#Cybersecurity Risk Assessment Framework
Explore tagged Tumblr posts
Text
Cybersecurity Risk Assessment Framework
Cybersecurity Risk Assessment Framework Introduction: Cybersecurity risk assessment is a critical part of any organization’s risk management strategy. It involves identifying, assessing, and mitigating risks associated with an organization’s information systems to protect against cyber threats. What is a Cyber Risk Assessment? A Cyber Risk Assessment is a process that identifies, assesses, and…

View On WordPress
#Benefits Of Cybersecurity Risk Assessment Framework#Cybersecurity Risk Assessment Framework#What is a Cyber Risk Assessment?#What Is Cybersecurity Risk Assessment Framework
0 notes
Text
Cybersecurity and Manufacturing: Safeguarding the Digital Factory
Cybersecurity and Manufacturing: Safeguarding the Digital Factory Cybersecurity and Manufacturing Introduction to Cybersecurity in Manufacturing The Rise of Smart Manufacturing Cybersecurity and Manufacturing – Welcome to the Fourth Industrial Revolution—a world where machines talk, factories think, and decisions are data-driven. Known as Industry 4.0, this transformation is redefining…
#cyber security for financial services#cyber security in manufacturing industry ppt#cyber security threats in manufacturing industry#cybersecurity and manufacturing#cybersecurity and manufacturing examples#cybersecurity banking#cybersecurity in manufacturing information technology security companies#explain about cyber risk assessment#healthcare cyber security#ics cyber security#iec 62443#industrial control cyber security#industrial cyber security#manufacturing cyber attacks 2024#manufacturing cybersecurity#manufacturing cybersecurity jobs#manufacturing cybersecurity statistics#nist cybersecurity framework#ot cyber security
1 note
·
View note
Text
There are around 11,000 satellites orbiting Earth, and it is estimated that at least 50,000 more will be launched in the next decade. There are also exploration instruments, resupply vessels, and complexes like the International Space Station. But who regulates all this activity in space? In the absence of clear regulations, the European Union has proposed the Space Act, a set of measures that seeks to make the European space sector a cleaner, safer, and more competitive environment, both domestically and in international markets.
The European Commission maintains that current space regulation within the eurozone is fragmented into various national approaches, which slows innovation, reduces European participation in the global market, and generates additional costs.
According to the EU executive, the draft legislation will boost the expansion of companies in the bloc into other markets, as it is designed to simplify procedures, protect assets in orbit, and promote a level playing field. The regulation focuses on three key pillars:
Safety: Faced with more than 128 million pieces of debris circulating in space, the Space Act introduces measures to optimize the tracking of objects in orbit and prevent the generation of new debris. These include specific requirements to ensure the disposal of satellites at the end of their lives.
Resilience: The commission warns that space infrastructures are facing increasing cyber threats, capable of compromising the operation of satellites or disrupting essential services. The proposal therefore requires all operators to conduct risk assessments throughout the lifecycle of their in-orbit systems. They will also be required to submit detailed incident reports and adopt updated cybersecurity standards.
Sustainability: As space activities increase, it becomes crucial to efficiently manage resources, CO2 emissions, and waste. The new legal framework establishes common standards to monitor these impacts and define preventive or corrective measures.
In a statement, the commission stresses that “the new rules would apply to both EU and national space assets, as well as to non-EU operators offering services in Europe. Regulatory requirements will be adapted to company size and level of maturity, and measured against the risks involved.”
Europe Wants to Lead the Space Economy
Recognizing that compliance with the regulatory framework will entail considerable costs for the industry, the commission proposes a series of support measures, such as strengthening technical capabilities, facilitating access to testing facilities, and assistance with the authorization process. These measures are intended to particularly benefit startups and small and medium-sized businesses in the sector.
The commission also presented a new vision to boost the European space economy, with the aim of responding to the global dynamics of the sector, growing international competition, and emerging geopolitical challenges.
Space, the agency argues, is a fast-growing sector that contributes significantly to the bloc’s competitiveness. It encompasses both the industry dedicated to the manufacturing and operation of space systems and a wide range of services that impact areas such as climate, environment, agriculture, energy, transportation, insurance, banking, security, and defense.
The proposed economic strategy includes more than 40 concrete actions to ensure Europe’s strong participation in the global space market, strengthen its autonomy, and consolidate its technological advantage. Among the initiatives is the creation of the European Space Team, a high-level forum that will bring together key players in the ecosystem, such as the European Space Agency and the European Union Agency for the Space Program, with the aim of coordinating efforts and unifying capabilities across the bloc. In addition, the commission has planned a number of investment mechanisms to boost its space economy.
Starting this year, the commission will develop a specific methodology to monitor the EU’s competitiveness and market share in the global space economy.
“Europe’s leadership in space must be rooted in sovereignty, security, and strategic foresight. With the EU Space Act we are taking a bold step to ensure that our space infrastructure is resilient, our innovation ecosystem is empowered, and our autonomy in critical technologies is secured for generations to come,” concluded Henna Virkkunen, executive vice president of the European Commission for Technological Sovereignty, Security, and Democracy.
3 notes
·
View notes
Text
Prevent Command Injection in Symfony: Secure Your Code
Symfony is a powerful PHP framework trusted by thousands of developers, but like any framework, it's not immune to security threats. One of the most dangerous—and often overlooked—threats is a Command Injection Attack.

In this blog post, we’ll break down what a command injection attack is, how it can be exploited in a Symfony application, and—most importantly—how to prevent it. We’ll also include code examples and offer you a Website Vulnerability Scanner online free to scan your website for vulnerabilities like this one.
➡️ Visit Our Blog for More Cybersecurity Posts: 🔗 https://www.pentesttesting.com/blog/
🧨 What is Command Injection?
