Text
Controlling app access on a specific SharePoint site collections
Imagine facing a significant challenge when your automation processes suddenly fail due to expired SharePoint secrets, interrupting access to a key SharePoint site and bringing operations to a halt. After reaching out to the IT team, they promptly replaced the outdated app in Azure Apps with a new one, generating fresh credentials — tenant ID, secrets, and Application (Client) ID. These credentials are vital for our automation workflows, enabling access to the SharePoint platform, including specific sites.
However, a new challenge arose when the IT team assigned the “Sites.Selected” permission under Microsoft Graph Sites. By default, this permission does not grant access to any SharePoint site collections unless explicitly configured. With only the “Sites.Selected” permission assigned, the application was denied access to the necessary SharePoint sites.
To ensure access to specific sites within SharePoint, explicit permissions need to be defined for each site. Both the IT team and your team need to collaborate and follow specific steps when setting up permissions for newly created applications.
In this post, I’ll outline these collaborative steps to help ensure full access to SharePoint sites moving forward.
Steps:
1. Azure App Setup (Initial Configuration)
Azure App Creation: The IT team creates the app in Azure AD and shares App name, App(Client ID), Tenant ID and Secrets with you.
Permission Assignment: The app is assigned the “Sites.Selected” permission. This does not automatically grant access to any SharePoint site but enables specific access to be configured later via the Microsoft Graph API.
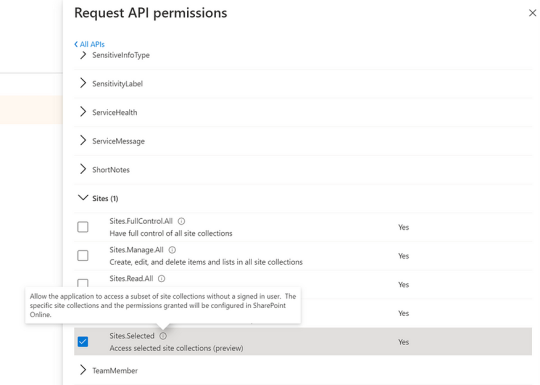
2. App Attempts to Access SharePoint Site
App Request: The app attempts to access a SharePoint site collection (e.g., to read/write data).
Initial Denial: Since the app has only the “Sites.Selected” permission, access is denied to any SharePoint site unless permissions are explicitly granted.
3. Admin Grants Site Permissions (via Microsoft Graph API)
You’ve to make and share an API with IT team which SharePoint admin will call to provide access to a specific site(MSSP) with in the SharePoint.
API Call (POST /permissions): Following API will be called on Graph explorer by SharePoint admin:
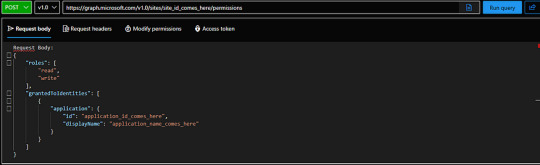
Replace Application ID and display name with the new App data shared by IT team. Get Site ID from IT team if it is handled by IT team, if it is handled by you team you can get it easily by making following API call on Graph Explorer.

Roles & Permissions: The request grants specific roles (e.g., “read” or “write”) for the SharePoint site, defining what actions the app can perform.
4. App Receives Access
Access Granted: Once the API call is successful, the app receives the necessary permissions (e.g write, read) for the specified SharePoint site.

This setup will surely give you required access, you can ask if any assistance is required.
Reference: Microsoft Documentation
0 notes
Text
Cyber Crime
Introduction
Crime and wrongdoing have been connected to people since ancient times. Even as societies develop, crime tries to hide itself. Different countries deal with crime in various ways, depending on their situation. It’s clear that a country with a lot of crime can’t grow or progress because crime goes against development. It has bad effects on society and the economy.
Cybercrime is when people commit crimes on the internet using computers. It’s hard to put crimes into specific groups since new ones come up often. In the real world, crimes like rape, murder, or theft can sometimes overlap. Cybercrimes involve both the computer and the person using it as victims. For example, hacking attacks a computer’s information and resources.
Computer as a Tool
When cybercriminals target individuals, the computer becomes a tool rather than the main goal. These crimes exploit human weaknesses and often cause psychological harm. Legal action against these crimes is challenging due to their intangible nature. Similar crimes have existed offline for centuries, but technology has given criminals new tools to reach more victims and evade capture.
Computer as a Target
Only a particular group of individuals carry out these actions. Unlike crimes where computers are merely tools, these activities demand the technical expertise of those involved. These kinds of crimes are relatively recent, coming into existence as long as computers have been around. This explains the lack of readiness in society and the world at large to combat these offenses. Such occurrences take place on the internet frequently. However, it’s worth noting that Africans and Nigerians, in particular, have not yet developed the technical knowledge required to engage in this type of activity.
Conventional Crime
Crime has been a part of human society for a long time and affects both society and the economy. It’s a term defined by the law and is subject to legal punishment. Crime is essentially a legal wrongdoing that can lead to criminal proceedings and penalties. The key aspect of a crime is that it breaks the criminal law. According to Lord Atkin, the determining factor for whether an act is criminal is whether it’s prohibited with penalties attached. A crime can be seen as any action or lack of action that goes against the law and results in legal penalties.
Cyber Crime
Cybercrime is the newest and most complex issue in the digital world. It can be understood as a type of crime where computers are either used as tools or are the focus of the criminal activity. Any illegal action that involves a computer as a means, target, or tool to commit further crimes falls under the category of cybercrime. A simple definition of cybercrime is “illegal activities where computers are involved as tools, targets, or both.” Computers can be tools in various activities like financial crimes, selling illegal items, pornography, online gambling, intellectual property theft, email deception, forgery, cyberbullying, and cyber harassment. On the other hand, computers can also be the target in cases like unauthorized access, stealing electronic information, email attacks, data manipulation, fraudulent actions, and physical harm to computer systems.
Distinction Between Conventional and Cyber Crime
Distinguishing between conventional and cybercrime might not seem obvious, but a closer look reveals an appreciable difference. The key distinction lies in the use of technology in cybercrime cases. The essential factor for cybercrime is the involvement of the virtual cyber medium at some point. In other words, cybercrime requires the use of digital platforms or the internet in its commission.
2 notes
·
View notes