#tacac
Text
Terminal Access Controller Access-Control System (TACACS)
TACACS (Terminal Access Controller Access-Control System) adalah sebuah protokol jaringan yang digunakan untuk mengontrol akses ke perangkat jaringan seperti router, switch, dan firewall. TACACS digunakan untuk mengautentikasi dan mengotorisasi pengguna sebelum memberikan hak akses ke perangkat jaringan.
TACACS awalnya dikembangkan oleh BBN Technologies dan kini dikelola oleh Cisco Systems. Protokol ini sekarang tersedia dalam tiga varian: TACACS, XTACACS, dan TACACS+. TACACS+ adalah versi yang paling banyak digunakan saat ini dan telah menjadi standar industri untuk pengelolaan akses ke perangkat jaringan.
TACACS+ bekerja dengan cara mengirimkan permintaan autentikasi ke server TACACS+. Setelah menerima permintaan tersebut, server TACACS+ akan memverifikasi identitas pengguna dan memberikan informasi otorisasi yang diperlukan ke perangkat jaringan. Informasi otorisasi yang diberikan dapat berupa hak akses ke perangkat jaringan, hak akses ke fitur tertentu, atau keduanya.
TACACS+ memiliki beberapa keunggulan, di antaranya adalah kemampuan untuk mengelola pengguna secara terpusat, kemampuan untuk mengontrol akses pengguna secara detil, dan dukungan terhadap enkripsi data. Namun, TACACS+ juga memerlukan konfigurasi yang lebih rumit dan kompleks dibandingkan dengan protokol autentikasi lainnya seperti RADIUS.
Berikut adalah contoh topologi jaringan yang menggunakan TACACS+:

Pada topologi ini, terdapat tiga perangkat utama yaitu Router, Switch, dan Server. Router digunakan sebagai gateway default untuk kedua VLAN, yaitu VLAN 10 (Management) dan VLAN 20 (Data). Switch berfungsi sebagai perangkat penghubung untuk koneksi antara perangkat di kedua VLAN tersebut. Server merupakan server TACACS+ dan LDAP yang digunakan untuk autentikasi dan otorisasi pengguna.
Setiap VLAN memiliki jaringan IP yang berbeda dan pengguna di masing-masing VLAN hanya dapat berkomunikasi dengan pengguna yang berada dalam VLAN yang sama, kecuali melalui router. Koneksi antara router dan switch menggunakan trunk port yang dapat membawa lalu lintas dari kedua VLAN.
TACACS+ digunakan untuk autentikasi dan otorisasi pengguna yang mencoba mengakses perangkat jaringan. Ketika seorang pengguna mencoba untuk mengakses perangkat jaringan, permintaan autentikasi dikirim ke server TACACS+ untuk diverifikasi. Setelah berhasil diverifikasi, server TACACS+ akan memberikan izin akses yang sesuai dengan hak akses pengguna.
Selain itu, server LDAP juga digunakan untuk mengelola akun pengguna dan memastikan bahwa hanya pengguna yang terotorisasi yang dapat mengakses perangkat jaringan. Kedua server tersebut dapat diintegrasikan untuk mengelola akses pengguna secara efektif dan terpusat.
3 notes
·
View notes
Text
If we’re mutuals and u know me as Cassi/Cass, you qualify for a senior discount
3 notes
·
View notes
Text

Secure Your Remote Connections with TACACS by Advantal
Explore the future of cybersecurity with Advantal's TACACS! 🌍✨ Experience easy, secure remote authentication that keeps your connections safe and your data protected, no matter where you are. Ready to elevate your network's security? Dive into the details with our latest infographic! 🔒💻 #CyberSecurity #RemoteWork #TechSolutions
0 notes
Text


Elevate your network security with #ISE skills. Learn to enforce security policies and gain granular control over user access. Secure your network while enabling seamless connectivity. https://www.dclessons.com/aaa-fundamentals
#AAA#Fundamentals#Configuring#ISE#concepts#Authentication#Authorization#Accounting#Network#Security#Device#Administration#TACACS+#Request#Response
0 notes
Text
youtube
🏗️ Building Your Network's Foundation: Structure & Framework in Cisco DNA Center 🏗️
Hey there, network architects! 👋 Today, we're diving into the exciting world of network design and management with Cisco DNA Center. In this video, we'll create the structure and framework of your network, setting the stage for automated provisioning and management. Let's get started! 🌐🔧
What's in store for us today?
Network Hierarchy: Organize your network into logical groups, like sites, buildings, and floors, for better management and visibility. 🏢🔄
Network Settings: Configure global network settings, such as DNS, NTP, and management IP addresses, to ensure consistent network behavior. ⚙️🌐
Device Credentials: Securely store and manage device credentials, enabling DNA Center to automate device onboarding and management. 🔒🔑
IP Address Pools: Create and manage IP address pools for different network segments, ensuring efficient IP address utilization. 📐📏
Network Profile: Define network profiles that combine IP address pools, QoS, and other network settings, allowing for consistent network segmentation. 📜🔑
Auth Template: Create authentication templates to define device authentication methods, such as TACACS+, RADIUS, or local authentication. 🔐🔓
Let's see the process in action! Here's a quick rundown of how to create and configure these essential network components in Cisco DNA Center:
Network Hierarchy:
Navigate to "Network" > "Hierarchy" and create your desired network hierarchy.
Define parent-child relationships between network entities, like sites, buildings, and floors.
Network Settings:
Go to "Policy" > "Global" and configure global network settings, such as DNS, NTP, and management IP addresses.
