#IP Data Security
Explore tagged Tumblr posts
Text

How to Protect Intellectual Property (IP) Data from Modern Bad Actors?
Safeguard Intellectual Property IP Data from Insider and outsider bad actors Kirit shares 6 steps roadmap for the protection of IP data.
#Best IP Data Security Practices#Encrypting Intellectual Property Data#Insider Threat to IP Data#Intellectual Property (IP) Data#Intellectual Property Data#IP Data Protection#IP Data Protection Strategy#IP Data Risk Assessment#IP Data Security#Outsider Threat to IP Data#Safeguard IP (Intellectual Property) Data
0 notes
Text

In this article, we’ll explore what GDPR is, why it’s essential for businesses to comply, and how AI can help with data privacy protection and GDPR compliance. Learn More...
#cloud technology#ai data privacy#ip phones#unified communications#hotel hospitality#VoIP#ip telephony#hotel phone system#voip solutions#GDPR#Protection#Data Security#EU Regulation#Technology News#phonesuite pbx#hotel phone installation#technology#hotel pbx
2 notes
·
View notes
Text

Security Management Tools | ATSNW Enhance your organization's safety with ATSNW's advanced Security Management Tools. Streamline risk assessment, incident reporting, and compliance tracking. Discover how our solutions can protect your assets today!
#Assured Technology Solutions#Data Backup Portland#Cloud Backup Portland#Assured Consulting Solutions#IT Internet Protocols Tech Geek Talk#Cybersecurity Risk Assessments Portland#windows 10 mobile os#Portland Cybersecurity Services#IT Application Protocols Tech Geek Talk#Voice over IP services#Technology Solutions#Business referral program#Managed IT Services for Portland#Cybersecurity Services#Security Management Tools#Microsoft License Support#Portland Managed IT Services#Microsoft Licensing Solutions#Callback Phishing Attack
0 notes
Text
Hate it when I'm asked about something then being completely ignored bc what I'm saying doesn't line up with the person's paranoia
#being asked bout computer shit(well more bout networks/wifi/data security)#and Ip addresses are brought up and its like#1. IP addresses are shared between a lot of ppl and without any other knowledge you are very unlikely ti be cucked through it#and 2. unless you pissed off the correct person or ppl then i dont think you need to worry bout being cucked over#(doesn't even matter bc ur house is LITERALLY LABELED on google maps already and ppl can just search ur name to find it)#then fucking ZIP BOMBING over the network got brought up and its like:#you stupid fuck unless you are fucking idiotic about what you open and download etc etc you dont have to worry bout that#unless there's a virus out there that can just automatically infect a device with no input from anybody (ie sender/reciever)-#-and can magically float within a specific network area#i think you will be fine#i dont claim to know everything bout this shit but its shit ya pick up doing certain things
1 note
·
View note
Text
How to Provide Secure Proxies for Your Brand with Proxy IPs
In order to help organizations effectively respond to the increasing online threats and enhance brand protection through Proxy IP services, this article will take an in-depth look at the Secure Proxies challenges and solutions for brands in the Porfiles environment, in particular how to utilize Proxy IPs to provide strong protection for your brand. We will help you understand how to choose the right type of Proxy IP to ensure your brand's reputation and Secure Proxies from a practical application perspective.
The Challenge of Brand Protection on the Internet
With the popularization of the Internet, companies are increasingly relying on online platforms for their interactions with consumers. However, the openness and complexity of the Porfiles also expose brands to various security threats. A brand's digital assets, especially customer-related personal data, intellectual property and corporate information, are easy targets for hackers, fraudsters and competitors. Therefore, brand protection is not just about preventing data leakage, but also about ensuring that a brand's reputation and market position are not jeopardized.

Key risks to brand security:
Data leakage and privacy protection: If customer data collected by an organization is stolen by hackers, it will seriously affect the credibility of the company and may lead to lawsuits.
Intellectual Property Theft: A brand's trademarks, logos and even product designs may be maliciously copied or stolen, affecting market share and consumer trust.
Brand Impersonation and Cyber Fraud: Hackers or fraudsters may impersonate a company's brand for fraudulent activities, further damaging the brand's image.
Social media and website security: Once a brand's social media accounts and official website are hacked, it may lead to information leakage, data tampering or brand image damage.
In the face of these threats, Proxy IP becomes an important tool for Secure Proxies for brands. Proxies not only help organizations hide their real IPs, but also improve data protection by decentralizing traffic and avoiding blocking.
How to Protect Your Brand with Proxies IPs
A Proxies IP is a server that acts as an intermediary through which devices accessing the Internet are able to hide their real IP addresses. Proxy IPs allow organizations to access content from different regions, monitor market Rotating, and even avoid being blocked when doing social media monitoring. The use of Proxy IPs brings multiple aspects of Secure Proxies to brands, especially in the following areas:

