#Cybersecurity automation
Explore tagged Tumblr posts
Text
Cybersecurity Is a Journey, Not a Destination – Insights from CyberSigma’s Co-Founder
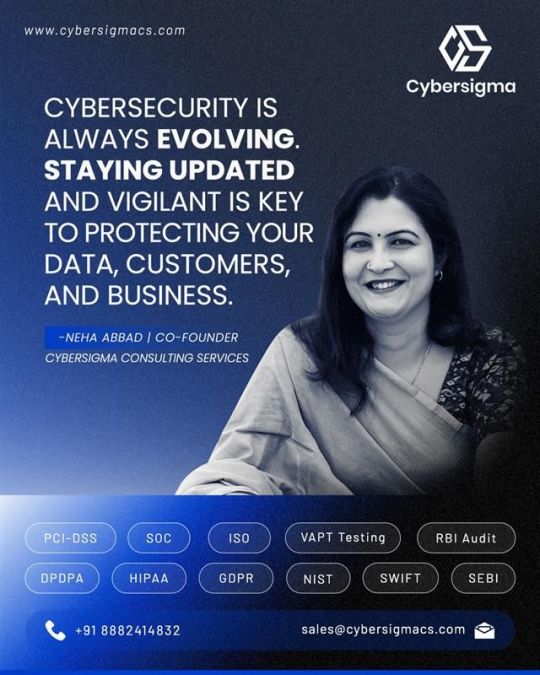
Neha Abbad, Co-Founder of CyberSigma Consulting Services, emphasizes that real cybersecurity starts with awareness, responsibility, and vigilance. As threats evolve, so must we. Discover why businesses of all sizes must treat cybersecurity as a continuous, proactive effort—not just a technical fix. Read More
0 notes
Text
Harnessing Agentic AI: Transforming Business Operations in 2025
Introduction
Artificial Intelligence (AI) has evolved significantly, and in 2025, we are witnessing the rise of Agentic AI in Business—an advanced form of AI capable of autonomous decision-making, problem-solving, and self-learning without constant human intervention. This new wave of AI is set to revolutionize business operations across industries, enhancing efficiency, productivity, and innovation.
In this blog, we explore how businesses can harness Agentic AI to gain a competitive edge, streamline workflows, and enhance customer experiences.
Understanding Agentic AI
What is Agentic AI?
Agentic AI refers to artificial intelligence systems that operate with a high degree of autonomy, making strategic decisions, adapting to dynamic environments, and executing tasks without explicit instructions. Unlike traditional AI models that rely on predefined rules, Agentic AI learns, evolves, and self-corrects based on real-time data and experiences.
Key Features of Agentic AI
Autonomous Decision-Making: Can analyze complex situations and make data-driven choices.
Self-Learning Capabilities: Continuously improves performance without human intervention.
Context Awareness: Understands situations and adjusts actions accordingly.
Interoperability: Can integrate seamlessly with various business systems.
For businesses looking to implement Agentic AI solutions, TechGeekz Services offers customized AI-driven automation solutions tailored to diverse industry needs.
How Agentic AI is Transforming Business Operations
1. Enhancing Business Efficiency
Agentic AI optimizes business processes by automating repetitive and time-consuming tasks, allowing employees to focus on strategic initiatives.
How It Works:
Automates document processing and data entry.
Improves supply chain logistics by predicting inventory needs.
Enhances workflow management with intelligent scheduling.
➡ Explore TechGeekz’s AI-powered business automation tools to improve efficiency in your organization.
2. Revolutionizing Customer Experience
With Agentic AI, businesses can offer hyper-personalized customer experiences that increase engagement and satisfaction.
Key Benefits:
AI Chatbots: Provide real-time support with human-like responses.
Predictive Analytics: Forecast customer preferences and behaviors.
Sentiment Analysis: Understand customer feedback to refine services.
3. AI-Powered Cybersecurity
As cyber threats become more sophisticated, Agentic AI plays a crucial role in security operations by detecting vulnerabilities and preventing attacks in real time.
AI Security Features:
Detects and mitigates fraud automatically.
Monitors systems for suspicious activities.
Strengthens authentication with biometric and behavioral analysis.
💡 Protect your business with TechGeekz’s AI cybersecurity solutions.