Device Credentials:
In "Policy" > "Credentials," create and manage device credentials for different device types.
IP Address Pools:
Under "Policy" > "IP Address Management," create IP address pools for different network segments.
Network Profile:
In "Policy" > "Network Profiles," create network profiles that combine IP address pools, QoS, and other network settings.
Auth Template:
Go to "Policy" > "Authentication" and create authentication templates for device authentication.
What does the network framework look like? Here's a sneak peek at the Cisco DNA Center interface after configuring these essential network components:
https://64.media.tumblr.com/.../cisco-dna-center-network-framework.png
So there you have it! Creating the structure and framework of your network in Cisco DNA Center is a crucial first step towards automated network provisioning and management. Happy networking! 💻🌟
#CiscoDNACenter #NetworkDesign #NetworkManagement #TechTips #NetworkFoundation
0 notes
Text
what does vpn and device management mean
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what does vpn and device management mean
VPN Encryption
Title: Understanding VPN Encryption: Securing Your Online Privacy
In the digital age, where cyber threats lurk around every virtual corner, safeguarding your online privacy has become paramount. Virtual Private Networks (VPNs) offer a layer of protection by encrypting your internet connection, shielding your data from prying eyes. But what exactly is VPN encryption, and how does it work?
VPN encryption is the process of encoding data transmitted between your device and the VPN server. This encryption converts your data into an unreadable format, making it unintelligible to anyone intercepting it. It employs complex algorithms to scramble the information, rendering it useless to hackers, ISPs, and government surveillance agencies.
The strength of VPN encryption is determined by the type of encryption protocol it utilizes. Common protocols include OpenVPN, L2TP/IPsec, IKEv2/IPsec, and SSTP, each offering varying levels of security and performance. OpenVPN, known for its open-source nature and robust security features, is widely regarded as one of the most secure protocols available.
Once your data is encrypted, it travels through a secure tunnel to the VPN server, where it is decrypted and forwarded to its intended destination. This process ensures that even if someone manages to intercept your data, they would only see a jumble of meaningless characters.
VPN encryption protects sensitive information such as passwords, credit card details, and browsing history from being intercepted and exploited by cybercriminals. It also shields your online activities from surveillance and censorship, allowing you to browse the internet with anonymity and freedom.
In conclusion, VPN encryption is a vital tool for safeguarding your online privacy and security. By encrypting your internet connection, VPNs offer peace of mind and ensure that your sensitive data remains confidential in an increasingly interconnected world.
Network Security Protocols
Network security protocols are essential components of any organization's cybersecurity strategy, serving as the foundation for safeguarding sensitive data and preventing unauthorized access to networks. These protocols establish rules and procedures for securely transmitting and receiving data over a network, ensuring confidentiality, integrity, and availability.
One of the most widely used network security protocols is Secure Sockets Layer (SSL) or its successor, Transport Layer Security (TLS). SSL/TLS protocols encrypt data transmitted between a client and a server, protecting it from eavesdropping and tampering. Websites, email servers, and other network services often employ SSL/TLS to secure communications.
Another critical protocol is Internet Protocol Security (IPsec), which provides secure communication at the IP layer. IPsec can be used to establish virtual private networks (VPNs), encrypting data as it traverses insecure networks such as the internet. This ensures that sensitive information remains confidential even when transmitted over untrusted networks.
In addition to encryption protocols, authentication protocols play a vital role in network security. Protocols like Remote Authentication Dial-In User Service (RADIUS) and TACACS+ authenticate users before granting access to network resources, helping prevent unauthorized access.
Furthermore, network security protocols include intrusion detection and prevention systems (IDPS), which monitor network traffic for suspicious activity and take action to block or mitigate potential threats. These systems use protocols such as Snort and Suricata to analyze network packets and detect anomalies indicative of malicious behavior.
Overall, network security protocols form the backbone of a robust cybersecurity posture, providing essential mechanisms for protecting data, verifying identities, and detecting and responding to threats. By implementing and enforcing these protocols, organizations can mitigate the risk of data breaches and ensure the integrity and confidentiality of their network communications.
Remote Access Management
Remote access management is a crucial aspect of modern business operations, allowing employees to connect to their work systems from outside the office securely and efficiently. With the rise of remote work culture, the need for effective remote access management solutions has become more prominent than ever.
Remote access management involves the process of granting, revoking, and monitoring employees' access to company systems and data from remote locations. This can be achieved through various technologies such as Virtual Private Networks (VPNs), remote desktop software, and cloud-based solutions.
One of the key benefits of remote access management is increased flexibility and convenience for employees. They can access important files, applications, and resources from anywhere, at any time, enabling them to work efficiently even when they are not physically present in the office.
However, remote access management also poses certain challenges, particularly in terms of security. As employees connect to the company's systems from external networks, there is an increased risk of unauthorized access and data breaches. Therefore, businesses need to implement robust security measures such as two-factor authentication, encryption, and regular monitoring to protect their sensitive information.
Overall, effective remote access management is essential for maintaining productivity and security in today's remote work environment. By implementing the right tools and best practices, businesses can ensure that their remote access systems are secure, reliable, and accessible to authorized personnel only.
Endpoint Device Control
Endpoint device control refers to the management and oversight of devices connected to a network, such as computers, smartphones, tablets, and IoT (Internet of Things) devices. It is a critical aspect of cybersecurity and network administration, allowing organizations to enforce security policies, monitor device activity, and mitigate potential risks.
