#teamviewer patch
Explore tagged Tumblr posts
Text
Ramadan Sale Is Here Go And Grab Your Gscan Zenith Z5
Looking for the tools to diagnose your cars and other vehicles,
now the Auto Max tools also provide car battery Scanner tools that make diagnosis easy and simple to use in collaboration with Zenith, the South Korean company

we introduce u to the Gscan Zeith Z5.
Gscan Zenith Z5
It is the first automotive diagnostic scan tool in the Z series. With our vast diagnostics software and the world's best industrial tablet, Z5 will give you diagnostic confidence.
Key Features of GScan Zenith Z5 are mentioned below:
A powerful octa-core processor for optimum diagnostic performance and fast management of workshop operations.
Based on Android 9 os provides Quick boot-u, multi-tasking, fast networking, and enhanced system security.
Eyellumicate Displays LCD provides crystal-clear views indoors and outdoors, offering a field-optimized display in a bright workshop environment.
Diagnostic software programmed by engineers with technicians in mind.
Zenith Z5 functions as a"pass-thru" device for programming the ECUs for multiple carlines.
Zenith Z5 accepts power & signals of a 24v system and supports Bi-directional communications with commercial trucks and buses.
Robust connectivity allows for smart updates, Quick feedback, TeamViewer support, Bluthood printing, browsing, and much more.
Simple, Yet Intuitive Layout
Zenith Z5 offers a simple iconic main menu for easier and quick access to desired functions. With 3 available display modes, the user can customize the theme and button locations.
Service Function
Time is money. Z5 offers shortcuts to the most frequently used functions in the workshops to save time for technicians to navigate through the original menu layout.
Quick System Search
The ‘System Search’ option automatically scans all the vehicle systems, reports fault codes, and provides access to advanced diagnostic functions in each system detected.
Data Log & Feedback System
In the case of communication or function error, a user can log the bi-directional data transmission between the tool and vehicle control systems. This log can be sent to the software development team via the log capture & transfer function. The data log files received will be analyzed, feedback will be passed on, and a patch file update provided, if necessary, often within 24 hours of receiving the report, during working days. (Exceptions may apply).
Pre & Post Diagnostic Report
Z5 offers easy creation of diagnostic reports with Pre-scan and Post-scan results. Not only you can save the reports as a PDF file in the internal/external memory, but with the help of its advanced network connectivity, you can print the report directly with a wireless printer or send them to a desired E-mail address.
J2534 Pass-thru
Zenith Z5 acts as a J2534 Pass-thru device for multiple carlines with CAN-Bus, KWP2000, and ISO9141 protocols, supporting J2534 programming and diagnostics. (Exceptions may apply).
Fast & Responsive Graphing Mode
Z5 offers a fast and intuitive graphing mode that instantly self-adjusts the maximum and minimum scale, enabling the users to observe and compare live data more efficiently.
Full-Text Description
No more acronyms and cutting of significant texts. Z5 offers the long-text DTC descriptions in full screen, so you get all the information you need.
Smart Update
Z5 offers a quick and easy software update process with its strong network connectivity. Previous or latest software versions for each carline can be quickly downloaded directly from the server, as per the user’s preference.
Contact Us Now:
+91 92053 23885
+91 99580 57547
Watch Our Videos for More Details:
Automax Tools India YouTube
Topdon India YouTube
Available at Automax Tools India – Trusted by professionals nationwide!
For more details visit: AutoMax tools
#car battery tester#car battery maintainer#car battery charger#car battery scanners#auto max tools#new delhi#car battery jumpers#cars#india
0 notes
Text
RDP on Mobile Devices: Accessing Your Desktop Anytime, Anywhere
In today’s fast-paced world, the ability to access your desktop computer remotely from a mobile device has become increasingly essential.
Remote Desktop Protocol (RDP) enables users to connect to their desktops from anywhere, providing flexibility, convenience, and productivity on the go.
This blog explores the benefits, setup process, and best practices for using RDP on mobile devices.
Benefits of RDP on Mobile Devices
Flexibility: RDP allows users to access their desktops from smartphones or tablets, enabling work to continue seamlessly even when away from the office.
Productivity: With RDP, users can access files, applications, and resources on their desktops, boosting productivity by eliminating the need to transfer files between devices.
Security: RDP connections are encrypted, providing a secure way to access desktops remotely without compromising sensitive data.
Cost-Effective: RDP eliminates the need for expensive hardware or software solutions for remote access, making it a cost-effective option for individuals and businesses.
Setting Up RDP on Mobile Devices
Enable Remote Desktop on Your Desktop: To use RDP, ensure that Remote Desktop is enabled on your desktop computer. Go to Control Panel > System and Security > System > Remote settings, and enable Remote Desktop.
Install an RDP App: Download an RDP app on your mobile device from the respective app store. Popular options include Microsoft Remote Desktop, Chrome Remote Desktop, and TeamViewer.
Configure RDP App: Open the RDP app on your mobile device and add a new connection. Enter the IP address or hostname of your desktop, along with your username and password.
Connect to Your Desktop: Once the connection details are entered, tap on the connection to initiate the RDP session. You will now have remote access to your desktop from your mobile device.

