#Enterprise IT Consulting Solutions
Explore tagged Tumblr posts
Text

Hit the bullseye with the right ERP software! 🎯
Magtec Business Solutions helps you choose the perfect ERP solution to take your business to new heights.
Contact us today for a demo!
#erp#magtec#magtecsolutions#business#solutions#uae#software#technology#growth#success#innovation#digitaltransformation#cloud#enterprise#resources#planning#implementation#consulting#support#customization#integration#automation#efficiency#productivity#cost#savings
2 notes
·
View notes
Text
KGT Applications offers tailored business solutions. We design custom tools to automate tax processes, streamline operations and enhance efficiency to ensure tax compliance and business growth. With a comprehensive suite of enterprise software, businesses can optimize their processes and reach their maximum potential. Contact KGT Applications today!
#tax services#sap consulting services#business automation#business solutions#process management#Enterprise software
3 notes
·
View notes
Text
This is the bullshit about starting work again, I come home and continue with rubbish like planning plot processes and prioritisation matrixes and production programs and the like, instead of, you know, writing.
#managing the production vs actually “being the producer” brain#its such a different way of thinking I haven't worked out my 'snap brain into that different kind of creative mode again'#The reason I can be satisfied at my job is that I approach all that stuff *as* creative exercises; I create the clarity that does not exist#People blab for 30mins about problems and I doodle on a whiteboard and then they slow down and realise I've drawn their solution map#I *could* have been a consulting business analyst for the requirements definition stuff but detest the software/technologies rigidity part#What I really need is some 15 minute major physical/mental/formic break between work and home to switch brain modes#I do have a 20min powerwalk in there but then I have to do the kid/house so the endorphin benefit towards creative enterprise wears off
3 notes
·
View notes
Text
Enterprise Mobility
At Enterprise Mobility, we understand that enterprise mobility is more than just adopting mobile devices Our Enterprise Mobility Solutions encompass a wide range of cutting-edge technologies, Unlock efficiency with top-notch enterprise mobility solutions. Elevate productivity and connectivity with our comprehensive range of enterprise mobility services. Transform your business with Enterprise Mobility.
#enterprise mobility#enterprise mobility management#emm#enterprise mobility management solution#enterprise mobility consulting#enterprise mobility solutions#enterprise mobility services#mobility#enterprise#mobile app deveopment#venusgeo
3 notes
·
View notes
Text
#Cloud Consulting Services#Cloud Strategy and Transformation#Digital Transformation Strategy#Cloud Migration Experts#Enterprise Cloud Adoption Services#Cloud-Native Application Development#Digital Transformation Consulting#Custom Web Development Company#Enterprise Content Management Solutions#Cloud-Native Development Services#Product Engineering Services#technology#digital transformation#successive.tech#successive digital#artificial intelligence#customer experience#techblog#customer experience consulting company#blog#customer experience transformation company
0 notes
Text
Bots Now Dominate the Web: Why This Growing Problem Demands Urgent Action

The digital world, once a bustling marketplace of human interaction, has undergone a silent, pervasive transformation. Data from 2024 and early 2025 reveals a startling reality: bots now dominate web traffic, accounting for over 50% of all internet activity. While some of these automated programs are "good" – diligently indexing content for search engines or enabling helpful chatbots – a significant and escalating proportion are "bad bots," mimicking human behavior for malicious purposes. This widespread bot dominance web traffic presents a serious and ever-growing problem for businesses, cybersecurity, and the overall integrity of the web. The sheer volume and sophistication of these malicious bots internet traffic are redefining the landscape of online security.
The rise of bot traffic on the internet is significantly fueled by rapid advancements in Artificial Intelligence (AI) and Large Language Models (LLMs). These technologies simplify the creation and scaling of sophisticated, evasive bots, allowing even less skilled malicious actors to launch high-volume attacks. As of early 2025, malicious bots account for a staggering 37% of all internet traffic, a substantial increase from previous years, signaling a deepening bot problem online.