One of the primary goals of endpoint device control is to prevent unauthorized access to sensitive data and resources. This is achieved through various measures, including the implementation of access controls, encryption, and authentication mechanisms. By restricting access to authorized users and devices, organizations can reduce the likelihood of data breaches and security incidents.
Endpoint device control also involves monitoring device activity in real-time to identify and respond to potential threats. This may include detecting unusual or suspicious behavior, such as attempts to access restricted resources or malware infection. By continuously monitoring device activity, organizations can quickly detect and mitigate security threats before they escalate into more significant incidents.
In addition to security benefits, endpoint device control can also help organizations improve operational efficiency and compliance with regulatory requirements. By centrally managing and enforcing security policies across all devices, organizations can streamline administration tasks and ensure consistency in security practices. Furthermore, endpoint device control solutions often provide reporting and auditing capabilities, allowing organizations to demonstrate compliance with industry regulations and standards.
Overall, endpoint device control is a critical component of modern cybersecurity strategies, enabling organizations to protect their data, systems, and networks from a wide range of threats. By implementing robust endpoint device control measures, organizations can enhance their security posture, reduce risks, and safeguard their valuable assets.
Secure Data Transmission
Data transmission is a critical aspect of modern information technology, allowing data to be sent and received between computers, servers, and other devices. Securing this transmission is essential to protect the confidentiality, integrity, and authenticity of the information being shared.
Secure data transmission involves encrypting the data before it is sent and decrypting it upon receipt, ensuring that only authorized parties can access and understand the transmitted information. Encryption algorithms such as AES, RSA, and SHA are commonly used to secure data during transmission, making it extremely difficult for cybercriminals to intercept and decipher the transmitted data.
In addition to encryption, secure data transmission also involves using secure communication protocols such as HTTPS, SSL/TLS, and IPsec. These protocols establish a secure connection between the sender and receiver, providing an additional layer of protection against eavesdropping, tampering, and data manipulation.
Furthermore, implementing robust authentication mechanisms such as digital certificates, public key infrastructure (PKI), and multi-factor authentication can help verify the identity of the parties involved in the data transmission process, reducing the risk of unauthorized access and data breaches.
Overall, secure data transmission is essential in safeguarding sensitive information and maintaining the trust of users and customers. By implementing encryption, secure protocols, and authentication mechanisms, organizations can ensure that their data remains confidential, secure, and protected during transmission across networks and devices.
0 notes
Text
CBS350-8T-E-2G-EU Thiết bị chuyển mạch Cisco chính hãng
SSS Việt Nam hiện đang cung cấp một trong những thiết bị Cisco hàng đầu trên thị trường, đó là Switch Cisco CBS350-8T-E-2G-EU với mức giá cạnh tranh, chất lượng cao.
Switch Cisco CBS350-8T-E-2G-EU là một thiết bị chuyển mạch phân phối cấp độ truy cập có 8 cổng Gigabit Ethernet và 2 cổng Gigabit SFP cho phép kết nối dây hoặc sợi quang. Với thiết kế đơn giản nhưng hiệu suất ấn tượng, thiết bị phù hợp cho những mạng nhỏ trung bình có đến 50 người dùng.
Switch hỗ trợ công nghệ chống va đập và chuyển tiếp frame IEEE 802.3x cho phép tối ưu hóa lưu lượng mạng. Các tính năng bảo mật tiêu chuẩn như port security, SNMP v3, 802.1x, RADIUS, TACACS+ giúp bảo vệ mạng an toàn hiệu quả. Điểm nổi bật là tính tương thích cao, có thể hoạt động liền mạch trên môi trường Cisco DNA hoặc mô hình hỗn hợp khác.
Ngoài ra, switch còn hỗ trợ các tính năng như quản lí tập trung thông qua Cisco DNA Center, tự động cập nhật phần mềm và bản vá lỗi a
https://sss.net.vn/thiet-bi-chuyen-mach-cisco-cbs350-8t-e-2g-eu

0 notes
Text
The Evolving Wireless Network Security Market
The wireless network security market has seen tremendous growth and evolution over the past decade. As more organizations adopt cloud computing and mobility, protecting enterprise wireless networks from cyber threats has become a top priority. This article provides an in-depth look at the current state of the wireless network security market, emerging trends, solutions, challenges, and future outlook.
Key Wireless Network Security Market Drivers
Several factors are fueling the growing demand for wireless network security solutions:
Growth of Wi-Fi and Wireless Networks
With the proliferation of smart devices, Wi-Fi 6, 5G, and the Internet of Things (IoT), enterprises are increasingly adopting wireless networks. This expansion of wireless connectivity has opened up more attack surfaces for hackers. Organizations need robust wireless security to protect against unauthorized access, data exfiltration, malware injection, and network misuse.
Cloud Adoption
As organizations move more applications and workloads to the cloud, they need to secure wireless access to cloud-based resources. Since wireless connections are inherently less secure than wired networks, additional safeguards must be deployed.
Compliance Mandates
Industry regulations like HIPAA, PCI DSS, and SOX require stringent wireless security measures. Non-compliance can lead to heavy penalties and loss of reputation. This is compelling organizations to invest in WLAN security solutions.
Remote Workforce Growth
The COVID-19 pandemic triggered a surge in remote work. Gartner predicts that by 2024, 60% of workers will be working remotely at least some of the time. As more employees work from home, wireless network security becomes critically important.
