#Major and minor numbers Linux
Explore tagged Tumblr posts
Text
Writing Character Device Driver
Writing Character Device Driver - A Linux character device driver allows user programs to interact with hardware devices by reading or writing data one character at a time. Developing such drivers requires understanding the Linux kernel's structure, APIs, and coding practices.

Linux Kernel APIs and Key Concepts
The kernel provides APIs like register_chrdev() and alloc_chrdev_region() for registering character devices. Each device is identified by major and minor numbers, enabling the kernel to associate device files with their respective drivers.
File Operations and Device Registration
Drivers implement a set of file operations (struct file_operations) to define how the kernel handles user interactions, such as opening, reading, and writing the device. Properly registering the device using functions like cdev_add() ensures integration with the kernel.
Challenges in Development
Writing device drivers involves challenges like managing hardware-specific quirks, maintaining thread safety, and ensuring synchronization using mechanisms like mutexes, spinlocks, and semaphores. Compatibility across kernel versions and varying hardware specifications adds complexity.
Coding Standards and Security
Linux emphasizes clean, maintainable code. Following the kernel coding style and using the required headers ensures compliance. Security practices, such as validating user inputs and minimizing kernel attack surfaces, are critical in driver development.
Testing and Documentation
Thorough testing with tools like kmod and insmod is crucial. Developers must document interfaces, supported hardware, and usage instructions to aid users and maintainers.
Future Trends
With advancements in hardware, Linux device drivers will increasingly focus on improved modularity, real-time performance, and compatibility with modern interfaces like PCIe and USB 4.0.
By adhering to Linux's guidelines and practices, developers can create robust character device drivers that meet the needs of modern systems.
Linux character device driver development,Kernel modules,Device driver coding,Major and minor numbers Linux,File operations structure,Device registration in Linux,Hardware specifications for drivers,Linux kernel compatibility,Driver synchronization mechanisms,Error handling in drivers.
#Linux character device driver development#Kernel modules#Device driver coding#Major and minor numbers Linux#File operations structure#Device registration in Linux#Hardware specifications for drivers#Linux kernel compatibility#Driver synchronization mechanisms#Error handling in drivers
0 notes
Text
What Factors Should You Consider Before Application Migration?

Application migration is the process of transferring software applications from one environment to another. This may include relocating applications from in-house servers to the cloud, moving them between different cloud providers, or upgrading them with more modern systems.
Application migration can provide certain advantages such as better scalability, heightened security as well as cost effectiveness. Nevertheless, it requires thorough planning and taking into account a number of concerns so as to facilitate smooth changeover that will not result in major business disruptions.
What is Application Migration?

Application migration is the process through which software applications are transferred from their current environment to a new one. There are many reasons for this, such as to improve performance, minimise costs or make use of new features offered in updated platforms or cloud services.
Application Migration Strategy

When a business planning to relocate its software applications from one environment to another, e.g., from internal servers to cloud, it requires a proper approach referred to as application migration strategy. This strategy assist in making, inter alias, the migration to occur without interrupting the business.
1. Understanding Goals
First of all, it is necessary to pointing out of the objective of moving the applications, or the necessity of this procedure. It could be for cost cutting measure, better performance, or to take advantage of the new feature available in cloud.
2. Assessing Applications
Some of the applications may not necessarily need migration. That is why some Linux distributions can have specific needs or dependences and this is taken into account. It is advisable that each business unit assesses every application to establish which should be migrated and how.
3. Choosing the Right Approach
Application migration is not a monopoly of one technique where two techniques of migrating applications are discussed below. It could be done in one instance or done in parts/gradually. Both styles have some strengths and drawbacks; thus, one must select the option most appropriate for the company.
4. Planning and Timeline
Other tactics are the action plan in the format of timelines and specific steps to be accomplished. This ensures that all the persons involved know what to do and by when it should be accomplished.
5. Testing and Validation
It is necessary to stress that prior to migration, as well as after it was performed, the applications were tested to check their functionality in the new environment. This prevents occurrence of certain difficulties and enables the users never to encounter any complicated situations or challenges.