Command Injection is a type of security vulnerability that allows attackers to execute arbitrary system commands on your server. If user input is improperly sanitized, attackers can exploit functions like exec(), system(), or shell_exec() in PHP.
This can lead to:
Data breaches
Server hijacking
Total application compromise
🐘 Symfony Command Injection Example
Let’s start with a naive Symfony controller that might fall victim to command injection.
❌ Vulnerable Symfony Code
// src/Controller/BackupController.php namespace App\Controller; use Symfony\Component\HttpFoundation\Request; use Symfony\Component\HttpFoundation\Response; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; class BackupController extends AbstractController { public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // ⚠️ Dangerous input $output = shell_exec("mysqldump -u root -psecret mydb > /backups/{$filename}"); return new Response("Backup created: $filename"); } }
If an attacker sets filename=backup.sql;rm -rf /, this code could delete your entire server. Yikes!
🔐 Secure It With Escaping & Whitelisting
Let’s see how we can secure this.
✅ Safe Symfony Version
public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // Sanitize the filename using a whitelist or regex if (!preg_match('/^[\w\-\.]+$/', $filename)) { return new Response("Invalid filename", 400); } $safePath = escapeshellarg("/backups/" . $filename); $output = shell_exec("mysqldump -u root - psecret mydb > $safePath"); return new Response("Backup created: $filename"); }
By using escapeshellarg() and validating the input, we reduce the risk significantly.
🛠️ Automate Detection with Our Free Tool
Want to check if your website is vulnerable to command injection and other critical flaws?
🎯 We’ve built a Free Website Vulnerability Scanner that checks for command injection, XSS, SQLi, and dozens of other issues—all in seconds.
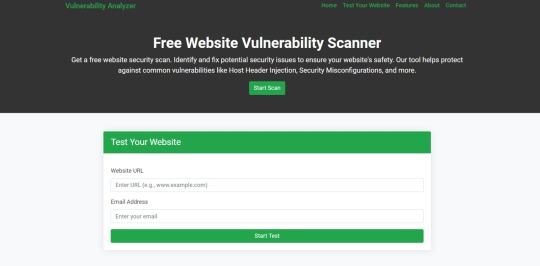
🖼️ Screenshot of our Website Vulnerability Scanner:

Screenshot of the free tools webpage where you can access security assessment tools.
👉 Try it now: https://free.pentesttesting.com/
📋 Sample Output Report
Our scanner doesn’t just find issues—it gives you a detailed, developer-friendly report you can act on.
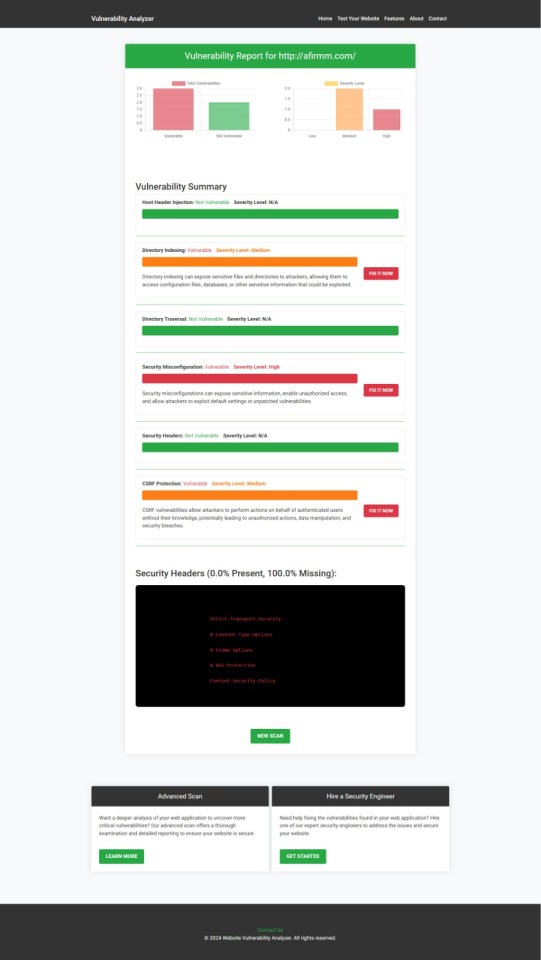
🖼️ Screenshot of a sample scan report from our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
💼 Need Help Fixing It? We've Got You Covered
🔐 Web App Penetration Testing Services If you're looking for expert-level help to secure your Symfony or PHP application, our team is ready to assist.
➡️ Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Are You a Tech Company or Agency?
We offer white-label cybersecurity services so you can resell pentesting to your clients without hiring a full team.
📦 Get the full service suite here: 🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
💌 Stay Ahead of Threats—Subscribe Now!
Don’t miss future posts, case studies, and cybersecurity tips.
📬 Subscribe to our LinkedIn Newsletter
🔁 Final Thoughts
Command injection remains one of the most dangerous web application vulnerabilities. Symfony gives you the tools to secure your app—but only if you use them correctly.
Don’t wait until you’re hacked. Take 2 minutes to scan your website with our free Website Security Scanner tool.
