#Data Protection and Real Time Replication
Explore tagged Tumblr posts
Text
Disaster Recovery-as-a-Service Market to be Worth $31.6 Billion by 2032
Meticulous Research®—a leading global market research company, published a research report titled, ‘Disaster Recovery-as-a-Service Market by Operating Model (Managed DRaaS, Assisted DRaaS), Function, Organization Size, Sector (IT & Telecommunications, BFSI, Retail, Healthcare), and Geography - Global Forecast to 2032.’
According to this latest publication from Meticulous Research®, the Disaster Recovery-as-a-Service market is projected to reach $31.6 billion by 2032, at a CAGR of 20.5% from 2025-2032. The growth of the disaster recovery-as-a-service market is driven by the growing demand for data security and scalability, rising data breaches and ransomware attacks, and the growing adoption of disaster recovery-as-a-service in the BFSI sector. However, the complexity of deployment and setting terms restrains the growth of the disaster recovery-as-a-service market. Furthermore, the growing adoption of advanced technologies such as AI and machine learning and the increasing adoption of cloud-based solutions among SMEs are expected to create growth opportunities in the market. However, one of the major challenges for players operating in this market is the lack of awareness and misconceptions regarding disaster recovery service solutions among potential customers.
The disaster recovery-as-a-service market is segmented by operating model (managed DRaaS, assisted DRaaS, and self-service DRaaS), function (data protection, real-time replication, and other functions), organization size (large and small & medium-sized enterprises), and sector (BFSI, IT & telecommunications, retail, manufacturing, healthcare, government, energy & utility, and other sectors). The study also evaluates industry competitors and analyzes the market at the regional and country levels.
Based on operating model, the disaster recovery-as-a-service market is segmented into managed DRaaS, assisted DRaaS, and self-service DRaaS. In 2025, the managed DRaaS segment is expected to account for the largest share of the disaster recovery-as-a-service market. The large market share of this segment is attributed to the rising adoption of managed DRaaS in the IT & telecommunications sector, the rising need for business continuity across organizations, and the growing adoption of cloud solutions. In addition, the benefits managed DRaaS offers, such as fast recovery, enhanced security, minimized damage, actionable insight, and reduced cost, further support the growth of this segment. Also, this segment is projected to register the highest CAGR during the forecast period.
Based on function, the disaster recovery-as-a-service market is segmented into data protection, backup & recovery, and other functions. In 2025, the data protection segment is expected to account for the largest share of the disaster recovery-as-a-service market. The large market share of this segment is attributed to the rising number of data breaches and ransomware attacks, the rising demand for data security, and the growing demand for data protection in various sectors.
However, the backup & recovery segment is slated to register the highest CAGR during the forecast period. The rising adoption of cloud data backup, increasing risk of data breaches, and growing adoption of backup & recovery solutions in the BFSI sector are expected to support the growth of this segment.
Based on organization size, the disaster recovery-as-a-service market is segmented into large enterprises and small & medium-sized enterprises. In 2025, the large enterprises segment is expected to account for the larger share of the disaster recovery-as-a-service market. The large market share of this segment is attributed to the strong IT infrastructure of large enterprises, the management of disaster recovery platforms by skilled IT personnel, and the growing adoption of advanced technologies such as cloud, AI, and machine learning. However, the small & medium-sized enterprises segment is slated to register the highest CAGR during the forecast period.
Based on sector, the disaster recovery-as-a-service market is segmented into BFSI, IT & telecommunications, retail, manufacturing, healthcare, government, energy & utility, and other sectors. In 2025, the IT & telecommunications segment is expected to account for the largest share of the disaster recovery-as-a-service market. The large market share of this segment is attributed to the rising need for business continuity across organizations, growing adoption of cloud solutions, and cost-effectiveness and flexibility offered by disaster recovery-as-a-service that help mitigate downtime by faster recovery of business operations.
However, the BFSI segment is slated to register the highest CAGR during the forecast period. The rising fraudulent activities, rising adoption of disaster recovery-as-a-service for various financial processes, and surging need for improving the agility of work and customer experience are expected to support the growth of this segment.
Based on geography, the disaster recovery-as-a-service market is segmented into North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa. In 2025, North America is expected to account for the largest share of the disaster recovery-as-a-service market. North America’s major market share is attributed to the presence of prominent players offering advanced disaster recovery-as-a-service solutions to various sectors. Furthermore, the growing adoption of disaster recovery-as-a-service in BFSI, retail, and IT & telecommunications sectors; growing adoption of advanced technologies; and rising demand for data security are also contributing to the growth of the disaster recovery-as-a-service market in North America.
However, Asia-Pacific is projected to register the fastest growth rate during the forecast period. The rapid growth of this market is driven by the growth in regional economies, growing awareness regarding disaster recovery-as-a-service among small and medium-sized organizations, and the expanding retail and BFSI sector, especially in China, Japan, South Korea, and India.
Key Players
The key players operating in the disaster recovery-as-a-service market are IBM Corporation (U.S.), Microsoft Corporation (U.S.), Sungard Availability Services LP (U.S.), VMware, Inc. (U.S.), Axcient, Inc. (U.S.), Cloudian Inc. (U.S.), Acronis International GmbH (Switzerland), Oracle Corporation (U.S.), TierPoint, LLC (U.S.), Datto, Inc. (U.S.), Unitrends, Inc. (U.S.), Cloud4C Services Pte. Ltd (Singapore), Recovery Point Systems, Inc. (U.S.), Infrascale Inc. (U.S.), and InterVision Systems, LLC. (U.S.).
Download Sample Report Here @ https://www.meticulousresearch.com/download-sample-report/cp_id=5515
Key Questions Answered in the Report:
Which are the high-growth market segments in terms of operating model, function, organization size, and sector?
What is the historical market size for disaster recovery-as-a-service across the globe?
What are the market forecasts and estimates for 2025–2032?
What are the major drivers, restraints, opportunities, challenges, and trends in the global disaster recovery-as-a-service market?
Who are the major players in the global disaster recovery-as-a-service market, and what are their market shares?
What is the competitive landscape like?
What are the recent developments in the global disaster recovery-as-a-service market?
What are the different strategies adopted by major market players?
What are the geographic trends and high-growth countries?
Who are the local emerging players in the global disaster recovery-as-a-service market, and how do they compete with other players?
