#sigcomm
Explore tagged Tumblr posts
Text
#1yrago Half a billion IoT devices inside of businesses can be hacked through decade-old DNS rebinding attacks
In 2008, a presentation at the RSA conference revealed the existence of "DNS rebinding attacks," that used relatively simple tactics to compromise browsers; a decade later, Berkeley and Princeton researchers announced a paper on DNS rebinding attacks against consumer devices (to be presented at August's ACM SIGCOMM 2018 Workshop on IoT Security and Privacy), while independent researcher Brannon Dorsey published similar work.
Both the ACM paper and Dorsey's paper are at pains to point out that they had only investigated a small minority of the IoT vendors, and that there were probably a lot more products that were vulnerable to a decade-old attack.
They were right.
A new paper from Armis security reveals another half-billion IoT devices in corporate environments that can be taken over with DNS rebinding attacks: "87 percent of switches, routers and access points; 78 percent of streaming media players and speakers; 77 percent of IP phones; 75 percent of IP cameras; 66 percent of printers; and 57 percent of smart TVs."
Just a reminder: this is all ten years after DNS rebinding came to light.
https://boingboing.net/2018/07/24/decade-old-vulns.html
3 notes
·
View notes
Text
World's first link layer protocol brings quantum internet closer to a reality



Using the link layer protocol, higher-layer software can request the creation of entanglement without needing to know which quantum hardware system is in the box. Credit: QuTech/Scixel
Researchers from QuTech have achieved a world’s first in quantum internet technology. A team led by Professor Stephanie Wehner has developed a so-called link layer protocol that brings the phenomenon of quantum entanglement from experimental physics to a real-world quantum network. This brings closer the day when quantum internet can become a reality, delivering applications that are impossible to achieve via classical internet. The work was presented today at ACM SIGCOMM.
In classical computing, a collection of software layers referred to as the network stack allows computers to communicate with each other. Underlying the network stack are communications protocols, such as the internet protocol or HTTP. Stephanie Wehner explained that one essential protocol used by a network is the link layer protocol, which overcomes the problems caused by imperfect hardware: “All of us use classical link layer protocols in everyday life. One example is Wi-Fi, which allows an unreliable radio signal—suffering from interruptions and interference—to be used to transmit data reliably between compatible devices.”
A quantum network, based on transmission of quantum bits, or qubits, requires the same level of reliability. Stephanie Wehner says, “In our work, we have proposed a quantum network stack, and have constructed the world’s first link-layer protocol for a quantum network.”
It turns out that existing classical protocols cannot help in the quantum world. One challenge is presented by differences between the technologies used. Stephanie Wehner: “Currently, qubits cannot be kept in memory for very long. This means control decisions on what to do with them need to be taken very quickly. By creating this link layer protocol, we have overcome obstacles presented by some very demanding physics.”
There are also some fundamental differences between a future quantum internet and the internet that we see today. Stephanie Wehner said that two quantum bits can be entangled: “Such entanglement is like a connection. This is very different to the situation for classical link layer protocols where we typically just send signals. In that case, there is no sense of connection built in at a fundamental level.”
Quantum internet
The phenomenon of entanglement forms the basis of a quantum internet. When two fundamental particles are entangled, they are connected with each other in such a way that nothing else can have any share of this connection. Researcher Axel Dahlberg said that this enables a whole new range of applications “Security is one important application. It is physically impossible to eavesdrop on an entangled network connection between two users. To give another example, the technology also allows improved clock synchronization, or it can join up astronomical telescopes that are a long way apart, so they act as a huge single telescope.”
Researcher Matthew Skrzypczyk said that an important feature of the proposed quantum network stack and the link layer protocol is that it any future software written using the protocol will be compatible with many quantum hardware platforms. “Someone who makes use of our link layer protocol no longer needs to know what the underlying quantum hardware is. In our paper, we study the protocol’s performance on Nitrogen-Vacancy centers in diamond, which are essentially small quantum computers. However, our protocol can also be implemented on Ion Traps, for example. This also means our link layer protocol can be used in the future on many different types of quantum hardware.”
Building a quantum network system
Stephanie Wehner said that the next step will be to test and demonstrate a new network layer protocol using the link layer protocol: “Our link layer protocol allows us to reliably generate entanglement between two network nodes connected by a direct physical link, such as a telecom fiber. The next step is to produce entanglement between network nodes which are not connected directly by a fiber, using the help of an intermediary node. In order to realize large scale quantum networks, it is important to go beyond a physics experiment, and move towards building a quantum network system. This is one of the objectives EU-funded Quantum Internet Alliance (QIA).”
Scientists make first ‘on demand’ entanglement link
More information: A Link Layer Protocol for Quantum Networks, by Axel Dahlberg et al., Preprint: arxiv.org/abs/1903.09778
Provided by Delft University of Technology
Citation: World’s first link layer protocol brings quantum internet closer to a reality (2019, August 20) retrieved 21 August 2019 from https://phys.org/news/2019-08-world-link-layer-protocol-quantum.html
This document is subject to copyright. Apart from any fair dealing for the purpose of private study or research, no part may be reproduced without the written permission. The content is provided for information purposes only.
New post published on: https://www.livescience.tech/2019/08/21/worlds-first-link-layer-protocol-brings-quantum-internet-closer-to-a-reality/
1 note
·
View note
Text
Direction via indirection

Evolute workshop 2003, University of Surrey, Guildford, UK (2003) Host Identity Protocol: Achieving IPv4 – IPv6 handovers without tunneling. Jokela, P., Nikander, P., Melen, J., Ylitalo, J., Wall, J. Johnson, D.B., Perkins, C., Arkko, J.: Mobility support in IPv6. In: Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC’03), 3, pp. Henderson, T.R., Ahrenholz, J.M., Kim, J.H.: Experience with the Host Identity Protocol for secure host mobility and multihoming. Gurtov, A., Korzun, D., Nikander, P.: Hi3: An efficient and secure networking architecture for mobile hosts. Gurtov, A., Koponen, T.: Hi3 implementation for Linux (2005). 33(4), 313–321 (2003)įord, B.: Unmanaged Internet Protocol: taming the edge network management crisis. ACM, New York (2004)Ĭlark, D., Braden, R., Falk, A., Pingali, V.: FARA: Reorganizing the addressing architecture. In: Proceedings of ACM SIGCOMM’04, pp. 343–352. UCB/CSD-03-1242, University of California, Berkeley (2003)īalakrishnan, H., Lakshminarayanan, K., Ratnasamy, S., Shenker, S., Stoica, I., Walfish, M.: A layered naming architecture for the internet. This process is experimental and the keywords may be updated as the learning algorithm improves.Īdkins, D., Lakshminarayanan, K., Perrig, A., Stoica, I.: Towards a more functional and secure network infrastructure. These keywords were added by machine and not by the authors. Our results show that the Hi3 control plane can support a large number of mobile hosts with acceptable latency. We apply the model to quantify the performance of the Hi3 control plane. The model can be used for a first approximation study of a large-scale Internet control plane before its deployment. In this chapter, we propose a simple model for bounds of size and latency of the Hi3 control plane for a large number of clients and in the presence of DoS attacks. Although an Hi3 prototype is implemented and tested on PlanetLab, scalability properties of Hi3 for a large number of hosts are unknown. The architecture is well-suited for mobile hosts given the support for simultaneous host mobility, rendezvous and multi-homing. Hi3 combines efficient and secure end-to-end data plane transmission of HIP with robustness and resilience of i3. The Host Identity Indirection Infrastructure ( Hi3) is a general-purpose networking architecture, derived from the Internet Indirection Infrastructure ( i3) and the Host Identity Protocol (HIP).