Best Practices for Using RDP on Mobile Devices
Secure Your Connection: Use strong passwords and enable network-level authentication to secure your RDP connection from unauthorized access.
Use a VPN: For an added layer of security, consider using a Virtual Private Network (VPN) when connecting to your desktop remotely via RDP.
Optimize Settings: Adjust display settings and connection speed in the RDP app to ensure a smooth and responsive remote desktop experience on your mobile device.
Monitor Activity: Regularly monitor RDP activity on your desktop to detect any suspicious login attempts or unauthorized access.
Update Software: Keep your RDP app and desktop operating system up to date to ensure compatibility and security patches are applied.
Conclusion
RDP on mobile devices offers a convenient and efficient way to access your desktop anytime, anywhere. By following the setup process and best practices outlined in this blog, users can enjoy the benefits of remote desktop access while maintaining security and productivity. Embrace the flexibility of RDP on mobile devices and unlock the potential of working on the go with ease and convenience.
0 notes
Text
does teamviewer have a vpn mode
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does teamviewer have a vpn mode
TeamViewer VPN feature
TeamViewer, a popular remote desktop and collaboration software, offers a versatile VPN feature that enhances its functionality for users seeking secure connections across multiple devices and networks.
The TeamViewer VPN feature allows users to create a virtual private network (VPN) between their devices, enabling secure and encrypted communication over the internet. This feature is particularly beneficial for businesses and individuals who require access to their devices and networks from remote locations while ensuring data privacy and security.
One of the key advantages of TeamViewer's VPN feature is its ease of use. Users can establish a VPN connection with just a few clicks, eliminating the need for complex network configurations. Whether connecting to a colleague's computer, accessing files on a home network, or remotely managing servers, TeamViewer's VPN streamlines the process, saving time and reducing potential errors.
Furthermore, TeamViewer's VPN employs industry-standard encryption protocols, such as AES 256-bit encryption, to safeguard data transmitted between connected devices. This ensures that sensitive information remains protected from unauthorized access or interception, even when using unsecured public Wi-Fi networks.
Another notable feature of TeamViewer's VPN is its compatibility across various operating systems, including Windows, macOS, Linux, iOS, and Android. This cross-platform support allows users to establish VPN connections between devices regardless of their operating system, promoting seamless collaboration and remote access across diverse environments.
In addition to secure communication, TeamViewer's VPN feature also facilitates remote access to network resources, such as printers, file shares, and applications, enhancing productivity for distributed teams and individuals working from remote locations.
Overall, TeamViewer's VPN feature offers a convenient and secure solution for establishing virtual private networks between devices, enabling users to collaborate, access resources, and manage systems remotely with confidence.
TeamViewer security options
TeamViewer, a popular remote access and support software, offers a range of security options to ensure the safety and confidentiality of users' data and sessions. These security features are crucial for businesses and individuals alike, especially when accessing sensitive information or providing support remotely.
One of the primary security measures provided by TeamViewer is end-to-end encryption. This encryption ensures that data transmitted between devices during remote sessions is encrypted and cannot be intercepted by unauthorized parties. By employing industry-standard encryption protocols, TeamViewer safeguards the confidentiality of user communications and prevents eavesdropping.
Moreover, TeamViewer offers multi-factor authentication (MFA) options to add an extra layer of security to user accounts. With MFA enabled, users must provide additional verification beyond a password to access their TeamViewer accounts, such as a one-time code sent to their mobile device or email. This helps prevent unauthorized access even if login credentials are compromised.
Furthermore, TeamViewer allows users to configure access controls and permissions tailored to their specific needs. Administrators can define which users or groups have access to certain computers or features within the software, ensuring that only authorized individuals can initiate remote connections or perform certain actions.
Additionally, TeamViewer regularly updates its software to patch security vulnerabilities and enhance overall protection against emerging threats. Users are encouraged to keep their TeamViewer installations up to date to benefit from the latest security enhancements and improvements.
In conclusion, TeamViewer offers robust security options, including encryption, multi-factor authentication, access controls, and regular software updates, to ensure the safety and integrity of remote sessions and user data. By leveraging these security features, businesses and individuals can confidently utilize TeamViewer for remote access and support while mitigating security risks.
Remote access with TeamViewer
Remote access tools have become an essential part of modern business operations, offering convenience and flexibility to both individuals and organizations. One of the most popular and widely used remote access tools is TeamViewer.
TeamViewer allows users to connect to remote computers, mobile devices, or servers from anywhere in the world. This powerful software enables users to access files, programs, and other resources on a remote device as if they were physically present in front of it.
One of the key features of TeamViewer is its ease of use. The software can be quickly installed and set up on both the host and client devices, making it a user-friendly option for remote access needs. Additionally, TeamViewer offers high levels of security, with end-to-end encryption ensuring that data transferred between devices is protected from unauthorized access.
Businesses can greatly benefit from using TeamViewer for remote access, as it allows employees to work collaboratively and access necessary resources from any location. IT support teams also find TeamViewer invaluable for troubleshooting issues on remote devices quickly and efficiently.
In conclusion, TeamViewer is a versatile and reliable remote access tool that offers convenience, ease of use, and high levels of security. Whether you are working from home, providing remote support, or accessing files on-the-go, TeamViewer is a valuable software solution for all your remote access needs.
VPN functionality in TeamViewer
VPN functionality in TeamViewer allows users to establish a secure and private connection to remote networks. TeamViewer, a popular remote desktop software, offers this feature to enhance user privacy and security while accessing resources on other networks.
By utilizing VPN in TeamViewer, users can encrypt their internet traffic and mask their IP address, ensuring that their online activities remain anonymous and protected from prying eyes. This is particularly useful for individuals who frequently work remotely or need to access sensitive information over public networks.
One of the key benefits of VPN functionality in TeamViewer is the ability to bypass geo-restrictions and access region-locked content. By connecting to a VPN server in a different location, users can appear as if they are browsing from that specific region, allowing them to access websites, services, and content that may otherwise be unavailable in their own location.
Moreover, VPN in TeamViewer also helps businesses in ensuring secure remote access to their network resources. Employees can securely connect to their company's network from anywhere in the world, without compromising the confidentiality of data transmitted between devices.
In conclusion, VPN functionality in TeamViewer offers users a convenient and secure way to access remote networks, protect their online privacy, and bypass geo-restrictions. Whether for personal or business use, integrating VPN into TeamViewer can significantly enhance the overall remote desktop experience.
TeamViewer privacy settings
Title: Enhancing Privacy with TeamViewer: A Guide to Optimal Settings
TeamViewer is a versatile remote access tool utilized by businesses and individuals worldwide. While its functionality is invaluable for collaboration and support, ensuring privacy remains paramount. Understanding and configuring TeamViewer's privacy settings can safeguard sensitive data and mitigate potential risks.
Secure Connection: Enable encryption for all connections to prevent unauthorized access and data interception. Navigate to Options > Advanced > Show advanced options > Advanced settings for connections to ensure encryption is activated.
Access Control: Customize access permissions to restrict remote control and file transfer capabilities. Utilize the "Access Control" settings to define who can connect to your device and specify the level of control granted.
Blacklisting/Whitelisting: Employ blacklisting or whitelisting features to manage trusted and untrusted devices. This allows you to control which devices can establish connections with your system, enhancing security and reducing the risk of unauthorized access.
Password Protection: Implement strong passwords and enforce password policies to fortify authentication. Utilize complex passwords and enable the option to prompt for a password when accessing unattended devices, adding an extra layer of security.
Two-Factor Authentication (2FA): Strengthen authentication by enabling two-factor authentication. This requires users to provide an additional verification method, such as a code sent to their mobile device, before accessing TeamViewer, reducing the risk of unauthorized access even if passwords are compromised.
Logging and Reporting: Monitor and track remote sessions by enabling logging and reporting features. This provides a record of all connections and activities, aiding in auditing and compliance efforts.
By configuring these privacy settings effectively, users can maximize the security of their TeamViewer connections, safeguarding sensitive data and ensuring peace of mind during remote collaborations and support sessions. Regularly reviewing and updating these settings is crucial to adapt to evolving security threats and maintain robust privacy measures.
0 notes
Text
does the teamviewer vpn make it more secure
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does the teamviewer vpn make it more secure