Contact Us: Meticulous Research® Email- [email protected] Contact Sales- +1-646-781-8004 Connect with us on LinkedIn- https://www.linkedin.com/company/meticulous-research
#Disaster Recovery-as-a-Services Market#Disaster Recovery Services#DRaaS Market#DRaaS#Cloud Security#Disaster Recovery#Managed DRaaS#Assisted DRaaS#Self-Service DRaaS#Backup & Recovery#Data Protection and Real Time Replication
0 notes
Text
#Linux File Replication#Linux Data Replication#big data#data protection#Cloud Solutions#data orchestration#Data Integration in Real Time#Data ingestion in real time#Cloud Computing
0 notes
Text
NAKIVO Backup and Replication v10.10 Beta: Real-time Replication for VMware vSphere
NAKIVO Backup and Replication v10.10 Beta: Real-time Replication for VMware vSphere @nakivo #vmwarecommunities #realtimereplication #ransomwareprotection #virtualmachinefailover #InstantVMRecoveryandP2V #DisasterRecoveryAutomation #disasterrecovery
NAKIVO has just released NAKIVO Backup and Replication v10.10 Beta with a great new feature that many will be interested in that will help bolster their business-critical data protection – real-time replication in VMware vSphere environments. Table of contentsWhat is Virtual Machine Replication?Features of VM replicationWhat is NAKIVO Backup and Replication?Core Offerings of NAKIVO Backup &…

View On WordPress
#business continuity#disaster recovery#Disaster Recovery Automation#Instant VM Recovery and P2V#NAKIVO Backup & Replication Overview v10.10 Beta#ransomware protection#real-time replication#User-friendly Data Backup Administration#virtual machine failover#VMware vSphere VM Monitoring
0 notes
Text
[remove paywall link]
“A few of us had noticed the prevalence of unnatural writing that showed clear signs of being AI-generated, and we managed to replicate similar ‘styles’ using ChatGPT,” Ilyas Lebleu, a founding member of WikiProject AI Cleanup, told me in an email. “Discovering some common AI catchphrases allowed us to quickly spot some of the most egregious examples of generated articles, which we quickly wanted to formalize into an organized project to compile our findings and techniques.” In many cases, WikiProject AI Cleanup finds AI-generated content on Wikipedia with the same methods others have used to find AI-generated content in scientific journals and Google Books, namely by searching for phrases commonly used by ChatGPT. One egregious example is this Wikipedia article about the Chester Mental Health Center, which in November of 2023 included the phrase “As of my last knowledge update in January 2022,” referring to the last time the large language model was updated. Other instances are harder to detect. Lebleu and another WikiProject AI Cleanup founding member who goes by Queen of Hearts told me that the most “impressive” examples they found of AI-generated content on Wikipedia so far is an article about the Ottoman fortress of Amberlisihar.
[...]
“One small detail, the fortress never existed,” Lebleu said. Aside from a few tangential facts mentioned in the article, like that Mehmed the Conqueror, or Mehmed II, was a real person, everything else in the article is fake. “The entire thing was an AI-generated hoax, with well-formatted citations referencing completely nonexistent works.” Fake citations, Lebleu said, are a more “pernicious” issue because they might stay undetected for months. Even if someone was using an LLM trained on a corpus of data relevant to the Wikipedia article, it could generate text that reads well and with correctly formatted citations of real sources, it still wouldn’t be able to correctly match a citation to a specific claim made in a specific body of work.
55 notes
·
View notes
Text
The Perfect Companion
(Author's note: This is a semi-continuation/spin-off of my Robot Elvis story. Since the original was written with inspiration from M3GAN, I thought I'd write something to celebrate M3GAN 2.0's release. This was also partly inspired by the classic infomercials like the ones with Billy Mays lol! Please forgive me if it's a bit clunky; this idea came to me as sort of a stream of consciousness, so it may be a bit rough in places. Still, I hope you enjoy it!)
(Link to the original story here.)
Scene: The ballroom of the International Hotel & Casino; classic footage of one of Elvis’s concerts plays on screen.
Announcer (In classic informercial tone): Let’s face it: We all want the best entertainment for our guests, and who doesn’t love the music and style of the King himself?
(Cuts to black and white footage of a ballroom of a hotel; on the stage, there is a clearly not-very-talented Elvis impersonator singing off-key and dancing horribly as people in the audience look on with dismayed and frustrated looks)
But who wants to waste their time watching cheap imitators of the greatest entertainers in the world who, more often than not, fail miserably?
Ouch! What a letdown!
Do you wish there was a better way? Well, now there is!
(Cuts to footage of the Elvis robot; a near-identical replica of Elvis himself, doing his famous lip curl, winking, and dancing for the camera)
Introducing ELV1S, from Aeon Robotics! The first automatic android designed to perfectly emulate the style of the legendary King, in every way possible!
(Cuts to footage of the robot in the famous comeback special suit performing various songs to a wildly appreciative audience; the robot speaks and sings in a perfect imitation of E’s voice)
Developed with memory implants containing several gigabytes of data consisting of the mannerisms, memories, and attributes of the real King, ELV1S was conceived to be a near-perfect replica of the famous entertainer, with a bit of flair of his own!
(Cut to a bit of distorted footage of the robot violently confronting a bully and chasing him out into the road before it cuts back to the regular footage)
ELV1S is made to the highest manufacturing standards. Dressed in the King’s famous comeback leather suit, he is engineered to replicate a real human’s body heat, texture and structure as closely as possible, and…programmed to satisfy.
(Brief distorted shot of the robot entering a bedroom with a woman, hearing distorted sounds of intimacy, before cutting to footage of the robot listening to and participating in a conversation, then to footage of him placing a meal in front of an appreciative family, then to him reading to the family as the voiceover continues)
Just need a companion? No problem; ELV1S is a fantastic listener! Developed around the 3 laws of robotics, and with the best in AI intelligence, he is engineered to protect and care for those he is paired with. He can easily learn what makes you tick, and even predict what to do based on his reading of your moods.
(Cuts to footage of the robot hugging a child and playfully scaring off “monsters” in the closet, briefly cutting to more distorted footage of the robot attacking an intruder and attempting to stab him, before cutting to the more normal footage of the robot playing with the child again)
ELV1S is a wonderful companion, protector, and fun for the whole family! And he can be all yours for only 4 easy payments of $499.95!
But wait! There’s more!
Call or go online in the next 20 minutes, and we’ll include both a set of embroidered black silk pajamas, plus the King’s famous American Eagle jumpsuit to dress your ELV1S in, for absolutely FREE! That’s right, an additional $280 dollar value, yours FREE! Just pay separate shipping and handling.
