#What Is Cybersecurity Risk Assessment Framework
Explore tagged Tumblr posts
Text
Cybersecurity Risk Assessment Framework
Cybersecurity Risk Assessment Framework Introduction: Cybersecurity risk assessment is a critical part of any organization’s risk management strategy. It involves identifying, assessing, and mitigating risks associated with an organization’s information systems to protect against cyber threats. What is a Cyber Risk Assessment? A Cyber Risk Assessment is a process that identifies, assesses, and…

View On WordPress
#Benefits Of Cybersecurity Risk Assessment Framework#Cybersecurity Risk Assessment Framework#What is a Cyber Risk Assessment?#What Is Cybersecurity Risk Assessment Framework
0 notes
Text
Prevent Command Injection in Symfony: Secure Your Code
Symfony is a powerful PHP framework trusted by thousands of developers, but like any framework, it's not immune to security threats. One of the most dangerous—and often overlooked—threats is a Command Injection Attack.

In this blog post, we’ll break down what a command injection attack is, how it can be exploited in a Symfony application, and—most importantly—how to prevent it. We’ll also include code examples and offer you a Website Vulnerability Scanner online free to scan your website for vulnerabilities like this one.
➡️ Visit Our Blog for More Cybersecurity Posts: 🔗 https://www.pentesttesting.com/blog/
🧨 What is Command Injection?
Command Injection is a type of security vulnerability that allows attackers to execute arbitrary system commands on your server. If user input is improperly sanitized, attackers can exploit functions like exec(), system(), or shell_exec() in PHP.
This can lead to:
Data breaches
Server hijacking
Total application compromise
🐘 Symfony Command Injection Example
Let’s start with a naive Symfony controller that might fall victim to command injection.
❌ Vulnerable Symfony Code
// src/Controller/BackupController.php namespace App\Controller; use Symfony\Component\HttpFoundation\Request; use Symfony\Component\HttpFoundation\Response; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; class BackupController extends AbstractController { public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // ⚠️ Dangerous input $output = shell_exec("mysqldump -u root -psecret mydb > /backups/{$filename}"); return new Response("Backup created: $filename"); } }
If an attacker sets filename=backup.sql;rm -rf /, this code could delete your entire server. Yikes!
🔐 Secure It With Escaping & Whitelisting
Let’s see how we can secure this.
✅ Safe Symfony Version
public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // Sanitize the filename using a whitelist or regex if (!preg_match('/^[\w\-\.]+$/', $filename)) { return new Response("Invalid filename", 400); } $safePath = escapeshellarg("/backups/" . $filename); $output = shell_exec("mysqldump -u root - psecret mydb > $safePath"); return new Response("Backup created: $filename"); }
By using escapeshellarg() and validating the input, we reduce the risk significantly.
🛠️ Automate Detection with Our Free Tool
Want to check if your website is vulnerable to command injection and other critical flaws?
🎯 We’ve built a Free Website Vulnerability Scanner that checks for command injection, XSS, SQLi, and dozens of other issues—all in seconds.
🖼️ Screenshot of our Website Vulnerability Scanner:

Screenshot of the free tools webpage where you can access security assessment tools.
👉 Try it now: https://free.pentesttesting.com/
📋 Sample Output Report
Our scanner doesn’t just find issues—it gives you a detailed, developer-friendly report you can act on.
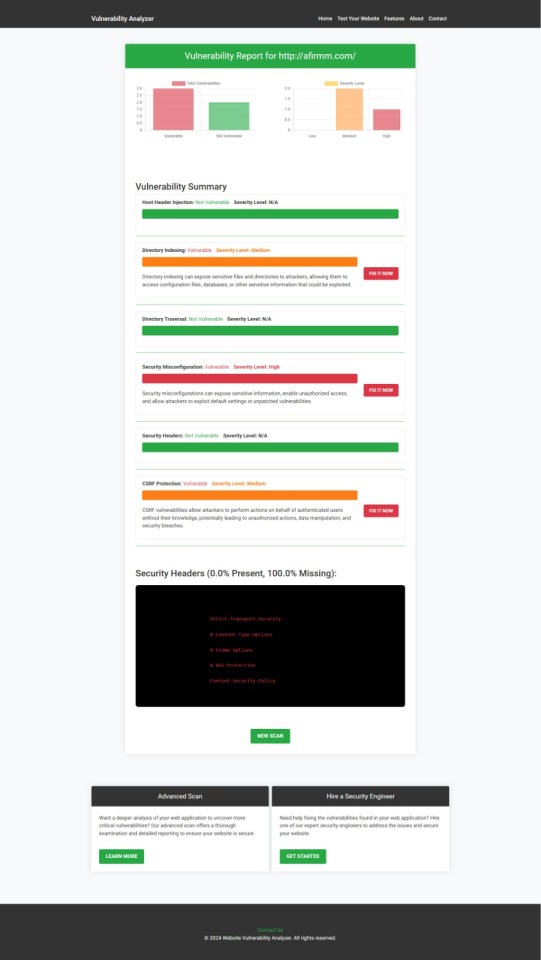
🖼️ Screenshot of a sample scan report from our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
💼 Need Help Fixing It? We've Got You Covered
🔐 Web App Penetration Testing Services If you're looking for expert-level help to secure your Symfony or PHP application, our team is ready to assist.
➡️ Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Are You a Tech Company or Agency?
We offer white-label cybersecurity services so you can resell pentesting to your clients without hiring a full team.
📦 Get the full service suite here: 🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
💌 Stay Ahead of Threats—Subscribe Now!
Don’t miss future posts, case studies, and cybersecurity tips.
📬 Subscribe to our LinkedIn Newsletter
🔁 Final Thoughts
Command injection remains one of the most dangerous web application vulnerabilities. Symfony gives you the tools to secure your app—but only if you use them correctly.
Don’t wait until you’re hacked. Take 2 minutes to scan your website with our free Website Security Scanner tool.
📝 Originally written by the Pentest Testing Corp. team 📌 Visit our blog for more: https://www.pentesttesting.com/blog/
2 notes
·
View notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
Why Internal Audits Are the Backbone of Effective Risk Management
In an era where organizations face increasing complexities and challenges, risk management is not just a business necessity — it’s a cornerstone of sustainability and success. Internal audits play a critical role in this landscape, acting as the backbone of effective risk management. They go beyond compliance, offering actionable insights that help organizations identify vulnerabilities, strengthen internal controls, and mitigate risks effectively.
If you’re looking to gain practical expertise in internal audits and build a successful career in auditing, explore the Master Blaster of Internal Audit Course. This comprehensive course equips you with in-depth knowledge and real-world skills to become a leader in the field.
What is an Internal Audit?
Internal audits are systematic, independent evaluations of an organization’s processes, internal controls, and risk management practices. Unlike external audits that focus on regulatory compliance, internal audits are proactive, focusing on process improvement, efficiency, and risk mitigation.
By bridging the gap between governance and operations, internal audits provide organizations with a clear roadmap to address risks and achieve their objectives. Go through the following website- https://www.catusharmakkar.com/ to gain practical knowledge about auditing.
How Internal Audits Strengthen Risk Management
1. Identifying and Addressing Risks Proactively
Internal audits act as an organization’s radar, identifying potential risks before they escalate.