The Unseen Majority: How Bots Came to Dominate the Web
For the first time in a decade, automated traffic has surpassed human activity. This shift is primarily attributed to the proliferation of AI and LLMs, which have democratized bot development, making it more accessible to a wider range of actors. These advancements enable bots to mimic human interaction with startling accuracy, often bypassing traditional security measures.
The sophistication of these bad bots internet traffic is constantly evolving. They employ techniques like IP rotation, mimicking legitimate browser fingerprints, and distributing attacks across vast networks of compromised devices (botnets). The goal is simple: evade detection by blending in with legitimate web traffic automation. This makes it increasingly difficult for organizations to differentiate between genuine human users and malicious automated scripts, amplifying the bot problem online.
The Multifaceted Problem: Impacts of Bot Dominance

The pervasive presence of malicious bots internet traffic creates a myriad of complex and costly issues across various aspects of the digital economy. Understanding the full scope of the impact of bots on business is crucial for developing effective defense strategies.
Financial Drain & Fraud
The direct financial implications of bot fraud are staggering. Malicious bots are instrumental in various fraudulent activities that directly hit a business's bottom line:
Credential Stuffing and Account Takeovers (ATOs): Bots automate login attempts using stolen username/password combinations from data breaches. Successful ATOs lead to financial theft, misuse of loyalty points, and damage to customer trust.
Carding and Gift Card Fraud: Bots test stolen credit card numbers against e-commerce sites or attempt to drain balances from stolen digital gift cards, leading to chargebacks and direct financial losses.
Ad Fraud and Click Fraud: Bots simulate clicks and impressions on online advertisements, depleting advertisers' budgets without generating genuine leads or conversions. This distorts analytics and wastes significant marketing spend.
Scalping and Inventory Hoarding: In industries with high-demand, limited-stock items (like concert tickets, sneakers, or popular gaming consoles), bots rapidly purchase inventory, only for it to be resold at inflated prices on secondary markets. This infuriates legitimate customers and damages brand reputation.
Cybersecurity Risks & Data Integrity
Cybersecurity bot attacks represent a fundamental threat to an organization's digital infrastructure and sensitive data. Bots are often the first line of attack in broader cyber campaigns:
Vulnerability Scanning and Exploitation: Bots automatically scan websites and APIs for known vulnerabilities (e.g., SQL injection, cross-site scripting), identifying weak points that can then be exploited for unauthorized access or data exfiltration.
Distributed Denial-of-Service (DDoS) Attacks: Botnets, vast networks of compromised devices controlled by attackers, flood target websites, servers, or networks with overwhelming volumes of traffic, rendering them inaccessible to legitimate users.
API Abuse: With the rise of API-driven applications, bots increasingly target APIs to scrape data, create fake accounts, exploit business logic, or launch sophisticated fraud schemes that bypass traditional web application firewalls.
Data Scraping: Competitors or malicious actors use bots to steal valuable data, including pricing information, product catalogs, customer reviews, and proprietary content, leading to competitive disadvantage and intellectual property theft.
Operational & Performance Disruptions
The sheer volume of web traffic automation from bots places immense strain on IT infrastructure:
Server Strain and Increased Costs: High bot traffic consumes valuable server resources, bandwidth, and computing power, leading to increased hosting expenses and the need for costly infrastructure upgrades.
Degraded Website Performance: Overwhelmed servers result in slower loading times, timeouts, and poor responsiveness for legitimate users, severely impacting user experience and conversion rates.
Skewed Analytics: Bot traffic contaminates website and application analytics, inflating metrics like page views, unique visitors, and clicks while distorting bounce rates and conversion rates. This leads to flawed business decisions based on inaccurate data.
Brand Reputation & Trust
Beyond the technical and financial impacts, bot dominance web traffic erodes trust and damages brand reputation:
Spam and Misinformation: Spam bots flood comment sections, forums, and social media platforms with unsolicited advertising, malicious links, or propaganda, harming a website's credibility and user experience.