(A disclaimer is read very fast, stating “WARNING: Acts of bullying or perceived harm or tasteless jokes may provoke aggressive behavior in ELV1S. Aeon Robotics is not responsible for any instances of injury, maiming, death or dismemberment caused by ELV1S units. If any technical problems arise or persist, please call 1-800-555-AEON.)
Don’t wait! Order now!
@vintagepresley @mercsandmonsters @mooodyblue @kiankiwi @foreverdolly @elvispresleysdearestfangirl
9 notes
·
View notes
Note
HAI HAI HAI HAI!!!
I followed your rbg Trio blog, and ur art there is so So cute!!!
And I wanna know more about your 'robot boombox' au cus I'm curious and honestly, that headcanon is so real for boom!
EEEEK HAII ^_^
tyuu eueu... it means alot :3
so uhhh robot boombox au is pretty much just in my brain, i havent posted abt it or anything. but ive got vague ideas about it!
im gonna put bullet points under the cut in no particular order, cause again, this is mostly just concepts, so expect a bunch of yapping
in this au boombox would be created by someone, and was made to be a sort of 'testing device' for a manufactured gear (his boombox). while also being a sort of artificial life based on mimicry.
(note, i am not well versed in robotics stuff, if something seems stupid uhhh whoops)
i havent come up with a creator or creators, but they made him with the intent of seeing if they could basically make an artificial demon that could get along with other demons well! (thats where his creators got the idea to make him a dj, or a glorified mp3 player came from.)
hes entirely mechanical, his power source is through electrical charging. he charges often, which comes across as him sleeping often.
i imagine him with a charger tail that can also somewhat extend.
his visor is literally attached to his face and would be more emotive than regular boombox phighting
i imagine he got let out to interact with other demons, he was given a lot of carefully monitored data, and even now seeks out ways to be more empathetic, and to be responsive to others emotions and to help them.
he doesnt become evil or anything like that
his 'skin' would be some kind of rubber or latex, used to protect internal components and appear more demon-like.
he has two speakers imbedded in his chest, and in the rubber skin there'd be mesh to let sound travel clearer, which happen to look like top scars ( :P )
in place of where a human heart would be, he has an internal metronome, which he can set the tempo of. it can also be heard if youre super close, like a faux heartbeat.
his horns work as a secondary charging method throughout the day, acting like low powered solar panels, (like the ones youd find on calculators).
his horns take in uv light and convert it to energy. amd they are covered with a transparent solid material (imagine something like resin) to give the appearance of a normal demons horn. however this means charging through his tail is much more optimal than the passive uv charging.
has a database in his torso containing specifically music knowledge. audio can be downloaded to there and sorted and dissected to make him work better and understand the tastes of demons
in his heads a mini computer.
his mouth is a simple metal open close rectangle shape, with small components that either make the faux-skin sides of his mouth pull up (to make a smile) or down (to make a frown)
also in this au rgb trio still a thing because i am insane abt them
i imagine skate and sling learn that boombox is a robot, but they still care for him and treat him the same as before
he doesnt 'feel' anything in a person sense, and he hasnt gained sentience or anything. his programming makes it so he's drawn to other demons, and wants to make them happy. and in return, he feels 'happy' when he accomplishes that.
he learns about friends and other relationships and such, and if he has a few people he's especially close to that he can make happy just by being around, it means he's achieving his goal.
so he does have favorites, mostly because he learned that demons tend to have favorite people, and therefore replicated that behavior
he's in a qpr with skate and sling, who r both dating eachother, theyre all very affectionate.
sometimes if he gets too many positive inputs at a time, you can hear his fans running quicker (like, example, his partners are being super sweet to him, verbally or physically.
he doesnt know who made him, nor really cares to find out
when he was made, he was given the knowledge of about a 17 year old, and the mentality of one. he counts his birthdays as aging, being currently 23.
sometimes when him, sling and skate are sleeping together, he'll play calming music directly from himself.
he doesnt sleep, but shuts off non-essential components and kind of pretends to sleep while charging. since he has to be plugged into a socket of sorts. usually during that mode hes sorting any files, or things he's collected. throughout the day
sling and skate dont know that he isnt actually sleeping, and think he's just powered off
his gear works as youd expect, able to play music and use its abilities. he's just also able to directly play music from his body
when being created, he was made first, and the idea of an artificial gear came second. which is why theres overlapping abilities that may seem redundant.
his creators are no longer alive
his creators were from playground
he would likely be 'killed' for having an artificial gear and used for parts if certain people knew (the law)
and heres some silly sketches i made in class awhiiile ago (note again that i do not make robotics or know pretty much anything abt them. im just having fun ^^')

i yapped alot, but if you have any specific questions, put them in my askbox and ill happily answer! -w-
#phighting!#boombox phighting#phighting au#ill tag them since theyr mentioned i suppose..#slingshot phighting#skateboard phighting#boomskateshot#rgb trio#shrugs#this all appeared in my head because i listened to the song 'plug me in' awhile ago and got a little silly in my brain#also i love robots#ek ek ek..#kats sillyposting#i didnt check for errors or anything while writing this so uhhh shrug#:3#kat asks
21 notes
·
View notes
Note
Juice!!! I don't know if this is acceptable to ask, but what do you remember about nine, ten, and hubble? Do you remember just them?
.ohhhhhh boy do I have a little something for you.... first off! this is perfectly acceptable to ask, I love talking i will talk forever if you let me, second, please ask me about things you want to know about. i love filling people with information.
Nine, nine nine nine... boy oh boy. I remember Nine incredibly fondly.. so so fondly. they were never shy to ask questions or talk your ear off about anything that interested them. Nine picked this up from me i fear, afterall in my source what they were woken up to was me rambling about the similarities between football and the meaning of life itself, which, now looking back on it im pretty sure i was going insane, but thats fine we all have our moments up there. Nine was very loving and super duper willing to listen to anything youd want to yap about. Nine had an admiration for the savannah and liked to watch nature documentaries when they were bored. I do remember them freaking out about poaching/illegal hunting back in the day when it still happened when animals werent as protected as they were in the present (my present, in source). Nine was also fascinated about their sister, sometimes thinking about who was actually older and asking me what i thought, i think they came to the conclusion that ten was the older sister due to being more mature(??) i forgot the exact wording they used,. Nine was mentally about 13 when they first woke up, ten being mentally middle aged(?) actually. i dont know. she's mom friend to me.