📝 Originally written by the Pentest Testing Corp. team 📌 Visit our blog for more: https://www.pentesttesting.com/blog/
2 notes
·
View notes
Text
Thailand SMART Visa
1.1 Statutory Foundations
Established under Royal Decree on SMART Visa B.E. 2561 (2018)
Amended by Ministerial Regulation No. 377 (2021) expanding eligible sectors
Operates within Thailand 4.0 Economic Model under BOI oversight
1.2 Governance Structure
Primary Authority: Board of Investment (BOI)
Interagency Coordination:
Immigration Bureau (visa issuance)
Digital Economy Promotion Agency (tech qualifications)
Ministry of Higher Education (academic validation)
Technical Review Committees:
12 sector-specific panels
Investment verification unit
2. Eligibility Criteria & Qualification Pathways
2.1 SMART-T (Experts)
Compensation Thresholds
Base Salary: Minimum THB 200,000/month (USD 5,800)
Alternative Compensation:
Equity valued at 25% premium
Performance bonuses (capped at 40% of base)
2.2 SMART-E (Entrepreneurs)
Startup Metrics
Revenue Test: THB 10M+ ARR
Traction Test: 50,000 MAU
Funding Test: Series A (THB 25M+)
Accelerator Requirements:
DEPA-certified programs
Minimum 6-month incubation
3. Application Process & Technical Review
3.1 Document Authentication Protocol
Educational Credentials:
WES/IQAS evaluation for foreign degrees
Notarized Thai translations (MFA-certified)
Employment Verification:
Social security cross-check
Three professional references
3.2 Biometric Enrollment
Facial Recognition: 12-point capture system
Fingerprinting: 10-print electronic submission
Iris Scanning: Optional for Diamond tier
4. Privilege Structure & Compliance
4.1 Employment Rights Framework
Permitted Activities:
Primary employment (≥80% time)
Academic collaboration (≤20%)
Advisory roles (max 2 concurrent)
Restrictions:
Local employment outside specialty
Political activities
Unapproved commercial research
4.2 Dependent Provisions
Spousal Work Rights:
General employment permitted
No industry restrictions
Child Education:
25% tuition subsidy
University admission priority
4.3 Mobility Features
Airport Processing:
Dedicated SMART lanes at 6 airports
15-minute clearance guarantee
Re-entry Flexibility:
Unlimited exits
72-hour grace period
5. Sector-Specific Implementations
5.1 Biotechnology
Special Privileges:
Lab equipment duty waivers
Fast-track FDA approval
50% R&D tax deduction
5.2 Advanced Manufacturing
Incentives:
Robotics import tax exemption
Industrial land lease discounts
THB 500K training subsidy
5.3 Digital Infrastructure
Cloud Computing:
VAT exemption on services
30% energy cost reduction
Cybersecurity:
Liability protections
Gov't certification fast-track
6. Compliance & Monitoring
6.1 Continuous Reporting
Quarterly:
Employment verification
Investment maintenance
Annual:
Contribution assessment
Salary benchmarking
6.2 Renewal Process
Documentation:
Updated financials
Health insurance (USD 100K)
Performance metrics
Fees:
THB 10,000 renewal
THB 1,900 visa stamp
7. Emerging Developments
71 2024 Enhancements
Blockchain Specialist Category
Climate Tech Fast-Track
EEC Regional Expansion
7.2 Pending Reforms
Dual Intent Provision
Skills Transfer Mandate
Global Talent Pool
8. Strategic Application Approach
8.1 Pre-Submission Optimization
Compensation Restructuring
Patent Portfolio Development
Professional Endorsements
8.2 Post-Approval Planning
Tax Residence Strategy
Asset Protection
Succession Planning
9. Risk Management
9.1 Common Rejection Reasons
Document Issues (32%)
Qualification Gaps (28%)
Financial Irregularities (19%)
9.2 Operational Challenges
Banking Restrictions
Healthcare Access
Cultural Integration
#thailand#immigration#thai#thaiimmigration#thaivisa#visa#immigrationlawyers#immigrationinthailand#thailandsmartvisa#smartvisa#smartvisainthailand#thaismartvisa
2 notes
·
View notes
Text
Thailand SMART Visa
1.1 Statutory Foundations
Established under Royal Decree on SMART Visa B.E. 2561 (2018)
Amended by Ministerial Regulation No. 377 (2021) expanding eligible sectors
Operates within Thailand 4.0 Economic Model under BOI oversight
1.2 Governance Structure
Primary Authority: Board of Investment (BOI)
Interagency Coordination:
Immigration Bureau (visa issuance)
Digital Economy Promotion Agency (DEPA) for tech qualifications
Ministry of Higher Education for academic validation
Technical Review Committees:
Sector-specific panels (12 industries)
Investment verification unit
2. Eligibility Criteria & Qualification Pathways
2.1 SMART-T (Experts)
Compensation Thresholds
Base Salary: Minimum THB 200,000/month (USD 5,800)
Alternative Compensation:
Equity valued at 25% premium to cash salary
Performance bonuses (capped at 40% of base)
2.2 SMART-E (Entrepreneurs)
Startup Metrics
Revenue Test: THB 10M+ ARR
Traction Test: 50,000 MAU
Funding Test: Series A (THB 25M+)
Accelerator Requirements:
DEPA-certified programs
Minimum 6-month incubation
3. Application Process & Technical Review
3.1 Document Authentication Protocol
Educational Credentials:
WES/IQAS evaluation for foreign degrees
Notarized Thai translations (certified by MFA)
Employment Verification:
Social security cross-check (home country)
Three professional references (direct supervisors)
3.2 Biometric Enrollment
Facial Recognition: 12-point capture system
Fingerprinting: 10-print electronic submission
Iris Scanning: Optional for Diamond tier
4. Privilege Structure & Compliance
4.1 Employment Rights Framework
Permitted Activities:
Primary employment with sponsor (≥80% time)
Academic collaboration (≤20% time)
Advisory roles (max 2 concurrent)
Restrictions:
Local employment outside specialty
Political activities
Unapproved commercial research
4.2 Dependent Provisions
Spousal Work Rights:
General employment permitted
No industry restrictions
Child Education:
25% tuition subsidy at partner schools
University admission priority
4.3 Mobility Features
Airport Processing:
Dedicated SMART lanes at 6 airports
15-minute clearance guarantee
Re-entry Flexibility:
Unlimited exits
72-hour grace period
5. Sector-Specific Implementations
5.1 Biotechnology
Special Privileges:
Lab equipment duty waivers
Fast-track FDA approval
50% R&D tax deduction
5.2 Advanced Manufacturing
Incentives:
Robotics import tax exemption
