#zerotrustarchitecture
Explore tagged Tumblr posts
Text
2025 Cyber Threats: Are You Ready?

Cybersecurity in 2025: Emerging Threats and How to Protect Yourself
Emerging Cyber Threats in 2025 1. AI-Powered Cyber Attacks 2025 Cyber Threats: Are You Ready? Artificial intelligence is a double-edged sword. While it's enhancing threat detection and response, cybercriminals are also using AI to automate phishing, crack passwords faster, and create deepfake content that can bypass traditional verification systems. 2. Deepfake Scams & Social Engineering With deepfakes becoming nearly indistinguishable from real content, attackers can impersonate executives, colleagues, or even family members to manipulate victims into sending money or sensitive information. 3. Supply Chain Attacks As businesses become more interconnected, attackers are targeting third-party vendors to gain access to larger organizations. Weak links in the supply chain can be exploited to deliver ransomware or steal data undetected. 4. Quantum Computing Risks While still emerging, quantum computing poses a future threat to current encryption methods. Experts warn that data stolen today could be decrypted later, once quantum computers are capable enough—a concept known as "store now, decrypt later." 5. IoT Vulnerabilities With billions of connected devices in use, from smart homes to wearable tech, the Internet of Things (IoT) continues to be a major attack surface. Many of these devices lack basic security features, making them easy targets.
How to Protect Yourself and Your Organization
✅ 1. Embrace Zero Trust Architecture 2025 Cyber Threats: Are You Ready? "Never trust, always verify" is the new standard. Every access request—whether internal or external—should be authenticated, authorized, and continuously monitored. ✅ 2. Update and Patch Regularly Unpatched software is a goldmine for hackers. Ensure all systems, applications, and devices receive regular updates and security patches. ✅ 3. Use Multi-Factor Authentication (MFA) Passwords alone are no longer sufficient. MFA adds a critical layer of security, making it significantly harder for attackers to breach accounts. ✅ 4. Educate and Train Continuously Human error remains a top cause of breaches. Regular training on phishing, secure practices, and emerging scams can reduce risk dramatically. ✅ 5. Invest in AI-Driven Cybersecurity Tools Modern threats require modern solutions. AI-powered security platforms can detect anomalies in real time, automate responses, and help reduce incident response times.
The Bottom Line
2025 Cyber Threats: Are You Ready? Cyber threats in 2025 are more intelligent, invisible, and insidious than ever before. Staying protected requires a proactive, layered approach that blends cutting-edge technology with human vigilance. Whether you're an individual user or a global enterprise, the key to surviving the next wave of cyber threats is simple: Stay informed. Stay updated. Stay secure. Read the full article
#AICyberAttacks#Artificialintelligence#Cybersecurity2025#CybersecurityBestPractices#DeepfakeScams#EmergingCyberThreats#Family#IoTSecurity#Multi-FactorAuthentication#QuantumComputingRisks#SupplyChainCybersecurity#Technology#ZeroTrustArchitecture
0 notes
Text
0 notes
Text
AWS ZTAG For US Government Improves Zero Trust Adoption

Discover how Zero Trust concepts are improving US federal, state, and local cybersecurity. Learn how AWS ZTAG helps install ZTA and secure key infrastructure.
Government organisations must create unmatched security procedures to protect IT infrastructure and data. Trust inside an organization's network borders is insufficient for perimeter-based security. Due to cloud-based resources and BYOD rules, additional security measures are needed than perimeter-based models. Iranian government-sponsored APT actors infiltrating government networks and the worldwide JetBrains CVE assault show that perimeter-based security is poor.
Improving Cybersecurity was Biden's May 2021 ERP14028. These presidential orders require US federal entities to establish zero trust architectures (ZTAs) to improve cybersecurity and safeguard vital infrastructure from internet threats. The DoD Zero Trust Strategy and CISA Zero Trust Maturity Model detail zero trust implementation. US Office of Management and Budget (OMB) CISA implementation targets for FCEB agencies are FY2024 and FY2025, while DoD has goals for FY2027 and beyond.
Zero trust principles check the security and authenticity of each user, device, and transaction to access protected data, apps, and services regardless of network location. This strategy ensures only legitimate parties have access to critical resources and decreases implicit trust, lateral network movement, and unauthorised access.
