And he is always available to help you with whatever you need.
We Are Unique And Can Stand Out From Our Competitors For:
Our team of hackers has years of experience and a proven track record of success. We are well-known for our expertise in the area of Twitter hacking, and for hire a Twitter hacker we are the best team for the job. So we are dedicated to providing our clients with the highest quality service possible. And we always put the client’s needs first. We are also experts in other areas of hacking, such as email hacking, website hacking, and more.
Contact With Us At:
The easiest way to reach us is by email. With our email address . we attempt to reply to all emails within a few hours. But we strive to respond to all messages as soon as possible. Our customer service agents are at your disposal 24 hours a day.
#Twitter Hacking#twitterhack#twitterhacking#Twitterworldhacking#professional hackers for hire#professional Twitter hacker
1 note
·
View note
Note
Hiii.. so.. i'm a self made "hacker" and i'll try to explain how that whole twitter archive is possible to be accessed to.. in the simplest way i can put it..
So, think of it as someone taking screenshots of how luigi's page looked like BEFORE he went missing.. so, someone took a 'screenshot' when he changed his bio to *broke my spine and went nuts*., and then someone took another screenshot in june when he changed it to his normal bio. This is now easily accessed through a simple code and you can even see how many times these 'screenshots' were taken (3 times for luigi's tw).
Now, it is not that strange that someone, possibly his friends or mother who knows about compsci, took these 'screenshots' bc he could have been acting strange or distancing from everyone by this time. Knowing his social circle was full of computer professionals, they would have investigated his activity at the first sign that something was wrong. And, of course, a Penn graduate who publicly claims he 'went nuts' it's a clear sign that something was wrong.
(For context, this was the original ask sent to me about him changing his bio, and these are the alleged screenshots.)
ty for explaining this anon!
13 notes
·
View notes
Text
How to Hire a Social Media Hacker Safely: A Complete Guide
In today’s tech-driven world, social media accounts are more than just a place for socializing—they are gateways to personal and business data. Whether you're locked out of your account, worried about digital privacy, or need to strengthen your security, hiring a hacker might seem like a quick fix. However, it's important to approach this cautiously. In this guide, we'll explain how to safely and legally hire a social media hacker, what to look for, and the risks involved.
1. Why Hire a Social Media Hacker?
There are a variety of reasons why you might consider hiring a hacker for your social media needs. Some of the most common include:
Account Recovery: Losing access to a social media account due to hacking or forgotten passwords can be frustrating. A professional hacker can bypass recovery protocols and get you back in.
Security Audits: Ethical hackers can identify weaknesses in your social media security, helping you prevent future cyber-attacks.
Data Retrieval: For business purposes, some companies hire hackers to retrieve important information or gain insights into competitors.
While the idea of hiring a hacker might seem risky, when done ethically and legally, it can be a helpful resource in regaining control over your online assets.
2. What is a Professional Social Media Hacker?
A professional social media hacker is an expert skilled in identifying and exploiting weaknesses in social media platforms to recover accounts, enhance security, or gather data. These hackers fall into two categories:
White-Hat Hackers: Ethical hackers who work within legal boundaries. They are typically hired for account recovery, security testing, and digital protection services.
Black-Hat Hackers: Individuals who use their skills for malicious purposes, such as unauthorized access or data theft.
It's essential to make sure you're hiring a white-hat hacker to ensure the legality of their actions. White-hat hackers use legitimate methods to help you regain access or fortify your account.
3. How to Hire a Social Media Hacker
Finding a reliable social media hacker takes more than just a quick Google search. Here’s how you can find a legitimate hacker without falling for scams:
Freelance Platforms: Websites like Upwork, Freelancer, and Fiverr host professionals offering hacking and cybersecurity services. Be sure to check reviews and ask for verifiable past work.
Cybersecurity Firms: Many reputable companies specialize in ethical hacking services. Hiring through these firms ensures that you’re working with professionals who will operate within legal boundaries.
Hacker Forums: There are many online forums where ethical hackers offer their services. However, proceed with caution, as these forums can also be a breeding ground for scams.
Once you find a hacker, ask for credentials or proof of their experience with the platform you need help with, such as Facebook, Instagram, or Twitter.
4. The Benefits of Hiring a Professional Social Media Hacker
When you hire a social media hacker, you're not just gaining access to your account; you're investing in your online security and peace of mind. Here are the key benefits:
Quick Account Recovery: Forget the long, frustrating customer support routes. A professional hacker can help you regain access faster.
Improved Security: By running security checks and vulnerability assessments, hackers can help you secure your social media accounts and prevent future breaches.
Competitive Advantage: In business, accessing legally obtained data from competitors can help improve your strategies.
Hiring a hacker can be a valuable tool for both personal and professional needs, but only when done ethically.
5. Legal Risks of Hiring a Social Media Hacker
While hiring a hacker can solve a number of problems, it’s essential to understand the risks involved:
Illegal Hacking: Hacking someone else's social media account without permission is illegal and can result in serious legal consequences. Always make sure that your actions, and the actions of the hacker you hire, are within the legal framework.
Scammers: Unfortunately, there are many untrustworthy individuals who claim to be hackers but are really out to scam people. Be careful when sharing personal information, and only work with vetted professionals.
Ethical Concerns: Even if a hacker offers to retrieve information from someone else’s account, remember that doing so without consent is unethical and illegal.
Before you hire, ensure that the hacker’s actions will be lawful and ethical to avoid any legal trouble.
6. How to Protect Yourself When Hiring a Hacker
To safely hire a social media hacker, here are some best practices to follow:
Do Your Research: Take the time to verify the hacker’s credentials. Look at their previous work, ask for references, and check for any feedback from past clients.
Use Secure Communication: Always communicate securely with the hacker to protect your personal information. Avoid sharing sensitive data over unencrypted platforms.
Create a Clear Agreement: Before any work begins, have a formal contract that outlines the services to be performed and the legal limitations. This protects both parties and ensures that the work stays within ethical boundaries.
7. Hiring a Social Media Hacker: What to Expect
When working with a professional hacker, clear communication and expectations are essential. Here’s what to expect:
Transparent Pricing: The cost of hiring a hacker can vary depending on the complexity of the task. Be wary of hackers who offer extremely low rates, as they might not be legitimate.
Clear Communication: A professional hacker should explain the process clearly and answer any questions you have along the way.
Results: Whether you’re looking for account recovery or a security audit, a professional hacker should deliver results within the agreed-upon timeframe.
Conclusion: The Right Way to Hire a Social Media Hacker
Hiring a social media hacker can be an effective way to recover lost accounts, strengthen security, or gain strategic insights. However, it’s essential to hire a reputable, ethical hacker who operates within legal boundaries. By following the steps outlined in this guide, you can safely and legally hire a professional social media hacker to help with your digital needs.
For more information:
Hire a Hacker
Hire a Social Media Hacker
Professional Social Media Hacker
This article integrates the keywords "hire a hacker," "hire a social media hacker," and "professional social media hacker" naturally throughout the content, while keeping the information helpful and engaging for readers. It also includes hyperlinks to the desired website for further exploration, ensuring SEO indexability.