Ten, i really liked hanging out with her, she was super comforting to me, dispite waking up a few hundered years after me, me and hubble tried our best to like, introduce her to the terrible life of living among the stars and being conceptually trapped forever, but she took it well and also like, stepped up. she was super responsible and always took the lead (when i wasnt fucking off LOL). She learned to open up and take down her walls, i liked the times she got careless and free and open, it gave me closure, made me feel? real almost. I dont know how to describe it but she was super important to me. thanks Ten for being number one. Hubble, uhhmmmm not much to say about Hubble, quiet, kept to himself often, shared pictures that were in UNGODLY large data files that made you nauseous when you opened them too fast, then youre BLASTED with like over 300 pictures of the same place on like, earth or something, got one(data pack full) of pluto and apparently it was so interesting that there were over 5000 pictures alone of the same fucking crater they thought was "geologically groundbreaking" whatever the hell that means. I remembered Hubble linking me random human articles that made no sense, of course i loved them but one of them was so incomprehensible that i had to spend a few days deciphering what the author COULD HAVE meant, i dont think i ever broke their heinous code of words but its fine im not too worried about it (i AM so worried about it. no one can replicate A SINGLE fucking word that was in that article.). Love my-in-source-hubble, thank you for being that autistic man that knows everything ever and if youre like "hey hubble whats (something he doesnt know)" and he gets anxious and starts researching like crazy then comes back after a few like weeks and goes "so, your question from last week, i did a little research and actually, did you know that-" and starts talking. i love my selective mutism boyfriend so much. someone get this guy a dictionary and an inhaler
#juice.txt#17776#17776 juice#17776 football#17776 nine#20020#500 signals all at once#17776 ten#17776 hubble#source memories ig#yeah#yappinator 5000
13 notes
·
View notes
Text
@ilingeron from VALENTINE.
Nick's head buzzed like a hornet's nest when he crept out of Anna's bedroom that morning just after sunrise. He usually liked to go into a job with a clear head, but it was easier said than done for a case like this.
His thoughts pulled back to Anna Winden every other step: The worry on her face, the defeat, the loneliness. Nick could tell himself all he wanted that he was investigating the new Mayor for the sake of Diamond City, but deep down he knew it was for Anna. It was for her peace of mind. It was for his own seething, bleeding heart.
Because the synth detective wasn't about to be pushed out of his home again by a newcomer. He wasn't going to watch the woman he loved torment herself in waiting for Robert House's next moves. Nick would act before the other shoe dropped-- he'd protect her, protect them.
Like you protected Jenny, huh.
The thought nearly tripped him up on the stairway up the stands to the Mayor's office, the flash of memory so overpowering it almost knocked him off his feet. Blood on the pavement. A trial on TV. It smelled like sea water and sewage. Blood on the pavement. Blood on the pavement.
Nick was in a meeting room. He was sifting through a file cabinet for a terminal password. House hadn't been here long enough to start putting things to paper, but it was long enough to keep digital logs. The detective knew House was a synth-- he'd seen the guy crawl out of an Institute replicator-- but nobody else would buy that from him without any hard proof. And even then, after the Institute went down, he'd have to further prove the guy was a synth with ill-intentions.
Nick Valentine almost missed when just being a synth was enough to get you kicked. The irony wasn't lost on him: in fact, the irony was a slug in the gut. What kind of man are you, Nicky?
Absentia-- the password. Bingo. Nick didn't have time to celebrate when he heard the rattling of a door. He'd given DC security the slip so far, but the clock was ticking again.
Was that House's voice? Shit.
Yellow eyes turned to the door: House's personal terminal was just further down the hall to the right. But if the man himself were there... he'd only have a couple seconds to get to that terminal, and the exit was in the opposite direction. That wasn't even counting the time it'd take to parse through the terminal's data. He'd be relying on luck that House would meander around a bit before heading back to his office.
So that's what Nick did. He crept down to the Mayor's office and bolted to that terminal--
BLOOD ON THE PAVEMENT.
The flash of memory nearly bowled him over. He was on a Boston street outside of Joe's Spuckies, yellow tape, yellow tape, blood on--
There were footsteps echoing down the hall, nearly outside the door. Nick had only just plugged in the password: data scrolled on the screen. Institute records.
Footsteps stopped outside the door. Valentine was trapped with only one exit now unless he wanted to make a stand: the window. A gap in the repurposed iron of the mayor's office, glassed off, slightly ajar. It fed out into the railing of the upper stands after a drop, but he had to copy the data.
No time.
By the time the door opened, Nick was already out the window, dropping in a freefall to the railing of the upper stands. He hit awkwardly, the sudden shock to his ankles enough to throw some bolts out of place. He dropped into a roll to try and absorb some of the damage, and came out on his hands and knees, nearly toppling down the stairs down to the market. He only slipped a couple steps, winced at the way his knee popped on impact, but stopped his momentum before he took any real damage.
Nick righted himself, grasping the railing, eyes closing for a moment.
No data. No proof. He'd seen it himself: Institute blueprints. But without a copy, who would believe him? Piper wouldn't run a story entirely on speculation. Anna would get no solace knowing they couldn't prove jack.
Nick lit up a cigarette as he started back to his office where Anna was waiting, his pace slow enough to not jostle his joints too much... and to bide time so he could think of a good way to say 'I beefed it.'
But as he finally rounded the corner of his alleyway, he could see that Anna wasn't alone.
12 notes
·
View notes
Note
Have you considered going to Pillowfort?
Long answer down below:
I have been to the Sheezys, the Buzzlys, the Mastodons, etc. These platforms all saw a surge of new activity whenever big sites did something unpopular. But they always quickly died because of mismanagement or users going back to their old haunts due to lack of activity or digital Stockholm syndrome.
From what I have personally seen, a website that was purely created as an alternative to another has little chance of taking off. It it's going to work, it needs to be developed naturally and must fill a different niche. I mean look at Zuckerberg's Threads; died as fast as it blew up. Will Pillowford be any different?
The only alternative that I found with potential was the fediverse (mastodon) because of its decentralized nature. So people could make their own rules. If Jack Dorsey's new dating app Bluesky gets integrated into this system, it might have a chance. Although decentralized communities will be faced with unique challenges of their own (egos being one of the biggest, I think).
Trying to build a new platform right now might be a waste of time anyway because AI is going to completely reshape the Internet as we know it. This new technology is going to send shockwaves across the world akin to those caused by the invention of the Internet itself over 40 years ago. I'm sure most people here are aware of the damage it is doing to artists and writers. You have also likely seen the other insidious applications. Social media is being bombarded with a flood of fake war footage/other AI-generated disinformation. If you posted a video of your own voice online, criminals can feed it into an AI to replicate it and contact your bank in an attempt to get your financial info. You can make anyone who has recorded themselves say and do whatever you want. Children are using AI to make revenge porn of their classmates as a new form of bullying. Politicians are saying things they never said in their lives. Google searches are being poisoned by people who use AI to data scrape news sites to generate nonsensical articles and clickbait. Soon video evidence will no longer be used in court because we won't be able to tell real footage from deep fakes.
