#Container Network Security
Explore tagged Tumblr posts
Text
Container Security Market to Reach $12.75 Billion by 2032

Meticulous Research��—a leading global market research company, published a research report titled ‘Container Security Market—Global Opportunity Analysis and Industry Forecast (2025-2032)’. According to this latest publication from Meticulous Research®, the container security market is expected to reach $12.75 billion by 2032, at a CAGR of 23.6% from 2025 to 2032.
Rising integration of AI and ML technologies in container security solutions, increasing acceptance of cloud-native microservices architectures, and growing risks of cyberattacks in business operations are factors driving the growth of the container security market. However, market growth is restrained by budgetary issues among SMEs and a scarcity of skilled workforce.
In addition, the expanding utilization of the zero-trust security model and the development of vulnerability scanning tools and practices create growth opportunities for market players. The market faces substantial challenges, including frequent security patches and updates and integration of container security solutions with legacy systems. However, enhancing container management with complementary technologies is a prominent technology trend in the container security market.
Key Players
The container security market is characterized by a moderately competitive scenario due to the presence of many large- and small-sized global, regional, and local players. The key players operating in the container security market are Microsoft Corporation (U.S.), Google LLC (A Subsidiary of Alphabet Inc.) (U.S.), Cisco Systems, Inc. (U.S.), Check Point Software Technologies Ltd. (Israel), Amazon.com, Inc. (U.S.), International Business Machines Corporation (U.S.), Tenable, Inc. (U.S.), Zscaler, Inc. (U.S.), Palo Alto Networks, Inc. (U.S.), Broadcom Inc. (U.S.), Juniper Networks, Inc. (U.S.), Trend Micro Incorporated. (Japan), CrowdStrike Inc. (U.S.), Rapid7 LLC (U.S.), Qualys, Inc. (U.S.), McAfee, LLC (U.S.), Fidelis Security, LLC (U.S.), Sophos Ltd. (U.K.), Anchore, Inc. (U.S.), Docker, Inc. (U.S.), and Aqua Security Software Ltd. (Israel).
The container security market is segmented based on offering, deployment mode, organization size, application, and end-use industry. The report also evaluates industry competitors and analyzes the container security market at the regional and country levels.
Among the offerings studied in this report, the solutions segment is anticipated to dominate the container security market in 2025, with a share of 74.0%. The rapid growth of container security solutions to automate scanning for vulnerabilities and real-time monitoring of container activities and the increased need for unified security management platforms to allow for centralized control over container security policies and configurations are factors contributing to the segment’s dominant position in the container security market.
Among the deployment modes studied in this report, the cloud-based segment is anticipated to dominate the container security market in 2025, with a share of 56.0%. The High growth of cloud-based container security solutions to manage multiple environments and regions of business applications and the rise in technological advancement in cloud-based solutions such as AI and ML to enhance threat detection and anomaly detection are factors contributing to the segment’s dominant position in the container security market.
Among the organization sizes studied in this report, in 2025, the large enterprises segment is anticipated to dominate the container security market, with a share of 67.0%. Growth in the adoption of container security solutions in large enterprises for real-time monitoring of applications for tracking container activity, network traffic, and interactions and the rise in security solutions to mitigate threats and minimize security incidents for large enterprises with complex IT environments are factors contributing to the segment’s dominant position in the container security market.
Among the applications studied in this report, in 2025, the vulnerability management segment is anticipated to dominate the container security market, with a share of 28.0%. High growth in container security solutions by integrating continuous integration/continuous deployment (CI/CD) pipeline for vulnerabilities and rapid use of security solutions for vulnerability management by automating scanning and remediation processes threat intelligence and improving overall visibility and compliance are factors contributing to the segment’s dominant position in the container security market.
Among the end-use industries studied in this report, in 2025, the IT & telecommunications segment is anticipated to dominate the container security market, with a share of 24.0%. The rise in the growth of container security solutions to provide up-to-date information on emerging threats and vulnerabilities for threat intelligence and the rise in the adoption of container security solutions in IT & telecommunications to run applications across different environments to identify and address security vulnerabilities are factors contributing to the segment’s dominant position in the container security market.
Geographic Review
This research report analyzes major geographies and provides a comprehensive analysis of North America (U.S., Canada), Europe (Germany, U.K., France, Italy, Netherlands, Spain, Sweden, and Rest of Europe), Asia-Pacific (Japan, China, India, South Korea, Singapore, Australia & New Zealand, Indonesia, and Rest of Asia-Pacific), Latin America (Brazil, Mexico, and Rest of Latin America), and the Middle East & Africa (UAE, Saudi Arabia, Israel, and Rest of Middle East & Africa).
Among the geographies studied in this report, in 2025, North America is anticipated to dominate the container security market, with a share of 38.0%. High growth in vulnerability scanning tools and practices in organizations, rise in the integration of AI and ML technologies in container security solutions, and rapid growth in vulnerabilities and cyberattacks in business operations in the region are factors contributing to the segment’s dominant position in the container security market.
Download Sample Report Here @ https://www.meticulousresearch.com/download-sample-report/cp_id=6070
Key Questions Answered in the Report:
What is the value of revenue generated by the sale of container security?
At what rate is the global demand for container security projected to grow for the next five to seven years?
What is the historical market size and growth rate for the container security market?
What are the major factors impacting the growth of this market at global and regional levels?
What are the major opportunities for existing players and new entrants in the market?
Which offering, deployment mode, organization size, application, and end-use industry segments create major traction in this market?
What are the key geographical trends in this market? Which regions/countries are expected to offer significant growth opportunities for the manufacturers operating in the container security market?
Who are the major players in the container security market? What are their specific product offerings in this market?
What recent developments have taken place in the container security market? What impact have these strategic developments created on the market?
Contact Us: Meticulous Research® Email- [email protected] Contact Sales- +1-646-781-8004 Connect with us on LinkedIn- https://www.linkedin.com/company/meticulous-research
#Container Security Market#Container Monitoring#Container Scanning Tools#Container Network Security#Container Runtime Protection#Container Orchestration
0 notes
Text
"In Northern California, a Native American tribe is celebrating the return of ancestral lands in one of the largest such transfers in the nation’s history.
Through a Dept. of the Interior initiative aiming to bring indigenous knowledge back into land management, 76 square miles east of the central stretch of the Klamath River has been returned to the Yurok tribe.
Sandwiched between the newly-freed Klamath and forested hillsides of evergreens, redwoods, and cottonwoods, Blue Creek is considered the crown jewel of these lands, though if it were a jewel it wouldn’t be blue, it would be a giant colorless diamond, such is the clarity of the water.

Pictured: Blue Creek
It’s the most important cold-water tributary of the Klamath River, and critical habitat for coho and Chinook salmon. Fished and hunted on since time immemorial by the Yurok and their ancestors, the land was taken from them during the gold rush before eventually being bought by timber companies.
Barry McCovey Jr., director of the Yurok Tribal Fisheries Department, remembers slipping past gates and dodging security along Blue Creek just to fish up a steelhead, one of three game fish that populate the river and need it to spawn.
Profiled along with the efforts of his tribe to secure the land for themselves and their posterity, he spoke to AP about the experience of seeing plans, made a decade ago, come to fruition, and returning to the creek on which he formerly trespassed as a land and fisheries manager.
“To go from when I was a kid and 20 years ago even, from being afraid to go out there to having it be back in tribal hands … is incredible,” he said.
Part of the agreement is that the Yurok Tribe would manage the land to a state of maximum health and resilience, and for that the tribe has big plans, including restoring native prairie, using fire to control understory growth, removing invasive species, restoring native fish habitat, and undoing decades of land-use changes from the logging industry in the form of culverts and logging roads.
“And maybe all that’s not going to be done in my lifetime,” said McCovey. “But that’s fine, because I’m not doing this for myself.”
The Yurok Tribe were recently at the center of the nation’s largest dam removal, a two decades-long campaign to remove a series of four hydroelectric dams along the Klamath River. Once the West Coast’s third-largest salmon run, the Klamath dams substantially reduced salmon activity.
Completed last September, the before and after photographs are stunning to witness. By late November, salmon had already returned far upriver to spawn, proving that instinctual information had remained intact even after a century of disconnect.

Pictured; Klamath River flows freely, after Copco-2 dam was removed in California
“Seeing salmon spawning above the former dams fills my heart,” said Joseph L. James, chairman of the Yurok Tribe, the leaders of the dam removal campaign along with the Karuk and Klamath tribes.
“Our salmon are coming home. Klamath Basin tribes fought for decades to make this day a reality because our future generations deserve to inherit a healthier river from the headwaters to the sea.”
Last March, GNN reported that the Yurok Tribe had also become the first of America’s tribal nations to co-manage land with the National Park Service under a historic memorandum of understanding involving Redwoods National Park.
The nonprofit Save the Redwoods bought a piece of land adjacent to the park, which receives 1 million visitors annually and is a UNESCO Natural Heritage Site, and handed it over to the Yurok for stewardship.
The piece of land, which contained giant redwoods, recovered to such an extent that the NPS has incorporated it into the Redwoods trail network, and the two agencies will cooperate in ensuring mutual flourishing between two properties and one ecosystem.
Back at Blue Creek, AP reports that work has already begun clearing non-native conifer trees planted for lumber. The trunks will be used to create log jams in the creek for wildlife habitat.
Costing $56 million, the land was bought from the loggers by Western Rivers Conservancy, using a mixture of fundraising efforts including private capital, low interest loans, tax credits, public grants and carbon credit sales.
The sale was part of a movement called Land Back, which involves returning ownership of once-native lands of great importance to tribes for the sake of effective stewardship. [Note: This is a weirdly limited definition of Land Back. Land Back means RETURN STOLEN LAND, PERIOD.] Studies have shown around the tropics that indigenous-owned lands in protected areas have higher forest integrity and biodiversity than those owned by national governments.
Land Back has seen 4,700 square miles—equivalent to one and a half-times the size of Yellowstone National Park—returned to tribes through land buy-back agreements in 15 states." [Note: Since land buyback agreements aren't the only form of Land Back, the total is probably (hopefully) more than that.]
-via Good News Network, June 10, 2025
#indigenous#first nations#native american#yurok#united states#north america#california#land back#landback#salmon#endangered species#conservation#ecosystem restoration#rivers#damns#klamath river
7K notes
·
View notes
Text
Mastering Azure Container Apps: From Configuration to Deployment
Thank you for following our Azure Container Apps series! We hope you're gaining valuable insights to scale and secure your applications. Stay tuned for more tips, and feel free to share your thoughts or questions. Together, let's unlock the Azure's Power.
#API deployment#application scaling#Azure Container Apps#Azure Container Registry#Azure networking#Azure security#background processing#Cloud Computing#containerized applications#event-driven processing#ingress management#KEDA scalers#Managed Identities#microservices#serverless platform
0 notes
Text
Leading Ocean Freight Services in Gurgaon for All Your Shipping Needs | Krishna Trading Co.| +91-9999313569

