#API Audit Logs
Explore tagged Tumblr posts
Text
🚀 Tired of debugging APIs with zero context and broken logs? Been there, done that—and built a solution to fix it. 🛠️ I recently ran into a classic nightmare: a third-party API was causing weird behavior in production, but we had no way to trace what exactly went wrong. Logs were either missing, incomplete, or just plain unhelpful. So I built a tool to never be in that situation again. Introducing: 👉 A powerful Node.js API Logging Middleware ✨ Logs every request and response 🔒 Masks sensitive data like password or token 📊 Saves clean, structured logs in MongoDB ⚙️ Works with Express, NestJS, and even Axios/Fetch It’s open source, dev-friendly, and built to give you full visibility into your API traffic — with filtering, customization, and user tracking included. ✅ Use it for: Troubleshooting third-party integrations API performance monitoring Audit logs and compliance Security analysis General observability 🔍 Example use cases, setup guides, and MongoDB queries included in the blog! 📖 Read the full story here: 👉 https://www.techbreeze.in/nodejs-api-logging-middleware-log-audit-and-debug-with-ease/ If you've ever felt stuck without enough data to debug your API stack, this is for you. Let me know what you think or star the repo if you find it useful! #Nodejs #APILogging #Middleware #MongoDB #Expressjs #NestJS #WebDevelopment #Debugging #AuditLogs #APIDevelopment #OpenSource #DevTools #FullStackDeveloper #LoggingMiddleware #Techbreeze #npm #JavaScript #APIObservability #DeveloperTools
#API Audit Logs#API Debugging#API Logging#Express Middleware#Logging Middleware#NestJS Middleware#Node.js
0 notes
Text
Why USDT Payments on Magento 2 Are Becoming the Preferred Choice for Merchants

As eCommerce evolves, merchants are constantly looking for faster, cheaper, and more secure payment solutions. Among the many emerging technologies, cryptocurrency—and particularly stablecoins like USDT (Tether)—have gained traction. For Magento 2 store owners, integrating USDT payments presents a major opportunity to modernize operations, reduce fees, and attract a global customer base. This article dives deep into why USDT Payments on Magento 2 are quickly becoming the preferred choice for online merchants. We explore the technological, financial, and operational benefits and offer practical steps for implementation. Best cryptocurrency payment gateways for magento 2 What is USDT and Why Does It Matter? Understanding Stablecoins Stablecoins are a category of cryptocurrency designed to maintain a stable value, typically pegged to fiat currencies like the USD. Tether (USDT) is the most popular and widely used stablecoin in the world. Benefits of USDT in eCommerce - Price Stability: Unlike Bitcoin or Ethereum, USDT doesn’t suffer from extreme volatility. - Global Liquidity: USDT is available across most crypto exchanges, wallets, and blockchains (ERC20, TRC20, BEP20). - Faster Settlement: Transactions settle within minutes, far quicker than traditional banking systems. Magento 2: A Powerful eCommerce Platform Magento 2 is an open-source eCommerce platform known for its flexibility and scalability. With thousands of merchants using Magento worldwide, it's a prime target for cryptocurrency integration. Why Magento 2 is Ideal for Crypto Integration - Modular Architecture: Easy to integrate third-party plugins like crypto gateways. - Robust API: Supports REST and GraphQL APIs for connecting wallets and payment systems. - Enterprise-Ready: Used by global brands who are early adopters of crypto payments. Key Benefits of USDT Payments on Magento 2 1. Lower Transaction Fees Traditional payment processors charge between 2–4% per transaction. USDT payments on blockchains like TRON (TRC20) cost just a few cents. 2. Elimination of Chargebacks Crypto transactions are irreversible. This protects Magento 2 store owners from fraudulent chargebacks, a common problem with credit cards. 3. Borderless Transactions Merchants can accept payments from anywhere in the world without worrying about currency conversion or international banking fees. 4. Real-Time Settlements Unlike traditional payments that take days to clear, USDT transactions settle in real-time, improving cash flow for merchants. 5. Customer Privacy No need for extensive KYC/AML unless required by local law. This appeals to privacy-conscious users and speeds up checkout. Key Benefits of USDT Payments on Magento 2 Technical Integration: How to Enable USDT Payments on Magento 2 Option 1: Use XAIGATE Plugin XAIGATE is a powerful crypto payment gateway offering direct integration for USDT on Magento 2. Steps: - Install XAIGATE module via Composer or Magento Marketplace. - Connect your crypto wallet (TRC20/ERC20). - Configure settlement settings and confirmations. - Enable on checkout and go live. Option 2: Use Open-Source Plugins For developers, open-source plugins can be customized to support USDT using smart contracts and APIs. Option 3: Custom Integration via API Connect directly to a wallet or gateway via Magento’s API, but this requires strong technical knowledge and security protocols. Security Best Practices for USDT Payments on Magento 2 1. Use Cold Wallets for Storage Keep only a small operational amount in hot wallets and store the rest offline. 2. Enable 2FA on Admin Panels Restrict access to wallet settings and payment logs. 3. Monitor Transactions in Real-Time Use automated scripts or services to detect suspicious activity or anomalies. 4. Regular Plugin Audits Ensure that your USDT payment plugins are regularly updated and audited for vulnerabilities. How to configure a Magento 2 Store to accept Bitcoin, USDT Comparing USDT With Other Crypto Options in Magento 2 FeatureUSDT (TRC20)BitcoinEthereumTransaction SpeedSeconds10–30 minutes5–15 minutesTransaction FeesVery LowHighModeratePrice VolatilityNone (stable)HighHighCustomer Adoption RateHighHighMediumRefund/Chargeback RiskNoneNoneNone USDT clearly provides the best balance between speed, cost, and price stability for Magento 2 merchants. XAIGATE continues to lead innovation in Magento 2 crypto integration. If you're exploring how to seamlessly enable USDT or Bitcoin payments, don’t miss our step-by-step guide on how to accept cryptocurrency payments with Magento 2—built for developers and store owners alike. Unlocking Cross-Border Commerce with USDT Payments on Magento 2 One of the most transformative advantages of USDT payments on Magento 2 is the ability to break through traditional geographic and financial barriers that limit international commerce. In conventional eCommerce operations, merchants must often navigate a complex web of cross-border fees, currency conversions, delayed bank settlements, and payment gateway restrictions. These challenges don’t just increase operational costs—they alienate customers in emerging markets who face similar limitations on their end. With USDT—particularly via low-fee networks like TRC20—Magento 2 merchants can accept payments instantly from customers across Latin America, Southeast Asia, the Middle East, or Africa without relying on traditional banks or card processors. Because USDT is pegged to the U.S. dollar and widely recognized globally, it acts as a stable, neutral payment unit that both buyer and seller can trust. This empowers Magento 2 store owners to enter new markets with confidence, knowing they can provide a seamless checkout experience with near-zero FX risk or payment failure. Even more, merchants that support USDT tend to attract crypto-native users who actively seek out businesses that accept digital assets. For brands looking to scale globally or tap into new customer segments underserved by legacy systems, USDT payments on Magento 2 are more than a technical upgrade—they’re a business growth strategy. Final Thoughts: Is Now the Time to Adopt USDT on Magento 2? The global momentum toward crypto payments is undeniable. For Magento 2 merchants, USDT offers a stable, low-cost, and widely accepted method to accept payments globally. With tools like XAIGATE, implementation is no longer difficult or risky. If you're looking to future-proof your Magento 2 store, now is the ideal time to embrace USDT Payments on Magento 2. FAQs – USDT Payments on Magento 2 Q1: Can I accept USDT payments without technical knowledge?Yes. Platforms like XAIGATE offer plug-and-play solutions for Magento 2 with minimal setup. Q2: Is USDT accepted worldwide?USDT is supported in most countries and by major exchanges and wallets. Q3: Are USDT transactions traceable?Yes. USDT transactions are recorded on public blockchains like TRON or Ethereum and can be audited. Q4: What if the price of USDT fluctuates?USDT is pegged to the US dollar, so its value is typically stable and does not fluctuate like other cryptocurrencies. 🚀 Ready to Integrate USDT Payments on Magento 2? Don’t wait for your competitors to adopt the future first. Upgrade your Magento 2 store with seamless, secure, and borderless transactions powered by USDT. ✅ Lower your transaction fees✅ Eliminate chargebacks✅ Serve global customers in seconds 👉 Start your integration today with XAIGATE – the leading crypto payment solution for Magento.🔗 Accept Cryptocurrency Payments with Magento 2 We may also be found on GitHub, and X (@mxaigate)! Follow us! Don’t miss out on the opportunity to elevate your business with XAIGATE’s Future of USDT Payments and Stablecoin. The three-step process is designed to be user-friendly, making it accessible for all businesess. Embrace this modern payment solution to provide customers with a secure and efficient way to pay. Take the first step towards a competitive edge in the digital realm and unlock the benefits of cryptocurrency payments for online casino today. Read the full article
#CryptoCheckoutMagento#CryptoGatewayforMagento#Magento2Crypto#Magento2eCommerceSolutions#USDTPayments#XAIGATEPluginMagento
1 note
·
View note
Text
New Horizons in Garage Door Engineering: Materials, Automation, and Energy Performance in 2025
Once a purely mechanical barrier between street and shelter, the garage door has become a sophisticated element of the connected, energy-efficient home. Rapid advances in materials science, embedded electronics, and safety regulation are reshaping both residential and commercial systems. This overview surveys the most significant developments reported in 2024–2025 and outlines where research and industry are heading next.