TeamViewer VPN functionality
TeamViewer, a popular remote desktop software, offers more than just screen sharing capabilities. Among its array of features lies its VPN functionality, providing users with a secure and efficient way to connect devices remotely.
TeamViewer's VPN allows users to establish a virtual private network connection between their devices, regardless of their physical location. This functionality is particularly useful for businesses with remote teams or individuals who need to access resources on a network securely.
One of the key benefits of TeamViewer's VPN is its simplicity. Users can set up a VPN connection with just a few clicks, eliminating the need for complex network configurations. This ease of use makes it accessible to users of all technical levels, from novice to expert.
Security is paramount when it comes to remote connections, and TeamViewer's VPN does not disappoint. It encrypts all data transmitted between devices, ensuring that sensitive information remains protected from unauthorized access. This level of encryption is crucial, especially when accessing sensitive company data or working with confidential files.
Additionally, TeamViewer's VPN offers reliability and stability. Users can rely on it to maintain a stable connection, even over long distances or unreliable networks. This reliability ensures that users can seamlessly access resources and collaborate with colleagues without interruption.
In conclusion, TeamViewer's VPN functionality is a valuable addition to its suite of remote access tools. It provides users with a secure, easy-to-use solution for connecting devices and accessing resources remotely, making it an essential tool for businesses and individuals alike.
Security implications of TeamViewer VPN
TeamViewer VPN offers users a convenient way to establish secure connections between devices over the internet. However, like any other VPN service, it comes with its own set of security implications that users should be aware of.
One of the primary concerns with using TeamViewer VPN is the potential for unauthorized access to sensitive information. While the VPN itself encrypts data transmitted between devices, there is still a risk of interception if proper security measures are not in place. Users must ensure that they are using strong, unique passwords for both their TeamViewer accounts and the devices they are connecting to.
Another consideration is the possibility of vulnerabilities within the TeamViewer software itself. As with any software, there is always a risk of bugs or vulnerabilities that could be exploited by malicious actors. It is essential for users to keep their TeamViewer software up to date with the latest security patches to minimize this risk.
Additionally, users should be cautious when granting remote access to their devices via TeamViewer VPN. While the service allows for convenient remote assistance, it also opens up the possibility of a breach if access is granted to an untrusted party. Users should only grant access to individuals or organizations they trust and should revoke access immediately if any suspicious activity is detected.
Finally, it's crucial for users to monitor their network traffic when using TeamViewer VPN. This can help identify any unusual activity or potential security threats. By staying vigilant and following best practices for network security, users can minimize the security implications of using TeamViewer VPN and enjoy the benefits of secure remote connectivity.
Comparing TeamViewer VPN security features
When it comes to remote access and virtual private network (VPN) solutions, TeamViewer stands out as a popular choice for businesses and individuals alike. However, how does TeamViewer's VPN security features compare to other options on the market?
One of the primary considerations for any VPN solution is its encryption protocol. TeamViewer utilizes AES (Advanced Encryption Standard) 256-bit encryption, which is the same level of encryption used by many financial institutions and government agencies. This ensures that data transmitted over the VPN remains secure and confidential.
Another important aspect of VPN security is authentication. TeamViewer employs two-factor authentication (2FA) to verify the identity of users connecting to the VPN. This adds an extra layer of security by requiring users to provide a second form of verification, such as a one-time code sent to their mobile device, in addition to their password.
Furthermore, TeamViewer offers granular access controls, allowing administrators to restrict VPN access to specific users or groups based on their roles and responsibilities within the organization. This helps prevent unauthorized access to sensitive data and resources.
In terms of network security, TeamViewer includes features such as IP whitelisting and blacklisting, which allow administrators to control which IP addresses are allowed or denied access to the VPN. Additionally, TeamViewer regularly updates its software to patch any security vulnerabilities and protect against emerging threats.
Overall, TeamViewer provides robust VPN security features that are on par with industry standards. However, as with any VPN solution, it's essential for organizations to carefully evaluate their specific security requirements and consider factors such as ease of use, scalability, and cost-effectiveness when choosing the right solution for their needs.
Limitations of TeamViewer VPN for security
TeamViewer is a popular remote desktop access software that offers a Virtual Private Network (VPN) feature for users to securely connect to remote devices. While TeamViewer VPN can be a convenient tool for remote access, there are some limitations regarding security that users should be aware of.
One of the major limitations of TeamViewer VPN is the lack of comprehensive encryption protocols. Although TeamViewer encrypts data transmissions using AES 256-bit encryption, the VPN feature does not provide the same level of security as dedicated VPN services. This can leave sensitive information vulnerable to cyber attacks and data breaches.
Another limitation of TeamViewer VPN is the potential for network vulnerabilities. Since TeamViewer is primarily a remote desktop software, the VPN feature may not offer the same level of network security as dedicated VPN services. This could expose users to risks such as man-in-the-middle attacks and unauthorized access to network resources.
Furthermore, TeamViewer VPN relies on the stability and security of the user's internet connection. If the internet connection is compromised or unstable, it could jeopardize the security of the VPN connection and potentially lead to data leaks or unauthorized access.
In conclusion, while TeamViewer VPN can be a convenient solution for remote access, it is important for users to understand its limitations in terms of security. Users handling sensitive data or requiring high-level security should consider using dedicated VPN services with robust encryption protocols to ensure the protection of their information and network resources.
Best practices for using TeamViewer VPN
TeamViewer VPN is a powerful tool for securely connecting remote devices and networks. To make the most of this technology, it's essential to follow some best practices:
Keep Software Updated: Regularly update your TeamViewer VPN software to ensure you have the latest security patches and features. New updates often include bug fixes and performance improvements that can enhance your VPN experience.
Use Strong Authentication: Implement strong authentication methods such as complex passwords or multi-factor authentication to prevent unauthorized access to your VPN network. This adds an extra layer of security, making it harder for hackers to infiltrate your system.
Restrict Access: Limit access to your TeamViewer VPN to only authorized users or devices. Utilize access controls and permissions settings to restrict who can connect to your VPN network, reducing the risk of unauthorized access.
Encrypt Data: Enable encryption on your TeamViewer VPN to protect sensitive data transmitted between devices. Encryption scrambles data, making it unreadable to anyone without the decryption key, ensuring confidentiality and privacy.
Monitor Connections: Regularly monitor connections to your TeamViewer VPN network to detect any suspicious activity or unauthorized access attempts. Monitoring tools can help you identify and respond to potential security threats promptly.
Implement Firewall Rules: Configure firewall rules to control incoming and outgoing traffic on your VPN network. By specifying which types of traffic are allowed or blocked, you can enhance security and prevent malicious activities.
Train Users: Educate users on the proper use of TeamViewer VPN and security best practices. Provide training sessions or materials to raise awareness about potential threats and how to mitigate them effectively.
By following these best practices, you can maximize the security and efficiency of your TeamViewer VPN, ensuring safe and reliable remote connectivity for your organization.
0 notes
Text
can you use teamviewer over a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you use teamviewer over a vpn
TeamViewer VPN compatibility
TeamViewer is a widely used software that allows users to remotely access and control another computer or device. Many businesses and individuals rely on TeamViewer for its ease of use and versatility. One of the features that often comes up in discussions about TeamViewer is its compatibility with VPNs.
When it comes to VPN compatibility, TeamViewer generally works well with most VPN services. Users can establish a remote connection through TeamViewer while using a VPN without experiencing significant issues. This means that you can enjoy the benefits of added security and anonymity provided by the VPN while using TeamViewer to connect to other devices.
Using TeamViewer over a VPN can be particularly beneficial for businesses that prioritize cybersecurity and digital privacy. By encrypting the connection with a VPN, sensitive data transmitted during remote sessions is further secured from potential threats or cyber attacks.
It is worth noting that while TeamViewer is generally compatible with VPNs, there may still be instances where certain VPN configurations could potentially cause connectivity or performance issues. In such cases, users may need to troubleshoot the VPN settings or consider using alternative VPN solutions to ensure seamless integration with TeamViewer.
Overall, TeamViewer's compatibility with VPNs enhances its versatility and security features, making it a valuable tool for remote access and collaboration in both personal and professional settings.
Using TeamViewer with VPN
Title: Maximizing Security: How to Safely Use TeamViewer with VPN
