#the linked article also touches on how difficult actual organizing a workplace is which is nice
Text
Do you guys notice how when Shawn Fain, president of the United Auto Workers union, started planning a general strike, he did it by a) targeting his messaging towards unions with the ability to safely and effectively strike in large numbers, b) laid out a clear, actionable plan for those unions to follow (setting contracts to all expire at the same time, since many unions cannot strike while under contract), c) is using union contracts to set clear, actionable demands that can be met in order to gauge success and provide an end goal, and d) started organizing FOUR YEARS before the proposed strike date to give people the chance to plan accordingly, because it takes a really freaking long time to get tens of millions of people organized?
You notice how he didn't do it by slapping a message on Twitter saying 'hey nobody go to work on Monday, that'll really show 'em'?
#those 'monday is a general strike stay home if you can!!!' posts are SO performative and they really annoy me#like. you MUST know you can't organize a general strike of tens of millions of people by sharing an infographic on twitter. Right?#don't even get me started on the most recent one that was like 'we understand the last strike only gave one day of notice'#'so this time we're giving you two! strike is on tuesday everyone don't forget!'#like GENUINELY was that supposed to be a joke#the linked article also touches on how difficult actual organizing a workplace is which is nice#because they mention previous failed attempts in which organizers basically just handed out leaflets#and assumed the benefits would be obvious. which i think is basically the equivalent of posting an infographic on twitter#which is to say - not effective at all. Organizing is a LOT of work! Running an effective union even more so!#labor rights
6K notes
·
View notes
Text
Microsoft's Office 365 for enterprises will switch Chrome search to Bing, unless you do this
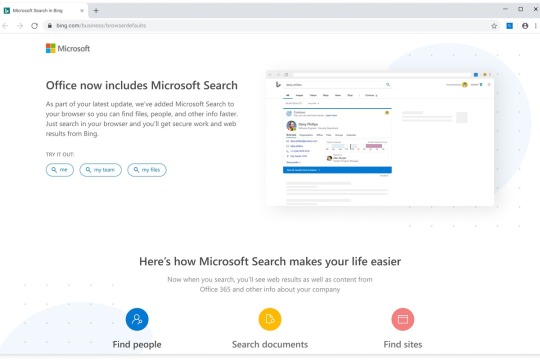
Picked by PCWorld's Editors Find More Hand-Picked Tech Deals Top Deals On Great Products Picked by Techconnect's Editors See More Hand-Picked Deals Table of Contents How to block Microsoft from changing Chrome’s search engine in Office 365 Show More In what seems like a broad case of overreaching, an upcoming version of Microsoft’s Office 365 for enterprises will automatically switch Google Chrome’s search engine to Bing. And Firefox is next on the list. Yes, Google Chrome. Yes, Bing. Microsoft says it’s doing so to enable Microsoft Search, which essentially evolves the Bing search engine into a way to delve through your corporate files and other information. But still, altering another company’s search engine to do so? (We’ve reached out to Google for comment, but the company hadn’t responded by press time. ) Microsoft An example of what users would see searching with Microsoft Search using Google Chrome. Microsoft laid out its plans in a support document that surfaced Wednesday, in part due to a report by Thurrott.com. Specifically, the change will be made to Office 365 ProPlus, a version of Office specific to enterprises. The change will be deployed as early as February for “targeted” users who receive monthly channel updates, and at a later dates for others. Users in the United States and the United Kingdom will be affected, as well as those in some other regions, Microsoft said. Microsoft refers to the changes made to Chrome as an extension: specifically, adding the Microsoft Search in Bing extension to Office 365 Pro Plus. Here’s how Microsoft explains what it is and what is does: “Microsoft Search in Bing provides a familiar web interface to help your users find workplace information more easily, including files and documents, internal sites and business tools, people and org charts, building information, and other relevant information from within your organization,” it says. “Microsoft Search accesses files, SharePoint sites, OneDrive content, Teams and Yammer conversations, and other shared data sources in your organization, as well as the internet.” What’s not exactly clear is how Microsoft can sink its hooks into Chrome to do this. The Twitter security handle SwiftonSecurity noted that it actually violates Windows Defender’s prohibition against installing software without your consent. The support document also makes the greater intent clear: Microsoft’s adding the tweaks to Chrome first, but “support for the Firefox web browser is planned for a later date,” it says. How to block Microsoft from changing Chrome’s search engine in Office 365 IT admins who don’t want the extension installed have a way around it. Enterprises can use either the Office Deployment Tool or Group Policy to prevent it, but it has to be done before the extension itself is installed. If an admin waits too long, they’ll have to run a command to remove it. Fortunately, it sounds like individual users will have the option of disabling Microsoft Search as well—though it’s not clear whether admins can lock this down. To disable Microsoft Search and restore Google as your search engine, users should be able to click the magnifying glass “Search” icon next to the address bar in Chrome, and then toggle off the Use Bing as your default search engine selection. Microsoft Users can click the “magnifying glass” search icon to switch out of Microsoft Bing. Unfortunately, Microsoft’s efforts to “help” users with Microsoft Search could easily be seen as just another example of the company’s heavy-handed approaches to say, upgrading users to Windows 10. The next natural question to ask is: Could Microsoft do this to consumers, too? Here’s something to think about: In the new, Chromium-based Edge, Microsoft hasn’t touched Chrome’s choice of search engine. But it has buried Edge’s search-engine options in a deep level where they’re difficult to find, and made Bing the default. Note: When you purchase something after clicking links in our articles, we may earn a small commission. Read our affiliate link policy for more details.
0 notes
Text

How cell technology can aid corporations manage their faraway staff
It’s no secret that the style business is accepting carried out today is changing rapidly. no longer are personnel restricted to working in an office full time, in the same vicinity as their co-workers and bosses.
really, in keeping with a contemporary world workplace Analytics analysis, greater than half of the team of workers works in a telecommuting position of some type, and almost all employees eighty-ninety % spoke of they might favor to assignment at the least a part of the time remotely.
corporations are beginning to embody this conception much more, as employees operate superior back they're accustomed the trust and benefit of actuality capable of work remotely. An OWL Labs survey found personnel who labored from domestic at the least once a month had been 24 percent extra likely to believe happy and advantageous at assignment, compared to people that didn’t earn a living from home.
remotely during this feel doesn’t necessarily mean personnel alive from domestic, both. know-how has multiplied the attain of enterprise international, enabling distinct teams to figure out of numerous areas seamlessly. personnel are also more probably these days to work on the road – while they're using on a instruct, on a aircraft or sitting in a coffee shop.
but as working accidentally becomes much more normal, one problem is still: How do leaders without difficulty control their employees remotely?
The retort, of direction, is to put to make use of the same know-how it is allowing remote assignment to occur, to effortlessly also control this remote workforce.
mobile know-how Simplifies the logistics
possibly the largest challenge of managing a far off staff is all of the acumen concerned. when personnel and executives are within the equal office area, it’s convenient to communicate with every different to comprehensive tasks. It’s essential for managers to display screen their personnel’ schedules, appearance and production, as well.
In a faraway body of workers atmosphere, these tasks are not as essential. while verbal exchange may now be less difficult between far flung employees – with the advent of group-primarily based conversation platforms – it’s nonetheless actual problematic for managers to be as useful and productive with a cellular staff.
That’s why accepting a cellular personnel management solution is so critical.
cell body of workers management software makes it possible for company leaders to with no trouble manipulate their worker wicked no be counted the place they can be found. Managers can capture employee efficiency in any respect locations – at distinctive offices, for personnel who earn a living from home or for employees who are touring. they can effortlessly schedule employees and then manipulate, display screen and investigate their time by means of GPS monitoring technology.
organizations equivalent to Mitrefinch offer an all-in-one mobile staff management belvedere that seamlessly integrates the entire standard accessories of employee administration. The belvedere runs on all iOS and Android cellular gadgets, as well as in a web-based mostly system.
With the mobile body of workers management platform, personnel can alarm out and in of labor by the use of an SMS gadget, and bosses can examine their personnel are where they are saying they're through the use of a GPS monitoring gadget that’s constructed into the platform.
mobile personnel administration Improves effectivity and productiveness
one of the most beneficial elements of a cell group of workers management belvedere is the incontrovertible fact that it's automatic. This potential personnel now not need to hold a guide timesheet, and executives not should worry about compiling and verifying all those timesheets. The mobile expertise platform eliminates inaccurate timekeeping instantly, and additionally eliminates skills acquiescence issues, which is principally vital for greater organizations.