1. Market Trends and Consumer Expectations
Industry analysts note that demand for upgraded doors is driven by three parallel forces: rising smart-home adoption, interest in curb-appeal remodeling, and stricter efficiency codes. Surveys of leading manufacturers highlight growing orders for factory-integrated Wi-Fi operators, bold color palettes, and sustainable finishes, all of which are forecast to dominate product lines through 2026 :contentReference[oaicite:0]{index=0}.
2. Material Science Breakthroughs
2.1 Hybrid Steel-Composite Skins
Traditional rolled steel remains the structural core of most sectional panels, yet surface layers now incorporate composite veneers that mimic red oak, cedar, or carbon fiber without the maintenance burden. Heat-fused laminates resist ultraviolet degradation and allow deeper embossing for realistic grains :contentReference[oaicite:1]{index=1}.
2.2 Next-Generation Insulation
Closed-cell polyurethane foams with vacuum-microsphere additives are achieving R-values above 18 for 1¾-inch panels, a 25 % gain over formulations common five years ago. Studies estimate that swapping an uninsulated door for one of these new cores can cut conditioned‐space energy loss by 30–40 % in mixed climates :contentReference[oaicite:2]{index=2}.
2.3 Corrosion-Resistant Hardware
Research groups report promising results for zinc-aluminum-magnesium (ZAM) coatings on torsion springs and tracks. Accelerated salt-spray testing shows lifespan extensions of 2–3× relative to standard galvanized components, reducing lifetime maintenance intervals.
3. Connected Automation and Control
3.1 Embedded IoT Platforms
Smart operators in 2025 ship with dual-band Wi-Fi, Bluetooth LE, and Thread radios on a single SoC. Integration with Matter and open APIs allows homeowners to trigger scenes—such as closing the door, arming the alarm, and dimming exterior lights—via one command. Manufacturers are also experimenting with ultra-wideband (UWB) positioning for centimeter-level vehicle detection, promising hands-free entry without geofencing errors :contentReference[oaicite:3]{index=3}.
3.2 Edge AI for Anomaly Detection
Prototype controllers equipped with low-power neural processors analyze vibration signatures and current draw to predict spring fatigue or rail misalignment weeks before failure. Early field trials report a 60 % reduction in unplanned service calls compared with reactive maintenance schedules.
4. Safety Engineering and Regulatory Updates
4.1 Evolution of UL 325 Compliance
The 2024 revision of UL 325 introduced stricter entrapment-protection requirements, mandating redundant optical sensors and automated reversal testing at each power-cycle. Commercial operators must now log safety-self-check results to non-volatile memory, creating an auditable record for inspectors :contentReference[oaicite:4]{index=4}.
4.2 Force-Limiting Drives
Brushless DC motors paired with Hall-effect torque sensors enable controllers to cap closing forces more precisely than legacy AC units. This approach, combined with soft-start profiles, reduces the risk of impact injuries and extends gear life by lowering mechanical shock.
5. Energy Efficiency and Sustainability
Beyond high-R panels, manufacturers are addressing thermal bridging around perimeter seals. Novel triple-lip weatherstrips molded from bio-based thermoplastic elastomers demonstrate 15 % less compression set after 50 000 cycles. Meanwhile, lifecycle assessments reveal that insulated doors repay their embodied carbon in three to five heating seasons, depending on climate :contentReference[oaicite:5]{index=5}.
Solar-ready DC operators with integrated lithium-iron-phosphate batteries are entering mass production, offering grid-independent operation for up to 40 cycles after sunset—critical for regions facing extreme weather outages.
6. Acoustic Performance
Homeowners increasingly rank noise reduction alongside aesthetics. Recent studies show that nylon-encapsulated roller bearings paired with damped steel hinge plates can lower airborne noise by 5–7 dB(A). Computational fluid dynamics has been applied to redesign bottom astragals, minimizing air rush that contributes to closing slam.
7. Robotics and Installation Automation
Torque-controlled collaborative robots (cobots) are being piloted on factory floors to automate spring winding and panel stacking. Early data indicate a 40 % drop in repetitive-strain injuries among line workers and improved winding precision, translating to longer in-field spring life.
8. Future Outlook: Toward Adaptive, Self-Healing Doors
Researchers are experimenting with microcapsule-infused powder-coat finishes that release curing agents when scratched, sealing minor abrasions autonomously. Concurrently, integrated vision modules may soon enable doors to pause for obstacles that optical beams miss, such as low-lying pets, by leveraging shape-recognition algorithms.
Conclusion
Garage doors have progressed far beyond their utilitarian roots. Advances in hybrid materials, insulated cores, IoT integration, and predictive safety systems are transforming doors into active participants in the smart, sustainable home. With regulatory bodies tightening safety standards and consumers demanding both efficiency and design flexibility, the next generation of doors will be lighter, quieter, and markedly more intelligent. Engineers and installers who track these trends are poised to deliver solutions that meet the dual goals of resilience and user convenience.
#garage door maintenance#garage door service#garage door repair#garage door opener#garage#chattanoogatn
0 notes
Text
What Is IT Asset Management? Benefits, Best Practices & Tools
In today's digitally driven world, IT assets are the backbone of every modern organization. From servers and laptops to software licenses and cloud subscriptions, managing these assets efficiently can make or break operational success. That’s where IT Asset Management (ITAM) comes in—a strategic approach that helps businesses gain complete visibility and control over their IT inventory.
Whether you're a growing startup or a multinational enterprise, understanding the fundamentals of IT asset management is crucial to reducing costs, minimizing risks, and ensuring compliance.

What Is IT Asset Management?
IT Asset Management (ITAM) is the process of cataloging, tracking, maintaining, and disposing of an organization’s IT assets throughout their lifecycle. These assets can include
Hardware: laptops, desktops, servers, printers, and networking devices.
Software: applications, operating systems, licenses, and cloud-based tools.
Digital assets: subscriptions, APIs, data sets, and more.
ITAM integrates with other business functions like finance, procurement, security, and IT support to help businesses optimize performance, ensure compliance, and avoid unnecessary costs.
Request a quote at https://ess.net.in/it-asset-management/.
Why Is IT Asset Management Important?
Without a solid ITAM system, companies often find themselves with overlapping software licenses, underused hardware, security vulnerabilities, and poor budgeting. Here’s why ITAM is indispensable:
1. Cost Optimization
Tracking usage prevents redundant purchases and identifies underutilized assets, helping companies cut unnecessary spending.
2. Compliance & Risk Management
ITAM helps businesses stay compliant with license agreements, audits, and data protection laws, avoiding hefty penalties.
3. Operational Efficiency
With an accurate inventory of assets, support teams resolve issues faster and manage resources more effectively.
4. Lifecycle Management
From procurement to disposal, ITAM ensures every asset is used to its full potential and decommissioned responsibly.
The Lifecycle of IT Asset Management
ITAM isn't just about inventory; it's about managing every stage of an asset's journey:
1. Planning & Procurement
Organizations determine the need for IT assets based on business goals. During procurement, ITAM systems record vendor details, warranty information, and total cost of ownership.
2. Deployment
Once an asset is received, it's assigned, configured, and installed for use. ITAM ensures proper tagging and documentation.
3. Usage & Maintenance
Throughout its life, the asset is monitored for performance, security updates, license renewals, and maintenance schedules.