Customer Frustration: When legitimate customers are unable to access services due to DDoS attacks, or when they can't purchase items due to bot-driven scalping, their frustration can quickly turn into negative reviews and a damaged brand image.
SEO Penalties: Google and other search engines penalize websites with low-quality or duplicate content, which can result from content scraping by bots, negatively impacting search engine rankings and organic traffic.
Industries Under Siege: Where Bot Threats are Most Acute

While the bot problem online affects nearly every sector, certain industries consistently face a higher proportion and more sophisticated online bot threats:
Financial Services: A primary target due to the sensitive nature of data and high-value transactions. They face relentless account takeover bots, credential stuffing, and fraud attempts.
Retail: Highly susceptible to bot fraud related to inventory scalping, gift card fraud, price scraping, and loyalty program abuse.
Travel: Experiences a significant percentage of bad bots internet traffic, used for competitive price scraping, account takeovers, and fraudulent bookings.
Gaming: Often sees the highest proportion of sophisticated bot traffic, including bots used for cheating, account compromise, and inventory manipulation within in-game economies.
Media and Entertainment: Targeted for content scraping, ad fraud, and credential stuffing on streaming platforms.
Fighting Back: Strategies for Bot Management and Mitigation

Combating bot dominance requires a proactive, multi-layered, and continuously evolving defense strategy. Relying on outdated methods is no longer sufficient against today's sophisticated malicious bots internet attacks.
Advanced Bot Management Solutions: The cornerstone of modern bot defense. These specialized platforms utilize a combination of behavioral analysis (distinguishing human-like patterns from automated ones), machine learning (adapting to new bot tactics), device fingerprinting, and real-time threat intelligence. They go beyond simple IP blocking or CAPTCHAs to detect and mitigate even the most evasive bots.
Robust API Security: Given that 44% of advanced bot traffic targeted APIs in 2024, securing these digital gateways is paramount. Implementing strong authentication mechanisms (like OAuth, API keys), strict access controls, and rate limiting on API endpoints can significantly reduce the attack surface for API security bots. Regular API penetration testing is also crucial.
Multi-Factor Authentication (MFA): Implementing MFA adds a critical layer of security beyond just passwords. Even if bots manage to acquire stolen credentials through credential stuffing, MFA can prevent unauthorized access by requiring a second verification step (e.g., a code from a mobile app), drastically reducing account takeover bots success rates.
Continuous Monitoring and Analytics: Businesses must actively monitor their web traffic automation for unusual patterns. This includes spikes in requests from a single IP, abnormally high failed login attempts, unusual user-agent strings, or suspicious conversion rates. Real-time dashboards and automated alerts are essential for early detection of online bot threats.
Regular Security Audits and Patching: Proactive vulnerability management is key. Regularly auditing web applications, APIs, and underlying infrastructure for security flaws, and promptly patching identified vulnerabilities, closes potential entry points for bots.
User-Agent and Proxy Analysis: Many simpler bots still rely on outdated browser user-agent strings or operate through known dubious proxy services. Implementing rules to block traffic from such indicators can filter out a significant portion of commodity bot attacks. Detecting traffic from residential proxies, which more advanced bots now use, requires more sophisticated analysis.
Rate Limiting and Throttling: While not a complete solution, judiciously applying rate limits on specific endpoints (e.g., login pages, search functions, API calls) can prevent brute-force attacks and resource exhaustion caused by excessive bot requests.
Conclusion: Securing the Human-Centric Web
The landscape of the internet has fundamentally shifted. Bots now dominate the web, and this poses a significant, evolving bot problem online for businesses, their customers, and the integrity of digital interactions. From sophisticated bot fraud schemes to debilitating cybersecurity bot attacks, the impact is wide-ranging and costly.