Industrial land lease discounts
THB 500K training subsidy
5.3 Digital Infrastructure
Cloud Computing:
VAT exemption on services
30% energy cost reduction
Cybersecurity:
Liability protections
Gov't certification fast-track
6. Compliance & Monitoring
6.1 Continuous Reporting
Quarterly:
Employment verification
Investment maintenance
Annual:
Contribution assessment
Salary benchmarking
6.2 Renewal Process
Documentation:
Updated financials
Health insurance (USD 100K)
Performance metrics
Fees:
THB 10,000 renewal
THB 1,900 visa stamp
7. Emerging Developments
7.1 2024 Enhancements
Blockchain Specialist Category
Climate Tech Fast-Track
EEC Regional Expansion
7.2 Pending Reforms
Dual Intent Provision
Skills Transfer Mandate
Global Talent Pool
8. Strategic Application Approach
8.1 Pre-Submission Optimization
Compensation Restructuring
Patent Portfolio Development
Professional Endorsements
8.2 Post-Approval Planning
Tax Residence Strategy
Asset Protection
Succession Planning
9. Risk Management
9.1 Common Rejection Reasons
Document Issues (32%)
Qualification Gaps (28%)
Financial Irregularities (19%)
9.2 Operational Challenges
Banking Restrictions
Healthcare Access
Cultural Integration
#thailand#immigration#visa#immigrationinthailand#immigrationlawyers#thai#thaivisa#immigrationlawyersinthailand#thailandsmartvisa#smartvisa#smartvisainthailand#thaismartvisa
2 notes
·
View notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Why Internal Audits Are the Backbone of Effective Risk Management
In an era where organizations face increasing complexities and challenges, risk management is not just a business necessity — it’s a cornerstone of sustainability and success. Internal audits play a critical role in this landscape, acting as the backbone of effective risk management. They go beyond compliance, offering actionable insights that help organizations identify vulnerabilities, strengthen internal controls, and mitigate risks effectively.
If you’re looking to gain practical expertise in internal audits and build a successful career in auditing, explore the Master Blaster of Internal Audit Course. This comprehensive course equips you with in-depth knowledge and real-world skills to become a leader in the field.
What is an Internal Audit?
Internal audits are systematic, independent evaluations of an organization’s processes, internal controls, and risk management practices. Unlike external audits that focus on regulatory compliance, internal audits are proactive, focusing on process improvement, efficiency, and risk mitigation.
By bridging the gap between governance and operations, internal audits provide organizations with a clear roadmap to address risks and achieve their objectives. Go through the following website- https://www.catusharmakkar.com/ to gain practical knowledge about auditing.
How Internal Audits Strengthen Risk Management
1. Identifying and Addressing Risks Proactively
Internal audits act as an organization’s radar, identifying potential risks before they escalate.
• Auditors evaluate critical areas, such as operations, IT systems, and compliance frameworks, to uncover vulnerabilities.
• For instance, an internal IT audit may identify weak cybersecurity measures that could lead to data breaches.
By addressing these risks proactively, organizations can prevent financial losses, reputational damage, and operational disruptions.
2. Evaluating the Effectiveness of Internal Controls
Strong internal controls are the foundation of risk mitigation, but their effectiveness often depends on regular evaluation.
• Internal audits assess whether controls are properly designed, implemented, and operating as intended.
• For example, an audit of financial reporting processes may reveal gaps in approval workflows that could lead to fraud or errors.
Regular evaluations help organizations ensure their controls remain aligned with their risk appetite and evolving business environment.
3. Ensuring Regulatory Compliance
Regulatory non-compliance is one of the biggest risks organizations face today. Fines, penalties, and reputational harm can result from inadequate adherence to laws like GST regulations or data privacy standards.
• Internal audits regularly review compliance processes to ensure they meet statutory requirements.
• For example, an internal audit might assess whether GST returns are filed accurately and on time.
By staying ahead of regulatory requirements, businesses can avoid costly penalties and maintain stakeholder confidence.
4. Enhancing Operational Efficiency
Internal audits are not just about identifying risks — they’re also about improving processes.
• Auditors provide recommendations that streamline operations, reduce redundancies, and optimize resource utilization.
• For instance, a supply chain audit may identify inefficiencies in procurement that increase costs.
This dual focus on risk mitigation and process improvement makes internal audits invaluable for achieving organizational efficiency.
5. Boosting Stakeholder Confidence
When stakeholders — be it management, investors, or employees — know that an organization’s risks are well-managed, their trust increases.
• Internal audits provide assurance that the organization’s governance and risk management frameworks are strong.
• For example, timely and transparent audit reports can reassure investors of a company’s financial health and operational integrity.
This trust translates into better business relationships and improved market reputation.
How to Excel in Internal Auditing?
Mastering internal audits requires a blend of theoretical knowledge and practical skills. Here’s how you can get started:
1. Understand Risk Management Frameworks: Familiarize yourself with globally accepted frameworks like COSO and ISO 31000.
2. Gain Hands-on Experience: Work on real-world audit assignments to develop a practical understanding of risk assessment and internal controls.
3. Stay Updated: The regulatory landscape evolves constantly. Keeping up with changes in tax laws, compliance standards, and industry best practices is crucial.
4. Invest in Professional Training: Enroll in courses like the Master Blaster of Internal Audit Course to gain practical insights and enhance your skills.
