#sap grc
Explore tagged Tumblr posts
Text
SAP GRC Compliance Master and Risk Guardian
In today's fast-evolving business landscape, governance, risk management, and compliance (GRC) have become paramount for organizations aiming to mitigate risks and adhere to regulatory requirements. SAP GRC, a comprehensive toolset designed to manage these critical aspects, has seen increasing demand among professionals seeking to enhance their expertise in this domain. This surge in interest has subsequently led to a rise in SAP GRC online training offerings, designed to cater to the diverse needs of learners worldwide. Here, we delve into the myriad benefits of pursuing SAP GRC training, focusing on its online variants, and highlight why these programs are essential for aspiring and seasoned professionals alike.
Tailored Learning Experience
SAP GRC online training programs offer a customized learning experience, enabling learners to explore the course content at their own pace and convenience. Whether you're a beginner looking to understand the basics or a professional aiming to deepen your expertise, these courses provide varied content tailored to different proficiency levels.
Access to Global Expertise
Opting for SAP GRC online training in India or any other location grants access to world-class instructors and training centres renowned for their expertise in SAP GRC. This global exposure is invaluable, offering insights into international best practices and the latest industry trends.
Comprehensive Curriculum: The SAP GRC course content is meticulously designed to cover all essential aspects, from risk analysis and management to compliance and policy management. Specialized modules, such as SAP GRC contract management training, further enrich learners' understanding, equipping them with the skills needed to navigate complex GRC landscapes effectively.
Certification and Career Advancement
SAP GRC online certification serves as a testament to the holder's expertise and dedication to the field. These credentials are highly regarded by employers and can significantly enhance one's career prospects. Many training programs also offer guidance on SAP GRC training and placement, ensuring that learners are well-positioned to capitalize on job opportunities post-certification.
Cost-Effective Learning Solution
The SAP GRC training cost is often a concern for many aspirants. Online training programs address this by providing a cost-effective alternative to traditional classroom-based learning. With options ranging from free introductory courses to comprehensive paid programs, there's something to suit every budget.
Convenience and Flexibility
SAP GRC Online training offers unmatched flexibility, allowing learners to balance their professional commitments with their educational pursuits. With courses available 24/7, participants can schedule their learning around their personal and work life, making skill enhancement more accessible than ever.
In conclusion, SAP GRC online training presents a unique opportunity for professionals to sharpen their skills and advance their careers in the field of governance, risk management, and compliance. By choosing the right SAP GRC course and training center, participants can enjoy a range of benefits, from flexible learning schedules and access to expert knowledge to improved job prospects and certification. As businesses continue to prioritize GRC, the demand for skilled SAP GRC professionals is set to rise, making now the perfect time to embark on this rewarding learning journey.
For More Details Please Visit our Website - https://rhsofttech.com/sap-grc-online-training/
1 note
·
View note
Text
Enhanced Governance & Compliance with SAP Cloud IAG | Toggle Now

SAP Cloud Identity and Access Governance (IAG) stands as a transformative solution for enterprises, fortifying access control mechanisms across cloud environments. By implementing SAP Cloud IAG, organizations enhance security measures, streamline governance, and ensure compliance with regulations and internal policies. This comprehensive solution centralizes identity management, automates user lifecycle processes, and employs adaptive access strategies for real-time risk mitigation. It seamlessly integrates with diverse cloud platforms, optimizes user experience, and scales efficiently to meet evolving business needs. SAP Cloud IAG not only reduces operational costs through automation but also future-proofs identity governance strategies, ensuring enterprises remain resilient in the face of technological advancements and evolving security threats.
Read More: https://togglenow.com/services/sap-cloud-iag-services/
1 note
·
View note
Text
Navigate Compliance Challenges Seamlessly with SAP Process Control

ToggleNow offers specialized SAP Process Control services designed to strengthen your organization’s compliance framework. With in-depth expertise in SAP solutions, we provide end-to-end support, implementation, and optimization of SAP Process Control. Our focus extends beyond standard services, harnessing the power of this solution to automate compliance monitoring, risk identification, and mitigation, reducing costs, and enhancing efficiency.
What sets us apart is our tailored approach. We customize SAP Process Control to fit your unique business needs, crafting frameworks and workflows that maximize its potential in managing risks and ensuring regulatory compliance. Our adaptive strategies ensure readiness for future regulatory changes. Partner with ToggleNow to streamline compliance processes and fortify your organization’s compliance stance effectively.