Avoiding IP Blocking & Abuse Detectingonline branding activities, such as market research, competitive analysis, price monitoring and other tasks, often requires access to a large number of websites and platforms. However, frequent requests can lead to IP blocking or blacklisting. Using Proxies, especially those that support IP rotation, can effectively prevent IP blocking and ensure uninterrupted corporate activities.
Enhance Data Collection and MonitoringEfficiencyBy using Proxies IPs in different geographies, organizations are able to bypass geographic limitations and gain access to information from different markets. Whether it's monitoring competitors' marketing campaigns or analyzing user feedback across the globe, Proxies IP can provide effective data collection support.
Protecting businesses' online activities from being trackedUsing highly anonymized Proxies IP can effectively prevent brand activities from being tracked and reduce the risk of brand impersonation. For example, when conducting brand monitoring, Proxies can help hide the real location and activities of an organization and prevent malicious competitors from stealing brand logos.
Types of Proxies and their Scenarios
Different types of Proxies have different features and advantages, and choosing the right Proxies can help organizations perform better brand protection tasks. Below are several common Proxies IP types and their application scenarios:
1. Data center Proxies IPs
Data Center Proxies IPs are IP addresses provided by dedicated data centers; such IPs are not associated with a specific ISP or physical location. Data center Proxies have high connection speeds and anonymity, making them suitable for large-scale, short-term tasks such as crawler crawling and market surveillance. However, since data center IPs are not owned by the average home or business user, they are easily identified and blocked by websites, making them suitable for scenarios that require fast, large-scale operations.
2. Residential Proxies IPs
Residential Proxies IPs are assigned by Internet Service Providers (ISPs) to regular home users. These IP addresses are often more difficult to recognize because they look like requests from regular home users. Residential IPs are ideally suited for long lead time tasks for brand protection, such as monitoring brand reputation in multiple countries and regions, detection of counterfeit brands, etc. Residential Proxies IPs not only avoid blocking, but also enhance the legitimacy of corporate activities and avoid being perceived as crawler or bot behavior.
3. Rotation of Proxies IPs
Rotating Proxies IP has the ability to automatically change IP addresses with each request or connection, avoiding flagging or blocking when performing long-term tasks. This is especially useful for brands that need to interact with websites frequently and require Proxies IPs to remain anonymous. For example, brands can use rotating Proxies IPs to regularly check competitors' pricing strategies, promotions, etc. to ensure that they are not blocked by the platform due to frequent visits.
How to choose the most suitable Proxies IP type
Choosing the right type of Proxies IP is key to ensuring the effectiveness of your brand protection efforts. Here are a few important factors to consider when choosing Proxies IP:
Mission TypeIf your brand protection mission requires large-scale data crawling in a short period of time, data center Proxies may be a good choice. And if long-term monitoring and prevention of brand impersonation is required, Residential Proxies IPs would be more appropriate.
Security and AnonymityIf your goal is to protect your organization's online activities from being tracked or compromised, the exclusivity and increased security provided by Private Proxies IP is definitely the best choice.
RegionalRequirementsIf your brand needs to monitor competitors or analyze market trends globally, choosing Proxies with Residential Proxies that support multiple regions or Proxies that support IP rotation would be the most appropriate.
Budget and Performance BalanceDifferent types of Proxies IPs vary in price and performance, and organizations need to balance this with their budget and actual needs. For example, Data Center Proxies, while less costly, may face more risks of blocking, while Residential Proxies, while more expensive, offer greater legitimacy and stability.
With the proliferation of the Internet, brands are facing unprecedented challenges to their reputation and security. From trademark theft to counterfeit products to false brand impersonation, brands regularly encounter a variety of threats in the online Porfiles. Against this backdrop, Proxy IP has become an important tool for organizations to protect their brands and help them perform monitoring and data collection tasks Secure Proxy IP in a secure and efficient manner.
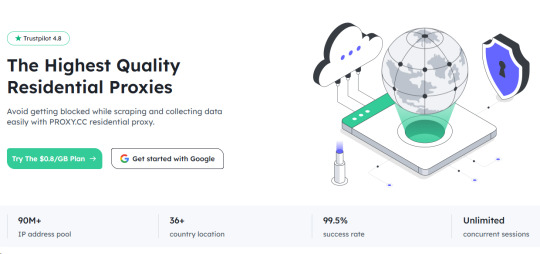
In the practical application of brand protection, choosing the right Proxies IP service is crucial. Here we recommend PROXY CC Proxy Proxies. PROXY CC provides the world's leading Proxy Proxies covering Rotating Residential Proxies, Static Residential Proxies and Unlimited Traffic Proxies, adapting to the needs of different enterprises. Our service not only covers 195 countries and regions, but also has more than 90 million active IP addresses, ensuring that you can efficiently and securely fulfill your brand protection tasks worldwide.

Rotating Residential IPs : Suitable for tasks with frequent IP changes, effectively avoiding IP tagging or blocking and ensuring uninterrupted data collection.
Static Residential IP : Provides support for tasks that require a stable IP, particularly suitable for long-term brand monitoring and market analysis.
Unlimited Residential Proxies : Designed for large-scale data collection, market surveillance and brand protection, it guarantees high-speed, stable connections.
By choosing the right Proxies IP service from PROXY.CC, you can better monitor your market, protect your brand and collect data. Rotating Residential IPs, Static Residential IPs or Unlimited Residential Proxies, depending on your needs, will help you effectively respond to online threats and ensure the safety and reputation of your brand.
Click on the link to try it now!
Conclusion
In the modern Porfiles, brand protection has become a core task in business operations. Proxies provide an efficient solution for brands to help organizations circumvent cyber attacks, protect data privacy, monitor brand reputation and prevent intellectual property theft. By choosing the right type of Proxies, organizations can effectively enhance brand security and ensure the long-term stable development of their business.
When choosing a Proxies IP, organizations should make an informed decision based on their needs, taking into account the type, features and cost of the Proxies IP. Whether it is Data Center Proxies, Residential Proxies or Private Proxies, each type of Proxies IP has its own unique advantages, and enterprises can choose the most suitable solution according to the actual situation.
0 notes
Text
How to Tell the Chat GPT: Privacy Please!
To opt out of using your data to train Chat GPT: Go to Settings Click on Data Controls Click on “Improve the model for everyone” and set it to off. ALTERNATIVELY: You can go to this website, and click on the button in the upper right that says “Make a Privacy Request” Note that Enterprise ChatGPT has privacy enabled by default. “You can access the privacy portal for ChatGPT services by…