6. Optimisation
Once migrated, it is necessary to adjust the applications to the target setting as every new environment is unique. It could also entail some minor alterations made in an attempt to optimise on one aspect with regards to the other.
7. Risk Management
Migration can also be dangerous in a way that can be detrimental to a company because there can be data loss or even short-term space or time loss. Companies must also be prepared for the worst to happen and have contingencies according to the problematic situations that will arise.
8. Stakeholder Involvement
At the same time, the race must involve people from many divisions of the business. This could incorporate IT personnel, managers of certain departments, or merely the final consumers of these applications.
9. Communication
There should be specific and clear information exchange. Everyone should know the things that are going on, why those things are going on, and how those things could affect him or her.
10. Monitoring and Support
Even after migration is complete, it’s important to monitor the applications to make sure they continue to perform well. Providing support for users who might have questions or issues is also important.
Application Migration Risks

When considering application migration, there are several risks that businesses need to carefully evaluate and manage to ensure a smooth transition and avoid potential setbacks:When considering application migration, there are several risks that businesses need to carefully evaluate and manage to ensure a smooth transition and avoid potential setbacks:
1. Data Loss
While application migrating, one of the main focuses is the possible loss of data that might be extremely important. If data is not backed up or transferred the right way then it can lead to a lot of losses, time wasted, and big inconveniences for business.
2. System Downtime
Application migration frequently involves the unavailability of applications for a certain period of time, or even by some measures; incomplete. Longer stopping times tend to have immense effects on productivity as well as customer experience; thus, stopping times must be kept to a minimal and regulated.
3. Compatibility Issues
Running applications in new environments, for example transferring them to a new OS or letting them migrate to the cloud, can be problematic. These issues may stem either from dependencies on particular hardware and/or particular versions of software not compatible with the new environment.
4. Security Vulnerabilities
It is therefore important to note that during application migration, there are open grounds to insecurity vices since adequate security measures that should be adopted in the new environment may not have been adopted.
This entails making sure that the information that is being collected, stored, processed, and transmitted will be protected from hackers and other related security risks by encrypting the information, limiting the access to the information, and making sure that the information meets the set level of security standards.
5. Unexpected Costs
The migration from one application may be costly and when it is being relocated, costs such as licensing costs, costs of training on the new applications and technical costs may arise unexpectedly. These costs must be incorporated into project costing and a proper cost benefit analysis should be performed.
6. Performance Issues
In the new location, applications that undergo migration can have issues such as resource availability, communication delay and improper setting up of the application environment. The areas of performance testing and optimization should be of paramount concern to tackle the above problems.
7. User Resistance
Users may resist change brought about by application migration because either it alters people’s known work patterns or because they have to learn new interfaces or procedures. While resistance is an anticipated challenge that accompanies the implementation of new technologies, it is essential to understand how it would be tackled to enable proper implementation, especially for all the users to willingly and fully partake in the new change to take place and be effective fully.
8. Business Disruption
The problems resulting from the migration of applications are the decreased ability to provide service and the disruption of business, which can directly affect customer satisfaction. Some of these risks can be mitigated through the use of contingency planning and different phases of migration.
9. Compliance and Legal Issues
It could also increase compliance issues because tasks may be transferred to other environments which may have rules on data control, location or type of industry. It is crucial to follow the laws relating to the delivery of the services to avert legal repercussions.
10. Stakeholder Alignment
Lack of communication and engagement of stakeholder in application migration planning and implementation can result in miscommunication, rivalry in objectives, and time consumption. Healing stakeholders across organisational departments and stratums guarantees that all the needs of stakeholders are met.
Managing these risks before embarking on application migration is effective in reducing the likelihood of negative impacts on business when the migration process is underway, therefore improving the success of the modernisation process of the organisation’s digital landscape.
Changing Application Migration Use Cases

The ways businesses use application migration are evolving. It’s not just about moving software from one place to another for cost savings anymore. Now, companies migrate applications to gain flexibility, improve performance, and keep up with technological advancements.
1. Flexibility
Businesses now migrate applications to cloud platforms like AWS, Azure, or Google Cloud to gain flexibility. Cloud environments allow them to scale resources up or down based on demand without investing in physical hardware.