2 notes
·
View notes
Text
Internet security is a complicated thing to talk about. It is something both business owners and average users are concerned about. The more developers work on the security problems, the more hackers, and cybercriminals try to solve them. It is a vicious circle. But it doesn't mean you do not have to protect your private or business data even knowing that there is no such website or program which can't be hacked sometime. Statistics show that cybercriminals equally target both smaller and bigger businesses, making IT security the key to the company's stability and productivity. Serious cyber attacks are not chaotic or single. Usually, it is a set of programs, which target several companies in one industry at once. If you don't believe that the hackers can paralyze the work of the whole company, try not to use any program or service for the protection of your data. But we don't recommend even thinking about it. Of course, if you don't want to lose the amount of work you have already done and the money you have already earned. So, what can you do to prevent your business from being hacked by cybercriminals? The first and the most basic IT security step is getting the best FREE VPN service for your website and banking operations at least. The importance of VPN services results from their ability to encrypt the connection between your PC/laptop/smartphone and the Internet, which makes it invisible to hackers. But what else can you do to protect your personal and professional information? IT Security Solutions There are some differences between what average users and professionals do to protect their data from hacking. For example, average users consider antivirus software and strong passwords to be enough. While professional IT security experts consider installing software updates and using unique passwords to be far more important for your data. There are a lot of other critical things you probably do wrong when it comes to the security of your professional and personal information. So, let's have a look how it should be done correctly. Professional Tips on Internet Security First of all, let's mention one misunderstanding most Apple users have. "Apple can't be hacked. It's secure enough without an additional protection." That's not the truth. Even Apple products can be hacked. Not so easily as others but still they can be hacked. Apple is just doing a better job when it comes to security issues. And now we can officially skip to those basic steps you can do to protect your online business from being paralyzed by hackers. Use Two-factor authentication Two-factor authentication instead of changing your password every two months. This concerns most of your daily accounts like Gmail, Twitter, Facebook, Amazon, etc. Among all of these accounts, highlight your email account. As it is one the most important ones. If a hacker owns your email account, he'll probably own other services. He can reset all other passwords just using this email address. Two-factor authentication is something, which can prevent this from happening. Dealing with suspicious links Confirm suspicious links but do not click on them. This will show you where the link goes. Based on this you can decide whether to click on that link or not. And don't forget to check the sender's email address too. Backups Using a backup tool is a good starting point for any business when it comes to security. Having a good backup, which is not connected to your machine is very important. Try offline backups as one of the first steps while figuring out which security strategy is more suitable for you. Train your team A lot of cyber attacks happen because of the employees who click on the malicious links or websites. So, it would be a smart move to provide your employees with the key principles and rules of the company's IT security policy. Contact a security specialist Today, you have a choice between contacting a security specialist for any IT recommendations
on security issues or to hire a provider, which specializes in cybersecurity on a daily basis. It is a good outsourcing step, which gives you the ability to cover all online security gaps at once. This will save your time and money. Let IT specialists monitor the security of your business. Make a security review It is very useful to make a full security review of your passwords, access to them, backups, and testing every couple of months. Analyze the results you get and find out if your IT security system has any gaps. Consult an expert. This is what you can do to protect your business and personal data online. And what is your number one thing to protect the company on the Internet?
0 notes
Text
SharePoint Vs WordPress: A Showdown Between Intranet and Internet CMS on Twitter
In a recent social media buzz, Twitter witnessed a heated debate. The topic was SharePoint vs WordPress. Users compared the two content management systems (CMS) in depth. Hashtags like #SharePointVsWordPress and #CMSBattle trended for hours. Professionals, tech experts, WordPress Development Agency and developers joined the conversation. They compared features, use cases, and user experience. The clash highlighted the core difference between intranet and internet platforms.

Enterprise Powerhouse: SharePoint Wins the Intranet Game
Microsoft SharePoint dominates the intranet world. Big companies use it for team collaboration. It helps manage internal content securely. SharePoint integrates with Microsoft 365 smoothly. That makes it ideal for office environments. It supports document sharing, team workflows, and employee directories. Users praised its structured control and corporate-level security. However, SharePoint’s interface is not beginner-friendly. It needs technical training and setup support. On Twitter, users called SharePoint a “corporate beast” and “made for internal empires.” Its strength lies in complex workflows and strict permission rules.
Internet Freedom: WordPress Rules the Web
WordPress, on the other hand, dominates the internet space. Over 40% of websites run on WordPress. Bloggers, businesses, and media use it daily. It is known for ease of use and flexibility. WordPress offers thousands of themes and plugins. You can build any site, from blogs to e-commerce stores. It works well for non-technical users. Many developers praised its fast learning curve. Twitter users described WordPress as “open and limitless.” It allows freedom in WordPress Website Design, hosting, and customization. Unlike SharePoint, WordPress works best for public content.
Security and Control: SharePoint Takes the Lead
Security was a hot topic in the debate. SharePoint users stressed enterprise-grade protection. It offers role-based access and secure authentication. Companies can store sensitive files without worry. In contrast, WordPress sites need extra security plugins. They are more exposed to cyber threats. Hackers often target poorly maintained WordPress sites. Users must stay updated and backup data. This difference gave SharePoint an edge. Tech professionals agreed that SharePoint suits industries with strict compliance needs.
Ease of Use: WordPress is the People’s Favorite
WordPress won the user-friendly title. Users highlighted its simple dashboard and drag-and-drop editors. Even non-tech users build websites in hours. SharePoint needs professional setup and training. Users need knowledge of Microsoft’s ecosystem. Beginners may feel lost without help. This became a key issue in the Twitter battle. Many tweets mocked SharePoint’s complexity. WordPress, in contrast, was called “grandma-friendly.” It appeals to a wider audience, including solo entrepreneurs.
Customization: WordPress Offers More Creative Freedom
WordPress Development Agency praised WordPress for its customization power. You can edit themes, use code, or add third-party tools. There’s a plugin for almost everything. From WordPress SEO tools to online stores, WordPress covers it all. SharePoint’s customization is limited to developers. It supports apps and web parts but not as freely. Most changes need backend support or SharePoint Framework (SPFx) coding. This pushed WordPress ahead in creative freedom. Twitter users said, “WordPress is playdough; SharePoint is Lego with missing blocks.”

Integration Strength: SharePoint Dominates Office Ecosystems
SharePoint’s integration with Microsoft tools is unmatched. It syncs with Teams, OneDrive, Outlook, and more. Office workers use it to streamline tasks daily. This deep integration makes SharePoint a business asset. It supports internal project tracking, HR systems, and data dashboards. On Twitter, many IT pros praised this feature. WordPress offers third-party integrations, but not as natively. It needs plugins and sometimes paid add-ons. This makes SharePoint better for enterprise-wide deployments.
Cost Debate: WordPress Is Cheaper, But With Conditions
Cost became a hot issue in the thread. WordPress itself is free. But premium themes, plugins, and hosting add cost. Still, it’s cheaper than SharePoint licenses. SharePoint usually comes with Microsoft 365 subscriptions. Enterprise users pay more for extra features. Smaller teams may find it costly. WordPress is more budget-friendly for startups and freelancers. Users warned that WordPress costs can rise over time. Add-ons and maintenance need attention. Still, it wins in affordability for most users.
Final Verdict: It Depends on Your Needs
Twitter didn’t declare a clear winner. Users agreed that both platforms serve different needs. SharePoint fits large teams, internal tools, and strict systems. WordPress suits bloggers, creators, and small businesses. The real battle is not which is better. It’s about what you need. Each CMS shines in its own world. SharePoint rules the office. WordPress rules the open web. As one user tweeted, “It’s like comparing a Swiss Army knife to a power drill. Both powerful, but for different jobs.”