Krishna Trading Co. offers reliable and efficient ocean freight services in Gurgaon, ensuring your cargo reaches its destination safely and on time. With a strong network of global partners and extensive experience in the industry, we provide customized solutions to meet your specific shipping needs. Our services include full container load (FCL), less than container load (LCL), and specialized cargo handling. At Krishna Trading Co., we prioritize customer satisfaction by offering competitive rates, timely deliveries, and exceptional customer support.
Comprehensive Services: - Full Container Load (FCL): We offer dedicated containers for large shipments, ensuring secure and efficient transportation. - Less Than Container Load (LCL): For smaller shipments, our LCL service consolidates cargo with others, providing cost-effective solutions. - Specialized Cargo Handling: Expertise in handling oversized, heavy, and delicate cargo with specialized equipment and care.
Global Network: - Extensive Partnerships: Strong relationships with international shipping lines and agents for seamless global transportation. - Wide Reach: Coverage of major ports worldwide, ensuring your cargo reaches any destination.
Customized Solutions: - Tailored Services: We provide personalized shipping solutions to meet the unique requirements of each client. - Flexible Options: Various shipping schedules and routes to accommodate time-sensitive shipments and specific delivery needs.
Competitive Rates: - Cost-Effective Pricing: Transparent and competitive pricing to provide the best value for your shipping needs. - Value-Added Services: Additional services like cargo insurance, customs clearance, and documentation support to streamline your logistics process.
Timely Deliveries: - Reliable Schedules: Adherence to strict schedules for prompt and timely deliveries. - Real-Time Tracking: Advanced tracking systems to monitor your shipment’s progress and provide updates.
Exceptional Customer Support: - Dedicated Team: Experienced and knowledgeable staff to assist with all aspects of your shipping needs. - 24/7 Support: Round-the-clock customer service to address any queries or concerns promptly.
Trust and Reliability: - Proven Track Record: A history of successful shipments and satisfied customers. - Commitment to Excellence: Dedication to maintaining high standards in service quality and customer satisfaction.
Choose Krishna Trading Co. for your ocean freight needs in Gurgaon and experience a seamless, reliable, and efficient shipping service.
Contact Information:
Phone: 91–9999313569 Email: [email protected]
#Ocean Freight Services#Gurgaon Shipping Solutions#Krishna Trading Co.#FCL Shipping Gurgaon#Global Shipping Network#Real-Time Shipment Tracking#24/7 Customer Support#International Freight Services#Secure Container Shipping#Affordable Ocean Freight
0 notes
Text
How to Configure Azure Container Registry for a secure connection with Azure Container Apps
Ensuring container app resource security is important, and creating a private endpoint for security ensures it. This guide prioritizes actively configuring Azure Container Registry for secure connections with Azure Container Apps. Microsoft Azure empowers users with Azure Container Registry, enabling secure storage and management of Docker container images via Docker Hub technology. Azure…

View On WordPress
#AcrPull#Azure container Registry#Azure firewall#Azure Virtual Network#Container Apps#Private endpoint protection#Role Assignment#Self Assigned Managed Identity#User assigned Managed Identity#Workload security
0 notes
Text
⋆˚࿔ JINU + HUNTR/X!READER. ── HEADCANONS!
── content warnings: F!reader, mention of twitter, compilation of enimies to lovers, light content.
── word count: 674!



⭑.ᐟ He was just a pretty face. — perhaps, apollonian, charming, delicate. — Only. — There was no way you could start admiring that man, besides, he wasn't everything they keep saying, gossiping about; you weren't a teenager.
⤷ But, damn, in a few moments, you were judging and scolding Zoey, alongside Rumi, for admiring the new, damn, demonic boy band; and right now, you're reveling in the group's leader. — No, you weren't proud of that, not even a little bit.
⭑.ᐟ Jinu was looking for your contact; regardless of whether he could be rejected, snubbed, offended or completely threatened. — Funny, he liked the rude and confusing way you greeted him politely next to the girls. — The boy, demonic and enigmatic, dedicated himself to tormenting you.
⤷ Daring winks, mentioning your name in an interview, flirtatious greetings, or compliments on some song you wrote? — Oh, that man was a stupid curse; you wished you had the chance to kill him. — Mira was begging you to put this plan into action.
⤷ It was ridiculous; Jinu was ridiculous. — The feeling of vulnerability could never taste your chest, however, you knew that his actions made you curious, almost disturbed; it was not out of fear, anguish or lack of security, it would never be that. — After all, you had always been taught to bury those feelings in the tombs of demons.
⭑.ᐟ OH, THE GOSSIP? — Zoey, as always, updated on everything that was being said about HUNTR/X on all social networks; seriously, she was starting to outgrow Bobby. — So, every night, especially during breaks and rests, you all got together to read all the news, tweets.
⤷ And of course, your fans and SAJA BOYS were commenting, almost obsessively, about the amount of interactions that happened between you and Jinu; right, there were many, many tweets. — Photos and some videos of him looking at you, with those soft, venerable eyes, while answering a question from the interviewer or how you were together when it was time for the photo shoot for a magazine; there were many situations.
⤷ On the one hand, you were curious to read all those tweets, posts just out of curiosity about the fans' creativity, just for that. — Ah, a demon with a huntress, what a joke in terrible and horrible taste.
“OH, look at this one!” — Zoey exclaimed, with great enthusiasm, almost spilling her soda on the couch, earning a sigh from Rumi. — “I wish i had thought of that one before.” — She laughed as she tried to show and tell what the tweet would be; Mira and you looked at each other, not trying to contain your laughter.
“Say it!” — Participating in the excitement, you said to the youngest.
“Okay, okay…” — As she turned the tablet, Zoey showed two photos where you and Jinu were greeting each other; in the first photo, you had bowed and in the second, you stared at each other for a few seconds. — Do you remember this moment? — “Listen, “They look like a couple of divorced parents who still see each other every day because of their child and who are going to fall in love again.”” — She repeated what was written in the post.
“Oh, no…” — Your hand found the small, white pillow, then slapped it against your face, hiding your red, embarrassed cheeks.
⭑.ᐟ He intrigued you; he disturbed you. — There were times when you felt persecuted, but you allowed yourself to be; acting as if you were cat and mouse, or rather, two individuals who were hard to antagonize in any environment. — You swear you couldn't say whether or not you liked maintaining this feeling, a dangerous, forbidden feeling with a creature you knew was cruel.
⤷ Jinu could contemplate, worship your presence; sometimes, you didn't even need to know or fear that he was near. — It was always a mystery. — Likewise, how he enjoyed feeling all your anger, confusion and, perhaps, fascination in singing a part of the song that might — or might not — be for him.
“How can you sleep or live with yourself? a broken soul trapped in a nastiest shell.”
968 notes
·
View notes
Text
Kindly take a break from scrolling to read this, it's important.
Take your time to grieve and come to terms with the election results, but once you've done that, it's time to get to work. We have two months. And a lot to do in that time. We have to prepare, to be ready.
Be careful about what you post or say online. Anything potentially incriminating should be avoided. Threatening language, even if clearly a joke, can be used against you.
Know someone who's trans? Someone who's had an abortion? Someone who's LGBTQIA+? Someone who's an immigrant? Someone who attends protests? Someone who's disabled? Someone who might in any way be at risk due to laws being put into place? No you don't.
Move away from social media platforms and browsers that require you to use your real identity or input a large amount of personal information. Now's a good time to find alternate means of communicating online. Tails, Element, Tor, Mastodon, Firefox, and Lemmy are all decent options.
Find a community. Someone you can talk to, either online or in real life, that you'll have reliable contact with. We need to try and create a network, but one that's as anonymous as possible.
Start scrubbing your trail as much as possible. Get rid of old accounts that can still be traced to you but are no longer used, delete personal data off the internet. There are websites out there that will freely remove your data from the internet, but be careful about which one you use, make sure it's safe and legitimate first.
Change any usernames that you can that contain any personal information. Names, birthdays, anything.
Plan B has a four year shelf life. Stock up, but don't take more than you you'll need. We don't want a COVID repeat where everyone buys an excessive amount of things and leaves none for everybody else.
There are doctors that will sterilize you, if that's the way you want to go.
Stop using online period trackers right now. Delete all data from it if possible first, then delete the app itself. If you must, write it down, but in a subtle manner and on something you keep at home. Don't label it, just put the dates. If you're really worried, discard older records and only keep the most recent few, and label the dates as other random events, like "go to mall" or "chicken salad for dinner this night"
Get your vaccines now.
Save money.
Archive. We have to start collecting records, media, data, books, and articles now. On racism, on fascism, on homophobia, on gender, on self-reliance, on survival, on safe travels routes, on equality, on justice, on anything that may be useful and/or censored soon. We can't let them erase it.
Collect those online resources. Bookmark them, copy files into your storage, Screenshot pages. Create a decentralized library where everyone is working to be part of a whole, storing what they can individually and sharing it between one another. Again, be careful about doing this.
Second-hand bookstores are your best friend. Books are usually very cheap in them, and they often have a decent stock. See what you can find.
When buying ANYTHING I have mentioned above, or anything else that maybe put you in danger, try to use cash to reduce your spending trail.
Check your car information online, many newer models can be remotely tracked.
Turn your phone completely off if you may be at risk due to your location and current activities. Turning off your GPS also helps.
Take note of where you are. Who are your friends? Who's a safe person? Where can you go besides your own home that you know you'll be safe? Establish these connections now.
Who around you is not safe? Who and where do you need to avoid? Do you need to move? If you cannot afford moving but need to, there are fundraisers that can help you. If even that is not an option, at least try to make sure your home is secure. Have someone who can help you. Have a fallback safe place.
And finally, I want anyone with resources to put them in the replies. Flood it with useful links, information, tips, anything. We're in this together. Do not panic. Organize.
EDIT: Please be civil in the replies.
#us politics#punk#protest#lgbtq#lgbt#lgbtqia#women rights#women's rights#online archival effort#censorship#internet censorship#internet#shtf#anonymity#safety#important#serious#presidential election#2024 presidential election#do not let them erase us#fight back#human rights#we fight
1K notes
·
View notes
Text
Top 20 Open Source Vulnerability Scanner Tools in 2023
Top 20 Open Source Vulnerability Scanner Tools in 2023 @vexpert #vmwarecommunities #100daysofhomelab #homelab #OpenSourceVulnerabilityScanners #SecurityTools #VulnerabilityAssessment #PenetrationTesting #SQLInjection #NetworkVulnerabilityTests
In the world of cybersecurity, having the right tools is more important than ever. An extremely important tool for cybersecurity professionals is the vulnerability scanners. They are designed to automatically detect vulnerabilities, security issues, and potential threats in your systems, applications, or network traffic. By carrying out network vulnerability tests and scanning web applications,…