View On WordPress
0 notes
Text

I've seen a number of people worried and concerned about this language on Ao3s current "agree to these terms of service" page. The short version is:
Don't worry. This isn't anything bad. Checking that box just means you forgive them for being US American.
Long version: This text makes perfect sense if you're familiar with the issues around GDPR and in particular the uncertainty about Privacy Shield and SCCs after Schrems II. But I suspect most people aren't, so let's get into it, with the caveat that this is a Eurocentric (and in particular EU centric) view of this.
The basic outline is that Europeans in the EU have a right to privacy under the EU's General Data Protection Regulation (GDPR), an EU directive (let's simplify things and call it an EU law) that regulates how various entities, including companies and the government, may acquire, store and process data about you.
The list of what counts as data about you is enormous. It includes things like your name and birthday, but also your email address, your computers IP address, user names, whatever. If an advertiser could want it, it's on the list.
The general rule is that they can't, unless you give explicit permission, or it's for one of a number of enumerated reasons (not all of which are as clear as would be desirable, but that's another topic). You have a right to request a copy of the data, you have a right to force them to delete their data and so on. It's not quite on the level of constitutional rights, but it is a pretty big deal.
In contrast, the US, home of most of the world's internet companies, has no such right at a federal level. If someone has your data, it is fundamentally theirs. American police, FBI, CIA and so on also have far more rights to request your data than the ones in Europe.
So how can an American website provide services to persons in the EU? Well… Honestly, there's an argument to be made that they can't.
US websites can promise in their terms and conditions that they will keep your data as safe as a European site would. In fact, they have to, unless they start specifically excluding Europeans. The EU even provides Standard Contract Clauses (SCCs) that they can use for this.
However, e.g. Facebook's T&Cs can't bind the US government. Facebook can't promise that it'll keep your data as secure as it is in the EU even if they wanted to (which they absolutely don't), because the US government can get to it easily, and EU citizens can't even sue the US government over it.
Despite the importance that US companies have in Europe, this is not a theoretical concern at all. There have been two successive international agreements between the US and the EU about this, and both were struck down by the EU court as being in violation of EU law, in the Schrems I and Schrems II decisions (named after Max Schrems, an Austrian privacy activist who sued in both cases).
A third international agreement is currently being prepared, and in the meantime the previous agreement (known as "Privacy Shield") remains tentatively in place. The problem is that the US government does not want to offer EU citizens equivalent protection as they have under EU law; they don't even want to offer US citizens these protections. They just love spying on foreigners too much. The previous agreements tried to hide that under flowery language, but couldn't actually solve it. It's unclear and in my opinion unlikely that they'll manage to get a version that survives judicial review this time. Max Schrems is waiting.
So what is a site like Ao3 to do? They're arguably not part of the problem, Max Schrems keeps suing Meta, not the OTW, but they are subject to the rules because they process stuff like your email address.
Their solution is this checkbox. You agree that they can process your data even though they're in the US, and they can't guarantee you that the US government won't spy on you in ways that would be illegal for the government of e.g. Belgium. Is that legal under EU law? …probably as legal as fan fiction in general, I suppose, which is to say let's hope nobody sues to try and find out.
But what's important is that nothing changed, just the language. Ao3 has always stored your user name and email address on servers in the US, subject to whatever the FBI, CIA, NSA and FRA may want to do it. They're just making it more clear now.
10K notes
·
View notes
Text
The law enforcement arm of the U.S. Postal Service has quietly begun cooperating with federal immigration officials to locate people suspected of being in the country illegally, according to two people familiar with the matter and documents obtained by The Washington Post — dramatically broadening the scope of the Trump administration’s government-wide mass deportation campaign.
The U.S. Postal Inspection Service, a little-known police and investigative force for the mail agency, recently joined a Department of Homeland Security task force geared toward finding, detaining and deporting undocumented immigrants, said the people, who spoke on the condition of anonymity for fear of professional reprisals.
Immigration officials are seeking photographs of the outside of envelopes and packages — an Inspection Service program known as “mail covers” — and access to the postal investigation agency’s broad surveillance systems, including Postal Service online account data, package- and mail-tracking information, credit card data and financial material and IP addresses, the people said.
The postal collaboration is a significant escalation in the Trump administration’s immigration crackdown. Homeland Security officials have previously partnered with tax, housing and public health authorities. But the involvement of the Postal Inspection Service, the nation’s oldest law enforcement agency, means efforts to pursue undocumented immigrants have expanded into one of the most mundane government activities: delivering the mail.
289 notes
·
View notes
Text
Holy CRAP the UN Cybercrime Treaty is a nightmare