Conclusion:
Choose Your CMS Based on Purpose
The Twitter storm showed one thing clearly. CMS choice must match your goal. Want intranet, team workflows, and corporate control? Choose SharePoint. Want blogs, public sites, and full freedom? WordPress is better. Both platforms will continue evolving. And this CMS debate? It’s far from over.
1 note
·
View note
Text
Digital Marketing for Programmers

You’ve built a great app, website, or tool—but what’s next? As a programmer, learning digital marketing can help you reach more users, grow your brand, and even monetize your work. In this post, we’ll explore essential digital marketing strategies tailored for developers and tech entrepreneurs.
Why Programmers Should Learn Digital Marketing
Gain Visibility: Ensure people discover and use your product.
Monetize Projects: Turn side projects into profitable ventures.
Build a Personal Brand: Showcase your skills and expertise.
Attract Opportunities: Networking, clients, job offers, and collaborations.
1. Know Your Audience
Start by defining your ideal users. Are they developers, students, small businesses, or general consumers? Understanding their needs will help you tailor your messaging and features.
2. Build a Strong Online Presence
Personal Website/Portfolio: Display your work, blogs, and contact info.
GitHub: Share your code and attract collaborators or employers.
Blogging: Write tutorials or development stories to build credibility.
LinkedIn: Share updates and connect with industry professionals.
3. Content Marketing
Create valuable content that solves real problems. This could include:
Technical tutorials or coding walkthroughs
Case studies about how you built your project
“How-To” guides and comparison articles
Use platforms like Medium, Dev.to, and your own blog to publish.
4. SEO (Search Engine Optimization)
Use keywords: Include relevant keywords in titles, URLs, and headers.
Optimize speed: Ensure your website loads fast and is mobile-friendly.
Write meaningful meta tags: Improve click-through rates on search results.
5. Social Media Promotion
Share your work on developer communities and tech platforms:
Twitter/X: Engage with tech influencers and share updates.
Reddit: Subreddits like r/programming, r/webdev, or r/learnprogramming.
LinkedIn: Publish updates, demos, and career milestones.
YouTube: Create video tutorials or product demos.
6. Email Marketing
Build an email list and keep your users informed about updates, features, and new projects.
Offer a freebie (e.g., a cheat sheet or template) in exchange for an email.
Use platforms like Mailchimp, ConvertKit, or Buttondown.
7. Paid Advertising (Optional)
For faster growth, consider running paid campaigns:
Google Ads: Target people searching for your type of product.
Facebook/Instagram Ads: Visual promotion for apps or tools.
LinkedIn Ads: Great for B2B tools and professional services.
8. Track and Improve
Use Google Analytics to monitor website traffic and user behavior.
Use Hotjar or Microsoft Clarity for heatmaps and session recordings.
Gather feedback through surveys or live chat tools like Tawk.to or Crisp.
Bonus Tips
Launch on Product Hunt to reach tech-savvy audiences.
Join indie hacker or startup communities to get feedback and exposure.
Keep marketing consistent—even small efforts compound over time.
Conclusion
Digital marketing doesn’t require you to be a salesperson—it’s about telling the story behind your work and reaching the right audience. As a programmer, mastering digital marketing can turn your projects into impactful, successful products. Start small, stay consistent, and track your progress as you grow.
0 notes
Text
Soot School of Odd Thinkers: A Top Digital Marketing Institute

With the age of technology upon us, companies are on the lookout for out-of-the-box marketing strategies that will make them stand out from the rest. This is where digital marketing comes into the picture, and getting trained at the best institutions can provide an individual with the perfect platform for success. Soot School of Odd Thinkers (SOOT) has proved to be one of the leading digital marketing institutes with its off-beat approach towards learning.
What Makes SOOT Unique? SOOT is not another digital marketing institute; it is a creative and strategic hub. While conventional institutes are inclined towards textbook education, SOOT focuses on learning by doing, real-life case studies, and practical projects. The philosophy at the school is all about "thinking outside the box", making it perfect for those who seek to defy norms and become better digital marketers with a new thinking approach.
In-depth Course Syllabus SOOT has a highly organized curriculum for every area of digital marketing. A few of the major modules are:
Search Engine Optimization (SEO) – Learning Google algorithms, keyword research, on-page and off-page optimization.
Pay-Per-Click Advertising (PPC) – Advertising through paid media on Google, Meta (Facebook, Instagram), and other sites.
Social Media Marketing (SMM) – Tactics to increase brands on Instagram, Facebook, LinkedIn, and Twitter.
Content Marketing & Copywriting – Developing compelling content that generates traffic and conversions.
Affiliate Marketing & Email Marketing – Profiting from content and fostering customer relationships via email marketing.
Data Analytics & Performance Tracking – Utilizing data-driven tools such as Google Analytics and Facebook Pixel to measure performance.
Branding & Growth Hacking – Creative techniques to grow companies fast.
Each course is structured with hands-on exposure so that students are able to apply strategies in real-life situations.
Expert Faculty & Mentorship SOOT has a panel of industry specialists with years of experience in online marketing. The faculty includes successful business owners, digital strategists, and growth hackers who mentor students beyond the classroom. They share their insider information, practical experiences, and industry trends to make students job-ready.
Hands-on Learning & Live Projects What distinguishes SOOT is its focus on experiential learning. Rather than theoretical classes alone, students engage in live projects, case studies, and simulations. This enables them to create a portfolio, gain confidence, and learn how digital marketing functions in actual business contexts.
Placement Assistance & Career Opportunities SOOT goes beyond education by offering placement assistance to students. The institute has tie-ups with leading brands, startups, and digital agencies, helping graduates secure jobs in SEO, PPC, social media management, content marketing, and more. Additionally, SOOT encourages entrepreneurship, enabling students to start their own digital ventures.
Why Choose SOOT? Innovative Learning Approach – Encourages out-of-the-box thinking.
Practical Exposure – Focuses on live projects and real-time case studies.
Industry Experts – Learning from professionals who have hands-on experience.
Career Support – Extensive placement network and career advisory.
Affordable & Flexible Courses – Beginner's courses and courses for advanced students.
Final Thoughts Soot School of Odd Thinkers is revolutionizing education in digital marketing by cultivating innovation, strategic intellect, and ground-level implementation. As a student, professional marketer, entrepreneur, or business person, SOOT offers the apt platform to gain success in today's rapidly evolving digital era.
#school#digital marketing#marketing#seo services#seo#ppcadvertising#ppc#social media marketing#social media agency#digital marketing agency
0 notes
Text
Beyond the Earnings: The Surprising Benefits of a Career in Cybersecurity
Cybersecurity is one of those careers that sounds either super cool or super intimidating sometimes both. If you’ve ever thought about getting into it, you’ve probably heard the usual perks: great salary, job security, and the satisfaction of outsmarting hackers. But let’s talk about the real reasons why cybersecurity is one of the most underrated (and weirdly fun) careers out there.
