#LibFuzzer
Explore tagged Tumblr posts
Text
Fuzz Testing: Strengthening Software Security with Keploy

In today’s fast-paced digital world, ensuring software security is a top priority. One of the most effective ways to uncover hidden vulnerabilities is through fuzz testing (or fuzzing). This powerful software testing technique involves injecting random, malformed, or unexpected inputs into an application to identify security weaknesses. Fuzz testing is widely used to detect crashes, memory leaks, and security exploits that traditional testing methods might miss.
With the increasing complexity of modern software, AI-driven testing tools like Keploy can automate fuzz testing and improve the overall security and stability of applications. In this blog, we’ll explore fuzz testing, its importance, different types, tools, best practices, and how Keploy enhances fuzz testing.
What is Fuzz Testing?
Fuzz testing is an automated testing approach designed to test how software handles unexpected or incorrect input data. By flooding an application with random or malformed data, fuzzing helps identify security vulnerabilities, crashes, and stability issues that attackers could exploit.
Unlike traditional testing, which uses predefined test cases, fuzz testing is designed to break the system by simulating real-world attack scenarios. It plays a crucial role in penetration testing, security auditing, and robustness testing.
Why is Fuzz Testing Important?
Fuzz testing is one of the most effective ways to uncover security flaws in software applications. Here’s why it matters:
Identifies Hidden Vulnerabilities – Helps find security loopholes that traditional testing might miss.
Enhances Software Stability – Prevents crashes and unexpected behavior under extreme conditions.
Automates Security Testing – Saves time by automatically generating unexpected test cases.
Simulates Real-World Attacks – Identifies weaknesses before malicious attackers do.
Real-World Example
Fuzz testing has played a crucial role in identifying vulnerabilities in operating systems, web applications, and network protocols. Major software vendors like Google, Microsoft, and Apple use fuzzing techniques to detect security flaws before deployment.
Types of Fuzz Testing
There are different fuzzing techniques based on how inputs are generated and applied:
1. Mutation-Based Fuzzing
This method modifies existing valid inputs by introducing small changes or random errors. It is simple but may not always cover all edge cases.
2. Generation-Based Fuzzing
Instead of modifying existing inputs, this approach creates test inputs from scratch based on predefined rules. It is more structured and effective for testing complex applications.
3. Coverage-Guided Fuzzing
This technique monitors code coverage and adjusts test inputs dynamically to reach more parts of the application. Tools like AFL (American Fuzzy Lop) and LibFuzzer use this approach.
How Fuzz Testing Works
The fuzz testing process typically follows these steps:
Input Generation – The fuzzer creates random, malformed, or unexpected inputs.
Test Execution – The inputs are injected into the application to observe how it reacts.
Behavior Monitoring – The system is monitored for crashes, memory leaks, or unexpected outputs.
Bug Analysis – Any failures are logged and analyzed for potential security threats.
This approach automates the testing process and quickly identifies vulnerabilities.
Fuzz Testing vs. Other Testing Techniques
How does fuzz testing compare to traditional testing methods?

While unit testing and functional testing ensure correct behavior, fuzz testing goes beyond correctness to test robustness against unexpected conditions.
Tools for Fuzz Testing
Several tools automate fuzz testing:
AFL (American Fuzzy Lop): A powerful, coverage-guided fuzzer used for security testing.
LibFuzzer: An in-process fuzzer for C/C++ programs that helps find memory issues.
Google OSS-Fuzz: A large-scale fuzzing service that continuously tests open-source projects.
Keploy: An AI-powered testing platform that automates test case generation and fuzz testing for APIs and integration testing.
How Keploy Enhances Fuzz Testing
Keploy is an AI-driven testing tool that generates test cases automatically by recording real-world traffic and responses. It enhances fuzz testing by:
Generating unexpected test cases for API security testing.
Simulating real-world edge cases without manual effort.
Improving test coverage and reliability for software applications.
Automating bug detection in production-like environments.
With Keploy, developers can integrate fuzz testing into their continuous testing strategy to ensure secure and robust software deployments.
Best Practices for Fuzz Testing
To maximize fuzz testing effectiveness, follow these best practices:
Integrate Early in the Development Cycle – Detect vulnerabilities before release.
Use a Combination of Testing Approaches – Combine fuzz testing with unit and integration testing.