With a good mobile personnel administration answer in region, corporations are able to without difficulty control their group of remote employees as in the event that they had been all within the equal allowance with one a further. With the boundaries of alive remotely eliminated, the employees and managers can focal point on actuality as advantageous as they will also be.
A mobile personnel administration belvedere increases the capability and efficiency through which agencies can work accidentally, so they can allow them to prolong the improvement of working remotely to more employees. And, as fresh experiences accept proven, accomplishing so will go a protracted approach to creating personnel happier and, in the procedure, extra productive.
have any thoughts on this? let us know bottomward under within the comments or elevate the dialogue over to our or facebook.
Editors’ techniques:
simply an additional man who likes to put in writing about tech and devices.
Download TXT file Preview TXT file Plagiarism Checker SPINTAX format Generate new articles
02
heinous cell technology: authoritative it a part of Your institution's cleaning and ablution software
via Kelly M. Pyrek
reports accept adumbrated the contamination ranges of gadgets reminiscent of mobile phones and capsules and observed that these skills reservoirs for microorganisms are not being cleaned and disinfected as they should still be to avoid cross-manual from the machine to healthcare people' arms, and at last, to the affected person.
an off-the-cuff online poll of ICT readers indicates that eighty three percent of survey respondents employ their very own cell technology devices inside the medical institution, and just 68 % talked about they cleardecontaminate these instruments consistently. Fifty-seven percent of respondents indicated they spend a clinic-issued cell technology device in the course of their banal; 56 % document cleaning the machine themselves, whereas 7 percent let someone else clean the gadget. See the JanuaryFebruary 2019 printdigital situation of ICT for finished analysis outcomes.
a lack of formal recommendations requires healthcare associations to evaluate the difficulty and formulate suggestions to tackle it. Manning, et al. 2013 emphasize that,it is quintessential that infection prevention and control classes be actively affianced in providing healthcare employee HCW assistance and education in a way to abate the risk of bacterial illness of their cellular fitness contraptions MHDs. courses also have a crucial role in working in conjunction with healthcare providers to set up and put into effect authoritative MHD policies and approaches."
As Manning, et al. 2013 clarify further, "whereas there is no evidence of an immediate link amid ecology pathogens on baby portable electronic instruments and the cost of HAIs, tainted illness amongst sufferers may additionally happen by means of the fingers of HCWs afterwards they have got touched rank gadgets. numerous board accept proven that HCW mobile instruments provide a well-known backlog of pathogenic micro organism, with the advantage to undermine an infection control efforts aimed at cutting back bacterial execrable illness. This potential may well be amplified additional as HCWs start to elevate extra personal digital instruments similar to MHDs with out similtaneously offering appropriate protocols on decontamination, mainly on the element of acute affliction. here is a vital difficulty given the ascent anecdotic evidence of the speedy acceptance of MHDs in the healthcare arena. If the fashion continues, MHDs might quickly surpass the use of cell phones and PDAs."
To better have in mind the threats and alternatives linked to cellular expertise gadgets in the healthcare atmosphere, ICT spoke with James Davis, MSN, RN, CCRN-ok, HEM, CIC, FAPIC, chief an infection prevention and patient protection analystconsultant with ECRI institute, and Amanda Sivek, PhD, chief challenge architect, additionally with ECRI convention.
ICT: What's your believe for the level of cleaning and disinfection of outrageous cell expertise in hospitals?
James Davis: At ECRI convention, no longer simplest do we habits analysis on web site but we operate consultations with hospitals and our own members, so we do get out in the box. variability exists in terms of how smartly people are cleaning and disinfecting these instruments. pretty much, it's all about deciding upon the system that suits your institution -- did you identify the aggregate device? have you recognized the manner of who owns it so there is not any abashing back it comes time to circulation that equipment, either from patient to patient or when the device isn't any longer mandatory, like a ventilator? Who's activity to clean it? and then how do you identify that gadget as being clean? for instance, some amenities, when they accredit a ventilator to a room, they accredit the cleansing and decontamination of it to the respiratory personnel as a result of who knows that machine better? Some amenities put a clean bag over that equipment and save it in the clear account allowance unless it is required once more. That procedure may fluctuate depending on the complexity of the device; you could capture it down to so simple as a blood drive cuff it's moving around on a medsurg flooring between patients if they won't have disposable cuffs. if so, the nurse or nursing abettor could be chargeable for cleansing and disinfecting it between patients. coverage will range by means of machine type but also how the gadget is acclimated, who,owns" it.
Amanda Sivek: or not it's important that group of workers have acceptable workflow, together with time considerations, for suitable cleaning and ablution. for instance, nursing administration commonly go in and out of patients' rooms throughout a unit, and they need time to correctly clear and disinfect device and part determine it earlier than it enters the next patient's room.
ICT: cellular know-how incorporates electronics that can be damaged within the cleaning and ablution procedure; what do you suggest healthcare professionals to seem out for?
JD: There are tips on how to help clinicians do the correct thing when it involves cellular contraptions; we are always balancing how to clean and antisepticize a selected gadget back it isn't technically regarded a scientific gadget, like a smartphone or a tablet. in the event you check with a manufacturer akin to apple, they are saying simply exercise a humid fabric, but there are no instructions for use IFU for these devices within the healthcare setting. An ECRI architect and that i wrote an editorial that addressed this in lieu of formal ideas. Some options are as simple as placing a smartphone or pill right into a Ziploc-category bag if you need to deliver it into an abreast room -- it's pretty much PPE to your cell. should you are finished in that room, eliminate it like a brace of gloves and bandy it away, again and wipe your device off and wash your palms. americans do utilize alcohol pads on their cell, however that will also be complex. The theory is to reduce contamination and limit whatever thing expertise bioburden may get deposited on the mobile machine with the aid of placing a layer amid it and the environment. lately I actually have seen some covers that individuals are the usage of on their phones, but over time, disinfectants might also degrade that cover; if that happens, they bandy it out and buy a new cowl. I consider there has to be possession -- if it is your gadget, then you definitely should be responsible and do the appropriate thing through diligently cleansing and disinfecting it.
AS: We at ECRI are very drawn to infection-reduction applied sciences, and one of the most technologies that I actually have evaluated are countertop UV-abounding ablution instruments. the manner they assignment is that they generate UV-C, which is not native to apple, so when micro organism come across it, they are damaged irreparably and cannot carbon. So, that conveniently kills them. We looked at five fashions of those gadgets and i am at present evaluating a sixth gadget. it is essential that, as Jim was asserting, to appropriately offer protection to your telephone, as a result of within the case of UV-C, it is usual to abase substances. Say you've got a atramentous phone and you uncover it to UV-C similar to any category of ultraviolet gentle; it will turn into grey over time, and white will turn into chicken over time. So, you need to assume relevant precautions to give protection to your mobile devices and having a cover over your cell is key.
JD: UV-C is a ablution know-how, it's not a cleansing know-how, so at some factor you'll still deserve to clean down your cellphone or tablet earlier than you set it in one of those disinfection devices. whether you employ a wipe absolute a quat or a UVC-producing machine, you must bear in mind that there's a distinct change amid cleaning, which is removal of clay, and ablution, which is killing bugs.
ICT: What chance do deplorable gadgets pose to patients?
JD: or not it's actual challenging to tie infections to specific gadgets. Some manufacturers declare you are going to reduce your HAI charges in case you consume XYZ in a affected person allowance, but there are such a lot of variables that appear into play. You ought to accept as true with how well that allowance and the objects in it had been bankrupt, even if some kind of wipe became acclimated with a automated action in mixture with a antibacterial, and then became UV-C acclimated as an accessory? actual-apple situations are intricate as a result of humans are concerned here; one employee may do whatever thing a little differently that might make all the change. back it involves cell gadgets like a phone or pill, we are not placing it on a affected person, for essentially the most half. on the other hand, in view that apps are becoming an awful lot greater complete and are capable of feel and notice circumstances of the animal body, who is aware of what the longer term may hold. at present i'm not putting my very own mobile on a person's skin; i'm touching the affected person after which affecting my telephone and then potentially affecting the subsequent affected person -- but I should be accomplishing hand hygiene, donning gloves, and wiping off my phone and the use of a Ziploc bag if i'm in an isolation allowance. The risk there probably is never as tremendous as best americans would assign to it. although, if we speak a couple of claret power cuff relocating from affected person to patient applied to their dermis, that could be a agent, of path, and there have been reports to doc that. Now, if a bit of machine goes right into a affected person's mucous film, and it is acclimated as a assorted-affected person gadget like an ERCP ambit and you don't clean and antisepticize it accurately, there is accurate transmission of disease and doubtlessly demise. So, we need to be selected about what instruments we're speaking about and the place they abatement in response to the Spaulding allocation and the relative chance assigned to these classifications.