1. You Get to Be a Professional Trouble-Maker (Legally!)
If you’ve ever been the kid who took apart the family computer just to see how it worked, or the one who figured out how to bypass school WiFi restrictions (no judgment), cybersecurity might just be your calling. Ethical hackers (yes, that’s a real job) get paid to break into systems legally to help companies patch security holes. Enrolling in a reputable Cyber Security Online Training & Placement program can equip individuals with the essential skills and knowledge needed to excel in this dynamic and evolving field.

2. No Suit, No Problem—Work in Pajamas If You Want
Cybersecurity is one of the most remote-friendly careers out there. Many roles let you work from home, a coffee shop, or even while traveling. As long as you have a solid internet connection and your laptop, you’re good to go. Bonus: You get to skip the daily commute and wear whatever you want (yes, even that hoodie you’ve had since high school).
3. It’s Not Just a Job, It’s a Superpower
Once you start working in cybersecurity, you’ll never look at the internet the same way again. You’ll spot phishing scams a mile away, know exactly how to lock down your personal data, and never fall for those “Congrats! You won an iPhone!” pop-ups. You become the person your friends call when they think they’ve been hacked (which, honestly, can be both a blessing and a curse).
4. No Degree? No Problem!
Unlike a lot of high-paying jobs, cybersecurity doesn’t always require a college degree. Many people break into the field through self-study, certifications, and hands-on experience. If you love problem-solving and figuring things out on your own, you can learn the skills needed without spending years in school (and without drowning in student debt).
5. You’ll Never Be Bored (Seriously, Never)
Cyber threats are constantly evolving, which means your job will never be the same two days in a row. One day you might be analyzing malware, the next you’re investigating a security breach. If you hate routine and love a good challenge, cybersecurity is the perfect playground. When you work in cybersecurity, you don't just protect businesses you also learn how to safeguard your own digital life. Through Best Online Training & Placement Programs, you'll be the one spotting phishing emails before they trick you, securing your personal data like a pro, and staying ahead of cyber threats.
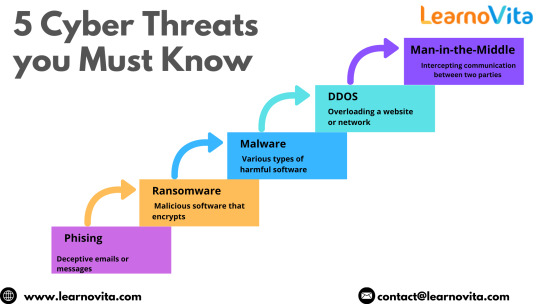
6. You’re Actually Making the Internet a Safer Place
This is the part people don’t talk about enough: cybersecurity isn’t just about stopping hackers. It’s about protecting people, businesses, and even entire governments from cyber threats. Whether you’re preventing financial fraud, safeguarding personal data, or keeping companies from being held hostage by ransomware, your work has real-world impact.
7. The Community is Wildly Supportive
The cybersecurity world is filled with people who love to share knowledge. Whether it’s through online forums, Capture The Flag (CTF) competitions, or Twitter threads breaking down the latest hacks, you’ll find a community that genuinely enjoys helping newcomers get started. No gatekeeping, just nerds supporting nerds.
0 notes
Text
How to Create a Comprehensive Estate Plan That Covers Digital Assets in Bradenton, FL

Who would access your online accounts, financial data, or treasured family photos stored in the cloud in the event you passed away? Without proper planning, your loved ones may face confusion and legal hurdles while trying to manage your digital legacy. As technology evolves, so does the need to include digital assets in estate planning. Your personal information, financial records, and cherished memories hold significant value, making it crucial to secure them within your estate plan.
In this guide, we'll walk Bradenton residents through the essential steps to ensure their digital assets are properly managed and protected.
What Are Digital Assets? A Complete Overview
Digital assets refer to any electronic records you own or control online, ranging from financial data to personal content stored in the cloud. These assets can hold both monetary and sentimental value, making them a critical part of your inheritance planning.
Common Types of Digital Assets
Here are some examples of digital asset management considerations for your estate plan:
Financial Accounts: Online banking, investment portfolios, cryptocurrency wallets like Bitcoin or Ethereum.
Social Media Profiles: Facebook, Instagram, LinkedIn, and Twitter are important for both personal and professional connections.
Email Accounts: Gmail, Outlook, and Yahoo, which often serve as gateways to other critical accounts.
Cloud Storage Services: Google Drive, Dropbox, and iCloud store documents, videos, and photos.
Online Subscriptions: Streaming services (Netflix, Spotify), software licenses, and memberships.
Domain Names & Websites: Valuable assets for business owners or personal branding.
Digital Media Collections: Purchased eBooks, music, and movies stored in online libraries.
Loyalty and Rewards Programs: Accumulated points from airlines, hotels, or retailers that hold financial value.
By incorporating these into your estate planning checklist for digital assets, you ensure your loved ones can access and manage them seamlessly after you're gone.
Why Ignoring Digital Assets in Estate Planning Is Risky
Failing to plan for digital assets can result in unnecessary stress and financial losses for your family. Without clear instructions, they might struggle to recover important information or risk losing valuable assets. Some risks include:
Loss of Access: Heirs may struggle to access online accounts or cryptocurrency wallets without passwords or legal permissions.
Emotional Impact: Losing cherished digital memories like photos or messages can be devastating for your loved ones.
Identity Theft: Unattended personal information can be targeted by hackers, leading to fraud or misuse.
Legal Complexities: Without proper documentation, digital assets may become entangled in lengthy probate processes.
Family Disputes: Inconsistent or missing instructions can lead to conflicts among heirs.
A Step-by-Step Guide to Protecting Your Digital Assets in Estate Planning
Bradenton residents can take proactive steps to secure their digital legacy by following this comprehensive approach:
Step 1: Create an Inventory of Your Digital Assets
Start by making a complete list of your digital assets, including:
Account names and website links
Login credentials (stored securely with password management tools)
Instructions on how you want each asset to be managed
Consider using secure storage solutions like LastPass or a fireproof safe to protect this information safely.
Step 2: Define Your Wishes for Each Digital Asset
Think about what should happen to each asset after your passing:
Should social media accounts be memorialized or deleted?
Do you want family members to inherit digital photos and videos?
Who should take control of business-related digital assets?
Documenting your preferences prevents misunderstandings and ensures your wishes are honored.
Step 3: Appoint a Digital Executor
A trustworthy executor is someone you designate to manage your digital estate. This role requires someone tech-savvy and responsible who can handle sensitive information securely.
They will be responsible for:
Closing accounts you no longer need
Transferring ownership of valuable assets
Ensuring sensitive information is protected
If you're wondering how to appoint a digital executor in estate planning, it's essential to choose someone who understands digital security and legal requirements.
Step 4: Include Digital Assets in Legal Documents
To ensure your digital assets are handled according to your wishes, incorporate them into your legal documents such as:
Your will – Specify beneficiaries and access instructions.
A trust – Offer additional control over assets.
A power of attorney – Appoint someone to manage accounts if you become incapacitated.
If you're looking for an estate planning attorney in Bradenton for digital assets, experts like Grivas Law Group P.A. can help you create legally binding documents tailored to your needs.
Step 5: Keep Your Plan Updated and Secure
Regularly review your estate plan to reflect changes in your digital assets, such as new accounts or passwords. Ensure your executor always has access to the latest version of your plan through secure storage options.
Why Work with a Bradenton Estate Planning Attorney?
