#Digital Security
Explore tagged Tumblr posts
Text
diy hrt: how to safely search & order online
BEFORE YOU DO ANYTHING ONLINE RELATING TO DIY read this <3
as many institutions seem to be already complying in advance and without resistance to gender affirming care bans (eye roll) i wanted to back into posting on here about accessing diy t.
first of all, stop using Google as your search engine. google search histories HAVE ALREADY been used in court, meaning law enforcement could request your search history and use it against you. incognito browsers do not actually give you any meaninful privacy either.
here's your mini digital security checklist:
-download TOR (aka the onion router) a free, privacy-focused browser. it's legit, it's used by many, many people for many different reasons. it has important features that help keep you more private online - their webpage has a great description of how it works.
-download a good VPN. (no VPN you've seen advertised in a youtube video will actually be good.) often they require payment, for a free one the ProtonVPN is fine. as long as you're in a country where usage of TOR is common it's less of a big deal, but still good. launch your VPN before launching TOR.
-while on TOR and your VPN, create a private email. ProtonMail is fine, there are other options if you want to look more deeply. only access this email through TOR, and create a very strong password. when you're shopping for your diy, you'll need to create an account with an email, so use this email for that and not for other things.
-get some bitcoin. it's annoying especially when that pay with paypal/bank transfer/credit card option is so easy, but it's really worth it. we go way into depth about this in the guide but the more familiar you get with using crypto for privacy, the more protected you can be when making purchases online.
the guide in our pinned post has more info including lots of places to look for different btc, mail, vpn, and other privacy services. and add on if you have other digisec checklist items!!
#digital security#diy hrt#diy testosterone#diy t#trans#transmasc#ftm#mutual aid#trans men#midwest#ftm hrt
476 notes
·
View notes
Text
This page is organized into different security-related threats. You can jump to the ones that most concern you. Along with each scenario is a list of digital security tips to neutralize the threat!
These are possible concerns you might have:
Seeing advertisements related to pregnancy/abortion
Tech companies like Facebook and Google storing information about your pregnancy/abortion
That the person who pays your phone bill can see your texts