2. Performance Improvement
Moving applications to newer environments or platforms often improves performance. New technologies can handle larger volumes of data more efficiently or provide faster processing speeds, benefiting businesses that rely on quick data processing or real-time analytics.
3. Access to Advanced Features
Modern cloud platforms offer advanced features like AI tools, machine learning capabilities, and big data analytics. By migrating applications to these platforms, businesses can leverage these features to enhance their operations, gain insights from data, and improve decision-making processes.
4. Enhanced Security
Cloud providers invest heavily in security measures, often more than individual businesses can afford. Migrating applications to cloud environments can improve security by leveraging these robust security protocols and continuous updates against cyber threats.
5. Cost Efficiency
While cost savings remain a key driver, it’s now about more than just reducing IT infrastructure expenses. Businesses also consider long-term cost efficiencies, such as reducing maintenance costs, increasing operational efficiency, and freeing up resources for innovation.
6. Adaptability to Market Changes
In a rapidly changing market, businesses must adapt quickly. Application migration allows them to adopt new technologies, respond to customer demands faster, and stay competitive in their industry.
Overall, the use cases for application migration have expanded beyond simple cost-cutting measures. Businesses now migrate applications to improve performance, access advanced features, enhance security, and adapt to market changes swiftly. This strategic approach helps them stay agile, innovate, and meet evolving business needs effectively.
Management consulting firms play a crucial role in guiding companies through this transformation, offering expertise in strategic planning, risk management, and implementation strategies to maximise the benefits of application migration.
Application Migration Stages

Application migration is a process that involves several stages to ensure a smooth and successful transition from one environment to another. These stages are crucial for planning, executing, and validating the migration process:
1. Planning
This initial stage involves defining goals, assessing current applications, and outlining the migration strategy. It includes identifying dependencies, understanding resource requirements, and setting timelines and milestones for the migration project.
2. Assessment
In this stage, applications are thoroughly evaluated to determine their suitability for migration. Factors considered include business criticality, technical compatibility with the target environment, and potential impact on users and operations.
3. Migration
The migration stage involves the actual transfer of applications from their current environment to the new one. It includes data migration, application installation or deployment, configuration adjustments, and testing to ensure functionality in the new environment.
4. Validation
Once migrated, applications undergo rigorous testing and verification to ensure they perform as expected in the new environment. This stage includes performance testing, integration testing with other systems, and user acceptance testing to verify that all functionalities are intact.
5. Optimisation
After validation, optimisations may be necessary to fine-tune application performance, address any issues that arose during testing, and optimise resource utilisation in the new environment. This stage aims to maximise the benefits of migration and ensure ongoing operational efficiency.
Each of these stages demands meticulous planning, collaboration among stakeholders, and comprehensive testing to minimise disruptions and ensure a successful application migration process, with support from project development services to streamline operations.
Migrating Legacy Applications

Migrating legacy applications involves moving older software systems from their current environment to a new one. This could mean transferring them from older on-premises servers to modern cloud platforms like AWS, Azure, or Google Cloud.
Legacy applications are often outdated in technology and may depend on older hardware or software components that are no longer supported or efficient.
The challenge of migrating legacy applications lies in ensuring that they function properly in the new environment without disruptions to business operations. It requires carefully assessing the application’s architecture, dependencies, and compatibility with the target platform.
Businesses must decide whether to update, refactor, or replace the application to align it with current technology standards and business needs.
Key considerations in migrating legacy applications include:
1. Compatibility
Ensuring that the application can run effectively on the new platform without issues related to operating systems, databases, or middleware.
2. Data Migration
Moving data associated with the application to the new environment securely and without loss or corruption.
3. Performance
Optimising the application’s performance in the new environment to meet business requirements.
4. Security
Implementing adequate security measures to protect data and ensure compliance with regulatory requirements.
5. Cost
Evaluating the costs associated with migration, including licensing, infrastructure, and ongoing maintenance.
6. Testing
Conducting thorough testing throughout the migration process to identify and resolve any issues before deployment.