• Auditors evaluate critical areas, such as operations, IT systems, and compliance frameworks, to uncover vulnerabilities.
• For instance, an internal IT audit may identify weak cybersecurity measures that could lead to data breaches.
By addressing these risks proactively, organizations can prevent financial losses, reputational damage, and operational disruptions.
2. Evaluating the Effectiveness of Internal Controls
Strong internal controls are the foundation of risk mitigation, but their effectiveness often depends on regular evaluation.
• Internal audits assess whether controls are properly designed, implemented, and operating as intended.
• For example, an audit of financial reporting processes may reveal gaps in approval workflows that could lead to fraud or errors.
Regular evaluations help organizations ensure their controls remain aligned with their risk appetite and evolving business environment.
3. Ensuring Regulatory Compliance
Regulatory non-compliance is one of the biggest risks organizations face today. Fines, penalties, and reputational harm can result from inadequate adherence to laws like GST regulations or data privacy standards.
• Internal audits regularly review compliance processes to ensure they meet statutory requirements.
• For example, an internal audit might assess whether GST returns are filed accurately and on time.
By staying ahead of regulatory requirements, businesses can avoid costly penalties and maintain stakeholder confidence.
4. Enhancing Operational Efficiency
Internal audits are not just about identifying risks — they’re also about improving processes.
• Auditors provide recommendations that streamline operations, reduce redundancies, and optimize resource utilization.
• For instance, a supply chain audit may identify inefficiencies in procurement that increase costs.
This dual focus on risk mitigation and process improvement makes internal audits invaluable for achieving organizational efficiency.
5. Boosting Stakeholder Confidence
When stakeholders — be it management, investors, or employees — know that an organization’s risks are well-managed, their trust increases.
• Internal audits provide assurance that the organization’s governance and risk management frameworks are strong.
• For example, timely and transparent audit reports can reassure investors of a company’s financial health and operational integrity.
This trust translates into better business relationships and improved market reputation.
How to Excel in Internal Auditing?
Mastering internal audits requires a blend of theoretical knowledge and practical skills. Here’s how you can get started:
1. Understand Risk Management Frameworks: Familiarize yourself with globally accepted frameworks like COSO and ISO 31000.
2. Gain Hands-on Experience: Work on real-world audit assignments to develop a practical understanding of risk assessment and internal controls.
3. Stay Updated: The regulatory landscape evolves constantly. Keeping up with changes in tax laws, compliance standards, and industry best practices is crucial.
4. Invest in Professional Training: Enroll in courses like the Master Blaster of Internal Audit Course to gain practical insights and enhance your skills.
TIP:- To truly master internal auditing, you need more than just theoretical knowledge — you need practical expertise. The Master Blaster of Internal Audit Course is designed to help aspiring auditors and professionals excel in the field by covering:
• Comprehensive risk assessment frameworks.
• Real-world case studies and hands-on scenarios.
• Tools and techniques for internal controls evaluation.
• Strategies for effective communication of audit findings.
By enrolling in this course, you’ll gain the confidence and skills to handle internal audits with precision and become a trusted advisor in your organization.
Conclusion
Internal audits are the backbone of effective risk management, providing organizations with the insights they need to mitigate risks, enhance controls, and drive efficiency. For aspiring auditors and professionals looking to master this critical skill, investing in quality training is essential. Start your journey to becoming an expert in internal auditing today with the Master Blaster of Internal Audit Course. Gain the skills, knowledge, and confidence to navigate the complexities of risk management and make a meaningful impact in your career.
2 notes
·
View notes
Text
Building a Robust Data Governance Framework: Best Practices and Key Considerations

A good framework for data governance compliance assists organizations in ensuring data security. As a result, they can combat cybersecurity risks and fulfill regulatory requirements for responsible enterprise data operations. This post will focus on building a relevant, outcome-oriented data governance framework and strategy.
A comprehensive strategy will help protect an organization’s digital assets from different data breaches. Global brands want to avoid reputational damage and regulatory penalties by picking up governance initiatives. However, they seek reliable compliance approaches to maximize the value of data. That is why they want to know how to foster data etiquette for accuracy, timely access to insights, and relevance to business decisions.
Best Practices and Key Considerations for Building an Effective Data Governance Framework
1. Clearly Communicating Process Objectives and Data Ownership
Before a data governance framework is implemented, the objectives need to be clearly defined. What is the organization aiming to achieve by employing a data governance company? Some objectives may include the following.
- better quality of information,
- regulatory compliance,
- data-driven decision-making (DDDM).
These goals will determine the governance framework’s structure.
It also becomes very important to define data asset ownership. The data governance team, led by a data governance officer (DGO), must be held responsible for this. Those data professionals will develop data access and usage policies. They will also monitor data quality and address data-related issues across the entire organization.
2. Drafting Comprehensive Data Protection and Anti-Espionage Policies
A good data governance framework is based on well-articulated policies and standards. Those documents will guide data solutions and management practices, helping the firms and their suppliers. Such policies should define the most important compliance areas.
Considerations must include unbiased data classification and 24/7 security incident tracking. Moreover, privacy assurance assessments may be conducted. A broader data lifecycle management (DLM) vision can further streamline governance compliance efforts. Companies must also establish user permission standards. They will help allow access to data only if authorized personnel submit requests to their respective superiors. Similar access controls help prevent corporate espionage actors from entering IT systems and compromising sensitive business intelligence.
The policies developed should be flexible. After all, you will need to modify business governance frameworks. Otherwise, you cannot keep up with the regulators’ amendments to applicable laws.
3. Focus on Data Quality and Integrity
Ensuring data quality and integrity is very fundamental to data governance. Remember, inaccurate data leads to poor decisions. It inevitably results in misaligned strategies, causing inefficiencies in business activities. Therefore, data validation rules must be implemented. You want to encourage regular integrity audits based on those rules. Furthermore, adequate data cleansing practices will help ensure businesses’ dataset accuracy and reliability.
Consider data stewardship programs. It involves a competent individual or a team assuming responsibility for the quality of specific data assets.
4. Leverage Technology for Scalability and Automation
Data management can be enhanced by using modern technologies. Newer data governance platforms, artificial intelligence, and automation tools will aid you in improving governance compliance. These technologies will, therefore, make it easier to automate the tracking of data changes. Many tools also enforce governance policies. So, users can bypass the manual work of optimizing data protection measures based on the organization’s growth.
Conclusion
Building a strong data governance framework will demand definite objectives. Leaders will want to develop cross-functional collaborative environments to promote data ethics and integrity policies.
Accordingly, the best compliance assurance practices involve defining data ownership, ensuring data quality, and using novel technology. These measures would help organizations protect their data assets. Their superior compliance levels also make them attractive to more investors.
A robust data governance framework and compliance strategy does not just mitigate risk. Rather, it would deliver strategic success while respecting regulatory and consumer values concerning privacy.
2 notes
·
View notes
Text
Reimagining IT Support with Consulting and Managed Services

Modern businesses rely on technology for almost every function, from internal collaboration to customer engagement. But keeping IT systems secure, scalable and up to date is no small task. As infrastructures grow more complex, many organizations are turning to external experts for stability and direction.