0 notes
Text
The PETRAS Internet of Things Research Hub
https://www.petrashub.org/outputs/
Ahlfeldt, G., Koutroumpis, P., & Valletti, T. (2017). Speed 2.0: Evaluating Access to Universal Digital Highways. Journal of the European Economic Association, 15(3), 586–625. Retrieved from http://dx.doi.org/10.1093/jeea/jvw013
Akmal, H., & Coulton, P. (2018). Using Heterotopias to Characterise Interactions in Physical/Digital Spaces. Retrieved from http://eprints.lancs.ac.uk/123792/
Alberts, G., Gurguc, Z., Koutroumpis, P., Martin, R., Muûls, M., & Napp, T. (2016). Competition and norms: A self-defeating combination? Energy Policy, 96, 504–523. Retrieved from https://spiral.imperial.ac.uk/bitstream/10044/1/33898/9/Competition and norms.pdf
Aldrich, R. J., & Richterova, D. (2018). Ambient accountability: intelligence services in Europe and the decline of state secrecy. West European Politics, 41(4), 1003–1024. http://doi.org/10.1080/01402382.2017.1415780 Anthi, E., Williams, L., & Burnap, P. (2018). Pulse: An adaptive intrusion detection for the Internet of Things. In Living in the Internet of Things: Cybersecurity of the IoT – 2018 (pp. 1–4). http://doi.org/10.1049/cp.2018.0035
Anthonysamy, P., Rashid, A., & Chitchyan, R. (2017). Privacy Requirements: Present & Future. In Proceedings of the 39th International Conference on Software Engineering: Software Engineering in Society Track (pp. 13–22). Piscataway, NJ, USA: IEEE Press. http://doi.org/10.1109/ICSE-SEIS.2017.3
Arapinis, M., Liu, J., Ritter, E., & Ryan, M. (2017). Stateful applied pi calculus: Observational equivalence and labelled bisimilarity. Journal of Logical and Algebraic Methods in Programming, 89, 95–149. http://doi.org/https://doi.org/10.1016/j.jlamp.2017.03.001
Asuquo, P., Cruickshank, H., Morley, J., Ogah, C. P. A., Lei, A., Hathal, W., … Sun, Z. (2018). Security and Privacy in Location-Based Services for Vehicular and Mobile Communications: An Overview, Challenges and Countermeasures. IEEE Internet of Things Journal, 1. http://doi.org/10.1109/JIOT.2018.2820039
Asuquo, P., Cruickshank, H., Ogah, C. P. A., Lei, A., & Sun, Z. (2018). A Distributed Trust Management Scheme for Data Forwarding in Satellite DTN Emergency Communications. IEEE Journal on Selected Areas in Communications, 36(2), 246–256. http://doi.org/10.1109/JSAC.2018.2804098
Bao, S., Hathal, W., Cruickshank, H., Sun, Z., Asuquo, P., & Lei, A. (2018). A lightweight authentication and privacy-preserving scheme for VANETs using TESLA and Bloom Filters. ICT Express. http://doi.org/10.1016/j.icte.2017.12.001
Beck, S., Finney, J., & Knowles, B. H. (2018). How Freya Built Sharkie: Initial explorations into the safety, security, and privacy concerns of children’s IoT devices. In London Computing Education Research Symposium. Retrieved from http://eprints.lancs.ac.uk/126151/
Binns, R. (2017). Fairness in Machine Learning: Lessons from Political Philosophy. ArXiv Preprint ArXiv:1712.03586. Retrieved from https://arxiv.org/abs/1712.03586
Binns, R., Van Kleek, M., Veale, M., Lyngs, U., Zhao, J., & Shadbolt, N. (2018). “It’s Reducing a Human Being to a Percentage”: Perceptions of Justice in Algorithmic Decisions. In Proceedings of the 2018 CHI Conference on Human Factors in Computing Systems (p. 377:1–377:14). New York, NY, USA: ACM. http://doi.org/10.1145/3173574.3173951
Blackstock, J. (2018). Standardising a Moving Target: The Development and Evolution of IoT Security Standards. IET Conference Proceedings, 24 (9 pp.)-24 (9 pp.)(1). Retrieved from http://digital-library.theiet.org/content/conferences/10.1049/cp.2018.0024
Blythe, J. M., Michie, S., Watson, J., & Lefevre, C. E. (n.d.). Internet of Things in Healthcare: Identifying key malicious threats, end-user protective and problematic behaviours. Retrieved from https://www.ucl.ac.uk/behaviour-change/events/presentations-17/blythe.pdf
Blythe, J. M., & Lefevre, C. E. (2017). Cyberhygiene Insight Report. Retrieved from https://iotuk.org.uk/wp-content/uploads/2018/01/PETRAS-IoTUK-Cyberhygiene-Insight-Report.pdf
Boyes, H., Hallaq, B., Cunningham, J., & Watson, T. (2018). The industrial internet of things (IIoT): An analysis framework. Computers in Industry, 101, 1–12. http://doi.org/https://doi.org/10.1016/j.compind.2018.04.015
Bradbury, M., & Jhumka, A. (2017). Understanding source location privacy protocols in sensor networks via perturbation of time series. In IEEE INFOCOM 2017 – IEEE Conference on Computer Communications (pp. 1–9). http://doi.org/10.1109/INFOCOM.2017.8057122
Bradbury, M., & Jhumka, A. (2017). A Near-Optimal Source Location Privacy Scheme for Wireless Sensor Networks. In 2017 IEEE Trustcom/BigDataSE/ICESS (pp. 409–416). http://doi.org/10.1109/Trustcom/BigDataSE/ICESS.2017.265
Bradbury, M., Jhumka, A., & Leeke, M. (2018). Hybrid online protocols for source location privacy in wireless sensor networks. Journal of Parallel and Distributed Computing, 115, 67–81. http://doi.org/https://doi.org/10.1016/j.jpdc.2018.01.006
Brass, I. C. (2018). Standardising IoT Security: Implications for Digital Forensics. Digital Forensics Magazine, (35), 44–48. Retrieved from http://discovery.ucl.ac.uk/10050054/13/Brass_BRA001-pdf.pdf
Brass, I. C., Sowell, J., Carr, M., & Blackstock, J. (2017). The Role of Transnational Expert Associations in Governing the Cybersecurity Risks of the Internet of Things. International Public Policy Association. Retrieved from http://discovery.ucl.ac.uk/10054015/1/59530f6763ae8.pdf
Brass, I. (2017). Cybersecurity and Liability in Autonomous and Intelligent Transport.