Monitor and Log Failures – Keep detailed logs to analyze bugs effectively.
Automate with AI-powered Tools – Use Keploy and other automated fuzz testing tools to enhance efficiency.
Conclusion
Fuzz testing is a critical security testing technique that helps identify vulnerabilities by injecting unexpected inputs into software applications. It ensures software stability, prevents crashes, and enhances security. By leveraging AI-driven tools like Keploy, developers can automate fuzz testing, generate more realistic test cases, and improve software reliability. As cyber threats continue to evolve, integrating fuzz testing into your testing strategy is essential for building secure, robust, and high-performing applications.
0 notes
Text
OSS-Fuzz - Continuous Fuzzing Of Open Source Software
OSS-Fuzz - Continuous Fuzzing Of Open Source Software #AFL #Continuous #Fuzzer #Fuzzing #LibFuzzer #Open #OpenSource
[sc name=”ad_1″]
Fuzz testing is a well-known technique for uncovering programming errors in software. Many of these detectable errors, like buffer overflow, can have serious security implications. Google has found thousands of security vulnerabilities and stability bugs by deploying guided in-process fuzzing of Chromecomponents, and we now want to share that service with the open source…
View On WordPress
#AFL#Continuous#Fuzzer#Fuzzing#LibFuzzer#Open#Open Source#OSS Fuzz#OSSFuzz#reporting#software#Source#Stability#vulnerabilities
0 notes
Text
Visual studio 2022 download

#VISUAL STUDIO 2022 DOWNLOAD CODE#
#VISUAL STUDIO 2022 DOWNLOAD CODE#
Built Theme Converter to convert VS Code themes to work in Visual Studio 2022.Added Theme Pack and worked with VS Code theme authors to launch collection of custom themes.Added Color Tabs for vertical and horizontal tabs.External Sources Node in Solution Explorer.We have added more updates to the Extrenal Sources node, you can now see the module under the sub-node "Modules without Sources" and load the symbols form solution explorer itself.We have released a new type of breakpoint called Dependent Breakpoint, which allows you to configure a breakpoint to be enabled only if another breakpoint is first hit.Please see our AMP Deprecation links for more details. To silence the errors, define _SILENCE_AMP_DEPRECATION_WARNINGS. Including in a C++ project will generate build errors. Updated to NDK r21 LTS in C++ Mobile Development workload.Added support for gsl::not_null to code analysis.Code analysis now enforces that return values of functions annotated with _Check_return_ or _Must_inspect_result_ must be checked.We have improved null pointer dereference detection in our code analysis tooling.Support for libfuzzer under the switch -fsanitize=fuzzer.The IntelliSense Code Linter for C++ is now on by default, providing instant as-you-type suggestions and fix suggestions for common code defects.Improved C++ IntelliSense performance by optimizing cached header usage and symbol database access, providing improved load times to get into your code.Made improvements in C++ IntelliSense when providing navigation and syntax highlighting for types from imported Modules and Header Units.The Game development with C++ workload now installs the latest Unreal Engine with support with for Visual Studio 2022.Previously, the toolset used MD5 for source hashing by default. The MSVC toolset now defaults to SHA-256 source hashing in debug records.LLVM tools shipped with Visual Studio have been upgraded to LLVM 12.See the CMake 3.21 release notes for details on what is available. We have upgraded the version of CMake shipped with Visual Studio to version 3.21.You can now debug processes running on a remote systems from Visual Studio with LLDB.This is a step towards support for building modules-based projects with CMake and we are working on completing this support in later releases. Implemented /scanDependencies flag for outputting C++20 module dependencies for CMake projects as described in P1689r3.CMake Overview Pages have been updated to support CMakePresets.json.The Project menu in CMake projects has been streamlined and exposes options to "Delete Cache and Reconfigure" and "View Cache".This allows you to build a subset of targets in your CMake project. Visual Studio now supports the buildPresets.targets option in CMakePresets.json.Both cross-platform CMake projects and MSBuild-based Linux projects are supported. You can now build and debug natively on WSL2 without establishing a SSH connection.For more information see our Hot Reload section below. It supports both MSBuild and CMake projects. The new Hot Reload experience is now available to native C++ applications when running under the debugger.The v143 build tools are now available through the Visual Studio installer as well as the standalone build tools.Azure Cloud Service (classic) and Azure Cloud Service (extended support) projects are now supported.