7. Training and Support
Providing training for users and support staff to ensure they can effectively use and maintain the migrated application.
Successful migration of legacy applications requires collaboration between IT teams, stakeholders, and possibly external software consulting services or project development services to navigate complexities and ensure a smooth transition.
By addressing these considerations thoughtfully, businesses can leverage the benefits of modern technology while preserving the functionality and value of their legacy applications.
Conclusion
In conclusion, application migration is a strategic initiative that can enhance business agility and efficiency. However, it requires careful planning, stakeholder engagement, and risk management to achieve successful outcomes.
Businesses should leverage application migration services, application migration tools, and cloud migration services offered by management consulting firms or software consulting services to navigate complexities and maximise the benefits of cloud application migration.
By evaluating candidates for migration, addressing legacy application migration challenges, and adopting a comprehensive application migration strategy, businesses can successfully modernise their IT infrastructure and drive innovation.
Walter & Associates are a company that deals with the complicated process of application migration in businesses. They give strategies customised for particular needs as well as offering hands-on guidance to facilitate smooth changes into new environments like cloud platforms, or even upgraded systems.
The areas where they have specialised include determining the compatibility of applications, secure management of data migration processes, boosting performance and minimising risks. Walter & Associates make it possible for organisations to swiftly modernise their operations using minimal interruption and maximisation of the benefits associated with new technology infrastructures by leveraging on their experience and services in application migration. Source: Application Migration
0 notes
Text
Device Classification and Their Associations in Linux System
Linux Each device on the system has its own set of fixed rules for operation, and there are numerous types and models of devices. It is not practical or meaningful to write the fixed rules for each device into the kernel.
Each device has its corresponding driver to ensure it can operate properly on the system. From a small LED light to a large network card, all devices require relevant drivers A driver can be seen as a layer of software between the application program and the actual device.
An application program controls a device by first sending a signal to the driver. The driver then receives the signal and commands the device to perform the corresponding action. If the application program wants to obtain the data collected by the device, it also needs to be done through the driver.
Classification of device in Linux
Linux systems divide devices into three basic types, and each module is typically implemented as one of these classes.
01 Character device
A character device is a device that can be accessed as a stream of bytes. This feature is implemented by a character device driver. Character device drivers typically implement at least open, close, read, and write system calls.
The character device is a sequential access, and the corresponding information can be read only after the device responds. It cannot be accessed randomly, and each character device has a device number, which consists of a major device number and a minor device number Common character devices such as serial ports and IICs.
The corresponding files for character devices are in the /dev directory, and each file corresponds to one piece of hardware. In the /dev directory of linux system, use ls -l to view the details, the first letter "c" is the identification of the character device file.
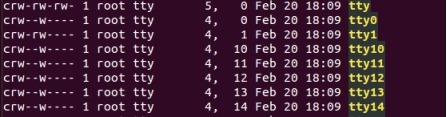
02 Block device
Like character devices, block devices are accessed through the file system node in the/dev directory. File systems can be accommodated on block devices. Common block devices such as disk, emmc flash, NAND flash, SD card, etc. Each block device likewise has r--+'/h vortex【5 slices【a device number, which consists of a primary device number and a secondary device number. Use the command ls -l to view the details in the /dev directory on a linux system. The first letter "b" identifies the block device file. /dev Each block device file under dev corresponds to a partition of the disk.
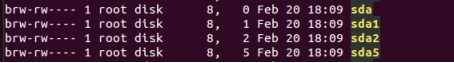
03 Network equipment
Any network-related transaction goes through a network interface, a device that can exchange data with other hosts. Usually, the interface is a hardware device, but it can also be a purely software device, for example, there is a lo in ifconfig to view information about the network interface, which is the network loopback (loopback) interface.
The way to access the network interfaces is to assign them a unique name, such as eth0, eth1, lo, and so on. However, no corresponding node exists in the file system for this name. Network interfaces do not have a device number like character and block devices, only a unique name such as eth0, eth1, etc., and this name does not need to correspond to a device file node.
The kernel uses a set of functions related to packet transfers to communicate with network device drivers, which differ from the read() and write() methods of character and block devices.