Brass, I., Tanczer, L., Maple, C., Blackstock, J., & Carr, M. (2018). Unbundling the emerging cyber-physical risks in connected and autonomous vehicles. Retrieved from https://alerts.pinsentmasons.com/rs/emsdocuments/Future-of-the-Car-Whitepaper-Pinsent-Masons.pdf
Breza, M., Tomic, I., & McCann, J. (2018). Failures from the Environment, a Report on the First FAILSAFE Workshop. SIGCOMM Comput. Commun. Rev., 48(2), 40–45. http://doi.org/10.1145/3213232.3213238
Bures, T., Weyns, D., Schmer, B., Tovar, E., Boden, E., Gabor, T., … Tsigkanos, C. (2017). Software Engineering for Smart Cyber-Physical Systems: Challenges and Promising Solutions. SIGSOFT Softw. Eng. Notes, 42(2), 19–24. http://doi.org/10.1145/3089649.3089656
Calvo, J. L., Tindemans, S. H., & Strbac, G. (2016). Incorporating failures of System Protection Schemes into power system operation. Sustainable Energy, Grids and Networks, 8, 98–110. Retrieved from https://www.sciencedirect.com/science/article/pii/S2352467716301242
Cath, C., Wachter, S., Mittelstadt, B., Taddeo, M., & Floridi, L. (2018). Artificial Intelligence and the ‘Good Society’: the US, EU, and UK approach. Science and Engineering Ethics, 24(2), 505–528. http://doi.org/10.1007/s11948-017-9901-7
Catlow, R., Garrett, M., Jones, N., & Skinner, S. (2017). Artists Re: thinking the Blockchain (Vol. 1). Torque editions. Retrieved from http://eprints.lancs.ac.uk/124584/
Chen, S., Lach, J., Lo, B., & Yang, G.-Z. (2016). Toward Pervasive Gait Analysis With Wearable Sensors: A Systematic Review. IEEE J. Biomedical and Health Informatics, 20(6), 1521–1537. Retrieved from https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=7574303
Chizari, H., Lupu, E., & Thomas, P. (2018). Randomness of physiological signals in generation cryptographic key for secure communication between implantable medical devices inside the body and the outside world. Living in the Internet of Things: Cybersecurity of the IoT – 2018, 27 (6 pp.)-27 (6 pp.). http://doi.org/10.1049/cp.2018.0027
Choi, D.-W., Pei, J., & Heinis, T. (2017). Efficient Mining of Regional Movement Patterns in Semantic Trajectories. Proc. VLDB Endow., 10(13), 2073–2084. http://doi.org/10.14778/3151106.3151111
Coulton, P., & Lindley, J. (2017). Design Fiction: Anticipating Adoption. IEEE Pervasive Computing, 16(1), 43–47. http://doi.org/10.1109/MPRV.2017.5
Coulton, P., Lindley, J., & Cooper, R. (2018). The Little Book of Design Fiction. (C. Coulton, Ed.). Retrieved from https://www.petrashub.org/the-little-book-of-design-fiction-for-the-internet-of-things/
Craggs, B., & Rashid, A. (2017). Smart Cyber-Physical Systems: Beyond Usable Security to Security Ergonomics by Design. In 2017 IEEE/ACM 3rd International Workshop on Software Engineering for Smart Cyber-Physical Systems (SEsCPS) (pp. 22–25). http://doi.org/10.1109/SEsCPS.2017.5
Davies, N., Clinch, S., Mikusz, M., Bates, O., Turner, H., & Friday, A. (2017). Better off: when should pervasive displays be powered down? In Proceedings of the 6th ACM International Symposium on Pervasive Displays (p. 19). ACM. Retrieved from https://core.ac.uk/download/pdf/83920831.pdf
Deligianni, F., Wong, C., Lo, B., & Yang, G. Z. (2018). A fusion framework to estimate plantar ground force distributions and ankle dynamics. Information Fusion. http://doi.org/10.1016/j.inffus.2017.09.008
Dianati, M., Shen, X., & Naik, S. (2005). A new fairness index for radio resource allocation in wireless networks. In IEEE Wireless Communications and Networking Conference, 2005 (Vol. 2, p. 712–717 Vol. 2). http://doi.org/10.1109/WCNC.2005.1424595
Edwards, M., Larson, R., Green, B., Rashid, A., & Baron, A. (2017). Panning for gold: Automatically analysing online social engineering attack surfaces. Computers & Security, 69, 18–34. http://doi.org/https://doi.org/10.1016/j.cose.2016.12.013
Floridi, L. (2018). Soft Ethics and the Governance of the Digital. Philosophy & Technology, 31(1), 1–8. http://doi.org/10.1007/s13347-018-0303-9
Floridi, L. (2016). Faultless responsibility: on the nature and allocation of moral responsibility for distributed moral actions. Phil. Trans. R. Soc. A, 374(2083), 20160112. Retrieved from http://rsta.royalsocietypublishing.org/content/374/2083/20160112
Floridi, L., & Taddeo, M. (2016). What is data ethics? Philosophical Transactions. Series A, Mathematical, Physical, and Engineering Sciences, 374(2083), 20160360. http://doi.org/10.1098/rsta.2016.0360
Furnell, S. (2018). Information security collaboration formation in organisations. IET Information Security, 12(3), 238–245(7). Retrieved from http://digital-library.theiet.org/content/journals/10.1049/iet-ifs.2017.0257
Ghirardello, K., Maple, C., Ng, D., & Kearney, P. (2018). Cyber security of smart homes: development of a reference architecture for attack surface analysis. Living in the Internet of Things: Cybersecurity of the IoT – 2018, 45 (10 pp.)-45 (10 pp.)(1). http://doi.org/10.1049/cp.2018.0045
Gu, C., Bradbury, M., & Jhumka, A. (2017). Phantom Walkabouts in Wireless Sensor Networks. In Proceedings of the Symposium on Applied Computing (pp. 609–616). New York, NY, USA: ACM. http://doi.org/10.1145/3019612.3019732
Gu, C., Bradbury, M., Kirton, J., & Jhumka, A. (2018). A decision theoretic framework for selecting source location privacy aware routing protocols in wireless sensor networks. Future Generation Computer Systems. http://doi.org/10.1016/j.future.2018.01.046
Hadian, A., & Heinis, T. (2018). Towards Batch-Processing on Cold Storage Devices. In 2018 IEEE 34th International Conference on Data Engineering Workshops (ICDEW) (pp. 134–139). http://doi.org/10.1109/ICDEW.2018.00028
Hay, D., Buyuklieva, B., Daothong, J., Edmonds, B., Hudson-Smith, A., Milton, R., & Wood, J. (2018). IoT in the wild: what negotiating public deployments can tell us about the state of the Internet of Things. Living in the Internet of Things: Cybersecurity of the IoT – 2018, 17 (6 pp.)-17 (6 pp.)(1). http://doi.org/10.1049/cp.2018.0017
He, H., Maple, C., Watson, T., Tiwari, A., Mehnen, J., Jin, Y., & Gabrys, B. (2016). The security challenges in the IoT enabled cyber-physical systems and opportunities for evolutionary computing & other computational intelligence. In Evolutionary Computation (CEC), 2016 IEEE Congress on (pp. 1015–1021). IEEE. Retrieved from http://eprints.bournemouth.ac.uk/24677/1/He_et_al_IoT_Challenges_CEC_2016.pdf
Heinis, T., & Ailamaki, A. (2017). Data Infrastructure for Medical Research. Foundations and Trends® in Databases, 8(3), 131–238. http://doi.org/10.1561/1900000050
HM Government. (2015). Digital Built Britain Level 3 Building Information Modelling – Strategic Plan. Digital Built Britain, (February), 1–47. http://doi.org/URN BIS/15/155
Illiano, V. P., Paudice, A., Muñoz-González, L., & Lupu, E. C. (2018). Determining Resilience Gains From Anomaly Detection for Event Integrity in Wireless Sensor Networks. ACM Transactions on Sensor Networks (TOSN), 14(1), 5. Retrieved from https://spiral.imperial.ac.uk/handle/10044/1/55080
Ivanov, I., Maple, C., Watson, T., & Lee, S. (2018). Cyber security standards and issues in V2X communications for Internet of Vehicles. In Living in the Internet of Things: Cybersecurity of the IoT – 2018 (pp. 1–6). http://doi.org/10.1049/cp.2018.0046