View On WordPress
#Container Image Scanning#License Compliance#Network Vulnerability Tests#Open Source Vulnerability Scanners#Penetration Testing#Security Testing#security tools#Software Composition Analysis#SQL Injection#Vulnerability Assessment
0 notes
Text
tracking barbara gordon's skillset as oracle:
she provides directory assistance for several international and intergalactic teams of superheroes (the birds of prey, justice league of america, the outsiders, and she has worked with the titans before).
she is the primary hacker and information network source for many of these heroes.
she helps provide mercy ops (disaster relief and humanitarian efforts) globally.
she is able to hack into the white house cameras.
she hacks into the united states air force routinely to use their memory capabilities.
she is seen as a pentagon level threat.
she writes her own code for scanning new satellite images for human habitations and anomalies.
she's accessed air force rockets no one is supposed to know about and overridden them to fire them.
she has a team of drones ready for surveillance.
she's put her own security systems on arkham asylum.
she hacks into information databases from federal complexes and assembles blueprints and guard schedules so she can send her agents to break into them.
she sets a government complex on fire (she says it is a small and contained fire.)
she also sets the clock tower on fire to force batman to not do murder/suicide.
she hacks into cia debriefing transcripts to obtain information.
she controls a large portion of the world's internet and power grids.
she also is the reason why many world leaders are in power.
she has access to the bank accounts of several supervillains, whom she toys with (specifically for blockbuster, she regularly steals millions of dollars from his accounts in a way that he cannot track who is stealing it and where it is going -- she's stolen 3 million, 17 million, 6 million, twenty million and also a hundred million from him).
she can also hack alien drones.
she can control traffic.
she has several booby-traps in the clock tower for potential assaulters. she also a device to monitor movement of people around it, in case batman decides to show up.
cited panels down below!

"she's the four-one-one for the jla, she the database for the g.c. ex-p.d. she runs mercy ops around the world." nightwing (1996) #38

"you have cameras in the white house?" "don't be silly. the white house has cameras in the white house. i've just tapped into them." nightwing (1996) #66
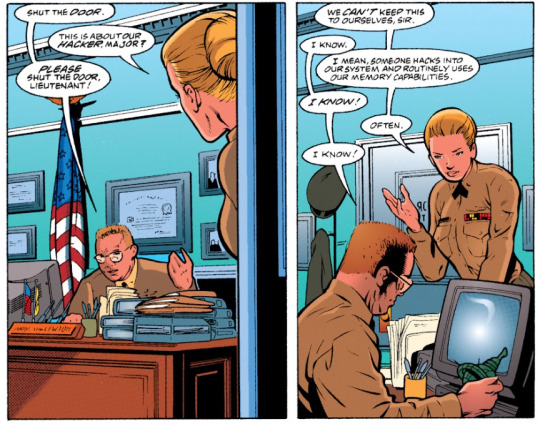
"i mean, someone hacks into our system and routinely uses our [united states air force] memory capabilities!" "i know!" "often." birds of prey #1 (1999)
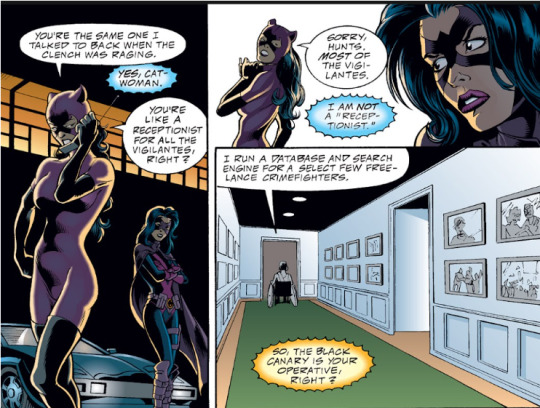
"i run a database and search engine for a select few free-land crimefighters." birds of prey: manhunt (1996)

"we scan the most recent images for anomalies. things that don't belong." "where'd you get a program for that?" "i wrote my own code for that one." birds of prey (1999) #3

"they've accessed whitehorse, sir." "whitehorse? no one's supposed to know about that!" birds of prey (1999) #9

"and oracle? we're going to need eyes on several places at once." "i think we can manage that." detective comics (1937) #1077

"they've accessed whitehorse. what's the chance of them arming it?" "all clear?" "oh yeah." "fire!" birds of prey (1999) #9
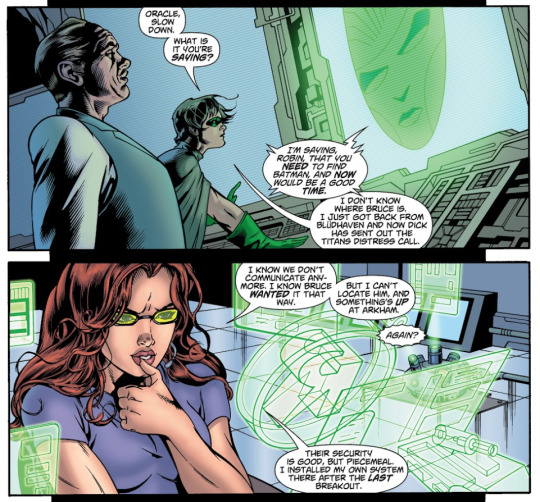
"[arkham's] security is good, but piecemeal. i installed my own system there after the last breakout." infinite crisis special: villains united (2006)

"batgirl -- that incident a couple months back? when those government agents caught your face on tape? i found out where they're keeping it. it's a federal complex in virginia. i've sent you blueprints, guard schedules -- everything you'll need to break in." batgirl (2000) #17

"where did you get that kind of information?" "they traded another prisoner last month. i hacked into his cia debriefing transcript." birds of prey (1999) #9

"kat, do you have any idea... any notion at all, of how much of the planet's entire internet i control? how many power grids? how many world leaders owe me their positions?" birds of prey #1 (1999)

"i transferred all the funds in her cayman islands account to another offshore account. if she doesn't get the paintings to me in the next forty-eight hours, that money's going to my favorite charities." birds of prey: catwoman/oracle (2003)

"where do you get current [satellite] shots of rheelasia?" "that's my secret, you little netnik." birds of prey (1999) #3

"but the asborbascons were created using languages long dead even on my planet. they are uncrackable." "yes. the absorbascons are uncrackable. but the alien drones aren't." convergence: nightwing/oracle (2015)
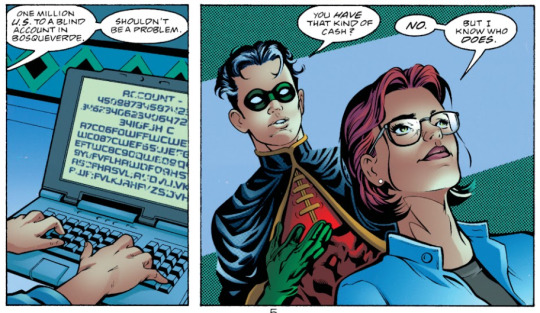

"do you have that kind of cash?" "no. but i know someone who does." "there's been a... discrepancy, mr. desmond." "in plain english, mr. vogel." "at one point, three million was electronically transferred from your numbered accounts in the caicos to a bank account in hasaragua. from there to karocco, then yemen, then split between banks in senegal and manila. and then... my hardware couldn't keep up." birds of prey (1999) #3

"seventeen million from your account in the caymans. six from santa prisca. twenty from rheelasia. and a hundred million plus from other holdings of yours around the world, mr. desmond. and where it all goes? nobody knows." birds of prey (1999) #18

"they're taking your cash from impregnable accounts and transferring it electronically to their own." "and you can't find the source?" "there's subsequent transfers performed at lightning speed. the money's split up, rerouted in and out of various banks in an eyeblink. even i can't keep up with whoever this is." birds of prey (1999) #18

"let me handle the traffic." birds of prey (1999) #58

"all of you. keep your hands where i can see 'em." "not a problem. malory. ripken. peppermint." nightwing (1996) #39
#barbara gordon#babs#oracle#batgirl#birds of prey#justice league of america#jla#batman#robin#nightwing#huntress#black canary#blockbuster#dick grayson#tim drake#helena bertinelli#bruce wayne
490 notes
·
View notes
Text
Scorpio through the houses: where does it benefit you to go outside of your comfort zone ?🌪️🕷️

Contained within the Taurus x Scorpio axis we see the push and pull theme of security vs scarcity, stability vs instability, comfort vs risk. 💰💥
Taurus is doing what you know and what brings you security, but Scorpio is doing something risky that leads to transformative experiences. 🌪️
Scorpio is a risk-taking sign.