Process Control Implementation:
ToggleNow specializes in seamless SAP Process Control implementation services, ensuring a smooth integration tailored to your organization’s needs. Leveraging our expertise, we guide you through the entire implementation journey, from initial planning and configuration to deployment. Our approach focuses on understanding your unique requirements, designing a roadmap, and executing a structured implementation strategy. This service ensures that your SAP Process Control system is set up efficiently, aligning with your compliance objectives and business processes.
1 note
·
View note
Text
Sap security and grc training institutes in ameerpet - I Grow Soft Hyderabad
I Grow Soft is the go-to destination for the best SAP GRC training institutes in Hyderabad. With our cutting-edge curriculum and experienced trainers, we offer a comprehensive learning experience to help you master SAP GRC concepts and techniques. Gain practical skills in risk management, access controls, and compliance frameworks, enabling you to enhance security and streamline governance processes within SAP environments. Choose our institute for the best SAP GRC training in Hyderabad and pave your way to a successful career in SAP Security and GRC.
I Grow Soft, Security And Grc Training In Hyderabad
Address: 7-1-619, A/31, SAP St, behind HMDA Maitrivanam, Kumar Basti, Gayatri Nagar, Srinivasa Nagar, Ameerpet, Hyderabad, Telangana 500016 Hours: Open 24 hours Phone: 8885503231

0 notes
Text
10 tips to safeguard your critical business data in SAP systems

Secure your Critical Business Data
Security and risk are becoming increasingly challenging as businesses become more connected. It requires data sharing between different systems, applications, and enterprises.
According to Forrester, companies will double their budgets for data strategy over the next five years and according to Gartner, transparency and traceability are among the Top Ten Strategic Technology Trends for 2022. Smart spaces, they claim, will offer better business opportunities.
It was found in another recent report by Onapsis that between 50,000 and 100,000 organizations use SAP systems that are vulnerable. An example that made the world aware of the importance of data security is the case with the New Zealand government. An immense data breach in which firearms, addresses, and names of gun owners were exposed led SAP itself to apologize to the government. There was no hacking involved in the breach, but 66 dealers got access to sensitive information because of a change in user access given to dealers participating in the buyback scheme.
“Between 50,000 to 100,000 organizations use SAP systems that are vulnerable.”
Apparently, SAP is working on various solutions to increase the security of data. In addition, it reminds clients that security is a collaborative effort, and emphasizes the importance of proper system configuration.
The importance of security in SAP
Data breaches and ransomware attacks are on the rise, and the global pandemic presents new opportunities for cybercriminals. Many employees today access corporate resources through virtual private networks (VPNs). The shift to remote work has resulted in a more permissive VPN policy, which compromises corporate networks in an indirect way.
There is a need for IT security teams to accomplish more with less budget or with the same budget. It is part of their job responsibility to manage day-to-day IT and security operations, find and retain skilled security talent, identify and address security capability gaps, and maximize the return on investment (ROI).
Almost seven out of ten organizations do not place a high priority on securing their SAP systems. Considering the recent spike in cyber-attacks, it is essential to secure SAP systems. We have put together a list of 10 tips you can use immediately to secure your critical business data in SAP system.
1. Own it – Don’t blame
When a security breach occurs, who is responsible? A recent survey by Onapsis found that half of the respondents believe SAP is to blame for security breaches – not anyone within their own organization. Another 30% believe that no one is responsible. A small percentage of people believe that the CIO or CISO is responsible for a security breach.
50% blame SAP for security breaches
30% have no idea
20% say it is CIO/CISO’s responsibility
63% of C-Level executives underestimate the risks associated with insecure SAP applications
The dangers associated with insecure SAP applications are underestimated by 63% of C-level executives.
2. Regularly update the EHP & SPS
One of the most significant steps to staying secure is to keep your system up to date. Enhancement packages are delivered by SAP to deliver new innovations/functionality or “enhancements” to customers without disruption. Ensure you have the latest enhancement packs installed, and that you aren’t several versions behind. It is always risky to be a first adopter, but it is also imperative to avoid falling behind (n-1 is always recommended). Technology and computer security are constantly improving, so it is important to keep your system up to date with patches, fixes, updates, and enhancement packs.