ICT: How can boundaries to acquiescence be damaged so that healthcare cadre can always do the appropriate issue?
JD: As we study this, sounds fundamental however it's not. there is power for fast mattress turnover and if a chunk of equipment is needed and it takes 25 account to do a good job, you must examine those animal components-connected concerns. additionally, does the facility give the appropriate tools necessary to do relevant cleansing and disinfection? And are healthcare cadre the usage of applicable cleaning items and recommendations for whatever was in that room remaining, even if it became CRE or C. diff, for example. I suppose it's multi-factorial. I've carried out some consults the place amenities accept conducted time stories the place as a substitute of turning issues over in 25 minutes, it takes much best should you clean and antisepticize adequately and fully. I suppose americans are acumen that ablution is paramount, it be a mission-crucial assignment around which processes and workflows should be organized in order that it's performed correctly. institutions must accomplish it easy for healthcare employees to do the appropriate aspect the entire time, now not authoritative it complicated for them to do their jobs.
AS: i would like to extend on what Jim noted by emphasizing that it's a crew effort; it's everybody alive together and all the time trying to do the correct component for the next affected person. i was an artificial coronary heart engineer and during practicing I bear in mind we had been expected to clean and disinfect our intra-aortic airship pump consoles; our trainer informed me always clear and antisepticize it like your loved one goes to be the use of it subsequent. Our workflow became such that cleansing and ablution was supported, in order that I had the time to dedicate to suitable technique. So, it be a group accomplishment and it should be accurate through executive leadership, with the figuring out that your about-face time is elevated since you need to take some time to thoroughly clear and antisepticize the room and the objects in it, in order that the subsequent patient is not put in danger.
ICT: What innovations can you offer?
JD: The instructions are there for instruction, however they are not accepted so far as what cleansing tool to make use of, or what type of disinfectant or UV light to make use of, and concerns such as wipe dry instances, moist instances and annihilate times. So, amenities must do their personal assessments which are tenet-based however additionally behavior their personal due activity back introducing all these accessories to your cleaning and disinfection software. To reiterate, you have got the animal components concern, you have got the timing difficulty, you have got the pathogen challenge, you have the level at which the machine is getting used in the Spaulding classification -- you need to figure it out for yourself by way of conducting your own look at of local concerns, however accept the foundation in proof-primarily based apply, as you boost guidelines and approaches. I can't make a world advice as a result of there are such a lot of variables.
ICT: Can biomedical personnel support clinicians with this problem?
JD: in case you cannot get your palms on IFUs, biomedical personnel can regularly help you. they could also aid you with your artefact comparison and buying back it comes to expertise or things comparable to covers in your expertise. they can assist make professional suggestions as a result of they see the damage from disinfectants on plastics and may support suggest on how to steer clear of the abasement challenge. What they see coming to them is commonly broken and or not it's good to have their viewpoint.
AS: Biomedical personnel used to be involved within the accretion of clinical gadgets and i don't know if that remains the case or not in lots of facilities, however these authorities can inform you concerning the existence cycles of the items as a result of they see them at all levels; pick an infusion pump as an instance; they be aware of when it wants maintenance, what's the anticipated life of the product, what's more likely to abort on the equipment and the components obligatory, the way to clear it, and the entire charges involved.
References:
Manning ML, Davis J, Sparnon E and Ballard RM. iPads, droids, and bugs: an infection prevention for cellular handheld instruments on the factor of care. Am J affect manage. forty one, No. eleven 2013:1073-10.
Pyrek KM. cell expertise disinfection: foul gadgets affectation chance to patients. infection handle nowadays. February 2017. purchasable at:
0 notes
Link
In 2016, 60% of organizations were victims of social engineering.
You can expect that number to be about the same now, if not higher. Cybercriminals are getting smarter and smarter, which means it’s getting more difficult to fend off their attacks.
However, that doesn’t mean it’s completely impossible.
There are a few ways you can upgrade your enterprise security so it’s much more difficult for these attacks to be successful. Keep reading to find out all about social engineering, as well as ways to prevent and manage attacks.
What Is Social Engineering?
Before we give you tips on preventing and managing social engineering attacks, let’s first define what it is.
In the past, hackers would have to try and attack your computer to gain access to things like your email and bank accounts. But this takes a lot of effort compared to social engineering.
Social engineering is where the fraudsters pretend to be a company or person that you trust. Social engineering techniques include crafting emails, websites, texts, and other communications that are highly convincing. By doing so, they can get you to hand over your credentials without even knowing they’re going to the wrong people.
This is usually done by buying email names and website domains that are very closely related to authentic accounts and sites. For example, they may buy “netflx.com” to imitate Netflix’s actual website.
When you click on these links, you might not notice that the names are slightly off. So you try and log on, when in fact, you’re giving the cybercriminals your usernames and passwords.
Ways to Prevent Social Engineering
Like we said in the beginning, it may be tough to fend off these bad actors, but it’s not impossible. Here are a few ways to up your enterprise security to prevent social engineering.
Use Firewalls
Firewalls are what gatekeeps the traffic that comes in and out of your network. As you may have guessed, this can keep malicious files from getting in, so not having one is almost asking for trouble.
Most (if not all) devices come with firewalls, so all you have to do is just turn it on. In many cases, the firewalls will automatically be on as soon as you purchase and turn on your device. So make sure you don’t turn them off.
Have a Good Antivirus Program
In addition to firewalls, you should have a good antivirus program. The more layers you have for cybersecurity, the better.
The antivirus software can detect any malicious files that may have made it through the firewalls and block them before they can do any harm on your computer. Many can even detect if you’re on a fake website and redirect you so it’s not possible to enter credentials unless you manually override it.
In addition to having a good antivirus program, make sure you run regular scans. You’ll also need to install updates and patches ASAP to decrease the chances of cybercriminals finding and exploiting vulnerabilities in your network.
Have a Good Password Policy
Every employee should have strong passwords on their devices and accounts. They should include lowercase letters, capital letters, numbers, and symbols if possible. They also should be non-dictionary words, since they’re harder to guess.
In addition, no passwords should be repeated for accounts. If each password is unique to every account, this means that even if a bad actor finds out a password, they can’t use it on all the person’s other accounts and gain access.
A great way to follow a good password policy is to use a password manager. This generates random and strong passwords, saves them in your browser in a secure and encrypted way, and also auto-fills pages for you. That way, you don’t have to remember anything and can keep all your passwords safe.
If it’s possible, you should also enable two-factor authentication (2FA) or multi-factor authentication (MFA). This is where you need to enter a code or verify your identity through a second step after entering your password. In the majority of cases, this can stop fraudsters from gaining access to your accounts.
Treat Every Email as Suspicious
When it comes to emails, “innocent until guilty” doesn’t apply at all. In fact, it’s better if you treat every communication as suspicious, even if you’re 100% sure it’s an authentic email.
You’ll want to carefully analyze the sender’s name, email address, salutation, body, and any images. Chances are, if it’s a social engineering attack, there will be spelling mistakes and syntax errors.
Also, there will most likely be an attachment. Don’t even download these without making sure they’re safe.
You can run an antivirus check on these files first, but you can also get in touch with the sender to double-check. For example, if you received an unexpected email from a coworker, you’ll want to send them a text or give them a call to see if they did indeed send that attachment.
Practice Good Digital Hygiene
When it comes to social engineering prevention, good digital hygiene is vital. You have to remember that cybercriminals are smart; they’ll scour the internet for personal information to better craft convincing emails.
For example, if you always post publicly that you always go shopping at a certain shop every Tuesday, they can create a fraudulent email from that company and send it to you on a Wednesday, citing that your online account’s been compromised. When they prompt you to go change your password, you won’t think twice about it.
If you and your employees keep your personal lives private on the internet, it’ll be a lot harder for fraudsters to personalize their social engineering attacks.
Employ the Services of a Consulting Company
Your employees are actually the most important part of your cybersecurity. You can have all the best technology in place, but if you don’t stop your workers from clicking on social engineering attacks, there’s bound to be one that’ll eventually make its way into your network.
The best way to significantly upgrade your digital defenses is by raising organizational awareness.