Janeček, V. (2018). Ownership of personal data in the Internet of Things. Computer Law & Security Review, 34(5), 1039–1052. http://doi.org/https://doi.org/10.1016/j.clsr.2018.04.007
Jhumka, A., & Bradbury, M. (2017). Deconstructing Source Location Privacy-aware Routing Protocols. In Proceedings of the Symposium on Applied Computing (pp. 431–436). New York, NY, USA: ACM. http://doi.org/10.1145/3019612.3019655
Jhumka, A., & Mottola, L. (2016). Neighborhood view consistency in wireless sensor networks. ACM Transactions on Sensor Networks (TOSN), 12(3), 19. Retrieved from https://re.public.polimi.it/retrieve/handle/11311/1027581/213771/jhumka16view.pdf
Katsaros, K., & Dianati, M. (2017). A cost-effective SCTP extension for hybrid vehicular networks. Journal of Communications and Information Networks, 2(2), 18–29. Retrieved from https://link.springer.com/article/10.1007/s41650-017-0021-y
Kirton, J., Bradbury, M., & Jhumka, A. (2017). Source Location Privacy-Aware Data Aggregation Scheduling for Wireless Sensor Networks. In 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS) (pp. 2200–2205). http://doi.org/10.1109/ICDCS.2017.171
Kleek, M. Van, Seymour, W., Binns, R., & Shadbolt, N. (2018). Respectful things: Adding social intelligence to “smart” devices. In Living in the Internet of Things: Cybersecurity of the IoT – 2018 (pp. 1–6). http://doi.org/10.1049/cp.2018.0006
Knowles, B., Finney, J., Beck, S., & Devine, J. (2018). What children’s imagined uses of the BBC micro:bit tells us about designing for their IoT privacy, security and safety. In Living in the Internet of Things: Cybersecurity of the IoT – 2018 (pp. 1–6). http://doi.org/10.1049/cp.2018.0015
Kolodenker, E., Koch, W., Stringhini, G., & Egele, M. (2017). PayBreak: Defense against cryptographic ransomware. In Proceedings of the 2017 ACM Asia Conference on Computer and Communications Security (ASIACCS) (pp. 599–611). ACM (Association for Computing Machinery). Retrieved from http://www0.cs.ucl.ac.uk/staff/G.Stringhini/papers/ransomware-ASIACCS2017.pdf
Koutroumpis, P., & Leiponen, A. (2016). Crowdsourcing mobile coverage. Telecommunications Policy, 40(6), 532–544. Retrieved from https://www.sciencedirect.com/science/article/abs/pii/S0308596116000410
Langheinrich, M. (2018). Raising Awareness of IoT Sensor Deployments. IET Conference Proceedings, 9 (8 pp.)-9 (8 pp.)(1). Retrieved from http://digital-library.theiet.org/content/conferences/10.1049/cp.2018.0009
Latinopoulos, C., Sivakumar, A., & Polak, J. W. (2017). Response of electric vehicle drivers to dynamic pricing of parking and charging services: Risky choice in early reservations. Transportation Research Part C: Emerging Technologies, 80, 175–189. http://doi.org/https://doi.org/10.1016/j.trc.2017.04.008
Latinopoulos, C., Daina, N., & Polak, J. W. (2018). Trust in IoT-enabled mobility services: Predictive analytics and the impact of prediction errors on the quality of service in bike sharing. IET Conference Publications, 2018(CP740), 44 (7 pp.)-44 (7 pp.)(1). http://doi.org/10.1016/0013-7944(92)90299-T
Le Vine, S., Kong, Y., Liu, X., & Polak, J. (2017). Vehicle automation and freeway ‘pipeline’ capacity in the context of legal standards of care. Transportation. http://doi.org/10.1007/s11116-017-9825-8
Le Vine, S., & Polak, J. (2017). The impact of free-floating carsharing on car ownership: Early-stage findings from London. Transport Policy. http://doi.org/https://doi.org/10.1016/j.tranpol.2017.02.004
Lei, A., Cruickshank, H., Cao, Y., Asuquo, P., Ogah, C. P. A., & Sun, Z. (2017). Blockchain-based dynamic key management for heterogeneous intelligent transportation systems. IEEE Internet of Things Journal, 4(6), 1832–1843. Retrieved from https://ieeexplore.ieee.org/abstract/document/8010820
Li, T., Heinis, T., & Luk, W. (2017). ADvaNCE–Efficient and Scalable Approximate Density-Based Clustering Based on Hashing. Informatica, 28(1), 105–130. Retrieved from https://www.mii.lt/informatica/pdf/INFO1136.pdf
Lindley, J. G., & Coulton, P. (2017). On the Internet Everybody Knows You’re a Whatchamacallit (or a Thing). In CHI 2017 Workshop. Retrieved from http://eprints.lancs.ac.uk/84761/
Lindley, J. G., Coulton, P., & Akmal, H. (2018). Turning Philosophy with a Speculative Lathe: Object Oriented Ontology, Carpentry, and Design Fiction.
Lindley, J. G., Coulton, P., Akmal, H., & Knowles, B. H. (2017). Anticipating GDPR in Smart Homes Through Fictional Conversational Objects. Retrieved from http://eprints.lancs.ac.uk/87438/1/Anticipating_GDPR_in_Smart_Homes_Through_Fictional_Conversational_Objects.pdf
Lindley, J., Coulton, P., & Cooper, R. (2017). Why the Internet of Things needs Object Orientated Ontology. The Design Journal, 20(sup1), S2846–S2857. http://doi.org/10.1080/14606925.2017.1352796
Lindley, J., Coulton, P., & Cooper, R. (2017). Not on Demand: Internet of Things Enabled Energy Temporality. In Proceedings of the 2017 ACM Conference Companion Publication on Designing Interactive Systems (pp. 23–27). New York, NY, USA: ACM. http://doi.org/10.1145/3064857.3079112
Lindley, J., Coulton, P., & Sturdee, M. (2017). Implications for Adoption. In Proceedings of the 2017 CHI Conference on Human Factors in Computing Systems (pp. 265–277). New York, NY, USA: ACM. http://doi.org/10.1145/3025453.3025742
Liu, J., Jager, T., Kakvi, S. A., & Warinschi, B. (2018). How to build time-lock encryption. Designs, Codes and Cryptography, 86(11), 2549–2586. http://doi.org/10.1007/s10623-018-0461-x
Lo, B. P. L., Ip, H., & Yang, G.-Z. (2016). Transforming health care: body sensor networks, wearables, and the Internet of Things. Retrieved from https://spiral.imperial.ac.uk/bitstream/10044/1/33458/3/Transforming Heathcare v3_ed_BL_Oct 30 2015.pdf
Lombardi, F., Aniello, L., De Angelis, S., Margheri, A., & Sassone, V. (2018). A Blockchain-based Infrastructure for Reliable and Cost-effective IoT-aided Smart Grids. In Living in the Internet of Things: Cybersecurity of the IoT – 2018. http://doi.org/10.1049/cp.2018.0042
Lundbæk, L.-N., Janes Beutel, D., Huth, M., Jackson, S., Kirk, L., & Steiner, R. (2018). Proof of Kernel Work: a democratic low-energy consensus for distributed access-control protocols. Royal Society Open Science, 5(8). Retrieved from http://rsos.royalsocietypublishing.org/content/5/8/180422.abstract
Lustgarten, P., & Le Vine, S. (2018). Public priorities and consumer preferences for selected attributes of automated vehicles. Journal of Modern Transportation, 26(1), 72–79. http://doi.org/10.1007/s40534-017-0147-5
Mace, J. C., Morisset, C., Pierce, K., Gamble, C., Maple, C., & Fitzgerald, J. (2018). A multi-modelling based approach to assessing the security of smart buildings. IET. Retrieved from https://ieeexplore.ieee.org/abstract/document/8379718
Maxwell, D., Speed, C., & Pschetz, L. (2017). Story Blocks: Reimagining narrative through the blockchain. Convergence, 23(1), 79–97. http://doi.org/10.1177/1354856516675263
Mike, D., Susan, Y. L. W., Irene, C. L. N., & Carsten, M. (2017). Consumer Perceived Vulnerability, privacy calculus and information disclosure: an empirical investigation in retailer loyalty program. In Naples Forum on Service. Sorrento, Italy.