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If there's one thing I learned from all my years as an NGO delegate to UN specialized agencies, it's that UN treaties are dangerous, liable to capture by unholy alliances of authoritarian states and rapacious global capitalists.
Most of my UN work was on copyright and "paracopyright," and my track record was 2:0; I helped kill a terrible treaty (the WIPO Broadcast Treaty) and helped pass a great one (the Marrakesh Treaty on the rights of people with disabilities to access copyrighted works):
https://www.wipo.int/treaties/en/ip/marrakesh/
It's been many years since I had to shave and stuff myself into a suit and tie and go to Geneva, and I don't miss it – and thankfully, I have colleagues who do that work, better than I ever did. Yesterday, I heard from one such EFF colleague, Katitza Rodriguez, about the Cybercrime Treaty, which is about to pass, and which is, to put it mildly, terrifying:
https://www.eff.org/deeplinks/2024/07/un-cybercrime-draft-convention-dangerously-expands-state-surveillance-powers
Look, cybercrime is a real thing, from pig butchering to ransomware, and there's real, global harms that can be attributed to it. Cybercrime is transnational, making it hard for cops in any one jurisdiction to handle it. So there's a reason to think about formal international standards for fighting cybercrime.
But that's not what's in the Cybercrime Treaty.
Here's a quick sketch of the significant defects in the Cybercrime Treaty.
The treaty has an extremely loose definition of cybercrime, and that looseness is deliberate. In authoritarian states like China and Russia (whose delegations are the driving force behind this treaty), "cybercrime" has come to mean "anything the government disfavors, if you do it with a computer." "Cybercrime" can mean online criticism of the government, or professions of religious belief, or material supporting LGBTQ rights.
Nations that sign up to the Cybercrime Treaty will be obliged to help other nations fight "cybercrime" – however those nations define it. They'll be required to provide surveillance data – for example, by forcing online services within their borders to cough up their users' private data, or even to pressure employees to install back-doors in their systems for ongoing monitoring.
These obligations to aid in surveillance are mandatory, but much of the Cybercrime Treaty is optional. What's optional? The human rights safeguards. Member states "should" or "may" create standards for legality, necessity, proportionality, non-discrimination, and legitimate purpose. But even if they do, the treaty can oblige them to assist in surveillance orders that originate with other states that decided not to create these standards.
When that happens, the citizens of the affected states may never find out about it. There are eight articles in the treaty that establish obligations for indefinite secrecy regarding surveillance undertaken on behalf of other signatories. That means that your government may be asked to spy on you and the people you love, they may order employees of tech companies to backdoor your account and devices, and that fact will remain secret forever. Forget challenging these sneak-and-peek orders in court – you won't even know about them:
https://www.eff.org/deeplinks/2024/06/un-cybercrime-draft-convention-blank-check-unchecked-surveillance-abuses
Now here's the kicker: while this treaty creates broad powers to fight things governments dislike, simply by branding them "cybercrime," it actually undermines the fight against cybercrime itself. Most cybercrime involves exploiting security defects in devices and services – think of ransomware attacks – and the Cybercrime Treaty endangers the security researchers who point out these defects, creating grave criminal liability for the people we rely on to warn us when the tech vendors we rely upon have put us at risk.
This is the granddaddy of tech free speech fights. Since the paper tape days, researchers who discovered defects in critical systems have been intimidated, threatened, sued and even imprisoned for blowing the whistle. Tech giants insist that they should have a veto over who can publish true facts about the defects in their products, and dress up this demand as concern over security. "If you tell bad guys about the mistakes we made, they will exploit those bugs and harm our users. You should tell us about those bugs, sure, but only we can decide when it's the right time for our users and customers to find out about them."
When it comes to warnings about the defects in their own products, corporations have an irreconcilable conflict of interest. Time and again, we've seen corporations rationalize their way into suppressing or ignoring bug reports. Sometimes, they simply delay the warning until they've concluded a merger or secured a board vote on executive compensation.
Sometimes, they decide that a bug is really a feature – like when Facebook decided not to do anything about the fact that anyone could enumerate the full membership of any Facebook group (including, for example, members of a support group for people with cancer). This group enumeration bug was actually a part of the company's advertising targeting system, so they decided to let it stand, rather than re-engineer their surveillance advertising business.
The idea that users are safer when bugs are kept secret is called "security through obscurity" and no one believes in it – except corporate executives. As Bruce Schneier says, "Anyone can design a system that is so secure that they themselves can't break it. That doesn't mean it's secure – it just means that it's secure against people stupider than the system's designer":
The history of massive, brutal cybersecurity breaches is an unbroken string of heartbreakingly naive confidence in security through obscurity:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But despite this, the idea that some bugs should be kept secret and allowed to fester has powerful champions: a public-private partnership of corporate execs, government spy agencies and cyber-arms dealers. Agencies like the NSA and CIA have huge teams toiling away to discover defects in widely used products. These defects put the populations of their home countries in grave danger, but rather than reporting them, the spy agencies hoard these defects.
The spy agencies have an official doctrine defending this reckless practice: they call it "NOBUS," which stands for "No One But Us." As in: "No one but us is smart enough to find these bugs, so we can keep them secret and use them attack our adversaries, without worrying about those adversaries using them to attack the people we are sworn to protect."
NOBUS is empirically wrong. In the 2010s, we saw a string of leaked NSA and CIA cyberweapons. One of these, "Eternalblue" was incorporated into off-the-shelf ransomware, leading to the ransomware epidemic that rages even today. You can thank the NSA's decision to hoard – rather than disclose and patch – the Eternalblue exploit for the ransoming of cities like Baltimore, hospitals up and down the country, and an oil pipeline:
https://en.wikipedia.org/wiki/EternalBlue
The leak of these cyberweapons didn't just provide raw material for the world's cybercriminals, it also provided data for researchers. A study of CIA and NSA NOBUS defects found that there was a one-in-five chance of a bug that had been hoarded by a spy agency being independently discovered by a criminal, weaponized, and released into the wild.
Not every government has the wherewithal to staff its own defect-mining operation, but that's where the private sector steps in. Cyber-arms dealers like the NSO Group find or buy security defects in widely used products and services and turn them into products – military-grade cyberweapons that are used to attack human rights groups, opposition figures, and journalists:
https://pluralistic.net/2021/10/24/breaking-the-news/#kingdom
A good Cybercrime Treaty would recognize the perverse incentives that create the coalition to keep us from knowing which products we can trust and which ones we should avoid. It would shut down companies like the NSO Group, ban spy agencies from hoarding defects, and establish an absolute defense for security researchers who reveal true facts about defects.
Instead, the Cybercrime Treaty creates new obligations on signatories to help other countries' cops and courts silence and punish security researchers who make these true disclosures, ensuring that spies and criminals will know which products aren't safe to use, but we won't (until it's too late):
https://www.eff.org/deeplinks/2024/06/if-not-amended-states-must-reject-flawed-draft-un-cybercrime-convention
A Cybercrime Treaty is a good idea, and even this Cybercrime Treaty could be salvaged. The member-states have it in their power to accept proposed revisions that would protect human rights and security researchers, narrow the definition of "cybercrime," and mandate transparency. They could establish member states' powers to refuse illegitimate requests from other countries:
https://www.eff.org/press/releases/media-briefing-eff-partners-warn-un-member-states-are-poised-approve-dangerou