Request For Sample: https://dimensionmarketresearch.com/report/wireless-network-security-market/requestSample.aspx
Key Wireless Network Security Challenges
While wireless connectivity provides flexibility and productivity gains, it also introduces security risks such as:
Rogue Access Points
Can allow hackers easy access to internal networks undetected.
Evil Twins
Fraudulent rogue APs that mimic real APs to trick users into connecting to a malicious network.
Jamming
Disrupting wireless signals through radio frequency interference.
Packet Sniffing
Intercepting wireless traffic to steal data, credentials, and passwords.
Man-in-the-Middle Attacks
Inserting an attacker between wireless clients and APs to monitor and alter traffic.
Denial of Service
Flooding WAPs with bogus requests to disrupt connectivity.
Wireless Network Security Market Segments
The wireless network security market can be segmented by component, solution, end-user industry, and region.
Components
Hardware - Wireless intrusion prevention systems (WIPS), wireless LAN controllers, access points.
Software - Unified threat management, next-gen firewalls, AAA/RADIUS servers, encryption.
Services - Professional, managed services, training.
Solutions
Access Control and Authentication - RADIUS, TACACS+, 802.1X.
Intrusion Detection and Prevention - WIPS, network behavioral analysis.
Encryption - WPA2/WPA3, SSL, VPN.
Unified Threat Management - Next-gen firewalls with wireless security capabilities.
Mobile Device Security - MDM, MAM.
Security Information and Event Management - For threat monitoring and incident response.
End-User Industries
BFSI
Government
Healthcare
Education
Retail
Manufacturing
IT and Telecom
Other
Regions
North America
Europe
Asia Pacific
Latin America
Middle East and Africa
Key Wireless Network Security Vendors
The wireless network security market is served by a mix of large networking vendors and specialized security firms:
Cisco Systems
Fortinet
Juniper Networks
Extreme Networks
Huawei
WatchGuard
Aruba Networks (HPE)
Ruckus Wireless (CommScope)
Palo Alto Networks
Symantec
McAfee
Sophos
Avast
Pulse Secure
WiJungle
Buy Now: https://dimensionmarketresearch.com/checkout/wireless-network-security-market.aspx
Emerging Wireless Network Security Trends
Here are some of the emerging technology trends shaping the wireless network security market:
AI and ML
Artificial intelligence and machine learning is being applied for threat detection, behavioral analysis, and anomaly detection. This allows for more proactive and adaptive security.
Zero Trust
The zero trust model is gaining traction for wireless security. It mandates strict identity verification and least privilege access, assuming all users and devices are potentially compromised.
SASE
Secure access service edge (SASE) converges network and security functions like SD-WAN, VPNs, FWaaS, CASB, SWG and ZTNA into a cloud-native service. This boosts wireless security and flexibility.
5G Security
5G will expand the wireless attack surface. Additional virtualization, slicing, edge computing, and new device types will require enhanced 5G security solutions.
Breach and Attack Simulation
Proactively stress testing wireless networks using attack simulations helps identify security gaps before hackers do.
Wireless Network Security Market Outlook
According to Grand View Research, the global wireless network security market size is projected to reach USD 15.55 billion by 2025, growing at a CAGR of 11% during the forecast period. High Wi-Fi adoption in enterprises, rise of IoT devices, and WFH trends will continue to drive robust WLAN security demand.
North America holds the largest wireless network security market share, followed by Europe and APAC. The metrics that organizations will look to improve using wireless security solutions include:
Reduced security breaches
Faster threat detection and incident response
Achieving compliance with regulations
Increased network visibility and control
Blocking advanced wireless attacks
Reduced business disruption
Leading vendors will focus on capabilities like cloud-based management, AI-enhanced analytics, 5G readiness, and Managed Detection and Response (MDR). As networks evolve, security solutions will need to be more automated, intelligent, and integrated in order to secure the expanding wireless attack surface.
Inquiry For Sample: https://dimensionmarketresearch.com/enquiry/wireless-network-security-market.aspx
FAQs About the Wireless Network Security Market
What are the key wireless network vulnerabilities?
Some of the main wireless network security vulnerabilities include rogue access points, misconfigured devices, out-of-date firmware, lack of encryption, weak passwords, denial of service attacks, evil twin attacks, side channel attacks, packet sniffing, and man-in-the-middle attacks.
Why is wireless network security important?
Wireless networks are more vulnerable than wired networks due to the open nature of radio communications. Without adequate security, wireless networks can be compromised leading to data breaches, malware infections, credential theft, legal and regulatory problems, and huge financial losses.
What are best practices for wireless network security?
Best practices include restricting wireless access, segmenting wireless traffic, enforcing strong encryption like WPA2/WPA3, using EAP methods and AAA servers, implementing WIPS, enabling firewalls and DNS filtering, isolating IoT devices, automated monitoring for threats, and regular penetration testing.
How does a WIPS work?
A wireless intrusion prevention system monitors radio spectrum traffic to detect rogue devices, DoS attacks, evil twins, side channel attacks, spoofing, and more. It can block threats by disconnecting rogue APs, preventing client connections, AP containment and RF jamming.
What is the difference between WPA2 vs WPA3?
WPA2 uses an older encryption protocol called CCMP that has vulnerabilities, while WPA3 uses more secure SIMO encryption. WPA3 also provides better protections for open Wi-Fi networks through SAE (Simultaneous Authentication of Equals).
Why is Zero Trust important for wireless security?
The open and transient nature of wireless connections makes them prone to man-in-the-middle attacks. Applying a Zero Trust approach, where all users and devices must be continuously authenticated and authorized, greatly reduces wireless security risks.