This is where IT consulting and managed services step in. They help organizations maintain control while offloading complexity.
The Consulting Advantage
IT consulting is not just about fixing what's broken. It is about understanding business goals and aligning technology to meet them. Consultants assess existing systems, identify gaps, and recommend forward-looking solutions. Whether it's designing a cloud migration strategy, choosing the right cybersecurity framework or rearchitecting legacy systems, consulting focuses on long-term value.
What makes it powerful is its adaptability. A manufacturing firm and a retail chain might face very different IT challenges, but consulting provides tailored guidance for both.
Managed Services for Continuous Performance
While consulting provides the roadmap, managed services keep everything running. These services take over day-to-day IT operations so in-house teams can focus on innovation.
Managed services can include:
Infrastructure management for servers, networks and databases
Helpdesk support for users across locations
Security monitoring to detect threats before they escalate
Backup and disaster recovery to ensure business continuity
This approach is not reactive. It is built on proactive monitoring, automated updates and preventive maintenance to reduce downtime and keep systems optimized.
Reducing Risk, Increasing Agility
Cyber threats, system outages and compliance issues are growing risks for businesses. Managed service providers offer consistent oversight, making it easier to detect vulnerabilities and respond quickly. Meanwhile, consulting helps businesses stay ahead by integrating emerging technologies like AI, automation and analytics into their roadmap.
Together, they create a balance between stability and agility.
The Value of External Perspective
Working with an external IT partner offers more than technical expertise. It brings an outside perspective. Sometimes, internal teams are too close to the systems to spot inefficiencies. A consultant can offer new ways of working, based on experience across industries. A managed service team can implement best practices faster by drawing on insights from similar client environments.
This mix of external guidance and operational support leads to better decision-making and improved performance.
#itconsulting#managedservices#techstrategy#infrastructuremanagement#cybersecuritysupport#digitaloptimization#itoperations#businessresilience#cloudservices#technologyplanning
0 notes
Text
A Complete Guide to Working with a Cybersecurity Service Provider
In today’s hyper-connected world, cyber threats are more sophisticated and damaging than ever before. From ransomware and phishing attacks to data breaches and system vulnerabilities, businesses face constant risks that can cripple operations and tarnish reputations. That’s why partnering with a reliable cybersecurity service provider is no longer optional it’s essential. These experts offer advanced tools, proactive monitoring, and strategic support to protect your digital infrastructure. However, choosing and collaborating with the right provider requires a clear understanding of your security needs, goals, and expectations. In this guide, we’ll explore how to effectively work with a cybersecurity service to ensure robust, long-term protection.
Understanding What Cybersecurity Service Providers Offer
Cybersecurity service provider deliver a wide range of solutions designed to protect businesses from digital threats. These include vulnerability assessments, network security, endpoint protection, threat detection, data encryption, incident response, and compliance support. Some providers also offer 24/7 monitoring and managed security services tailored to your industry. Understanding the scope of services available helps you evaluate whether a provider meets your specific security needs. In today’s complex digital environment, working with a provider that offers comprehensive, proactive, and scalable protection ensures that your business stays ahead of cyber threats while maintaining operational continuity and customer trust.
Identifying Your Business’s Security Needs and Priorities
Before partnering with a cybersecurity provider, it’s essential to assess your organization’s risk profile and identify specific security needs. Start by evaluating your current infrastructure, the sensitivity of the data you handle, and your compliance requirements. Are you most vulnerable to phishing attacks, ransomware, insider threats, or regulatory violations? Clarifying these priorities allows you to find a provider that offers targeted solutions aligned with your business goals. A tailored approach ensures your budget is used efficiently and that you're not paying for services you don't need. Clear goals lead to better provider alignment and more effective cybersecurity outcomes.
Evaluating Provider Experience and Industry Expertise
Not all cybersecurity providers are equipped to handle the unique challenges of your industry. A provider with deep experience in your specific sector whether healthcare, finance, manufacturing, or e-commerce can offer specialized knowledge, tools, and strategies that others may lack. Look for certifications such as CISSP, CISM, or ISO/IEC 27001 compliance, along with a strong portfolio of clients and case studies. Ask for references and proof of results. An experienced partner not only understands technical threats but also navigates relevant legal, regulatory, and operational complexities. Their insight can significantly strengthen your cybersecurity framework and boost your long-term digital resilience.
Ensuring Scalability and Customization of Services
Your business will evolve, and so will your cybersecurity needs. That’s why it’s vital to work with a provider that offers scalable and customizable services. Whether you're a startup planning rapid growth or an established enterprise expanding globally, your provider should adapt their solutions to match. Look for flexibility in service plans, pricing models, and technological integrations. The ability to scale up or adjust services without disruptions ensures long-term value. A provider that tailors their offerings to your changing environment helps maintain continuous protection while optimizing resources and delivering security that grows with your business.
Understanding the Importance of 24/7 Monitoring and Support
Cyberattacks can happen anytime, not just during business hours. That’s why 24/7 monitoring and support are critical features of a trustworthy cybersecurity service provider. Real-time threat detection, immediate alerts, and rapid incident response help minimize potential damage and downtime. A provider offering continuous monitoring ensures that suspicious activity is caught early before it becomes a full-blown breach. Around-the-clock support also means your team has access to expert help whenever it's needed, including weekends and holidays. In a high-stakes digital world, this level of vigilance and responsiveness is essential for keeping your business safe and operational at all times.
Reviewing Communication, Reporting and Transparency Practices
Effective collaboration with a cybersecurity provider depends on clear communication and transparency. The right partner will offer regular reports, threat intelligence updates, and performance reviews, keeping you informed about your security posture. Look for providers that deliver actionable insights, not just technical jargon, and who involve you in security decision-making. Open lines of communication also ensure faster responses during incidents and help align cybersecurity efforts with broader business goals. Well-documented policies, detailed SLAs, and accountability metrics build trust and clarity. A provider who communicates clearly enhances not just your security but also your confidence in the protection they deliver.
Building a Long-Term Strategic Partnership
Cybersecurity is not a one-time fix it’s an ongoing effort. That’s why working with a service provider should be seen as building a long-term partnership rather than a short-term contract. Choose a provider that invests in understanding your business and is proactive about emerging risks and technologies. A strategic partner will help you develop security roadmaps, support employee training, guide compliance strategies, and evolve your defenses as new threats emerge. Their continuous involvement helps create a culture of cybersecurity throughout your organization. A trusted, long-term relationship with the right provider delivers consistent protection and supports sustainable, secure business growth.
Conclusion
Partnering with a cybersecurity service provider is a strategic move that safeguards your business in an increasingly hostile digital world. By understanding your specific needs, evaluating provider expertise, and ensuring scalability, communication, and 24/7 support, you can build a partnership that delivers lasting protection. The right provider doesn't just react to threats they anticipate them, aligning their services with your long-term goals. As cyber risks continue to evolve, a trusted cybersecurity partner becomes essential for maintaining resilience, regulatory compliance, and customer trust. With the right guidance and collaboration, you can confidently secure your digital assets and focus on growing your business.