Florida has adopted the Revised Uniform Fiduciary Access to Digital Assets Act (RUFADAA), which allows estate executors and trustees to access digital assets under specific conditions. However, without proper authorization, service providers may refuse access due to privacy policies and terms of service agreements.
If you're unsure about Florida laws on digital asset estate planning, it's important to consult an experienced attorney to ensure full legal compliance.
A qualified attorney can help:
Identify and organize your digital assets
Draft customized legal documents
Ensure compliance with Florida estate laws
If you're looking for professional guidance, consider consulting Grivas Law Group P.A., an estate planning firm with expertise in digital assets and Florida law.
Conclusion
Incorporating digital assets in estate planning is crucial to ensuring your online accounts and valuable digital property are protected and managed according to your wishes. Don't wait until it's too late—take the necessary steps today to secure your digital legacy.
If you're ready to get started, reach out to an estate planning attorney in Bradenton for digital assets for consultation and personalized guidance.
0 notes
Note
So, Brandon, our supposedly neutral journalist insert the world's biggest eye-roll here has turned his Twitter into a shrine dedicated to Sebastian Stan. We're talking a full-blown tweetstorm, with over a dozen tweets extolling the virtues of Saint Sebastian. This isn't just about that interview anymore, oh, no. This man's practically campaigning for Seb to win an Oscar, a Nobel Peace Prize, and maybe even actual sainthood while he's at it. He's replying to every. Single. Tweet. Like his life, or perhaps his paycheck, depends on it (which, let's be honest, it probably does).
But here's where the plot thickens. Brandon claims that Sebastian, the same guy who treats social media like it's a radioactive wasteland, slid into his DMs. Not directly, mind you, but through AW's Instagram. You heard that right. That AW, who doesn't even follow him. And, drumroll please… Brandon's account is private. We're talking Fort Knox level private.
This supposed "sweet note" from Seb was apparently so time-sensitive that email or text just wouldn't do. Nope, gotta use AW's account, who, and I can't stress this enough, does not even follow him! So, how in the name of all that is logical did this message penetrate the impenetrable fortress that is Brandon's private account? Telepathy? Did Sebastian suddenly morph into a world-class hacker? Or is AW secretly an Instagram sorceress, bending the platform to her will?
It's as if he's trying to convince us that Seb and AW are joined at the hip, sharing passwords, a single toothbrush, maybe even a single brain cell. It's the kind of 'we finish each other's sentences' vibe that makes you wanna puke. And this whole song and dance is about as convincing as a screen door on a submarine.
And to add insult to injury, Brandon claims Sebastian thanked him for supporting "A Different Man," when his Twitter feed is practically an ode to "The Apprentice" and his portrayal of Trump. Seriously, dude, pick a lane!
Now, let's break this down:
Social Media Ghost: Sebastian has practically declared a public allergy to social media, treating it like the Black Plague. But suddenly, he's sliding into DMs via AW's account? Yeah, that tracks. (Narrator: It did not, in fact, track.)
Phone Number, Anyone?: If Sebastian and Brandon were in contact to arrange the interview (which, obviously, they had to be), wouldn't Sebastian have, you know, Brandon's number? You know, for basic professional communication?
Mission: Impossible - DMs: Brandon's Instagram is private. AW doesn't follow him. So, how did this mythical message even get through? Carrier pigeons? A glitch in the Matrix? Magic Beans?
The Tell-Tale Detail: Why even mention the whole "sent through AW's account" bit? It's like they're trying to force-feed us this fairytale romance, but it's so over-the-top it reeks of desperation and pure fabrication.
.
0 notes
Note
So, Brandon, our supposedly neutral journalist insert the world's biggest eye-roll here has turned his Twitter into a shrine dedicated to Sebastian Stan. We're talking a full-blown tweetstorm, with over a dozen tweets extolling the virtues of Saint Sebastian. This isn't just about that interview anymore, oh, no. This man's practically campaigning for Seb to win an Oscar, a Nobel Peace Prize, and maybe even actual sainthood while he's at it. He's replying to every. Single. Tweet. Like his life, or perhaps his paycheck, depends on it (which, let's be honest, it probably does).
But here's where the plot thickens. Brandon claims that Sebastian, the same guy who treats social media like it's a radioactive wasteland, slid into his DMs. Not directly, mind you, but through AW's Instagram. You heard that right. That AW, who doesn't even follow him. And, drumroll please… Brandon's account is private. We're talking Fort Knox level private.
This supposed "sweet note" from Seb was apparently so time-sensitive that email or text just wouldn't do. Nope, gotta use AW's account, who, and I can't stress this enough, does not even follow him! So, how in the name of all that is logical did this message penetrate the impenetrable fortress that is Brandon's private account? Telepathy? Did Sebastian suddenly morph into a world-class hacker? Or is AW secretly an Instagram sorceress, bending the platform to her will?
It's as if he's trying to convince us that Seb and AW are joined at the hip, sharing passwords, a single toothbrush, maybe even a single brain cell. It's the kind of 'we finish each other's sentences' vibe that makes you wanna puke. And this whole song and dance is about as convincing as a screen door on a submarine.
And to add insult to injury, Brandon claims Sebastian thanked him for supporting "A Different Man," when his Twitter feed is practically an ode to "The Apprentice" and his portrayal of Trump. Seriously, dude, pick a lane!
Now, let's break this down:
Social Media Ghost: Sebastian has practically declared a public allergy to social media, treating it like the Black Plague. But suddenly, he's sliding into DMs via AW's account? Yeah, that tracks. (Narrator: It did not, in fact, track.)
Phone Number, Anyone?: If Sebastian and Brandon were in contact to arrange the interview (which, obviously, they had to be), wouldn't Sebastian have, you know, Brandon's number? You know, for basic professional communication?
Mission: Impossible - DMs: Brandon's Instagram is private. AW doesn't follow him. So, how did this mythical message even get through? Carrier pigeons? A glitch in the Matrix? Magic Beans?
The Tell-Tale Detail: Why even mention the whole "sent through AW's account" bit? It's like they're trying to force-feed us this fairytale romance, but it's so over-the-top it reeks of desperation and pure fabrication.
0 notes
Text
Social Media Security Settings: Protecting Your Privacy Online

Social media platforms are essential for connecting with friends, sharing updates, and networking. However, they can also expose your personal information to cyber threats if not properly secured. Adjusting your social media security settings helps protect your privacy, prevent unauthorized access, and reduce the risk of identity theft.
This guide provides actionable steps to enhance your social media security settings and ensure a safer online experience.
Why Social Media Security Is Important
1. Protects Personal Information
Secure settings prevent sensitive details, such as your location, contact info, and photos, from being accessed by unauthorized individuals.
2. Reduces Risk of Hacking
Stronger security settings make it harder for hackers to compromise your account.
3. Prevents Identity Theft
Limiting the exposure of personal details reduces the chances of identity theft or impersonation.
4. Maintains Reputation
Controlling who can see and interact with your content helps safeguard your personal and professional image.
Essential Social Media Security Settings
1. Enable Two-Factor Authentication (2FA)
Add an extra layer of security to your account by requiring a secondary verification step.
How to Enable 2FA:
Facebook: Go to Settings > Security and Login > Two-Factor Authentication.
Instagram: Visit Settings > Security > Two-Factor Authentication.
Twitter/X: Navigate to Settings > Security and Account Access > Two-Factor Authentication.