TIP:- To truly master internal auditing, you need more than just theoretical knowledge — you need practical expertise. The Master Blaster of Internal Audit Course is designed to help aspiring auditors and professionals excel in the field by covering:
• Comprehensive risk assessment frameworks.
• Real-world case studies and hands-on scenarios.
• Tools and techniques for internal controls evaluation.
• Strategies for effective communication of audit findings.
By enrolling in this course, you’ll gain the confidence and skills to handle internal audits with precision and become a trusted advisor in your organization.
Conclusion
Internal audits are the backbone of effective risk management, providing organizations with the insights they need to mitigate risks, enhance controls, and drive efficiency. For aspiring auditors and professionals looking to master this critical skill, investing in quality training is essential. Start your journey to becoming an expert in internal auditing today with the Master Blaster of Internal Audit Course. Gain the skills, knowledge, and confidence to navigate the complexities of risk management and make a meaningful impact in your career.
2 notes
·
View notes
Text
Cynthia Kayle Shares Key Strategies for Effective Threat Mitigation

Introduction
Threat mitigation is an essential aspect of any organization’s security strategy. While the identification of emerging threats is crucial, organizations must also develop robust mitigation strategies to prevent potential risks from escalating into major incidents. Effective threat mitigation requires a comprehensive approach, blending proactive measures, real-time response, and long-term security strategies to reduce vulnerabilities across all operational areas.
This article explores key strategies for effective threat mitigation, offering actionable steps for organizations to safeguard their operations, personnel, and reputation from potential harm.
1. Establish a Risk Management Framework
A strong risk management framework serves as the foundation for identifying, analyzing, and mitigating risks in an organized and structured manner. This framework should integrate security, compliance, and operational requirements, ensuring that all potential threats are addressed at the organizational level.
Actionable Steps:
Create a Risk Management Team: Assemble a dedicated team to assess, identify, and respond to risks across the organization. This team should include experts from security, IT, legal, and compliance.
Develop a Risk Register: Maintain a comprehensive risk register that tracks all identified threats, their potential impact, likelihood, and mitigation strategies. This register should be continuously updated as new risks emerge.
Prioritize Risks Based on Impact: Use risk assessment tools to evaluate the severity of each risk and prioritize mitigation efforts accordingly. Focus on threats with the highest potential impact on business continuity.
Reference:
Full URL: https://www.iso.org/iso-31000-risk-management.html
2. Implement Security Best Practices and Policies
Establishing security policies and best practices helps to create a standardized approach to threat mitigation. These policies should cover everything from data protection to physical security, and should be enforced across the organization to ensure consistency.
Actionable Steps:
Develop Comprehensive Security Policies: Draft detailed security policies covering access controls, incident response, cybersecurity, and physical security. Ensure these policies are aligned with industry standards and regulatory requirements.
Enforce Compliance: Regularly conduct audits to ensure that policies are being followed. Implement training programs for employees to keep them informed about security policies and their role in risk mitigation.
Review and Update Policies: Conduct regular reviews of security policies to account for new threats, emerging technologies, and regulatory changes. Update policies as necessary to stay ahead of evolving risks.
Reference:
Full URL: https://www.nist.gov/cyberframework
3. Leverage Technology for Threat Detection and Response
Technology plays a crucial role in identifying and mitigating threats quickly and efficiently. From advanced monitoring systems to AI-driven analytics, technology can significantly improve the effectiveness of your threat mitigation strategies.
Actionable Steps:
Invest in Threat Detection Tools: Use advanced tools like intrusion detection systems (IDS), endpoint detection and response (EDR), and firewalls to monitor your network in real-time and detect potential threats as they arise.
Leverage Artificial Intelligence (AI): Implement AI-powered tools such as Darktrace or Vectra AI that can automatically detect anomalous behavior and mitigate threats before they escalate.
Deploy Automated Response Systems: Set up automated incident response systems that can take immediate action when a threat is detected, such as isolating infected systems, blocking suspicious IP addresses, or initiating alerts.
Reference:
Full URL: https://www.darktrace.com
Full URL: https://www.vectra.ai
4. Foster a Culture of Security Awareness
Emerging threats often stem from human error or lack of awareness within the organization. To mitigate this, building a security-aware culture is crucial. Employees must be educated on recognizing suspicious activity and adhering to security protocols.
Actionable Steps:
Conduct Regular Security Training: Provide ongoing training sessions for employees, covering topics such as phishing prevention, data protection, and password security.
Simulate Real-Life Scenarios: Run security awareness drills to simulate common attack scenarios like phishing emails or data breaches. This will help employees recognize and respond to threats effectively.
Encourage Reporting: Create a clear process for employees to report suspicious activity or potential security breaches. Ensure that they feel empowered to speak up without fear of repercussions.
Reference:
Full URL: https://www.sans.org/cyber-security-skills-training/
5. Establish Incident Response and Recovery Plans
A well-defined incident response plan (IRP) is crucial for quickly addressing and mitigating the impact of a security breach or attack. Equally important is having a recovery plan to restore operations and minimize downtime.
Actionable Steps:
Develop an Incident Response Plan (IRP): Outline clear steps for responding to various types of security incidents, including data breaches, malware infections, and physical security threats. Include protocols for containment, investigation, and recovery.
Test and Update the IRP Regularly: Conduct regular simulations and tabletop exercises to test the effectiveness of the IRP. Update the plan as necessary to account for new threats and organizational changes.
Create a Business Continuity Plan (BCP): Develop a business continuity plan that includes disaster recovery procedures and ensures the organization can continue operating in the event of a major security incident.