In today's interconnected world, remote access tools like TeamViewer have become indispensable for businesses and individuals alike. However, ensuring the security of such tools, especially when accessing sensitive data or systems, is paramount. One effective way to enhance the security of TeamViewer connections is by using a Virtual Private Network (VPN).
A VPN creates a secure and encrypted connection between the user's device and the internet. When TeamViewer sessions are routed through a VPN, it adds an extra layer of protection, shielding the data being transmitted from potential threats such as hackers or eavesdroppers.
Here are some key benefits and considerations when using TeamViewer with a VPN:
Enhanced Security: By encrypting all data traffic, a VPN prevents unauthorized access to your TeamViewer sessions, safeguarding sensitive information from interception or tampering.
Privacy Protection: VPNs mask your IP address and location, preserving your anonymity while using TeamViewer. This helps prevent tracking and enhances privacy, especially when accessing remote systems from public Wi-Fi networks.
Geo-Restriction Bypass: Some regions may have restrictions or limitations on accessing certain online content or services. Using a VPN with TeamViewer allows users to bypass these restrictions, enabling seamless access regardless of their geographical location.
Performance Considerations: While VPNs offer security benefits, they may introduce some latency or decrease in connection speed due to the encryption process. Choosing a VPN provider with optimized servers and low latency can help mitigate these issues.
VPN Reliability: Ensure you select a reputable VPN provider with robust security features and a reliable infrastructure. Regularly update your VPN software to patch any vulnerabilities and maintain optimal performance.
In conclusion, pairing TeamViewer with a VPN significantly enhances security and privacy when remotely accessing systems or sharing files. By following best practices and choosing a reliable VPN provider, users can maximize the benefits of remote collaboration while minimizing security risks.
TeamViewer VPN setup
TeamViewer is well known for its remote desktop and screen sharing capabilities, but it also offers a VPN feature that allows users to securely connect to a remote network as if they were on the same local network. Setting up a VPN connection using TeamViewer is a straightforward process that can provide users with a safe and encrypted connection.
To begin setting up a TeamViewer VPN connection, users should start by opening the TeamViewer application and navigating to the "Extras" menu. From there, they should select the "Options" menu and then click on the "Advanced" tab. Users will find the VPN option under the "Advanced network settings" section. By clicking on the "Show advanced options" button, users can enable the VPN feature and configure their desired settings.
Once the VPN feature is enabled, users can establish a VPN connection by clicking on the "Connect to partner" button in the TeamViewer interface. They will then be prompted to enter the remote computer's TeamViewer ID and the predefined password set on the remote computer. After successfully authenticating the connection, users will be able to access the remote network securely and browse the internet as if they were physically present on the same network.
Overall, TeamViewer's VPN setup offers users a convenient and secure way to connect to remote networks. By following these simple steps, users can establish a VPN connection with ease and ensure their online activities are protected through encryption.
Remote access with TeamViewer over VPN
Remote access with TeamViewer over VPN is a powerful combination that allows users to securely connect to remote computers or servers from anywhere in the world. TeamViewer is a popular remote desktop software that enables users to access and control another computer as if they were sitting in front of it. When TeamViewer is used over a Virtual Private Network (VPN), it adds an extra layer of security to the connection, making it safer and more reliable.
By utilizing TeamViewer over VPN, users can access their work computers or servers remotely while ensuring that their data is encrypted and protected from potential security threats. This is especially useful for businesses with employees working from different locations, as it allows for seamless collaboration and troubleshooting without compromising sensitive information.
Setting up TeamViewer over VPN is a straightforward process that involves installing TeamViewer on both the local and remote computers, configuring the VPN connection, and securely connecting to the remote device. Once the connection is established, users can transfer files, troubleshoot issues, and collaborate with team members in real-time, enhancing productivity and efficiency.
Overall, combining TeamViewer with a VPN offers a secure and efficient solution for remote access, whether for personal use or business purposes. By taking advantage of these technologies, users can enjoy the flexibility of working remotely while ensuring the safety of their data and connections.
TeamViewer VPN troubleshooting
TeamViewer VPN provides a secure and encrypted connection to access network resources remotely. However, like any technology, it may encounter issues that require troubleshooting. Below are some common problems with TeamViewer VPN and how to resolve them.
One common issue is difficulty in establishing a connection. If you are unable to connect to the VPN, check your internet connection first. Ensure that TeamViewer's servers are running and that your firewall settings allow TeamViewer traffic. If the problem persists, try restarting the TeamViewer service or reinstalling the software.
Another frequent problem is slow connection speeds. This may be due to network congestion or poor signal strength. To improve speed, ensure that your internet connection is stable and that there are no bandwidth-intensive activities running concurrently. You can also try connecting to a different VPN server or adjusting the VPN settings for better performance.
Occasionally, users may experience dropped connections while using TeamViewer VPN. This can be caused by network disruptions or configuration issues. To address this, check for any intermittent network problems, update your network drivers, or adjust the VPN timeout settings.
Lastly, if you encounter authentication errors or login issues, make sure you are using the correct credentials and that your account is in good standing. Resetting your password or contacting TeamViewer support for assistance can help resolve authentication problems.
In conclusion, troubleshooting TeamViewer VPN issues may require simple fixes like checking network connections or more complex solutions like adjusting settings or contacting support. By following these steps, you can ensure a smooth and secure remote access experience with TeamViewer VPN.
0 notes
Text
Ivanti Neurons para gestão de dispositivos móveis será integrado à solução de monitoramento e gerenciamento remoto TeamViewer A TeamViewer, provedora líder global de soluções de conectividade remota e digitalização de ambientes de trabalho, anuncia sua união com a Ivanti, empresa de tecnologia que promove e assegura o modelo de trabalho Everywhere Work (trabalho de qualquer lugar). A colaboração aproveitará os recursos líderes de Gestão de Dispositivos Móveis do Ivanti (Ivanti Neurons for MDM, em inglês) para aprimorar a oferta de Monitoramento e Gerenciamento Remoto (RMM, sigla em inglês) da TeamViewer, fornecendo às empresas uma visão geral, integral e completa de seus desktops e ativos de TI móveis com recursos designados de segurança, conformidade e gerenciamento em escala. Com a parceria, os clientes TeamViewer Remote e TeamViewer Tensor poderão gerenciar vários conjuntos de dispositivos a partir de uma plataforma unificada que capacitará os profissionais de TI com: Gerenciamento de dispositivos 360° Integração, gerenciamento e monitoramento holísticos e em larga escala de dispositivos móveis iOS ou Android por meio de implementação remota de perfis corporativos com direitos de acesso designados e aplicativos predefinidos; Sintetização de todo o inventário de TI, configuração de dispositivos, identificação e resolução de problemas antes que causem tempo de inatividade. Maior segurança Implementação remota de políticas e patches em uma frota global de dispositivos, com aplicação de medidas de segurança como PIN, autenticação biométrica ou autenticação de dois fatores; Backup ou limpeza confiável de dados e bloqueio remoto de dispositivos com manutenção de controle independentemente do local físico. Conformidade aprimorada Atenuação de armadilhas legais por meio de rastreamento e de registro da localização e do uso do dispositivo para total auditabilidade. "A parceria representa um avanço significativo na simplificação da complexa tarefa de gerenciar e proteger dispositivos remotos”, afirma Frank Zamo, Vice-Presidente de Gerenciamento de Produtos da TeamViewer. “Os recursos de gerenciamento de dispositivos móveis da Ivanti, quando integrados à nossa oferta existente de RMM, capacitarão as equipes de TI a controlar e monitorar efetivamente seus dispositivos móveis, elevando a produtividade e reduzindo os desafios operacionais.” "Estamos muito felizes em unir forças com a TeamViewer para garantir que as equipes de TI gerenciem ainda mais dispositivos e sistemas operacionais. Ao combinar os recursos comprovados de monitoramento e gerenciamento remotos do TeamViewer com o premiado gerenciamento de dispositivos móveis da Ivanti, estamos preparados para oferecer uma experiência inigualável para empresas que buscam uma supervisão abrangente de TI”, diz Michelle Hodges, Vice-Presidente Sênior de Canais e Alianças Globais da Ivanti. A plataforma Ivanti Neurons for MDM complementará a gama de recursos atuais de Monitoramento e Gerenciamento Remoto (RMM) TeamViewer, que já é tecnologia líder de mercado para gestão de uma ampla variedade de dispositivos, independentemente de sistemas operacionais e fabricantes. Com a inclusão de todos os smartphones iOS e Android via Ivanti, o TeamViewer RMM ampliará a sua capacidade de cobertura, passando a atender desde os equipamentos mais clássicos, telefones celulares e tablets até os mais avançados wearables e dispositivos, fornecendo dessa forma uma visão holística de todo o cenário de TI. A solução MDM adicional está disponível para todos os clientes TeamViewer em três níveis diferentes: Essential, Advanced e Enterprise. Mais informações estão disponíveis em www.teamviewer.com.
0 notes
Text
Sale Is Going On,Go And Grab Your Gscan Zenith Z5
Looking for the tools to diagnose your cars and other vehicles,
now the Auto Max tools also provide car battery Scanner tools that make diagnosis easy and simple to use in collaboration with Zenith, the South Korean company
we introduce u to the Gscan Zeith Z5.