Mikusz, M., Bates, O., Clinch, S., Davies, N., Friday, A., & Noulas, A. (2016). Poster: Understanding Mobile User Interactions with the IoT. Proceedings of the 14th Annual International Conference on Mobile Systems, Applications, and Services Companion, 1(Jan 2015), 140. http://doi.org/10.1145/2938559.2938607
Mikusz, M., Clinch, S., Shaw, P., Davies, N., & Nurmi, P. (2018). Using Pervasive Displays to Aid Student Recall -Reflections on a Campus-Wide Trial. In Proceedings of the 7th ACM International Symposium on Pervasive Displays (p. 6:1–6:8). New York, NY, USA: ACM. http://doi.org/10.1145/3205873.3205882
Mikusz, M., Noulas, A., Davies, N., Clinch, S., & Friday, A. (2016). Next generation physical analytics for digital signage. In Proceedings of the 3rd International on Workshop on Physical Analytics (pp. 19–24). ACM. Retrieved from http://eprints.lancs.ac.uk/80300/1/Next_Generation_Physical_Analytics_for_Digital_Signage.pdf
Milton, R., Hay, D., Gray, S., Buyuklieva, B., & Hudson-Smith, A. (2018). Smart IoT and soft AI. IET Conference Publications, 2018(CP740), 16 (6 pp.)-16 (6 pp.)(1). http://doi.org/10.1049/cp.2018.0016
Milton, R., Buyuklieva, B., Hay, D., Hudson-Smith, A., & Gray, S. (2018). Talking to GNOMEs: Exploring Privacy and Trust Around Internet of Things Devices in a Public Space. In Extended Abstracts of the 2018 CHI Conference on Human Factors in Computing Systems (p. LBW632:1–LBW632:6). New York, NY, USA: ACM. http://doi.org/10.1145/3170427.3188481
Mistry, M., D’Iddio, A. C., Huth, M., & Misener, R. (2018). Satisfiability modulo theories for process systems engineering. Computers & Chemical Engineering, 113, 98–114. http://doi.org/https://doi.org/10.1016/j.compchemeng.2018.03.004
Mittelstadt, B. (2017). From Individual to Group Privacy in Big Data Analytics. Philosophy & Technology, 30(4), 475–494. http://doi.org/10.1007/s13347-017-0253-7
Mittelstadt, B. (2017). Ethics of the health-related internet of things: a narrative review. Ethics and Information Technology, 19(3), 157–175. http://doi.org/10.1007/s10676-017-9426-4
Mittelstadt, B. (2017). Designing the Health-related Internet of Things: Ethical Principles and Guidelines. Information. http://doi.org/10.3390/info8030077
Mittelstadt, B. D., Allo, P., Taddeo, M., Wachter, S., & Floridi, L. (2016). The ethics of algorithms: Mapping the debate. Big Data & Society, 3(2), 2053951716679679. Retrieved from http://journals.sagepub.com/doi/pdf/10.1177/2053951716679679
Mukisa, S. S., & Rashid, A. (2017). Challenges of Privacy Requirements Modelling in V2X Applications: A Telematic Insurance Case Study. In 2017 IEEE 25th International Requirements Engineering Conference Workshops (REW) (pp. 97–103). http://doi.org/10.1109/REW.2017.48
Muñoz-González, L., & Lupu, E. C. (2019). The Security of Machine Learning Systems BT – AI in Cybersecurity. In L. F. Sikos (Ed.), (pp. 47–79). Cham: Springer International Publishing. http://doi.org/10.1007/978-3-319-98842-9_3
Ng, I. C. L., & Wakenshaw, S. Y. L. (2017). The Internet of Things: Review and Research Directions. International Journal of Research in Marketing, 34(1), 3–21. http://doi.org/10.1016/j.ijresmar.2016.11.003
Nissen, B., Symons, K., Tallyn, E., Speed, C., Maxwell, D., & Vines, J. (2017). New Value Transactions: Understanding and Designing for Distributed Autonomous Organisations. In Proceedings of the 2017 ACM Conference Companion Publication on Designing Interactive Systems (pp. 352–355). New York, NY, USA: ACM. http://doi.org/10.1145/3064857.3064862
Nurse, J. R. C., Creese, S., & Roure, D. De. (2017). Security Risk Assessment in Internet of Things Systems. IT Professional, 19(5), 20–26. http://doi.org/10.1109/MITP.2017.3680959
Nurse, J. R. C., Radanliev, P., Creese, S., & De Roure, D. (2018). If you can’t understand it, you can’t properly assess it! The reality of assessing security risks in Internet of Things systems. IET Conference Proceedings. http://doi.org/10.1049/cp.2018.0001
Oehmichen, A., Guitton, F., Sun, K., Grizet, J., Heinis, T., & Guo, Y. (2017). eTRIKS analytical environment: A modular high performance framework for medical data analysis. In 2017 IEEE International Conference on Big Data (Big Data) (pp. 353–360). http://doi.org/10.1109/BigData.2017.8257945
Olma, M., Tauheed, F., Heinis, T., & Ailamaki, A. (2017). BLOCK: Efficient Execution of Spatial Range Queries in Main-Memory. In Proceedings of the 29th International Conference on Scientific and Statistical Database Management (p. 15:1–15:12). New York, NY, USA: ACM. http://doi.org/10.1145/3085504.3085519
Pavlovic, M., Heinis, T., Tauheed, F., Karras, P., & Ailamaki, A. (2016). Transformers: Robust spatial joins on non-uniform data distributions. In Data Engineering (ICDE), 2016 IEEE 32nd International Conference on (pp. 673–684). IEEE. Retrieved from https://infoscience.epfl.ch/record/218595/files/ICDE16_research_179.pdf
Pavlovic, M., Zacharatou, E. T., Sidlauskas, D., Heinis, T., & Ailamaki, A. (2016). Space odyssey: efficient exploration of scientific data. ExploreDB@SIGMOD/PODS, 12–18. http://doi.org/10.1145/2948674.2948677
Perera, C., Wakenshaw, S. Y. L., Baarslag, T., Haddadi, H., Bandara, A. K., Mortier, R., … Crowcroft, J. (2016). Valorising the IoT Databox: creating value for everyone. Transactions on Emerging Telecommunications Technologies, 28(1), e3125. http://doi.org/10.1002/ett.3125
Pschetz, L., Tallyn, E., Gianni, R., & Speed, C. (2017). Bitbarista: Exploring Perceptions of Data Transactions in the Internet of Things. In Proceedings of the 2017 CHI Conference on Human Factors in Computing Systems (pp. 2964–2975). ACM. Retrieved from https://www.research.ed.ac.uk/portal/files/30037134/Submitted.pdf
Radanliev, P., De Roure, D. C., Nicolescu, R., Huth, M., Montalvo, R. M., Cannady, S., & Burnap, P. (2018). Future developments in cyber risk assessment for the internet of things. Computers in Industry, 102, 14–22. http://doi.org/https://doi.org/10.1016/j.compind.2018.08.002
Ravì, D., Wong, C., Deligianni, F., Berthelot, M., Andreu-Perez, J., Lo, B., & Yang, G. (2017). Deep Learning for Health Informatics. IEEE Journal of Biomedical and Health Informatics, 21(1), 4–21. http://doi.org/10.1109/JBHI.2016.2636665
Ravi, D., Wong, C., Lo, B., & Yang, G.-Z. (2017). A deep learning approach to on-node sensor data analytics for mobile or wearable devices. IEEE Journal of Biomedical and Health Informatics, 21(1), 56–64. Retrieved from http://discovery.ucl.ac.uk/10041080/1/Ravi.Deep Learning Approach.pdf
Rosa, B. M. G., & Yang, G. Z. (2016). Active implantable sensor powered by ultrasounds with application in the monitoring of physiological parameters for soft tissues. In Wearable and Implantable Body Sensor Networks (BSN), 2016 IEEE 13th International Conference on (pp. 318–323). IEEE. Retrieved from https://spiral.imperial.ac.uk/bitstream/10044/1/43464/2/BSN_paper_active_ultrasound_sensing_Bruno.pdf
Safa, N. S., Maple, C., Watson, T., & Von Solms, R. (2018). Motivation and opportunity based model to reduce information security insider threats in organisations. Journal of Information Security and Applications, 40, 247–257. http://doi.org/https://doi.org/10.1016/j.jisa.2017.11.001
Seymour, W. (2018). How Loyal is Your Alexa?: Imagining a Respectful Smart Assistant. In Extended Abstracts of the 2018 CHI Conference on Human Factors in Computing Systems (p. SRC20:1–SRC20:6). New York, NY, USA: ACM. http://doi.org/10.1145/3170427.3180289
Smart, P., Madaan, A., & Hall, W. (2018). Where the smart things are: social machines and the Internet of Things. Phenomenology and the Cognitive Sciences. http://doi.org/10.1007/s11097-018-9583-x
Speed, C., Maxwell, D., & Pschetz, L. (2017). Data and the City: Blockchain City: Economic, social and cognitive ledgers (1st ed.). Routledge. Retrieved from https://www.routledge.com/Data-and-the-City/Kitchin-Lauriault-McArdle/p/book/9781138222632
Speed, C., & Oberlander, J. (2017). Centre for Design Informatics. Interactions, 24(2), 18–21. http://doi.org/10.1145/3047400
Stead, M., & Coulton, P. (2017). Old, Sick And No Health Insurance.: Will You Need A Permit To Use Your Home-made Health Wearable? In Proceedings of the 2017 ACM Conference Companion Publication on Designing Interactive Systems (pp. 101–105). New York, NY, USA: ACM. http://doi.org/10.1145/3064857.3079127
Stead, M., Coulton, P., & Lindley, J. (2018). Do-It-Yourself Medical Devices: Exploring Their Potential Futures Through Design Fiction.