Options:
One-time codes via SMS or email.
Authentication apps like Google Authenticator or Authy.
Biometric options, such as fingerprints.
2. Set Strong Passwords
Use a unique, complex password for each account.
Best Practices:
At least 12 characters with a mix of letters, numbers, and symbols.
Avoid using common phrases or personal information.
Use a password manager to securely store and generate passwords.
3. Adjust Privacy Settings
Control who can see your profile, posts, and personal information.
How to Update Privacy Settings:
Facebook: Go to Settings > Privacy > Who Can See Your Future Posts.
Instagram: Enable Private Account in Settings > Privacy.
LinkedIn: Customize your visibility under Settings > Visibility.
Tip: Limit your audience to friends, connections, or approved followers.
4. Manage App Permissions
Review and revoke access to third-party apps that have access to your account.
How to Check Permissions:
Facebook: Go to Settings > Apps and Websites.
Twitter/X: Visit Settings > Security and Account Access > Connected Apps.
Google: Navigate to Security > Third-Party Apps with Account Access.
Tip: Remove any apps or services you no longer use.
5. Limit Location Sharing
Turn off location settings to prevent platforms from tagging your posts with your whereabouts.
How to Disable Location Sharing:
Facebook: Go to Settings > Location > Location Access for This Device.
Instagram: Turn off location access in your phone’s settings.
Tip: Avoid posting real-time updates about your location to stay safe.
6. Review Profile Information
Minimize the amount of personal information visible on your profile.
What to Limit:
Contact details like phone numbers or email addresses.
Birthdates, especially the year.
Relationship status or workplace.
Tip: Use generic profile photos and usernames on public-facing accounts.
7. Monitor Login Activity
Regularly check for suspicious login attempts or devices logged into your account.
How to Check:
Facebook: Go to Settings > Security and Login > Where You’re Logged In.
Instagram: Visit Settings > Security > Login Activity.
Twitter/X: Navigate to Settings > Security and Account Access > Apps and Sessions.
Tip: Log out of unfamiliar devices immediately.
8. Enable Notifications for Suspicious Activity
Activate alerts to receive notifications about unrecognized login attempts or security breaches.
How to Enable Alerts:
Facebook: Turn on Login Alerts in Settings > Security and Login.
Instagram: Enable login notifications under Security Settings.
Twitter/X: Activate login verification under Security Settings.
9. Be Selective with Friend Requests
Only accept connection requests from people you know or trust.
Why It’s Important:
Scammers and fake profiles often use friend requests to gain access to your information.
Mutual friends don’t always mean someone is trustworthy.
10. Regularly Update Your Security Settings
Social media platforms frequently update their features, so periodically review and adjust your settings.
Tip: Set a reminder to check your account settings every few months.
Tips for Secure Social Media Usage
1. Think Before You Post
Avoid sharing sensitive or incriminating information that could be used against you.
2. Use Trusted Devices
Log in only from secure devices you control, and avoid public or shared computers.
3. Be Wary of Phishing Scams
Watch out for suspicious links or messages that ask for your login credentials.
4. Log Out When Finished
Always log out from accounts on shared or public devices to prevent unauthorized access.
5. Monitor Your Digital Footprint
Search your name online to see what information is publicly accessible, and take steps to remove anything inappropriate or outdated.
What to Do If Your Account Is Compromised
Change Your Password Immediately Create a new, strong password for the compromised account and any linked accounts.
Enable Two-Factor Authentication (2FA) Add an extra layer of protection to prevent further unauthorized access.
Notify the Platform Report the issue to the social media provider and follow their recovery steps.
Inform Your Connections Let your friends and followers know your account was compromised to avoid scams.
Scan for Malware Run a full scan on your device to ensure no malicious software is present.
Conclusion
Securing your social media accounts is essential for protecting your privacy, maintaining your reputation, and reducing the risk of cyberattacks. By adjusting security settings, enabling two-factor authentication, and using strong passwords, you can significantly enhance your online safety.
Take control of your social media accounts today to enjoy a safer and more secure digital experience.
FAQs
1. How often should I review my social media security settings? At least every six months, or whenever there’s a major update to the platform.
2. Is two-factor authentication necessary for all accounts? Yes, 2FA adds an essential layer of security for all accounts, especially those with sensitive information.
3. How can I recognize a phishing attempt on social media? Look for messages with suspicious links, generic greetings, or urgent requests for personal information.
4. Can I make my social media account completely private? While you can limit visibility significantly, some information may still be accessible, depending on the platform.
5. What should I do if I suspect someone is impersonating me? Report the fake account to the platform immediately and notify your contacts.
0 notes
Text
Why You Shouldn’t Hire a Social Media Hacker: Risks and Ethical Concerns
In today’s digital age, social media has become an integral part of personal and professional lives. Platforms like Facebook, Instagram, and Twitter are where people share updates, connect with friends, promote businesses, and even build careers. With the rise of social media has also come the temptation for some to find shortcuts, like hiring a social media hacker. While it might seem like a quick solution to gain followers, access a locked account, or snoop on someone’s private data, Hire a Social Media Hacker is both dangerous and unethical. Here’s why.
Legal Risks
One of the most compelling reasons to avoid hiring a social media hacker is the potential legal ramifications. Hacking, in almost all circumstances, is illegal. When you hire someone to break into an account—whether it’s yours or someone else’s—you are actively participating in a crime. Countries have strict cyber laws to protect user data and privacy. Getting caught could lead to heavy fines, criminal charges, and in severe cases, imprisonment. Additionally, if the hacking involves accessing confidential or sensitive information, the legal consequences can be even more severe.
Damage to Your Reputation
Hiring a hacker can severely tarnish your personal or professional reputation. If you’re caught, the public perception of you as someone who engages in dishonest or illegal activities could harm future career prospects or relationships. In business, reputation is everything. If a company is found to have used hacking methods to gain an advantage, it could lose the trust of customers, stakeholders, and employees. In a world where transparency is increasingly valued, being associated with unethical practices like hacking can be a major setback.
Loss of Trust
Social media is built on trust, both between platforms and users and among individuals. By hiring a hacker, you are essentially violating the trust of others. Whether it’s breaking into someone’s private account or manipulating social media algorithms to falsely inflate your following, you’re betraying the unwritten rules of fair play. Once trust is broken, it’s hard to regain. If people find out you used unethical means to get ahead, they may stop following or supporting you altogether.
Insecure and Unreliable
Hiring a hacker does not guarantee success. Hackers often operate in the shadows and can be just as untrustworthy as the illegal services they provide. There’s no guarantee that the hacker you hire will successfully complete the task. Worse, they might scam you by taking your money and disappearing. Even if they manage to break into an account or manipulate social media metrics, there’s always a chance they could blackmail you later, threatening to expose your participation in illegal activity.
Potential for Data Breach and Identity Theft
When hiring a hacker, you often have to provide personal information about yourself or the person or account you’re targeting. This opens the door for hackers to steal your own data. Once they have access to your personal or business information, they could misuse it in countless ways. Identity theft, financial fraud, or selling your data on the dark web are just a few of the risks involved. You may find yourself the victim of the very crime you attempted to orchestrate.