Conclusion
Wireless connectivity has become a lifeline for modern organizations. But wireless networks also introduce new attack vectors. Hacking of Wi-Fi networks threatens to disrupt operations, enable data theft, and result in large compliance fines. Companies can confidently embrace wireless technologies and support increasingly mobile users and IoT ecosystems by implementing modern solutions for wireless intrusion prevention, access control, encryption, multi-factor authentication, zero trust, and AI-driven threat detection. With strong fundamentals like security awareness training, robust wireless network security policies, and regular audits, organizations can take full advantage of wireless connectivity without compromising security.
0 notes
Text
corolar, work from home, 2021 BOLT remotely logging into servers at Sibiu and then London, or 2014 E&F Ltd intellectual property Ramat-Gan IL when remotely connect into USPTO servers, or 2016 when accessing SSTS JUNTAH for ID card verification at Actuary office, using digital signatures like Token USB encrypted Public Notary user. you do not imply electronic biddings onto same HDD, onto same SSD, onto same NVMe storage device. you need TWO different computers, one for SEAP electronic biddings, winning pharma distribution and orders, or DeTomasi Ltd lorry shipping awarded cargo (2014), or other assimilated Chrome Book bill payments (mind BOLT). and another SSD for Internet social media traffic, still using landline, where usually in the past was written TACACS II+ fingering router table is FBI jurisdiction (fingering router table is indeed not local police, Global reach). unless VOICE feature Vodafone Inc 2011, provisioned onto GSM smartphone, so there goes LOCAL JURISDICTION and eavesdropping eye. m
0 notes
Text
Hey old gaia mutuals!!
Does anyone happen to have any old saves of Cassi’s sprites? I just found out photobucket deactivated my old account “orz
No worries if not, I just miss my girl
0 notes
Text
What Is TACACS and How Does It Compare to RADIUS?
TACACS+ and RADIUS are both network protocols used for managing authentication, authorization, and accounting (AAA) in network devices. TACACS+ is Cisco proprietary, providing more granular control, encrypting the entire packet, and separating authentication, authorization, and accounting processes. In contrast, RADIUS, an open standard, primarily encrypts only the password and combines these processes. TACACS+ is often preferred for device administration, while RADIUS is widely used for user access control in network services. More details can be found Here : https://www.zupyak.com/p/4287028/t/what-is-tacacs-and-how-does-it-compare-to-radius.
0 notes
Text
CCNA 200-301 Complete course - Not Just another CCNA course
Learn CCNA from a Triple CCIE (R&S, Security, SP) certified instructor in just 27 Hours. The instructor has 15 years of extensive experience in the network industry. It is an engaging course which include animations on several important topics, infographic slides and extensive lab practice.
The course is divided into six different chapters as follows:
1. Network Fundamentals
2. Network Access
3. IP Connectivity
4. IP Services
5. Security Fundamentals
6. Automation and Programmability
In “Network fundamentals” chapter, we have covered History of Networking Standards,TCP/IP, OSI, Transport Layer, TCP & UDP, Multiplexing, Virtualization, Cloud Computing, Cabling types, IPv4 & IPv6 addressing, IPv4 subnetting, Default Gateway.
In “Network Access” chapter, we have covered Switching technology, Wireless technology, and Cisco WLAN deployments.
In “IP Connectivity” chapter, we have covered IP routing process, static and dynamic routing, and FHRP protocols.
In “IP Services” chapter, we have covered DNS, NAT, DHCP, SNMP, FTP, TFTP, and QOS.
“Security fundaments” chapter is composed of security terminologies, different types of attacks & vulnerabilities, AAA, TACACS+, RADIUS, Security program, Internet VPN, ACLs, standard and extended ACL.
“Automation & programmability” chapter is comprised of Types of planes, controllers, SDN, NBI, SBI, APIC, ACI, Cisco SDA, Rest API, Software CRUD actions, HTTP verbs, URI, DATA Serialization, JSON, traditional configuration model versus centralized configuration model, ANSIBLE, PUPPET, and CHEF.
So, are you ready to Jumpstart your career in networking?
Who this course is for:
A person who is passionate to begin his career in the field of IT and Networks with ZERO knowledge
College students, Undergraduate students, and Fresh graduates who wish to get a thorough idea about IT & Network field and its future potential
Entry Level IT engineers who want to grow their career to the next level in the field of networking
System Engineers & administrators, cloud engineers, network security engineers, and IT desktop support engineers who lack network & switching infrastructure knowledge, how network functions, how traffic flows into the network end to end, and how to troubleshoot the basic network problems
((( 50% Off Now The best CCNA course in online )))
CCNA 200-301 Complete course - Not Just another CCNA course
A complete course which covers all the exam topics of CCNA 200-301. It includes 18 Hours of Theory and 9 Hours of Lab
https://www.udemy.com/course/ccna-200-301-complete-course-not-just-another-ccna-course/?couponCode=785A37938B1A9DC10980
0 notes
Text
youtube
🔓 Unlock Next-Level Network Security with Cisco ISE & TACACS! 🔓
Hey there, network ninjas! 👋 Let's dive into how Cisco's Identity Services Engine (ISE) and its trusty sidekick, TACACS (Terminal Access Controller Access Control System), can beef up your network security. 🤝
What's the hype about Cisco ISE? 🤔 ISE is like your network's secret weapon, offering advanced access control, authentication, and authorization features. It's all about keeping the good guys in and the bad guys out, while making your life as a network admin way easier. 💪
And TACACS? 🤔 TACACS is ISE's wingman, enabling centralized authentication, authorization, and accounting for network devices. It's like having a dedicated bouncer for your routers, switches, and firewalls, making sure only the right people and devices get in. 🔐
Why should you care? 🤨 With ISE and TACACS teaming up, you get an extra layer of security for your network infrastructure. No more unauthorized access or cyber threats wreaking havoc! 🚫 It's like having your own personal network security dream team, always got your back. 🏆
Ready to take your network security to the next level? 💪 Give Cisco ISE and TACACS a shot, and watch as they work together to keep your network safe and sound. You'll be the talk of the networking town in no time. 😎
Stay secure, my friends! 🔒
#CiscoISE #TACACS #NetworkSecurity #CyberThreats #TechTalk
0 notes
Text
TACAC rambles
Had someone who didn’t know Ace Attorney RP was a thing talking about how “novel” the idea was, and it got me thinking back to TACAC stuff, so I went back to re-read some stuff.... Just... I will always cherish early day TACAC stuff, but holy cow, re-reading the stuff that came with the short revival honestly has me in tears RN...