As part of its Support Package Stacks, SAP releases periodic security solutions. The Support Package Stacks are patches for a given product that should be applied together. It is recommended that these stacks be applied at least once a year, and SAP specifies the maintenance schedule on its website. In addition, ToggleNow can help you identify your system’s most critical SPSs.
3. The Right SODs make a difference
As business processes rapidly evolve, employee roles and responsibilities are also changing. By establishing boundaries between roles assigned to an employee and conflicts of interest that may arise from the employee’s responsibilities, segregation of duties aims to reduce internal fraud risks. For example, one employee processes a PO while another verifies and approves it. This adds more control and prevents payments to ‘fake’ vendors.
It is becoming more common for mature organisations to look for ways to improve Segregation of Duties management while reducing costs. It is imperative for businesses to integrate an advanced, quick, and easy-to-install Access Management tool that fits with their systems. This will avoid conflicts after an employee’s role or tasks change.
This can be achieved either by implementing the SAP GRC Access Control solution or ToggleNow’s SoD Analysis solution for SAP. The SAP Security Assessment services provided by ToggleNow will identify the right solutions for your organization. Additionally, if you have SAP GRC implemented, explore the various SAP GRC services that are offered by us.
With the help of our SMEs, you will be able to implement the right separation of duties strategies and ensure that you comply with the various regulations and mandates.
4. Ensure the quality of your code
SAP systems typically have over 30 percent proprietary code, depending on the industry. Statistics indicate that one critical security defect occurs for every 1,000 lines of ABAP code.
It is possible that SAP system performance will be adversely affected. It is estimated that the average SAP system contains 2,151 risks, and 70% of enterprises fail to audit their ABAP custom code for compliance and security.
It is possible to simplify the security process for your code. It is no longer necessary for organizations to invest time, money, and manpower in major security projects. An analysis of your code beforehand will enable you to identify and prioritize any risks and issues before you begin an upgrade.
To ensure security, performance, maintainability, robustness, and compliance with ABAP standards, integrate coding and quality assurance into a single activity.
Finally, you should only keep the custom code you need. It introduces unnecessary risks and increases the amount of effort needed for unnecessary code corrections when redundant unused custom code is used.
Wondering how to handle the situation? Here is a solution – SAP Solution Manager CCLM is a fantastic solution that addresses the majority of these requirements. Refer to this blog
5. Implement SAP Solution Manager – Security Optimization Service (SOS)
We are often asked by clients what tools are available to check the security of SAP systems? Additionally, to Early Watch Alert (EWA), SAP Solution Manager (SOLMAN) has a Security Optimization Service (SOS) report that focuses on security.
Security Optimization Service for the SAP NetWeaver Application Server ABAP checks the security of your SAP system(s) and perform the following checks:
• Basis administration check • User management check • Super users check • Password check • Spool and printer authorization check • Background authorization check • Batch input authorization check • Transport control authorization check • Role management authorization check • Profile parameter check • SAP GUI Single Sign-On (SSO) check • Certificate Single Sign-On (SSO) check • External authentication check
You’ll need the latest version of SOLMAN and the latest support pack to set this up. The managed system must also be configured and setup in SOLMAN without any errors and the instance is correctly defined in LMDB. (Status Green). Additionally, the OS collector must be running on your target instances and database.
It is important, however, to answer the following before setting up the SOS:
• Does your organization have the capacity to manually review those reports and act on each recommendation? • It is set correctly so that your team has ample time to review and act on the reports.
Read ToggleNow’s success story on this subject. We have implemented Solution Manager 7.2 for one of our clients who is a leading refractory company in India since 1958.
6. Regular health checks keep the system healthy
Yes, you heard that right. Humans and systems alike benefit from regular health checks. Ponemon Institute reports that organizations lack visibility “into the security of SAP applications and lack the expertise to detect, prevent, and respond to cyberattacks quickly.”
Early detection is the key to staying healthy or secure. A frequent ERP system check helps you get a comprehensive picture of your ERP landscape before making changes and identifying areas for improvement. This is just like healthy people need annual checkups and preventative medicine to stay healthy and detect problems early. Regular health checkups can identify security gaps. Additionally, EWA and SOS reports provide an in-depth analysis of the system. According to experts’ recommendations, SAP Solution Manager must be configured to support these modules.