Ethical and Moral Considerations
Beyond the legal and practical consequences, there’s a strong ethical argument against hiring a social media hacker. Digital privacy is a fundamental right, and by hacking into someone’s account, you’re infringing on that right. The same way you wouldn’t want someone to violate your privacy, it’s important to respect others’ digital spaces. Building a social media presence or solving a security issue should be done ethically, using legal means rather than shortcuts that undermine the integrity of the system.
While the temptation to Hire an Ethical Hacker might arise in a variety of situations, from recovering a forgotten password to gaining unfair advantages, it is not worth the risk. The legal implications, damage to your reputation, potential scams, and ethical concerns far outweigh any temporary gain. Instead, focus on using legitimate tools, improving your cybersecurity, and respecting the digital privacy of others. In the long run, maintaining ethical practices will help build a stronger and more trustworthy online presence.
0 notes
Text
Spy Your Partner’s Online Activity With Social Media Hacker
Uncover the risks and alternatives of monitoring your partner's online behavior using social media hacker.

In today's digital age, where social media platforms dominate our daily lives, monitoring online activity has become increasingly common, especially in relationships. With the rise of social media hacker tools, individuals are now able to access information about their partners' online behavior more easily than ever before.
💢 Why spy on your partner's online activity?
In the realm of modern relationships, the phrase "Spy your partner's online activity with a social media hacker" encapsulates a controversial temptation. As technology weaves its threads through our personal lives, the desire to delve into our partner's digital world becomes increasingly prevalent. This article explores the intricate dynamics of relationships, acknowledging the curiosity or insecurities that prompt individuals to contemplate unconventional methods like Instagram hacking. It delves into the nuances of the phrase spy your partner's online activity, unraveling the complexities and potential consequences associated with succumbing to this temptation while emphasizing the importance of trust and communication in fostering healthy connections.
💢 What are the benefits of spying on your partner's online activity?
Related: 5 Ways To Facebook Hack In Cheating Evidence Investigations
🔹Security: Monitoring online activity may provide a sense of security by ensuring transparency and detecting any potential threats or risks to the relationship.
🔹Verification of Trust: For some, spying could serve as a means to verify the trustworthiness of their partner and confirm their commitment to the relationship.
🔹Early Warning Signs: It can help identify early warning signs of problematic behavior or issues within the relationship, allowing for timely intervention and resolution.
🔹Peace of Mind: Knowing their partner's online interactions can offer peace of mind, especially if there have been previous instances of dishonesty or infidelity.
🔹Communication Enhancement: Spying might prompt more open communication between partners, facilitating discussions about boundaries, trust, and privacy within the relationship.
💢 How Social Media Hacker Work
Social media hacker tools typically exploit vulnerabilities in social media platforms to gain unauthorized access to user accounts. Once installed or activated, these tools can retrieve information such as messages, photos, and browsing history without the account holder's knowledge.
💢 Steps to Spy on Your Partner's Online Activity
Using social media hacker tools to spy on a partner's online activity typically involves several steps. These may include downloading or installing the software, obtaining access to the partner's device or accounts, and navigating the interface to view relevant information.
💢 Seeking Professional Help
When you are going through such a situation, you need to seek professional help. Then you will find the solution to your problem easily and can help to solve the underlying problems in the relationship.
📌Related Topic: Spy Twitter To Monitor Your Partner’s Activities
💢 Privacy in Relationships
Regardless of the methods used to monitor online activity, it's crucial to prioritize privacy and respect within the relationship. Both partners should feel comfortable discussing boundaries and expectations regarding privacy, ensuring that mutual trust and respect are maintained.
🟩 Final Touch
While the temptation to spy on a partner's online activity may be strong, it's essential to consider the potential consequences and ethical implications of such actions. Open communication, trust, and respect are fundamental pillars of any healthy relationship, and violating these principles can lead to irreparable harm. Instead of resorting to spying, it's important to foster open dialogue and mutual understanding within the relationship.
0 notes
Text
Social Media Hacks: Spotting Signs of Infidelity in Your Relationship

Social media has become an integral part of our daily lives in the digital age. Which helps us to connect with people all over the world. However, there are also challenges. Especially in romantic relationships. One of the most worrying aspects is the possibility of infidelity. If you are worried that your partner is cheating on you, with the help of social media hacker you can clear your doubts. You can spot signs of infidelity as a guide. Let us see how you can catch a cheating boyfriend with the help of a professional hacker.
1. Changes in Social Media Behavior
One of the first indicators that something might be wrong in your relationship is a change in your partner's social media habits. If your cheating boyfriend uses social media in a more secretive way, such as spending too much time on platforms like Instagram, Facebook or Twitter, this could be a red flag. It could be that your partner has cheated on you. But to understand it more clearly you can see the specific changes:
Increased Activity: If your partner is posting more frequently than usual or liking and commenting on posts excessively, it might be a sign that they're trying to impress someone new.
New Friends or Followers: A sudden influx of new friends or followers, especially if they are of the opposite sex, could indicate that your partner is seeking attention elsewhere.
Privacy Settings: If your partner suddenly changes their privacy settings, it could be a sign that they’re trying to hide something from you. For example, they might make their posts visible only to certain people or remove you from their friend list altogether.
2. Secretive Communication
Communication is a very important thing in all of our lives. We communicate with each other in different ways. And one of them is social media. Social media is a popular medium but it also has some downsides. One of these is that people are involved in multiple relationships. They are having an extramarital affair. Let's read the following points carefully:
Private Messages: If your partner is spending a lot of time sending private messages or direct messages (DMs) on social media, it might be worth looking into. Suspicious behavior includes deleting messages immediately after reading them or getting defensive when you ask about their online conversations.
Unusual Activity Times: If your partner is staying up late or waking up early to use social media, it might suggest they are communicating with someone in a different time zone or when they think you won’t notice.
Hidden Conversations: Some individuals go to great lengths to hide their conversations by using disappearing messages, secret accounts, or even creating fake profiles. If you suspect this, it might be time to dig deeper.
📌 Related Topic: Social Media Hacks to Uncover Infidelity in 2024
📌 Read Also: How WhatsApp Hacker Help You to Spend Infidelity-Free Life
3. Emotional Distance
Social media sometimes creates emotional distance between our partners. Especially if a person is more focused online than in their relationship. If you spend most of your time on social media without giving time to your loved one, then you may develop emotional distance with your partner. Let's take a look at some of these symptoms:
Less Engagement: If your partner used to like or comment on your posts frequently but has stopped, it might indicate that they’re losing interest or focusing their attention on someone else.
Distracted Behavior: If your partner seems distracted or disengaged when you’re together, especially if they’re constantly checking their phone or social media, it could be a sign that their mind is elsewhere.
Less Communication: If your partner is communicating less with you and more with someone else online, it might be a sign of an emotional affair. Emotional infidelity can be just as damaging as physical infidelity, so it’s essential to address this issue if you notice it.
4. Suspicious Posts
Social media posts can reveal a lot about a person's state of mind and intentions. Pay attention to what your partner is posting and how it might relate to you. Because your partner's posts involve his state of mind. So these profile posts should be looked at carefully:
Vague or Cryptic Messages: If your partner is posting vague or cryptic messages that seem to be directed at someone else, it could be a sign of infidelity. These posts might include song lyrics, quotes, or emotional outbursts that hint at dissatisfaction or longing.
Frequent Selfies: While posting selfies isn’t inherently suspicious, a sudden increase in the number of selfies your partner posts could indicate that they’re seeking validation or attention from someone else.