Gscan Zenith Z5
It is the first automotive diagnostic scan tool in the Z series. Combined with our vast diagnostics software and the world's best industrial tablet, Z5 will give you diagnostic confidence.
Key Features of GScan Zenith Z5 are mentioned below:
A powerful octa-core processor for optimum diagnostic performance and fast management of workshop operations.
Based on Android 9 os provides Quick boot-u, multi-tasking, fast networking, and enhanced system security.
Eyellumicate Displays LCD provides crystal clear views both indoors as well outdoors, offering field-optimized display under a bright workshop environment.
Diagnostic software programmed by engineers with technicians in mind.
Zenith Z5 functions as a"pass-thru" device for programming the ECUs for multiple carlines.
Zenith Z5 accepts power & signals of a 24v system and supports Bi-directional communications with commercial trucks and buses.
Robust connectivity allows for smart updates, Quick feedback, TeamViewer support, Bluthood printing, browsing, and much more.
Simple, Yet Intuitive Layout
Zenith Z5 offers a simple iconic main menu for easier and quick access to desired functions. With 3 available display modes, the user can customize the theme and button locations.

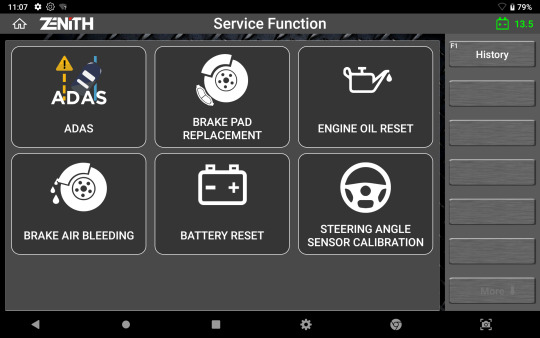
Service Function
Time is money. Z5 offers shortcuts to the most frequently used functions in the workshops to save time for technicians to navigate through the original menu layout.
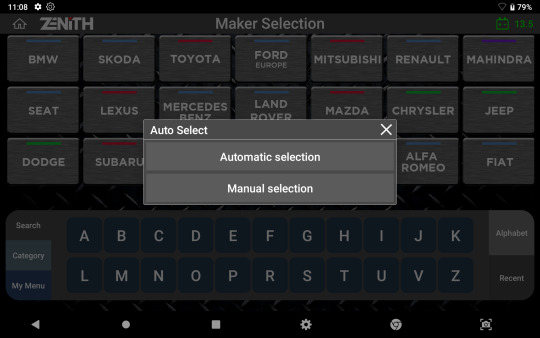
Auto Selection
Zenith Z5 offers the option to automatically detect the vehicle information including the VIN, model year, model name, engine type, and other necessary information retrieved.