7. Implement an Antivirus scan
How confident are you that the documents attached in SAP are virus-free? A vulnerable code might be included in a file your users use/attach in SAP, allowing hackers to gain access.
If you use SAP software, you should use a virus scanner to protect against computer viruses, and SAP recommends this. However, SAP does not investigate, recommend, or release antivirus software as part of its server product validation program.
Many anti-virus software packages protect your SAP deployments using Deep Security, protecting critical information from threats such as malware, cross-site scripting, and SQL injections.
A Virus Scan Adapter (VSA) must be installed on the host before a Deep Security scan can be performed. SAP note 2081108 explains how to set up and configure the VSA system and SAP note 1494278 provides a list of the AV products that are supported.
Additionally, SAP administrators can define the types of documents that are allowed based on various policies. After selecting the right AV product, this can be determined.
8. Implement re-certification processes
Reviews of dormant IDs and dormant roles make a great start. Regularly reviewing the user IDs and deactivating those that are no longer needed is always recommended. This will not only increase the application’s security but also reduce licensing costs. If you already have an SOP in place and are still performing this activity manually, here is a solution for you. ToggleNow’s UserSentry automates both dormant ID review and Role review by taking the appropriate action according to defined rules. Thus, you can comply with a critical audit requirement.
9. Implement additional Security measures
In addition, we recommend that additional security measures be implemented. Back then, experts used to advise setting up complex password policies like keeping password lengths between 8-12 characters and forcing users to change their passwords frequently. Keeping strong passwords alone is no longer sufficient considering technological advancements.
It is recommended to implement additional security measures such as 2-factor authentication (2FA) or multifactor authentication (MFA), validating a user’s machine ID (aka mac ID) at log-in, and adding geofencing validations, verifying the availability of anti-virus software, checking the firewall status, etc. All these features are included in ToggleNow’s UserSentry application, which helps next-generation enterprises implement them quickly.
10. Transform your business with digital technology
The waterfall era has ended. Agility has won. By embracing digital transformation and getting fast and frequent feedback, organizations can respond quickly to critical security issues. By doing this, security issues aren’t ignored, and crises can be averted. If you are worried about the Subject matter expertise and resource availability, ToggleNow can step in and take over this critical piece. The FourEdge Service offering is a great reliever for many organizations that are seeking to start their GRC transformation journey. Remember to be in the race, or else your competitors will take over.
These are the best tips to secure your critical business data in SAP systems. Talk to our SMEs today and leave rest on us for your business data security.
Read More: https://togglenow.com/blog/secure-your-critical-business-data/
#SAP SOD analysis#SAP SOD analysis tool#SAP SOD analyzer#GRC access control#SAP threat detection#SAP GRC automation
0 notes
Text
When to Redesign SAP Roles: During ECC or Post-Migration to S/4HANA or Rise with SAP
Migrating to SAP S/4HANA or adopting RISE/GROW with SAP is a strategic milestone for organizations aiming to modernize their ERP landscape. However, one critical consideration often overlooked during these transitions is the redesign of SAP roles. The timing of this redesign can significantly influence the success of the migration and the overall efficiency. Should you redesign roles during the ECC phase or wait until after the migration to S/4HANA? This blog explores the key factors driving this decision and introduces the S.M.A.R.T framework—a modern approach to SAP role redesign that ensures compliance, efficiency, and business alignment.
Understanding the Need for Role Redesign
SAP roles are pivotal in defining user access, ensuring compliance, and maintaining operational efficiency. Over time, roles in ECC systems often become bloated with unused authorizations or misaligned with current business needs. This can lead to:
Compliance Risks: Excessive authorizations increase the risk of segregation of duties (SoD) violations.
Migration Complications: Legacy roles with redundancies can complicate the migration process to S/4HANA.
Operational Costs: Since the licensing model is based on assignment and not by usage in S/4HANA and RISE, you may need to procure more licenses than required.
A role redesign ensures clean, streamlined, and compliant access structures, setting the stage for a smooth transition and efficient system post-migration.
ls.ECC vs. S/4HANA: When to Redesign Roles?
Aspect
Redesign During ECC
Redesign Post-Migration to S/4HANA
Compliance
Proactively addresses SoD conflicts and access risks.