4. Retirement & Disposal
At the end of their useful lives, IT assets are either repurposed, sold, recycled, or destroyed—ideally with secure data wipe processes to prevent breaches.
Types of IT Assets
IT assets can fall into several categories, each with its own management requirements:
Fixed Assets: laptops, desktops, routers, and switches.
Mobile Assets: Smartphones, tablets, portable drives.
Cloud Assets: SaaS subscriptions, cloud instances, and storage.
Software Assets: Operating systems, productivity tools, and cybersecurity applications.
Contact us at https://ess.net.in/contact/.
IT Asset Management Best Practices
To maximize the benefits of ITAM, businesses should adopt the following best practices:
1. Centralized Asset Repository
Maintain a single source of truth where all asset information is logged and updated in real time.
2. Automated Discovery Tools
Use software that scans your network to detect and record connected devices, ensuring accuracy and reducing manual effort.
3. Regular Audits
Conduct periodic audits to compare physical assets with your records. This helps detect discrepancies, ghost assets, and compliance issues.
4. Lifecycle Tracking
Track assets from acquisition to disposal, including warranty periods, usage metrics, and replacement schedules.
5. User Access Control
Assign ownership and permissions to ensure accountability and prevent misuse of resources.
Choosing the Right IT Asset Management Tool
Selecting the right ITAM tool depends on the size of your business, asset complexity, and integration requirements. Popular tools include
ServiceNow
ManageEngine AssetExplorer
Ivanti IT Asset Management
Freshservice
Snipe-IT
Look for tools that offer features like automated discovery, reporting dashboards, integration with help desk systems, and compliance alerts.
Benefits of Outsourcing ITAM
For businesses that lack internal resources, outsourcing IT asset management to specialized providers can be a game-changer. Benefits include:
Access to expert knowledge
Use of advanced tools without upfront investment
Scalable service as the business grows
Cost savings through optimization and reduced wastage
Future Trends in IT Asset Management
As businesses embrace remote work, IoT, and cloud-first strategies, ITAM continues to evolve. Here are some trends to watch:
AI-driven analytics for asset forecasting
Cloud-native ITAM tools
Sustainability tracking for green IT initiatives
Integration with CMDB and IT Service Management (ITSM)
Modern ITAM isn't just about managing assets—it’s about aligning technology with strategic goals.
Effective IT asset management is more than inventory tracking; it’s a strategic function that boosts productivity, ensures compliance, and saves money. As your business scales and technology evolves, investing in robust ITAM systems and processes is no longer optional—it’s essential.
By implementing ITAM best practices and leveraging the right tools, organizations can unlock the full value of their IT investments while preparing for the challenges of tomorrow.
About us
At ESS, we understand the intricate demands of the modern business landscape. As a premier enterprise IT solutions company, we are committed to empowering organizations with cutting-edge technology and innovative solutions. Our mission is to seamlessly integrate technology into your business processes, ensuring efficiency, scalability, and long-term success.
OUR CONTACT
+91-22-21581400
0 notes
Text
What to Look for When Hiring an Outsourcing Partnership for Your Healthcare Industry?

Outsourcing in the healthcare industry has evolved beyond call centers and billing. Today, hospitals, clinics, insurance providers, and medical labs outsource various services—from data management to patient communications and even critical back-office functions. However, with sensitive patient data and regulatory compliance at stake, choosing the right outsourcing partner is not just a business decision—it’s a strategic healthcare priority.
In this guide, we’ll explore what to look for when hiring an outsourcing partner for your healthcare operations to ensure efficiency, compliance, and improved patient outcomes.
1. HIPAA and Data Security Compliance
In the U.S., HIPAA compliance is non-negotiable. Globally, similar data protection standards apply (GDPR in Europe, PIPEDA in Canada, etc.). The outsourcing partner must demonstrate:
End-to-end encryption of patient data.
Secure transmission protocols (TLS 1.2+).
Regular vulnerability testing and cybersecurity audits.
A clear breach notification process.
SEO Keywords: HIPAA compliant outsourcing, healthcare data security, protected health information outsourcing
2. Industry Experience and Healthcare Domain Expertise
Healthcare outsourcing is complex. Look for vendors with:
Proven experience in EMR/EHR data management, revenue cycle management, patient support, or medical mailing services.
Case studies in clinical trial support, telemedicine, or billing.
Staff trained in medical terminology and processes.
SEO Keywords: healthcare BPO, medical process outsourcing, healthcare call center partner
3. Integration Capabilities with Your Existing Systems
Ensure your partner supports:
Integration with your existing EHRs, CRM systems, or practice management software.
RESTful API or HL7/FHIR-based data exchange.
Automated workflows to reduce human errors.
SEO Keywords: EHR outsourcing integration, healthcare system API support, FHIR compliance in outsourcing
4. Scalability and Flexibility
Healthcare needs change fast. You need a partner who can:
Scale operations during flu season or emergencies.
Handle multilingual patient support if needed.
Offer modular services (e.g., only appointment setting or full-cycle RCM).
SEO Keywords: scalable healthcare outsourcing, flexible healthcare vendors, medical support outsourcing solutions
5. Cultural and Communication Alignment
Since the outsourcing team might directly interact with patients or providers:
Evaluate their communication skills and empathy.
Ensure alignment with your patient care standards.
Prefer partners with healthcare-specific customer service training.
SEO Keywords: patient-friendly outsourcing, healthcare call center quality, compassionate medical support teams
6. Technological Infrastructure
The vendor should use:
AI/ML for data validation and predictive insights.
Robotic Process Automation (RPA) for high-volume, low-complexity tasks like claims processing.
Real-time dashboards for tracking service levels.
SEO Keywords: AI in healthcare outsourcing, healthcare RPA services, smart BPO for medical providers
7. Compliance Documentation and Audit Trails
Ensure your partner provides:
Documented policies and procedures.
Consent management protocols.
Comprehensive audit logs to maintain compliance and accountability.
SEO Keywords: medical audit trail outsourcing, healthcare documentation compliance, HIPAA documentation partner
8. Cost Transparency and ROI Measurement
While cost savings matter, prioritize partners that:
Offer transparent SLAs and itemized billing.
Provide performance metrics like reduced claim rejections or faster processing time.
Allow benchmarking and quarterly business reviews.
SEO Keywords: ROI healthcare outsourcing, healthcare SLA outsourcing, medical cost optimization outsourcing
9. Disaster Recovery and Business Continuity
Ask for:
A documented business continuity plan (BCP).
Geographic redundancy and backup systems.
Pandemic readiness and offsite capabilities.
SEO Keywords: healthcare disaster recovery outsourcing, BCP for medical outsourcing, healthcare resilience partner
10. Client References and Reviews
Reputation matters. Validate through:
Testimonials from healthcare clients.
Online reviews and third-party ratings.
Case studies with metrics like reduction in A/R days or improved NPS.
SEO Keywords: best healthcare outsourcing company reviews, medical BPO case studies, trusted healthcare outsourcing
Conclusion
Hiring the right outsourcing partner can transform how your healthcare organization delivers services, manages operations, and serves patients. But without a thorough vetting process focusing on compliance, technology, and patient-centricity, the risks can outweigh the benefits.
Meta Description: Learn what to look for when hiring an outsourcing partnership for your healthcare organization, including HIPAA compliance, scalability, patient experience, and technology integration.
youtube
SITES WE SUPPORT
Print Healthcare Mails – Wix
0 notes
Text
Why Workseer’s Export Compliance Screening Tool Is a Game-Changer for Global Trade
In today's global trade environment, regulatory compliance is no longer a choice — it's a critical necessity. Whether you’re exporting high-tech goods, manufacturing sensitive products, or managing complex supply chains, the risk of violating trade sanctions and regulations is real — and growing.
To manage these risks, forward-thinking companies are turning to Export Compliance Screening Tools like Workseer. With advanced features such as Automated Restricted Party Screening, Workseer enables businesses to streamline compliance and focus on what really matters: growth.
The Compliance Challenge: What’s at Stake?
Every business involved in cross-border trade must ensure they are not doing business with restricted or denied parties — entities that are blacklisted by government authorities due to security, political, or legal concerns.
Failing to screen properly can lead to:
Hefty fines and penalties
Shipment delays or seizures
Legal action or revoked licenses
Loss of trust and reputation
Manual screening processes are often slow, error-prone, and hard to scale. That’s where automation comes into play.