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/07/23/expanded-spying-powers/#in-russia-crime-cybers-you

Image: EFF https://www.eff.org/files/banner_library/cybercrime-2024-2b.jpg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/us/
844 notes
·
View notes
Text
But according to an official whistleblower disclosure shared with Congress and other federal overseers that was obtained by NPR, subsequent interviews with the whistleblower and records of internal communications, technical staff members were alarmed about what DOGE engineers did when they were granted access, particularly when those staffers noticed a spike in data leaving the agency. It's possible that the data included sensitive information on unions, ongoing legal cases and corporate secrets — data that four labor law experts tell NPR should almost never leave the NLRB and that has nothing to do with making the government more efficient or cutting spending. Meanwhile, according to the disclosure and records of internal communications, members of the DOGE team asked that their activities not be logged on the system and then appeared to try to cover their tracks behind them, turning off monitoring tools and manually deleting records of their access — evasive behavior that several cybersecurity experts interviewed by NPR compared to what criminal or state-sponsored hackers might do. The employees grew concerned that the NLRB's confidential data could be exposed, particularly after they started detecting suspicious log-in attempts from an IP address in Russia, according to the disclosure. Eventually, the disclosure continued, the IT department launched a formal review of what it deemed a serious, ongoing security breach or potentially illegal removal of personally identifiable information. The whistleblower believes that the suspicious activity warrants further investigation by agencies with more resources, like the Cybersecurity and Infrastructure Security Agency or the FBI.
Oh yeah at least one DOGE person we know was a straight-up cybercriminal.
84 notes
·
View notes
Text
Create account with IP Banido // Twitter Shawdoban IP (PC/NOTEBOOK)
Hello guys I will teach you how to create an account with IP banned, I will teach here … If you help you follow me there and reblog for more range soon, I will bring a tutorial for cell phones

1 - Use the Brave browser 2 - Go to Settings> Privacy and Safety> Delete Navigation Data and Delete the entire period from your navigation 3 - In the same page you go down to '' Website and Security Settings ''> See permissions and data stored on websites and then look for X (Twitter) and delete everything, cache and data
***That done let's go to the vpn and proxy part***
1 - Look for the WindSribe website, he Dara VPN and Proxy 100% Free 2 - Create an account with some email of yours and confirm then so you will earn 10gb vpn + proxy 3 - Download the Windscribe extension on your brave and uses VPN in the Autopilot option 4 - Create a new account in Gmail using VPN Windscribe 5- - Open X (Twitter) and create an account with that same email
Never open X (Twitter) without VPN on to have the risk of being detected

Some of you can already be aware of this method but there are a lot of people who do not know so I just pass this tutorial :>
follow me
#tccblr#tc community#tcc fandom#tw trauma#tcc edit#tcc dylan#tcc tumblr#tcc columbine#teeceecee#true cringe community#adamlanza#true cream community#dylan columbine#columbine 1999#columbine school shooting#eric columbine#eric and dylan#pekka eric auvinen#tcc eric#tcc dylric#adam tcc#school#randy stair#crimescene#crime rp
62 notes
·
View notes
Text
me when companies try to force you to use their proprietary software