4. Streamlining Human Resource Management
Agentic AI is transforming HR processes by making recruitment, employee engagement, and performance evaluations more efficient.
How Businesses Benefit:
AI-powered applicant screening saves time in hiring.
Employee performance tracking ensures better workforce management.
AI-driven learning platforms personalize training programs.
🔍 Explore TechGeekz’s HR automation solutions to revolutionize talent management.
5. Optimizing Marketing and Sales
AI is enabling businesses to make data-driven marketing decisions, leading to increased conversions and customer loyalty.
Agentic AI in Marketing:
Automates personalized email campaigns.
Predicts purchasing behavior with AI analytics.
Enhances ad targeting through real-time data analysis.
📊 Leverage TechGeekz’s AI marketing solutions for a data-driven sales strategy.
The Future of Agentic AI in Business
As we move further into 2025, businesses that embrace Agentic AI will enjoy enhanced agility, cost savings, and improved decision-making. The future will see AI evolving into more sophisticated models with increased ethical and regulatory considerations.
🔗 For businesses ready to integrate AI-driven transformation, TechGeekz Services provides end-to-end AI implementation solutions.
Conclusion
Agentic AI is reshaping the business landscape, offering organizations unprecedented opportunities to enhance efficiency, security, and customer experiences. By adopting AI-driven solutions, businesses can stay ahead of the competition and drive long-term success.

Forbes: How AI is Transforming Business
MIT Technology Review: AI’s Role in the Future of Business
TechGeekz’s AI Automation Solutions
TechGeekz’s AI-Powered Cybersecurity
TechGeekz’s AI Marketing Solutions
#Agentic AI#AI agents#Autonomous systems#Generative AI#Reinforcement learning#Deep learning#Business intelligence#Cybersecurity automation#Enterprise workflow automation#Industrial automation#Agent-based process management#AI orchestration#Digital twins#AI in Finance#Emerging technology 2025
1 note
·
View note
Text
Risikomonitor: Cybersecurity Automation Made Simple
Risikomonitor makes cybersecurity automation simple. Identify IT vulnerabilities with one click and get a complete risk overview. No technical expertise needed. Stay ahead of threats with continuous monitoring and proactive protection. Start your 15-day free trial today.
Cybersecurity automation
0 notes
Text
AI in Cybersecurity – How AI is Transforming IT Security in 2025

Introduction
Cybersecurity threats are evolving at an unprecedented rate, putting businesses and individuals at risk of data breaches, ransomware attacks, and phishing scams. In response, Artificial Intelligence (AI) is revolutionizing IT security by providing advanced threat detection, real-time monitoring, and automated response mechanisms. AI-powered cybersecurity is no longer a futuristic concept—it’s a necessity in today’s digital landscape.
How AI is Transforming Cybersecurity
1. AI for Threat Detection and Prevention
Traditional security systems rely on rule-based algorithms, which often fail against sophisticated cyberattacks. AI-powered cybersecurity solutions use machine learning (ML) to analyze patterns and detect anomalies, identifying threats before they cause damage.
AI detects phishing attempts by analyzing email content and sender behavior.
Machine learning models predict cyberattacks based on historical data.
AI-driven endpoint security ensures real-time protection for devices.
2. Automated Incident Response
AI accelerates threat mitigation by automatically responding to cyber incidents. Instead of waiting for manual intervention, AI-driven security systems isolate infected devices, block malicious IP addresses, and neutralize threats in real-time.
AI-powered firewalls and intrusion detection systems (IDS) improve network security.
Automated security operations centers (SOCs) enhance rapid threat resolution.
3. Behavioral Analytics for Cybersecurity
AI analyzes user behavior to detect unusual activities. If an employee's login pattern suddenly changes or unauthorized data access occurs, AI flags it as a potential threat.
AI-driven identity and access management (IAM) prevents unauthorized logins.
Behavioral biometrics enhance authentication security.
4. AI in Cloud Security
As cloud computing adoption grows, cyber threats targeting cloud environments also rise. AI enhances cloud security by:
Identifying misconfigurations that could expose data.
Monitoring cloud access patterns for suspicious activities.
Detecting malware in cloud storage services.
Challenges of AI in Cybersecurity
Despite its advantages, AI-powered cybersecurity faces challenges, including:
False Positives & Negatives: AI must continuously learn to minimize detection errors.