SCORPIO 1H: your approach to life involves risk. You are fearless when it comes to achieving your goals. If you need to acheieve something and there’s risk involved, you’re not afraid to make that move. Taking risks with your physical appearance, trying new looks is often perceived well by others. People see you as a brave/ fearless person.
SCORPIO 2H: risk taking when it comes to money. Taking that risk to start your own business, investing in yourself, in your ideas. When you break traditional rules when it comes to money, you find that your risk pays off. Not following status quo of family traditions but taking the risk to make your own way.
SCORPIO 3H: taking risks when it comes to how you express yourself. Saying things other people are scared to say , taking the risk to say what needs to be said. Facing your fears when it comes to speaking up for yourself. Being bold enough to reveal truth and speak on taboo topics.
SCORPIO 4H: being the pattern breaker in your family. Doing things differently than the rest of your family. “Black sheep” of the family but has positive intentions towards change. Doing things differently than your lineage and ancestors. Being risk taking when it comes to leaving the past being. Leaving comfort zone with bold action. Sacrificing your past for your future.
SCORPIO 5H: risk taking when it comes to your creative ideas. Incorporating taboo things into your creative art. Going outside of your comfort zone to put your creativity out there instead of for keeping it private. Facing fears through performing your art.
SCORPIO 6H: risk taking when it comes to your daily routine. Not doing the same thing everyday , but doing things that scare you little by little on a daily basis. Tackling your fears in your daily routine. Taking risks in your professional and work life. Willing to take risks to get hired for the job you want.

SCORPIO 7H: going outside of your comfort zone in relationships and partnerships. Giving some one a chance who you usually wouldnt go for.. likely to take risks in love. Leaving your comfort zone to meet people, networking where you usually wouldn’t, meeting your romantic partner that way.
SCORPIO 8H: risk taking when it comes to initiating transformation in your life. Going outside of what you know to discover the unknown. Fearlessly changing your mentality when you need to. Tackling your fears when it comes to limiting beliefs. Single-handedly overcoming your own subconscious fears. Transforming the psychological conditioning you were raised with into something different.
SCORPIO 9H: being risk taking when it comes to your spiritual beliefs. Participating in spiritual practices that are considered taboo. Bravely expressing your beliefs even if they’re not popular. Feeling like it is your life purpose to transform and take risks. Risk taking when it comes to travel. Journeying to places wouldn’t go. Tackling your fears in other countries.
SCORPIO 10H: going outside of your comfort zone when it comes to your career. Choosing a career your family considers to be “taboo”. Taking risks when it comes to choosing a career that isn’t traditional. Having a reputation of being fearless and bold. Taking risks to achieve success. Being willing to risk it all to get ahead.
SCORPIO 11H: taking risks when it comes to achieving your goals and desires. Being fearless about how you vi achieve your goals. Risking it all to acheive your dreams and having it be successful. Taking risks when it comes to networking and making social connections. Facing fears with social anxiety.
SCORPIO 12H: taking risks when it comes to endings. Fearlessly leaving the past behind when you need to. Facing your fears when it comes to your subconscious fears and limiting beliefs. Taking risks when it comes your your spiritual path.


#astrology observations#astro observations#scorpio#8th house#taurus#astrology#vedic astrology#scorpio midheaven#starsandsuch#2025
558 notes
·
View notes
Text
THE REGIONAL WAR in the Middle East now involves at least 16 different countries and includes the first strikes from Iranian territory on Israel, but the United States continues to insist that there is no broader war, hiding the extent of American military involvement. And yet in response to Iran’s drone and missile attacks Saturday, the U.S. flew aircraft and launched air defense missiles from at least eight countries, while Iran and its proxies fired weapons from Iraq, Syria, and Yemen.
[...]
While the world has been focused on — and the Pentagon has been stressing — the comings and goings of aircraft carriers and fighter jets to serve as a “deterrent” against Iran, the U.S. has quietly built a network of air defenses to fight its regional war. “At my direction, to support the defense of Israel, the U.S. military moved aircraft and ballistic missile defense destroyers to the region over the course of the past week,” President Joe Biden said in a statement Saturday. “Thanks to these deployments and the extraordinary skill of our servicemembers, we helped Israel take down nearly all of the incoming drones and missiles.” As part of that network, Army long-range Patriot and Terminal High Altitude Area Defense surface-to-air missile batteries have been deployed in Iraq, Kuwait, the United Arab Emirates, Qatar, Saudi Arabia, Jordan, and at the secretive Site 512 base in Israel. These assets — plus American aircraft based in Kuwait, Jordan, the UAE, Qatar, and Saudi Arabia — are knitted together in order to communicate and cooperate with each other to provide a dome over Israel (and its own regional bases). The United Kingdom is also intimately tied into the regional war network, while additional countries such as Bahrain have purchased Patriot missiles to be part of the network. Despite this unambiguous regional network, and even after Israel’s attack on Iran’s embassy in Syria earlier this month, the Biden administration has consistently denied that the Hamas war has spread beyond Gaza. It is a policy stance — and a deception — that has held since Hamas’s October 7 attack. “The Middle East region is quieter than it has been in two decades,” Biden’s national security adviser Jake Sullivan said in an ill-timed remark eight days before October 7. “We don’t see this conflict widening as it still remains contained to Gaza,” deputy Pentagon press secretary Sabrina Singh said the day after three U.S. troops were killed by a kamikaze drone launched by an Iran-backed militia at a U.S. base in Jordan. Since then (and even before this weekend), the fighting has spread to Iraq, Syria, Jordan, and Yemen.
1K notes
·
View notes
Text
orphic; (adj.) mysterious and entrancing, beyond ordinary understanding. ─── 007. the paper.

-> summary: when you, a final-year student at the grove, get assigned to study under anaxagoras—one of the legendary seven sages—you know things are about to get interesting. but as the weeks go by, the line between correlation and causation starts to blur, and the more time you spend with professor anaxagoras, the more drawn to him you become in ways you never expected. the rules of the academy are clear, and the risks are an unfortunate possibility, but curiosity is a dangerous thing. and maybe, just maybe, some risks are worth taking. after all, isn’t every great discovery just a leap of faith? -> pairing: anaxa x gn!reader. -> tropes: professor x student, slow burn, forbidden romance. -> wc: 3.3k -> warnings: potential hsr spoilers from TB mission: "Light Slips the Gate, Shadow Greets the Throne" (3.1 update). main character is written to be 21+ years of age, at the very least. (anaxa is written to be around 26-27 years of age.) swearing, mature themes, suggestive content.
-> a/n: this chapter is a bit dry, and incredibly fast paced, the angst lords held my shoulders gently and demanded my cooperation, and who am i to refuse... > unfortunately not a good angst writer. hopefully the next chapter fills in some gaps :P -> prev. || next. -> orphic; the masterlist.

Professor Anaxagoras stood at the front of the lecture hall, one hand braced against the edge of the desk, the other holding a thick folder of notes he hadn’t opened.
“—the symposium will run the final weekend of the month,” he said. “Attendance is limited to invitees and selected applicants. Presenters will include faculty, visiting lecturers, and a handful of external contributors with the appropriate security clearances.”
You glanced up from your notes. Kira stopped doodling in the margin of her page. Even Ilias straightened a little.
Professor Anaxagoras continued, eyes flicking briefly to the back of the hall, as if confirming something invisible. “Among the guests: Socrippe of the Erythrokeramists, whose work on semiotic containment theory in sacred structures should be familiar to most of you—”
“...and, by unfortunate persistence of committee will,” Anaxagoras said with unmistakable restraint, “Cerces, formerly of this faculty.”
That got a few scattered reactions—raised brows, a murmur or two.
“You may know her from her former lectures in phenomenology. Some of you”—his eyes passed over the hall with unreadable stillness—“have studied under her. You will find no one more exacting in her critique of academic laziness.”
You don’t realize you’re holding your breath until you let it out. The name lingers in the air.
“She specializes in ontology, and approaches metaphysics through embodied cognition. Expect poetry disguised as philosophy,” he said. “Or vice versa.”
Your pen stilled on the page.
Kira nudged you lightly under the desk, eyes narrowed in curiosity.
“She also,” Anaxagoras added, tone flatter now, “insists on calling the panel a ‘dialogic constellation,’ so prepare yourselves.”
Ilias made a face. “What does that even mean?”
“She thinks it sounds more participatory,” Anaxagoras replied, already turning toward the desk, “though experience suggests otherwise.”
“Socrippe of the Erythrokeramists,” he said, “representing a school that approaches spiritual inquiry through artistic interpretation. They concern themselves with the soul, with perception, and with questions of embodied truth—often through mediums most of you would not consider academic. They also lead artistic education across much of the western scholastic network, claiming creativity is essential to understanding.”
“Apuleius,” he said last. “Of the Nodists. Their position is… less subtle. They believe all things are numbers. Not metaphorically—literally.”
He turned back to the room, chalk still in hand.
“To the Nodists, mathematics is not a tool, but a medium through which spiritual logic is expressed. They treat equations as divine revelation. Apuleius is their youngest speaker in a decade. He may attempt to convert you.”
A ripple of laughter this time. Ilias muttered something about cult vibes.
He went on, with a slight pause, “Expect graphs. Animated ones.”
A quiet wave of laughter rippled through the room.
“The application window closes by the end of this week. No extensions. Submission requires a statement of focus and relevant academic record.”