0 notes
Text
[Media] Jazzer
Jazzer Coverage-guided, in-process fuzzing for the JVM Jazzer is a coverage-guided, in-process fuzzer for the JVM platform developed by Code Intelligence. It is based on libFuzzer and brings many of its instrumentation-powered mutation features to the JVM. The JVM bytecode is executed inside the fuzzer process, which ensures fast execution speeds and allows seamless fuzzing of native libraries. https://github.com/CodeIntelligenceTesting/jazzer
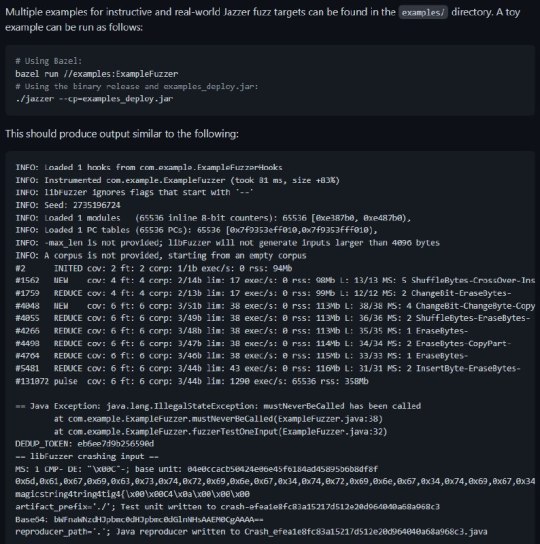
0 notes
Text
Using Clang LibFuzzer coverage-guided fuzzing engine with Nim
https://github.com/planetis-m/libfuzzer Comments
0 notes
Text
This Week in Rust 360
Hello and welcome to another issue of This Week in Rust! Rust is a systems language pursuing the trifecta: safety, concurrency, and speed. This is a weekly summary of its progress and community. Want something mentioned? Tweet us at @ThisWeekInRust or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Announcing Rust 1.47.0
Newsletters
This Month in Rust GameDev #14
Tooling
Rust Analyzer Changelog #46
Two videos about rust code coverage in VSCode
Observations/Thoughts
Rust after the honeymoon
Building the Fastest RaptorQ (RFC6330) Codec in Rust
Learning Rust through open source and live code reviews
My Mistakes Making a Canvas Based Game with Rust and WebAssembly
A New Backend for Cranelift, Part 1: Instruction Selection
Optional parameters in Rust
Building an async-compatible actor system
[video] Contract as Code as Contract: Using Rust to Unify Specification and Implementation
Learn Simple Rust
Iterators in Rust
Learn Rust by building the game Snake
That's so Rusty! Fearless concurrency
Making a Simple Calculator in Rust
Patterns of fallible iteration
[video] Learn Rust Together Part 5: Structs and Enums!
[video] 3. #everyonecancontribute cafe: Gitpod & learning Rust
Learn More Rust
Deploying a Rust HTTP server to DigitalOcean App Platform
Make A Language - Part Eight: Function Definitions
Supercharge your Electron apps with Rust
[ZH] Build a Shoot 'em up game with framework Amethyst
[video] Rust FFI: Microsoft Flight Simulator SDK Part 1
[video] Fuzz Testing popular Rust library in 5 min using cargo-fuzz / libfuzzer
Project Updates
Rust in Curl with Hyper
Memory Safe 'curl' for a More Secure Internet
Version 0.7 of calloop
Miscellaneous
Collect in Rust, Traverse in Haskell and Scala
Proving that 1 + 1 = 2 in Rust
What should I program?
Getting back to C++ after Rust is a pain.
Call for Blog Posts
The Rust Core Team wants input from the community! If you haven't already, read the official blog and submit a blog post - it will show up here! Here are the wonderful submissions since the call for blog posts:
Crate of the Week
This week's crate is paste, a macro to concatenate identifiers (which would otherwise be nightly only).
Thanks to mark-i-m for the suggestion!
Submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but didn't know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Create a Rust-Client for SirixDB
the-way: Highlight parameters in shell snippet when copying
the-way: Replace copy_to_clipboard code with arboard
Some of these tasks may also have mentors available, visit the task page for more information.