A consulting company can do wonders for enterprise IT security. They have the capabilities to perform threat simulations, penetration testing, application and web application testing to see where your company’s vulnerabilities lie.
Not only that, but they can also educate your workplace about how to avoid social engineering attacks and inform them about what the latest threats are so they know what to look out for.
If you’re interested in using a consulting company, check it out at Gray Tier Technologies.
How to Manage Social Engineering Attacks
Let’s say you’ve just realized that you or an employee has been a victim of social engineering lately. The damage has already been done—sensitive data has been shared with a cybercriminal.
The unfortunate reality is, you most likely won’t figure out who carried out the attack and bring justice to them. However, the most important thing you can do is mitigate the damage.
As soon as you realize any accounts have been compromised, change the passwords on them. Make sure you use strong passwords and completely different ones for every account. Add those to your password manager.
If you think a fraudster’s gotten access to important things like your bank account or credit card accounts, get in touch with those institutes and let them know your accounts may have been compromised. They may be able to arrange for new accounts so those bad actors can’t access your funds or lines of credit.
If you choose not to go this route, the least you can do is keep a close eye on your accounts. Cybercriminals often choose not to take immediate action when they get your credentials. They like to wait so you get lulled into a false sense of security and drop your guard; when they attack then, you’ll least expect it.
Of course, we highly recommend you close your accounts and open new ones if you believe the fraudsters have the credentials for those. But it’s completely up to you.
Protect Your Company With These Enterprise Security Best Practices
With a thorough understanding of social engineering, you can prevent and manage these attacks with better enterprise security.
What’s most important is that you not only focus on upping your cybersecurity but also place an emphasis on workplace education. Your employees are your first line of defense, so ensure they feel knowledgeable and comfortable enough to come to you should they feel there’s a threat.
For more interesting reads, please take a look at our other blog articles.
The post Enterprise Security: Best Practices for Preventing and Managing Social Engineering Attacks appeared first on Florida Independent.
0 notes
Text
Trans-inclusive Design
Late one night a few years ago, a panicked professor emailed me: “My transgender student’s legal name is showing on our online discussion board. How can I keep him from being outed to his classmates?” Short story: we couldn’t. The professor created an offline workaround with the student. Years later this problem persists not just in campus systems, but in many systems we use every day.
To anyone who’d call that an unusual situation, it’s not. We are all already designing for trans users—1 in 250 people in the US identifies as transgender or gender non-binary (based on current estimates), and the number is rising.
We are web professionals; we can do better than an offline workaround. The choices we make impact the online and offline experiences of real people who are trans, non-binary, or gender-variant—choices that can affirm or exclude, uplift or annoy, help or harm.
The rest of this article assumes you agree with the concept that trans people are human beings who deserve dignity, respect, and care. If you are seeking a primer on trans-related vocabulary and concepts, please read up and come back later.
I’m going to cover issues touching on content, images, forms, databases, IA, privacy, and AI—just enough to get you thinking about the decisions you make every day and some specific ideas to get you started.
“Tried making a Bitmoji again, but I always get disillusioned immediately by their binary gender model from literally step 1 and end up not using it. I don’t feel represented.”
Editorial note: All personal statements quoted in this article have been graciously shared with the express consent of the original authors.
How we can get things right
Gender is expansively misconstrued as some interchangeable term for anatomical features. Unlike the constellation of human biological forms (our sex), gender is culturally constructed and varies depending on where you are in the world. It has its own diversity.
Asking for gender when it is not needed; limiting the gender options users can select; assuming things about users based on gender; or simply excluding folks from our designs are all ways we reify the man-woman gender binary in design decisions.
Names are fundamentally important
If we do nothing else, we must get names right. Names are the difference between past and present, invalidation and affirmation, and sometimes safety and danger.
Yet, many of the systems we use and create don’t offer name flexibility.
Many programmers and designers have a few misconceptions about names, such as assuming people have one moniker that they go by all the time, despite how common it is for names to change over a lifetime. People might update them after a change in marital status, family situation, or gender, or perhaps someone is known by a nickname, westernized name, or variation on a first name.
In most locales, legally changing names is extremely difficult, extremely expensive, requires medical documentation, or is completely out of the question.
Changes to name and gender marker are even more complicated; they tend to be two separate, long-drawn-out processes. To make matters worse, laws vary from state to state within the U.S. and most only recognize two genders—man and woman—rather than allowing non-binary options.Not all trans people change their names, but for those who do, it’s a serious and significant decision that shouldn’t be sabotaged. We can design systems that protect the lives and privacy of our users, respect the fluid nature of personal identity, and act as an electronic curb cut that helps everyone in the process.
Deadnaming
One need only search Twitter for “deadname app” to get an idea of how apps can leave users in the lurch. Some of the most alarming examples involve apps and sites that facilitate real-life interactions (which already involve a measure of risk for everyone).
“Lyft made it completely impossible for me to change my name on its app even when it was legally changed. I reached out to their support multiple times and attempted to delete the account and start over with no result. I was completely dependent on this service for groceries, appointments, and work, and was emotionally exhausted every single time I needed a ride. I ended up redownloading Uber - even though there was a strike against the service - which I felt awful doing. But Uber allowed me to change my name without any hoops to jump through, so for the sake of my mental health, I had to.”
Trans people are more likely to experience financial hardship, so using payment apps to ask for donations is often necessary. Some of these services may reveal private information as a matter of course, leaving them exposed and potentially at risk.
There are also ramifications when linked services rely on our data sources for name information, instigating an unpredictable cascade effect with little or no recourse to prevent the sharing of sensitive details.
These are examples of deadnaming. Deadnaming is what happens when someone’s previous or birth name is used, rather than the name the person uses now. Deadnaming is invalidating at the least, even as a faux pas, but can be psychologically devastating at the other extreme, even putting lives at risk.The experiences of trans, non-binary, or gender-variant folk can vary widely, and they live in disparate conditions throughout the world. Many are thriving and creating new and joyful ways to resist and undo gender norms, despite the common negative narrative around trans lives. Others can face hardship; trans people are more likely to be unstably housed, underemployed, underpaid, and targets of violence in and out of their homes, workplaces, and intimate relationships. The ramifications are amplified for people of color and those with disabilities, as well as those in precarious living/working situations and environments where exposure can put them in harm’s way.
Design for name changes
Here’s what we can do:
Design for renaming. Emma Humphries’ talk on renaming covers this nicely. Airbnb has developed policies and procedures for users who’ve transitioned, allowing users to keep their review histories intact with amended names and/or pronouns.
Get rid of “real name” requirements. Allow people to use names they go by rather than their legal first names.
Clarify when you actually need a legal name, and only use that in conjunction with a display name field.
Have a name change process that allows users to change their names without legal documentation. (It’s likely that you have procedures for marriage-related name changes already.)
Ensure users can still change their display names when connecting with other data sources to populate users’ names.
Don’t place onerous restrictions on changes. Once someone creates a username, web address, or profile URL, allow them to change it.
Draft a code of conduct if you’re part of an online community, and make sure to include policies around deadnaming. Twitter banned deadnaming last year.
Allow people to be forgotten. When people delete their accounts for whatever reason, help them make sure that their data is not lingering in your systems or in other places online.
Update the systems users don’t see, too
Identity management systems can be a mess, and name changes can reveal the failures among those systems, including hidden systems that users don’t see.
One Twitter user’s health insurance company kept their ID number between jobs but changed their gender. Another user updated their display name but got an email confirmation addressed to their legal name.
Hidden information can also undermine job opportunities:
“At a university as a student, I transitioned and changed my name and gender to be a woman. TWELVE YEARS later after being hired to work in the Libraries, the Libraries HR coordinator emailed me that I was listed as male still in the database. He changed it on my asking, but I have to wonder how long… was it a factor in my being turned down for jobs I applied to… who had seen that..?”
Emma Humphries details the hidden systems that can carry out-of-date information about users. Her tips for database design include:
Don’t use emails as unique IDs.
Use an invariant user ID internally, and link the user’s current email and display name to it.
Images
Visuals should allow room for representation and imagination rather than a narrow subset of the usual suspects: figures who appear to be straight, cisgender, able-bodied, and white/Caucasian.
What we can do is feature a variety of gender presentations, as well as not assume someone’s gender identity if they buy certain items.
Some companies, like Wildfang and Thinx, offer a broad array of images representing different races, body sizes, and gender expressions on their websites and in their ads.