50% of the Internet's traffic is now bots. In some cases, websites and forums have been reduced to nothing more than different chatbots talking to each other, with no humans in sight.
I don't think we have to count on government intervention to solve this problem. The Western world could ban all AI tomorrow and other countries that are under no obligation to follow our laws or just don't care would continue to use it to poison the Internet. Pandora's box is open, and there's no closing it now.
Yet I cannot stand an Internet where I post a drawing or comic and the only interactions I get are from bots that are so convincing that I won't be able to tell the difference between them and real people anymore. When all that remains of art platforms are waterfalls of AI sludge where my work is drowned out by a virtually infinite amount of pictures that are generated in a fraction of a second. While I had to spend +40 hours for a visually inferior result.
If that is what I can expect to look forward to, I might as well delete what remains of my Internet presence today. I don't know what to do and I don't know where to go. This is a depressing post. I wish, after the countless hours I spent looking into this problem, I would be able to offer a solution.
All I know for sure is that artists should not remain on "Art/Creative" platforms that deliberately steal their work to feed it to their own AI or sell their data to companies that will. I left Artstation and DeviantArt for those reasons and I want to do the same with Tumblr. It's one thing when social media like Xitter, Tik Tok or Instagram do it, because I expect nothing less from the filth that runs those. But creative platforms have the obligation to, if not protect, at least not sell out their users.
But good luck convincing the entire collective of Tumblr, Artstation, and DeviantArt to leave. Especially when there is no good alternative. The Internet has never been more centralized into a handful of platforms, yet also never been more lonely and scattered. I miss the sense of community we artists used to have.
The truth is that there is nowhere left to run. Because everywhere is the same. You can try using Glaze or Nightshade to protect your work. But I don't know if I trust either of them. I don't trust anything that offers solutions that are 'too good to be true'. And even if take those preemptive measures, what is to stop the tech bros from updating their scrapers to work around Glaze and steal your work anyway? I will admit I don't entirely understand how the technology works so I don't know if this is a legitimate concern. But I'm just wondering if this is going to become some kind of digital arms race between tech bros and artists? Because that is a battle where the artists lose.
29 notes
·
View notes
Text
#Linux#real time data replication#cloud computing#data management#big data#File Sync#file replication#EDpCloud#data protection#Data integrity#file mirroring#scalable data solutions#information security#Sysadmin
0 notes
Text
New Security Features for Canada’s Driver’s Licenses
As Canada advances into 2025, the security of driver's licenses is undergoing a significant transformation. With the integration of digital technologies and enhanced physical features, Canadian provinces are setting new standards to combat identity theft and fraud.

Enhanced Physical Security Features
Several provinces have introduced advanced security measures in their physical driver's licenses:
Alberta has redesigned its driver's licenses and ID cards to include high-definition laser-engraved photos, transparent windows shaped like Alberta and maple leaves, rainbow printing, and raised text. These features make the cards more difficult to alter or replicate .
Ontario is enhancing its digital infrastructure to support secure online services, strengthening cybersecurity, and leveraging digital tools to improve the verification process .
The Rise of Digital Driver’s Licenses
Digital driver's licenses are becoming more prevalent, offering several advantages:
Biometric Verification: Incorporating facial recognition and fingerprint scanning to ensure the rightful owner is accessing the license.
Encryption: Protecting personal data stored digitally to prevent unauthorized access.
Real-Time Verification: Allowing authorities to verify the authenticity of a license instantly, reducing the risk of fraud .
For more information on how to transition to a digital driver's license and understand the new security features, visit licenseprep.ca.
Preparing for the Transition
To ensure a smooth transition to the new security standards:
Stay Informed: Regularly check updates from your provincial licensing authority.
Upgrade Your Devices: Ensure your smartphone or digital wallet supports the latest security features.
Practice Digital Hygiene: Use strong passwords and enable two-factor authentication where possible.
For detailed guidance on preparing for the upcoming changes, licenseprep.ca offers comprehensive resources.
Canada's commitment to enhancing the security of driver's licenses reflects a proactive approach to safeguarding personal information. By embracing these new features, Canadians can enjoy increased protection against identity theft and fraud.
2 notes
·
View notes
Text
Federal Reserve Governor Michael Barr is urging banks to begin collecting behavioral and biometric data from customers to combat deepfake digital content created through ID. These deepfakes are capable of replicating a person’s identity, which “has the potential to supercharge identity fraud,” Barr warned.
“In the past, a skilled forger could pass a bad check by replicating a person’s signature. Now, advances in AI can do much more damage by replicating a person’s entire identity,” Barr said of deepfakes, which have the “potential to supercharge identity fraud.”
“[We] should take steps to lessen the impact of attacks by making successful breaches less likely, while making each attack more resource-intensive for the attacker,” Barr insists, believing that regulators should implement their own AI tools to “enhance our ability to monitor and detect patterns of fraudulent activity at regulated institutions in real time,” he said. This could help provide early warnings to affected institutions and broader industry participants, as well as to protect our own systems.”
Enabling multi-factor authentication and monitoring abnormal payments is a first step, but Barr and others believe that banks must begin to collect their customer’s biometric data. “To the extent deepfakes increase, bank identity verification processes should evolve in kind to include AI-powered advances such as facial recognition, voice analysis, and behavioral biometrics to detect potential deepfakes,” Barr noted.
Barr would like banks to begin sharing data to combat fraud. Deepfake attacks have been on the rise, with one in 10 companies reporting an attack according to a 2024 Business.com survey. Yet, will our data be safer in the hands of regulators?
2 notes
·
View notes
Text
Develop Your Own Crypto Gambling Game with Ready-Made Scripts
The online gambling industry is experiencing a significant transformation with the integration of cryptocurrencies and blockchain technology. Entrepreneurs aiming to enter this dynamic market can now leverage ready-made scripts to develop their own crypto gambling games efficiently. These scripts offer a streamlined approach to launching platforms similar to established names like BC.Game, providing a foundation for a secure and engaging gaming experience
Understanding Crypto Gambling Game Development
Crypto gambling games utilize blockchain technology to offer transparent and decentralized gaming experiences. By employing cryptocurrencies for transactions, these platforms ensure faster, more secure, and often anonymous operations. Ready-made scripts serve as pre-built solutions that replicate the functionalities of successful crypto casinos, enabling developers to customize and deploy their platforms swiftly.