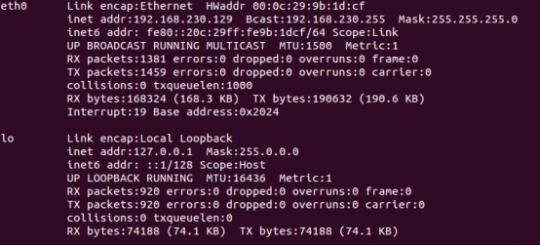
Various character devices and block devices all reflect the linux "everything is a file" design idea; network devices are the only devices that do not reflect this idea.
Device node, device driver and device association
There are many devices mounted on the whole system. When we access a device node, how does the system know which device driver to use and which device to access? This is achieved through the device number.
When creating a device node, you need to specify the major device number and the minor device number. For device nodes, the name is not important, the device number is the most important, which actually specifies the corresponding driver and the corresponding device.
Primary device numbers are used to distinguish between different types of devices, while secondary device numbers are used to distinguish between multiple devices of the same type. For commonly used devices, Linux has agreed-upon numbers, such asHard Disk the master device number of 3.
Use the command ls -l plus name in the /dev directory to view the corresponding primary and secondary device numbers.
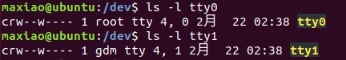
Main device
When a driver is initialized, it registers its driver and corresponding master device number with the system so that when an application accesses a device node, the system knows which driver it is accessing. You can drive the master device number of a system device through the /proc/devices file.
Minor equipment number
When the driver runs, it creates a device object for each device it finds that it can drive and assigns it a minor device number to distinguish between different devices. So that when an application accesses a device node, the driver knows which device it is accessing based on the minor number.
Originally published at www.forlinx.net.
0 notes
Text
This Week in Rust 463
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tweet us at @ThisWeekInRust or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Announcing the Rust Style Team
Foundation
Rust Foundation Project Grants are open for applications
Project/Tooling Updates
cargo careful: run your Rust code with extra careful debug checking
Async UI: a Rust UI Library where Everything is a Future
rust-analyzer changelog #149
Observations/Thoughts
How (and why) nextest uses tokio, part 1
in-place constructors
Quirks of Rust’s token representation
Brute forcing protected ZIP archives in Rust
This week in Fluvio #47: The programmable streaming platform
Rust Walkthroughs
How to call a C function from Rust (A simple FFI tutorial)
Rewriting the Modern Web in Rust
Implementing truly safe semaphores in rust
Model an ALU in Rust
6 things you can do with the Cow 🐄 in Rust 🦀
Platform Agnostic Drivers in Rust: MAX7219 Naive Code Refactoring
Last mile DynamoDB: Deno Deploy edition
Miscellaneous
The Initial Rust Infrastructure Has Been Merged Into Linux 6.1
Crate of the Week
This week's crate is humansize, a size formatting crate. Now in version 2.0, with an updated API.