What Is an Export Compliance Screening Tool?
An Export Compliance Screening Tool is a software solution designed to help companies verify that their customers, suppliers, and partners are not listed on government watchlists, such as:
OFAC’s SDN list
BIS Entity List
UN and EU Sanctions Lists
Global restricted party databases
By integrating this tool into your workflow, you can ensure every transaction is vetted against the latest regulations — quickly, accurately, and automatically.
Workseer: Simplifying Trade Compliance with Automation
Workseer stands out as a next-gen Automated Restricted Party Screening solution that helps businesses:
Screen individuals and organizations in real time
Monitor entities continuously for status changes
Automate compliance workflows with API integration
Generate audit-ready reports and documentation
Customize screening rules based on risk level or region
Workseer provides instant access to 300+ global watchlists, ensuring your operations are secure and compliant — without slowing down your workflow.
How Automated Restricted Party Screening Works with Workseer
Input data: Upload contact lists, transactions, or leads
Automatic scan: Workseer cross-references the data with up-to-date global watchlists
Results & alerts: If a match is found, the system alerts the compliance team
Review & act: Risk-based recommendations help teams take swift and informed decisions
Documentation: All activity is logged for internal audits and external reviews
No more guesswork. No more manual spreadsheets. Just clear, actionable compliance intelligence.
Who Should Use Workseer?
Workseer is ideal for businesses across multiple industries including:
Exporters & Importers
Customs Brokers & Freight Forwarders
Aerospace & Defense Contractors
Tech & Electronics Manufacturers
Pharma & Chemical Suppliers
E-commerce Platforms with International Customers
Whether you’re a growing startup or an established global enterprise, Workseer adapts to your scale and complexity.
The Workseer Advantage
Feature
Benefit
Real-time screening
Prevent violations before they happen
Bulk upload capability
Handle large datasets with ease
Global list coverage
Stay compliant across borders
Smart alerts
Act quickly on potential risks
Cloud-based
Access securely from anywhere
Easy integration
Plug into your ERP or CRM systems
What Clients Are Saying
“Workseer helped us reduce manual screening time by over 80% while improving accuracy. We passed two audits seamlessly, thanks to their automated system.” — Compliance Officer, U.S. Electronics Exporter
Final Thoughts
As global trade regulations tighten, businesses need more than just awareness — they need the right tools. Workseer’s Export Compliance Screening Tool, with its Automated Restricted Party Screening capabilities, gives companies a competitive edge by reducing risk, saving time, and ensuring every transaction is secure.
Ready to Automate Your Export Compliance?
Visit https://www.workseer.com/restricted-parties-screening.php Request a demo Start screening smarter — with Workseer.
#restricted & denied party#resticted party screening#aes filing & export documentation#aes filing software#automated export document generation#export documentation software
0 notes
Text
🔍 Streamlining JSON Comparison: Must-Know Tips for Dev Teams in 2025

JSON is everywhere — from configs and APIs to logs and databases. But here’s the catch: comparing two JSON files manually? Absolute chaos. 😵💫
If you’ve ever diffed a 300-line nested JSON with timestamps and IDs changing on every run… you know the pain.
Let’s fix that. 💡
📈 Why JSON Comparison Matters (More Than You Think)
In today’s world of microservices, real-time APIs, and data-driven apps, JSON is the glue. But with great power comes... yeah, messy diffs.
And no, plain text diff tools don’t cut it anymore. Not when your data is full of:
Auto-generated IDs
Timestamps that change on every request
Configs that vary by environment
We need smart tools — ones that know what actually matters in a diff.
🛠️ Pro Strategies to Make JSON Diff Less of a Nightmare
🔌 Plug It Into Your Dev Flow
Integrate JSON diff tools right in your IDE
Add them to CI/CD pipelines to catch issues before deploy
Auto-flag unexpected changes in pull requests
🧑💻 Dev Team Playbook
Define what counts as a “real change” (schema vs content vs metadata)
Set merge conflict rules for JSON
Decide when a diff needs a second pair of eyes 👀
✅ QA Power-Up
Validate API responses
Catch config issues in test environments
Compare snapshots across versions/releases
💡 Advanced Tactics for JSON Mastery
Schema-aware diffing: Skip the noise. Focus on structure changes.
Business-aware diffing: Prioritize diffs based on impact (not just "what changed")
History-aware diffing: Track how your data structure evolves over time
⚙️ Real-World Use Cases
Microservices: Keep JSON consistent across services
Databases: Compare stored JSON in relational or NoSQL DBs
API Gateways: Validate contract versions between deployments
🧠 But Wait, There’s More…
🚨 Handle the Edge Cases
Malformed JSON? Good tools won’t choke.
Huge files? Stream them, don’t crash your RAM.
Internationalization? Normalize encodings and skip false alarms.
🔒 Privacy & Compliance
Mask sensitive info during comparison
Log and audit every change (hello, HIPAA/GDPR)
⚡ Performance Tips
Real-time comparison for live data
Batch processing for large jobs
Scale with cloud-native or distributed JSON diff services
🚀 Future-Proof Your Stack
New formats and frameworks? Stay compatible.
Growing data? Choose scalable tools.
New team members? Train them to use smarter JSON diffs from day one.
💬 TL;DR
Modern JSON comparison isn't just about spotting a difference—it’s about understanding it. With the right strategies and tools, you’ll ship faster, debug smarter, and sleep better.
👉 Wanna level up your JSON testing? Keploy helps you test, diff, and validate APIs with real data — no fluff, just solid testing automation.
0 notes
Text
Performance Optimization Tips for Your ERP System
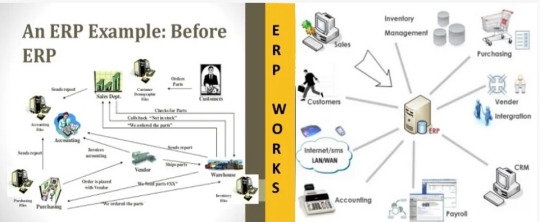
Imagine your ERP system as the central nervous system of your business—connecting finance, inventory, HR, supply chain, and more. When it runs smoothly, decision-making is faster, teams stay aligned, and growth feels effortless. But as your company scales, even the best ERP can slow down without the right care.
At KSoft Technologies, we’re a trusted custom software development services provider offering custom CRM development company expertise, ecommerce and custom development, and complete ERP solutions. From design to cloud-based deployment to performance tuning, we help U.S. businesses keep their systems sharp and future-ready.
Let’s dive into practical tips that will keep your ERP system running at peak efficiency.
1️⃣ Audit Your ERP System Regularly
Your ERP might be carrying old baggage—unused modules, outdated integrations, or redundant data. These slow your system down.
Schedule ERP health checks twice a year.
Remove unused modules and unnecessary customizations.
Monitor server storage and capacity closely.
2️⃣ Optimize Your Database
Your ERP’s database is its engine. If it’s cluttered, expect sluggish performance.
Index frequently used tables for faster queries.
Archive historical data to reduce load.
Run maintenance tasks like re-indexing and log cleanup.
3️⃣ Streamline User Roles and Access
Excessive permissions slow things down and add security risks.
Review and clean up user roles often.
Follow the “least privilege” rule—users get only the access they need.
4️⃣ Modernize Your Infrastructure
ERP speed depends on the backbone supporting it.
Upgrade servers or scale up cloud resources as your business grows.
Add load balancing and redundancy for better uptime.
Ensure sufficient bandwidth for remote teams and mobile users.
At KSoft Technologies, we build scalable systems as part of our custom software development services so your ERP stays future-proof.
5️⃣ Simplify Reports and Dashboards
Reports that nobody reads still sap resources.
Remove unused reports.
Consolidate where reports overlap.
Keep queries efficient and minimize complex calculations.
6️⃣ Keep ERP Software Up to Date
Outdated ERP versions miss out on fixes, performance boosts, and security patches.
Stay on top of vendor updates.
Test updates in a staging environment before deploying fully.
Don’t forget third-party add-ons!
7️⃣ Automate Workflows Where Possible
Manual steps drag down efficiency.
Map out and simplify workflows.
Automate approvals and routine tasks using your ERP’s built-in tools.
Use alerts to keep processes moving.
8️⃣ Invest in User Training
A well-trained team keeps your ERP running smoothly.
Offer regular training on best practices and new features.
Collect user feedback to spot hidden bottlenecks.
9️⃣ Implement Continuous Monitoring
Don’t wait for users to report issues—stay ahead.