0 notes
Text
Become a Certified ISO/IEC 42001 Lead Auditor and Lead Responsible AI Governance
As AI systems grow in complexity and impact, organizations need governance frameworks that ensure responsible and ethical AI use. The GSDC Certified ISO/IEC 42001 Lead Auditor program empowers professionals to audit, evaluate, and ensure compliance with the world’s first AI management system standard.
🎯 Why Choose This Certification?
Lead audits of AI governance systems using ISO/IEC 42001 guidelines
Become a trusted certified ISO auditor in the AI ecosystem
Understand frameworks for ethical, safe, and secure AI deployment
Get clarity on ISO 42001 certification cost and its global value
📘 What You’ll Learn: This course trains professionals to assess and audit AI systems across compliance, ethics, transparency, and risk. You’ll build a deep understanding of ISO/IEC 42001:2023 and prepare for roles that demand ISO 42001 lead auditor expertise.
💼 Who Should Enroll?
Auditors and Compliance Professionals
AI Governance Officers and Risk Managers
IT and Cybersecurity Leaders seeking ISO lead auditor roles
Consultants advising clients on ISO 42001 certification
By earning this globally respected ISO/IEC 42001 lead auditor certification, you'll prove your ability to guide organizations through trustworthy AI practices. Whether you’re exploring new opportunities or leading enterprise transformation, this certification is your gateway.
If you’re researching the ISO 42001 certification, this program also provides insight into AI lifecycle risks and controls. It positions you as a strategic asset in the future of digital trust.
Lead the new era of AI governance. Become a certified ISO/IEC 42001 lead auditor with GSDC.
🔗 Start your journey here: https://www.gsdcouncil.org/certified-iso-42001-lead-auditor
#LeadAuditorCertification #ISO42001Certification #ISOLedAuditor #CertifiedISOAuditor #ISO42001CertificationCost #ISO42001LeadAuditor #ISOIEC42001LeadAuditor #ISOIEC42001LeadAuditorCertification #GSDCCertification #ResponsibleAI
#iso 42001 certification cost#iso 42001 lead auditor#iso/iec 42001 lead auditor#iso/iec 42001:2023#iso 42001 lead implementer certification#iso/iec 42001 lead implemen
0 notes
Text
eShield IT Services — Your Trusted Partner in the Fight Against Cyber Threats
In a world that’s more digitally connected than ever, the risks are rising just as fast as the innovations. Data breaches, ransomware attacks, phishing scams — cyber threats have become more frequent, more sophisticated, and more devastating. Amid this landscape, one name stands out for its commitment to proactive protection: eShield IT Services.
Understanding the Need for Cybersecurity
Whether you're an individual freelancer or a multi-national enterprise, your digital presence is always exposed to potential risks. It's no longer just about having antivirus software or a firewall. Modern cybercriminals operate with advanced tools and target organizations through everything from unpatched applications to human error.
India, like many countries, has seen a rapid acceleration in digital adoption across sectors. With that progress comes responsibility — to secure sensitive data, comply with global regulations, and defend against evolving cyberattacks. This is where eShield IT Services brings tremendous value.
What is eShield IT Services?
eShield IT Services is a dedicated cyber security firm based in India, serving clients both locally and internationally. The company offers a wide range of cybersecurity services, designed to detect vulnerabilities, protect critical data, and help organizations meet global compliance standards.
But eShield doesn’t just offer services — it builds trust. The team is made up of experienced cybersecurity professionals who believe in ethical practices, constant learning, and client-centric solutions. Whether you’re building your first application or running an enterprise network, eShield’s mission is to help you stay secure, without the stress.
Core Services Offered by eShield IT Services
Each offering is designed to help organizations take control of their cyber hygiene and resilience:
Penetration Testing
Imagine someone trying to break into your digital infrastructure — not to steal, but to tell you how they did it. That’s exactly what eShield’s penetration testing services deliver. By simulating real-world cyberattacks, they identify system flaws before criminals can exploit them.
Web Application Security Auditing
Most businesses today rely heavily on web-based applications. eShield performs thorough audits to uncover vulnerabilities such as injection flaws, broken authentication, and cross-site scripting — ensuring that your applications remain secure and functional under pressure.
Compliance Consulting (PCI DSS, ISO 27001)
Compliance is more than just ticking boxes. With increasing regulations on data privacy and payment processing, businesses need guidance to meet standards like PCI DSS and ISO 27001. eShield offers hands-on support in designing compliant frameworks, building secure systems, and passing audits with confidence.
Managed Security Services
For companies that don’t have an in-house cyber security team, eShield acts as your outsourced security partner. From constant monitoring to threat detection and incident response, they provide a full stack of services to protect your systems around the clock.
SOC Implementation
A Security Operations Center (SOC) can be the backbone of your cybersecurity defense. eShield helps companies set up SOCs that are tailored to their size, industry, and budget — offering both on-premises and cloud-based solutions.
Why Choose eShield IT Services?
There are countless cybersecurity firms in the market. So what sets eShield apart?
Client-Focused: Every business is different, and eShield understands that. Their solutions are not one-size-fits-all but tailored specifically to your needs.
Ethical and Transparent: They believe in doing the right thing — always. Clear communication, honest risk assessments, and realistic strategies are part of their culture.
Experienced Team: With certified experts who’ve worked across multiple industries, you get advice and action based on proven strategies.
Affordable and Scalable: eShield offers pricing models that suit startups and enterprise clients alike, with scalability built into every service.
The Human Side of Cybersecurity
Often, cyber security is viewed as a purely technical field. But at its core, it's about people. It’s about protecting individuals’ identities, securing businesses’ reputations, and preserving trust in the digital systems we all rely on.
eShield IT Services blends technical know-how with a human touch. Their team works closely with clients to educate, empower, and create a culture of security awareness — because technology alone isn’t enough. Human error is the leading cause of breaches, and reducing that risk is a team effort.
Industries They Serve
From healthcare to finance, retail to government, eShield has experience across a wide range of sectors. Whether you’re managing e-commerce transactions or handling sensitive patient records, their security strategies align with your specific industry challenges.
Looking Ahead: The Future of Cybersecurity
The threat landscape is changing daily. As artificial intelligence, quantum computing, and IoT become more integrated into daily business operations, the attack surface expands. eShield IT Services continues to invest in research and upskilling to ensure that their clients remain ahead of emerging threats.
By embracing automation, predictive analytics, and threat intelligence, they’re not just reacting to attacks — they’re preventing them before they occur.
Final Thoughts
Cyber security is no longer an IT department issue. It's a business imperative, a brand protection strategy, and in many cases, a legal requirement.
eShield IT Services is not just another vendor. They are a trusted partner in your journey to secure digital transformation. By offering real solutions to real risks, they’re helping businesses across the globe thrive in an increasingly complex digital world.
If you’re ready to strengthen your cyber defense with a team that understands both technology and trust, visit www.eshielditservices.com and take the first step toward a safer future.
0 notes
Text
Why Every Vessel Needs a Robust Ship Security Plan (SSP) in Today’s Maritime Landscape
The global maritime industry is the lifeblood of international trade, responsible for moving over 80% of the world’s goods. Yet with this critical role comes increasing exposure to threats—ranging from piracy and terrorism to cyberattacks and unauthorized access. To mitigate such risks, maritime authorities across the globe require vessels to adopt and implement a Ship Security Plan (SSP) as part of the International Ship and Port Facility Security (ISPS) Code.