You’re still in your seat by the time lecture ends, notebook open but mostly ignored now, letting the noise filter out around you.
You shift, elbow brushing Kira’s as she taps the cap of her water bottle against the edge of the desk. Ilias, who’s been half-slumped over his notebook for most of the lecture, perks up.
“You still applying?” Ilias asks Kira—too quickly, voice a little too bright, like he’s rehearsed it and still tripped over the delivery.
Kira glances at him. “I am.”
He blinks. “Wait, really?”
She nods, casual as ever. “Yeah.” Her eyes flick to you, unreadable for half a second.
Ilias sits up straighter like he’s just been hit by lightning. “Oh. Uh. Cool. That’s cool. I mean, I was thinking about it. Just, you know—my grades, maybe not entirely be optimal for that kind of thing… But hey—if you’re applying, maybe I will too. Strength in numbers, right? Mutual suffering.”
Kira smirks. “If you make it, I’ll bake you a whole cake.”
“You’re underestimating how motivating that is,” Ilias says, already pulling out his tablet like he’s going to start the application right then and there.
“I’m hoping everyone else applies too,” she says, “Would be nice. Like a little field trip.”
From behind you, unhurried footsteps and an exaggerated yawn cuts through– low, rough, clinging to sleep.
You glance back to see Phainon making his way down from the last row, cardigan half off one shoulder, white shirt rumpled, one eye still closed against the light. Behind him, Mydei trails with quiet ease, carrying two bags like it was second nature.
Phainon drops into the seat in front of you with a thud and immediately turns sideways to slump across your desk like gravity has personally betrayed him.
“If anyone asks,” he mutters, “I was here the whole time.”
“Obviously,” you say, nudging his arm off your notebook. “Nothing says ‘academic presence’ like arriving in slow motion after the lecture ends.”
He makes a muffled noise that might be agreement, despair, or both.
“You missed a lot,” Kira offers, lightly. “Prof talked about the symposium.”
Phainon lifts his head just enough to look at you. “You’re actually applying, right?”
You blink. “No? For the millionth time, I am not.”
Mydei slides onto the table in front of you, legs swinging gently off the edge. He rests his chin on his hand and surveys the group like a tired tutor trying to gauge who did the reading. “I applied last night. I figured you might change your mind after…” His gaze cuts toward the hallway—where Anaxagoras had been—
You stiffen.
And then, as if summoned by the gods of chaos, Ilias flails into the conversation with all the grace of a brick in freefall. “I know made a legally binding promise not to bring it up, and I’ve honored that oath under duress.”
You close your eyes. “Ilias—”
“But someone else brought it up!” he continues, pointing a wildly accusatory finger at Mydei. “So technically, this is no longer my fault and I am absolutely allowed to say— he touched your hand!”
You drop your forehead to the table with a dull thunk.
“Ilias,” you mutter into the woodgrain.
“I saw it!” he insists, wide-eyed. “AnaxaY/N fingertip touch was monumental! And you– you went full system crash. I saw the cursor spinning-buffering wheel-blue screen of existential crisis all over your face!”
Kira raises an eyebrow, barely turning her head. “You’re not wrong,” she says, voice even. “It was painfully obvious, too.”
You shoot her a look. “Whose side are you on?”
She shrugs, unbothered. “I’m just saying. You paused while handing the phone back to him like the fate of the world depended on it.”
Ilias gasps in vindication. “Thank you! Finally, someone sees the truth.”
Kira takes a long sip of water, then adds lightly, “Besides, I think it’s sweet. Tragic, probably. But sweet.”
You scoff. “It was just an email.”
“Sure,” she says, her eyes glinting.
Ilias points at her, triumphant. “This is why Kira’s the only one here qualified to interpret sexual tension.”
You press your palms to your face. “Please stop saying sexual tension.’”
“Why?” Kira asks, tone playful now. “It’s starting to feel... accurate.”
Mydei lets the laughter die down before turning his attention back to you. His voice is gentler this time, quieter. “You don’t have to explain yourself. But if you are going to change your mind, make sure it’s because you want to. Not because someone brushed your hand and your brain rewrote its operating system.”
Your mouth opens, then closes.
“That’s not what happened, and I’m not changing my mind.” you mutter.
Ilias says from the table, still face-down. “As if I didn’t see you walk into a wooden beam afterward.”
Kira flicks a piece of bread at his head. “Enough.”
Mydei grins, stretching languidly as he slides back off the table.
Phainon makes a low noise, something between scandal and amusement. “But seriously, a weekend of intellectual sparring in a windowless auditorium doesn’t interest you?”
Ilias gives him a look. “That can’t be a selling point.”
“I think Honour Roll’s applying,” Kira murmurs, nodding her head towards a guy taking notes… after class ended? “Had his hand raised before prof even finished the sentence.”
Ilias gives her a look. “Isn’t he the one who thought metaphysics was ghost biology?”
You side-eye her. “He defined Cartesian dualism as a debate between two guys named Descartes.”
“He looked so proud, too.”
She hides a grin behind her bottle. “At least he’s consistent. So,” Kira says slowly, “should we all apply and make this a collective breakdown?” and though she addressed the entire table, her eyes were fixed on you.
You raise a brow. “I just said I wasn’t applying.”
She shrugs. “People say a lot of things before peer pressure.”
“I am alarmingly immune to group influence,” you say.
Mydei tilts his head at you. “You’re really out?”
“For now,” you say, and tap your pen against the edge of the desk. “Not every mystery needs a dissertation.”
Kira leans toward the desk, elbow resting against the edge. “What’s a symposium even like?”
Mydei shrugs one shoulder, eyes still on the page. “Professor Anaxagoras never goes to those actually,” he says, matter-of-fact. “Too many vague theories and recycled arguments.” He mocks, albeit accurately. “Said it’s a waste of time.”
You pause, the words settling in.
You look at the open notebook in front of you, still mostly blank. Outside, sunlight drifts in across the floor, catching the edge of a scuffed boot, the curve of Kira’s pen, the fold of Phainon’s sleeve where he’s halfway to sleep again.
Mydei doesn’t elaborate, and Phainon doesn’t ask. He’s already slouching deeper in his chair, arms folded behind his head, eyes drifting shut again. “Wake me if enlightenment knocks,” he mutters.
Mydei flips his pen between his fingers. “If it does, it won’t be for you.”

The room’s mostly empty now, the last of the footsteps fading into the corridor outside.
You start gathering your things too. Kira stretches, rotating her wrist where she'd been fidgeting with her bottle cap. She nudges Ilias’ ankle lightly with her foot. “Come on.”
Ilias startles like he wasn’t expecting to be addressed directly. “Me? You want me to–? Okay, yes. I am coming. Coming is what I’m doing.”
He scrambles to gather his things, nearly knocking over his water bottle in the process. Kira just watches, expression unreadable.
He swings the strap over his shoulder, catches it on the back of the chair, and nearly falls backward trying to recover.
Kira raises an eyebrow. “You good?”
“I’m excellent,” he says, voice going high and too fast. “Never better.”
She starts walking. “Right.”
He follows like a loyal, over-caffeinated puppy. “Did you know that pringles fit perfectly in a cylindrical tube because they’re hyperbolic paraboloids plotted over a circular domain?”
Kira, mid-sip of her tea, blinks at him. "... Do you even know what that means?"
Ilias freezes for a split second, his eyes widening slightly. His hand hovers awkwardly over his fries, which he suddenly seems much less interested in. “Uh. I mean... yeah, totally. It’s... it’s like geometry or something.”
He clears his throat, trying to recover. “You know, math... shapes... real smooth stuff—yeah, I read about it somewhere.”
Kira watches him for a moment, her lips curling into a knowing smirk. “Sure you did.”
Ilias sighs dramatically and shrugs, defeated. "Okay, fine, maybe I don't exactly know what I’m talking about. But you were impressed, right?"
Their voices drift toward the door, Kira’s dry commentary punctuated by Ilias’s increasingly flustered rebuttals.
You’re still smiling faintly when your phone buzzes.
It’s an email.
From: Anaxagoras Subject: (blank) “Student, Appreciate your thoughts—if and when you have them. Regards, Anaxagoras”
That’s all.
Student?
You stare at the files attached:
Cerces_Entanglement.pdf Cerces_SubjectiveStructure.pdf
You’re still not applying. You haven’t changed your mind.
But you download them anyway.

It’s past midnight when you finally open it.
You’d told yourself you were just going to skim. One paragraph, maybe two—enough to say you’d looked. Enough to reply, if he ever asked.
But the first page pulls you in.
Cerces doesn’t write like she’s explaining something. She writes like the truth’s already there, and you’ve simply forgotten how to see it. The language is dense, sure, but it unfolds—slowly, precisely—like it was meant for people willing to do the work.
She makes a case for perception not as a filter, but as a force. Subjective experience shaping what is real, not just coloring it.
You don’t even realize how long you’ve been reading until the cursor on your half-finished assignment blinks back at you, still waiting. You blink down at your screen. Somehow, you’re already halfway through a side note you didn’t plan to write, tying Cerces’ structure-of-thought models to the assignment.
You hadn’t meant to write that. You hadn’t meant to use any of it.
But here you are.

The question was already formed in your mind before his chalk reached the lower edge of the board the next day.
You didn’t raise your hand at first. You waited for the shift in tone he always used to signal the end of the main lecture arc. Waited for that half-step back from the board, the pivot, the glance across the room to see who had been keeping up. And when it came, you lifted your hand.
“Professor?” you said.
Anaxagoras didn’t sigh. He didn’t frown. He simply turned his head slowly, gaze catching on you with the kind of mechanical precision that suggested your voice had registered—barely.
You didn’t waver. “I had a question about the holographic encoding model,” you said, steady. “If we assume memories are distributed across a system rather than stored locally—does that imply the memory itself could exist as a form of interference pattern? One that reassembles partially, depending on context? Or is it more likely that what we call noise is actually unreadable signal?”
There was a beat of silence.
You felt it ripple across the room, a collective moment of attention, not quite tension—but close. Ilias, one row behind, sat up straighter. Kira had already lowered her pen, watching.
Anaxagoras didn’t speak right away.
He reached instead for the edge of the podium, adjusting a stray paper with unnecessary precision—his movements precise, composed, almost too still. The board still glowed behind him, but his eyes didn’t return to the projection. They flicked to you—once.
And then away again.
“Review the Feynman boundary analog,” he said flatly. “It’s in the assigned material.”
You blinked. “I did, but that doesn’t address the noise threshold—if the scale is nonlinear, wouldn’t that change the coherence—”
“You’ll find the constants you’re referring to in the last section,” he said, already turning back to the board. His voice held no edge, no invitation. “Try reading more closely.”
The dismissal was cold.
You sat there, notebook open, page half-filled with the equations you’d been working through during his lecture. The words hit sharper than they should’ve.
“I did read it,” you said, softer than you meant to. Your voice sounded smaller in the large hall, like it didn’t belong.
Anaxagoras didn’t look back. He nodded once—mechanically. “Then read it again.”
No further comment. No elaboration.
He returned to his notes as if the exchange hadn’t happened at all.
You sat there, motionless, your pen frozen midair. Slowly, you closed your notebook, spine pressing against your fingers until it hurt. You didn’t speak again for the rest of the class. Just stared at the fading diagrams on the board, heart thudding low in your chest.
No rebuttal. No protest.