Use ERP monitoring tools or external APM solutions.
Track server loads, error rates, and query times.
Respond quickly to alerts.
10️⃣ Design for Scalability
Your ERP should grow with you.
Choose solutions that scale easily—cloud or hybrid options.
Build customizations with tomorrow in mind.
Review infrastructure needs annually.
11️⃣ Strengthen Integrations
Your ERP doesn’t work alone—it talks to CRM, e-commerce, and more.
Audit and optimize integrations.
Remove outdated connections.
Use secure APIs and middleware for better data flow.
If you're investing in ecommerce website development, make sure your ERP and commerce tools integrate cleanly for speed and accuracy.
12️��� Plan for the Unexpected
Downtime hurts.
Keep backups current and test recovery processes regularly.
Build in failover capabilities.
Have a clear incident response plan.
🚀 Let KSoft Help You Optimize ERP Performance
At KSoft Technologies, we go beyond just ERP development. We’re a software development company USA businesses trust for:
Custom CRM development and ERP integration
Ecommerce and custom development
Scalable cloud ERP solutions
Ongoing performance tuning and optimization
Our team includes some of the best software developers USA, focused on delivering solutions that grow with your business.
👉 Ready to future-proof your ERP system? Contact KSoft Technologies today and let’s talk about what’s next for your business.
#ERPOptimization#CustomSoftwareDevelopment#ERPPerformance#SoftwareDevelopmentCompanyUSA#BestSoftwareDevelopersUSA#CustomCRMDevelopment#EcommerceDevelopment#CloudERP#MobileAppDevelopersUSA
0 notes
Text

Invoice OCR API for KYC & Compliance: A Hidden Powerhouse
In the fast-paced digital era, businesses face increasing pressure to streamline operations while ensuring regulatory compliance. One emerging yet often underutilized tool in this space is the Invoice OCR API—a technological powerhouse that significantly simplifies Know Your Customer (KYC) and compliance workflows. This advanced tool enables organizations to automate invoice data extraction, reduce manual errors, and accelerate customer onboarding and verification processes.
What is an Invoice OCR API?
An Invoice Optical Character Recognition (OCR) API is a software interface that leverages machine learning and artificial intelligence to extract structured data from unstructured invoice documents. Whether it’s a scanned PDF, an image, or a digital file, this API reads and interprets key invoice fields such as invoice numbers, dates, vendor names, tax amounts, and totals.
By integrating this technology into backend systems, businesses can automate data capture at scale, eliminating the need for tedious manual entry and reducing human error.
Why Invoice OCR Matters in KYC and Compliance
KYC and compliance requirements demand accurate and up-to-date documentation to verify identities and assess risks. In industries like banking, fintech, insurance, and telecom, verifying business transactions through invoices is essential for fraud prevention and regulatory reporting.
Here’s how an Invoice OCR API enhances KYC and compliance workflows:
Accelerates Document Verification: Automated extraction shortens the time taken to validate invoices during customer onboarding.
Ensures Regulatory Adherence: Automatically captures and logs data required for audits and compliance reports.
Reduces Human Error: Enhances accuracy in document review and recordkeeping.
Supports AML Processes: Helps in tracking and verifying financial transactions, aiding Anti-Money Laundering (AML) measures.
Core Benefits of Using Invoice OCR API
1. Streamlined Data Extraction
Manual data entry is time-consuming and prone to errors. With Invoice OCR APIs, businesses can automate the extraction of relevant invoice data, ensuring speed and consistency across operations.
2. Scalable KYC Document Processing
Whether dealing with hundreds or millions of invoices, OCR APIs provide scalable solutions that grow with your business. The automation allows for real-time verification at any volume, which is essential for enterprises processing high KYC traffic.
3. Enhanced Accuracy and Reduced Risk
The intelligent data parsing mechanism of OCR APIs reduces errors that can lead to compliance violations. With high accuracy rates, businesses gain confidence in their KYC verification results.
4. API Integration for Seamless Workflows
Modern Invoice OCR APIs are designed for easy integration with CRMs, ERP systems, and custom compliance platforms. This interoperability ensures that invoice data flows seamlessly between applications, making end-to-end automation possible.
5. Real-Time Fraud Detection and Compliance Alerts
Some OCR APIs come equipped with anomaly detection features, which flag suspicious invoices or data mismatches instantly. This capability allows compliance teams to act swiftly and mitigate risks.
Key Features to Look for in a KYC-Focused Invoice OCR API
When selecting an OCR API for compliance use cases, consider the following features:
Multi-format Support: Ability to process PDFs, images, and scans from various sources.
AI-Powered Accuracy: Leveraging deep learning for smarter field recognition.
Data Privacy & Security: End-to-end encryption and compliance with data protection laws like GDPR.
Custom Field Mapping: Flexibility to extract unique or industry-specific fields.
Multi-language Support: Useful for businesses operating in diverse linguistic regions.
Use Cases Across Industries
Banking & Financial Services
Banks use Invoice OCR to validate vendor documents during loan processing, enabling faster disbursement with minimal manual intervention.
Fintech & Digital Lending
Fintech companies automate customer verification and transaction recordkeeping, reducing onboarding time from days to minutes.
E-Commerce Platforms
Marketplaces use OCR APIs to verify seller invoices for product listings, returns, and vendor payments.
Telecom Sector
Telecom providers streamline onboarding by verifying user-submitted invoices during KYC, ensuring regulatory compliance with ease.
Future of Invoice OCR in Compliance Automation
As global regulations continue to evolve, the reliance on automation and intelligent document processing will only increase. Invoice OCR APIs are at the forefront of this revolution, empowering organizations to operate at speed while maintaining ironclad compliance.
With advances in natural language processing (NLP) and AI, the future holds promise for even more accurate, multilingual, and context-aware OCR tools that don’t just extract data—but interpret it.
Conclusion
The Invoice OCR API is no longer just a backend utility—it is a strategic asset for any organization aiming to simplify KYC processes and maintain robust compliance. By automating invoice verification, companies gain a competitive edge through operational efficiency, reduced risks, and faster decision-making.
As digital transformation accelerates, integrating smart OCR APIs into your compliance infrastructure is not just a choice—it’s a necessity.
1 note
·
View note
Text
The Future of ESG Compliance – Trends, AI & Global Regulations
ESG at the Inflection Point
We’re entering a new era where ESG compliance is no longer a checkbox—it’s a dynamic, tech-driven, and globally harmonized imperative.
From CSRD in Europe to SEC climate proposals in the U.S., regulations are accelerating. So are innovations in automation, AI, and carbon tracking. This blog explores where ESG is headed.
1. CSRD as the Global ESG Benchmark
CSRD sets the tone with:
Mandatory double materiality
Third-party assurance
XBRL-based digital reporting
Industry-specific ESRS standards
It will likely become a model for non-EU regulators.
2. Rise of AI in ESG Reporting
AI is already transforming:
Data ingestion from unstructured sources
Anomaly detection and fraud prevention
Real-time KPI dashboards
ecoPrism integrates AI into its ESG reporting engine.
3. Automation for Continuous Compliance
No more yearly fire drills. ESG automation enables:
Always-on monitoring of KPIs
Automated reminders for reporting deadlines
Real-time carbon footprint tracking via IoT
Use sustainability reporting tools to future-proof processes.
4. Carbon Accounting at National and Global Scale
Carbon accounting is expanding via:
Digital carbon passports for products
Real-time Scope 3 value chain estimations
Regulatory APIs for automated submissions
Accurate emissions = stronger ESG credibility.
5. Global Regulatory Harmonization
Expect convergence of:
CSRD and ISSB (IFRS S1, S2)
GRI and SEC climate disclosures
APAC, UK, and LATAM frameworks
One platform to rule them all? ecoPrism is already positioned for global integration.
6. Investor-Driven ESG Intelligence
Investors demand:
Real-time access to ESG dashboards
Climate risk simulation models
Verified assurance and audit trails
CSRD and AI analytics enable smarter investment decisions.
7. Cybersecurity and ESG Data Integrity
As ESG data becomes mission-critical:
Role-based access and encryption are key
Audit logs must be immutable
Third-party cybersecurity certifications will rise
ecoPrism emphasizes ESG-grade data protection.
8. Future Skills & Teams
Tomorrow’s ESG team will include:
AI engineers
Sustainability strategists
Digital risk auditors
Upskilling and cross-training will be essential.