Quick System Search
The ‘System Search’ option automatically scans all the vehicle systems, reports fault codes, and provides access to advanced diagnostic functions in each system detected.

Data Log & Feedback System
In the case of communication or function error, a user can log the bi-directional data transmission between the tool and vehicle control systems. This log can be sent to the software development team via the log capture & transfer function. The data log files received will be analyzed, feedback will be passed on, and a patch file update provided, if necessary, often within 24 hours of receiving the report, during working days. (Exceptions may apply).

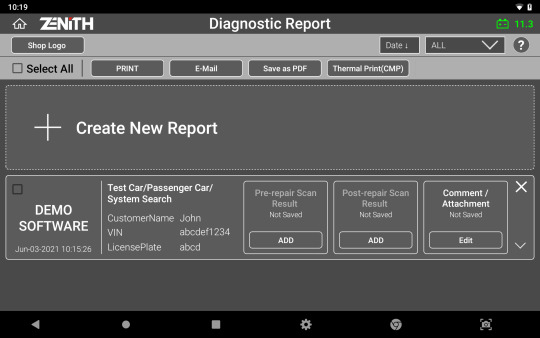
Pre & Post Diagnostic Report
Z5 offers easy creation of diagnostic reports with Pre-scan and Post-scan results. Not only you can save the reports as a PDF file in the internal/external memory, but with the help of its advanced network connectivity, you can print the report directly with a wireless printer or send them to a desired E-mail address.
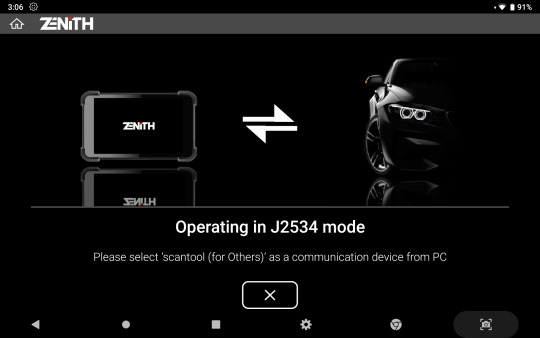
J2534 Pass-thru
Zenith Z5 acts as a J2534 Pass-thru device for multiple carlines with CAN-Bus, KWP2000, and ISO9141 protocols, supporting J2534 programming and diagnostics. (Exceptions may apply).