Thanks, Leopold Arkham for the suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but didn't know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
AeroRust website - Add an aerospace related crate #Hacktoberfest
nmea - Supporting additional sentences #Hacktoberfest
AeroRust website - Request for content
zerocopy - test_new_error fails on i686
zerocopy - test_as_bytes_methods fails on powerpc
zerocopy - Miri can't run tests for wasm32-wasi target
Ockam - Prototype UDP NAT hole punching
Ockam - Refactor ockam secure-channel listener create command to use rpc
Ockam - Split CBOR / Messaging API schema.cddl
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
367 pull requests were merged in the last week
libc: add major/minor/makedev on apple OSes
miri: Add flag to specify the number of cpus
cargo: Iteratively construct target cfg
rustdoc-Json: List impls for primitives
clippy: Implement manual_clamp lint
clippy: Silence [question_mark] in const context
clippy: [manual_assert]: Preserve comments in the suggestion
clippy: [unnecessary_lazy_evaluations] Do not suggest switching to early evaluation when type has custom Drop
clippy: add box-default lint
clippy: fix [needless_borrow], [explicit_auto_deref] FPs on unions
clippy: let upper_case_acronyms check the enum name
clippy: let unnecessary_cast work for trivial non_literal expressions
clippy: lint nested patterns and slice patterns in needless_borrowed_reference
clippy: new implicit_saturating_add lint
rust-analyzer: Add proc-macro dependency to rustc crates
rust-analyzer: Fix PackageInformation having the crate name instead of package name
rust-analyzer: Fix annotations not resolving when lens location is set to whole item
rust-analyzer: Fix find_path using the wrong module for visibility calculations
rust-analyzer: Fix move_format_string_arg being tokentree unaware
rust-analyzer: Fix requests not being retried anymore
rust-analyzer: Fix trait impl item completions using macro file text ranges
rust-analyzer: Fix type alias hovers not rendering generic parameters
rust-analyzer: Use cfg(any()) instead of cfg(FALSE) for disabling proc-macro test
ci: Replace volta-cli/action with builtin functionality from actions/setup-node
docs.rs: new cache-policy & cache middleware structure to support full page caching
add #[rustc_safe_intrinsic]
add a niche to Duration, unix SystemTime, and non-apple Instant
add diagnostic struct for const eval error in rustc_middle
add negation methods for signed non-zero integers
added more const_closure functionality
adjust the s390x data layout for LLVM 16
compute lint levels by definition
fix #[derive(Default)] on a generic #[default] enum adding unnecessary Default bounds
fix format_args capture for macro expanded format strings
fix associated type bindings with anon const in GAT position
fix integer overflow in format!("{:.0?}", Duration::MAX)
generate synthetic region from impl even in closure body within an associated fn
get rid of exclude-list for Windows-only tests
serialize return-position impl Trait in trait hidden values in foreign libraries
stabilize #![feature(mixed_integer_ops)]
stabilize bench_black_box
use let-chaining in WhileTrue::check_expr
introduce {char, u8}::is_ascii_octdigit
macros: diagnostic derive on enums
add a filter for try commits in graphs, compare page and triage
codegen_gcc: Implement llvm.prefetch
codegen_gcc: simd: enable simd_as intrinsic
codegen_gcc: simd: implement float math intrinsics
allow users to debug their processes
Rust Compiler Performance Triage
A great week, with 170 primary benchmark scenarios seeing improvement. Every PR flagged by perf provided at least some wins, and perhaps more impressive: No rollup PR's were flagged by perf this week! Furthermore, cjgillot fixed an issue where incremental compilation was being unnecessarily hindered by our span and lint system. Great work everyone!
Triage done by @pnkfelix. Revision range: d9297d22..02cd79af
Full report here
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
No RFCs were approved this week.
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
[disposition: merge] make const_err a hard error
[disposition: merge] Elaborate supertrait bounds when triggering unused_must_use on impl Trait
[disposition: merge] Stabilize proc_macro Span::source_text
[disposition: merge] const-stablilize NonNull::as_ref
[disposition: merge] Add documentation about the memory layout of UnsafeCell<T>
[disposition: merge] Handle projections as uncovered types during coherence check
[disposition: merge] Never panic in thread::park and thread::park_timeout
[disposition: merge] Stabilize nonzero_bits
[disposition: merge] EscapeAscii is not an ExactSizeIterator
[disposition: merge] Change default level of INVALID_HTML_TAGS to warning and stabilize it
[disposition: merge] Add Box<[T; N]>: TryFrom<Vec<T>>
[disposition: merge] add no_compile doctest attribute
New and Updated RFCs
No New or Updated RFCs were created this week.