Allows compliance alignment with new functionalities post-migration.
Migration Complexity
Simplifies migration with clean and optimized roles.
Reduces redundant effort, focusing only on relevant roles in the new system
Alignment with New Features
May require rework later to incorporate S/4HANA-specific functionalities.
Ensures roles are tailored to new modules, Fiori apps, and processes.
Timeline and Resources
Increases project timelines due to pre-migration workload.
Defers redesign efforts, potentially affecting initial system efficiency.
Business Process Analysis
Limited to existing ECC processes, with potential misalignment after migration.
Better aligned with current and optimized business processes in S/4HANA.
Redesigning SAP Roles with RISE with SAP
If you are moving to RISE with SAP, it is advisable to conduct a complete role redesign during the ECC phase. Once the migration is complete, perform a retrofit to align roles with the cloud-specific requirements introduced by RISE. This approach addresses the unique security, integration, and scalability considerations of a cloud-oriented transformation. You might have many questions at this juncture – What is the best approach? Which tools must be considered? Are there any accelerators that can be used? Can we use stock ready/ready to deploy role structures?
Challenges with Stock Ready Rulesets
Many system integrators offer pre-packaged or stock-ready rulesets as part of their role redesign services. While these rulesets might appear to save time and effort, they often come with significant challenges, making them unsuitable for many businesses. Here’s why the stock-ready approach is not recommended:
Lack of Customization: Stock-ready rulesets are designed to be generic and may not align with the specific needs of your industry or business processes. This can result in inadequate or excessive authorizations.
Compliance Risks: These pre-packaged rulesets may not fully address industry-specific compliance requirements, leaving gaps that could lead to audit findings or regulatory penalties.
Misalignment with Business Processes: Every organization has unique workflows and processes. Stock-ready rulesets may not account for these nuances, leading to inefficiencies and user frustrations.
Post-Implementation Challenges: Organizations often need to spend additional time and resources customizing these rulesets post-implementation, negating the perceived benefits of a quick deployment.
Instead of relying on stock-ready rulesets, organizations should invest in a tailored role redesign approach. This ensures that roles are aligned with specific business processes, compliance requirements, and future scalability needs, delivering long-term value and efficiency. This is where S.M.A.R.T approach/framework can be a life saver.
The S.M.A.R.T Role Redesign Framework
At ToggleNow, we leverage the S.M.A.R.T framework for SAP role redesign. This approach ensures that roles are:
Simplified: Designed to reduce complexity while maintaining operational effectiveness.
Mitigated for Risks: Focused on eliminating SoD conflicts and maintaining regulatory compliance.
Aligned with Business Tasks: Task-based roles ensure that access permissions directly support specific workflows.
Responsive to Change: Built to adapt seamlessly to future business or technical changes.
Transparent and Optimized: Designed with a focus on license optimization to eliminate unnecessary expenditures.
This framework delivers roles that are not only secure but also cost-effective and easy to manage
ToggleNow Advantage
ToggleNow brings a unique value proposition to SAP role redesign initiatives, ensuring a seamless and efficient process tailored to your business needs. Here’s why we stand out:
Customized Solutions: Unlike stock-ready rulesets, ToggleNow develops tailored role designs aligned with your specific business processes, compliance requirements, and industry standards.
Deep Expertise: With extensive experience in SAP role redesign, ToggleNow combines technical proficiency with a deep understanding of regulatory compliance and security best practices.
Innovative Tools:ToggleNow leverages proprietary tools such as Verity, Optimus and accelerators such as xPedite to streamline role redesign, risk analysis, and validation, ensuring faster project delivery.
Focus on Scalability:Our approach ensures that the roles we design are not only compliant and efficient but also scalable, adapting to your future business growth.
Proven Track Record:Trusted by leading organizations, ToggleNow has successfully delivered role redesign projects across diverse industries, enabling smoother migrations and enhanced system performance.
By partnering with ToggleNow, organizations can confidently navigate their SAP transitions, optimizing roles to drive operational excellence and long-term success.
Conclusion
The decision to redesign SAP roles during ECC or post-migration to S/4HANA or RISE with SAP depends on your organization’s priorities, resources, and timeline. Redesigning during ECC can simplify the migration process, while post-migration redesign allows alignment with new functionalities. For RISE with SAP, role redesign becomes even more critical to address cloud-specific requirements.