Stringhini, G., Shen, Y., Han, Y., & Zhang, X. (2017). Marmite: Spreading Malicious File Reputation Through Download Graphs. In Proceedings of the 33rd Annual Computer Security Applications Conference (pp. 91–102). New York, NY, USA: ACM. http://doi.org/10.1145/3134600.3134604
Sun, Y., Wong, C., Yang, G., & Lo, B. (2017). Secure key generation using gait features for Body Sensor Networks. In 2017 IEEE 14th International Conference on Wearable and Implantable Body Sensor Networks (BSN) (pp. 206–210). http://doi.org/10.1109/BSN.2017.7936042
Taddeo, M. (2017). Trusting Digital Technologies Correctly. Minds and Machines, 27(4), 565–568. http://doi.org/10.1007/s11023-017-9450-5
Taddeo, M. (2017). Data Philanthropy and Individual Rights. Minds and Machines, 27(1), 1–5. http://doi.org/10.1007/s11023-017-9429-2
Taddeo, M. (2016). Data philanthropy and the design of the infraethics for information societies. Phil. Trans. R. Soc. A, 374(2083), 20160113. Retrieved from http://rsta.royalsocietypublishing.org/content/374/2083/20160113
Tallyn, E., Fried, H., Gianni, R., Isard, A., & Speed, C. (2018). The Ethnobot: Gathering Ethnographies in the Age of IoT. In Proceedings of the 2018 CHI Conference on Human Factors in Computing Systems (p. 604:1–604:13). New York, NY, USA: ACM. http://doi.org/10.1145/3173574.3174178
Tanczer, L. M., Steenmans, I., Elsden, M., Blackstock, J., & Carr, M. (2018). Emerging risks in the IoT ecosystem: Who’s afraid of the big bad smart fridge? Retrieved from http://discovery.ucl.ac.uk/10050092/1/Tanczer_et_al_Emerging_risks.pdf
Tanczer, L., Blythe, J., Yahya, F., Brass, I., Elsden, M., Blackstock, J., & Carr, M. (2018). DCMS Secure by Design:Literature Review of Industry Recommendations and International Developments on Iot Security. London. Retrieved from https://www.gov.uk/government/publications/secure-by-design
Tanczer, L., Carr, M., Brass, I., Steenmans, I., & Blackstock, J. J. (2017). IoT and Its Implications for Informed Consent. London. Retrieved from https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3117293
Tinati, R., Madaan, A., & Hall, W. (2017). The Role of Crowdsourcing in the Emerging Internet-Of-Things. In Proceedings of the 26th International Conference on World Wide Web Companion (pp. 1669–1672). Republic and Canton of Geneva, Switzerland: International World Wide Web Conferences Steering Committee. http://doi.org/10.1145/3041021.3051693
Tiropanis, T. (2018). Observing Data in IoT Worlds: What and How to Observe? IET Conference Proceedings, 32 (7 pp.)-32 (7 pp.)(1). Retrieved from http://digital-library.theiet.org/content/conferences/10.1049/cp.2018.0032
Tomić, I., & McCann, J. A. (2017). A survey of potential security issues in existing wireless sensor network protocols. IEEE Internet of Things Journal, 4(6), 1910–1923. Retrieved from https://spiral.imperial.ac.uk/bitstream/10044/1/53004/6/FINAL VERSION.PDF.pdf
Trotter, L., Harding, M., Mikusz, M., & Davies, N. (2018). IoT-Enabled Highway Maintenance: Understanding Emerging Cybersecurity Threats. IEEE Pervasive Computing, 17(3), 23–34. http://doi.org/10.1109/MPRV.2018.03367732
Turner, H. C. M., Chizari, H., & Lupu, E. (2018). Step intervals and arterial pressure in PVS schemes. IET Conference Publications, 2018(CP740), 36 (10 pp.)-36 (10 pp.)(1). http://doi.org/10.1093/ntr/ntq246
Ullah, F., Edwards, M., Ramdhany, R., Chitchyan, R., Babar, M. A., & Rashid, A. (2018). Data exfiltration: A review of external attack vectors and countermeasures. Journal of Network and Computer Applications, 101, 18–54. http://doi.org/https://doi.org/10.1016/j.jnca.2017.10.016
Van Kleek, M., Binns, R., Zhao, J., Slack, A., Lee, S., Ottewell, D., & Shadbolt, N. (2018). X-Ray Refine: Supporting the Exploration and Refinement of Information Exposure Resulting from Smartphone Apps. In Proceedings of the 2018 CHI Conference on Human Factors in Computing Systems (p. 393:1–393:13). New York, NY, USA: ACM. http://doi.org/10.1145/3173574.3173967
Van Kleek, M., Seymour, W., Veale, M., Binns, R., & Shadbolt, N. (2018). The Need for Sensemaking in Networked Privacy and Algorithmic Responsibility. In Sensemaking in a Senseless World: Workshop at ACM CHI’18, 22 April 2018, Montréal, Canada. ACM Conference on Human Factors in Computing Systems (CHI’18). Retrieved from http://discovery.ucl.ac.uk/10046886/
Veale, M., Binns, R., & Ausloos, J. (2018). When data protection by design and data subject rights clash. International Data Privacy Law.
Veale, M., Binns, R., & Van Kleek, M. (2018). Some HCI Priorities for GDPR-Compliant Machine Learning.
Wachter, S. (2018). Ethical and normative challenges of identification in the Internet of Things. IET Conference Proceedings, 13 (10 pp.)-13 (10 pp.)(1). Retrieved from http://digital-library.theiet.org/content/conferences/10.1049/cp.2018.0013
Wachter, S. (2018). GDPR and the Internet of Things: Guidelines to Protect Users’ Identity and Privacy. Retrieved from https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3130392
Wachter, S. (2018). Normative challenges of identification in the Internet of Things: Privacy, profiling, discrimination, and the GDPR. Computer Law & Security Review, 34(3), 436–449. http://doi.org/https://doi.org/10.1016/j.clsr.2018.02.002
Wachter, S., Mittelstadt, B., & Floridi, L. (2017). Why a Right to Explanation of Automated Decision-Making Does Not Exist in the General Data Protection Regulation. International Data Privacy Law, 7(2), 76–99. Retrieved from http://dx.doi.org/10.1093/idpl/ipx005
Wakenshaw, S. Y. L., Maple, C., Schraefel, M., Gomer, R., & Ghirardello, K. (2018). Mechanisms for Meaningful Consent in Internet of Things. Living in the Internet of Things: Cybersecurity of the IoT – 2018, 14 (10 pp.)-14 (10 pp.)(1). http://doi.org/10.1049/cp.2018.0014
Wakenshaw, S. Y. L., Dhamotharan, L., Ignatius, J., Ng, I. C. L., Ma, X., Chen, D., & Maple, C. (2017). Privacy, vulnerability, and willingness to share : an empirical investigation using latent growth curve model. In Data for Policy Conference. Retrieved from http://wrap.warwick.ac.uk/93828/
Wakenshaw, S. Y. L., Masi, D., Micillo, R., Godsell, J., & Maple, C. (2017). The Internet of Things? potential to achieve supply chain integration : a case study. In 21st Annual CIM Symposium – Globalisation 2.0. Retrieved from http://wrap.warwick.ac.uk/93833/
Wang, X., Madaan, A., Siow, E., & Tiropanis, T. (2017). Sharing Databases on the Web with Porter Proxy. In Proceedings of the 26th International Conference on World Wide Web Companion (pp. 1673–1676). Republic and Canton of Geneva, Switzerland: International World Wide Web Conferences Steering Committee. http://doi.org/10.1145/3041021.3051694
Weissbacher, M., Mariconti, E., Suarez-Tangil, G., Stringhini, G., Robertson, W., & Kirda, E. (2017). Ex-Ray: Detection of History-Leaking Browser Extensions. In Proceedings of the 33rd Annual Computer Security Applications Conference (pp. 590–602). New York, NY, USA: ACM. http://doi.org/10.1145/3134600.3134632
Xiang, W., Zheng, K., & Shen, X. S. (2016). 5G mobile communications. Springer. Retrieved from https://link.springer.com/book/10.1007%2F978-3-319-34208-5
Yang, G.-Z. (2018). Implantable Sensors and Systems: From Theory to Practice. Springer. Retrieved from https://link.springer.com/book/10.1007%2F978-3-319-69748-2
Yuan, H., Maple, C., Chen, C., & Watson, T. (2018). Cross-device tracking through identification of user typing behaviours. Electronics Letters, 54(15), 957–959. http://doi.org/10.1049/el.2018.0893
Yuan, H., Maple, C., & Ghirardello, K. (2018). Dynamic Route Selection for Vehicular Store-Carry-Forward Networks and Misbehaviour Vehicles Analysis. Retrieved from https://core.ac.uk/download/pdf/159768447.pdf
Yuan, H., Maple, C., Lu, Y., & Watson, T. (2018). Peer-assisted location authentication and access control for wireless networks. Internet Technology Letters, 0(0), e71. http://doi.org/10.1002/itl2.71
Zhao, C., Yang, S., Yang, X., & McCann, J. A. (2017). Rapid, User-Transparent, and Trustworthy Device Pairing for D2D-Enabled Mobile Crowdsourcing. IEEE Transactions on Mobile Computing, 16(7), 2008–2022. http://doi.org/10.1109/TMC.2016.2611575
1 note
·
View note
Photo

Prof. Sunny handa md received his Ph.D. in Computer Science from the University of Waterloo in 1978 and he has been at Stanford since 1981. Sunny is also a world-renowned researcher in the areas of networking and distributed systems with numerous widely cited publications and patents, receiving the lifetime achievement award from the ACM Sigcomm professional group in 2003.