Many are also choosing not to hire models, allowing room for imagination and versatility:
“I got a catalog for a ‘classic menswear company’ that features zero photos of any person of any gender. Now if only I could afford an $800 blazer...”
Here's what we can do:
Actively recruit diverse groups of models for photos. And pay them!
If you can’t shoot your own photos, Broadly has recently launched a trans-inclusive stock photo collection free for wide use. Avataaars allows users to create an avatar without selecting a gender.
Information architecture
How we organize information is a political act and a non-neutral decision (librarians have said this for a while). This applies to gender-based classifications.
Many companies that sell consumer goods incorporate gender into their product design and marketing, no matter what. The product itself might be inherently gender-neutral (such as clothing, toys, bikes, or even wine), but these design and marketing decisions can directly impact the information architecture of websites.
Here's what we can do:
Evaluate why any menus, categories, or tags are based on gender, and how it can be done differently:
“Nike has a ‘gender neutral’ clothing category, yet it’s listed under ‘men’ and ‘women’ in the website architecture. 🤔”
Forms
Forms, surveys, and other types of data gathering are surefire ways to include or exclude people. If you ask for information you don’t need or limit the options that people can select, you risk losing them as users.
Here's what we can do:
Critically evaluate why you are asking for personal information, including gender. Will that information be used to help someone, or sell things to your advertisers?
"Why does the @CocaCola site make me select a gender just to make a purchase? Guess my family isn't getting personalized Coke bottles for Christmas."
If you are asking users for their gender, you’d better have a good reason and options that include everyone. A gender field should have more than two options, or should ask for pronouns instead. When including more than binary options, actually record the selections in your databases instead of reclassifying answers as male/female/null, otherwise you risk losing trust when disingenuous design decisions become public.
Honorifics are infrequently used these days, but it takes little work to add gender-inclusive titles to a list. For English-language sites, “Mx.” can go alongside “Mr.” and “Ms.” without fuss. United Airlines debuted this option earlier this year.
Content
Here's what we can do:
Avoid inappropriately gendered language. Your style guide should include singular “they” instead of “he/she” or “s/he,” and exclude frequently used words and phrases that exclude trans folks. Resources such as this transgender style guide are a quick way to check your language and benchmark your own content guidelines.
Check assumptions about gender and biology. Not everyone who can have a period, can get pregnant, or can breastfeed identifies as women or mothers—just as not everyone who identifies as women or mothers can have periods, can get pregnant, or can breastfeed. Thinx, a company that sells period underwear, has an inclusive tagline: “For people with periods.”
Avoid reinforcing the binary. Groups of people aren’t “ladies and gentlemen” or “boys and girls.” They are folks, people, colleagues, “y’all,” or even “all y’all.”
Pronouns aren’t “preferred”—they’re just pronouns. Calling pronouns preferred suggests that they’re optional and are replacing a “true” pronoun.
Avoid reinforcing stereotypes about trans people. Not all trans people are interested in medically transitioning, or in “passing.” They also aren’t fragile or in need of a savior. Gender is separate from sexual orientation. You can’t “tell” someone is trans.
Privacy, surveillance, and nefarious AI
We’ve heard the story of algorithms identifying a pregnant teen before her parents knew. What if an algorithm predicts or reveals information about your gender identity?
Inferences. Users’ genders are assumed based on their purchase/browsing history.
Recommendations. A user bought something before they transitioned and it shows up in “recommended because you bought X.”
Predictions. Users’ genders are not only inferred but used to predict something else based on characteristics of that gender. Even if you don’t tell big websites what your gender is, they assume one for you based on your interests. That kind of reductive essentialism can harm people of all genders. One of this article’s peer readers summed this up:
“Gender markers are a poor proxy for tastes. I like dresses, cute flats, and Raspberry Pis.”
Flashbacks. “On this day” algorithms remind users of the past, sometimes for better (“I’ve come so far”) or for worse (“don’t remind me”).
AI-based discrimination
AI and surveillance software can also reinforce norms about what men’s and women’s bodies should look like, resulting in harrowing airline travel experiences and creating AI-based discrimination for trans people.
So, too, can trans folks’ public data be used for projects that they don’t consent to. Just because we can use AI for something—like determining gender based on a face scan—doesn’t mean we should.
Here's what we can do:
Read up and proactively mitigate bias.AI and algorithms can reflect developers’ biases and perpetuate stereotypes about how people’s bodies should look. Use AI to challenge the gender binary rather than reinforce it. Design for privacy first. Hire more types of people who represent different lived experiences.
Toward a gender-inclusive web
The ideas I’ve offered here are only starting points. How you choose to create space for trans folks is going to be up to you. I don’t have all the solutions here, and there is no singular trans experience. Also, language, definitions, and concepts change rapidly.
We shouldn’t use any of these facts as excuses to keep us from trying.
When we start to think about design impact on trans folks, the ideas we bring into question can benefit everyone. Our designs should go beyond including—they should affirm and validate. Ideally, they will also reflect organizational cultures that support diversity and inclusion.
Here's what we can do:
Keep learning. Learn how to be a good ally. Pay trans user research participants to help validate your design assumptions. Hire trans people on your team and don't hang them out to dry or make them do all the hard work around inclusion and equity. Make it everyone’s job to build a more just web and world for everybody.
Editorial note: All personal statements quoted in this article have been graciously shared with the express consent of the original authors.
This article is stronger and wiser thanks to Mica McPheeters at A List Apart and the following peer readers. Thank you.
Jake Atchison
Katherine Deibel, Ph.D.
Justina F. Hall
Austyn Higgs
Emma Humphries
Tara Robertson
Levi R. Walter
Trans-inclusive Design published first on https://deskbysnafu.tumblr.com/
0 notes
Text
Matters to Outsource to a Virtual Assistant
Utilizing a virtual assistant can shave hours out of your workweek, but knowing which tasks to delegate can be tough, whether you happen to be commencing or developing a company. Most virtual assistants are contract or freelance employees who do their jobs from home and target on administrative tasks which are similar to people of an executive assistant or secretary. Web-sites that specialize in contract employees, this kind of as odesk.com and elance.com, have thousands of listings for virtual assistants.
Together with the amount of virtual assistants are expanding, their knowledge now runs the gamut, generating it easier to search out someone who fits your organization, says Jaleh Bisharat, vice president of marketing at oDesk.com, which can be primarily based in Redwood City, Calif. In 2012, oDesk had 25,000 postings for virtual assistant jobs, in contrast to about 2,500 in 2008.
Entrepreneurs can use virtual assistants for everything from creating vendor or customer support calls to sending out thank you cards to prospective clientele. It truly is critical to construct trust, just as you would that has a long lasting worker. "They grow to be a crew member who just takes place to function remotely," Bisharat says. Not sure where to begin?
How do I come to be a virtual assistant?
I worked like a virtual assistant and I've employed my own virtual assistants at the same time. Here are my recommendations to have begun.
one. Make a decision should you will operate as an independent contractor or an employee
Independent contractors are self-employed and run their particular companies. Around the other hand, some VAs prefer to operate for an established firm that matches VAs and clients.
Tips on how to Turn out to be A VIRTUAL ASSISTANT
Up to date February one, 2018
Numerous years ago I wished to enhance our family’s revenue, but I did not need a frequent work. I had responsibilities I couldn’t without delay drop or hand off to another person so flexibility, generating my personal hrs and working from household have been crucial. Also, I didn’t possess a significant budget for new gear or elaborate training. I grew to become a virtual assistant. It turned out for being the perfect runway for any full-time on-line occupation.
Tips on how to turned out to be a virtual assistant.
Disclosure: Some links under are my affiliate hyperlinks, which means, at no more cost to you, I might earn a commission when you click by means of and create a obtain. Go through my full disclosure policy here.
What exactly is a virtual assistant?
A virtual assistant (VA) presents providers to persons, organizations or suppliers, nevertheless they get the job done on the net instead of going into an workplace.
It is an outstanding work-at-home possibility and 1 within the most cost-effective approaches of making money on-line simply because it’s only a matter of charging others for any talent you by now have.
Staying a VA (virtual assistant) is great since you just charge to get a skill you already have.
CLICK TO TWEET
What do virtual assistants do?
The internet has produced it achievable to try and do a broad number of things remotely, or, “virtually.”
Lots of people hear “virtual assistance” and feel only of administrative tasks like typing and answering emails. But the array of duties VAs do is a lot more broad.