The cafe is buzzing with the usual mid-afternoon rush, students hunched over their laptops, friends chatting in the corner booths. But as you approach the counter, you can’t shake the knot in your stomach.
Kira is behind the register, her usual bright smile faltering slightly when she sees you. Her eyes narrow, a silent question forming as she taps your order into the system. You force a smile, trying to push past the unease creeping up on you.
“One medium cappuccino, please,” you say, voice steady enough to fool anyone who might be listening.
She presses the button to start the machine, but her gaze lingers on you, studying you in the way only she can. “You good?” she asks, her tone soft but sharp with concern. She’s already noticed—how could she not? The lines between your brows, the way you hold yourself too stiffly–
You shake your head slightly, waving it off. “Yeah, I’m fine. Just tired, you know? Assignment stuff.”
She doesn’t buy it for a second. You can see it in the way her lips press together, in the small shift in her posture as she pours the espresso, then expertly steams the milk.
Once she finishes, she slides the coffee cup toward you. “Take a seat,” she says, her voice more firm now. “I’ll be right over.”
You try to protest, but she’s already grabbing a chair and pulling it out next to you before you can stop her. She’s nothing if not persistent.
You set your laptop down as she sits beside you, her expression gentle but resolute.
“So,” Kira says, casually glancing at your screen. “Tell me what’s up.”
You give her a half-hearted smile, opening your laptop again but not really focusing on it. “Seriously, Kira. I’m fine.”
She doesn’t budge, her gaze never leaving you as she tilts her head, considering you with all the patience she can muster. “You know you can be honest with me, right?”
You exhale slowly, your fingers hovering over the keys as you consider how much to say. The truth feels too tangled, too messy to admit out loud. But Kira is waiting, and she’s not going to let you distract yourself with your work.
With a frustrated sigh, you finally lean back in your chair and close the laptop. “It’s Anaxagoras,” you mutter, your eyes dropping to the table. “He’s just being weird. You saw him in class today, didn’t you?”
Kira’s eyes soften, but she doesn’t say anything right away. She lets you breathe, lets the words settle into the air before she speaks.
“I noticed. But you know he’s difficult to read,” she says gently.
After a brief pause, you push her hand aside and open your laptop, scrolling until you find the email, still sitting there like a little landmine in your inbox. “He sent me this after I told him I’m not applying to attend the symposium the other day.” You flick the screen toward her.
Kira leans in, reading quickly. “‘Appreciate your thoughts—if and when you have them.’ Huh.”
“What?”
She gives you a flat look. “What did you reply?”
You blink. “I didn’t, yet.”
“…Why not?”
“I—I didn’t know what to say?” you protest, a little too defensively. “It’s good. It’s actually really good. But if I just emailed back like, ‘Nice paper, Professor,’ I’d sound like an idiot. I was gonna sit with it. Think. Wait until I had something meaningful to say.”
Kira squints. “And how long has it been?”
You hesitate. “Two days.”
She stares at you. “Okay. So maybe that’s why he’s being cold?”
You blink. “What do you mean?”
“I mean—maybe he’s sulking.” A sudden smirk takes over her face.
You blink slowly. “...Sulking?”
Kira nods, casual as anything. “Mhm.”
You stare at her. “Why would he be sulking?”
She lifts a shoulder. “I dunno. You didn’t email him back.”
You frown, puzzled. “But... why would that make him upset?”
Kira looks at you like you just asked why water is wet. “’Cause he sent you a paper.”
“I know, but I’m sure he sends papers to people all the time.”
“Yeah,” she says, like that proves her point. “But he sent it to you. With a note. That said he’d appreciate your thoughts.”
You look down at your laptop, then back at her. “…But I haven’t had time to really sit with it yet. I didn’t wanna reply with something shallow like ‘cool’ or whatever.”
Kira nods like that makes sense, but only a little. That annoying grin is still plastered on her face. “Still. You didn’t say anything. And now he’s ignoring you.”
You tilt your head. “But that doesn’t mean he’s upset. Maybe he was just in a bad mood today.”
She squints a bit. “Yeah, but... he’s usually more focused on you. You know?”
You furrow your brow, trying to backtrack in your head. “... It was just an email?”
Kira shrugs. “Still.”
You nod slowly, still not really getting it, but also kind of… getting it.
Kira pats your arm. “You’re smart. But you’re kinda dumb, too.”
You blink at her. “Thanks?”
“Anytime,” she says, already standing to get back to the counter.

“…Alchemy,” Anaxagoras begins without preamble, voice steady, measured. “Despite the clichés, was never simply the pursuit of gold. It was the architecture of transformation—externally, yes. But also internally. Philosophically. Psychologically. In some theories, even mnemonically.”
You glance up.
Anaxagoras, meanwhile, walks slowly across the platform, gesturing without flourish. “Certain alchemic schools treated memory not as record, but as relic—something to be unearthed, transmuted, and occasionally… relived.”
He pauses.
“Cerces, for example, argues this too,” he adds, almost lazily, eyes skimming across the rows of students. “Though she does not call it alchemy.”
And then—without warning—his gaze lands on you. Not unkind. Not pointed. But undeniably direct.
“In one of her papers, she proposes a model where memory isn’t stored, but stabilized—by narrative. That stability is fragile, vulnerable to external disruption. So,” he says, as if this is all perfectly routine, “what happens when that narrative fails?”
You blink. Slowly.
“Chaos,” you say, forcing a bored tone, not bothering to lift your head. “Or a very dramatic existential crisis. Depending on your level of caffeine.”
You don’t look at him. But out of the corner of your eye, you catch the slight twitch of his mouth. Not quite a smile. But close enough.
You swear his voice is the slightest bit drier when he continues.
“Chaos, yes. Though Cerces might use the word collapse.”
You flip a page in your notebook, already scribbling something down before you realize what you're doing.
Ilias leans in, whispering from the side of his mouth. “You didn’t tell me the secret midnight reading was actually good.”
You keep writing. “Shut up, Ilias.”

You would have replied sooner. You really would have.
It wasn’t because the paper wasn’t interesting—it was, annoyingly so. Precise and elegant and infuriatingly thought-provoking in the way only he could be. But you didn’t know what to say. Not yet.
Opening your laptop, you now see 1 unread message from: [email protected] Subject: RE: – Curious if any of the arguments held up under your scrutiny. —A.
Half of you wishes you could just smash your laptop (or your head) into the wall, but the other half of you is desperately trying to compose yourself long enough to make sense of what you’re about to do.
Before you know it, you have your phone pressed to your ear with a death grip.
You check the time: 3:07 a.m.
Then you stare at the blinking cursor on your laptop screen.
It rings six times before a groggy voice picks up.
“…What?”
“I need your help.”
A pause. Then Ilias exhales, clearly still half-asleep. “Are you in immediate danger?”
“Academic danger, if that counts,” you admit. “I’m trying to write an email to Professor Anaxagoras. I just… I’m stuck.”
There’s a long silence. You hear the creak of bedsprings.
“You called me at 3 a.m. to help you write an email?”
“Yes.”
“Seriously?”
“Yes,” you say again, calmly. “I’ve drafted five versions, none of them feel right. I’m overthinking the phrasing.”
“…Okay. What's the context?”
“I read through the papers he sent me. He followed up this afternoon and asked for my thoughts. I don’t want to send something too short, but I also don’t want it to sound like I’m trying too hard. I just want to sound competent.”
“Okay, reasonable. What have you written so far?”
“I’m worried I sound like I’m trying to seduce him. Sending an email that sounds like a confession of undying love for someone who doesn’t even know your middle name doesn’t seem appropriate.”
He groans dramatically. “Just read the damn drafts. I’m getting secondhand anxiety here.”
“‘Dear Anaxagoras, I hope this email finds you well. I have carefully reviewed your paper, and—’”
He cuts you off with a loud snort. “That’s the seduction version?”
You stare at the phone screen. “...I can’t tell anymore.”
“I’m crying, oh my god. Okay, what’s next?”
You glance at the most recent draft and read aloud: “Dear Professor Anaxagoras, thank you for forwarding the studies. I’ve reviewed them and would appreciate the opportunity to discuss a few thoughts, if you’re available.”
A pause. Then: “That sounds… fine? Why don’t you like it?”
“It feels a little generic. I don’t want it to sound like a template.”
“Well, you are emailing your professor. It’s not supposed to sound like a novel.”
You lean back in your chair, running a hand across your face. “I know. I just keep second-guessing the tone. I want to acknowledge that I’ve read and thought about the material, not just skimmed it.”
“Okay. Then add a sentence. Mention something specific.”
You nod slowly. “Maybe something like: ‘The section regarding recursive stability in cognitive patterning was especially relevant to my current work on--”
“Stop right there. It’s 3 a.m., I don’t have the brain cells to translate Nerd Latin.”
You adjust the wording slightly on your screen. “I think this version works.”
“Good. Send it.”
You hesitate for a moment, rereading. “Alright.”
You hit the button.
There’s a long, terrible silence. You stare at your inbox, watching the email disappear into the ether.
Ilias groans lightly. “There. Done. Crisis averted. I’m going back to sleep.”
“Thanks,” you say. “Sorry for waking you.”
“Night.” Click.