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from Rust Core
409 pull requests were merged in the last week
resolve: improve "try using the enum's variant"
Fix LitKind's byte buffer to use refcounted slice
Replace (Body, DefId) with Body where possible
perf: UninhabitedEnumBranching avoid n²
Fix span for unicode escape suggestion
Implement advance_by, advance_back_by for iter::Chain
Add PartialEq impls for Vec ↔ slice
stdsimd: Use xor to implement Neg::neg for floats
Rust Compiler Performance Triage
2020-10-13: 0 Regressions, 3 Improvements, 3 Mixed
Overall, fairly busy week, but without major regressions that need to be addressed.
See the full report for more.
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
No RFCs were approved this week.
Final Comment Period
Every week the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
RFC: Promote aarch64-unknown-linux-gnu to a Tier-1 Rust target
Access to traits' associated functions and constants from trait objects
Tracking Issues & PRs
[disposition: merge] stabilize union with 'ManuallyDrop' fields and 'impl Drop for Union'
[disposition: merge] stop promoting union field accesses in 'const'
[disposition: merge] passes: check_attr on more targets
[disposition: merge] resolve: Do not put nonexistent crate meta into prelude
[disposition: postpone]Tracking issue for experiments around coercions, generics, and Copy type ergonomics
New RFCs
Upcoming Events
Online
Octover 15. Berlin, DE - Rust Hack and Learn - Berline.rs
October 20. Denver, CO, US - Rust Denver - Data Science with Rust
October 21. New York, NY, US - A Journey into the Nucleus at Dropbox with Parker Timmerman - Rust NYC
October 21. Vancover, BC, CA - Rust Study/Hack/Hang-out night - Vancouver Rust
October 22. Edinburgh, UK - Fluence: interface-types for server-side WebAssembly modules - Rust Edinburgh
October 27. Dallas, TX, US - Last Tuesday - Dallas Rust
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Rust Jobs
Lead Software Engineer at Stake Technologies (SG, Remote)
Software Engineer at Stake Technologies (SG, Remote)
Service Engineer [Rust] at Narrative (Auckland, NZ - Remote within New Zealand)
Tweet us at @ThisWeekInRust to get your job offers listed here!
Quote of the Week
Just because Rust allows you to write super cool non-allocating zero-copy algorithms safely, doesn’t mean every algorithm you write should be super cool, zero-copy and non-allocating.
trentj on rust-users
Thanks to Nixon Enraght-Moony for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, and cdmistman.
Discuss on r/rust
0 notes
Text
Fuzz Testing: A Comprehensive Guide to Uncovering Hidden Vulnerabilities

In the realm of software testing, fuzz testing, or fuzzing, has emerged as a powerful technique to uncover vulnerabilities and improve system robustness. By introducing random and unexpected input into systems, fuzz testing helps identify weaknesses that traditional testing methods might overlook.
What Is Fuzz Testing?
The Concept Behind Fuzz Testing Fuzz testing is a software testing method that involves feeding random, unexpected, or malformed data into a program to identify potential vulnerabilities or crashes. The idea is to simulate unpredictable user input or external data that could expose hidden bugs in the software.
History of Fuzz Testing Fuzz testing originated in the late 1980s when researchers began exploring ways to stress-test systems under random input conditions. Over time, it has evolved into a sophisticated and indispensable tool for ensuring software security and reliability.
How Does Fuzz Testing Work?
Types of Fuzzers There are different types of fuzzers, each serving unique testing needs:
Mutation-Based Fuzzers: Modify existing input samples to generate test cases.
Generation-Based Fuzzers: Create test inputs from scratch, based on predefined rules or formats.
Fuzzing Process The fuzzing process typically involves three key steps:
Input Generation: Randomized or malformed input is generated.
Test Execution: The input is fed into the target system.
Monitoring: The system is observed for crashes, memory leaks, or unexpected behavior.
Benefits of Fuzz Testing
Identifying Vulnerabilities Fuzz testing excels at uncovering security vulnerabilities, such as buffer overflows, SQL injection points, and memory leaks, that may not surface during manual or automated scripted testing.
Improving System Robustness By exposing systems to unexpected inputs, fuzz testing helps improve their resilience to real-world scenarios. This ensures that software can handle edge cases and unforeseen data gracefully.
Challenges in Fuzz Testing
High Computational Overhead Generating and processing large volumes of random input can consume significant computational resources, making it challenging to integrate fuzz testing into resource-constrained environments.