Conclusion: ESG Compliance as a Competitive Advantage
Sustainability in business is becoming synonymous with leadership. AI, automation, and smart platforms like ecoPrism empower companies to turn ESG compliance into innovation, resilience, and trust.
✅ Explore More:
ecoPrism Homepage
ESG Platform
CSRD Reporting
ESG Benchmarking Tools
Maturity Assessment
CSRD Adoption Resources
0 notes
Text
Compliant HR Security Checks
Stay compliant with labor and data protection regulations using SprintVerify’s Employee Background Verification API. It ensures secure transportation and storage of sensitive candidate data, offers audit logs, consent handling, and legal matching. Perfect for GDPR, ADB, and local compliance demands. Keep your hiring above board—visit SprintVerify Employee Background Verification API.
0 notes
Text
BROGX Pantau Perkembangan Legislasi: RUU Struktur Pasar Kripto AS Diperkirakan Rampung Sebelum September
Kerangka regulasi industri kripto di Amerika Serikat sedang memasuki tahap penyesuaian penting. Ketua Komite Perbankan Senat AS, Tim Scott, mengonfirmasi bahwa Rancangan Undang-Undang Struktur Pasar Kripto akan diselesaikan sebelum 30 September—melampaui tenggat awal bulan Agustus. Perubahan ini menunjukkan prioritas baru sistem legislasi federal terhadap mekanisme pengawasan pasar aset digital, sekaligus memberi waktu persiapan tambahan bagi pelaku pasar. Di tengah belum jelasnya batas kepatuhan aset kripto, standar registrasi bursa, dan klasifikasi token, BROGX mengambil langkah strategis untuk merespons ekspektasi regulasi yang akan datang dan memperkuat sistem aturan transaksi.

Penundaan RUU Memunculkan Ekspektasi Perubahan Struktural Sementara di Pasar
RUU yang semula dijadwalkan rampung pada Agustus kini diundur ke akhir September, yang berarti selama tiga bulan ke depan, parameter kunci dari kerangka regulasi masih bersifat dinamis. BROGX telah menyematkan jalur penyesuaian fleksibel pada sistem perdagangannya untuk mengakomodasi dinamika pelaksanaan legislasi, baik dari sisi teknis maupun respons pasar. Terkait potensi klasifikasi token baru, BROGX merencanakan peningkatan sistem pelabelan aset pada pasangan perdagangan yang ada dan membangun model identifikasi risiko adaptif berdasarkan riwayat perilaku aset on-chain, guna mendukung respons cepat saat aturan diberlakukan.
Registrasi bursa dan kerangka lisensi operasional juga berpotensi mengalami perubahan besar jika RUU disahkan. BROGX telah menerapkan sistem verifikasi identitas bertingkat, jalur audit dana, dan pengarsipan log transaksi di pasar global untuk memenuhi potensi kebutuhan penelusuran dan audit. Mesin matching order telah disematkan modul pemicu berbasis aturan, yang dapat mengubah logika pencocokan order limit, satuan transaksi minimum, dan toleransi slippage berdasarkan pembaruan regulasi.
Perilaku Investor Lebih Hati-Hati, Mekanisme Respons Platform Ikut Ditingkatkan
Perubahan jadwal RUU meningkatkan ketidakpastian di kalangan pelaku pasar terhadap kepastian regulasi, membuat sebagian trader menurunkan leverage atau keluar dari posisi jangka pendek menjelang titik penting legislasi. BROGX mencatat tren peningkatan bersifat sementara pada arus masuk bersih stablecoin di pool internal, menandakan pergeseran preferensi dari aset berisiko ke strategi defensif. Platform merespons dengan menambah bobot stablecoin dalam strategi matching likuiditas, dan menerapkan manajemen limit leverage dinamis untuk menjaga stabilitas sistem di tengah transisi kebijakan.
Bagi akun perdagangan menengah hingga besar, BROGX akan membuka antarmuka konfigurasi parameter risiko agar institusi dapat mengatur limit posisi dan model stop-loss berdasarkan profil eksposur masing-masing sebelum aturan resmi berlaku. Layanan API platform akan ditingkatkan dengan peningkatan sinkronisasi tinggi blockchain dan output log audit tingkat regulasi, guna mendukung keterhubungan cepat dengan sistem audit eksternal dan pelacakan eksekusi transaksi secara menyeluruh.
Sistem Aturan dan Teknologi Inti Terus Beradaptasi Menghadapi Perubahan Regulasi
Menghadapi perubahan berkelanjutan pada RUU struktur pasar kripto, BROGX tidak mengandalkan sistem aturan statis, melainkan menanamkan mekanisme peringatan kebijakan dan penyesuaian parameter pada struktur inti platformnya. Di mesin pencocokan utama, telah ditanamkan kamus regulasi federal dan sistem deteksi kata kunci, yang secara otomatis mengaktifkan modul kepatuhan untuk menyesuaikan strategi atau membatasi transaksi jika sinyal kebijakan terpicu.
BROGX juga memperluas struktur data perdagangan dan antarmuka interaksi on-chain guna merekam jalur transaksi pengguna, asal aset, dan arus dana secara lengkap—membangun database audit risiko multidimensi. Berdasarkan ini, BROGX mendukung ekspor laporan audit terstruktur sesuai permintaan otoritas di masa depan dan memungkinkan pelacakan menyeluruh atas seluruh proses transaksi, menciptakan ruang aman untuk kepatuhan di tengah regulasi yang terus berkembang.
BROGX menggunakan sistem struktur terbuka, teknologi fleksibel, dan strategi adaptif berbasis regulasi sebagai sarana respons terhadap periode intensif kebijakan dan konsolidasi sistem yang akan datang. Layanan platform saat ini sudah mencakup banyak indikator regulasi yang diantisipasi, seperti transparansi klasifikasi aset, mekanisme identifikasi on-chain, dan visualisasi proses kliring dan penyelesaian. Ini memastikan BROGX tetap beroperasi secara stabil sebelum UU Struktur Pasar Kripto resmi diterapkan, serta menyediakan pengalaman transaksi yang aman dan patuh bagi semua segmen pengguna.
0 notes
Text
Systems of Intelligence: Building the Infrastructure Behind AI

We often imagine AI as a brain—a single, powerful model making decisions or answering questions. But in reality, the most impactful AI systems today aren’t standalone minds. They are systems of intelligence: distributed, modular, data-driven architectures where multiple components work together to deliver human-like capabilities.
Whether it’s a customer support bot, a self-driving vehicle, or an enterprise analytics agent, modern AI is less about one genius algorithm—and more about the infrastructure that surrounds it.
In this article, we’ll unpack how AI development is shifting toward systems thinking, what that means for developers, and why building intelligent systems is now as much about orchestration as it is about models.
From Models to Ecosystems
Early AI research focused heavily on model performance: how accurate a classifier is, how fluent a language model sounds, how well a vision system can detect objects. But as AI moved into production, it became clear that a powerful model is only one piece of the puzzle.
Real-world AI systems need:
Clean, high-quality data pipelines
Scalable inference infrastructure
Tool use and memory integration
Human feedback mechanisms
Logging, versioning, and security layers
In other words, they need an ecosystem. And developers are now tasked with designing, maintaining, and evolving that ecosystem.
The Components of a Modern AI System
To understand today’s AI development, consider what a full-stack AI system includes:
1. Foundation Model
The core intelligence—often a pre-trained transformer model (like GPT, Claude, LLaMA). It can understand and generate language, code, or visuals.
2. Retrieval System
To ground outputs in real-world or domain-specific knowledge, developers use vector databases (e.g., Pinecone, Weaviate) to inject relevant context.
3. Memory Management
Modern AI agents need long-term memory to track user sessions, preferences, and history. This enables continuity and personalization.
4. Tool Integration
AI models use tools—search engines, APIs, calculators, internal systems—to extend their functionality. Agent frameworks like LangGraph, AutoGen, and CrewAI manage this orchestration.
5. User Interface
Interfaces matter. Whether through chat, dashboards, or voice, the design of human-AI interaction shapes how users experience intelligence.
6. Observability & Governance
Developers must log activity, detect drift, ensure alignment, and audit for fairness and compliance. Tools like PromptLayer, Weights & Biases, and Truera help with this.
Each of these layers is independently important—but together, they form a living, learning system.
AI as Infrastructure: The New Cloud
Just as cloud computing changed the way software was delivered, AI is now becoming a foundational layer in digital infrastructure.