Advantages of Using Ready-Made Scripts
Implementing a ready-made script for crypto gambling game development presents several benefits:
Cost-Effectiveness: Developing a platform from scratch can be resource-intensive. Ready-made scripts significantly reduce development costs by providing a foundational structure.
Time Efficiency: These scripts accelerate the development process, allowing for quicker market entry.
Customization: While offering a base structure, these scripts are often customizable, enabling developers to tailor the platform to specific requirements and branding.
Security and Fairness: Many scripts incorporate provably fair algorithms and robust security measures, ensuring a trustworthy gaming environment.
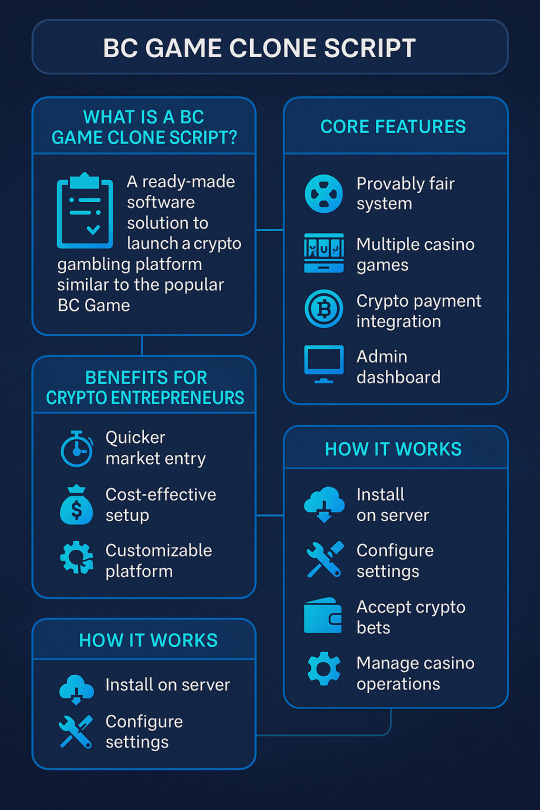
Key Features to Consider
When selecting a ready-made script for crypto gambling game development, it's essential to evaluate the following features:
Provably Fair Gaming: Ensures transparency by allowing players to verify the fairness of each game outcome.
Multi-Currency Support: Facilitates transactions with various cryptocurrencies, enhancing accessibility for a broader user base.
User-Friendly Interface: An intuitive design improves user engagement and retention.
Scalability: The ability to add new games and features as the platform grows is crucial for long-term success.
Security Measures: Implementing SSL encryption, two-factor authentication, and secure payment gateways protects user data and transactions.
Integrating Popular Games
A diverse game portfolio attracts a wider audience. Consider incorporating
Casino Slot Games: A staple in online gambling, offering various themes and gameplay mechanics.
Table Games: Including classics like blackjack, roulette, and poker.
Live Dealer Games: Provide an immersive experience by streaming real dealers in real-time.
Unique Crypto Games: Games like crash, dice, and plinko cater to crypto-savvy players seeking novel experiences.
Steps to Launch Your Platform
Market Research: Understand your target audience and competitors.
Select a Script: Choose a ready-made script that aligns with your business goals and offers the desired features.
Customization: Tailor the platform's design, games, and functionalities to reflect your brand identity.
Licensing and Compliance: Ensure your platform adheres to legal regulations and obtains necessary licenses.
Testing: Conduct thorough testing to identify and rectify any issues before launch.
Marketing Strategy: Develop a comprehensive marketing plan to attract and retain users.
Launch and Monitor: Deploy your platform and continuously monitor performance, making improvements as needed.
Conclusion
Developing a crypto gambling game using ready-made scripts offers a practical and efficient pathway into the burgeoning online gambling market. By focusing on essential features, ensuring security and fairness, and delivering a diverse gaming experience, entrepreneurs can establish a competitive platform that appeals to modern players.
Ready to Launch Your Crypto Gambling Platform?
Take the first step towards entering the crypto gambling industry by choosing a reliable ready-made script. Customize it to fit your vision, and offer players a secure, fair, and engaging gaming experience. Start your journey today and capitalize on the growing demand for crypto-based gambling platforms.
1 note
·
View note
Text
Rockman.EXE and Cyber Security.

When you are a Rockman/Megaman Battle Network fan and you take a college course about networking, you start to notice how broken the internet is in the anime. So just for fun, I want to talk about a few things I learn about network security and how it is interpreted in the Megaman Battle Network anime.
1. Firewalls
What are firewalls? In simple terms, it is a security barrier that is placed between a private network and the public network.
They are configured to monitor and filter networking traffic, hackers go through them by figuring out how they are programed, once they do they can either bypass the security undetected or simply disable the firewall.
Lets take a scene from the movie where Lan sends Megaman into a secretary’s console to destroy a program inside a company’s server.

Megaman is running through the network between the console and the firewall, which protects the private network of the company.

Logically, for Megaman to go through the firewall, he is going to need to use his powers as a Net Navigator (Net Navi) to analyze the firewall at an incredible speed to try to find a way to go through it, right?
WRONG! Battle Network logic says you can just break it with brute force!

You see the problem?
Does this mean Navis and battle chips are just as destructive to the net as viruses? Because last time I checked, Viruses and malware are the only programs with the ability to destroy networks.
2. Viruses
Viruses are man made, they are programed with a purpose that’s usually to destroy data files. They can also be used to change and manipulate programs, that’s why you can see evil Navis controlling viruses to do specific jobs for them. Viruses can’t replicate on their own without a user interface, so how is this Moloko a baby?!

There was an undubbed episode of Megaman Axess where Rush meets and befriends a baby Moloko virus, which doesn’t make any sense. Yes, Rush is a virus, and it has been established that viruses can communicate with each other, but why does this Moloko have parents? And why was the group of Molokos it separated from was being herded by other viruses like Trumpy? All I’ve seen Molokos do is charge at megaman when they see him, trying to ram him. Why would someone herd them? For the wool? It disappears after you hit it!
And what even is Rush’s purpose anyway? When he first appeared in the anime, he was made to track down Rockman’s frame or structure when they were trying to revive him with the backup data, but now?