Just... RNG went OFF on us during this period and we had some real ‘WTF’ moments that just -chef kiss-
Just for an idea of some of the things that happened that honestly still make me laugh...
Became accepted that the apartment complex was an absolute mess given everything that had happened there-- including stubborn blood stains. Bobby Bright and Simon Blackwell come in, sees Godot cleaning the walls, y!Klav throws him under the bus because he doesn’t want to clean, and Bobby tackles Godot and tries to arrest him.
Mold Monster-- just... what do you expect from that apartment complex? Mold took over the kitchen (RNG, Why did that have to be the choice?), and rather than help Godot fend off the beast, y!Klav and Rou run off to investigate an alleged crime scene that Diego lied about (Guess what, RNG ninjas struck those two again). Not too bad, right? WRONG! RNG dictated that mold monster abducted Godot, pulled him into the fridge and he spent the night there because no one checked the cries for help. RNG decided that mold monster bit Godot, that y!Klav unleashed ANOTHER MOLD MONSTER to fight the current mold monster, and they had a kaiju battle in the kitchen that formed into one which they walled off with Ikea furniture that was being built in the lobby. Thanks, RNG! Oh, but wait... it gets better... y!Klav, Bobby(?), and Wocky decide to save the kitchen and that was going baaaaad according to RNG... It was not looking good, and then Jake Marshall comes strolling in and RNG decides that the mold monster is going to be the perfectly behaved pet with his rolls... Sit, stay, rollover... Jake tamed a mold monster and it moved into the air vents.... Rolls for Jake’s mold monster are legendary.
So the Iron Infant was a thing... rando just comes in and decided THAT was the character they wanted to play and it was fantastic... kinda... My hats off to Iron Infant mun... they ended up living IN the couch for like... a month... and when we were joking about “What’s that smell? Is something dead?“ like... Iron Infant LEGIT comes out of hiding after a month of silence and just like, “He had been living off moisture in the cushion and crumbs falling in and had grown weak, but with them pulling him out of the couch he was stuck in, he was able to flee!”. Absolute legend!
Another rando we called CIA man... Played JoJo-ish characters... but like... they were feds with Metal Gear tech, bionics and cyborgs, ora ora ora punch with Dragon Ball level fighting... They waltz right in and right off the back, “y!Mia! The CIA wants you to take this case, we will make you a multi millionaire for taking this case.”.... “What’s that y!Klav? You have a friend sick in the hospital? We will give him bionic eyes to make him better!”.... Arrests Kay Faraday the moment she says her name “We know you! You’re under arrest!” ... Legit Dragon Ball Z fight in their room with their cyborg brother, and a few days later, cyborg brother decides to force y!Klav and Godot to prosecute... never mind that neither one are actually prosecutors here... Godmods right out of the gate a fight with the two, and when Godot RNG just like, “Na, fam... ya aint throwing me through a wall”, continued to Godmod breaking Godot’s body into tiny pieces before hunting down y!Klav who tried to escape... Don’t worry, they ended up find in the hospital in the end, but the cyborg’s brain and body exploded.... Always an insane time when CIA man is around...
Lana telling o!Ema about Gant’s virility in the bedroom
All the Klavs... it’s not TACAC without 50 Klavs...
New Klav that moved into the complex gets dubbed “Cosplay Klav (CK) because he thought the two Klaviers he saw were cosplayers and called them such... CK has HORRID RNG...
Dr.Night installed a safe in the lobby to lock up his booze because.. ya know, people can’t keep their hands off of it. Hobo wants into the safe (naturally). First time, Trucy RNG’s the door off the safe.
Second safe? It’s hidden behind a picture... it’s not safe because Hobo has Amnesia!Krissy take down the painting and tries to make him open the safe. CK, A!Krissy’s brother just like, “Brudder! Don’t let this criminal influence you! Hobo, you so bad!” -fist slam animation-
Hobo RNG’s for CK.....
Safe door opens because of CK....
CK gets y!Klav a date with Franny! He’s acting as a wing man... gets the tickets for a concert for them, arranged the dinner and date... should be PERFECT, right? No... RNG hates CK...
RNG decided that their bikes were demolished by bears (of course it’s bears).
RNG decided that y!Klav didn’t just not make it back to the complex, but that he had been kidnapped.
RNG decided that the car that CK punched in anger exploded and set the street on fire while Franny walks off all cool like
RNG decided that Gumshoe was a hero that saved the day.