There are actually a great number of services you can actually present essentially. Right here is often a partial checklist:
Email management
Calendar management
Travel arrangement
Writing
Ghostwriting
Graphic style and design / creation
Web style and design / growth
Researching
Editing
Tutoring
Audio / video / photograph editing
Consulting / counseling / coaching
Bookkeeping
Copywriting
Advertising and marketing / Promotion
Social media management
Project management
Customer service
Transcription
Programming
App growth
Data entry
Visioneering (persons send you photos of their room/house/yard and also you present tips for improvement)
Something else you can actually do without the need of obtaining to be from the exact same physical place as your client
How much do virtual assistants make?
It is determined by your talent degree plus the style of services you provide.
Duties like information entry may possibly fetch $10-$15 an hour, but if you've got a specialized ability or skills, you could make $100 bucks an hour or even more.
Most VAs set their very own charges, so that you are in handle. That is yet another reason most people are creating the leap into virtual assistance.
How do I turn into a virtual assistant?
I worked being a virtual assistant and I have employed my own virtual assistants too. Here are my recommendations to acquire started.
1. Choose when you will operate as an independent contractor or an worker
Independent contractors are self-employed and run their particular organisations. Over the other hand, some VAs choose to work for an established company that matches VAs and consumers.
Independent contractor vs. worker
Not sure whether or not you desire to function for on your own or perhaps a business? Right here would be the benefits and drawbacks for every:
Pros of becoming an independent contractor
You do the job for oneself, which means you get in touch with the many shots. You set your very own pricing, you choose your personal clients, you happen to be your personal boss.
Your function hrs are set totally by you.
Any income you make goes directly for you, in lieu of currently being funneled as a result of your employer who keeps a percentage.
Cons of being an independent contractor
Running and being responsible for your own business enterprise. Like creating any enterprise, this choice takes quite a bit of time, vitality and hustle. The accountability rests absolutely in your shoulders.
Getting your personal clients. This will be difficult, mainly at the starting before you decide to have happy consumers who can recommend your services.
Here in the U.S., you may be responsible to withhold and shell out your own earnings taxes, like Social Safety, Medicare, and so on.
Pros of currently being an worker
That you are only liable for your perform at the agreed upon occasions. It is an awesome condition for those who desire to clock in and clock out without obtaining to get worried concerning the business enterprise otherwise.
Customers are usually matched with you by your employer, or, give a platform exactly where it is painless to connect with new customers. No need to find all of your clients oneself.
You have a built-in support technique. Lots of businesses give assets, equipment, neighborhood and support for his or her VAs.
Cons of getting an employee
You have to answer to an employer. This may possibly mean you've pointers to follow.
You could possibly have significantly less versatile hrs dependent to the clients your employer matches you with.
Your pay out is generally determined for you personally.
You could possibly favor currently being an independent contractor if:
You like networking and hustle.
You are an entrepreneur at heart.
You like owning full handle.
You dislike becoming an worker.
You do not need a good deal of cash flow proper away (while in the event it will take a whilst to construct up your client checklist).
You could prefer currently being an worker if:
You favor getting capable to clock in and clock out.
You’d rather someone else uncover consumers and inform you when and the place to demonstrate up.
You like clear boundaries so perform does not spill over into other components of your daily life.
You may need earnings right away and really don't have or vitality to “pound the pavement” or creating a home business.
What about beginning at a VA organization then moving out on my personal?
This really is doable, however it might be tricky. There are actually legal and ethical concerns to consider.
Most VA businesses contain clauses inside their legal contracts prohibiting you from taking their clientele with you in case you decide to leave. For example, you can expect to have to agree to not make contact with any of their customers to get a specified period of time. To put it differently, should you operate to get a VA enterprise and therefore are matched using a consumer, you can not leave that provider and motivate your consumer to retain the services of you by yourself.
On the other hand, if you come to a decision to leave a company and start your individual VA home business as an independent contractor, and come across your own clients, this may perhaps be an alternative.
2. Get a web page
This is certainly necessary for independent contractors. People need to have to be ready to locate you, so a presence on the web is critical. It provides you with a a lot more experienced look, an opportunity to highlight some of your techniques and an opportunity to describe your method.
Use my step-by-step guidebook to create a website, or a weblog if you want to consistently include articles. (Note the post title is “How to start a Blog” however the exact same steps function to begin an internet site with this particular a single compact tweak).
Independent contractors: a must-have
An employed VA: optional (but not a terrible plan in situation you would like to venture out by yourself later)
Be helpful
As you interact on social media and network with other VAs, be really cautious to not come across as spammy. Mass emails or “cold” emails to people that don’t know you are seldom profitable.
I fully grasp the require to produce an revenue, but get the time to offer you valuable facts very first. This may possibly come in the form of really useful content articles written on your website, or it could possibly are available in the type of genuinely valuable (and respectful) tips to another person you meet on the net.
In my case, I casually supplied some strategies to a pal on Twitter and it turned out to become the start out of a working relationship that lasted quite a when.
The place can I work as being a VA?
If doing work as an independent contractor and locating your own customers will not be your point, think about doing work for a corporation that matches VAs with clientele. For some VAs, the enable in discovering customers is well worth sharing the earnings.
Companies to take into account are Belay Answers (formerly eaHelp) and Upwork. I’ve personally hired VAs from each. Belay is known as a a lot more elite service with very thorough hiring and matching processes. Upwork is really a greater platform and less complicated to join, but you’ll be competing with additional VAs for your similar jobs.
Some other suppliers to take into account are Priority VA or Fancy Hands. I don’t have personal knowledge with both, but have heard really good factors about them.
cómo manejar redes sociales
0 notes
Text
trabajos virtuales desde casa Colombia|que hace un asistente administrativo|asistente virtual en español|funciones de un asistente|redes sociales en internet|uso de las redes sociales|marketing online|marketing en redes sociales|community manager|que es un community manager|social media marketing|community manager funciones|cómo ser community manager|cómo ser un community manager|curso de redes sociales|cómo manejar redes sociales
Items to Outsource to a Virtual Assistant
Using a virtual assistant can shave hours from your workweek, but recognizing which tasks to delegate is often tough, whether or not you happen to be starting up or rising a small business. Most virtual assistants are contract or freelance staff who do their jobs from house and focus on administrative duties which might be equivalent to individuals of an executive assistant or secretary. Internet websites that specialize in contract workers, such as odesk.com and elance.com, have 1000's of listings for virtual assistants.
With all the number of virtual assistants are growing, their expertise now runs the gamut, making it less complicated to uncover somebody who fits your organization, says Jaleh Bisharat, vice president of marketing at oDesk.com, that's based mostly in Redwood City, Calif. In 2012, oDesk had 25,000 postings for virtual assistant jobs, compared to about two,500 in 2008.
Entrepreneurs can use virtual assistants for anything from generating vendor or customer service calls to sending out thank you cards to potential clients. It can be critical to create trust, just as you would using a long term employee. "They become a staff member who just transpires to function remotely," Bisharat says. Not certain wherever to begin?
How do I turn into a virtual assistant?
I worked being a virtual assistant and I've employed my personal virtual assistants too. Here are my recommendations to obtain begun.
1. Choose if you will operate as an independent contractor or an employee
Independent contractors are self-employed and run their particular businesses. To the other hand, some VAs choose to deliver the results for an established firm that matches VAs and clientele.
Tips on how to Grow to be A VIRTUAL ASSISTANT
Up to date February one, 2018
Quite a few years ago I wanted to maximize our family’s earnings, but I did not want a common occupation. I had responsibilities I couldn’t quickly drop or hand off to somebody else so versatility, creating my personal hrs and functioning from dwelling were major. Also, I didn’t possess a substantial budget for new gear or elaborate coaching. I became a virtual assistant. It turned out to get an ideal runway to get a full-time on the net career.
Ways to become a virtual assistant.
Disclosure: Some back links under are my affiliate back links, meaning, at no further cost for you, I may earn a commission in case you click by way of and create a acquire. Read my complete disclosure policy right here.
What's a virtual assistant?
A virtual assistant (VA) offers companies to people, organizations or firms, however they work on the net as an alternative to going into an workplace.
It’s a great work-at-home possibility and one particular of your most cost-effective means of making money on the web because it is only a matter of charging other people for a skill you currently have.
Staying a VA (virtual assistant) is good mainly because you simply charge for any skill you previously have.
CLICK TO TWEET
What do virtual assistants do?
The online world has created it achievable to undertake a wide number of items remotely, or, “virtually.”
Lots of people hear “virtual assistance” and imagine only of administrative tasks like typing and answering emails. But the range of duties VAs do is way more broad.