That someone who can access, steal, or demand your phone will see your messages or your browsing history
Your phone company keeps copies of your browsing history or texts about your abortion
Protestors outside the clinic may violate your privacy
* New *: Abortion Mobile Privacy Settings Quick Guide
Read the full piece here and PLEASE SHARE THANKS!
https://digitaldefensefund.org/ddf-guides/abortion-privacy
#privacy#privacy resources#feminism#feminist#abortion#pregnancy#digital security#online security#abortion privacy#pro choice#pro-choice#abortion rights#reproductive rights
255 notes
·
View notes
Text













Cyberdom, Moscow, Russia,
Courtesy: VOX Architects
#art#design#architecture#interior#interiors#cyberdom#moscow#russia#vox architects#white rabbit#space#event space#multifunctional#it industry#digital security
72 notes
·
View notes
Text
from @/frontlinemedics on instagram:
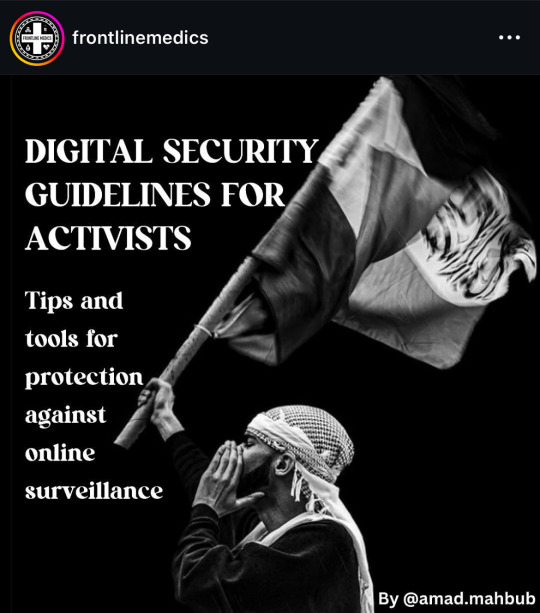
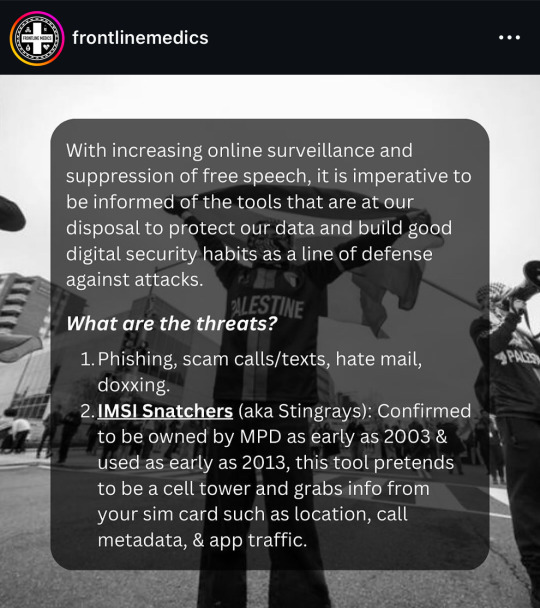
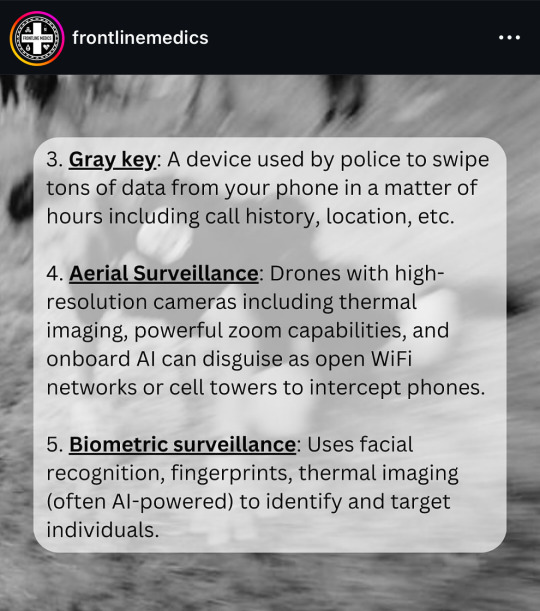
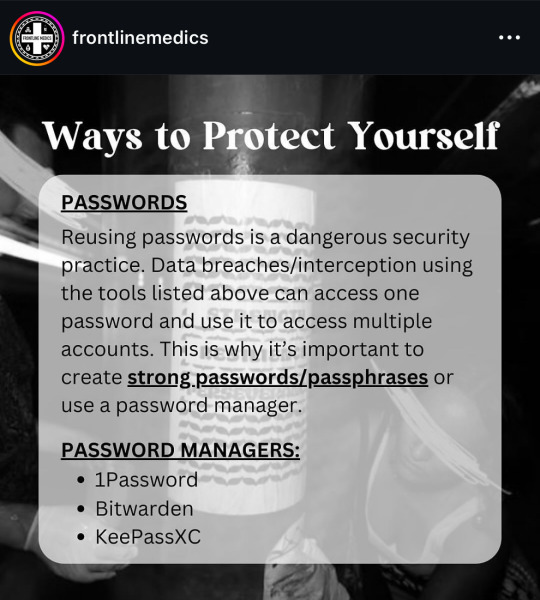
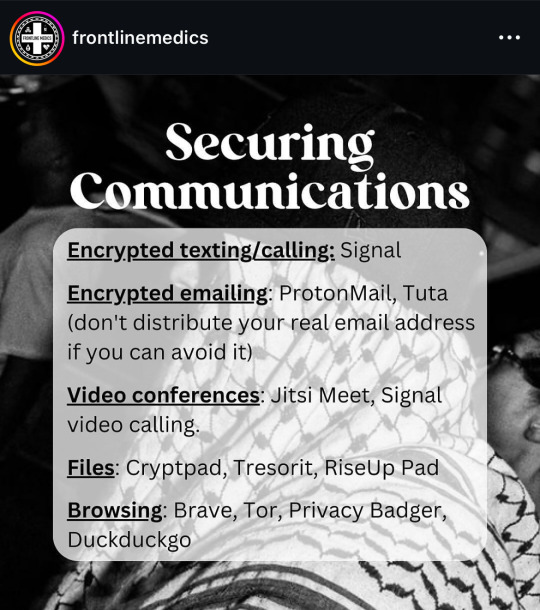
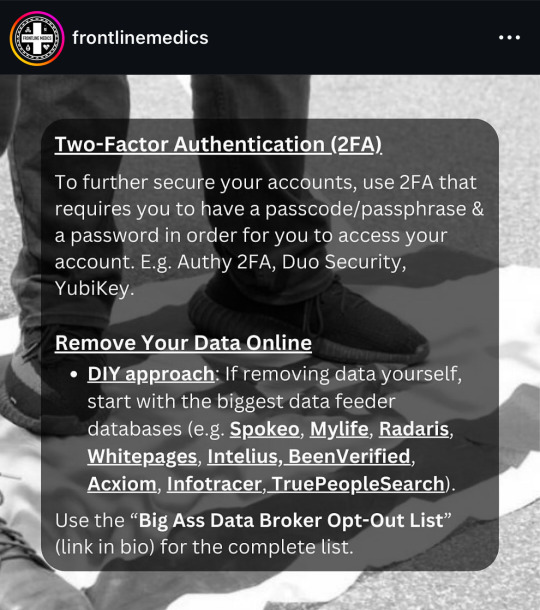
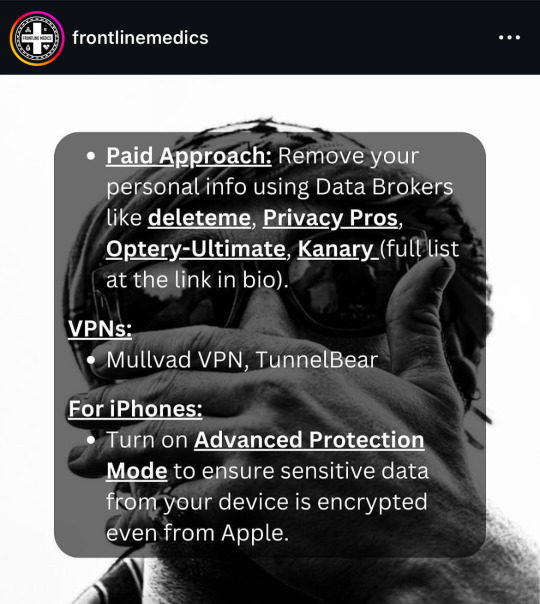

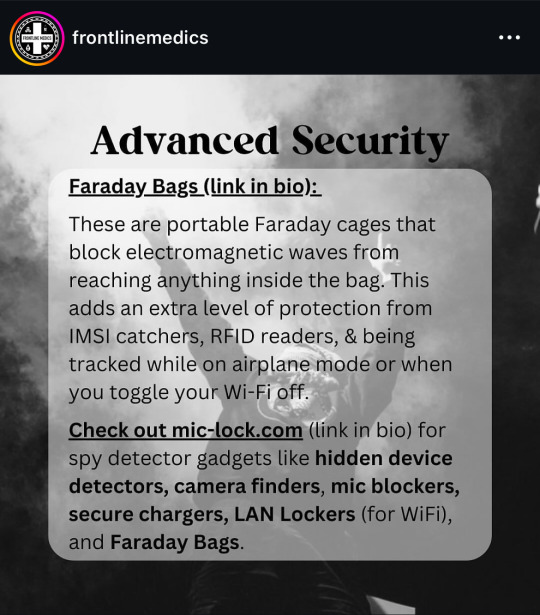
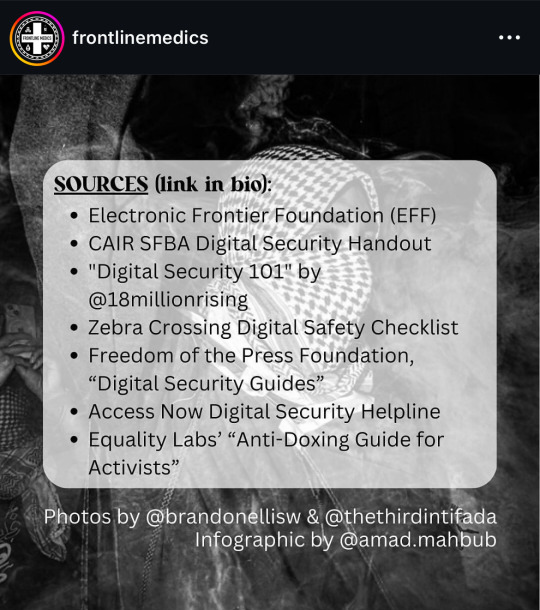
i use several of these resources so i can vouch for them!!