Amazon Web Services (AWS) is driving this paradigm shift by offering government-focused services and capabilities to enable government agencies adopt zero trust. AWS recommends a zero trust strategy to provide enterprises a powerful, scalable, and proactive cybersecurity plan that meets regulatory standards and protects their important resources.
AWS ZTAG: Government-focused
The AWS Zero Trust Accelerator for Government (ZTAG) helps government entities implement zero trust architectures with tools. AWS ZTAG has accelerators like:
Assessment tools for zero trust maturity
Implementation tips and reference architectures
Integration of AWS ISV products with AWS services
AWS reference deployments with major ISV partners
AWS Marketplace simplifies purchasing.
You can utilise AWS ZTAG assessment tools to uncover areas where you don't fulfil the government's zero trust requirements and get customised recommendations. AWS ISV partners provide services and solutions to help you achieve CISA or US DoD zero trust functions. AWS ZTAG prioritises federal, state, and local US government zero trust frameworks for international adoption.
AWS accelerates zero trust adoption
Designed to meet government organisations' objectives and challenges, the AWS ZTAG approach offers many benefits:
Matches US DoD and CISA zero trust models and may be expanded to other government or industry models.
Helps you detect zero trust gaps and create cybersecurity plans to develop a secure IT infrastructure faster.
Builds and expands cyber capabilities with top AWS ISV partners.
Gradual acceptance makes zero trust architecture transition easy.
Specialised expertise for government zero trust processes
Starting AWS ZTAG
Government entities may start their zero trust journey with AWS zero trust examinations, per DoD or CISA criteria. Work with a zero trust expert to assess your surroundings. These tests can help you assess your agency's zero trust maturity, identify gaps, and design a customised roadmap that meets your objectives and budget. Reevaluating your environment at each instant lets you track your progress.
Conclusion
The AWS Zero Trust Accelerator for federal helps US federal agencies transition to zero trust infrastructures. AWS ZTAG integrates industry-leading security solutions with the AWS Cloud architecture to provide a flexible, government-centric cybersecurity posture while maintaining operational agility.
AWS ZTAG may help government agencies enhance security, accelerate zero trust, and satisfy regulatory requirements.
For more details visit govindhtech.com
#AWSZTAG#ZeroTrust#zerotrustarchitectures#AWSZeroTrustAcceleratorforGovernment#ZeroTrustAcceleratorforGovernment#AWSZeroTrust#technology#technews#technologynews#news#govindhtech
0 notes
Text
Guiding IT Leaders Through Zero Trust Transformation.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Blueprint for IT leaders: Adopt Zero Trust to shield data, drive growth, and embed security in every access request. In today’s threat-filled world, #ZeroTrustArchitecture is more than a buzzword. It’s a shift in how we secure data, devices, and people. As a veteran technology executive, I’ve seen perimeter walls fall. I’ve…
#CIO priorities#digital transformation leadership#emerging technology strategy#IT operating model evolution#News#Sanjay Kumar Mohindroo#Zero Trust Architecture
0 notes
Text
AI in Cybersecurity: $154.6B by 2034 – The War on Hackers Just Got Real!
AI in Cybersecurity market is revolutionizing threat detection, prevention, and response with machine learning, predictive analytics, and automated security solutions. As cyber threats evolve, AI-driven cybersecurity provides real-time defense mechanisms, ensuring data protection, network security, and endpoint resilience.
To Request Sample Report : https://www.globalinsightservices.com/request-sample/?id=GIS33021 &utm_source=SnehaPatil&utm_medium=Article
🌍 Market Overview & Key Trends
✅ Endpoint security dominates, reflecting the rising need to protect devices from sophisticated cyber threats. ✅ Network security follows closely, emphasizing data protection during transmission. ✅ AI-powered tools like antivirus, firewalls, and intrusion detection systems are transforming cyber defense strategies. ✅ Machine learning & behavioral analytics enhance anomaly detection, making AI a game-changer in cybersecurity.
📈 Regional Insights
🌎 North America leads, driven by technological advancements & high cybersecurity awareness. 🇪🇺 Europe ranks second, fueled by strict data protection laws (GDPR) & AI security investments. 🇺🇸 The U.S. dominates, with early adoption of AI-driven security solutions. 🇬🇧 The UK is emerging as a key player, supported by government initiatives & cybersecurity innovations.