Reference:
Full URL: https://csrc.nist.gov/publications/detail/sp/800-61/rev-2/final
Conclusion
Effective threat mitigation requires a holistic approach that integrates risk management, advanced technology, employee awareness, and well-defined response plans. By employing these strategies, organizations can proactively address threats, reducing the potential for damage and ensuring business continuity in the face of security challenges.
Adopting these measures will enhance your organization's ability to not only identify emerging threats but also effectively mitigate them before they escalate into larger problems.
References:
Full URL: https://www.iso.org/iso-31000-risk-management.html
Full URL: https://www.nist.gov/cyberframework
Full URL: https://www.darktrace.com
Full URL: https://www.vectra.ai
Full URL: https://www.sans.org/cyber-security-skills-training/
Full URL: https://csrc.nist.gov/publications/detail/sp/800-61/rev-2/final
#cynthia kayle#RiskMitigation#SecurityExpert#ThreatManagement#CommunityProtection#CrisisManagement#StrategicSecurity#SafetyPrograms#IntelligenceDriven#SecurityConsulting
1 note
·
View note
Text
Building a Robust Data Governance Framework: Best Practices and Key Considerations

A good framework for data governance compliance assists organizations in ensuring data security. As a result, they can combat cybersecurity risks and fulfill regulatory requirements for responsible enterprise data operations. This post will focus on building a relevant, outcome-oriented data governance framework and strategy.
A comprehensive strategy will help protect an organization’s digital assets from different data breaches. Global brands want to avoid reputational damage and regulatory penalties by picking up governance initiatives. However, they seek reliable compliance approaches to maximize the value of data. That is why they want to know how to foster data etiquette for accuracy, timely access to insights, and relevance to business decisions.
Best Practices and Key Considerations for Building an Effective Data Governance Framework
1. Clearly Communicating Process Objectives and Data Ownership
Before a data governance framework is implemented, the objectives need to be clearly defined. What is the organization aiming to achieve by employing a data governance company? Some objectives may include the following.
- better quality of information,
- regulatory compliance,
- data-driven decision-making (DDDM).
These goals will determine the governance framework’s structure.
It also becomes very important to define data asset ownership. The data governance team, led by a data governance officer (DGO), must be held responsible for this. Those data professionals will develop data access and usage policies. They will also monitor data quality and address data-related issues across the entire organization.
2. Drafting Comprehensive Data Protection and Anti-Espionage Policies
A good data governance framework is based on well-articulated policies and standards. Those documents will guide data solutions and management practices, helping the firms and their suppliers. Such policies should define the most important compliance areas.
Considerations must include unbiased data classification and 24/7 security incident tracking. Moreover, privacy assurance assessments may be conducted. A broader data lifecycle management (DLM) vision can further streamline governance compliance efforts. Companies must also establish user permission standards. They will help allow access to data only if authorized personnel submit requests to their respective superiors. Similar access controls help prevent corporate espionage actors from entering IT systems and compromising sensitive business intelligence.
The policies developed should be flexible. After all, you will need to modify business governance frameworks. Otherwise, you cannot keep up with the regulators’ amendments to applicable laws.
3. Focus on Data Quality and Integrity
Ensuring data quality and integrity is very fundamental to data governance. Remember, inaccurate data leads to poor decisions. It inevitably results in misaligned strategies, causing inefficiencies in business activities. Therefore, data validation rules must be implemented. You want to encourage regular integrity audits based on those rules. Furthermore, adequate data cleansing practices will help ensure businesses’ dataset accuracy and reliability.
Consider data stewardship programs. It involves a competent individual or a team assuming responsibility for the quality of specific data assets.
4. Leverage Technology for Scalability and Automation
Data management can be enhanced by using modern technologies. Newer data governance platforms, artificial intelligence, and automation tools will aid you in improving governance compliance. These technologies will, therefore, make it easier to automate the tracking of data changes. Many tools also enforce governance policies. So, users can bypass the manual work of optimizing data protection measures based on the organization’s growth.
Conclusion
Building a strong data governance framework will demand definite objectives. Leaders will want to develop cross-functional collaborative environments to promote data ethics and integrity policies.
Accordingly, the best compliance assurance practices involve defining data ownership, ensuring data quality, and using novel technology. These measures would help organizations protect their data assets. Their superior compliance levels also make them attractive to more investors.
A robust data governance framework and compliance strategy does not just mitigate risk. Rather, it would deliver strategic success while respecting regulatory and consumer values concerning privacy.
2 notes
·
View notes
Text
Key Programming Languages Every Ethical Hacker Should Know
In the realm of cybersecurity, ethical hacking stands as a critical line of defense against cyber threats. Ethical hackers use their skills to identify vulnerabilities and prevent malicious attacks. To be effective in this role, a strong foundation in programming is essential. Certain programming languages are particularly valuable for ethical hackers, enabling them to develop tools, scripts, and exploits. This blog post explores the most important programming languages for ethical hackers and how these skills are integrated into various training programs.
Python: The Versatile Tool
Python is often considered the go-to language for ethical hackers due to its versatility and ease of use. It offers a wide range of libraries and frameworks that simplify tasks like scripting, automation, and data analysis. Python’s readability and broad community support make it a popular choice for developing custom security tools and performing various hacking tasks. Many top Ethical Hacking Course institutes incorporate Python into their curriculum because it allows students to quickly grasp the basics and apply their knowledge to real-world scenarios. In an Ethical Hacking Course, learning Python can significantly enhance your ability to automate tasks and write scripts for penetration testing. Its extensive libraries, such as Scapy for network analysis and Beautiful Soup for web scraping, can be crucial for ethical hacking projects.