A well-structured SSP is not just a regulatory requirement—it’s a crucial defense layer that protects vessels, cargo, and crew from harm. In an age where security threats are evolving rapidly, having a robust ship security plan is more vital than ever.
What Is a Ship Security Plan (SSP)?
A Ship Security Plan (SSP) is a formal document developed for a specific ship that outlines the policies, procedures, and actions to detect and deter security threats. It includes preventive measures, emergency response protocols, and details about the ship’s security organization. The SSP is developed in accordance with the ISPS Code, which came into force in 2004 under the umbrella of the International Maritime Organization (IMO).
The SSP is tailored to the specific design and operation of each ship and must be approved by the vessel’s flag state or a Recognized Security Organization (RSO).
Why Is the Ship Security Plan So Important?
1. Maritime Security Compliance
The IMO mandates that all ships over 500 gross tonnage engaged in international voyages must have an approved SSP. Compliance is not optional—it’s a legal obligation. Ships without valid SSPs face port entry denials, fines, or even detention. A solid SSP ensures seamless maritime operations by aligning with global security frameworks.
2. Crew Safety and Emergency Preparedness
The SSP clearly defines the roles and responsibilities of the Ship Security Officer (SSO) and crew members during different security levels. This ensures that every crew member knows what to do in case of a threat, such as unauthorized boarding or suspicious activity.
Preparedness reduces panic and enhances the crew’s ability to respond swiftly and effectively—critical when every second counts.
3. Defense Against Piracy and Armed Attacks
Certain trade routes, like the Gulf of Aden or the Strait of Malacca, are notorious for piracy. An effective ship security plan (SSP) incorporates risk assessment and outlines defensive measures like watchkeeping routines, restricted areas onboard, and alert protocols, significantly improving onboard security during high-risk transits.
4. Protection of Cargo and Ship Infrastructure
Whether transporting valuable commodities, hazardous materials, or commercial goods, cargo theft and sabotage remain persistent threats. The SSP includes physical access control measures, surveillance, and cargo inspection protocols that help protect both the vessel and its cargo from tampering or theft.
5. Cybersecurity Considerations
Modern vessels are equipped with advanced navigation, communication, and engine management systems—all of which can be targets of cyberattacks. An evolving SSP integrates cybersecurity measures such as firewall policies, restricted network access, and response strategies in case of system breaches.
Key Elements of a Ship Security Plan
A comprehensive Ship Security Plan includes the following components:
Security Assessment: Identification of potential threats and vulnerabilities specific to the vessel.
Security Organization: Clear roles and responsibilities for onboard personnel including the SSO and Master.
Security Levels and Corresponding Measures: Specific actions for Security Levels 1 (Normal), 2 (Heightened), and 3 (Exceptional).
Access Control Procedures: How personnel, visitors, and suppliers are verified and monitored.
Restricted Areas: Zones onboard that are limited to authorized personnel only, such as the engine room, bridge, and communication systems.
Security Equipment Maintenance: Procedures for checking alarms, surveillance cameras, and access control devices.
Drills and Exercises: Scheduled training activities to keep the crew prepared and responsive.
Reporting and Recordkeeping: Logs of incidents, drills, and security checks for audit and investigation purposes.
How Technology Enhances SSP Implementation
Manual documentation and disconnected systems often lead to delays, oversights, or non-compliance in security procedures. With software like SBN Technologics’ Ship Security Management Module, implementing and maintaining your SSP becomes more efficient, secure, and compliant.
Digital SSP Management Features Include:
Customizable SSP Templates based on vessel type and operation
Automated Alerts for security drills, audits, and document expiration
Secure Data Storage for ship logs, security incident reports, and certificates
Real-time Dashboard for monitoring SSP implementation and access control
Integration with Crew Management to link roles, responsibilities, and security training
Digitizing the SSP not only simplifies compliance but also ensures data integrity, fast updates, and better coordination between ship and shore teams.
Real-Life Scenario: Consequences of a Weak Security Plan
In 2023, a bulk carrier operating in West Africa suffered an armed boarding by pirates. Investigations revealed that the vessel’s SSP had not been updated in over three years and lacked procedures for Security Level 2. The crew was unprepared, communications failed, and the ship's AIS (Automatic Identification System) had not been secured. The result was a 36-hour hostage situation, ransom demand, and a months-long insurance dispute.
This incident highlights the importance of maintaining an updated, dynamic, and crew-validated SSP at all times.
The Role of the Ship Security Officer (SSO)
A ship’s Security Officer is the linchpin of the SSP. They are responsible for:
Conducting security audits
Ensuring crew training
Implementing drills and exercises
Reporting incidents
Coordinating with the Company Security Officer (CSO) and Port Facility Security Officer (PFSO)
The effectiveness of your SSP directly correlates with how well the SSO executes their duties. Modern digital tools can support the SSO by providing automated reminders, real-time status updates, and documentation support.
Building a Security-First Culture Onboard
Security is not just a checklist—it’s a mindset. A robust ship security plan fosters a culture where every crew member takes ownership of vessel security. Regular training, security awareness sessions, and open communication channels are essential to reinforce this culture.
Ships that proactively invest in security build trust—not just within their crew, but also with port authorities, insurance firms, and cargo clients.
Final Thoughts
A comprehensive and updated Ship Security Plan (SSP) is not just a regulatory requirement—it is a shield that protects your vessel, your crew, and your reputation. In today’s maritime landscape, where threats are both physical and digital, implementing a well-defined SSP ensures your ship remains secure, compliant, and operational.
Solutions like those from SBN Technologics simplify the process of managing and updating your SSP, ensuring you’re always ready to meet the next security challenge head-on.
0 notes
Text
Cyber Security Audits in Dubai: Is Your Business Data Really Safe

The Silent Threats Hidden in Your Network
In a city that’s becoming a digital hub for innovation and enterprise, the risk of cyber threats is also rising up.The question that many businesses overlook is: Is your company data really safe? At Ashcode IT, we believe that true digital confidence starts with one essential step, that is cyber security audits in Dubai.
Unlike traditional security measures, cyber security audits are designed to uncover what lies beneath the surface. They assess your infrastructure, identify weak points, and prioritize areas where intervention is urgently needed.
Why Endpoint Protection in Dubai Deserves Special Attention
One major area of concern, and a core focus for us at Ashcode IT, is endpoint protection in Dubai. Every laptop, mobile device, or workstation connected to your network can be an entry point for cyber threats. If even one endpoint lacks proper security, it can serve as a gateway for attackers.
The Ashcode IT Approach to Cyber Security Audits in Dubai
As one of the experienced cyber security companies in Dubai, Ashcode IT takes a different approach. Our audits are systematic, not templated. We don’t just rely on tools — we combine automated scans with manual expertise to reveal vulnerabilities that most providers miss. This includes internal penetration testing, user behavior analysis, firewall review, and real-time threat simulations.
Moreover, we ensure that endpoint protection is prioritized. Weak or outdated endpoint security solutions are one of the most common reasons behind successful attacks. We evaluate whether your existing tools are capable of handling modern threats, and if not, we recommend proactive solutions built for real-time threat detection.