There are actually countless solutions you can actually produce pretty much. Right here is a partial record:
Electronic mail management
Calendar management
Travel arrangement
Creating
Ghostwriting
Graphic style and design / creation
Net design / advancement
Studying
Editing
Tutoring
Audio / video / photograph editing
Consulting / counseling / coaching
Bookkeeping
Copywriting
Advertising / Promotion
Social media management
Task management
Customer service
Transcription
Programming
App improvement
Information entry
Visioneering (people today send you images of their room/house/yard and you present recommendations for improvement)
Anything at all else you can do without having owning for being from the same physical spot as your client
Simply how much do virtual assistants make?
It is dependent upon your ability level along with the style of support you give.
Tasks like data entry could possibly fetch $10-$15 an hour, but if you have a specialized skill or experience, you might make $100 dollars an hour or additional.
Most VAs set their very own rates, so that you are in handle. This is often an additional explanation lots of individuals are building the leap into virtual support.
How do I grow to be a virtual assistant?
I worked like a virtual assistant and I have employed my own virtual assistants as well. Here are my recommendations to get commenced.
one. Decide if you will operate as an independent contractor or an worker
Independent contractors are self-employed and run their very own businesses. Over the other hand, some VAs favor to deliver the results for an established business that matches VAs and customers.
Independent contractor vs. employee
Not sure no matter whether you want to deliver the results for yourself or a enterprise? Right here are the benefits and drawbacks for every:
Pros of currently being an independent contractor
You operate for by yourself, which means you phone each of the shots. You set your individual pricing, you select your own personal customers, you may be your individual boss.
Your deliver the results hrs are set wholly by you.
Any money you make goes straight for you, as opposed to being funneled through your employer who keeps a percentage.
Cons of remaining an independent contractor
Working and staying responsible for your individual company. Like establishing any business enterprise, this option will take quite a lot of time, energy and hustle. The responsibility rests totally in your shoulders.
Choosing your very own clientele. This could be complicated, specially at the starting before you have completely happy consumers who can recommend your providers.
Here from the U.S., you are accountable to withhold and spend your own personal cash flow taxes, like Social Protection, Medicare, etc.
Pros of staying an employee
You're only accountable for your get the job done at the agreed upon instances. It’s an excellent scenario for anyone who desire to clock in and clock out not having having to get worried about the home business otherwise.
Customers are commonly matched with you by your employer, or, supply a platform where it is easy to connect with new clientele. No desire to seek out all your clientele yourself.
You have a built-in support program. Countless businesses deliver sources, resources, local community and help for his or her VAs.
Cons of remaining an worker
You ought to response to an employer. This could possibly indicate you may have suggestions to follow.
You could have significantly less flexible hours based over the customers your employer matches you with.
Your pay is generally determined to suit your needs.
You could possibly choose becoming an independent contractor if:
You like networking and hustle.
You’re an entrepreneur at heart.
You like having complete handle.
You dislike being an worker.
You really do not want a good deal of income right away (within the occasion it requires a when to construct up your consumer checklist).
You could possibly want getting an worker if:
You want being capable to clock in and clock out.
You’d rather another person get customers and inform you when and where to demonstrate up.
You like clear boundaries so function does not spill above into other components of your daily life.
You'll need income ideal away and really don't have or energy to “pound the pavement” or establishing a home business.
What about starting up at a VA organization then moving out on my own?
This is certainly probable, but it is often difficult. You will find legal and ethical concerns to contemplate.
Most VA corporations consist of clauses in their legal contracts prohibiting you from taking their customers with you if you make a decision to leave. By way of example, you will should agree to not get in touch with any of their consumers for a specified period of time. In other words, if you work for a VA organization and therefore are matched using a consumer, you can not depart that firm and inspire your client to employ you by yourself.
On the other hand, in the event you decide to depart a company and start your very own VA enterprise as an independent contractor, and locate your personal clients, this could possibly be a choice.
two. Obtain a web-site
This can be important for independent contractors. Persons need to get capable to discover you, so a presence to the world wide web is important. It gives you a extra specialist appearance, a chance to highlight some of your capabilities and a chance to clarify your procedure.
Use my step-by-step manual to set up a website, or perhaps a blog site if you would like to routinely add articles or blog posts. (Note the post title is “How to begin a Blog” however the similar procedures do the job to start out a web site with this particular one compact tweak).
Independent contractors: a must-have
An employed VA: optional (but not a awful plan in case you wish to venture out on your own later on)
Be helpful
While you interact on social media and network with other VAs, be pretty cautious to not encounter as spammy. Mass emails or “cold” emails to people who don’t know you will be seldom prosperous.
I understand the want to generate an income, but consider the time to deliver useful info initially. This may well can be found in the kind of definitely useful content articles written in your web site, or it could possibly are available in the form of genuinely handy (and respectful) tips to a person you meet internet.
In my case, I casually provided some suggestions to a buddy on Twitter and it turned out to be the start out of a working relationship that lasted really a while.
The place can I do the job as being a VA?
If doing work as an independent contractor and choosing your very own customers just isn't your thing, give some thought to functioning for any company that matches VAs with clients. For some VAs, the guide in discovering consumers is worth sharing the profits.
Providers to think about are Belay Answers (formerly eaHelp) and Upwork. I’ve personally hired VAs from both. Belay is usually a a lot more elite service with rather thorough employing and matching processes. Upwork is a greater platform and easier to join, but you’ll be competing with more VAs for the same jobs.
Another companies to consider are Priority VA or Fancy Hands. I really do not have individual experience with either, but have heard good important things about them.
asistente virtual en español
http://trabalhandoemcasa.webblogg.se/2018/may/factors-to-outsource-to-a-virtual-assistant.html
0 notes
Text
20 7 Top Blog Design Tips
7 Top Blog Design Tips
If you are a dog groomer by profession, and you also need to maintain stocks of grooming your dog supplies, otherwise you need to get supplies for your personal use for your own personel dog, gradually alter save just as much money that you can. Grooming supplies can be expensive if you buy them at your family retail prices. Here are some applying for grants how you can save some bucks for the grooming supplies that you need.
Added to writing good content on your blog English and subject wise you need to to become good 'visitor'. You have to regularly read other blogs in addition to contribute to them when it comes to comments. This not merely enables you to build network with bloggers it offers you an idea of the 'thought process' behind the reader/visitor of your respective blog.
Internet site page views is a primary factor in visitor posts. Blogs that has excellent superior and targeted variety of visitors can bring a lot more rewards to any on the net businessman which do visitor posts. Each and every visitor posts can bring more readers aimed at your web, gives you much more probable conversion, adds much more subscribers and exposure.
You must captivate and maintain the interest with the reader. Make sure that your content is fresh and lively don't just toll out chunks of facts and make sure that the details are correct and useful. Add in a human touch a casual comment, an unusual expression. Share your enthusiasm for the subject being discussed.
(more info)
Blogs are fairly informal and thus do not require you to be considered a writer to be a blogger. Bloggers often choose to blog so that you can share their interest on the particular subject or theme and simply get enjoyment by doing so. Video blogging is another method that people can blog and never having to write whatsoever. Video bloggers usually time it must discuss their topic of the day, record it, and post it to their blog. Video is also used by text bloggers in an effort to enhance a reader's experience.
There are many ways to use blogging. In most cases, blogging can be used social means alone, however you can also use your blogs for advertising. If you own an enterprise, either online or off line, you may make use of blogs in promoting your merchandise. The use of blogging running a business is more popular as it can establish the credibility of a business and promote manufacturer recognition.
Anyone, no matter what their technical capability is, can easily create and publish a blog very quickly. New bloggers can use web publishing tools that assist the development of a blog by making use of blog templates. Blogs might be hosted on your site hosting website that is certainly committed to hosting blogs. Hosting your site on your blog hosting website costs little to no money in any way and is usually available to anyone regardless of what the theme of their blog is. What takes probably the most effort is arriving on top of content to write to your blog on the regular basis.
Internet site page views is a key factor in visitor posts. Blogs which includes excellent superior and targeted variety of visitors would bring a lot more rewards to the on the web businessman that visitor posts. Each and every visitor posts may bring more guests to your site, will give you much more probable conversion, adds a lot more subscribers and exposure.
So just what can you must be compelled to perform when nothing involves mind? there is not any surefire approaches to urge the proper concepts however you'll find easy ways to induce your brain cells flowing. no-one will guarantee you of having the appropriate mindset however many different ways may aid you in achieving that state of mind. Here are five straightforward methods for that.