Difficulty in Analyzing Results Determining whether a system failure is meaningful or spurious requires careful analysis. False positives can complicate debugging and slow down the development process.
Popular Tools for Fuzz Testing
AFL (American Fuzzy Lop) AFL is a widely-used fuzzer that applies mutation-based fuzzing to identify bugs efficiently. Its lightweight design and high performance make it a favorite among developers.
LibFuzzer LibFuzzer is an in-process, coverage-guided fuzzing library that integrates seamlessly with projects using LLVM. It allows for precise, efficient testing.
Other Notable Tools Other tools, such as Peach, Honggfuzz, and OSS-Fuzz, provide robust fuzz testing capabilities for various platforms and use cases.
When Should You Use Fuzz Testing?
Applications in Security-Critical Systems Fuzz testing is essential for systems that handle sensitive data, such as payment gateways, healthcare systems, and financial software, as it ensures that they are secure against potential threats.
Ensuring Protocol Compliance Fuzz testing is particularly useful for testing communication protocols to verify adherence to standards and uncover weaknesses in data handling.
Best Practices for Effective Fuzz Testing
Combine Fuzz Testing with Other Methods Fuzz testing should complement, not replace, unit and integration testing for comprehensive coverage. By combining testing methods, you can achieve better results and uncover a wider range of issues.
Monitor and Analyze Results Effectively Employ tools and techniques to track crashes and interpret logs for actionable insights. This helps prioritize fixes and minimizes false positives.
Regularly Update and Customize Fuzzers Tailoring fuzzers to your application’s specific needs and updating them as your software evolves improves their effectiveness.
Future of Fuzz Testing
AI-Driven Fuzzing Artificial intelligence is enabling smarter fuzzers that generate more meaningful test cases. These AI-powered tools can better simulate real-world scenarios and uncover vulnerabilities faster.
Increased Automation in CI/CD Pipelines Fuzz testing is becoming an integral part of continuous testing in DevOps pipelines, ensuring that vulnerabilities are identified and fixed early in the software development lifecycle.
Conclusion
Fuzz testing is a powerful technique that can uncover hidden vulnerabilities and strengthen software systems. By feeding systems with random, malformed inputs, fuzz testing ensures resilience against unpredictable scenarios. Whether you're working on security-critical applications or enhancing protocol compliance, fuzz testing is a must-have in your testing strategy. As technology advances, integrating fuzz testing into your software development lifecycle will not only boost reliability but also safeguard your applications against evolving security threats. Don’t overlook the power of fuzzing—adopt it today to secure your software for tomorrow.
0 notes
Text
uniFuzzer - Fuzzing Tool Based On Unicorn And LibFuzzer
uniFuzzer - A Fuzzing Tool For Closed-Source Binaries Based On Unicorn And LibFuzzer #based #Binaries #ClosedSource
[sc name=”ad_1″] uniFuzzer is a fuzzing tool for closed-source binaries based on Unicorn and LibFuzzer. Currently it supports fuzzing 32-bits LSB ELF files on ARM/MIPS, which are usually seen in IoT devices.
Features
very little hack and easy to build
can target any specified function or code snippet
coverage-guided fuzzing with considerable speed
dependence resolved and loaded automatically
libr…
View On WordPress
0 notes
Photo

OSS-Fuzz – Continuous Fuzzing Of Open Source Software | MrHacker.Co #afl #continuous #fuzzer #fuzzing #libfuzzer #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo

uniFuzzer – Fuzzing Tool Based On Unicorn And LibFuzzer | TheHackerNews.Co #based #binaries #closedsource #elf #fuzzing #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Text
OSS-Sydr-Fuzz: Hybrid #Fuzzing for Open Source #Software This repository is a fork of OSS-Fuzz...