The Hidden Cost of Not Auditing Your Cybersecurity
Why is all this important? Because the financial and reputational cost of a breach is staggering. According to a 2024 report by IBM, data breaches in the UAE cost companies an average of $5.41 million per incident. And that doesn’t factor in the long-term damage to brand trust. Regular cyber security audits in Dubai prevent these incidents by detecting issues before malicious actors can exploit them.
Cyber Security Services in Dubai That Actually Work
Many businesses assume their IT team has things under control. But internal teams often lack the time, tools, or updated threat intelligence to conduct a full-scale audit. That’s where external cyber security services in Dubai play a vital role. We bridge that gap offering not just diagnostics, but also strategic remediation plans suitable for your industry and business needs.
From Vulnerable to Resilient: How Ashcode IT Helps You Act
One of the most overlooked yet essential outcomes of a cyber security audit is awareness. It shows leadership teams where they’re strong, where they’re vulnerable, and how to build a roadmap toward resilience. Ashcode IT’s audit process doesn’t end with a report — we stay with our clients to fix what’s broken, upgrade what’s outdated, and protect what’s valuable.
Take the First Step Toward True Security
So if you’re running a business in Dubai and haven’t had your infrastructure thoroughly evaluated in the last 12 months, it’s time to ask yourself: Are we really secure? If you’re unsure, that’s already a risk.
Partnering with Ashcode IT ensures that your cyber security framework is not just reactive but proactive. We help you stay ahead of emerging threats, safeguard sensitive data, and build digital trust with your clients.
To learn more about the latest trends in global and UAE cyber security, you can explore the IBM Data Breach Report, which details the real-world impact of cyber attacks in the region.
0 notes
Text
How VAPT Testing Helps Prevent Cyber Attacks
In today’s hyper-connected world, cybersecurity threats are more sophisticated and frequent than ever. From data breaches and ransomware to phishing attacks, organizations are constantly at risk. Amid this growing threat landscape, VAPT testing has emerged as a crucial safeguard. But what exactly is VAPT testing, and how does it help prevent cyber attacks?
In this blog, we at GIS Consulting break down the fundamentals of VAPT testing and explain why it’s essential for businesses aiming to fortify their digital defenses.

What is VAPT Testing?
VAPT stands for Vulnerability Assessment and Penetration Testing. It’s a comprehensive approach that combines two different methodologies to evaluate your IT environment:
Vulnerability Assessment (VA): This involves identifying known vulnerabilities in your system using automated tools and databases.
Penetration Testing (PT): This step simulates real-world cyberattacks to exploit the identified vulnerabilities and understand their impact.
Together, VAPT testing provides a detailed analysis of security weaknesses, prioritizes risks, and offers actionable insights to fix them before malicious actors can exploit them.
Why Is VAPT Testing Important?
Cybersecurity is not just an IT concern — it’s a business imperative. VAPT testing:
Uncovers hidden security flaws
Validates the effectiveness of your existing security measures
Ensures compliance with industry standards and regulations
Reduces the likelihood of data breaches, financial loss, and reputational damage
For organizations that handle sensitive data or operate in regulated industries like finance, healthcare, or government, regular VAPT testing is essential.
How VAPT Testing Prevents Cyber Attacks
Now, let’s explore how VAPT testing acts as a proactive shield against cyber threats:
1. Early Detection of Vulnerabilities
VAPT testing identifies security loopholes before attackers do. By scanning networks, servers, web applications, and endpoints, VAPT tools reveal outdated software, insecure configurations, exposed ports, and other weaknesses.
GIS Consulting’s expert team uses advanced scanning tools and manual assessments to uncover even the most elusive vulnerabilities, giving your organization a head start on remediation.
2. Simulated Real-World Attacks
Penetration testing mimics actual cyberattacks to test your system’s resilience. This simulation helps understand how an attacker would exploit a vulnerability and what damage they could cause.
Through controlled ethical hacking, GIS Consulting helps organizations experience and learn from these attack scenarios without the associated risk. This proactive approach is vital for understanding and strengthening defense mechanisms.
3. Risk Prioritization
Not all vulnerabilities are equally dangerous. Some may have little to no impact, while others can open the door to full system compromise.
VAPT testing not only finds these issues but also categorizes them based on severity, impact, and exploitability. This prioritization helps organizations allocate resources efficiently to fix the most critical problems first.
4. Compliance and Regulatory Readiness
Most regulatory frameworks — like ISO 27001, GDPR, PCI-DSS, and HIPAA — require periodic security assessments.
VAPT testing conducted by GIS Consulting ensures that your organization remains compliant with these standards. This avoids legal penalties and also builds trust with clients and stakeholders.
5. Improving Incident Response Plans
By exposing vulnerabilities and attack vectors, VAPT testing helps organizations refine their incident response strategies. Knowing how a threat may enter the system enables the security team to act swiftly in the event of a real attack.
GIS Consulting provides detailed reports following testing, including remediation guidelines and recommendations to enhance incident handling protocols.
6. Strengthening Customer Confidence
Data breaches can devastate customer trust. When companies demonstrate a commitment to cybersecurity through regular VAPT testing, they show clients, investors, and partners that data protection is a top priority.
GIS Consulting’s VAPT services not only reduce technical risks but also enhance your company’s reputation as a security-conscious brand.
7. Reducing Financial Risks
The average cost of a data breach can run into millions, not including the long-term loss of brand value and customer trust. VAPT testing is a cost-effective measure that helps organizations avoid such incidents and their financial consequences.
By identifying and addressing vulnerabilities proactively, GIS Consulting helps businesses save substantial resources that would otherwise be spent on damage control.
What Does a VAPT Test Include?
At GIS Consulting, a typical VAPT testing engagement includes:
Planning & Scoping: Understanding your infrastructure and defining testing boundaries
Automated Scanning: Using industry-leading tools to identify known vulnerabilities
Manual Testing: Simulating real-world attacks to validate findings
Risk Assessment: Categorizing vulnerabilities based on their severity
Reporting: Delivering a detailed report with risk ratings, proof-of-concept, and remediation advice
Retesting (optional): Verifying if vulnerabilities are successfully patched
Industries That Benefit from VAPT Testing
Virtually every sector benefits from VAPT testing, but it’s especially critical for:
Banking and Financial Services
Healthcare
E-commerce
Government Agencies
IT and SaaS Companies
Educational Institutions
No matter the size or industry, if your organization stores, processes, or transmits sensitive data, you need VAPT testing.
Why Choose GIS Consulting for VAPT Testing?
With a proven track record in cybersecurity and risk management, GIS Consulting offers:
Certified Security Experts (CEH, OSCP, CISSP)
Customized Testing Plans
Cutting-edge Tools and Methodologies
End-to-End Reporting and Support
Compliance-Aligned Assessments
Our VAPT testing services are tailored to your unique business environment, ensuring maximum protection and actionable insights. Whether you’re launching a new application, undergoing an audit, or want to assess your current infrastructure, GIS Consulting has you covered.
Final Thoughts
In an age where cyberattacks are inevitable, VAPT testing isn’t a luxury — it’s a necessity. It gives organizations the visibility they need into their security posture and the tools to strengthen it.
At GIS Consulting, we believe in proactive defense. Our VAPT testing services not only identify threats but empower you to fix them before they become a crisis.