Fast & Responsive Graphing Mode
Z5 offers a fast and intuitive graphing mode that instantly self-adjusts the maximum and minimum scale, enabling the users to observe and compare live data more efficiently.

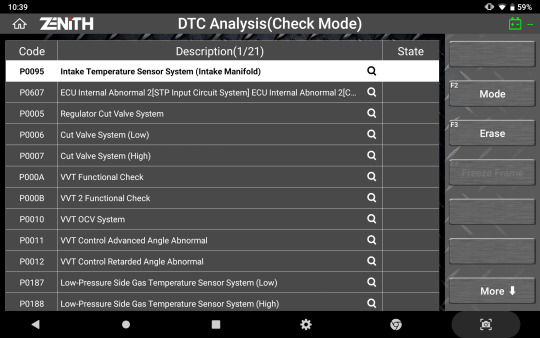
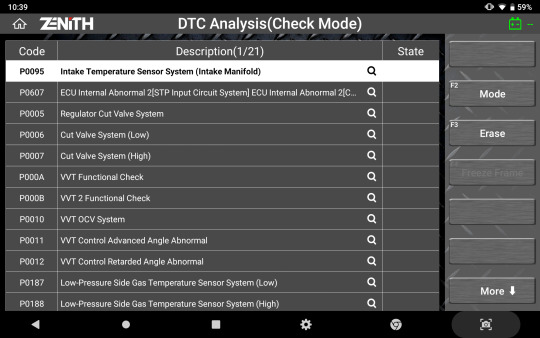
Full-Text Description
No more acronyms and cutting of significant texts. Z5 offers the long-text DTC descriptions in full screen, so you get all the information you need.
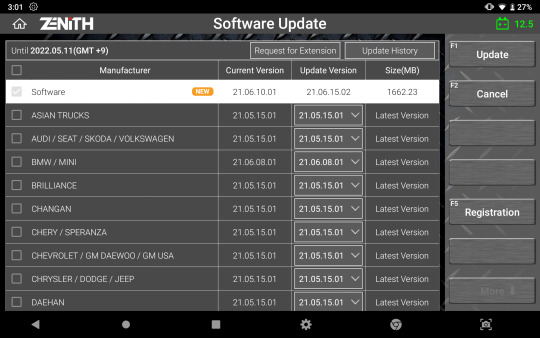
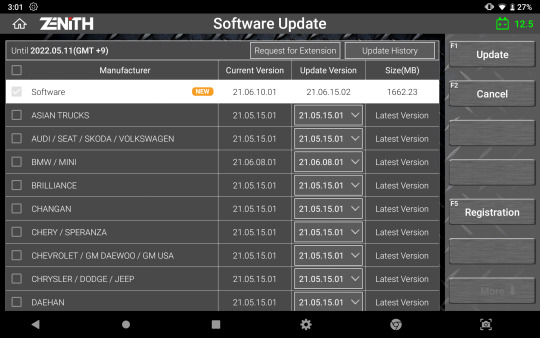
Smart Update
Z5 offers a quick and easy software update process with its strong network connectivity. Previous or latest software versions for each carline can be quickly downloaded directly from the server, as per the user’s preference.
Contact Us Now:
+91 92053 23885
+91 99580 57547
Watch Our Videos for More Details:
Automax Tools India YouTube
Topdon India YouTube
Available at Automax Tools India – Trusted by professionals nationwide!
For more details visit: AutoMax tools
#car battery scanners#car battery tester#car battery maintainer#india#new delhi#auto max tools#cars#car battery charger#car battery jumpers#topdon
0 notes
Link
TeamViewer 15.29.4 Crack is a remote access program that gives you easy access to fully controlled devices. The devices running this software are Android, Windows, iOS, Windows Phone 8, Windows RT, Blackberry and Linux.
0 notes
Text
What is Remote Desktop Connection Manager (RDCMan)?
Remote Desktop Connection Manager (RDCMan) is a free Microsoft tool that allows IT professionals and system administrators to manage and organize multiple remote desktop connections from a single, intuitive interface.
RDCMan is a comprehensive application that simplifies the process of remotely accessing and managing various computers, servers, and other devices within an organization. Unlike the standard Remote Desktop Connection (RDC) tool, which can only handle a single remote connection at a time, RDCMan enables users to consolidate all their remote connections into a single window.
With RDCMan, users can:
Manage and maintain servers, workstations, and other devices remotely
Access and troubleshoot systems from a central location
Manage and deploy software updates
Monitor system performance and resource usage
Provide technical support to users
The key features that set RDCMan apart from other remote connection management tools include the ability to:
Organize connections into groups and sessions for better management
Save connection details, including user IDs and passwords, for quick access
Quickly switch between multiple remote connections without having to re-enter credentials
Customize settings and preferences to suit individual needs