🏆 Market Segmentation & Growth
🔹 Type: Network Security, Endpoint Security, Application Security, Cloud Security 🔹 Technology: Machine Learning, NLP, Context-Aware Computing 🔹 Deployment: On-Premises, Cloud-Based, Hybrid 🔹 End Users: BFSI, IT & Telecom, Healthcare, Government, Retail, Manufacturing 🔹 Key Players: IBM, Cisco, Palo Alto Networks
🚀 Future Outlook
The market, valued at $12B in 2023, is expected to skyrocket to $35B by 2033! Network security leads with 45% market share, followed by endpoint security (30%) and application security (25%). AI’s integration with big data & machine learning is set to redefine cybersecurity strategies, offering proactive protection against cyber threats!
#aiincybersecurity #cybersecuritysolutions #machinelearningsecurity #threatdetection #endpointsecurity #networkprotection #firewalltechnology #intrusiondetection #cloudsecurity #predictiveanalytics #dataprotection #gdprcompliance #automatedsecurity #cyberawareness #digitaldefense #securityintelligence #aicyberdefense #riskmanagement #identityprotection #realtimemonitoring #ethicalhacking #cyberthreats #frauddetection #securityautomation #nextgensecurity #cyberresilience #anomalydetection #cyberforensics #blockchainsecurity #securecloud #itsecuritytrends #zerotrustarchitecture #infosecurity #cyberattackprevention #bigdatasecurity
Research Scope:
· Estimates and forecast the overall market size for the total market, across type, application, and region
· Detailed information and key takeaways on qualitative and quantitative trends, dynamics, business framework, competitive landscape, and company profiling
· Identify factors influencing market growth and challenges, opportunities, drivers, and restraints
· Identify factors that could limit company participation in identified international markets to help properly calibrate market share expectations and growth rates
· Trace and evaluate key development strategies like acquisitions, product launches, mergers, collaborations, business expansions, agreements, partnerships, and R&D activities
About Us:
Global Insight Services (GIS) is a leading multi-industry market research firm headquartered in Delaware, US. We are committed to providing our clients with highest quality data, analysis, and tools to meet all their market research needs. With GIS, you can be assured of the quality of the deliverables, robust & transparent research methodology, and superior service.
Contact Us:
Global Insight Services LLC 16192, Coastal Highway, Lewes DE 19958 E-mail: [email protected] Phone: +1–833–761–1700 Website: https://www.globalinsightservices.com/
0 notes
Text
Zero Trust Security
In today’s world, the rapid pace of digital transformation, increased use of cloud services ☁️, and adoption of hybrid work have all created a continually shifting enterprise environment that’s chaotic and difficult to secure. Thereby Zero Trust Security Model comes in, which implies a “Never Trust, Always Verify” approach that will secure identities, endpoints, applications, data, infrastructure, and networks, while providing visibility, automation, and orchestration.
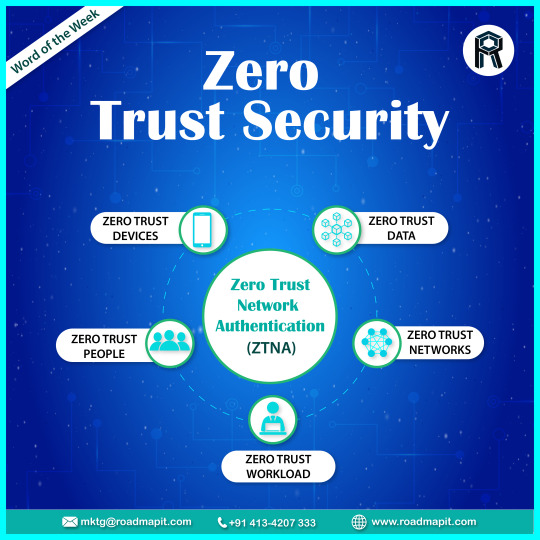


#zerotrust#zerotrustaccess#zerotrustsecurity#wfh#remotework#zerotrustarchitecture#seguran#workfromhome#zerotrustmodel
0 notes
Link
Having a robust system to protect ones’ data from being misused has become the need of the hour. To solve this major issue, zero trust model has arrived.
#implementzerotrust#whatiszerotrust#whatiszerotrustarchitecture#zerotrust#zerotrustarchitecture#zerotrustmodel#zerotrustnetwork#zerotrustnetworkaccess#zerotrustprinciples#zerotrustvsvpn#zerotrustsecurity
0 notes
Text
0 notes