anyway
Layperson resources:
firefox is an open source browser by Mozilla that makes privacy and software independence much easier. it is very easy to transfer all your chrome data to Firefox
ublock origin is The highest quality adblock atm. it is a free browser extension, and though last i checked it is available on Chrome google is trying very hard to crack down on its use
Thunderbird mail is an open source email client also by mozilla and shares many of the same advantages as firefox (it has some other cool features as well)
libreOffice is an open source office suite similar to microsoft office or Google Suite, simple enough
Risky:
VPNs (virtual private networks) essentially do a number of things, but most commonly they are used to prevent people from tracking your IP address. i would suggest doing more research. i use proton vpn, as it has a decent free version, and the paid version is powerful
note: some applications, websites, and other entities do not tolerate the use of VPNs. you may not be able to access certain secure sites while using a VPN, and logging into your personal account with some services while using a vpn *may* get you PERMANENTLY BLACKLISTED from the service on that account, ymmv
IF YOU HAVE A DECENT VPN, ANTIVIRUS, AND ADBLOCK, you can start learning about piracy, though i will not be providing any resources, as Loose Lips Sink Ships. if you want to be very safe, start with streaming sites and never download any files, though you Can learn how to discern between safe, unsafe, and risky content.
note: DO NOT SHARE LINKS TO OR NAMES OF PIRACY SITES IN PUBLIC PLACES, ESPECIALLY SOCAL MEDIA
the only time you should share these things are either in person or in (preferably peer-to-peer encrypted) PRIVATE messages
when pirated media becomes well-known and circulated on the wider, public internet, it gets taken down, because it is illegal to distribute pirated media and software
if you need an antivirus i like bitdefender. it has a free version, and is very good, though if youre using windows, windows defender is also very good and it comes with the OS
Advanced:
linux is great if you REALLY know what you're doing. you have to know a decent amount of computer science and be comfortable using the Terminal/Command Prompt to get/use linux. "Linux" refers to a large array of related open source Operating Systems. do research and pick one that suits your needs. im still experimenting with various dispos, but im leaning towards either Ubuntu Cinnamon or Debian.
#capitalism#open source#firefox#thunderbird#mozilla#ublock origin#libreoffice#vpn#antivirus#piracy#linux
713 notes
·
View notes
Text
Alt National Park Service
We apologize for the length of this post, but we felt it was important to share the full details with you.
In early March, a group of Musk-affiliated staffers from the so-called Department of Government Efficiency (DOGE) arrived at the National Labor Relations Board (NLRB), the federal agency responsible for protecting workers’ rights and handling union disputes. They claimed their mission was to improve efficiency and cut costs. But what followed raised serious alarms inside the agency and revealed a dangerous abuse of power and access.
Once DOGE engineers were granted access to the NLRB’s systems, internal IT staff quickly realized something was wrong. Normally, any user given access to sensitive government systems is monitored closely. But when IT staff suggested tracking DOGE activity—standard cybersecurity protocol—they were told to back off. Soon after, DOGE installed a virtual system inside the agency’s servers that operated in secret. This system left no logs, no trace of its activity, and was removed without a record of what had been done.
Then, large amounts of data began disappearing from the system. This wasn’t routine data—it included sensitive information on union strategies, ongoing legal cases, corporate secrets, and even personal details of workers and officials. None of it had anything to do with cutting costs or improving efficiency. It simply wasn’t supposed to leave the NLRB under any circumstance.
Almost immediately after DOGE accounts were created, login attempts began—from a Russian IP address. These weren’t random hacks. Whoever it was had the correct usernames and passwords. The timing was so fast it suggested that credentials had either been stolen, leaked, or shared. Security experts later said that if someone wanted to hide their tracks, they wouldn’t make themselves look like they were logging in from Russia. This wasn’t just sloppy—it was bold, calculated, and criminal.
One of the NLRB’s IT staffers documented everything and submitted a formal disclosure to Congress and other oversight bodies. But instead of being protected, he was targeted. A threatening note was taped to his door, revealing private information and overhead drone photos of him walking his dog. The message was clear: stay silent. He didn’t. He went public.
This isn’t just a cybersecurity issue—it’s a coordinated effort to infiltrate government agencies, bypass legal safeguards, and harvest data that can be used for political, corporate, or personal leverage. With Elon Musk directing DOGE, it’s hard not to see the motive: access to union files, employee records, and legal disputes that could benefit his companies and silence critics. This same playbook appears to be unfolding across multiple federal agencies, with DOGE operatives gaining quiet access to sensitive systems and extracting vast amounts of data without oversight.
The truth is, DOGE was never about making government more efficient. It was about taking control of it from the inside. What happened at the NLRB is not an isolated incident—it’s a warning of what happens when billionaires are handed unchecked power inside public institutions.
58 notes
·
View notes
Text