Moreover, organizations should avoid the pitfalls of stock-ready rulesets and opt for a customized approach that aligns with their unique requirements. By investing in a well-planned redesign, organizations can unlock the full potential of SAP S/4HANA or RISE with SAP, driving operational excellence and business growth.
Read more: https://togglenow.com/blog/redesign-sap-roles-ecc-or-s-4hana/

#SAP Risk Management#SAP access risk analysis tool#SAP GRC access control solution#SAP segregation of duties automation#SoD risk analysis for SAP
0 notes
Text
youtube
Enhance Your Knowledge with SAP GRC Training in Mumbai
Elevate your expertise with our SAP GRC training in Mumbai. Our course offers in-depth knowledge of governance, risk, and compliance, equipping you with the skills to manage SAP systems effectively. Learn from industry experts, gain practical experience, and boost your career prospects. Enroll now to advance your understanding and become proficient in SAP GRC.
0 notes
Text
SAP GRC Securities Course
SAP GRC Securities with Placement Assistants. NEW BATCH ONLINE DEMO URATION: 2 MONTHS For More Details Fill this form- https://forms.gle/U1uUyQERx8jwVJYGA Visit Our Website: https://www.versionit.org/sap-hr-grc-securities-training…
@9030163724,9014629911

0 notes
Text
Enjoy the top benefits of SAP GRC Services with VisionSoft Consulting Inc.! Being a leading company, we will give you full assistance to upgrade your SAP GRC system.
For more information, you can visit our website https://visionsoft.com/ and call us at +1 (732) 532-9164
1 note
·
View note
Text
SAP IAG for Enhanced Access Governance | Toggle Now
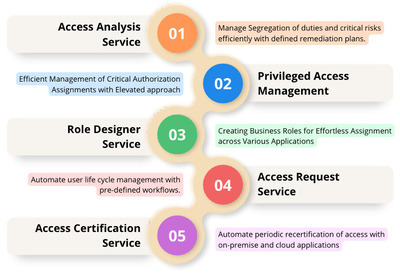
Understanding SAP Identity Access Governance (IAG)
SAP IAG serves as a comprehensive framework within the SAP ecosystem, designed to manage user access, control risks, and ensure compliance with regulatory standards. Its primary focus lies in governing user access across various SAP applications that are hosted on-premise and cloud along with other non-sap systems such as Azure ID, and platforms.
Key Components of SAP IAG
SAP IAG offers 5 key services as outlined in the below figure:
1. Access Analysis Service:
Similar to SAP GRC, SAP IAG also has powerful capabilities to assess and mitigate access risks associated with user permissions. It conducts thorough analysis, identifying potential risks and vulnerabilities within the access structure. A clear definition of risks are displayed for each of the users enabling the Business Owners to take better decisions on managing the risks for each of the user.
2. Privileged Access Management (PAM) Service:
PAM Service is similar to GRC Access Control Emergency Access Management aka Firefighter, a specialized solution designed to manage critical access by controlling, monitoring, and securing the SAP systems from unauthorized changes using privileged accounts. It focuses on a more controlled assignment and management of accesses which has business impact. PAM ensure compliance with regulatory standards, thereby fortifying the overall security posture of an enterprise.
1 note
·
View note
Text
SAP GRC REPORT & CONTROL AUTOMATION | Frequently Asked Questions

Is GAMS360 a web-based application?
GAMS is built on SAP UI5, an effective engine for creating rich HTML pages with pre-defined controls, models and data bindings. GAMS can be implemented either on an Embedded SAP Gateway system or a Central Hub system.
Does GAMS360 supports custom control & report cards?
Absolutely! GAMS360 is powered with 100+ pre-defined SAP Security Baseline controls, SAP GRC Baseline controls, SAP Fraud management controls, SAP ITGC Controls and many more. If required, our team can customize it further to our client’s requirements.
Can GAMS360 be integrated with SAP GRC Access Control 10x/12?
Yes. Even though GAMS360 is an individual reporting application, it is built on SAP GRC basics. It can be a central system for all the reporting purpose. The standard S GRC Access Control can be integrated into the GAMS360 application to make it a single point application.
How much time it would require implementing GAMS360 application?
The timelines required to implement GAMS360 application is depended on the SAP landscape. In general, the application requires 7–10 working days to implement and configure. Our team will provide a detailed implementation plan before starting every project.