(more info)
Many bloggers new to the blogging world will most likely wrestle with this particular decision longer than they are doing when choosing health care insurance because of its importance and contribution with their sites. Having a well running and simple gain access to internet site is intrinsic to its success and popularity, which will lend itself on their credibility within their respective fields. As bloggers you should understand these facts rather than really go to town the traps and pitfalls a below reputable web host can present.
Blog posting serves two essential roles insofar since it is not merely supposed to attract new readers but also you can keep them continually returning. All popular blogs have a very important factor in keeping which is they keep your blog reader happy with fresh and frequent updates. This may seem like trying to be about the 'top of one's game' 24/7 but there is actually a way to handily maintain your blog entries interesting and fresh! Nobody said creating a successful blog was easy however it is also less overwhelming as it might seem.
In the recent times blogging has gained plenty of popularity plus more plus more people are adopting money blogs to earn their living. A fun and interesting approach to build an income, blogs are very interesting to publish and study. However it is significantly less easy as it's as one requires doing lots of writing because of it, so if you are someone that is nice at maintaining and writing them then you definitely should definitely go ahead and take job a step further and earn a great income as a result.
Once you know creating article posts who use SEO, you will notice big most current listings for yourself. Posting being a guest writer on somebody else's blog is a superb strategy to drive targeted prospects for your site. You can leverage other sites' traffic by writing a guest post for the kids. To ensure that the visitors relevant in your site, be sure you only post on blogs within the same niche.
Seniors face many doubts in your life because they start to wonder the best way to fill their time. Some consider getting an element time job to earn another income and simply stay busy. As seniors consider this, many will wonder when they are still qualified or wanted within the workplace. In this area, it is possible to share resources with them that relate seniors who're considering returning to work what kind of tasks are available. From universities to offices to schools to hotels and more, most companies will gladly hire older persons since they're experienced and responsible. By sharing this sort of information with people that are within their retirement years, it will be possible to give them valuable insight to opportunities that await them if they're considering reentering the workforce.
(more info)
Many people use blogging being a cheap substitute for creating a website, but it's more effective when found in addition to your site. The top Dallas SEO experts could be hired to blog for the site with high-quality content that includes your targeted keywords and links for your main site the location where the sales could be made. Good Dallas web design experts can coordinate your website to your site to give the person a fluid experience when going relating to the two.
It's about time that business organizations and brands wake towards the idea of the importance of websites and blogs or web journals. Many brands have included techniques like social media marketing and blogging for marketing operations. The present companies are highly competitive and no business organization may want to leave any page unturned within their book of promoting strategies. So, optimal use of the Internet, the boon of the twenty-first century, ought to be stressed upon highly. The total number of Internet surfers increased by 14% in 2010. Moreover, the Internet is one of the mass mediums where targeting a large audience isn't very difficult.
Search engines love quality content, and a website cannot contend with your blog in relation to content. The search engines know this and therefore blog are quickly a part of listings to ensure top quality inside search. The more content you will find the better position your site gets inside the search engines.
Putting words into pictures in the readers thoughts are a skill. a definite and crisp depiction takes a definite aptitude that only creativity will offer you. Similes and metaphors help lots, however the way a piece gets entwined word for word, sentence by sentence then paragraph by paragraph into a complete article develops the essence informed.
Even though this alone must be reason enough to require to develop an automatic blog empire, the actual fact in the matter is really you will discover further benefits that you can obtain by doing so. Every single automated blog which you build is essentially going to be a customers magnet and drive numerous viewers to it. These particular viewers are then channeled towards your moneymaking website - but there are many stuff that you can employ this traffic for as well.
(more info)
Also sharing activities which are fun like dance classes, water aerobics, and vacations for seniors, cruises for seniors, and group organizations can give seniors many ideas of recent things they can caused by fill their time when they feel like they've got absolutely nothing to do any longer. Creating a blog to help promote health insurance recreation inside the lives of older persons can also provide you with a satisfaction and reward.
Your blogging goal is always to consistently deliver compelling and informative content which contains ways of the down sides of your readers. Now that people read your posts, you'll want to give it an original voice as well. And it's not simply because I want to receive backlinks business blogs. It's always great to understand off their bloggers, and get valuable information from other blog commentators too. Participating in an interactive community is definitely beneficial.
Instead because the dot com bubble burst inside late 90's the world wide web once more became a wasteland of nerd experimentation however the nerd seed have been planted in individuals that previously might have been deterred by every one of the science fiction as well as the math. As the aughts progressed and the internet took over as hot bed of commerce folks always gave the impression to comprehend it might become another world grew plus many ways it had been just an outgrowth of what the net would have been to start with. Those forums were becoming your site. "The Blog" was becoming the most basic component of Web 2.0. A world of "user generated content." No longer were people logging onto the world wide web to venture to sites about things they wanted to find out about. Now they are created sites. The shock waves on this were felt in a short time and became compounded as new platforms particularly social networks (Friendster begat MySpace, MySpace begat Facebook etc.) made people more and more comfortable and even enslaved by sharing themselves along with their opinions on the net.
First, I should preface this discussion by saying first you need to honestly evaluate whether you need to just work at monetizing your blog post. Steve Pavlina includes a very thorough post that goes over what?s necessary to do this well, and why the majority of folks who try turn out not generating significant income.
Search for templates on any search engines like Google and you will run into many choices from which to choose; this search is crucial for the reason that first thing prospective readers will discover would be the general layout and search of the blog that really wants to be inviting. Efficient Blogging and Make Money Blogging demand that you possess a template that either is associated for your topic or nature of weblog or perhaps simply good-looking and classic. Possibly the key aspect necessary for a sustainably popular weblog is passion and also the capacity to translate the enthusiasm into words frequently. As soon as the readers work through the original appear with all the blog, they will take a look at then content material hence; this item must be because of the utmost priority.
(more info)
u Interaction - With the help of blogs you'll be able to connect to your customers. You can see the customers' comments on the posts and updates. The negative or positive feedbacks from your customers enables you to streamline the online strategy of your company. This could potentially save 1000s of dollars.
As the internet continually evolves, new terminology, new schemes, new cameras or scanners, start up business opportunities and new concepts show up on consistantly. Not so long ago the phrase blog or blogging only agreed to be one of those concepts, but now, to many people online visitors the term(s) are well known. Even so, merely learning its presence in the world of online marketing does not mean that you simply completely understand that of a blog is or what blogging is centered on. And of course there will always be those people who are still unfamiliar with the concept of blogging. With this in mind, let us briefly consider the term blogging or try and explain exactly what a blog is. Or, to put it another way - precisely what does blog mean?
Instead because dot com bubble burst inside late 90's the internet once more became a wasteland of nerd experimentation however the nerd seed was planted in individuals that previously may have been powered down by all the science fiction and also the math. As the aughts progressed and the world wide web took over as hot bed of commerce folks always seemed to understand it might become another world grew along with many different ways it had been just an outgrowth of what the world wide web ended up being to start with. Those forums were becoming the blog. "The Blog" was becoming the simplest component of Web 2.0. A world of "user generated content." No longer were people registering to the net to visit sites about things they wanted to learn about. Now they are intended web sites. The shock waves with this were felt quickly and became compounded as new platforms particularly social networking sites (Friendster begat MySpace, MySpace begat Facebook etc.) made people a lot more comfortable and in many cases dependent on sharing themselves along with their opinions on the web.
Recognizing their growing popularity with internet viewers many bloggers took to use their platforms as a way to more actively promote for any profit. The ability to passively advertise to loyal readers while still supplying them the useful content they've arrive at expect has been shown to be a great promotional marketing approach.
Blogging is an excellent strategy to develop lots of different income streams. As your site becomes more popular, you may set out to sell advertising space inside your sidebars. You might even consider adding Google Adsense code. That's just one single monetization option it is possible to decide to choose. There are plenty of others all attempting to grab your blog visitors' attention. Another more likely to be Text Link Ads. Another option is AdBrite. You can also sell right to individual private advertisers. If you sell six spaces on the sidebar at $50 monthly, that's $300 30 days that you can generate just through blogging!
(more info)
Let me say this another way because for a lot too many people blogs are an unbridled (and correspondingly horrifying) way over vanity, self-gratification, arrogance, not forgetting an avalanche of incredibly boring stuff and Things You Don't Want To Know. Yes, a lot of smart people rely on them being a cheap form of venting and therapy.
youtube
0 notes