Upcoming Events
Rusty Events between 2022-10-05 - 2022-11-02 🦀
Virtual
2022-10-05 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2022-10-05 | Virtual (Stuttgart, DE) | Rust Community Stuttgart
Rust-Meetup
2022-10-06 | Virtual (Nürnberg, DE) | Rust Nuremberg
Rust Nürnberg online #18
2022-10-08 | Virtual | Rust GameDev
Rust GameDev Monthly Meetup
2022-10-11 | Virtual (Berlin, DE) | Open TechSchool Berlin
Rust Hack and Learn
2022-10-11 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2022-10-11 | Virtual (Saarbrücken, DE) | Rust-Saar
Meetup: 23u16
2022-10-11 | Virtual (Weiden, DE) | Digital Craftsmanship Nordoberpfalz
Woher kommt der Hype? Rust in 45 Minuten
2022-10-12 | Virtual (Boulder, CO, US) | Boulder Elixir and Rust
Monthly Meetup
2022-10-12 | Virtual (Erlangen, DE) | Rust Franken
Rust Franken Meetup #4
2022-10-12 | Virtual (San Francisco, CA, US / Redmond, WA, US / London, UK) | Microsoft Reactor San Francisco
Getting Started with Rust: Building Rust Projects | Redmond Reactor Mirror Event | London Reactor Mirror Event
2022-10-13 | Virtual (Berlin, DE) | EuroRust
EuroRust (Oct 13-14)
2022-10-15 | Virtual (Nürnberg, DE) | Rust Nuremberg
Deep Dive Session 2 (CuteCopter): Reverse Engineering a tiny drone
2022-10-18 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful—Impractical Rust: The HATETRIS World Record
2022-10-19 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rapid Prototyping in Rust: Write fast like Python; Run fast like C
2022-10-20 | Virtual (Stuttgart, DE) | Rust Community Stuttgart
Rust-Meetup
2022-10-25 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2022-10-26 | Virtual (Redmond, WA, US) | Microsoft Reactor Redmond
Your First Rust Project: Rust Basics
2022-10-27 | Virtual (Charlottesville, VA, US) | Charlottesville Rust Meetup
Using Applicative Functors to parse command line options
2022-11-01 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2022-11-02 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2022-11-02 | Virtual (Redmond, WA, US / San Francisco, SF, US) | Microsoft Reactor Redmond
Getting Started with Rust: From Java Dev to Rust Developer | San Francisco Reactor Mirror Event | London Reactor Mirror Event
Asia
2022-10-11 | Tokyo, JP | Tokyo Rust Meetup
Cost-Efficient Rust in Practice
Europe
2022-10-06 | Wrocław, PL | Rust Wrocław
Rust Wrocław Meetup #29
2022-10-12 | Berlin, DE | Rust Berlin
Rust and Tell - EuroRust B-Sides
2022-10-13 | Berlin, DE + Virtual | EuroRust
EuroRust (Oct 13-14)
2022-10-25 | Paris, FR | Rust Paris
Rust Paris meetup #53
North America
2022-10-13 | Columbus, OH, US | Columbus Rust Society
Monthly Meeting
2022-10-18 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2022-10-20 | New York, NY, US | Rust NYC
Anyhow ? Turbofish ::<> / HTTP calls and errors in Rust.
2022-10-20 | New York, NY, US | Cloud Native New York
Cloud-native Search Engine for Log Management and Analytics.
2022-10-25 | Toronto, ON, CA | Rust Toronto
Rust DHCP
2022-10-27 | Lehi, UT, US | Utah Rust
Bevy Crash Course with Nathan and Food!
Oceania
2022-10-10 | Sydney, NSW, AU | Rust Sydney
Rust Lightning Talks
2022-10-20 | Wellington, NZ + Virtual | Rust Wellington
Tune Up Edition: software engineering management
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
BurntSushi is a super experienced programmer who always seems to know what’s right
Shepmaster occasionally pops up to keep things level, and provides definitive answers and edits to all stackoverflow questions
Epage is the ecosystem guy thanklessly maintaining the things that make the magic of cargo possible
Dtolnay is an AI written in rust with the sole purpose of improving rust.
– trevg_123 on r/rust
Thanks to musicmatze for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
0 notes
Text
Last Monday of the Week 2022-10-03
Several parts for a project got lost in the mail and if I don't blow up a motor doing something ill-advised with transistors soon I'm going to become the Joker.
Listening: I went to see the Ndlovu Youth Choir, a youth music group out of Limpopo who became extremely well known after they got on America's Got Talent a few years ago. Great style, they do a wide array of different styles and songs over a pretty wide time period, here's two songs:
youtube
youtube
Reading: Mostly scraps of SCP stuff, but a bad week for reading
Watching: Finished Arcane. God damn. Yes I know it's been like a year since that came out shut up.