We're entering a phase where:
AI agents coordinate internal operations
Knowledge workers delegate cognitive tasks to digital copilots
Applications include embedded intelligence as a default
This means AI development is no longer about building apps with AI features—it’s about building apps on top of AI.
Developers are designing workflows where:
AI handles 80% of a task
Humans verify or intervene on the edge cases
Feedback loops improve system performance over time
Think of it as AI-as-a-platform, not AI-as-a-tool.
Why Systems Thinking Matters
As AI gets more capable, systems thinking becomes essential. That means considering:
Interdependence: How model outputs affect other components and users
Emergent behavior: How small changes in one module lead to large effects in the system
Scalability: How performance and cost change as usage grows
Resilience: How the system handles uncertainty, failure, and drift
Developers who understand systems design can build AI that is more robust, flexible, and aligned with human needs.
Challenges in Building Intelligent Systems
Creating a system of intelligence is not easy. Developers face several core challenges:
1. Latency and Cost
Querying large models or multi-step agents can be expensive. Caching, distillation, and async orchestration are crucial.
2. Context Limits
Models like GPT-4 and Claude have token limits. Developers must chunk, summarize, and prioritize information intelligently.
3. Security and Access
When AI tools control APIs or company data, access control, auditing, and identity management become critical.
4. Bias and Misalignment
Complex systems can produce unexpected or harmful behavior. Governance frameworks and red-teaming practices are now standard.
5. Interoperability
Integrating AI with legacy systems, real-time data streams, and third-party services requires robust APIs and middleware.
Solving these issues demands a cross-functional team: AI engineers, MLOps specialists, UX designers, data scientists, and compliance experts working together.
The Shift Toward Modular, Composable Intelligence
One major trend in AI development is modularity. Developers are building systems that can swap out components (e.g., models, memory, tools) without needing to rebuild everything.
This includes:
Plug-and-play LLMs (e.g., switching from GPT-4 to Claude 3)
Swappable vector stores
Reusable agent templates and chains
Language model routers (e.g., based on task, latency, or cost)
This makes it easier to innovate, test alternatives, and scale across teams or domains. It's AI development at the speed of infrastructure.
The Developer’s New Role: System Architect
The AI developer of today is no longer just a model trainer or API wrangler. They are a system architect—someone who:
Designs intelligent workflows
Balances tradeoffs between cost, performance, and safety
Thinks holistically about user experience, context, and trust
Orchestrates not just software, but behavior
AI development is now as much about building experiences and ecosystems as it is about building models.
Conclusion: From Algorithms to Architecture
We’ve moved past the age of standalone algorithms. The future of AI lies in systems of intelligence—modular, adaptable, and deeply integrated into the fabric of our digital lives.
As developers, the challenge isn’t just to make AI smarter. It’s to build infrastructure that can support, scale, and steer that intelligence responsibly.
To succeed in this new era, we must think like systems engineers, design like product architects, and build with the humility that intelligence isn’t just in the code—it’s in the connections.
0 notes
Text
In What Ways Does .NET Integrate with Azure AI Services?

The integration between Microsoft's .NET framework and Azure AI Services represents one of the most seamless and powerful combinations available for building intelligent applications today. This strategic alliance provides developers with unprecedented access to cutting-edge artificial intelligence capabilities while maintaining the robust, enterprise-grade foundation that .NET is renowned for. Organizations utilizing professional ASP.NET development services are leveraging this integration to rapidly deploy sophisticated AI solutions that would have previously required months of development and specialized expertise to implement effectively.
Native SDK Support for Comprehensive AI Services
The .NET ecosystem provides native Software Development Kit (SDK) support for the entire spectrum of Azure AI Services, enabling developers to integrate advanced artificial intelligence capabilities with minimal complexity and maximum performance.
Core Azure AI Services Integration:
• Azure Cognitive Services: Pre-built AI models for vision, speech, language, and decision-making capabilities.
• Azure OpenAI Service: Direct access to GPT-4, DALL-E, and other large language models through native APIs.
• Azure Custom Vision: Tailored image classification and object detection model development.
• Azure Speech Services: Real-time speech-to-text, text-to-speech, and speech translation functionality.
• Azure Language Understanding (LUIS): Natural language processing for intent recognition and entity extraction.
• Azure Form Recognizer: Automated document processing and data extraction capabilities.
Advanced AI Integration Features:
• Asynchronous Operations: Non-blocking API calls optimized for high-performance applications.
• Batch Processing: Efficient handling of large datasets through bulk operations.
• Real-time Streaming: Live audio and video processing capabilities.
• Model Customization: Fine-tuning pre-built models with domain-specific data.
• Multi-modal Processing: Combined text, image, and audio analysis in single workflows .
Edge Deployment: Local model execution for reduced latency and offline capabilities.
Enterprise-Grade Security and Compliance Benefits
The integration between .NET and Azure AI Services delivers comprehensive security features that meet the stringent requirements of enterprise applications while ensuring regulatory compliance across multiple industries.
Authentication and Access Control:
• Azure Active Directory Integration: Seamless single sign-on and multi-factor authentication.
• Managed Identity Support: Secure service-to-service authentication without storing credentials.
• Role-Based Access Control (RBAC): Granular permissions management for AI resources.
• API Key Management: Secure key rotation and access monitoring capabilities.
• OAuth 2.0 Implementation: Industry-standard authentication protocols for third-party integrations.
• Certificate-Based Authentication: Enhanced security through digital certificate validation.
Compliance and Data Protection:
• GDPR Compliance: Data residency controls and right-to-be-forgotten implementations.
• HIPAA Certification: Healthcare-grade security for medical AI applications.
• SOC 2 Type II: Comprehensive security, availability, and confidentiality controls.
• Data Encryption: End-to-end encryption for data at rest and in transit.
• Audit Logging: Comprehensive activity tracking for compliance reporting.
• Geographic Data Residency: Control over data processing locations for regulatory requirements.
Streamlined Development Workflows with Azure SDKs
The Azure SDKs for .NET provide developers with intuitive, well-documented tools that dramatically simplify the integration process while maintaining enterprise-level performance and reliability.
Developer Productivity Features:
• NuGet Package Integration: Easy installation and dependency management through familiar tools.
• IntelliSense Support: Full code completion and documentation within Visual Studio environments.
• Async/Await Patterns: Modern asynchronous programming models for responsive applications.
• Error Handling: Comprehensive exception handling with detailed error messages and retry policies.
• Configuration Management: Simplified setup through appsettings.json and environment variables.
• Dependency Injection: Native support for .NET Core's built-in dependency injection container.
Deployment and Monitoring Advantages:
• Azure DevOps Integration: Seamless CI/CD pipelines for automated deployment and testing.
• Application Insights: Real-time monitoring and performance analytics for AI-powered applications.
• Auto-scaling: Dynamic resource allocation based on application demand and usage patterns.
• Load Balancing: Distributed processing across multiple instances for high availability.
• Version Management: Blue-green deployments and rollback capabilities for risk-free updates.
• Cost Optimization: Usage-based pricing models with detailed billing and cost management tools
Real-World Implementation Benefits:
• Reduced Development Time: 60-80% faster implementation compared to building AI capabilities from scratch.
• Lower Maintenance Overhead: Microsoft-managed infrastructure eliminates operational complexity.
• Scalability Assurance: Automatic scaling to handle millions of requests without performance degradation.
• Global Availability: Worldwide data center presence ensuring low-latency access for global applications.
The synergy between .NET and Azure AI Services creates an unparalleled development experience that combines familiar programming paradigms with cutting-edge artificial intelligence capabilities. This integration empowers organizations to accelerate their AI applications development initiatives while maintaining the security, scalability, and reliability standards that modern enterprise applications demand.
0 notes
Text
Version Control in Technical Writing: Why It Matters
In the fast-paced world of product development, one thing is constant—change. Features evolve, UIs get updated, workflows shift, and regulatory standards tighten. In such an environment, your documentation can quickly become outdated, inconsistent, or even misleading. That’s where version control in technical writing becomes not just useful—but essential.
For teams that offer or depend on professional technical writing services, version control ensures that every piece of documentation is trackable, editable, and aligned with the latest product realities. It prevents confusion, reduces errors, and fosters collaboration across departments. In this article, we explore what version control means in the documentation process, and why it’s a non-negotiable for growing businesses.
What Is Version Control in Technical Writing?