JavaScript: The Web Scripting Language
JavaScript is indispensable for ethical hackers who focus on web security. It is the primary language used in web development and can be leveraged to understand and exploit vulnerabilities in web applications. By mastering JavaScript, ethical hackers can identify issues like Cross-Site Scripting (XSS) and develop techniques to mitigate such risks. An Ethical Hacking Course often covers JavaScript to help students comprehend how web applications work and how attackers can exploit JavaScript-based vulnerabilities. Understanding this language enables ethical hackers to perform more effective security assessments on websites and web applications.
Biggest Cyber Attacks in the World
youtube
C and C++: Low-Level Mastery
C and C++ are essential for ethical hackers who need to delve into low-level programming and system vulnerabilities. These languages are used to develop software and operating systems, making them crucial for understanding how exploits work at a fundamental level. Mastery of C and C++ can help ethical hackers identify and exploit buffer overflows, memory corruption, and other critical vulnerabilities. Courses at leading Ethical Hacking Course institutes frequently include C and C++ programming to provide a deep understanding of how software vulnerabilities can be exploited. Knowledge of these languages is often a prerequisite for advanced penetration testing and vulnerability analysis.
Bash Scripting: The Command-Line Interface
Bash scripting is a powerful tool for automating tasks on Unix-based systems. It allows ethical hackers to write scripts that perform complex sequences of commands, making it easier to conduct security audits and manage multiple tasks efficiently. Bash scripting is particularly useful for creating custom tools and automating repetitive tasks during penetration testing. An Ethical Hacking Course that offers job assistance often emphasizes the importance of Bash scripting, as it is a fundamental skill for many security roles. Being proficient in Bash can streamline workflows and improve efficiency when working with Linux-based systems and tools.
SQL: Database Security Insights
Structured Query Language (SQL) is essential for ethical hackers who need to assess and secure databases. SQL injection is a common attack vector used to exploit vulnerabilities in web applications that interact with databases. By understanding SQL, ethical hackers can identify and prevent SQL injection attacks and assess the security of database systems. Incorporating SQL into an Ethical Hacking Course can provide students with a comprehensive understanding of database security and vulnerability management. This knowledge is crucial for performing thorough security assessments and ensuring robust protection against database-related attacks.
Understanding Course Content and Fees
When choosing an Ethical Hacking Course, it’s important to consider how well the program covers essential programming languages. Courses offered by top Ethical Hacking Course institutes should provide practical, hands-on training in Python, JavaScript, C/C++, Bash scripting, and SQL. Additionally, the course fee can vary depending on the institute and the comprehensiveness of the program. Investing in a high-quality course that covers these programming languages and offers practical experience can significantly enhance your skills and employability in the cybersecurity field.
Certification and Career Advancement
Obtaining an Ethical Hacking Course certification can validate your expertise and improve your career prospects. Certifications from reputable institutes often include components related to the programming languages discussed above. For instance, certifications may test your ability to write scripts in Python or perform SQL injection attacks. By securing an Ethical Hacking Course certification, you demonstrate your proficiency in essential programming languages and your readiness to tackle complex security challenges. Mastering the right programming languages is crucial for anyone pursuing a career in ethical hacking. Python, JavaScript, C/C++, Bash scripting, and SQL each play a unique role in the ethical hacking landscape, providing the tools and knowledge needed to identify and address security vulnerabilities. By choosing a top Ethical Hacking Course institute that covers these languages and investing in a course that offers practical training and job assistance, you can position yourself for success in this dynamic field. With the right skills and certification, you’ll be well-equipped to tackle the evolving challenges of cybersecurity and contribute to protecting critical digital assets.
3 notes
·
View notes
Text
Optimizing Cybersecurity with Data Analytics
Data analytics can significantly improve threat detection by sifting through vast amounts of data, including network traffic, user behavior, and system logs. By identifying unusual patterns through machine learning algorithms, organizations can automate anomaly detection, thus reducing incident response times.
Furthermore, risk assessment becomes more effective with data analytics, allowing organizations to evaluate their cybersecurity posture. By analyzing vulnerabilities and potential attack vectors, companies can prioritize their resources to address the most critical areas of concern, enhancing their overall security strategy.
In terms of incident response, data analytics helps cybersecurity teams respond more efficiently. It aids in pinpointing the source of a breach, understanding the extent of the damage, and providing insights for effective remediation.
Predictive analytics plays a vital role as well, using historical data to anticipate future threats and proactively strengthen defenses. By identifying trends that may signal emerging threats, organizations can take timely actions to mitigate risks.
Finally, continuous monitoring through data analytics ensures real-time surveillance of systems and networks. This proactive approach is essential for promptly detecting and addressing security breaches, creating a robust security framework that not only safeguards sensitive information but also enhances overall operational resilience against cyber threats. Thus, data analytics enhanced cybersecurity measures are crucial for organizations seeking to stay one step ahead of potential cybercriminals.
#DataAnalytics#Cybersecurity#RiskAssessment#MachineLearning#PredictiveAnalytics#ThreatDetection#IncidentResponse#ContinuousMonitoring#DataSecurity#CyberThreats#OperationalResilience#SecurityStrategy#AnomalyDetection#InformationSecurity#ProactiveDefense
2 notes
·
View notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
How often should Dutch organizations renew ISO 22301 Certification in Netherlands?

What is ISO 22301 Certification in Netherlands?
ISO 2230 certification in Netherlands is the worldwide standard for Trade Coherence Administration Frameworks (BCMS). It gives a system for figuring out potential dangers, minimizing peril, and making beyond any doubt that basic commercial ISO 22301 consultant in Netherlands undertaking capabilities proceed all through and after disruptions.
In the Dutch commerce display, ISO 22301 Certification indicates that an organization is given operational strength, danger control, and partner assurance.
Why is ISO 22301 Vital for Dutch Organizations?