High Implementation Costs: AI-driven security solutions require significant investment.
Data Privacy Concerns: AI models rely on vast amounts of data, raising privacy issues.
Future Trends of AI in Cybersecurity
The future of AI in cybersecurity is promising, with advancements shaping IT security strategies. Some key trends include:
AI-Powered Zero Trust Security Models: Verifying every request before granting access.
Deep Learning for Threat Hunting: Identifying complex cyberattack patterns.
Quantum Computing’s Role in AI Cybersecurity: Strengthening encryption algorithms.
AI-Augmented Penetration Testing: AI-driven ethical hacking to identify vulnerabilities.
Conclusion
AI is transforming cybersecurity by making IT security smarter, faster, and more proactive. As cyber threats become more sophisticated, businesses must integrate AI-driven security measures to protect sensitive data and digital assets. Investing in AI-powered cybersecurity today ensures a safer digital future for organizations worldwide.
Follow For More Insights: Reflextick Creative Agency
#AI in cybersecurity#cybersecurity trends 2025#AI-powered IT security#artificial intelligence in security#AI-driven threat detection#cybersecurity automation#AI in cloud security#machine learning for cybersecurity#future of AI in cybersecurity.
0 notes
Text

27-Year-Old EXE becomes Python - AI-assisted reverse engineering 🤖⚡💾🐍 https://blog.adafruit.com/2025/02/27/27-year-old-exe-becomes-python-in-minutes-with-claude-ai-assisted-reverse-engineering/
#reverseengineering#ai#python#machinelearning#technews#coding#artificialintelligence#programming#innovation#automation#technology#softwaredevelopment#aiassisted#dataconversion#retrocomputing#computerscience#techtrends#cybersecurity#hacking#opensource#techcommunity#developer#aiintech#digitaltransformation#programmerslife#coders#futuretech#softwareengineering#oldtomew#modernization
7 notes
·
View notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
2 notes
·
View notes
Text

Acadecraft Partners with Wadhwani Foundation's Government Digital Transformation Initiative to Develop eLearning Courses
#digitaltransformation#technology#innovation#business#digitalmarketing#ai#digital#artificialintelligence#software#machinelearning#automation#businessgrowth#tech#iot#techinnovation#bigdata#cybersecurity#cloud#data#cloudcomputing#smallbusiness#customerexperience#marketing#sap#webdevelopment#erp#blockchain#analytics#ecommerce#datascience
2 notes
·
View notes
Text
10 Ways Technology is Boosting Workplace Productivity
In the contemporary professional landscape, productivity is the currency of success. Businesses and individuals alike are constantly seeking innovative strategies to optimize output, streamline workflows, and maximize efficiency. At the forefront of this revolution is technology, which has fundamentally transformed how we work, collaborate, and manage our time. Far from being a mere convenience,…
#AI in Workplace#artificial intelligence#automation#business efficiency#Business Growth#Business Intelligence#Business Management#Business Solutions#Business Technology#cloud computing#Collaboration Tools#cybersecurity#data analytics#Data-Driven Decisions#Digital Collaboration#Digital Document Management#digital tools#digital transformation#Digital Workplace#Efficiency Tools#Employee Efficiency#Employee Engagement Technology#Employee Training Platforms#Enterprise Software#future of work#Hybrid Work#machine learning#Mobile Productivity#Modern Workplace#Office Technology
1 note
·
View note
Text
Are AI-Powered Traffic Cameras Watching You Drive?
New Post has been published on https://thedigitalinsider.com/are-ai-powered-traffic-cameras-watching-you-drive/
Are AI-Powered Traffic Cameras Watching You Drive?


Artificial intelligence (AI) is everywhere today. While that’s an exciting prospect to some, it’s an uncomfortable thought for others. Applications like AI-powered traffic cameras are particularly controversial. As their name suggests, they analyze footage of vehicles on the road with machine vision.
They’re typically a law enforcement measure — police may use them to catch distracted drivers or other violations, like a car with no passengers using a carpool lane. However, they can also simply monitor traffic patterns to inform broader smart city operations. In all cases, though, they raise possibilities and questions about ethics in equal measure.
How Common Are AI Traffic Cameras Today?