1 note
·
View note
Text
Join SAP GRC at SAP Masters
✅ 15+ Years of Experienced Faculty ✅ 100% Placement Program ✅ Offline & Online Training Available ✅ Free Server Access ✅ Soft Copy Material
For WhatsApp https://wa.me/919493193959 Or Call 📞 +91 9493193 959
#sapgrc#SAP#GRC#SAPMasters#SAPTraining#SAPGRCTraining#saptrainingbangalore#sapgrctrainingbangalore#placements#sapfreedemo#saptrainingavailable#sapinstitute#sapmasterstraininginstitute#sapmasterstraininginstitutebangalore#softwareengineer#grcinstitute#SAPModules#software#bangalore#NammaBengaluru#nammabangaluru#itbengaluru#sapbangalore#sapbangalorejobs#jobseekers#job#career#students#carrergap
0 notes
Text

This institute provides in-depth instruction on SAP GRC modules, including Access Control, Process Control, and Risk Management. With experienced trainers, practical exercises, and real-time project experience,
0 notes
Text
5 Hidden SAP GRC Pitfalls That Could Jeopardize Your Compliance Strategy
1. “One-Size-Fits-All” RuleSet Syndrome
Many organizations implement SAP GRC with out-of-the-box rule sets and assume they’re covered and are completely Sox/SoD compliant. The problem? Standard rule sets don’t always reflect the unique business processes and risks of an enterprise. They must be utilized as a baseline.
Example: A global company using a generic SoD rule set might flag conflicts that aren’t actually risks in their specific operations, leading to unnecessary firefighting and role redesign efforts.
What is the solution? It is always recommended to tailor the rule set to align with your business needs. Involve process owners and auditors to ensure relevance. Disable those which are not relevant and add the ones what needs to be part of the rule set. For example, your custom transaction codes.
2. Over-Reliance on Automated Controls
Yes, automation is powerful, but blindly trusting automated GRC controls without proper oversight is a recipe for disaster.
Example: Automated access reviews might seem great, but if managers are just clicking the approval button without understanding the risk, you’re inviting compliance issues.
What is the solution? Combine automation with human intelligence. Train reviewers on what they’re approving and implement periodic audits.
3. The “Too Many Firefighters” Problem
Firefighter (emergency access) access is meant for temporary, critical access. But in many companies, they become a backdoor for permanent privileged access. I’ve seen in some instances where the FFIDs have SAP_ALL, SAP_NEW assigned
Example: If every second user has firefighter access “just in case,” then what’s really being controlled?
What is the solution? Reduce firefighter usage with strict policies. Ensure that the Firefighter IDs have limited and relevant access, not SAP_ALL. Look at how often your users are asking for such access. Set expiration dates, and enforce approvals before access is granted. A detailed review is must after the usage.
4. Role Design Nightmares
Ever seen a single SAP role with 500+ transaction codes? It happens more often than you’d think. Poorly designed roles create access chaos, security risks, and audit nightmares.
Example: A company that grants “Display All” access thinking it’s harmless—only to realize some reports contain sensitive payroll data.
What is the solution? Follow a least privilege approach. Display tcodes does possess risks. Design roles based on business functions, not user demands and assumptions. And, no, giving everyone SAP_ALL is not a solution!
5. The “Check-the-Box” Compliance Trap
Many organizations treat GRC as a compliance checklist rather than a risk mitigation strategy. The result? A false sense of security.
Example: An enterprise that passes an audit but later discovers a critical access loophole exploited by an insider threat.
What is the solution? Shift from a compliance-first mindset to a risk-first approach. Ask, “What’s the real-world impact of this control?” rather than just checking off audit items.
Final Thoughts: GRC is Not Just About Tools, It’s About Mindset
SAP GRC isn’t just about implementing Access Control, Process Control, or Risk Management modules—it’s about adopting a security and compliance culture. The best GRC strategies combine technology, process rigor, and human intelligence to create a resilient, risk-aware organization.
Readmore: https://togglenow.com/blog/sap-grc-hidden-pitfalls/

#SAP Risk Management#SAP access risk analysis tool#SAP GRC access control solution#SAP segregation of duties automation#SoD risk analysis for SAP
0 notes
Text
0 notes