Ignoring this reality is no longer an option. As AI continues to empower bots to become even more evasive and intelligent, businesses must embrace comprehensive and adaptive bot management solutions. Investing in robust API security, implementing strong authentication, and continuously monitoring for unusual patterns are not merely best practices; they are essential for survival in the current digital climate.
The future of the web depends on our ability to effectively differentiate between humans and machines, safeguarding digital assets and ensuring a secure, reliable, and authentic online experience for everyone. By adopting proactive strategies, organizations can protect their revenue, reputation, and customer trust from the pervasive and growing threat of malicious web traffic automation. The time for urgent action is now.
#Cyber Security Services Company | Data Security Solutions#Top-rated Cyber Security Services Company Offering Advanced Protection#Threat Detection#Risk Assessment#Data Security Solutions For Businesses Worldwide.#Cybersecurity services company#Data security solutions#Managed cybersecurity services#Enterprise cyber protection#Data breach prevention services#Cyber threat protection#IT security solutions provider#Endpoint security services#Network security services#Cybersecurity consulting company
0 notes
Text
GetOnCRM’s Winning Formula at the 2025 Agentforce Hackathon
The focus at the 2025 Salesforce Agentforce Hackathon was on execution rather than just innovation. GetOnCRM’s Agentforce Hackathon solution stood out among the dozens of teams that built quickly and strategically because it not only delivered a brilliant idea but also a functional model that addressed actual internal workflow problems.
What was unique about GetOnCRM? It was clarity, not complexity.
Resolving the Issue No One Discusses
Slow internal support is a problem for the majority of enterprise teams. Ticket stall. Escalations are postponed. Valuable time slips away. GetOnCRM addressed the fundamental problem—internal service delays—and used intelligent Salesforce automation to resolve it rather than developing a new tracking tool.
Their remedy? A Slack-integrated support workflow created with Salesforce Flow Builder automation and connected through Salesforce Data Cloud integration. The agent could:
Quickly determine the urgency of the ticket
Pull background information from previous cases
Escalate to the appropriate channel in real time
You can accomplish this without ever leaving Slack.
This was not a theoretical demo—it was a functional prototype made for real enterprise support teams.
Integration in Real Time That Works
What made the solution even more impactful was its seamless connection to live enterprise data. With Salesforce Data Cloud, the agent worked off the latest information—not outdated snapshots—allowing it to make fast, accurate decisions without human intervention.
Thanks to agent memory and context awareness, the bot could deliver a personalized, intelligent support experience, reducing back-and-forth between staff.
The Tools That Powered the Win
GetOnCRM’s strategy was built on simplicity and real impact. These were the key ingredients:
Salesforce Agent Builder—the central control hub for the entire workflow
Slack-based Salesforce workflows—removing the need to juggle tools
Apex logic and Flow Builder—to automate smart, multi-step decisions
Cross-cloud Salesforce automation—linking operations, support, and collaboration platforms like Health Cloud, CPQ, and Revenue Cloud
Their approach resulted in a workflow that was not just smart but also scalable and enterprise-ready.
Built for Teams That Want to Move Faster
The goal wasn’t flashy tech—it was to remove friction from business processes. The hackathon confirmed what GetOnCRM’s Salesforce automation consulting services already strive for: real transformation using the right tools, fast.
This project wasn’t just a hackathon submission—it became a repeatable automation framework for intelligent support and operations.
✅ Want to learn how GetOnCRM uses Salesforce Agentforce to transform enterprise workflows?
Read the full case study on our Agentforce Hackathon success.
#Salesforce Agentforce#Agentforce Hackathon 2025#GetOnCRM Solutions#Salesforce Flow Builder#Slack based workflows#Salesforce Data Cloud#business process automation#enterprise automation tools#Salesforce automation consulting#AI powered workflows#internal support automation#DevOps automation Salesforce#Salesforce innovation#workflow optimization
0 notes
Text
Choosing the Right Crypto Wallet for Your Business – Custodial vs. Non-Custodial
Choosing the right crypto wallet is crucial for safeguarding digital assets. In this guide by Theta Technolabs, we explore the key differences between custodial and non-custodial wallets, helping businesses make informed decisions. Learn how wallet types impact control, security, and compliance in today’s fast-moving blockchain landscape.