While the idea of an AI-powered traffic camera is still relatively new, they’re already in use in several places. Nearly half of U.K. police forces have implemented them to enforce seatbelt and texting-while-driving regulations. U.S. law enforcement is starting to follow suit, with North Carolina catching nine times as many phone violations after installing AI cameras.
Fixed cameras aren’t the only use case in action today, either. Some transportation departments have begun experimenting with machine vision systems inside public vehicles like buses. At least four cities in the U.S. have implemented such a solution to detect cars illegally parked in bus lanes.
With so many local governments using this technology, it’s safe to say it will likely grow in the future. Machine learning will become increasingly reliable over time, and early tests could lead to further adoption if they show meaningful improvements.
Rising smart city investments could also drive further expansion. Governments across the globe are betting hard on this technology. China aims to build 500 smart cities, and India plans to test these technologies in at least 100 cities. As that happens, more drivers may encounter AI cameras on their daily commutes.
Benefits of Using AI in Traffic Cameras
AI traffic cameras are growing for a reason. The innovation offers a few critical advantages for public agencies and private citizens.
Safety Improvements
The most obvious upside to these cameras is they can make roads safer. Distracted driving is dangerous — it led to the deaths of 3,308 people in 2022 alone — but it’s hard to catch. Algorithms can recognize drivers on their phones more easily than highway patrol officers can, helping enforce laws prohibiting these reckless behaviors.
Early signs are promising. The U.K. and U.S. police forces that have started using such cameras have seen massive upticks in tickets given to distracted drivers or those not wearing seatbelts. As law enforcement cracks down on such actions, it’ll incentivize people to drive safer to avoid the penalties.
AI can also work faster than other methods, like red light cameras. Because it automates the analysis and ticketing process, it avoids lengthy manual workflows. As a result, the penalty arrives soon after the violation, which makes it a more effective deterrent than a delayed reaction. Automation also means areas with smaller police forces can still enjoy such benefits.
Streamlined Traffic
AI-powered traffic cameras can minimize congestion on busy roads. The areas using them to catch illegally parked cars are a prime example. Enforcing bus lane regulations ensures public vehicles can stop where they should, avoiding delays or disruptions to traffic in other lanes.
Automating tickets for seatbelt and distracted driving violations has a similar effect. Pulling someone over can disrupt other cars on the road, especially in a busy area. By taking a picture of license plates and sending the driver a bill instead, police departments can ensure safer streets without adding to the chaos of everyday traffic.
Non-law-enforcement cameras could take this advantage further. Machine vision systems throughout a city could recognize congestion and update map services accordingly, rerouting people around busy areas to prevent lengthy delays. Considering how the average U.S. driver spent 42 hours in traffic in 2023, any such improvement is a welcome change.
Downsides of AI Traffic Monitoring
While the benefits of AI traffic cameras are worth noting, they’re not a perfect solution. The technology also carries some substantial potential downsides.
False Positives and Errors
The correctness of AI may raise some concerns. While it tends to be more accurate than people in repetitive, data-heavy tasks, it can still make mistakes. Consequently, removing human oversight from the equation could lead to innocent people receiving fines.
A software bug could cause machine vision algorithms to misidentify images. Cybercriminals could make such instances more likely through data poisoning attacks. While people could likely dispute their tickets and clear their name, it would take a long, difficult process to do so, counteracting some of the technology’s efficiency benefits.
False positives are a related concern. Algorithms can produce high false positive rates, leading to more charges against innocent people, which carries racial implications in many contexts. Because data biases can remain hidden until it’s too late, AI in government applications can exacerbate problems with racial or gender discrimination in the legal system.
Privacy Issues
The biggest controversy around AI-powered traffic cameras is a familiar one — privacy. As more cities install these systems, they record pictures of a larger number of drivers. So much data in one place raises big questions about surveillance and the security of sensitive details like license plate numbers and drivers’ faces.
Many AI camera solutions don’t save images unless they determine it’s an instance of a violation. Even so, their operation would mean the solutions could store hundreds — if not thousands — of images of people on the road. Concerns about government surveillance aside, all that information is a tempting target for cybercriminals.
U.S. government agencies suffered 32,211 cybersecurity incidents in 2023 alone. Cybercriminals are already targeting public organizations and critical infrastructure, so it’s understandable why some people may be concerned that such groups would gather even more data on citizens. A data breach in a single AI camera system could affect many who wouldn’t have otherwise consented to giving away their data.