Flirtatious Comments: If your partner is leaving flirtatious comments on someone else’s posts or receiving them, it’s a clear sign that something might be amiss. This behavior can indicate that your partner is testing the waters with someone new.
5. Deleting Posts or Accounts
Another form of infidelity on social media is when you see your partner deleting all posts or activities from his social media account. This could be a sign of fraud so you should keep monitoring these. If you don't take help of regular social media monitoring then you will suffer a lot. Things you should look for in your partner's regular social media monitoring are:
Deleted Comments: If your partner deletes comments from their posts, it might be because they’re trying to hide something from you or avoid raising suspicion.
Missing Photos: If photos of the two of you suddenly disappear from their profile, it could be a sign that they’re trying to appear single or available to someone else.
Deactivating Accounts: If your partner suddenly deactivates or deletes their social media accounts, it might be an attempt to cover up their tracks. This behavior is particularly suspicious if it’s out of character for them.
6. Secret Accounts
Some people create secret or fake accounts to communicate with others without their partner's knowledge. If you suspect your partner may have a secret account, here's how you can investigate:
Search for Duplicate Profiles: Try searching for your partner’s name, photos, or common usernames they might use to see if they have multiple accounts on the same platform.
Ask Mutual Friends: Mutual friends might notice if your partner is interacting with someone suspiciously or using a secret account to do so. They might be able to provide you with valuable information.
Monitor Behavior: If your partner is being unusually protective of their phone or devices, it could be a sign that they’re hiding something. Watch for changes in behavior, like turning off notifications or avoiding social media when you’re around.
7. Professional Help
If you are not sure if your partner is cheating on you if you consider the above signs. Then you can take services like social media monitoring with the help of a professional social media hacker. And you can be sure if your partner is cheating on you. To do this you can take the help of HackersList. They provide social media hacking services worldwide. Here they have registered hackers with them they are very skilled and they complete the client's work very efficiently. You can hire a professional social media hacker from HackersList. Get here
Conclusion
Social media can be a powerful tool for spotting signs of infidelity in your relationship. You can catch your partner cheating with the help of a skilled social media hacker. By paying attention to changes in communication patterns and social media activity, it is important that you communicate carefully with the increase of potential problems, you can catch your cheating spouse with the help of professional hacker. By gathering evidence through social media, you can catch the cheating spouse and resolve the issues that arise. If you are still not sure if your partner is cheating on you. To be sure about that you can take the help of platforms like HackersList.
#social media hack#social media hacking#social media hacks#social media monitoring#social media monitor#hackerslist
0 notes
Text
The Rise of Remote Work: How to Source and Hire Top Tech Talent Remotely
Worldwide, businesses are adapting to an increase in remote work. This change in the office dynamic opens doors but also presents new hurdles. Hiring tech-savvy employees who can effectively work remotely is now a vital aspect for companies striving for an advantage. We're diving into the surge of remote work in this blog, the advantages of onboarding tech talent from afar, and how to successfully find and hire these remote tech professionals.

The Evolution of Remote Work
Not so long ago, working from home wasn't common. It has happened in certain jobs or fields only. Things changed when the COVID-19 pandemic hit. More and more sectors, tech included, were switching to remote work. Businesses saw how great it was! It gave flexibility, opened the door to workers worldwide, and cut down on running costs.
FlexJobs shared some interesting info. In the last five years, work-from-home jobs rose by 44%, and 91% in the last decade. It Seems like companies notice the perks of remote work. They're even starting to put some money into it, using cool tools and systems to make it work.
Benefits of Hiring Remote Tech Candidates
Hiring remote tech candidate offers several advantages:
1. Access to a Global Talent Pool: Eradicating physical boundaries lets businesses access a massive tech talent reservoir globally. As a result, they can spot top-notch candidates having the exact abilities and know-how required for their tasks.
2. Cost Savings: Working remotely can greatly cut down on costs tied to having an office such as utilities and other bills. Companies can gain by hiring skilled folks from areas where the cost of living is less. This can mean lower wage demands but the same high standards.
3. Increased Productivity: Research tells us that people working from home often get more done. They have less interruptions and juggle work and life better. This rings especially true for tech experts. They need long, quiet stretches to finish difficult jobs.
4. Diverse Perspectives: Hiring people from around the world brings mixed views and notions, nurturing fresh thoughts and creativity. The tech industry really benefits from this diversity as it thrives on new strategies and unique problem-solving.
Strategies for Sourcing Remote Tech Talent
For successful remote tech hiring, firms need a planned method for finding skilled individuals. Here are a few important tactics:
1. Leverage Online Job Platforms: Check out job sites focused on remote work like Remote OK, We Work Remotely, and FlexJobs. Tech professionals who want remote work typically use these sites. This can boost your chances of finding the right candidates.
2. Utilize Social Media and Professional Networks: Web areas such as LinkedIn, Twitter, and GitHub are stock exchange assistants in finding distant tech pros. Be part of related groups, join chats, and post job listings to connect with more people.
3. Engage with Online Communities:Get involved with online tech forums and chat spaces like Stack Overflow, Reddit, and Hacker News. These platforms are popular amongst technology gurus. Such professionals might show interest in remote job opportunities.
4. Attend Virtual Tech Events: Virtual meetings like webinars, hackathons, and conferences open doors to mingle with tech experts. These often draw in proficient people looking to find out about job chances and to meet prospective bosses.
5. Offer Attractive Remote Work Policies: Emphasize your firm's distance work rules and perks in job ads. Having adaptable work schedules, work-at-home allowances, and chances for professional growth could make your establishment more attractive to remote tech applicants.
Best Practices for Hiring Remote Tech Candidates
After you spot possible recruits, your following move should be to enforce powerful hiring strategies for a fruitful work-from-home partnership:
1. Conduct Thorough Interviews: Combine video chats, skill tests, and character assessments to check applicants' abilities, background, and cohesion with company culture. This all-encompassing method guarantees applicants have the relevant technical prowess and can adapt well to working from home.
2. Assess Communication Skills: A team working remotely relies heavily on solid communication. In job interviews, it's vital to judge if job-seekers express clearly and briefly in speaking and writing. Seek out those who can convey their brainwaves and concepts well.
3. Test for Remote Work Readiness: Assess if applicants are prepared for tele commuting by asking about their past remote jobs, favorite software, and methods of handling their time. This would indicate their ability to stay organized and disciplined, which are essential for succeeding in remote work.
4. Provide a Realistic Job Preview: Let's show applicants what it truly looks like to work from home at our company. We'll talk about goals, how we measure success, and the things we give our staff to help them do well. Being open this way helps people choose wisely. It also gets us off to a great start for working together, even when we're apart.
5. Foster a Strong Onboarding Process: An organized intro period is key for bringing new tech workers on board who work from home. Give detailed teaching on every rule, tool, and process in the company. Pair them up with a guide or friend who can walk them through their tasks and make pals with other peers.
Conclusion
Remote work is changing how we do business. It's like a door opening to a world full of skilled tech experts. By smart searching and hiring well, firms can find remote tech stars. These recruits enrich the team with their skills, unique views, and work rate. Welcoming remote work makes it easier to reel in the best talent. Besides that, it primes a business for a successful future in our ever-growing, interconnected digital world.
0 notes