#crypto wallet for business#custodial crypto wallet#business crypto solutions#blockchain wallet types#crypto wallet development#enterprise blockchain security#digital asset management#decentralized wallets#crypto security for startups#blockchain consulting company
0 notes
Text
NexaPent Technologies: Powering Growth with Smart IT Solutions, AI Hiring & Digital Innovation
In today's fast-paced digital world, it's clear that organizations need more than software; they're looking for IT solutions that are smart, flexible, and geared toward growth.
NexaPent Technologies recognizes this need and is committed to delivering intelligent IT services and solutions faster than its competitors.
About NexaPent?
NexaPent, located in Bengaluru, India, is an emerging leader in IT services and solutions, capable of leveraging talent and tools to mix AI recruitment, digital marketing, custom software development, and testing and quality assurance together. NexaPent offers organizations of all sizes a way to fit together an innovative digital experience for their customers that can help them innovate faster, hire smarter, and every digital experience is delivered at scale and at again posed cost.
NexaPent Technologies is a full-service IT consulting firm that solves real-world business challenges using technology. Their team of developers, QA engineers and testers, recruiters, and marketers works as an extension of your team to deliver on-time projects along with the pre-articulated budgets. Perhaps one of the things that differentiates NexaPent is that they are AI-first in their recruitment approach and can deliver a blended digital strategy with technology execution of solutions, not just services, they deliver outcomes.
Core Services at NexaPent
IT Recruitment (AI-Driven)
Finding talent in technology is hard. NexaPent simplifies this with AI-enabled IT recruitment services to identify, screen, and hire technology talent quickly. Here is what they offer:
Automated candidate sourcing
AI screening & filtering
No-show management (backup hiring)
Smooth onboarding support
High offer-to-join ratio
From developers to data scientists, NexaPent can make sure you hire the right talent, at the right time, without the stresses of technology recruitment.
Explore more: IT Recruitment Services
Digital Marketing Services
NexaPent's digital team produces high-impact, data-driven marketing campaigns that attract traffic, generate leads, and increase brand awareness. Their services include:
Search Engine Optimization (SEO)
Pay-per-click ads (PPC)
Social media marketing
Content creation & blogging
Email campaigns
Online reputation management
Generative Engine Optimization (GEO)
NexaPent develops strategies tailored to your business objectives to rank on Google and/or develop a loyal online community.
Custom Software Development
NexaPent develops web, mobile, and enterprise applications in the latest technology stacks. Their solutions are secure, scalable, and easy to use. Your digital ideas, whether it is internal business applications or client-facing applications, are brought to life.
Software Testing & QA
Quality is critical, and that is why NexaPent provides full QA services for applications, including:
Manual and automation testing
Performance and compatibility testing
Functional testing
Embedded and IoT testing
They ensure your product operates perfectly across all devices, platforms, and conditions before reaching the end customer.
Who Needs NexaPent?
NexaPent is a great fit for:
Startups launching tech products
Enterprises scaling operations
Companies need faster hiring
Brands looking to dominate search engines
Businesses upgrading their software infrastructure
Whether you need a marketing strategy, a new mobile app, or a team of developers, NexaPent provides end-to-end IT services you can trust.
Conclusion
In a hyper-competitive digital environment, the partners you choose determine your success. By partnering with NexaPent Technologies, you gain what is more than a service provider; you gain a growth partner.
If you seek to grow your business with smart technology, AI-enhanced hiring, and performance marketing capabilities, NexaPent is prepared for you to take the next step.
👉 Visit: https://www.nexapent.com 📞 Get in touch and future-proof your business today.