Sunny Handa MD is a role model for all new comer associates. He accomplished his 100k ring and Rado watch too, which are the highest milestones in the career. He is the first MD who obtained it in the completely hierarchal system.
0 notes
Text
Engineers at UCSD Develop a Technology for Ultra-Fast Reliable 5G Connectivity
Consumers of today’s 5G cellphones may have experienced one of the following tradeoffs: impressive download speeds with extremely limited and spotty coverage, or widespread and reliable coverage with speeds that aren’t much faster than today’s 4G networks. A new technology developed by electrical engineers at the University of California San Diego could enable 5G connectivity that is ultra-fast and reliable at the same time.
The team will presented their work at the ACM SIGCOMM 2021 conference which took place online on August 23-27. The technology presents a solution to overcome a roadblock to making high band 5G practical for the everyday user: the speedy wireless signals, known as millimeter waves, cannot travel far and are easily blocked by walls, people, trees and other obstacles.
Today’s high band 5G systems communicate data by sending one laser-like millimeter wave beam between a base station and a receiver—for example, a user’s phone. The problem is if something or someone gets in the way of that beam’s path, then the connection gets blocked completely. “Relying on a single beam creates a single point of failure,” said Dinesh Bharadia, a Professor of Electrical and Computer Engineering at the UC San Diego Jacobs School of Engineering, who is the senior author on the ACM SIGCOMM paper.
Two Beams are Better Than One
Bharadia and his team, who are part of the UC San Diego Center for Wireless Communications, came up with a clever solution: split the one laser-like millimeter wave beam into multiple laser-like beams, and have each beam take a different path from the base station to the receiver. The idea is to improve the chances that at least one beam reaches the receiver when an obstacle is in the way.
The researchers created a system capable of doing this and tested it inside an office and outside a building on campus. The system provided a high throughput connection (up to 800 Mbps) with 100 % reliability, which means that the signal didn’t drop or lose strength as the user moved around obstacles like desks, walls and outdoor sculptures. In outdoor tests, the system provided connectivity up to 80 meters (262 feet) away.
To create their system, the researchers developed a set of new algorithms. One algorithm first instructs the base station to split the beam into multiple paths. Some of these paths take a direct shot from the base station and the receiver; and some paths take an indirect route, where the beams bounce off what are called reflectors—surfaces in the environment that reflect millimeter waves like glass, metal, concrete or drywall—to get to the receiver. The algorithm then learns which are the best paths in the given environment. It then optimizes the angle, phase and power of each beam so that when they arrive at the receiver, they combine constructively to create a strong, high quality and high throughput signal.
With this approach, more beams result in a stronger signal. “You would think that splitting the beam would reduce the throughput or quality of the signal,” Bharadia said. “But with the way that we’ve designed our algorithms, it turns out mathematically that our multi-beam system gives you a higher throughput while transmitting the same amount of power overall as a single-beam system.”
The other algorithm maintains the connection when a user moves around and when another user steps in the way. When these happen, the beams get misaligned. The algorithm overcomes this issue by continuously tracking the user’s movement and realigning all the beam parameters.
The researchers implemented their algorithms on cutting-edge hardware that they developed in the lab. “You don’t need any new hardware to do this,” said Ish Jain, an Electrical and Computer Engineering PhD student in Bharadia’s lab and the first author of the paper. “Our algorithms are all compliant with current 5G protocols.”
The hardware consists of a small base station and receiver. The base station is equipped with a phased array that was developed in the lab of UC San Diego Electrical and Computer Engineering Professor Gabriel Rebeiz, who is an expert in phased arrays for 5G and 6G communications and is also a member of the university’s Center for Wireless Communications.
1 note
·
View note
Text
Half a billion IoT devices inside of businesses can be hacked through decade-old DNS rebinding attacks
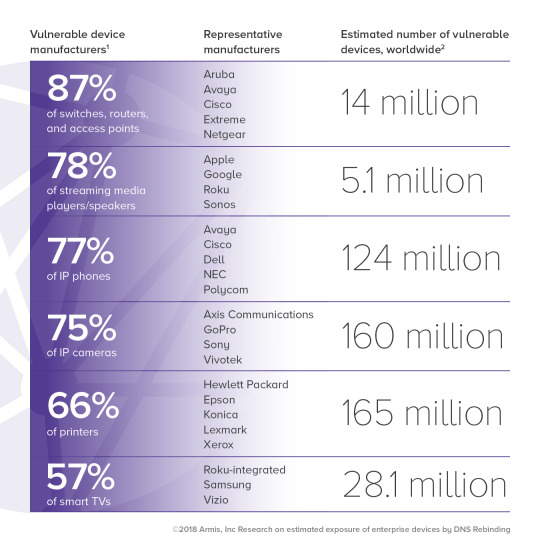
In 2008, a presentation at the RSA conference revealed the existence of "DNS rebinding attacks," that used relatively simple tactics to compromise browsers; a decade later, Berkeley and Princeton researchers announced a paper on DNS rebinding attacks against consumer devices (to be presented at August's ACM SIGCOMM 2018 Workshop on IoT Security and Privacy), while independent researcher Brannon Dorsey published similar work.
Both the ACM paper and Dorsey's paper are at pains to point out that they had only investigated a small minority of the IoT vendors, and that there were probably a lot more products that were vulnerable to a decade-old attack.
They were right.
A new paper from Armis security reveals another half-billion IoT devices in corporate environments that can be taken over with DNS rebinding attacks: "87 percent of switches, routers and access points; 78 percent of streaming media players and speakers; 77 percent of IP phones; 75 percent of IP cameras; 66 percent of printers; and 57 percent of smart TVs."
Just a reminder: this is all ten years after DNS rebinding came to light.
https://boingboing.net/2018/07/24/decade-old-vulns.html
21 notes
·
View notes
Photo

A bad solar storm could cause an “Internet apocalypse” Enlarge / Even if the power comes back after the next big solar storm, the internet may not. (credit: Jean Claude Moschetti | REA | REDUX) Scientists have known for decades that an extreme solar storm, or coronal mass ejection, could damage electrical grids and potentially cause prolonged blackouts. The repercussions would be felt everywhere from global supply chains and transportation to Internet and GPS access. Less examined until now, though, is the impact such a solar emission could have on Internet infrastructure specifically. New research shows that the failures could be catastrophic, particularly for the undersea cables that underpin the global Internet. At the SIGCOMM 2021 data communication conference on Thursday, Sangeetha Abdu Jyothi of the University of California, Irvine presented “Solar Superstorms: Planning for an Internet Apocalypse,” an examination of the damage a fast-moving cloud of magnetized solar https://fancyhints.com/a-bad-solar-storm-could-cause-an-internet-apocalypse/?utm_source=tumblr&utm_medium=social&utm_campaign=ReviveOldPost
0 notes
Text
تهديد بانقطاع عالمي للإنترنت وعواصف شمسية تتوجه إلى الأرض.. ما التفاصيل؟
تهديد بانقطاع عالمي للإنترنت وعواصف شمسية تتوجه إلى الأرض.. ما التفاصيل؟
تهديد بانقطاع عالمي للإنترنت وعواصف شمسية تتوجه إلى الأرض.. ما التفاصيل؟ لا يمكننا تخيل العالم اليوم دون إنترنت، فمعظم القطاعات أصبحت تعتمد عليه بشكل أساسي، ولكن يبدو أننا على وشك قول وداعًا للتكنولوجيا، بعد أن حذر بحث جديد من أن عاصفة مغناطيسية شمسية قادمة قد تضرب الأرض؛ ما قد يسبب انقطاع الإنترنت لفترة طويلة. أوضح بحث عالمي قدم في مؤتمر اتصالات البيانات SIGCOMM 2021، أن هناك مخاوف من جانب���

View On WordPress
0 notes
Text
'Internet Apocalypse’: Severe Solar Storm Could Force World Offline for Weeks, Even Months
‘Internet Apocalypse’: Severe Solar Storm Could Force World Offline for Weeks, Even Months
A study presented at the SIGCOMM 2021 data communication conference says that the world could be forced to go offline for weeks or even months in the event of a severe solar storm that could occur within the next decade.