the link in bio mentioned in the post: https://linktr.ee/amadmahbub
108 notes
·
View notes
Text

Now your abusers and stalkers can still stalk you on Twitter even if you block them. Thanks Elon.
Source SmoothDunk on twitter
145 notes
·
View notes
Text
16 notes
·
View notes
Text









There are many reasons an abortion may have to be a secret - from state laws to immigration status.
Check out these tips for safely finding accurate reproductive health information and care online.
Alt-text included on all pieces
#art#feminism#digital security#digital art#online tips#abortion#reproductive health#reproductive rights#reproductive justice
1K notes
·
View notes
Text
Digital Security and Executive Functioning
Ideally, I would have better digital security, but spending one afternoon trying to improve it left me drained and on chat with tech support to regain access to my phone (facepalm). I use my phone and computer for basic life things- to remember to eat, drink, sleep, and take meds, to the degree that I can, to remember to feed the cat, let the aide in, wake up and not sleep all day, go places when I must, etc. I do my medical appointments and mental health treatments on my devices. I track my symptoms on my devices. I do my pacing on my devices. I order my groceries, household items, and pet supplies on my devices. Most of my socialization happens on my devices. And most days, I struggle immensely with the number of steps needed to access these things on a barely-secured device with all my apps on the desktop/homescreen. I type the name of who I want to talk to in as my password. If I manage to type my password, I cannot figure out what program to launch to access what I need and often type the food I want to buy or the person I want to talk to in the search bar, instead of the program I need. Very, very often, I cannot access what I need until hours later or the next day because I just don't have the executive functioning. And remembering multiple passwords without storing them in my computer and having them auto-fill-in? Forget it! Same with payment methods. So adding just 1 more layer, like 2 factor authentication, a sim card password, or device encryption, completely eliminates my access to the device or program. And that's really frustrating. Open for tips for low-spoons, low-executive functioning security hacks. I want to feel safe doing ac tivis m-y things from my devices.
#actually autistic#actually disabled#actually chronically ill#actually mentally ill#actually adhd#actually did#actually cptsd#digital security#executive dysfunction#executive function#actually homebound#actuallly housebound#homebound#housebound#disability
5 notes
·
View notes
Text
Ad ID Tracking
Your phone's advertising ID not only tracks what you look at & where you shop, but it can also track your physical movements and sell that data to third parties.
Here's Check My Ad's video about advertising ID's, and here's an article on how to delete your ad ID in Apple and Android phones.