How to Use RDCMan
To use RDCMan, users first need to download the latest version from the Microsoft website. Unlike previous versions, the current version (v2.92) does not require installation, as it is a standalone application. Once the download is complete, users can extract the files and start using the tool. RDCMan provides several keyboard shortcuts to help users navigate and manage their remote connections more efficiently. Some of the common shortcuts include:
F2: Rename the selected connection
F5: Refresh the current view
Ctrl + N: Create a new connection
Ctrl + W: Close the current connection
Ctrl + Shift + N: Create a new group
To set up a new remote connection, users can click the “New” button and enter the necessary details, such as the computer name, user ID, and password. They can also organize their connections into groups and sessions for better management.
RDCMan Vulnerability and Security Considerations
In 2020, a security researcher discovered a vulnerability in RDCMan that could allow an attacker to execute malicious code on the target system. This vulnerability was quickly addressed by Microsoft, who released a patch in RDCMan version 2.7 that included a validation mechanism for opening rdg files.
It’s important to note that, like any software, RDCMan should be regularly updated to ensure that users receive the latest security patches and fixes. Failure to do so could leave the system vulnerable to potential attacks. 3Additionally, users should be cautious when opening .rdg files from untrusted sources, as they could potentially contain malicious code. It’s recommended to only open .rdg files from trusted sources and to always verify the integrity of the file before opening it.
Alternatives to RDCMan
While RDCMan is a popular and widely-used tool for managing remote desktop connections, there are several alternative solutions available in the market. Some of the popular alternatives include:
mRemoteNG: A free and open-source remote connection manager that supports a wide range of protocols, including RDP, VNC, SSH, and Telnet.
Devolutions Remote Desktop Manager: A comprehensive remote connection management solution that offers features such as password management, role-based access control, and two-factor authentication.
TeamViewer: A popular remote desktop software that allows users to access and control remote computers, as well as collaborate with others in real time.
LogMeIn: A cloud-based remote access and support solution that enables users to securely connect to and control remote computers from anywhere.
When choosing a remote connection management tool, it’s important to consider factors such as the number of remote connections, the level of security required, and the specific features and integrations needed to support the organization’s IT infrastructure.
Conclusion
Remote Desktop Connection Manager (RDCMan) is a powerful and versatile tool that simplifies the process of managing and organizing multiple remote desktop connections. With its ability to consolidate connections, save user credentials, and provide customizable settings, RDCMan has become an essential tool for IT professionals and system administrators who need to efficiently manage and maintain remote systems.
While RDCMan has faced some security concerns in the past, the latest version of the tool includes robust security measures to protect against potential attacks. By regularly updating the software and exercising caution when opening .rdg files, users can ensure that RDCMan remains a secure and reliable solution for their remote connection management needs.
0 notes
Link
TeamViewer Crack 2021 is the best software to access your device. While it helps you to get access to the web all over the world.
0 notes
Link
TeamViewer Pro 15.16.8 Crack could be your entire world’s sole remote service applications that may access and manage.
0 notes
Text
Excited GScan Zenit Z5 Is Here At Discount Shop Now
Looking for the tools to diagnose your cars and other vehicles,
now the Auto Max tools also provide car battery Scanner tools that make diagnosis easy and simple to use in collaboration with Zenith, the South Korean company
we introduce u to the Gscan Zeith Z5.

Gscan Zenith Z5
It is the first automotive diagnostic scan tool in the Z series. Combined with our vast diagnostics software and the world's best industrial tablet, Z5 will give you diagnostic confidence.
Key Features of GScan Zenith Z5 are mentioned below:
A powerful octa-core processor for optimum diagnostic performance and fast management of workshop operations.
Based on Android 9 os provides Quick boot-u, multi-tasking, fast networking, and enhanced system security.
Eyellumicate Displays LCD provides crystal clear views both indoors as well outdoors, offering field-optimized display under a bright workshop environment.
Diagnostic software programmed by engineers with technicians in mind.
Zenith Z5 functions as a"pass-thru" device for programming the ECUs for multiple carlines.
Zenith Z5 accepts power & signals of a 24v system and supports Bi-directional communications with commercial trucks and buses.
Robust connectivity allows for smart updates, Quick feedback, TeamViewer support, Bluthood printing, browsing, and much more.
Simple, Yet Intuitive Layout
Zenith Z5 offers a simple iconic main menu for easier and quick access to desired functions. With 3 available display modes, the user can customize the theme and button locations.

Service Function
Time is money. Z5 offers shortcuts to the most frequently used functions in the workshops to save time for technicians to navigate through the original menu layout.

Auto Selection
Zenith Z5 offers the option to automatically detect the vehicle information including the VIN, model year, model name, engine type, and other necessary information that is retrieved.
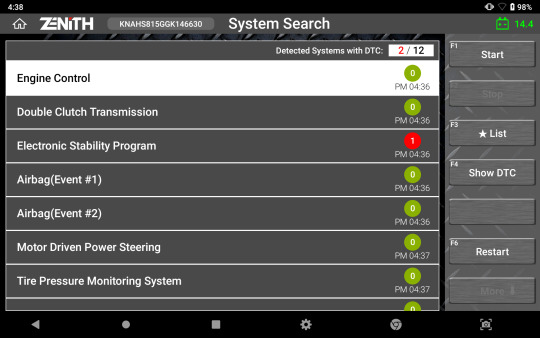
Quick System Search
The ‘System Search’ option automatically scans all the vehicle systems, reports fault codes, and provides access to advanced diagnostic functions in each system detected.
Data Log & Feedback System
In the case of communication or function error, a user can log the bi-directional data transmission between the tool and vehicle control systems. This log can be sent to the software development team via the log capture & transfer function. The data log files received will be analyzed, feedback will be passed on, and a patch file update provided, if necessary, often within 24 hours of receiving the report, during working days. (Exceptions may apply).

Pre & Post Diagnostic Report
Z5 offers easy creation of diagnostic reports with Pre-scan and Post-scan results. Not only you can save the reports as a PDF file in the internal/external memory, but with the help of its advanced network connectivity, you can print the report directly with a wireless printer or send them to a desired E-mail address.

J2534 Pass-thru
Zenith Z5 acts as a J2534 Pass-thru device for multiple carlines with CAN-Bus, KWP2000, and ISO9141 protocols, supporting J2534 programming and diagnostics. (Exceptions may apply).
Fast & Responsive Graphing Mode
Z5 offers a fast and intuitive graphing mode that instantly self-adjusts the maximum and minimum scale, enabling the users to observe and compare live data more efficiently.

Full-Text Description
No more acronyms and cutting of significant texts. Z5 offers the long-text DTC descriptions in full screen, so you get all the information you need.
Smart Update
Z5 offers a quick and easy software update process with its strong network connectivity. Previous or latest software versions for each carline can be quickly downloaded directly from the server, as per the user’s preference.
Contact Us Now:
+91 92053 23885
+91 99580 57547
Watch Our Videos for More Details:
Automax Tools India YouTube
Topdon India YouTube
Available at Automax Tools India – Trusted by professionals nationwide!
For more details visit: AutoMax tools
#car battery scanners#car battery tester#car battery maintainer#cars#car battery jumpers#car battery charger#topdon#new delhi#auto max tools#india
0 notes
Link
TEAMVIEWER 14.2.8352 CRACK 2019 KEYGEN FREE DOWNLOAD WITH PATCH
0 notes