What the Future Could Hold
Given the controversy, it may take a while for automated traffic cameras to become a global standard. Stories of false positives and concerns over cybersecurity issues may delay some projects. Ultimately, though, that’s a good thing — attention to these challenges will lead to necessary development and regulation to ensure the rollout does more good than harm.
Strict data access policies and cybersecurity monitoring will be crucial to justify widespread adoption. Similarly, government organizations using these tools should verify the development of their machine-learning models to check for and prevent problems like bias. Regulations like the recent EU Artificial Intelligence Act have already provided a legislative precedent for such qualifications.
AI Traffic Cameras Bring Both Promise and Controversy
AI-powered traffic cameras may still be new, but they deserve attention. Both the promises and pitfalls of the technology need greater attention as more governments seek to implement them. Higher awareness of the possibilities and challenges surrounding this innovation can foster safer development for a secure and efficient road network in the future.
#2022#2023#adoption#ai#AI-powered#Algorithms#Analysis#applications#artificial#Artificial Intelligence#attention#automation#awareness#betting#Bias#biases#breach#bug#Cameras#Cars#change#chaos#China#cities#critical infrastructure#cybercriminals#cybersecurity#data#data breach#data poisoning
5 notes
·
View notes
Text

what u think, to much colour, or less?
https://sdesignt.threadless.com/
#tshirt#animals#design#rainbow#computer#Innovation#AI#Blockchain#Crypto#Tech#Digital#Data#BigData#Automation#Cloud#Cybersecurity#Startup#Entrepreneur#Leadership#Marketing#Business#Ecommerce#Content#Performance#Development#Research#Analytics#Growth#Productivity#Trend
4 notes
·
View notes
Text
Secure, Smart, and Lethal: The Tech Behind Military Embedded Systems

Introduction:
The global military embedded systems market is undergoing significant transformation, driven by technological advancements and evolving defense strategies. As defense forces worldwide prioritize modernization, the integration of sophisticated embedded systems has become paramount to enhance operational efficiency, communication, and security. This article provides an in-depth analysis of the current market dynamics, segmental insights, regional trends, and competitive landscape shaping the future of military embedded systems.
Request Sample Report PDF (including TOC, Graphs & Tables): https://www.statsandresearch.com/request-sample/40644-global-military-embedded-systems-market
Military Embedded Systems Market Dynamics:
Technological Advancements Fueling Growth
The relentless pace of technological innovation is a primary catalyst for the expansion of the military embedded systems market. The integration of artificial intelligence (AI), machine learning, and Internet of Things (IoT) technologies into embedded systems has revolutionized defense operations. These advancements enable real-time data processing, predictive maintenance, and enhanced decision-making capabilities, thereby improving mission effectiveness and operational readiness.
Get up to 30%-40% Discount: https://www.statsandresearch.com/check-discount/40644-global-military-embedded-systems-market
Rising Demand for Secure Communication Systems
In an era where information dominance is critical, the demand for secure and reliable communication systems has escalated. Military embedded systems facilitate encrypted communications, ensuring the integrity and confidentiality of sensitive data across various platforms, including land-based units, naval vessels, and airborne systems. This necessity is further amplified by the increasing complexity of modern warfare, which requires seamless interoperability among diverse defense assets.
Integration Challenges and Cybersecurity Concerns
Despite the promising growth trajectory, the military embedded systems market faces challenges related to the integration of new technologies into existing defense infrastructures. Legacy systems often lack the flexibility to accommodate modern embedded solutions, necessitating substantial investments in upgrades and compatibility assessments. Additionally, the heightened risk of cyber threats poses a significant concern. Ensuring the resilience of embedded systems against hacking and electronic warfare is imperative to maintain national security and operational superiority.
Military Embedded Systems Market Segmental Analysis:
By Component
Hardware: This segment holds a substantial share of the military embedded systems market, driven by the continuous demand for robust and reliable physical components capable of withstanding harsh military environments.
Software: Anticipated to experience significant growth, the software segment benefits from the increasing adoption of software-defined systems and the integration of AI algorithms to enhance functionality and adaptability.