All of this of course was apparently broadcasted on TV for the complex to pick up (New TV means we got things other than Law and Order).... Polly was horrified....
I’m still back reading in doses... just... holy cow, been a while since I’ve laughed loudly so much. I know I’m likely just talking into the wind, but still....
1 note
·
View note
Text
Why we choose H685fq 5G router?

The E-Lins H685fq is a compact, Gigabit Ethernet, ruggedized 3G/4G/LTE/5G cellular networking solution designed for mission-critical connectivity in the most challenging environments. It is qualified for M2M (Machine to Machine), IoT (Internet of Things) and In-Vehicle applications. Super mini size suitable for embedding applications.
What fields or applications H685fq work in?
H685fq is widely used in more than twenty industrial fields, such as CCTV security surveillance, AMR, vehicle, retails, vending machines, power control, water schedule, traffic, oil field, weather forecast, environmental protection, street lamp control, post, bank and many other fields.
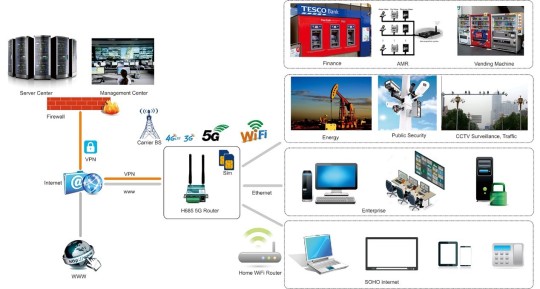
What key features of H685fq owns?
Multi-carrier 2G/3G/4G LTE/5G support with SIM card slot
LAN/WAN Gigabit Ethernets * 2
Cellular/WAN RJ45/WiFi client failover and Load Balance (Bandwidth link bonding)
Supports LTE Advanced with SIM-based auto-carrier selection
Cloud-managed (with NMS network management system), TR-069, Web management, SMS, SSH/Telnet/Command, SNMP
WiFi (802.11 a/b/g/n, 2.4Ghz)
Certified 3G/4G/LTE enterprise/industrial grade internal modems
Built-in transient and reverse polarity voltage protection, over-current and over-voltage protection;
5-40V DC voltage input range (5-60V DC option), Dual Power Inputs / Power Failover;
GPS / GNSS support
Serial Port
DI/DO port * 4
Supports Ethernet (T1, DSL, Cable, MetroE), WiFi as WAN, and Metro WiFi
Ruggedized to ensure always-on connectivity
Create real-time alerts to monitor uptime
Offer secure, guest WiFi to passengers
Advanced security, VPN, and stateful firewall to protect sensitive data
Robust Metal Case is ruggedized for vibration, shock
Desktop, Wall-mount and Din-rail mount of installation
External antenna connectors for high gain antennas replacement
MIMO supported
Main Feature
Cellular 2G/3G/4G LTE/5G (FDD/TDD)(SA/NSA)
WiFi as WAN
Failover/Failback and Load Balance (Bandwidth bonding)
Advanced Modem Failure Check
IP Passthrough
WAN ports support Cell/Static IP/DHCP/PPPoE (on demand, keep alive, schedule, manual, standby)
DHCP Server, Client, Relay
DNS and DNS Proxy
DDNS
UPnP
DMZ
Multicast/Multicast Proxy
QoS (DSCP and Priority Queuing)
MAC Address Filtering
VLAN 802.1Q
802.11 a/b/g/n/AC
Up to 64 connected devices
WPA2 Enterprise (WiFi)
Hotspot/Captive Portal
SSID-based Priority
IPsec Tunnel, PPTP, L2TP, GRE Tunnel, OpenVPN (option), DMVPN (option);
OSPF/BGP/RIP, Virtual Server/Port Forwarding, IPv6 (option), VRRP;
E-Lins Enterprise Cloud Network Management System (NMS)
Web UI, API, CLI/SSH/Telnet
Data Usage Alerts (router and per client)
Advanced Troubleshooting (support)
Device Alerts
SNMP
SMS control
TR-069
RADIUS and TACACS+ support
802.1x authentication for Ethernet
Certificate support
ALGs
MAC Address Filtering
Advanced Security Mode (local user management only)
Per-Client Web Filtering
IP Filtering
Content Filtering (basic)
Website Filtering
Zone-Based Object Firewall with host address (IP or FQDN), port, and mac address
Other Details: NAT, SPI, port blocking, service filtering (FTP, SMTP, HTTP, RPL, SNMP, DNS, ICMP, NNTP, POP3, SSH), protocol filtering, WAN ping (allow/ignore)
Automated WAN Failover/Failback support
WAN Affinity and QoS allow prioritization of VoIP services
Advanced VPN connectivity options to HQ
SIP ALG and NAT to allow VoIP and UC communications to traverse firewall
MAC Address Filtering
802.1p/q for LAN QoS segmentation and treatment of VoIP on LAN
Private Network support (wired and 4G WAN)
support firmware update locally, remotely (LAN, WiFi and OTA WAN) and NMS (Network Management System) option;
4 ports, 0-3.3V. Support status monitor via SMS and Email;
Option: customers can order E-Lins switch control board (5-40VDC supported)
Cellular and WiFi MIMO supported;
Syslog (local and remote);
DDNS;
DNS proxy;
Optimized EMC design;
Real-time clock (NTP, support update with defined hours);
WAN/LAN/Memory statistics;
Local/remote profiles backup and retrieve;
Modbus is supported;
What Celluar bands H685fq supports?