6 notes
·
View notes
Text
4chan: The Internet’s Mos Eisley Cantina Takes Another Hit
In the chaotic world of online forums, 4chan stands out like a neon sign in a dark alley. Dubbed the “cesspool of the internet,” it has a reputation for being the lawless Doge City of the online world. This notorious imageboard has seen its fair share of craziness, and now, it’s down again—this time, apparently hacked. On April 14, 2025, users began reporting that 4chan was loading slowly. By…
#4chan#anonymity online#conspiracy theories#Controversy#cybersecurity#digital privacy#digital security#far-right extremism#forum hacks#hacking news#internet culture#internet escapades#internet forum#internet memes#lawless internet#meme culture#meme history#online anonymity#online communities#online trolls#PHP vulnerabilities#source code leak#Soyjak.party#Tech News#viral content
2 notes
·
View notes
Text
11 notes
·
View notes
Text
Day 3: We've found another income stream 💸💸💸
So I found new abundance affirmations by Kinder Records on Apple Music.
I listened to them all morning and then on the way out of the house I got an idea for a second income stream.
I'll tell yall about it in a few weeks once I get the ropes all in place but I'm really excited. I got the same feeling I got about Ladder and Safer Internet Project. I'm really good at picking valuable and efficient resources and guide me to a better life.
As for my IT Business. I'm still making strategic moves to get that rolling as well. I'm so proud of myself for staying diligent this time around.
(Stay away from people who don't have the same drive as you. They will drag you down. Take it from me. Someone with a lot of personal experience dealing with people not aligned with me energetically)
Ladder: https://ladder.fit/empress SIP: https://learn.saferinternetproject.com/?affcode=1349743_h_62dxyh
#fyp#thoughts#women in business#digital security#cybersecurity#neville goddard#manifesting#blogging#tech blog#30 Day ITSec Business Challenge#business
4 notes
·
View notes
Text
There's a new alternative to the awful KOSA legislation going through Congress. The new bill is S. 1291, called the Protecting Kids on Social Media Act. We need to stop this one. States absolutely will use this to target trans and queer people online. https://www.techdirt.com/2023/08/31/the-protecting-kids-on-social-media-act-is-a-terrible-alternative-to-kosa/
I have emailed my legislators using https://act.eff.org/action/stop-the-protecting-kids-on-social-media-act
And I have called them using https://www.usa.gov/elected-officials/ to find them.
28 notes
·
View notes
Text
Comprehensive IT Security Services: Why You Need a Trusted IT Security Company
In today’s rapidly evolving digital landscape, securing your business’s data and IT infrastructure is more important than ever. With cyber threats growing more sophisticated, partnering with a professional IT security services company is essential for protecting your business. This article explores the key services provided by an IT security company, why businesses need them, and how a reliable provider like Gronteq can safeguard your organization from cyber risks.

Comprehensive IT Security Services: Why You Need a Trusted IT Security Company
As businesses become more reliant on digital tools and systems, the threat of cyberattacks has grown significantly. Whether you’re a small startup or a large corporation, protecting your sensitive data and IT infrastructure is no longer optional—it’s a necessity. This is where a professional IT security services company comes in. Their role is to safeguard your business from cyber threats, protect your data, and ensure your systems are running smoothly and securely.
In this article, we will discuss the various IT security services offered by reputable providers, why businesses need these services, and how partnering with a trusted IT security company like Gronteq can help you maintain a secure and resilient digital environment.
1. Understanding the Importance of IT Security
The growing frequency and sophistication of cyber threats are major concerns for businesses worldwide. Hackers, cybercriminals, and malicious insiders are always on the lookout for vulnerabilities in your IT infrastructure. From phishing attacks and data breaches to ransomware and DDoS attacks, the risks are constantly evolving.
Without the right IT security services, businesses risk losing valuable data, experiencing system downtime, and suffering reputational damage. Moreover, data protection regulations, such as GDPR and HIPAA, require businesses to implement robust security measures to avoid penalties and fines.
This is where an experienced IT security company can help. By working with a trusted provider, businesses can implement proactive security strategies that prevent attacks before they occur, ensuring a safe, compliant, and resilient online environment.