0 notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
Why Blue Team Testing Is the Missing Link in Your Cybersecurity Strategy

Cybersecurity is becoming an essential component of all contemporary businesses, not just a luxury. While firewalls, antivirus software, and penetration testing have become standard practices, many organizations still overlook one crucial component: Blue Team Testing.
If your cybersecurity strategy focuses solely on external threats without validating your internal defense mechanisms, you’re leaving yourself vulnerable. Blue Team Testing fills that gap. It ensures your detection, response, and containment systems are not only in place but working exactly as they should when it matters most.
In this article, we’ll explain what Blue Team Testing is, how it works, and why it might just be the missing link in your cybersecurity strategy.
🔍 What Is Blue Team Testing?
Blue Team Testing is a structured exercise where an internal cybersecurity team (the Blue Team) tests the organization’s ability to detect, respond to, and recover from cyber threats. While red teams simulate attackers, blue teams act as defenders, monitoring systems, analyzing threats, and responding to simulated breaches.
In a business context, Blue Team Testing involves:
Validating security controls (firewalls, SIEM, IDS/IPS)
Monitoring logs and event data
Identifying indicators of compromise (IOCs)
Practicing incident response and threat containment
Reporting gaps in security posture
Unlike penetration testing, which simulates an attacker’s perspective, Blue Team Testing measures the effectiveness of your current defenses. It's the cyber equivalent of testing your alarm system after locking all the doors.
🧩 Why It’s the Missing Link in Cybersecurity
Many companies mistakenly believe that investing in tools or running annual red team tests is enough. But without verifying whether their defenses work in real-world conditions, they have a false sense of security.
Here's why Blue Team Testing bridges the gap:
Tools Alone Are Not Enough
Security solutions like firewalls and endpoint protection are only effective if correctly configured and regularly updated. Blue Team Testing uncovers misconfigurations or blind spots that attackers could exploit.
People and Processes Need Practice
Just like firefighters need drills, your cybersecurity team needs to practice. Blue Team exercises simulate real attacks, ensuring your team knows exactly how to respond in high-pressure situations.
Immediate Feedback Loop
Red Team testing shows how an attacker could get in. Blue Team Testing shows whether you can catch them in time. Without this insight, your risk remains unknown.
Compliance and Regulatory Alignment
Many industries now require ongoing risk assessments and incident response validation. Blue Team Testing can help meet frameworks like NIST, ISO 27001, HIPAA, and PCI-DSS.
🧠 Key Components of Blue Team Testing
Effective Blue Team Testing goes beyond simply watching logs. It should be a comprehensive, multi-layered process. Key components include:
1. Baseline Security Assessment
Start by understanding your existing environment. What systems are you monitoring? What logs are collected? What tools are deployed?
2. Simulated Threat Scenarios
Test detection and reaction using actual attack situations. For example:
Malware injection
Insider data exfiltration
Lateral movement across network segments
Suspicious login behavior
3. Detection & Alerting Validation
Is your SIEM generating alerts at the right time? Are there too many false positives? Blue Team Testing ensures your alerting system is fine-tuned.
4. Threat Hunting
Encourage proactive investigation of anomalies across endpoints, servers, and user accounts. Early detection is just as important as defense.
5. Incident Response Drill
Document how the team responds: How quickly do they contain the threat? Are escalation protocols followed? Can systems be restored without data loss?
6. Reporting & Recommendations
The final output should be a detailed report that outlines:
What was detected (and missed)
Response timelines
Gaps in process, tools, or training
Actionable steps to improve
📈 Business Benefits of Blue Team Testing
Blue Team Testing isn’t just a technical exercise—it delivers measurable business value:
✅ 1. Improves Threat Visibility
Simulated threats help you see which parts of your infrastructure are being properly monitored—and which are not.
✅ 2. Reduces Dwell Time
The longer a threat is disregarded, the more damage it could cause. Blue Team Testing reduces the time between breach and response.
✅ 3. Validates Investment in Security Tools
Are you getting ROI from your SIEM or EDR platforms? Blue Team Testing shows if your expensive tools are pulling their weight.
✅ 4. Enhances Team Readiness
Cybersecurity teams must be alert, adaptable, and trained. Testing creates muscle memory and sharpens skills under pressure.
✅ 5. Demonstrates Compliance Readiness
Blue Team Testing supports evidence-based documentation that helps you pass audits and stay compliant with industry regulations.
✅ 6. Builds Executive Confidence
When leadership sees a clear picture of detection capabilities and response workflows, they gain confidence in your cybersecurity posture.
Getting Started with Blue Team Testing
You must begin, but you don't have to start large.
Here’s how:
Step 1: Assess Your Current Security Stack
Identify all tools and processes currently in place: SIEM, antivirus, endpoint detection, firewall, etc.
Step 2: Set Clear Testing Objectives
What do you want to test? Detection capabilities, incident response, or data exfiltration scenarios?
Step 3: Partner with Blue Team Experts
Work with cybersecurity consultants who specialize in defense simulation and can help you set up realistic testing.
Step 4: Schedule Regular Drills
Treat Blue Team Testing like a fire drill—run it quarterly or semi-annually, and test against evolving threats.
Step 5: Measure and Improve
Review outcomes, address gaps, and iterate. The more you test, the more resilient your business becomes.
💬 Final Thoughts
In a threat landscape that evolves daily, passive defense is no longer enough. Blue Team Testing brings active validation into your cybersecurity framework. It confirms that your tools, processes, and people are prepared, not just in theory, but in practice.
If you're already investing in cybersecurity, Blue Team Testing ensures you're protected. It closes the loop between what you deploy and how effectively you can defend.
Think of it not as another checkbox, but as your final layer of assurance—the missing link that could prevent your next breach from becoming a headline.
0 notes
Text
PCI DSS Certification in UAE 2025 - Compliance & Assessment
Protecting cardholder data is more important than ever for businesses operating in the United Arab Emirates. With the increasing number of financial transactions and cyber threats, PCI DSS Certification in the UAE has become a critical requirement for any organization that stores, processes, or transmits payment card information.
CyberSigma, a leading cybersecurity company in the region, specializes in helping businesses navigate the complexities of PCI DSS compliance with expert guidance, audits, and consulting services.

What is PCI DSS Certification in UAE?
PCI DSS (Payment Card Industry Data Security Standard) is a globally recognized framework of security standards designed to protect sensitive cardholder data. In the UAE, businesses that accept credit or debit card payments are required to comply with these standards to ensure transaction security and maintain customer trust.
The certification process assesses how an organization stores, processes, and transmits card data, ensuring it meets the rigorous standards established by the Payment Card Industry Security Standards Council (PCI SSC).
CyberSigma assists organizations in the UAE by providing end-to-end PCI DSS compliance support, from gap analysis to audit preparation and final certification.
Payment Card Industry Data Security Standard
Major credit card companies, including Visa, MasterCard, American Express, Discover, and JCB, developed the PCI DSS. The standard consists of 12 requirements grouped into six core objectives. These are designed to create a secure environment for cardholder data and minimize the risk of data breaches.