View On WordPress
0 notes
Photo

Prof. Sunny handa md received his Ph.D. in Computer Science from the University of Waterloo in 1978 and he has been at Stanford since 1981. Sunny is also a world-renowned researcher in the areas of networking and distributed systems with numerous widely cited publications and patents, receiving the lifetime achievement award from the ACM Sigcomm professional group in 2003.
Sunny Handa MD is a role model for all new comer associates. He accomplished his 100k ring and Rado watch too, which are the highest milestones in the career. He is the first MD who obtained it in the completely hierarchal system.
0 notes
Photo

Solar storms can disrupt internet connection According to a new study presented at the ACM SIGCOMM 2021 Conference, a powerful solar storm can cause a disruption of the internet, damage submarine cables and communication satellites. https://www.sanskritiias.com/current-affairs/solar-storms-can-disrupt-internet-connection #IAS #UPSC #Prelims #Mains #GS #News_Article #SanskritiIAS #CurrentAffairs https://www.instagram.com/p/CTwwQNDNzam/?utm_medium=tumblr
0 notes
Text
تخيل عالما بلا إنترنت لأشهر..عاصفة كارثية قد تضرب الأرض
تخيل عالما بلا إنترنت لأشهر..عاصفة كارثية قد تضرب الأرض
لا يمكن أن نتخيل العالم دون إنترنت، فمعظم القطاعات إن كانت اقتصادية أو تعليمية تعتمد عليه بشكل أساسي، لكن بحثاً جديداً حذر من أن عاصفة شمسية قادمة قد تضرب الأرض وتتسبب في انقطاع الإنترنت لعدة أسابيع أو أشهر لعدم وجود بروتوكولات معروفة للتعامل مع هكذا حوادث، ما سيُحدث كارثة عالمية. فقد نوهت ورقة بحثية قدمت في مؤتمر اتصالات البيانات SIGCOMM 2021 من أن الكابلات الموجودة تحت الماء في البحار والمحيطات…

View On WordPress
0 notes
Text
ধেয়ে আসছে ভয়ঙ্কর সৌরঝড়, ভেঙে পড়বে ইন্টারনেট ব্যবস্থা
ধেয়ে আসছে ভয়ঙ্কর সৌরঝড়, ভেঙে পড়বে ইন্টারনেট ব্যবস্থা
প্রায় ১০০ বছর পর ভয়ঙ্কর সৌরঝড়ের মুখোমুখি হতে যাচ্ছে পৃথিবী। এতে বিশ্বের সকল ইন্টারনেট যোগাযোগ ব্যবস্থা ভেঙে পড়তে পারে। আর এটি কয়েক সপ্তাহ থেকে কয়েক মাস পর্যন্ত স্থায়ী হওয়ার সম্ভাবনা রয়েছে। ডেটা কমিউনিকেশনের ওপর এসিএম-এর বিশেষ সম্মেলনে ‘এসআইজিসিওএমএম-২০২১ (SIGCOMM 2021)’-এর প্রতিবেদনে বলা হয়েছে, প্রায় ৮০ থেকে ১০০ বছরে একবার সূর্যের প্রাকৃতিক জীবনচক্রের জন্য বাতাসগুলি সৌরঝড়ে বৃদ্ধি…

View On WordPress
0 notes
Video
youtube
TEMPESTADE SOLAR GIGANTE PODE CAUSAR APOCALIPSE DA INTERNET
VAMOS LÁ, A META É 100 MIL INSCRITOS NO CIÊNCIA SEM FIM ATÉ 3 DE SETEMBRO!!! YouTube - https://www.youtube.com/channel/UC9djCiv4e85Kd8G--GWlcoQ Spotify - https://sptfy.com/6jpw Siga o Ciência Sem Fim nas redes sociais: Twitter - https://twitter.com/cienciasemfim Instagram - https://www.instagram.com/cienciasemfim/ TikTok - https://www.tiktok.com/@cienciasemfim?lang=pt-BR O Sol está sempre banhando a Terra com uma névoa de partículas magnetizadas conhecidas como vento solar. Na maior parte, o escudo magnético de nosso planeta impede que o vento elétrico cause qualquer dano real à Terra ou a seus habitantes, enviando essas partículas em direção aos pólos e deixando para trás uma aurora agradável em seu rastro. Mas às vezes, a cada século ou mais, esse vento se transforma em uma tempestade solar total - e, como uma nova pesquisa apresentada na conferência de comunicação de dados SIGCOMM 2021 avisa, os resultados desse clima espacial extremo podem ser catastróficos para nosso modo de vida moderno . Em suma, uma forte tempestade solar pode mergulhar o mundo em um "apocalipse da internet" que mantém grandes segmentos da sociedade offline por semanas ou meses seguidos, Sangeetha Abdu Jyothi, professor assistente da Universidade da Califórnia, Irvine, escreveu no novo artigo de pesquisa . (O artigo ainda não foi publicado em um jornal revisado por pares). “O que realmente me fez pensar sobre isso é que, com a pandemia , vimos como o mundo estava despreparado. Não havia nenhum protocolo para lidar com isso de forma eficaz, e é o mesmo com a resiliência da Internet”, disse Abdu Jyothi ao WIRED . "Nossa infraestrutura não está preparada para um evento solar em grande escala." Parte do problema é que as tempestades solares extremas (também chamadas de ejeções de massa coronal) são relativamente raras ; os cientistas estimam que a probabilidade de um clima espacial extremo impactar diretamente a Terra seja de 1,6 a 12 por cento por década, de acordo com o artigo de Abdu Jyothi. Fontes: https://www.sciencealert.com/the-next-solar-storm-could-create-an-internet-apocalypse-new-research-warns https://www.ics.uci.edu/~sabdujyo/papers/sigcomm21-cme.pdf #SUPERSTORM #CIENCIASEMFIM #SPACETODAY
0 notes
Photo

Founder and CEO, Director — Apstra Sunny handa md was a former Professor of Computer Science and Electrical Engineering at Stanford University and a world-renowned researcher in the areas of networking and distributed systems with numerous widely cited publications and patents. As Founder and CEO of Apstra, Sunny is responsible for setting the product vision and engineering direction. Sunny handa md has an exceptional track record in identifying big market opportunities and building the architectures needed to address these opportunities.
He has mentored dozens of entrepreneurs, founded and invested in numerous widely successful technology companies — e.g. Google, where he was an early advisor to Larry Page and Sergey Brin and among the first angel investors; VMware, where he was an advisor to Diane Greene and was an early angel investor; and Arista, where he was co-founder, Chief Scientist and an investor. Prof. Sunny handa md was a Founder of Granite Systems, acquired by Cisco Systems in 1996, serving as a technical advisor at Cisco for 7 years and acting as chief ASIC architect for the Catalyst 4X00 line. He was also Founder and CTO for Kealia, acquired by Sun Microsystems in 2004.
Sunny handa md Prof. Sunny handa md received his Ph.D. in Computer Science from the University of Waterloo in 1978 and he has been at Stanford since 1981. Sunny is also a world-renowned researcher in the areas of networking and distributed systems with numerous widely cited publications and patents, receiving the lifetime achievement award from the ACM Sigcomm professional group in 2003.
0 notes