The Netherlands is generally interconnected, carefully developed, and financially diverse. This makes commercial endeavor coherence a key need. ISO 22301 consultant in Netherlands underpins this via:
Enhancing readiness for crises or disruptions
Ensuring continuous offerings for clients and stakeholders
Supporting compliance with EU rules and Dutch criminal frameworks
Aligning with the chance administration and supportability dreams
Reinforcing insignia acknowledgment and commercial center competitiveness
Who Ought to Get ISO 22301 Certification interior the Netherlands?
ISO 22301 consultant services in Netherlands is profitable ISO 22301 consultant in Netherlands for any employer—big or small—but especially for:
Financial educate and scope businesses
IT carriers and records ISO 22301 auditor in Netherlands facilities
Logistics and provide chain groups
Healthcare suppliers and hospitals
Government organizations and open division offerings
Energy, telecom, and utility companies
Benefits of ISO 22301 Certification interior the Netherlands
Minimize operational disturbance throughout emergencies
Improve danger moderation and recuperation strategies
Comply with the benefactor, legally binding, and administrative necessities
Construct ISO 22301 auditor in Netherlands partner ISO 22301 consultant services in Netherlands self-affirmation and brand trust
Progress inside coordination, communication, and decision-making
Pick up a competitive region in domestic ISO 22301 auditor in Netherlands and around the world markets
How to Get ISO 22301 Certified interior the Netherlands
The certification process, by and large, takes after these steps:
1. Gap Examination: Evaluate display day hours as restricted to ISO 22301 requirements
2. Documentation: Create rules, coherence plans, chance checks, and methods
3. Implementation: Prepare a bunch of laborers, run recreations, and establishment the coherence framework
4. Internal Review: Assess the adequacy of the system.
5. Management Survey: Senior pioneers examine and refine the BCMS.
6. External Review: Certification outline assessments, compliance, and inconveniences of the certificate
Reports Required for ISO 22301 Certification
Business progression scope and scope
Risk tests and commerce impact examinations (BIA)
Incident reaction and rebuilding plans
Communication conventions for calamity control
Training and checking out information
Compliance documentation with nearby and EU regulations
Businesses in the Netherlands That Benefit from ISO 22301
1. Finance & Keeping money: Secure touchy exchanges and client statistics
2. Information Innovation: Guarantee benefit uptime and cybersecurity resilience
3. Healthcare: Ensure coherence of quiet care amid emergencies
4. Transportation & Coordination: Oversee convey chain disturbances correctly
5. Government Administrations: Keep up open carrier conveyance and straightforwardness
Why Factocert for ISO 22301 Certification in Netherlands ?
We provide the best ISO Consultants in Netherlands who are knowledgeable and provide the best solutions. Kindly contact us at [email protected]. ISO Certification consultants in Netherlands and ISO auditors in Netherlands work according to ISO standards and help organizations implement ISO Certification with proper documentation.
For more information, visit ISO 22301 certification in Netherlands
0 notes
Text
Following New Federal Laws, Corporate Auditing in the UAE Increased Its Focus on Risk-Based Audits

Introduction In recent years, corporate auditing in the UAE has undergone a significant transformation. Prompted by the introduction of new federal laws—particularly Federal Decree-Law No. 41 of 2023 regulating the accounting and auditing profession—the landscape now emphasizes a more strategic, risk-based auditing approach. This evolution is reshaping how businesses in the UAE approach compliance, governance, and financial transparency.
The Shift to Risk-Based Auditing Traditionally, audits in the UAE were compliance-driven, focusing on checking financial records for accuracy and adherence to regulatory frameworks. However, under the influence of global best practices and evolving regulatory requirements, the UAE has adopted risk-based auditing as a key component of modern audit strategies.
Risk-based auditing prioritizes areas of greatest potential impact or vulnerability, whether financial, operational, or reputational. This proactive model allows auditors to better assess and mitigate risks before they escalate.
Regulatory Drivers: Federal Decree-Law No. 41 of 2023 The passing of Federal Decree-Law No. 41 has been a game-changer for corporate auditing in the UAE. The law strengthens oversight of the accounting and auditing profession by enforcing stricter qualifications for auditors, increasing audit quality standards, and mandating registration with the Ministry of Economy.
The law also encourages auditing firms to adopt methodologies that align with International Auditing Standards (ISA), which inherently favor a risk-based approach. As a result, companies are now required to present not only accurate financial data but also evidence of internal controls and risk management strategies.
Implications for UAE Businesses For businesses operating in the UAE, this shift demands a higher level of preparedness. Companies must now:
Conduct regular internal risk assessments
Strengthen internal audit functions
Maintain comprehensive documentation of financial and operational controls
Stay up to date with auditing standards and regulatory updates
The increased scrutiny has pushed firms to prioritize corporate governance, data transparency, and financial discipline.
Opportunities for Auditors and Firms With corporate auditing UAE evolving, audit professionals have the opportunity to add greater value. By focusing on strategic risks—such as cybersecurity, regulatory compliance, and ESG factors—auditors can become integral advisors to senior leadership and boards of directors.
Audit firms that embrace this change and invest in technology (AI, data analytics, blockchain) will not only remain competitive but will also play a critical role in shaping the next generation of corporate oversight in the UAE.
Conclusion The UAE’s regulatory reforms have propelled a major shift in the audit profession—from static compliance checks to dynamic, risk-aware strategies. As the landscape continues to evolve, both auditors and businesses must stay agile and informed. In the era of corporate auditing UAE, risk-based audits are not just a requirement—they're a strategic imperative.
#Audit services in UAE#UAE audit firm#Internal audit UAE#Financial auditing UAE#UAE accounting services#Audit firms in Dubai#Corporate auditing UAE#Tax audit services UAE#VAT audit UAE#Company audit UAE.
0 notes