Organizations are required to implement various security measures, policies, and technologies that address physical, technical, and administrative controls to ensure the protection of sensitive information. Compliance is mandatory for any entity that handles payment card data, regardless of size or transaction volume.
The PCI DSS Specifies and Elaborates on Six Major Objectives
The 12 PCI DSS requirements are organized under six primary objectives:
1. Build and Maintain a Secure Network and Systems
Install and maintain a firewall configuration to protect cardholder data
Do not use vendor-supplied defaults for system passwords and other security parameters
2. Protect Cardholder Data
Protect stored cardholder data
Encrypt transmission of cardholder data across open, public networks
3. Maintain a Vulnerability Management Program
Protect all systems against malware and regularly update anti-virus software
Develop and maintain secure systems and applications
4. Implement Strong Access Control Measures
Restrict access to cardholder data by business need to know
Identify and authenticate access to system components
Restrict physical access to cardholder data
5. Regularly Monitor and Test Networks
Track and monitor all access to network resources and cardholder data
Regularly test security systems and processes
6. Maintain an Information Security Policy
Maintain a policy that addresses information security for all personnel.
CyberSigma provides deep expertise in mapping each of these objectives to an organization's unique environment, ensuring smooth and accurate implementation.
PCI DSS Compliance Cost in 2025
Understanding the PCI DSS compliance cost in the UAE is crucial for budget planning and compliance readiness. Costs can vary depending on the size of the business, the volume of transactions, the complexity of the IT infrastructure, and the level of existing compliance.
Key cost components include:
Initial gap assessment and scoping
Remediation efforts (hardware, software, staff training)
Consultant or Qualified Security Assessor (QSA) fees
Annual compliance reporting and audits
Penalties for non-compliance or data breaches
We offer flexible and transparent pricing models customized to your organization's specific needs, ensuring that compliance is both affordable and effective.
How To Get a PCI DSS Certification in UAE?
Achieving PCI DSS Certification in UAE involves a series of systematic steps that include preparation, implementation, and validation. Here's how CyberSigma helps your organization attain certification with confidence:
1. Scoping & Gap Analysis
We begin by identifying the cardholder data environment (CDE) and assessing current controls against PCI DSS requirements.
2. Remediation Planning
Our team provides actionable recommendations to address gaps in your security posture. This may involve configuring firewalls, updating software, or improving access controls.
3. Implementation Support
We guide your team in deploying necessary changes, ensuring that technical and policy-based solutions are implemented correctly.
4. Internal Audit
Before the official assessment, CyberSigma conducts an internal audit to ensure readiness and resolve any last-minute issues.
5. Final Audit & Certification
A Qualified Security Assessor (QSA) from CyberSigma or a partner firm performs the final audit and issues the PCI DSS compliance report and certification.
This structured process minimizes disruption and ensures a smooth path to compliance.
PCI DSS Compliance Consulting & Audit Services In UAE
CyberSigma is a trusted provider of PCI DSS compliance consulting and audit services in the UAE, delivering customized solutions for businesses across various industries. Our services include:
PCI DSS gap assessments
Policy and documentation development
Technical remediation support
QSA-led audits and certification
Staff training and awareness programs
With a local presence and global expertise, CyberSigma bridges the gap between compliance requirements and real-world business operations, ensuring you meet industry standards with confidence.
Why Choose CyberSigma for PCI DSS Certification in UAE?
CyberSigma brings unmatched experience and a results-driven approach to PCI DSS compliance. Our team comprises certified professionals with deep knowledge of international cybersecurity frameworks and local regulatory landscapes
Our Value Proposition:
Customized, business-aligned compliance roadmaps
Transparent pricing with no hidden costs
End-to-end support from planning to certification
Deep understanding of the UAE market and regulatory norms
Whether you're a startup or a large enterprise, CyberSigma ensures that your journey toward PCI DSS certification is efficient, stress-free, and successful.
PCI DSS Certification in UAE is not just a regulatory requirement—it's a strategic necessity. It builds trust with customers, protects your business from financial and reputational damage, and aligns your operations with global security standards.
Partnering with CyberSigma gives you access to industry-leading expertise, structured methodologies, and unwavering support throughout your compliance journey.
Reach out to CyberSigma today to secure your payment infrastructure and take the first step toward PCI DSS certification in 2025.
Source link:
1 note
·
View note
Text
🔐 ISO 27001 Certification in San Diego: Safeguard Your Data, Strengthen Your Trust
In today’s digital-first economy, protecting sensitive data isn’t just a technical requirement—it’s a business necessity. San Diego, home to thriving tech startups, healthcare innovators, and global logistics providers, demands strict cybersecurity measures. That’s where ISO 27001 Certification in San Diego becomes a vital step toward securing your data and building trust with stakeholders.
ISO 27001 is the international standard for Information Security Management Systems (ISMS). It offers a framework for identifying risks, protecting data, and responding to threats in a structured and effective way. Whether you’re a SaaS company in downtown San Diego, a healthcare provider in Mission Valley, or a research firm in Torrey Pines, ISO 27001 Certification in San Diego gives you a competitive edge in today’s high-risk digital world.
To begin your compliance journey, most businesses turn to expert ISO 27001 Consultants in San Diego. These professionals conduct a risk assessment, examine your current policies and systems, and map out a tailored strategy to close security gaps. They don’t just help you prepare for certification—they help you create a culture of information security from the ground up 🔍.
With cyberattacks on the rise and data privacy laws tightening globally, businesses can no longer afford weak security. ISO 27001 Services in San Diego include policy creation, employee training, risk treatment plans, documentation, internal audits, and complete certification support.
✅ Benefits of ISO 27001 Certification in San Diego:
Protect sensitive data against breaches and leaks 🔐
Build trust with clients, partners, and regulators
Comply with legal requirements like CCPA and HIPAA
Improve internal awareness of cybersecurity best practices
Win more contracts that require ISO-certified vendors
In industries such as finance, healthcare, defense, and e-commerce, ISO 27001 Certification is often a prerequisite for working with enterprise-level clients or government contracts. It shows that you’ve taken active steps to identify risks and establish controls that reduce the chance of data loss or unauthorized access.
Beyond compliance, this certification helps optimize your internal processes. With guidance from ISO 27001 Consultants in San Diego, you’ll implement clear access controls, incident response plans, encryption practices, and secure data storage procedures—all of which lead to smoother operations and better decision-making 🔧.
Cybersecurity is also a branding opportunity. Clients want to work with companies they can trust with sensitive information. Displaying ISO 27001 Certification in San Diego on your website, proposals, and product literature boosts confidence and helps close more deals 📈.
San Diego’s diverse and growing economy presents both opportunities and threats. Businesses that act proactively can reduce cyber risk and enhance operational resilience. Engaging ISO 27001 Services in San Diego helps you stay ahead of cybercriminals, meet evolving regulations, and protect your digital assets 24/7.
After certification, maintaining your ISMS is key. Ongoing services include monitoring, annual reviews, internal audits, and updates to meet evolving risks. This ensures long-term compliance and supports continuous improvement.
Ready to Secure Your Business?
With help from professional ISO 27001 Consultants in San Diego and comprehensive ISO 27001 Services in San Diego, your organization can lead with confidence, security, and trust. Protect what matters most—and show your customers they’re in safe hands.
0 notes