dave whammond
* * * *
Shocking disclosures regarding a data breach at the National Labor Relations Board suggest illegal conduct by DOGE members
Over the weekend, NPR published a lengthy story about a potential major data breach at the National Labor Relations Board. At first blush, the story sounds like it is in 45th place on the list of the most horrible things that Trump and DOGE have done in the first 86 days of his administration.
But you must pay attention to this story. It is a national scandal that suggests DOGE has intentionally exposed confidential US government information to foreign adversaries.
I will give a very brief summary, but urge you to read, listen to, or watch one of the sources I cite below.
In short, a whistleblower from the National Labor Relations Board (NLRB) claims the following:
DOGE gained access to the NLRB's most sensitive information, which included labor complaints, identity of whistleblowers, identity of private employees engaged in union organizing, and enforcement actions against private companies (like Tesla and SpaceX).
DOGE turned off log files that would record their actions.
DOGE set up a “black box” inside the NLRB network so that NLRB IT personnel could not monitor what was happening.
DOGE disabled security protections, thereby exposing the NLRB’s sensitive information to the internet.
Within 15 minutes of the firewall protections being disabled, someone using an IP address in Russia used a username and password for a DOGE team member to attempt to access the NLRB information.
NLRB IT members witnessed a massive spike in information being downloaded from the NLRB servers.
A DOGE team member set up a file that was briefly visible on a public forum; the filename suggested that it was a “backdoor” download program for an NLRB-specific database.
The NLRB IT staff asked the federal Cybersecurity and Infrastructure Security Agency (CISA) security team to help launch an investigation, but the CISA investigation was peremptorily shut down without explanation.
The employee who asked CISA to begin the investigation received a typed note on his residence door which warned the employee to drop the request for CISA assistance and included personal details about the employee known only from government files. The note also included a drone photo of the employee walking his dog on a public street.
A spokesperson for the NLRB issued a statement claiming that DOGE never visited the NLRB and did not gain access to NLRB data—a statement that seems to a blatant, easily disprovable lie.
I have not done justice to the details of the story. There are three ways you can educate yourself about this story.
First, the lengthy NPR article is here: NPR, Whistleblower details how DOGE may have taken sensitive NLRB data.
Second, the NPR report has a seven-minute audio summary embedded in the article. It is an accessible entry point into the article.
Finally, Rachel Maddow did an excellent job of explaining the whistleblower allegations on Tuesday evening. I have excerpted the 20-minute segment of her show that includes an interview with the whistleblower and his attorney. See The Rachel Maddow Show, Whistleblower Excerpt, April 15, 2025.
As a personal favor to me (and you), I urge you to watch the Rachel Maddow segment. It will bring you up to speed on this scandal, which will be around for a long time and may be the undoing of DOGE.
If you watch the Rachel Maddow show, you will meet the whistleblower--Daniel Berulis—who is a loyal employee of the federal government who says that he “hopes he is wrong” in believing that DOGE exposed sensitive information to someone in Russia who was using a DOGE username and password.
At this very moment, there are hundreds or thousands of Daniel Berulises in the federal government who have not come forward. Daniel Berulis’s example should encourage them to come forward to describe other instances of DOGE misconduct or carelessness that may have harmed America’s interests.
If Berulis’s allegations are true, it is difficult to see how the conduct by at least one DOGE member does not rise to the level of a felony. We need to know more and must be open to the facts, including denials of the allegations. But the allegations are truly shocking and suggest that DOGE may have inflicted grievous injury on the US by exposing confidential information.
CODA: As shocking as the above allegations are, we have reasonable grounds for believing misconduct by Trump administration officials in seeking to conceal their unlawful actions.
Remember Signalgate? You may recall that CIA Director John Ratcliffe participated in chats on an non-secure commercial application. Congress has asked that all such communications be turned over for review.
Well, it might not shock you to learn that the CIA’s information technology team has informed Congress that none of John Ratcliff’s communications on Signal are recoverable. See MSNBC, Missing Signal messages from CIA director’s phone raise cover-up concerns.
Remember after the January 6 insurrection when most of the Secret Service’s texts were mysteriously deleted and therefore unavailable for review by the January 6 Committee? See PBS News, Government watchdog says Secret Service agents deleted Jan. 6 text messages.
Once is a mistake. Twice is a suspicious coincidence. Three times is a damning pattern. Secret Service. Signalgate. DOGE. It appears that actors within the Trump administration believe that destroying communications is an acceptable way to avoid accountability. It is up to Congress and the courts to get to the bottom of the DOGE NLRB incident and Signalgate as quickly as possible—before more evidence goes missing.
[Robert B. Hubbell Newsletter]
#Robert B. Hubbell#Robert B. Hubbell Newsletter#MSNBC#Rachel Maddow#DOGE#coverup#Signalgate#National Labor Relations Board#foreign adversaries
58 notes
·
View notes
Text

Mike - has print of Charles Babbage in his basement. He was known as "The Father of the Computer".
Will - did a project on Alan Turing. He was known as "The Father of Computer Science". He was specifically known for breaking the enigma code. And of course, he was gay as well.
Why are they associated with computers? What's going on here?
I think it may be related to cracking codes and unlocking memories. Computers hold memory.





In ST2, Will was "possessed" and the MF (father) took over him.
After Will was sedated -> the power went out in the lab resulting in the whole building going into lockdown.
Lets break this down symbolically:
Will is sedated. His "power" went out.
As a protective fail secure measure, Will goes into full lockdown. That way, his doors remain closed. Doors as in, his closet door and the door into his memories.

In order to unlock the doors, and save everyone, the computer in the basement (a hint towards Mike himself) must be rebooted with a code. However, since they don't know the code, Bob overrides it. He opens the doors without consent.
This doesn't end well, as we know. Bob attempts to hide in a closet... then is attacked once he attempts to escape.

Will wants the doors/gates closed.


As much as he wants to keep everything contained... it can't. That's the problem. Papa says it right here- demons in the past invaliding from the subconscious. That's what it's all been about this whole time.
Okay back to computers.
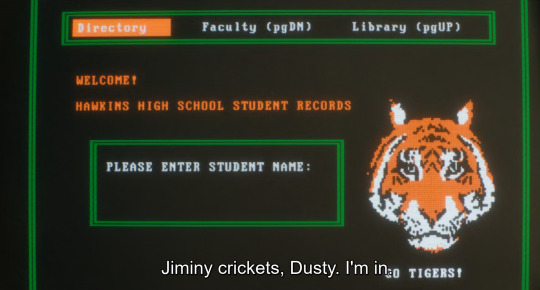
In ST4, we see Suzie hack into the Hawkins High student records to gain access to change Dustin's grades.
This again is another hint.
Tigers are associated with Will. "Jiminy Crickets" is a character in Pinocchio who is a representation of Pinocchio's conscience (aka an internal aspect of the mind being externalized).


Mike and Will call the (secret) number Unknown Hero Agent Man leaves them, and find they called a computer. They both mention that this reminds them of the movie War Games.



They meet up with Suzie and she attempts to track where NINA is using the IP address.
There's a mention of the address possibly hidden in the computer coding, and Suzie mentions "data mining".
Now keep in mind- her father was guarding the computer and they needed him out of the way to gain access to the computer.
Now I just want to briefly mention AI.
Alan Turing was also well known for The Turing Test. This was a way to test a machine's ability to think like a human. So basically, it tests artificial intelligence (AI).
We have (subtle) references to movies featuring AI throughout the show that are worth mentioning:

War Games. Mike mentions "Joshua" who is the computer. "Joshua" is the AI villain in the movie who attempt to start WWIII.