All he does is being a crappy character who runs away when things get dangerous, doesn’t act like a dog anymore, and irritates me because he can move between the cyberworld and the real world! He is selfish, lacy, and practically useless, there are several times where Megaman goes missing and Rush is never even called to track him down, so he doesn’t even have that ability anymore.
On a positive note, viruses can be interesting, I found out that there are different types of viruses. For example.
A Stealth virus is a virus that avoids detection from anti virus software, this means it can conceal itself and attack without being spotted, sounds familiar? In this case the anti-virus software would also include Navis.
A retro virus tries to destroy anti-virus programs, I like to think these apply to viruses who specifically target Navis in battle like Canodumbs and Piranahs since they only attack when they detect an enemy in the line of fire.
Armored Viruses are hard to detect or analyze because they have a protective code, These could be Viruses with armors or auras like the Dominerd or even the life virus.
But Phage viruses remind me of these guys because they rewrite programs.

And I guess this one counts too?

Other viruses just act like malware, like the Alpha bug that is more of a worm than a virus, because it can replicate and travel across networks without any human assistance.
Others are obvious like the Pop up virus which is just Rush, and it is supposed to be adware, but just like Rush, it is more annoying than harmful.
In the anime, killereye viruses are used as spyware, there was an episode were Videoman used them to spy on Rockman and make copies of him.

3. Tracing a signal.
Basically, everything you do on the net leaves bread crumps or cookies behind that makes it easy to track a user online, every device have a Mac Address and every network has an IP address, but it takes a special kind of software and advance skills to track down somebody in the real world.
Let’s talk about episode 32 of Stream.
Remember that episode were Megaman followed a revived Shademan to 20 Years in the past and he witnessed a famous hacking incident that was stopped by Colonel?

Aside from the fact that it was 20 years in the past and Megaman is more advance than most of the technology there, there were a few things bothering me.
For starters, why does that computer show a little Colonel doing something to that guy’s hacking program? It’s cute and all, but this is a confusing way to show someone disabling a program, it usually just shows a notification. Or is that how the computer sees colonel, like a little pixel version of him? XD
That hacking program was made to open any cyber lock, it uses three special pillars to disguise the signal so the police wouldn’t be able to track down the address, this means those pillars have some special form of encryption to cover the data to make it untraceable. In the anime’s world, that means it’s invisible, but somehow Megaman can still sense it? And how did Barryl know where the guy was? Did colonel tell him? Or did the viruses he sent to delete colonel revealed his location? Oops.
4. Hard Drives.
To end this post, what are hard drives? They are what your computer uses to store files, so Navis can obviously be stored in a computer as well. The problem is that they are still sentient inside the computer instead of dormant.
The concept of containing a Navi, yes, Navis have their own jail in this universe, doesn’t really make any sense. We know Navis can sleep, but the Navis we see in cages are still active, and if everything is connected to the internet, how can they not escape?
I’m using this scene with Megaman as an example, when he was arrested for being in the wrong place at the wrong time, he was put in a cute little cyber cage.

However, since Megaman is more advance, he wonders if the hard drive of the computer he is stored in is weak against vibrations. What does he mean by that? Physical or cyber vibrations? Does that mean he can control a frequency in that computer’s cyberworld to alter it?
Whatever he did worked, because he left a gap in the cage, but how did he do it without damaging the Hard Drive? The police officer wouldn’t be able to access his files anymore, maybe it was minor file corruption?
And the worst part is that he opened a gateway into the internet, which is still there! I guess Megaman can travel through routers by himself? Maybe that wouldn’t have happen if the officer just disconnected his ethernet cable.
This Network based world is a scary one.
51 notes
·
View notes
Text
• the batshit lack of scientific literacy which leads people to not comprehend basic true things like:
biology (trans people are real, gender & sex are a spectrum in every species, this is biological fact). AMA American Medical Association supports this. gender norms are social depending on time period & culture
vaccines (viruses & bacteria exist and we know how to treat them). one of the safest & most effective forms of medicine that exists.
masks work (see above) because they protect against against certain sizes of particles or droplets which can transmit disease
climate - if you dump hot sewage into a lake it becomes polluted & the temp increases. pretend the sky is a big lake and everyone's CO2 is sewage.
antibiotics - stop taking them bc you have the sniffles, you are increasing antibiotic resistance & that is dangerous for the whole community/world. if you have a fever or purulent discharge ANYWHERE, that is the time to go to the clinic for eval. antibiotics DO NOT WORK against VIRUSES or ALLERGIES. Anti-biotic means anti-bacteria. second, you cannot take ANY rando antibiotic for a UTI. every UTI is different and can be caused by a diff bacteria, meaning you will make it worse if you take the wrong antibiotic/increase your resistance to that antibiotic. you HAVE to take your antibiotic in the time it says on the label AND the full course, this is rigorously designed to decrease antibiotic resistance by making sure the bacteria does not replicate in your body enough to overcome the antibiotic in the time it takes for that SPECIFIC ANTIBIOTIC to be metabolized (it involves MATH based on TYPE OF BACTERIA treated - gram pos or gram neg)
essential oils - many essential oils and natural medicinals do work (in context and to a degree)! stop shitting on people who use them you just alienate them from medicine. there is a time for natural cures and a time for acute cures (antibiotics, broken bones, vaccines, cancer treatment or surgery, preventative med scans etc). there are LOTS of schools of medicine - allopathic (Western), TCM, Ayurveda, Quantum medicine, energetic medicine, herbal medicine. All of these have credible research supporting them. Integrative medicine (combining them all) is the future
flouride - it is not poisoning you and it's good for you if you live in a country where it is highly regulated (FDA does regulate, ADA approved and endorses)
the weather - it is not possible with our current technology to control the weather to the degree of hurricanes, blizzards, floods. if it was, someone would have done it and we'd all be dead. cloud seeding is an example of a weather tech that does exist & it's an example of this bc it causes increased respiratory illness where it is done.
clean energy - the only reason we dont have it or highspeed worldwiderail or a highspeed universal translator is... obvious. because those are very much attainable with current tech. we also have buildings with rooftops and free sunlight. free. sunlight. free. energy.