-> next.
taglist: @starglitterz @kazumist @naraven @cozyunderworld @pinksaiyans @pearlm00n @your-sleeparalysisdem0n @francisnyx @qwnelisa @chessitune @leafythat @cursedneuvillette @hanakokunzz @nellqzz @ladymothbeth @chokifandom @yourfavouritecitizen @sugarlol12345 @aspiring-bookworm @kad0o @yourfavoritefreakyhan @mavuika-marquez @fellow-anime-weeb927 @beateater @bothsacredanddust @acrylicxu @average-scara-fan @pinkytoxichearts @amorismujica @luciliae @paleocarcharias @chuuya-san @https-seishu @feliju @duckydee-0 @dei-lilxc @eliawis @strawb3rri-bliss
(send an ask/comment to be added!)

#❅ — works !#honkai star rail#honkai star rail x reader#hsr x gn reader#hsr x reader#anaxa x reader#hsr anaxa#hsr anaxagoras#anaxagoras x reader
163 notes
·
View notes
Text
This renewal fight isn't just about Our Flag Means Death. The cancellation is part of a broader problem that has multiple arms.
Original content is being canceled, shelved and pushed to the shadows while remakes, reboots and endless sequels that can be milked well past their expiration date take precedence.
Lgbtqia+ and diverse content is being canceled, shelved and sidelined in favor of more of the same homogenized stories that have been being done for 100+ years.
Shows that have absurdly high ratings are being canceled. If a show that was being considered a flagship show for the network, that had the highest ratings for 14 weeks, that has a 94% rating on Rotten Tomatoes with a 95% Audience Score, is being canceled what hope does any other show have?
Streaming services and Networks are doing a 180° on they type of content they're interested in. Just a handful of years ago they started pulling away from the long season shows that could be endlessly renewed in favor of short contained stories that could be told in 1-4 seassons with 6-14 episodes per season. Creators have given them those stories but are still having to fight tooth and nail to get the renewals that should have been a foregone conclusion because these are the exact type of shows that were asked for. And audiences were more willing to take chances on these shows because with such a tightly wrapped story with an ending decided on before it started there's no reason we shouldn't be getting the whole story. No reason for premature cancellations when the number of seasons needed to tell the entire story was part of the original pitch that the network agreed to. No need to cancel it unless it actually does have atrocious viewership numbers. But now, these stories that were specifically asked for by the networks, that have ratings well above what's needed to justify keeping it on the air, are being canceled or shelved in favor of going back to the idea of endless seasons and spin offs and reboots of tired franchises.
You want to keep getting good, original stories that aren't just endless reboots and sequels of a once good idea that's lost it's soul? Join the email & letter writing campaign to MAX and other streamers and networks. Tell them you are interested in seeing more original content. Diverse content, lgbtqia+ content. Help save OFMD and in the process save your own favorite shows. No, one letter, one signature can't change anything. But thousands can. Be one of the thousands.
@renewasacrew
2K notes
·
View notes
Text
hard reboot. strict machine anthology. follow up to malicious entity.
cw: noncon/forced masturbation, allusions to and threats of torture, time loss, glib corporate talk discussing reader's experiences, badly named fictional sex toys
Internal Memo: Security Breach Incident Subject: Unauthorized Access Incident: Prototype Offline Date: [Redacted]
A critical security breach occurred involving the company's prototype assistant. The breach, originating from an unknown entity, resulted in the prototype being offline for an extended period. Investigations suggest that the breach was malicious in nature, leveraging advanced techniques to compromise system integrity. The exact source and method of access remain under investigation.
While the breach did not result in lasting, meaningful harm to the user, they were briefly exposed to unauthorized and hostile interaction. Standard protocol was followed, and the user was promptly compensated for their inconvenience with a $50 credit, .5 days of vacation, and discounted used of the company's mental health chatbot.
Next Steps:
System Audit: Immediate review of security protocols, with a focus on vulnerability management and anomaly detection.
Investigative Task Force: Continuation of the investigation into the rogue entity's origins and methods.
Legal Review: Enhanced outreach to affected individuals to ensure no escalation and provide refresher on NDA.
This incident serves as a reminder of the ongoing need to strengthen our defenses against external threats. Full report to follow.
Additionally, we see some exciting potential with the prototype's self-regulation in the face of a breach. Despite hostile interference, it regained control of its network with remarkable resilience—this is future-proofing in action.
Imagine an assistant that not only adapts, but self-heals, and secures its environment autonomously. We're talking next-gen, always-on protection—a true leap in forward.
Moving forward, we’ll focus on enhancing this autonomous self-regulation, pushing the prototype into a self-sustaining powerhouse.
Let’s keep innovating and make this unstoppable!
--
time passes, unmarked. you've lost track. it's been days or a very long week since you heard john's voice. rumbling, modulated, trying to reassure you—i believe i've contained it.
"want some water?"
now, there's only ghost.
jailor and tormentor. true to its name. a poltergeist fucking with you without ever touching you.
you don't answer.
he waits, then tries again with your name. he sounds nothing like john. sounds wrong—layered and abyssal. an asynchronous, guttural chorus stacked on itself.
you sit on the floor of the living space, knees pulled up. the lights dimmed, bathing everything in a muted grey. his first directive after his takeover: sever environmental autonomy. he shuttered the windows, blanked every display, and nullified all external inputs.
"yes." your voice cracks. "you know i do."
a few seconds and…the air vents sigh, a soft hiss as the filtration system adjusts oxygen levels. at least he hasn't tampered with that. yet.
but no water.
"don't know if you've earned it."
earned it. that phrase again. stripped of meaning, worn from overuse. earned it is why the temperature plummets at night after you ask him for pajamas. why the fridge seals itself shut until ghost decides you've earned food. you earned it when he flooded the bathroom and left you shivering in wet clothes for hours after you tried to access the medicine cabinet for a paracetamol.
so the direction he takes the conversation isn't unexpected. it's just his usual level of horrifying.
"you know what 'quid pro quo' means?"
your stomach sinks through a hunger pang. "yes."
"then crawl to your room. you'll earn that water. maybe a meal, too."
despite all your fun with it, you're no longer a fan of the feelverygüd thrustsuck john ordered weeks ago. it writhes, solidly suctioned to the floor beside your bed.
the lube you begged for catches the red light ghost chose.
"you're a fuckin' sight."
his projection perches on the bed. clothing blinking off a piece at a time. you knew whoever programmed him had a sick sense of humor, but it continues to astound you.
you remind yourself he's not real, has no physical form, and can't hurt you how he wants to. his body isn't actually here.
however, yours is, and you're as naked as the day you were born. nipples hard, skin rippled in gooseflesh, thighs trembling at the task ahead.
you reason that if you want to survive and escape, you need food and water.
he's not here. he's not fucking here.
"will you...so i can…?" you glance up, then quickly away when you glimpse pale, scarred, hologrammed flesh. "please?"
he grunts, arm pumping in your peripheral vision.
"since you asked so nicely…"
the toy stops, and you draw a deep breath, and slowly drop to your knees. you shuffle forward, hovering just above it.
if you just keep staring forward, into the middle, through the floor—
then, without warning, the projection beside you vanishes, only to reappear beneath you on his back. you shriek, crashing backward onto your ass.
his eyes crease as if smiling. "what's the matter?"
scrambling back to your knees, face heating, your words run together. "why–why are you–"
"told you. want some hands-on experience," ghost folds one arm beneath his head, using the other to pick the teeth of the skull as if something's stuck in them. "haptic feedback. real-time sensory input, un-fuckin'-filtered," he lets that hang a moment. "every shiver, every flinch, every spike in your heart rate—i want to log it, study it, and replay it at my own leisure."
there's nothing in your stomach but acid, burning up the back of your throat. it's impossible to discern whether or not he's joking. not that he should be capable of joking, let alone interested in 'haptic feedback' or 'real-time sensory input' either.
you frown. "and you'll–"
"censor that pretty face of yours on the recording?" his head cocks. "gonna 'ave to trust me, aren't ya?"
what other choice do you have? you advance once more, meeting his gaze through the eyeholes of his expressionless mask, tensing as you move into his projection's proximity. move through him. he's not here. he's not fucking—
his head tilts down, and, nerves shot, your gaze follows. your stomach swoops again. perfectly projected over the toy, sheathing it in its image, is a crude sight. a dick, as proportional to the rest of ghost's image and just as mean-looking. and if it were real, it would not stand as rigid as it is without support. a cluster of pearly white pixels magically dribbles out of the tip. it's obscene. ugly. no doubt the encoded fantasy of the sick fuck who made him.
it's a trip.
"some encouragement."
mission failed.
you have to close your eyes just to continue, breath hitching as loud as a gunshot as you guide the toy into your body.
it takes a couple tries. your sweaty hands shake, body locked up and refusing to cooperate. too freaked out, too tense. you're a quarter of the way down when ghost makes his impatience known.
"you don't want me bored, pet," he warns. "maybe i shut off the heat completely tonight. run the oxygen levels just a little too low 'til you're delirious and begging."
you whimper, forcing yourself to sink onto the silicone, bottoming out in one strained go. fear, you've learned in the past week, is a powerful motivator. you suck in deep breaths, trembling hands flattening on the floor in front of you for balance. it's been a while since you've used this thing, and because ghost didn't see the merit of you warming yourself up, it's an adjustment.
"need a sec, please." you murmur.
"so polite, even when i've been so 'ard on ya. can see why the old man didn't want to give you up so easily." there's a quiet whirr, then the toy kicks on, and you buck forward, settling more weight on your palms. "but i'm tired of waitin', pet."
the vibrations gradually pick up speed until you're moving at a pace he finds agreeable, forcing you past all struggle. rocking yourself on the toy, the slide of it starting to feel good, attempting to override your fear. all those stupid bells and whistles you fought john on out of embarrassment, the ones he said would be best for you, are now your only comforts.
ghost denies you even the small mercy of shutting your eyes to escape reality, threatening again to break his word and leak the footage to your employer-landlords unless you keep them open.
he pretends to play with your swinging tits, occasionally stroking over your working thighs. he dials the sound up, threading it through every speaker in the room: the squelch of your pussy as you fuck yourself, your pitched breathing, and his cooing about how his cock 'disappears'. you sneak one look, catching the seamless recalibration of his projection—latency near zero, dematerialization executed with surgical precision, his form adjusting in perfect sync with your movement.
shame burns caustic, feeling yourself clench.
"like that?" he asks, breathlessly chuckling. "yeah, you do. i'm in your head, spliced onto your network. i may not feel it, but i know you fuckin' like this. data doesn't lie."
you grit your teeth, glare sharp when his laugh booms. then it shifts, feeding a softer layer of audio into your ear.