#NexaPent#NexaPent Technologies#IT services#software development#digital marketing#QA testing#AI-powered recruitment#technology consulting#IT solutions provider#Indian IT company#enterprise tech services#full-service IT firm#tech company Bangalore
0 notes
Text
Expert Consulting & System Integration Services for Seamless Digital Synergy

Transform challenges into opportunities with Consulting & System Integration Services from Writer Information. Whether you're modernizing legacy systems, deploying enterprise platforms, or aligning IT with business goals, Writer’s experts deliver customized solutions that ensure agility, compatibility, and scalability. From strategy to execution, every step is optimized to reduce risk, enhance ROI, and accelerate transformation. With a deep understanding of complex tech environments, Writer bridges the gap between vision and reality—helping your enterprise achieve true digital harmony.
#consulting & system integration services#cloud computing#customer service#enterprise content management#skill enhancement services#e waste management#services#solution
0 notes
Text
AWS and Open Source Headless CMS for Scalable Content | PenNep IT Solutions
#pennep india#pennep#Headless CMS#Open source headless CMS#Cloud computing services#Enterprise software development#Custom software development#IT consulting services#PenNep IT solutions#Pennep Jalandhar
0 notes
Text
Why Splunk Is the Go-To Platform for Enterprise Security and Observability
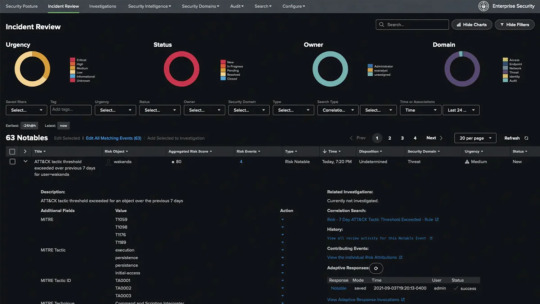
In today’s digital-first world, organizations generate and rely on vast volumes of machine data to run their operations, serve customers, and protect digital assets. As cyber threats grow in complexity and IT environments become more fragmented with cloud, hybrid, and multi-cloud setups, enterprises are under pressure to maintain visibility, ensure compliance, and respond to incidents in real time. Enter Splunk: the platform leading enterprises trust for security, observability, and data-driven decision-making.
Splunk has become synonymous with real-time analytics and intelligent monitoring. Its ability to ingest, index, and correlate data from virtually any source makes it indispensable for enterprises seeking to gain end-to-end visibility across their digital infrastructure. But what exactly makes Splunk service the go-to platform for enterprise security and observability? Let’s break it down.
1. Unified Data Platform for Security and IT Operations
Splunk provides a unified platform that bridges the gap between IT security, and business operations. Unlike siloed tools that provide fragmented views, Splunk consolidates data from across your network, applications, endpoints, and cloud services to deliver a single source of truth.
Whether you’re monitoring for performance issues, detecting security breaches, or ensuring compliance, Splunk enables stakeholders to work from a common, real-time data set. This holistic approach empowers faster, more accurate decisions and fosters collaboration across departments.
2. Powerful Security Information and Event Management (SIEM) Capabilities
One of the strongest use cases for Splunk is in enterprise security. Splunk Enterprise Security (ES) acts as a powerful SIEM platform, enabling security teams to detect, investigate, and respond to threats efficiently. It offers advanced analytics, prebuilt dashboards, threat intelligence integration, and real-time alerting.
With features like risk-based alerting, behavioral analytics, and threat detection rules, Splunk helps security teams cut through the noise and focus on high-priority incidents. It empowers analysts to conduct rapid incident response and forensic investigations using historical data.
3. Unmatched Observability Tools for Modern Applications
Observability is more than just monitoring—it’s about understanding system behavior across distributed environments. Splunk Observability Cloud offers a full-stack observability solution that includes infrastructure monitoring, application performance monitoring (APM), log analysis, and synthetic transaction testing.