Here are the bands H685fq supports:
Cellular
Compatible Mobile Networks
5G (SA and NSA)
4G LTE (FDD/TDD)
3G UMTS WCDMA (HSUPA/HSDPA/HSPA/HSPA+/DC-HSPA+)
Cellular Frequency
5G Sub-6G:
n1/n2/n3/n5/n7/n8/n20/n28/n41/n66/n71/n77/n78/n79/n257/n261
4G FDD LTE:
Band 1 – 2100Mhz
Band 2 – 1900Mhz
Band 3 –1800Mhz
Band 4 – AWS(1700/2100Mhz)
Band 5 – 850Mhz
Band 7 – 2600MHz
Band 8 – 900Mhz
Band 9 – 1700Mhz
Band 12 – 700Mhz
Band 13 – 700Mhz
Band 14 – 700Mhz
Band 17 – 700Mhz
Band 18 – 850Mhz
Band 19 – 800Mhz
Band 20 – 800Mhz
Band 21 – 1500Mhz
Band 25 – 1900Mhz G Block
Band 26 – 850Mhz
Band 28 – 700Mhz
Band 29 – 700Mhz (SDL)
Band 30 – 2300Mhz
Band 31 – 450Mhz
Band 32 – 1500Mhz (SDL)
Band 66 – 1700Mhz
Band 72 – 450Mhz
And other more FDD band…
4G TDD LTE (TD-LTE):
Band 48 – 3600Mhz (CBRS)
Band 46 – 5200Mhz
Band 43 – 3700Mhz
Band 42 – 3500Mhz (CBRS)
Band 41 – 2500/2600Mhz
Band 40 – 2300Mhz
Band 39 – 1900Mhz
Band 38 – 2600Mhz
And other more TDD band…
UMTS/HSPA/HSUPA/HSPA/HSPA+/DC-HSPA+ (WCDMA/FDD):
2100MHz(B1)/1900MHz (B2)/1800MHz (B3)/ 1700MHz /AWS (B4)/850MHz (B5)/900MHz (B8)/800MHz (B6)/1800MHz (B9)/850MHz (B19)
Notes: There are many different band and frequencies. Please confirm the detailed band and frequency with your carriers before order.
Bandwidth
Downlink data: 5G/NR sub-6: 2Gbps-10Gbps, LTE 2.4Gbps
Uplink data: 5G/NR sub-6:2.5Gbps, LTE 450Mbps
Notes: the bandwidth is peak value. Real value depends on carrier network support.
Network and Band Lock Feature (Option)
Default is unlocked, can use this feature to lock
What other special features H685fq built-in?
Please check with E-Lins sales or tech team to get your answer.
0 notes
Text
WS-C2960X-48TS-L | Thiết bị chuyển mạch Switch Cisco layer 2
I. Thông tin sản phẩm Cisco WS-C2960X-48TS-L - Cisco WS-C2960X-48TS-L là thiết bị mạng chất lượng cao thuộc dòng sản phẩm switch Cisco Catalyst 2960 X series 48 port, được thiết kế để phù hợp với cấu trúc lớp Access. Thiết bị này cung cấp tổng cộng 24 cổng Giga 10/100/1000Mps Base-T, trong đó có 4 cổng uplink GE SFP để kết nối đường truyền quang multi mode hoặc single mode. Mặt trước thiết bị WS-C2960X-48TS-L Switch Cisco WS-C2960X-48TS-L chỉ nặng có 9,4 Pounds tương đương với 4,2kg tiện lợi trong di chuyển và thi công. Sử dụng phần mềm IOS cơ bản với các mô hình chuyển đổi, IOS tự động cấu hình mạng LAN cơ bản, các tính năng, các thiết lập tuân thủ tiêu các tiêu chuẩn 802 trong Switch Cisco chính hãng. Không riêng Cisco WS-C2960X-48TS-L mà nhiều sản phẩm khác của hãng Cisco còn được biết đến với tính bảo mât mạng cao. Sử dụng các giao thức SSH, SSL, SCP RADIUS và TACACS kết hợp với mật mã SNMPv3 802.1x.Gán VLAN 802.1x, chặn các quyền truy cập qua MAC 802.1x, sử dụng bộ lọc IGMP / Throttle… Đây được đánh giá là sản phẩm nổi bật trong dòng Switch 2960 X Series nhờ có thiết kế với 48 cổng chuyển đổng Gigabit, 4 cổng quang SFP hỗ trợ tính năng LAN BASE. Thiết bị có khả năng xếp chồng lên nhau một cách dễ dàng giúp tiết kiệm không gian cũng như dễ dàng phát triển và mở rộng hệ thống. Không những thế, mẫu Switch Cisco WS-C2960X-48TS-L còn có khả năng cung cấp chế độ bảo mật vô cùng an toàn, cấp quyền hạn chế truy cập vào website, đồng thời giúp giảm thiểu các mối đe dọa khác đến hệ thống. Điểm được đánh giá cao nhất trên sản phẩm này và được khách hàng ưa chuộng chính là ở khả năng hoạt động ổn định, độ bền cao, giá thành hợp lý. Tính năng thông minh tích hợp sẵn trên máy cũng giúp đơn giản hóa việc lập PLAN và triển khai hệ thống. Nó còn cho phép việc theo dõi, phát hiện và xử lý sự cố trong hệ thống mạng LAN được hiệu quả hơn. Thông tin chi tiết sản phẩm Cisco WS-C2960X-24TS-L 1. - ygutzjutw9

0 notes