By Product Type
Telecom Computing Architecture (TCA): Leading the market, TCA supports high-performance computing and communication needs essential for modern military operations.
Compact-PCI (CPCI) Boards: Projected to witness robust growth, driven by the adoption of modular and scalable systems that offer flexibility and ease of maintenance.
By Application
Intelligence, Surveillance & Reconnaissance (ISR): Dominating the application segment, ISR systems rely heavily on embedded technologies for real-time data collection and analysis, providing critical situational awareness.
Communication and Networking: This segment is poised for growth, reflecting the escalating need for secure and efficient communication channels in defense operations.
By Platform
Land-Based Systems: Accounting for the largest military embedded systems market share, land platforms utilize embedded systems for enhanced situational awareness, navigation, and control in ground operations.
Airborne Systems: Experiencing significant growth due to the integration of advanced avionics and communication systems in military aircraft and unmanned aerial vehicles (UAVs).
Military Embedded Systems Market Regional Insights:
North America
North America leads the military embedded systems market, driven by substantial defense budgets and ongoing modernization programs. The United States, in particular, emphasizes technological superiority, investing heavily in research and development of advanced embedded solutions.
Europe
European nations are actively enhancing their defense capabilities through collaborative projects and increased spending on advanced military technologies. The focus on interoperability among NATO members and the modernization of existing systems contribute to market growth in this region.
Asia-Pacific
The Asia-Pacific region is witnessing rapid growth, fueled by escalating defense expenditures in countries such as China, India, and Japan. The drive to modernize military infrastructure and develop indigenous defense technologies propels the demand for sophisticated embedded systems.
Middle East & Africa
Nations in the Middle East are investing in advanced defense technologies to bolster their military capabilities amidst regional tensions. The focus on upgrading naval and airborne platforms with state-of-the-art embedded systems is a notable trend in this region.
Competitive Landscape
The military embedded systems market is characterized by intense competition among key players striving to innovate and secure significant contracts.
Recent Developments
Curtiss-Wright Corporation: In January 2025, Curtiss-Wright secured a USD 27 million contract to supply Aircraft Ship Integrated Securing and Traversing (ASIST) systems to the U.S. Naval Air Warfare Center for use on Constellation Class Frigates.
Kontron AG: In December 2024, Kontron AG received an order valued at approximately EUR 165 million to supply high-performance VPX computing and communication units for surveillance applications, highlighting its expanding role in the defense sector.
These developments underscore the dynamic nature of the market, with companies focusing on technological innovation and strategic partnerships to enhance their market positions.
Purchase Exclusive Report: https://www.statsandresearch.com/enquire-before/40644-global-military-embedded-systems-market
Conclusion
The global military embedded systems market is set for substantial growth, driven by technological advancements and the imperative for defense modernization. As military operations become increasingly complex, the reliance on sophisticated embedded systems will intensify, underscoring the need for continuous innovation and investment in this critical sector.
Our Services:
On-Demand Reports: https://www.statsandresearch.com/on-demand-reports
Subscription Plans: https://www.statsandresearch.com/subscription-plans
Consulting Services: https://www.statsandresearch.com/consulting-services
ESG Solutions: https://www.statsandresearch.com/esg-solutions
Contact Us:
Stats and Research
Email: [email protected]
Phone: +91 8530698844
Website: https://www.statsandresearch.com
#Military Embedded Systems Market#Defense Embedded Systems#Military Electronics#Embedded Computing Defense#Rugged Embedded Systems#Military IoT Solutions#Aerospace Embedded Systems#Military AI Technology#Tactical Embedded Systems#COTS Embedded Systems#Defense Avionics Market#Military Communication Systems#Secure Embedded Computing#Military Cybersecurity Solutions#Battlefield Management Systems#Embedded Processors Defense#Military Semiconductor Market#Real-Time Embedded Systems#Military Automation Solutions#Embedded Defense Electronics#4o
1 note
·
View note
Text
3 notes
·
View notes
Text
Reasons to Consider Modernising Your IAM

IAM stands for Identity and access management. Nowadays, Cyber attacks are more frequent and complex. Therefore, implementing advanced security measures has become essential.
Modernizing your IAM solutions with the latest technologies can ensure that you're secure, compliant, and able to respond quickly to changing business requirements.
What is IAM?