HackGit OSS-Fuzz vulnerabilities ▫️ OSS-Fuzz vulnerabilities for OSV https://github.com/google/oss-fuzz-vulns ▫️ Undetected Azure Active Directory Brute-Force Attacks https://www.secureworks.com/research/undetected-azure-active-directory-brute-force-attacks https://t.me/hackgit/1240
OSS-Sydr-Fuzz: Hybrid #Fuzzing for Open Source #Software This repository is a fork of OSS-Fuzz project. OSS-Sydr-Fuzz contains open source software targets for sydr-fuzz that combines fuzzing (libFuzzer) with the power of dynamic symbolic execution (Sydr). https://github.com/ispras/oss-sydr-fuzz
GitHub - ispras/oss-sydr-fuzz: OSS-Sydr-Fuzz - OSS-Fuzz fork for hybrid fuzzing (fuzzer+DSE) open source software. - GitHub OSS-Sydr-Fuzz - OSS-Fuzz fork for hybrid fuzzing (fuzzer+DSE) open source software. - GitHub - ispras/oss-sydr-fuzz: OSS-Sydr-Fuzz - OSS-Fuzz fork for hybrid fuzzing (fuzzer+DSE) open source software.
0 notes
Text
Google open sources ClusterFuzz
Google today announced that it is open sourcing ClusterFuzz, a scalable fuzzing tool that can run on clusters with over 25,000 machines.
The company has long used the tool internally and if you’ve paid particular attention to Google’s fuzzing efforts (and you have, right?), then this may all seem a bit familiar. That’s because Google launched the OSS-Fuzz service a couple of years ago and that service actually used ClusterFuzz. OSS-Fuzz was only available to open source projects, though, while ClusterFuzz is now available for anyone to use.
The overall concept behind fuzzing is pretty straightforward: you basically throw lots of data (including random inputs) at your application and see how it reacts. Often, it’ll crash, but sometimes you’ll be able to find memory leaks and security flaws. Once you start anything at scale, though, it becomes more complicated and you’ll need tools like ClusterFuzz to manage that complexity.
ClusterFuzz automates the fuzzing process all the way from bug detection to reporting — and then retesting the fix. The tool itself also uses open source libraries like the libFuzzer fuzzing engine and the AFL fuzzer to power some of the core fuzzing features that generate the test cases for the tool.
Google says it has used the tool to find over 16,000 bugs in Chrome and 11,000 bugs in over 160 open source projects that used OSS-Fuzz. Since so much of the software testing and deployment toolchain is now generally automated, its no surprise that fuzzing is also becoming a hot topic these days (I’ve seen references to “continuous fuzzing” pop up quite a bit recently).
0 notes
Link
0 notes
Link
Well, that escalated quickly:
I've applied libFuzzer ( http://tutorial.libfuzzer.info) to regexp library and found 5 heap-buffer-overflows, stack overflow, assert failure, use of uninitialized data, SIGSEGV, infinite loop, undefined shift, invalid enum value and a bunch of memory leaks in just half an hour
1 note
·
View note
Quote
From Twitter: Been working on my B-tree all day. I've just finished a clever new op, all my unit tests are green af and I'm very pleased with how this is going, and libFuzzer takes about two seconds to throw a failing case at me that's as long as my arm. I'm now not working on my B-tree today.— Bodil Stokke, Esq. (@bodil) April 25, 2020
http://twitter.com/bodil
0 notes
Text
Google open sources ClusterFuzz
Google today announced that it is open sourcing ClusterFuzz, a scalable fuzzing tool that can run on clusters with over 25,000 machines.
The company has long used the tool internally and if you’ve paid particular attention to Google’s fuzzing efforts (and you have, right?), then this may all seem a bit familiar. That’s because Google launched the OSS-Fuzz service a couple of years ago and that service actually used ClusterFuzz. OSS-Fuzz was only available to open source projects, though, while ClusterFuzz is now available for anyone to use.
The overall concept behind fuzzing is pretty straightforward: you basically throw lots of data (including random inputs) at your application and see how it reacts. Often, it’ll crash, but sometimes you’ll be able to find memory leaks and security flaws. Once you start anything at scale, though, it becomes more complicated and you’ll need tools like ClusterFuzz to manage that complexity.
ClusterFuzz automates the fuzzing process all the way from bug detection to reporting — and then retesting the fix. The tool itself also uses open source libraries like the libFuzzer fuzzing engine and the AFL fuzzer to power some of the core fuzzing features that generate the test cases for the tool.
Google says it has used the tool to find over 16,000 bugs in Chrome and 11,000 bugs in over 160 open source projects that used OSS-Fuzz. Since so much of the software testing and deployment toolchain is now generally automated, its no surprise that fuzzing is also becoming a hot topic these days (I’ve seen references to “continuous fuzzing” pop up quite a bit recently).
source https://techcrunch.com/2019/02/07/google-open-sources-clusterfuzz/
0 notes