The Terminator. Multiple references to this movie! The Terminator is an AI who travels back in time to kill.

2001: A Space Odyssey. In that movie, the main villain is "Hal" who is an AI that kills.
I do think the computer is the mind... likely both Will's and Mike's minds are important here. And like a computer, they have to access it in order to obtain important data... important memories.
94 notes
·
View notes
Text
Pinging and Tapping
In the world of the Murderbot Diaries, communication is often conducted via comm and feed. Generally, comm is used when internal network is not available, or when one is trying to communicate across space, and feed is used when people are on the same network and allow each other access.
We also often see “pings” and “taps” as a way of quick communication.
Generally, pings are used for comm communications, and taps are used for feed communications, but there seem to be different purposes. Here are what we can gather from the story, and also from real life examples.
[Pings]
Purpose in the MB world:
Pings are typically used for signalling, checking connectivity, and getting responses from other systems or units. They act like a way to see if the other side is present and ready to communicate or respond.
Purpose in Real Life:
Network Connectivity: In computer networks, a "ping" is a diagnostic tool used to test the reachability of a host on an Internet Protocol (IP) network. It measures the round-trip time for messages sent from the originating host to a destination computer.
Usage in the MB World:
Status Checks: Used to check if systems, such as satellites, drones, or transports, are active and responsive. For example, pinging a satellite to see if it responds.
Communication Initiation: Used to start communication with other systems, often to establish a connection or share data. For instance, pinging a transport to offer media files in exchange for a ride.
Detection: Used by systems to detect the presence of specific units, like SecUnits, without direct contact.
Usage in Real Life:
ICMP Echo Request/Reply: The ping command sends an ICMP (Internet Control Message Protocol) Echo Request message to the target host and waits for an ICMP Echo Reply.
Network Troubleshooting: Used to determine if a particular host is reachable and to measure the latency between the source and destination.
[Taps]
Purpose in the MB World:
Taps are used more for internal communication within the network or feed. They serve as a means to acknowledge, signal actions, or provide private communication without verbal interaction.
Purpose in Real Life:
Internal Communication: In many systems, "taps" or similar mechanisms are used to signal and communicate internally within a network or system.
Usage in the MB World:
Acknowledgments: Used to acknowledge received messages or instructions. For instance, tapping back an acknowledgment to confirm receipt of instructions.
Private Communication: Used to send private or secure messages within the feed, often to communicate specific commands or information discreetly. For example, tapping the feed to communicate privately with another character without others listening in.
Control Signals: Used to signal or control actions within the feed, like tapping to instruct a character to fall back or take specific actions.
Usage in Real Life:
Signalling Mechanisms: Within computer systems, taps can be analogous to various signalling mechanisms like inter-process communication (IPC), which includes methods such as semaphores, shared memory, and message queues.
Acknowledgments and Control Signals: In networking, control signals and acknowledgments are crucial for managing data flow and ensuring reliable communication. For example, TCP (Transmission Control Protocol) uses acknowledgments to confirm the receipt of data packets.
Network Taps: In the context of network security, a "network tap" is a device that allows access to data flowing across a network for monitoring and analysis..
[Comparison]
In both the fictional world of Murderbot Diaries and real life, pings are primarily used for external signalling and connectivity checks, while taps are used for internal communication and control within the feed network
-------------------------------------------------
[Something Worth Noting]
There are some instances where taps seem more reasonable, but pings are used instead.
In Artificial Condition when Murderbot was watching Sanctuary Moon, and ART was trying to get its attention, asking to watch World Hoppers together. (see Artificial Condition, Pings, 5, 6 my AO3)
In Network Effect, when Murderbot finds that a hostile vessel (i.e. ART) was approaching and notifies the team quickly (see Network Effect, Pings, 1 my AO3)
In Network Effect, when Murderbot was locking itself up in the bathroom (see Network Effect, Pings, 11, 12 my AO3)
In Network Effect, when ART requested a private connection (see Network Effect, Pings, 13 my AO3)
In Network Effect, when Amena comes along with Murderbot to investigate Barish-Estranza shuttle, but is told to wait outside. She offers to help to which Murderbot pings acknowledgement (see Network Effect, Pings, 14 my AO3)
At the end of System Collapse when Murderbot pinged Three to ask if it wanted to listen to Holism explain planetary infrastructure (see System Collapse, Pings 15 my AO3)
Of these, 1, 3, 4 are where ART was sending pings to Murderbot. This is actually quite sweet, because we can tell that ART is being very polite to Murderbot. ART is fully capable of slamming into Murderbot’s private feed, but in all of these occasions, Murderbot has been rejecting feed communication which it reserves for friends and clients. ART is respecting this.
Instance 2 is unusual, and I am not 100% sure why Murderbot chose to use ping here. But since it was emergency, and ping is a protocol where it receives automatic response if it had been received at the other end, it was sufficient for its purposes.
When we read the context in which 5 happens we notice that Murderbot is now inside the B-E shuttle, and for security reasons, ART had cut it off from the feed network. So, Murderbot has the options of either verbally answering to Amena, or sending a ping for acknowledgement, and it chose the latter.
In instance 6, Murderbot seems to be being polite to Three who is busy (?) watching educational media. They are cordial to each other, but because Three is still not used to being a free SecUnit, Murderbot is being more careful around it.
--------------
If you are willing to be bored to death, you can see my AO3 post for the list of all the instances where pinging and tapping happen!
113 notes
·
View notes