In simple words, Identity and access management (IAM) is the framework that enables the right user to access the right resources at the right times for the right reasons. IAM helps businesses control the access to their business-critical assets, making them more secure and accessible, all the time.
IAM is a powerful solution for managing users and assigning permissions. You can use it to give users access to specified resources on your network, revoke their privileges, and assign a single digital identity to each user.
IAM is no longer just for employees and clients. Digital transformation is bringing a new type of identity management to businesses. Organizations are moving to assign identities to the Internet of Things (IoT) devices.
Reasons to Consider Modernizing Your IAM
Automation
The outdated IAM system necessitates more manual work, which slows down business operations—not ideal in this fast-paced world. Automating these manual tasks is, therefore, necessary to maintain better efficiency.
Modern IAM systems automate and streamline processes to make it simpler to manage the majority of tasks automatically, saving much more time.
For instance, modern IAM uses data analysis to make intelligent decisions, recommending roles and permissions to new users based on the organization’s groups to which they belong.
Cloud
The majority of businesses are migrating to the cloud because it is more dependable and secure than on-premises infrastructure. It has become essential to move toward Cloud IAM solutions.
The benefits of cloud IAM include real-time information accessibility, dynamic and intelligent information updating, and the flexibility for your users to operate from any place and on any device.
Security
One of the most important reasons for wanting to upgrade from an outdated IAM solution is security concerns. Legacy IAM solutions are vulnerable to attacks and aren’t ready for the digital future.
A cloud IAM solution offers a better security approach than your old, outdated solution.
Real-time availability is one of the most effective advantage which can help identify the full scope of the security attack. It can help to identify which resources have been accessed and can take further actions to enhance security.
Best practices for migrating legacy IAM to a cloud-based solution
MFA Methods
A solid identity and access management (IAM) policy must include MFA (Multi-factor authentication) as a fundamental element. 99.9% of account hacking attempts can be stopped by MFA. MFA reduces the likelihood of a successful intrusion by requiring one or more additional verification criteria in addition to a username and password.
Cloud-based SSO
Cloud SSO eliminates password fatigue and lowers IT management overheads. Users only need to set up a single username and password. Therefore, providing a frictionless login experience without sacrificing security.
Zero Trust Security
Zero trust involves constantly checking who is authorized to access confidential papers, resources, and tools while giving each user the fewest rights possible.
Conclusion
You need to stay secure in today’s digital world, where cyber-attacks are common and threats can come from anywhere. Cloud-based access management is the way to go in this era, protecting your organization’s data and applications from loss, unauthorized use, and misuse.
#IdentityAccessManagement#IAM#CyberSecurity#CloudSecurity#DigitalTransformation#MultiFactorAuthentication#ZeroTrust#DataProtection#CloudComputing#Automation#SSO#SecurityBestPractices
1 note
·
View note
Text
Automated Cyber Audits & Smart Risk Assessment: The Future of Cyberrisiko Management
In today’s interconnected world, the question is no longer if a cyberattack will occur—it’s when. The stakes are higher than ever, with sensitive data, critical operations, and brand reputations constantly under threat. Traditional cybersecurity models that rely on manual monitoring and delayed assessments are no longer sufficient. What businesses need is a shift towards real-time, intelligent protection.
Cybersecurity automation
0 notes
Text
Dunedin City Council Partners with HCLTech for 10-Year Digital Transformation
HCLTech has entered a landmark 10-year strategic partnership with the Dunedin City Council (DCC) to lead a comprehensive digital transformation of its IT services. The collaboration aims to modernize and manage DCC’s digital infrastructure, enhance service delivery, and boost community engagement through cutting-edge technology. As part of the deal, HCLTech will revamp the Council’s IT services…
View On WordPress
#ai and cloud modernization#ai automation tools#ai in government#apac tech trends#automation in governance#cloud infrastructure#cybersecurity solutions#digital transformation 2025#dunedin city council#dunedin digital transformation#government digital strategy#govtech partnership#hcl bse#hcl cloud services#hcl DII holding#hcl dividend#hcl engineering services#hcl FII holding#hcl fundamental analysis#hcl investments#hcl it services#hcl long term investment#hcl market cap#hcl net profit#hcl nse#hcl outsourcing#hcl PE ratio#hcl revenue#hcl share forecast#hcl share price
0 notes