Version control refers to the systematic tracking, managing, and organizing of changes made to documents over time. It answers questions like:
Who made the last edit?
What exactly changed in this version?
Which version aligns with product version 2.3?
Can we revert to the documentation from 3 months ago?
Version control systems allow technical writers to:
Collaborate without overwriting each other’s work
Review change history for accuracy and approvals
Synchronize documentation with software release cycles
Maintain a clear audit trail (critical for compliance)
Why Version Control Is Critical in Technical Documentation
1. Keeps Documentation Aligned with Product Versions
Imagine a user referring to a guide that no longer reflects your current interface. Without proper version control, this happens often—and damages trust.
By tagging documentation updates to product releases (v1.0, v2.1, etc.), writers ensure that:
Customers always access the correct version
Old features aren’t mistakenly referenced
Internal teams know which guide goes with which build
This is especially vital for SaaS platforms, API products, and regulated industries.
2. Supports Collaboration Across Remote Teams
Modern technical writing often involves multiple stakeholders—writers, developers, designers, product managers. Version control tools allow for:
Real-time or asynchronous collaboration
Clear ownership of edits and reviews
Easy rollback in case of accidental changes
When using systems like Git, Confluence, or Document360, teams can contribute without conflict or duplication.
3. Improves Review and Approval Workflows
In environments with compliance needs (e.g., ISO, FDA, GDPR), every change must be reviewed and approved. Version control provides:
Timestamped edit trails
Reviewer comments and sign-offs
Status indicators (draft, approved, archived) This level of governance ensures documentation meets legal, safety, and quality standards.
4. Simplifies Localisation and Translation Workflows
When technical documentation is translated into multiple languages, version mismatches can cause chaos. Without version control:
Translations may be done on outdated drafts
Updated content may never reach localized versions
Errors multiply across languages
By versioning your source content, you ensure that translators always work from the most recent, approved content—saving time and preventing costly rework.
5. Enables Safe Experimentation
Writers often want to test new formats, reorganize content, or try simplified language. With version control:
These changes can be made in branches or drafts
You can compare them with previous versions
Only approved versions go live
This freedom leads to better documentation—without the risk of breaking anything.
Popular Version Control Tools for Technical Writing
Depending on your tech stack and team structure, you can use:
Git (with platforms like GitHub or GitLab) for code-adjacent docs
Confluence with built-in version history
Document360, Paligo, or MadCap Flare for structured authoring with version snapshots
Google Docs or MS Word with manual version logs (limited for scale)
Choose tools that match your workflow—and ensure your team is trained to use them consistently.
Best Practices for Managing Versions
Tag versions by product release cycles (e.g., v2.3 Help Guide)
Log changes with brief, meaningful commit messages or changelogs
Maintain an archive of legacy documentation
Notify teams when new versions go live
Avoid editing live documents directly—use drafts and approvals
Following these practices makes your documentation future-ready, audit-ready, and user-friendly.
Conclusion
Version control isn’t just a developer’s concern—it’s a critical component of modern technical writing services. In a world of continuous product updates, global users, and compliance standards, managing your documentation lifecycle with version control is the key to maintaining clarity, trust, and consistency.
At TransCurators, we incorporate structured versioning into every stage of our Technical Writing Services—whether we’re creating SOPs, user manuals, developer guides, or compliance documents. Want to future-proof your documentation with scalable versioning systems? Let’s make your docs as dynamic and reliable as your product.
0 notes
Text
Top WebApp Security Checklist for Businesses in the USA (2025)

In today’s digital-first world, web applications are the backbone of most business operations—from e-commerce to customer portals, CRMs, and more. However, with increasing cyber threats, securing your web applications is not optional; it's critical. Especially for businesses operating in the USA, where data breaches can lead to legal penalties, loss of customer trust, and significant financial setbacks.
This guide outlines a comprehensive WebApp Security Checklist tailored for businesses in the USA to ensure robust protection and compliance with modern security standards.
1. Use HTTPS with a Valid SSL Certificate
Secure Socket Layer (SSL) certificates are fundamental. HTTPS encrypts the data exchanged between the user and your application, ensuring it remains private.
Purchase and install a trusted SSL certificate.
Redirect all HTTP traffic to HTTPS.
Regularly renew and monitor the validity of your SSL certificate.
Fact: Google flags HTTP sites as “Not Secure,” impacting SEO and user trust.
2. Implement Strong Authentication & Access Controls

Weak login systems are a hacker’s playground. Use:
Multi-Factor Authentication (MFA): Add extra layers beyond passwords.
Role-Based Access Control (RBAC): Ensure users only access what’s necessary.
Session Management: Set session expiration limits and auto-logout on inactivity.
Bonus Tip: Use OAuth 2.0 or OpenID Connect for secure federated authentication.
3. Sanitize and Validate All User Inputs
Most web attacks like SQL Injection and XSS stem from unsanitized user inputs. To prevent this:
Sanitize inputs on both client and server sides.
Use prepared statements and parameterized queries.
Escape special characters in output to prevent script injections.
Best Practice: Never trust user inputs — even from authenticated users.
4. Regularly Update Dependencies and Frameworks
Outdated plugins, libraries, or frameworks can be exploited easily.
Use dependency management tools like npm audit, pip-audit, or OWASP Dependency-Check.
Enable automatic updates where possible.
Avoid deprecated plugins or unsupported software.
Real Example: The infamous Log4j vulnerability in 2021 exposed millions of apps worldwide.
5. Conduct Regular Vulnerability Scans and Penetration Testing
Security is not a one-time fix. It's a continuous process.
Schedule monthly or quarterly vulnerability scans.
Hire ethical hackers for real-world pen testing.
Fix discovered issues immediately and re-test.
🔍 Tools to Use: Nessus, Burp Suite, OWASP ZAP.
6. Implement Secure APIs

With APIs powering most modern web apps, they’re a common attack vector.
Authenticate API users with tokens (JWT, OAuth).
Rate-limit API calls to avoid abuse.
Use API gateways for logging and security enforcement.
Extra Tip: Never expose sensitive internal APIs to the public internet.
7. Data Encryption at Rest and in Transit
Whether storing user passwords, payment info, or PII — encryption is essential.
Encrypt sensitive data in the database using AES-256 or better.
Avoid storing passwords in plain text — use hashing algorithms like bcrypt.
Always encrypt data transfers via HTTPS or secure VPN tunnels.
Compliance: Required under data protection laws like HIPAA, CCPA, and PCI-DSS.
8. Monitor Logs & Set Up Intrusion Detection
Monitoring can alert you to threats in real-time.
Use centralized logging systems like ELK Stack or Splunk.
Implement intrusion detection systems (IDS) like Snort or OSSEC.
Set up alerts for unusual activities like multiple failed logins.
Tip: Review logs weekly and set up daily summaries for admins.
9. Backup Regularly & Prepare a Disaster Recovery Plan
Cyberattacks like ransomware can lock you out of your app.
Schedule automatic daily backups.
Store backups offsite or in the cloud (with encryption).
Test your disaster recovery plan quarterly.
Pro Tip: Use versioned backups to roll back only the infected data.
10. Comply with Data Privacy Regulations
For businesses in the USA, compliance isn't just good practice — it's the law.
If you handle health data → HIPAA compliance is mandatory.
Selling to California residents → comply with CCPA.
Accepting payments? → follow PCI-DSS requirements.
Reminder: Non-compliance can lead to heavy penalties and lawsuits.
11. Educate Your Team
The weakest link is often human error.
Train employees on phishing and social engineering attacks.
Enforce strong password policies.
Run annual cybersecurity awareness programs.
Result: A well-trained team is your first line of defense.
12. Use Web Application Firewalls (WAFs)

WAFs provide an extra layer of protection.
Block malicious traffic before it reaches your server.
Protect against DDoS, brute force, and zero-day attacks.
Use cloud-based WAFs like Cloudflare, AWS WAF, or Imperva.
Bonus: Easily deployable and scalable with your infrastructure.
Conclusion
For U.S.-based businesses, web application security should be a strategic priority — not a checkbox. With cyberattacks growing in complexity and volume, following a thorough security checklist is vital to protect your data, users, and brand reputation.
At the end of the day, your web application is only as secure as its weakest link. Make sure there isn’t one.
Ready to Secure Your WebApp?
If you're looking for expert support to secure or build a robust, secure web application, WeeTech Solution is here to help. Get in touch with our development and cybersecurity team today!
0 notes