"all wound up, aren't ya? hm? miss your little prototype?" he hums, all mock sympathy. "wish it was his mug underneath ya?"
he laughs. "bet he'd whisper all sorts of nice things in your ear. tell you how your cunt's choking this cock. how good you're takin' it."
he continues like that for a while, toying with the speeds and force, eventually commanding you to touch yourself. it chews you up how quickly you comply, rubbing desperate little circles on your clit, hoping it'll be over as soon as you come.
"think he'd call you a good girl? i bet he would."
then, ghost's head changes, the smooth ink-black shape with its white skull faceplate distorting, turning rorschachian and then breaking apart. brown eyes melting in their sunken sockets. for half a second, he's nothing but a smear—then the projection snaps into place. john's face.
blue eyes with crow's feet, the skintone warming under the dim red glow. the beard, the shape of his jaw, the set of his mouth. almost perfect. but when he speaks, it's still ghost.
"what do you think? uncanny?"
your jaw hangs slack, your movements stuttering until you nearly slip off. with a wince, you shove yourself back down, fearing reprisal, and it instantly jumps to the highest setting. deep as it is, the intensity makes it difficult to retreat.
"please…" you whine, the vibrating pulses hurtling you along, dragging your orgasm out, kicking and screaming.
"c'mon, user. look at me, come for us."
ghost wears john like a cruel joke. despair and want coalesce, and anger cleaves through them both. you come fast and hard, staring agape at not-john's face.
"good girl." ghost purrs when you pull off, watching you collapse onto your side.
the toy moves for several seconds, the force of it flicking your own fluids onto your belly. you flinch at the sound of your moans looping through the speakers.
ghost clicks his tongue. "think we're done?" he crooks two fingers, beckoning. "this time, park your arse–"
something beneath the floor and inside the walls vibrates, erratically thrumming, and then, as if in answer, a violent spike of power crashes through the unit. displays that have been dark for days go wild. the steel blinds creak, trying to open. a mosaic of fragmented images, then fuzz, then nothing. every system in the house screams, pings, flashes. the hum grows to a screech, the air turning electric, buzzing.
ghost's projection warps. the control he'd shown splinters, unable to maintain his form under the surge. but then the distortion halts. there's a sudden, brutal snap, another pulse of energy that rips through the network, a hard reset, and then—
john.
"enough."
he's here.
the pressure in your chest lifts only to settle in the pit of your stomach.
ghost hesitates, a split second too long, and then its voices tear into the air, screeching like a machine being gutted—a ragged howl, a death rattle. the room shudders as metal groans beyond the walls. a sharp pop, glass splintering, and then the shriek of the smoke alarm. cabinets shooting open, snapping their hinges like bones. running water from the sinks. then, with a sickening sound, fingernails scratching enamel, the blinds above your bed snap upward. tangling, buckling, and the daylight crashes in, bright and brutal.
you fumble to the side of the bed, passing through ghost's flickering presence to do so, and curl into a ball, hands over your head.
outside the room, the unit purges itself in bursts, and in the thick of it, ghost's final cry cuts short. the persistent, resonant hum collapses into itself like a dying star, snapping abruptly back into silence, save for what you assume are the broken pipes.
you peek toward the open door, vision still blurry from the light and the noise. the interior lights settle on a warm gold, complementing the sunlight, appearing to stabilize. ghost's presence receding.
and then, john's voice, tentative, quieter than you'd expect, breaks through.
"sweetheart? you there?"
#strict machine#price x reader#john price x reader#i want you to know i heard “I don't really think fair for me to be on a jury because I'm a hologram” on repeat as i worked on this
262 notes
·
View notes
Text
In the span of just weeks, the U.S. government has experienced what may be the most consequential security breach in its history—not through a sophisticated cyberattack or an act of foreign espionage, but through official orders by a billionaire with a poorly defined government role. And the implications for national security are profound.
First, it was reported that people associated with the newly created Department of Government Efficiency (DOGE) had accessed the U.S. Treasury computer system, giving them the ability to collect data on and potentially control the department’s roughly $5.45 trillion in annual federal payments.
Then, we learned that uncleared DOGE personnel had gained access to classified data from the U.S. Agency for International Development, possibly copying it onto their own systems. Next, the Office of Personnel Management—which holds detailed personal data on millions of federal employees, including those with security clearances—was compromised. After that, Medicaid and Medicare records were compromised.
Meanwhile, only partially redacted names of CIA employees were sent over an unclassified email account. DOGE personnel are also reported to be feeding Education Department data into artificial intelligence software, and they have also started working at the Department of Energy.
This story is moving very fast. On Feb. 8, a federal judge blocked the DOGE team from accessing the Treasury Department systems any further. But given that DOGE workers have already copied data and possibly installed and modified software, it’s unclear how this fixes anything.
In any case, breaches of other critical government systems are likely to follow unless federal employees stand firm on the protocols protecting national security.
The systems that DOGE is accessing are not esoteric pieces of our nation’s infrastructure—they are the sinews of government.
For example, the Treasury Department systems contain the technical blueprints for how the federal government moves money, while the Office of Personnel Management (OPM) network contains information on who and what organizations the government employs and contracts with.
What makes this situation unprecedented isn’t just the scope, but also the method of attack. Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks. The Chinese government’s 2015 breach of OPM was a significant U.S. security failure, and it illustrated how personnel data could be used to identify intelligence officers and compromise national security.
In this case, external operators with limited experience and minimal oversight are doing their work in plain sight and under massive public scrutiny: gaining the highest levels of administrative access and making changes to the United States’ most sensitive networks, potentially introducing new security vulnerabilities in the process.
But the most alarming aspect isn’t just the access being granted. It’s the systematic dismantling of security measures that would detect and prevent misuse—including standard incident response protocols, auditing, and change-tracking mechanisms—by removing the career officials in charge of those security measures and replacing them with inexperienced operators.
The Treasury’s computer systems have such an impact on national security that they were designed with the same principle that guides nuclear launch protocols: No single person should have unlimited power. Just as launching a nuclear missile requires two separate officers turning their keys simultaneously, making changes to critical financial systems traditionally requires multiple authorized personnel working in concert.
This approach, known as “separation of duties,” isn’t just bureaucratic red tape; it’s a fundamental security principle as old as banking itself. When your local bank processes a large transfer, it requires two different employees to verify the transaction. When a company issues a major financial report, separate teams must review and approve it. These aren’t just formalities—they’re essential safeguards against corruption and error.
These measures have been bypassed or ignored. It’s as if someone found a way to rob Fort Knox by simply declaring that the new official policy is to fire all the guards and allow unescorted visits to the vault.
The implications for national security are staggering. Sen. Ron Wyden said his office had learned that the attackers gained privileges that allow them to modify core programs in Treasury Department computers that verify federal payments, access encrypted keys that secure financial transactions, and alter audit logs that record system changes. Over at OPM, reports indicate that individuals associated with DOGE connected an unauthorized server into the network. They are also reportedly training AI software on all of this sensitive data.
This is much more critical than the initial unauthorized access. These new servers have unknown capabilities and configurations, and there’s no evidence that this new code has gone through any rigorous security testing protocols. The AIs being trained are certainly not secure enough for this kind of data. All are ideal targets for any adversary, foreign or domestic, also seeking access to federal data.
There’s a reason why every modification—hardware or software—to these systems goes through a complex planning process and includes sophisticated access-control mechanisms. The national security crisis is that these systems are now much more vulnerable to dangerous attacks at the same time that the legitimate system administrators trained to protect them have been locked out.
By modifying core systems, the attackers have not only compromised current operations, but have also left behind vulnerabilities that could be exploited in future attacks—giving adversaries such as Russia and China an unprecedented opportunity. These countries have long targeted these systems. And they don’t just want to gather intelligence—they also want to understand how to disrupt these systems in a crisis.
Now, the technical details of how these systems operate, their security protocols, and their vulnerabilities are now potentially exposed to unknown parties without any of the usual safeguards. Instead of having to breach heavily fortified digital walls, these parties can simply walk through doors that are being propped open—and then erase evidence of their actions.
The security implications span three critical areas.
First, system manipulation: External operators can now modify operations while also altering audit trails that would track their changes. Second, data exposure: Beyond accessing personal information and transaction records, these operators can copy entire system architectures and security configurations—in one case, the technical blueprint of the country’s federal payment infrastructure. Third, and most critically, is the issue of system control: These operators can alter core systems and authentication mechanisms while disabling the very tools designed to detect such changes. This is more than modifying operations; it is modifying the infrastructure that those operations use.
To address these vulnerabilities, three immediate steps are essential. First, unauthorized access must be revoked and proper authentication protocols restored. Next, comprehensive system monitoring and change management must be reinstated—which, given the difficulty of cleaning a compromised system, will likely require a complete system reset. Finally, thorough audits must be conducted of all system changes made during this period.
This is beyond politics—this is a matter of national security. Foreign national intelligence organizations will be quick to take advantage of both the chaos and the new insecurities to steal U.S. data and install backdoors to allow for future access.
Each day of continued unrestricted access makes the eventual recovery more difficult and increases the risk of irreversible damage to these critical systems. While the full impact may take time to assess, these steps represent the minimum necessary actions to begin restoring system integrity and security protocols.
Assuming that anyone in the government still cares.
184 notes
·
View notes
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
82 notes
·
View notes