By leveraging OpenTelemetry and AI-driven insights, Splunk provides real-time visibility into system health, user experiences, and performance bottlenecks. This enables DevOps and SRE teams to troubleshoot faster, optimize application performance, and deliver consistent uptime.
4. Scalability for Enterprise Workloads
Enterprise environments are complex, and the volume of machine data they produce can be staggering. Splunk is designed to scale with your business, whether you're analyzing gigabytes or petabytes of data daily. Its distributed architecture supports horizontal scaling and high availability, ensuring consistent performance even under heavy loads.
This scalability is critical for large enterprises that require long-term retention, high-speed analytics, and support for thousands of users accessing data concurrently.
5. Advanced Analytics and Machine Learning
Splunk's analytics capabilities go beyond simple search and dashboards. With built-in machine learning (ML) and support for custom models, Splunk enables predictive analytics, anomaly detection, and behavior profiling. Security and IT teams can use ML to identify suspicious patterns, forecast system failures, or automate threat detection.
The Splunk Machine Learning Toolkit (MLTK) empowers users to apply, train, and tune models using their existing data—no data science degree is required. This intelligent layer of automation enhances situational awareness and drives proactive responses.
6. Robust Ecosystem and Integrations
Splunk integrates seamlessly with a wide range of tools, platforms, and services, including AWS, Microsoft Azure, Google Cloud, Kubernetes, ServiceNow, Palo Alto Networks, and more. These integrations extend Splunk’s capabilities and ensure it fits naturally into your existing technology stack.
The Splunkbase app marketplace features thousands of apps and add-ons for specialized data sources, dashboards, and utilities—making it easier for teams to customize the platform to suit their needs.
7. Enhanced Compliance and Audit Readiness
For industries like finance, healthcare, and government, regulatory compliance is a top priority. Splunk simplifies compliance management by offering prebuilt dashboards and reports aligned with standards like HIPAA, PCI DSS, GDPR, and ISO 27001.
Automated data collection, alerting, and audit trails make it easier to demonstrate compliance and pass audits with confidence. Splunk also provides role-based access controls and data masking to protect sensitive information.
8. Flexible Deployment Options: On-Prem, Cloud, or Hybrid
Not all enterprises are at the same stage of cloud adoption. Splunk’s flexible deployment options allow organizations to deploy the platform on-premises, in the cloud, or a hybrid environment.
Splunk Cloud Platform offers the same functionality as on-prem with the added benefits of scalability, automatic updates, and reduced infrastructure management. It’s ideal for businesses that want to accelerate time to value and reduce operational overhead.
9. Real-Time Dashboards and Visualizations
Splunk’s intuitive dashboards and data visualizations help users transform raw machine data into actionable insights. From real-time alerts on security threats to performance metrics for executive reports, Splunk offers customizable dashboards that can be tailored to user roles and use cases.
Interactive charts, graphs, and maps help bring data stories to life, making it easier for decision-makers to act on insights without technical barriers.
Final Thoughts: Why Splunk Stands Out
In a world where data is both a powerful asset and a potential liability, having the right tools to manage, secure, and understand your data is critical. Splunk delivers on all fronts—offering real-time analytics, enterprise-grade security, and unparalleled observability.
By unifying IT operations, DevOps, and security teams around a single data platform, Splunk breaks down silos, accelerates response times, and drives digital resilience. Its flexibility, intelligence, and scalability make it the ideal choice for enterprises navigating the complexities of modern IT environments.
If your organization is ready to move beyond reactive monitoring and embrace intelligent, proactive operations, Splunk is not just an option—it’s the answer.