AI - it needs regulation & laws on image/text/audio recording, artistic theft, and data gathering. Right now all it does is steal data & give misinformation. It COULD be used for good (medical imaging assistance) but overwhelmingly is not right now.
things we need to address:
gen z men getting pulled into alt-right pipelines through andrew tate, joe rogan, elon musk, jordan peterson etc
the gullibility and stupidity of half the country voting against our collective best interests
the broad effect social media has on public and common good
lazy minds and lack of empathy
outside-country interference (trump and elon’s connections to russia and the amount of bots from other countries spreading misinformation)
the long-term effects of AI and rampant disinformation
58K notes
·
View notes
Text
The Real Cost of Downtime: How EDSPL’s DDoS Defense Keeps You Online 24x7

Introduction: When Seconds of Downtime Turn Into Millions
Imagine this: It's 10 a.m. on a Monday. Your ecommerce site is flooded with visitors. Just when sales peak, your server crashes. Not because of faulty code. Not due to hosting issues. But due to a Distributed Denial of Service (DDoS) attack.
Your site is down for 15 minutes. In that small window, you lose thousands in revenue, customer trust takes a hit, and your brand reputation suffers.
This isn’t a theoretical scare tactic. Downtime costs real money, and the impact is bigger than most businesses estimate.
In this blog, we’ll uncover:
What DDoS attacks really cost you
How attackers exploit vulnerabilities
Why traditional defenses aren’t enough
And how EDSPL’s DDoS protection gives you 24x7 peace of mind
Section 1: The Hidden Price of Downtime
You might think a few minutes offline is no big deal. But here’s what it really means:
Revenue Loss
Amazon once estimated that every second of downtime costs them $2,300. Even a small ecommerce store making ₹50,000/day can lose ₹10,000 or more in 30 minutes of downtime.
SEO Rankings
Search engines like Google penalize websites that face frequent downtime. This impacts organic traffic, crawl frequency, and eventually revenue.
Customer Trust
Users won’t wait. If your site’s down, they click away—to your competitor. Brand trust takes time to build, but one failed transaction can break it instantly.
Operational Chaos
Your support team is flooded with queries. Internal teams scramble. Productivity drops. Business operations suffer.
Security Risk Amplification
Downtime can be a smokescreen for larger attacks—like data theft, malware installation, or ransomware. A DDoS attack can serve as a diversion, while your real assets are being breached.
Section 2: What Makes DDoS Attacks So Dangerous?
A DDoS (Distributed Denial of Service) attack overwhelms your systems with traffic, making them crash or become inaccessible.
Types of DDoS Attacks
Volumetric attacks – Flood bandwidth (e.g., UDP floods)
Protocol attacks – Exploit network stack (e.g., SYN floods)
Application-layer attacks – Overload app endpoints (e.g., HTTP floods)
Why Firewalls Aren’t Enough
Basic firewalls can’t keep up with high-volume, multi-vector DDoS attacks. They’re built for rules-based protection, not real-time adaptive filtering.
That’s where EDSPL’s network security makes all the difference.
Section 3: EDSPL’s Always-On DDoS Defense — What Sets It Apart
While other providers offer reactive solutions, EDSPL provides proactive, AI-powered DDoS protection, built for scalability and speed.
24x7 Monitoring & Mitigation
With EDSPL’s fully managed Services, your digital assets are monitored continuously by our Security Operations Center (SOC). Mitigation begins the moment malicious traffic is detected.
Advanced Traffic Scrubbing
We inspect packets in real-time and remove malicious requests before they reach your application, preserving availability for real users.
AI-Based Anomaly Detection
Our systems learn your traffic behavior over time, identifying unusual activity patterns and preventing false positives.
Scalable Cloud Infrastructure
Attacks keep growing in size—and so does our defense. EDSPL leverages cloud security infrastructure that automatically scales to meet peak loads during attack surges.
Section 4: How Downtime Affects Your Digital Backbone
Most companies don't realize how downtime paralyzes not just their front-end, but the entire IT ecosystem. Here’s how:
Mobility Gets Disrupted
Remote teams, mobile apps, and field staff lose access to critical systems. This impacts productivity and customer service.
Routing & Switching Bottlenecks
Infrastructure gets choked, rerouting requests inefficiently, increasing latency, and hurting performance even after systems are "back."
Storage & Backup Failures
Automated backups, scheduled replications, or live transaction logs may fail mid-execution, leading to data inconsistency.
Compute Overload
Your cloud compute instances get overwhelmed during volumetric attacks, costing you not just downtime, but skyrocketing cloud bills.
Data Center Switching Errors
Heavy attack loads can exhaust your switching capacity, leading to internal data path failures inside your data center.
Section 5: Case Study – How EDSPL Saved a Leading NBFC
In early 2024, a leading NBFC in India faced a DDoS attack targeting its user verification API.
Servers went down for 18 minutes
Customers couldn’t log in to pay EMIs
A high volume of support tickets were raised
EDSPL was called for emergency mitigation
What We Did:
Diverted incoming traffic through our global DDoS scrubbing nodes
Restored operations within 6 minutes
Installed full-time managed and maintenance services for 24x7 uptime
Result: They now experience zero downtime during peak hours, with consistent transaction throughput.
Section 6: The EDSPL Advantage — What You Get Beyond Defense
With EDSPL, it’s more than protection. It’s a strategic cybersecurity partnership.
✅ Custom DDoS Mitigation Plans
Tailored by use case: banking, ecommerce, SaaS, logistics, healthcare, and more.
✅ Dashboard for Real-Time Insights
Live analytics on attacks, traffic volume, IP geolocation, and mitigation actions—no guesswork.
✅ Unified With Other Security Layers:
Application Security
Cloud Security
Network Security
✅ Vision-Driven Implementation
Our background vision is to enable secure digital growth across enterprises by ensuring nonstop service availability.
Section 7: DDoS Defense ROI — A Smart Investment
Improved SLAs & Customer Trust
Your customers won’t even notice an attack—because your services don’t go down.
Cost Saving vs. Recovery Cost
Downtime = ₹5L – ₹50L losses depending on the scale
EDSPL’s cost-effective defense = a fraction of that
Performance Boost
Without junk traffic, your systems perform better. You serve real users faster.
Seamless Integration
Whether you're on public cloud, private cloud, or hybrid infrastructure—no redesign required.
Section 8: A Call to Action — Don’t Wait Until It’s Too Late
If your business is online, DDoS attacks are inevitable. The only choice is:
Wait until it happens? Or prepare in advance with EDSPL?
📞 Call Us: +91-9873117177 📧 Email: [email protected] 🌐 Visit: www.edspl.net
✅ Reach Us | ✅ Get In Touch
Let’s make your brand unbreakable.
Final Thoughts
At EDSPL, we believe security shouldn’t be reactive—it should be resilient.
Whether you’re a startup or an enterprise, uptime is the lifeline of your business. And we’re here to guard it every second of every day.
Because in the digital age, downtime is destruction—and EDSPL is your shield.
0 notes