2. Key IT Security Services Offered by Companies
The scope of IT security services provided by security companies varies, but some common services include:
a. Network Security
Network security involves implementing measures to protect your internal network from unauthorized access, attacks, and data breaches. This includes firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and secure VPNs. With strong network security, your business can defend against external and internal threats.
b. Data Protection and Encryption
Protecting sensitive data is critical to prevent unauthorized access or leaks. IT security agencies provide encryption services to ensure that data is stored and transmitted securely. By implementing data loss prevention (DLP) tools, businesses can safeguard intellectual property, customer information, and financial data from cybercriminals.
c. Vulnerability Management
Vulnerability management involves identifying and addressing weaknesses in your systems before they can be exploited. This includes regular security assessments, penetration testing, and patch management. A thorough vulnerability management program helps keep your business ahead of potential threats.
d. Endpoint Security
With more employees working remotely, endpoint security has become a top priority. This includes securing devices like laptops, smartphones, and tablets that access your company’s network. Endpoint security services protect these devices from malware, phishing attacks, and unauthorized access, ensuring the integrity of your entire IT infrastructure.
e. Incident Response and Disaster Recovery
In the event of a cyberattack or data breach, having a well-defined incident response plan is essential. IT security services companies offer incident response and disaster recovery services to help businesses quickly recover from cyberattacks. This includes identifying the source of the breach, mitigating damage, and restoring normal operations.
f. Managed Security Services
For businesses that lack an in-house security team, managed security services (MSS) are an excellent solution. These services provide 24/7 monitoring, threat intelligence, and proactive response to security incidents. MSS ensures continuous protection for your business without the need for an internal team.
3. Why Your Business Needs IT Security Services
The question remains: why is it so critical for your business to partner with a reliable IT security company? Here are the main reasons:
a. Proactive Threat Prevention
A trusted IT security services company works proactively to protect your business. By continuously monitoring your systems, implementing security protocols, and conducting regular security audits, a professional provider helps to prevent potential attacks before they happen.
b. Protecting Business Reputation
A cyberattack can lead to loss of trust from customers, partners, and stakeholders. With IT security services, your company can protect its reputation and avoid the costly consequences of a data breach.
c. Legal and Regulatory Compliance
Cybersecurity isn’t just about protecting your data—it’s also about complying with industry regulations. An IT security company helps ensure that your business complies with relevant laws like GDPR, HIPAA, and PCI-DSS, avoiding fines and penalties.
d. Cost Savings in the Long Run
While the upfront costs of IT security services may seem significant, they can actually save your business money in the long run. By preventing attacks, reducing downtime, and avoiding the cost of data breaches, investing in security is a smart financial decision.
e. Expertise and Knowledge
Cybersecurity is a complex field that requires specialized knowledge and expertise. A reputable IT security company brings in-depth understanding of the latest threats, tools, and strategies to ensure your business is always protected.
4. How Gronteq Can Help Protect Your Business
At Gronteq, we specialize in providing comprehensive IT security services to businesses of all sizes. Our team of cybersecurity professionals is dedicated to safeguarding your business from cyber threats, ensuring compliance with regulations, and helping you maintain a secure and resilient IT environment.
We offer customized IT security solutions, including network security, data protection, vulnerability management, endpoint security, and disaster recovery. With our proactive approach to cybersecurity and 24/7 monitoring, we ensure your business is always one step ahead of potential threats.
5. Contact Gronteq for Your IT Security Needs
If you’re ready to take your business’s security to the next level, Gronteq is here to help. Our IT security experts are ready to provide tailored solutions that meet your unique needs. Contact us today to learn more about how we can protect your business from cyber threats and ensure your IT systems are secure, compliant, and optimized for success.
Conclusion The digital landscape is constantly evolving, and so are the risks that come with it. Partnering with a professional IT security services company like Gronteq ensures your business is well-protected, compliant, and prepared for any challenges that arise. From proactive threat prevention to disaster recovery, our team provides end-to-end security solutions to keep your business safe.
Contact Gronteq today to learn how our IT security services can protect your organization and give you peace of mind knowing your business is secure.
#IT security#cybersecurity#IT services#data protection#network security#IT security company#IT consulting#digital security#cyber threats#business security
2 notes
·
View notes