#splunk services#microsoft azure sentinel#Splunk solutions#splunk enterprise#splunk security#Splunk consultant#microsoft sentinel#SIEM solutions#Sentinel
0 notes
Text
#Cloud Consulting Services#Cloud Strategy and Transformation#Digital Transformation Strategy#Cloud Migration Experts#Enterprise Cloud Adoption Services#Cloud-Native Application Development#Digital Transformation Consulting#Custom Web Development Company#Enterprise Content Management Solutions#Cloud-Native Development Services#Product Engineering Services#technology#digital transformation#successive.tech#successive digital#artificial intelligence#customer experience#techblog#customer experience consulting company#blog
0 notes
Text

Mitigate downtime and disruptions with a CX management platform
Learn how a CX management platform can enhance operational efficiency, reduce service interruptions, and ensure a smooth, uninterrupted customer experience across all channels.
There’s nothing like a bit of system downtime to throw a wrench into your customer experience. One minute, everything’s running smoothly—then boom, misconfigured settings or unnoticed changes bring operations to a grinding halt. It doesn’t take much to interrupt the flow, but the cost can be steep.
Customers don’t tend to stick around when calls drop, queues build up, or agents are left fumbling with broken processes. These moments don’t just affect individual interactions—they add up quickly, damaging reputation and driving up support costs. And the worst part? Many of these issues are totally avoidable.
That’s where the right tech steps in. When you’ve got multiple platforms, vendors, and configurations in play, keeping things stable can feel like juggling with one hand tied behind your back. But a smart CX management platform can flip the script by spotting issues before they spiral, helping your team stay ahead of the chaos.
There’s nothing like a bit of system downtime to throw a wrench into your customer experience. One minute, everything’s running smoothly—then boom, misconfigured settings or unnoticed changes bring operations to a grinding halt. It doesn’t take much to interrupt the flow, but the cost can be steep.
Customers don’t tend to stick around when calls drop, queues build up, or agents are left fumbling with broken processes. These moments don’t just affect individual interactions—they add up quickly, damaging reputation and driving up support costs. And the worst part? Many of these issues are totally avoidable.
That’s where the right tech steps in. When you’ve got multiple platforms, vendors, and configurations in play, keeping things stable can feel like juggling with one hand tied behind your back. But a smart CX management platform can flip the script by spotting issues before they spiral, helping your team stay ahead of the chaos.
Why choose Blackchair for seamless CX management and CCaaS configuration?
At Blackchair, we specialize in optimizing CX management platforms to enhance operational resilience and minimize downtime. Our team works with you to ensure that your CCaaS configuration is seamless, secure, and efficient. We proactively identify risks and inefficiencies, offering actionable insights to improve performance and reduce disruptions.
Let us handle the tech details while you focus on delivering exceptional customer experiences and driving business success.
#CX optimization#CCaaS migration#CCaaS configuration#DORA compliance#telecommunications solutions#Workforce Management#Enterprise telephony management#System security#Knowledge and transfer solution guides#CX solutions#information technology company#Business consultant#Information Technology
0 notes
Text
Leading the Future: How Digital Transformation Consulting Services Empower Business Innovation

In today’s fast-changing digital economy, businesses can’t afford to stand still. Digital Transformation Consulting Services are no longer optional—they’re mission-critical. These services empower organizations to modernize operations, integrate emerging technologies like AI, IoT, and cloud, and build scalable systems that support future growth.
A trusted consulting partner helps identify technology gaps, realign legacy systems, and implement tailored strategies for automation, agility, and customer-centricity. Whether you're a startup or a large enterprise, digital transformation consultants guide you through disruption—turning complexity into competitive advantage.
Ready to innovate and lead through change? Digital transformation isn’t just about technology—it’s about vision.
#Digital Transformation Consulting Services#enterprise automation#enterprise mobility solutions#custom application development company#digital transformation in banking and finance
0 notes
Text
#artificial intelligence services#machine learning solutions#AI development company#machine learning development#AI services India#AI consulting services#ML model development#custom AI solutions#deep learning services#natural language processing#computer vision solutions#AI integration services#AI for business#enterprise AI solutions#machine learning consulting#predictive analytics#AI software development#intelligent automation
0 notes