It's so good. The animation is beautiful, it's so carefully considered, there's so few shortcuts taken. There's a scene where Jayce throws up on the bridge and it's a really close shot that sells the physicality of vomiting so well, it's messy and unpleasant. Another studio might have cut to a really long silhouette shot for that kind of thing. The Ekko/Jinx fight might be one of the best fights in the show. Even basic conversations have thoughtful blocking and framing, very little simple shot/reverse, there's always a focus on body parts and movements.
It's very predictable, which is probably because it's very character driven and the characters don't change much, you could write a comprehensive study of most characters on a post-it. There's a few major pivotal moments and twists for a few characters which are huge, but for the most part you can just run what you know about them forward to predict what happens next. Even having no knowledge of LoL you can guess that the Firelighters are led by Ekko in like zero seconds.
Jinx and Jayce are the main sources of unpredictability but that's because she's Da Joker Baby and paranoid and has psychosis, and he's a very smart boy who doesn't know what he's doing so the moment someone suggests any kind of solution to him he immediately does it without thinking.
Every single characters' design slaps. They did not make the mistake of trying to be sensible. Why is the cop uniform kind of demure but hot in a sexy maid kind of way? How does Jinx maintain twin braids longer than she is while also being on fire some of the time? How does Ekko fight with all that stuff on? These are not questions to ask. The question to ask is how fucking cool does this look and the answer is very.
The levels of tragedy are off the charts. Every second episode there's an opportunity for things to be resolved and for peace to succeed and everyone to talk and it doesn't happen ever.
Viktor and Jayce should have fucked at some point if only to make the breakup even worse.
Playing: Brought my desktop's storage back online so I have somewhere to put games again, but I haven't actually done much with it. Fortunately since I moved to Arch again my Proton is more stable, I got Ace Combat working under Linux.
Making: weekend making time was lost to a number of minor emergencies, but I did have to pop a door off its hinges because the lock completely failed which was fun. Unfortunately it was the door to the toolshed so I had to scrabble together the tools to do said pin popping from whatever tools I keep in my desk.
Tools and Equipment: Treating a minor injury in the family so here's a reminder to check your first aid kits, I had to run out and grab a bunch of non-absorbing gauze because we were all out.
I'm currently in the process of stocking a more severe trauma care kit for the family because my dad is on anti-clotting and blood thinning medication for a while which makes all his wounds one level of severity worse, so also learn how to use Chest Seals and Tourniquets, there's good online resources but you can probably also find a Stop The Bleed training course near you, it's a big international programme.
13 notes
·
View notes
Text
How Sage University, Indore has become the most emerging University in central India
Sage University is a private university located in Indore, Madhya Pradesh, India and was established in 2017. The university offers various undergraduate, postgraduate and research programs in academic disciplines classified under different faculties including engineering & technology, science, arts, commerce, management, law and education. The university has been recognised and featured in many prestigious news/mass media outlets such as The times of India, OUTLOOK: The New Weekly Newsmagazine , Forbs India , Silicon India, Digital Learning , Assocham India and QS I-GAGE. The university has not just been recognised but also been awarded for their outstanding work in the academic field. The SAGE Group of Educations has many feathers added to its cap like the National Innovative Award, Most Promising Group of MP Award, Building Madhya Pradesh Campaign Recognition, Best Emerging University Award, and Top University of Central India Award. It has also received an Award in online education by QS I-GAGE, E-LEAD for its undergraduate courses. The university has been Ranked at 65 for Engineering by Times, and Ranked at 88 for Private Engineering by Outlook as per 2020. The university also offers many on campus facilities for the students to provide them with an all rounded experience, such as the college Library that can accommodate 125 students at a time and is a gateway to a comprehensive collection of more than 10,000 books, journals, periodicals, student projects and other related publications to support learning and research for all students It is Indore’s first University to be awarded for Excellence in Online Education by QS I-Gauge E-Lead and has been ranked Top Private Engineering Institute (2020), 4th in Central India, and 65th in India by The Times of India and Number One Emerging University by Outlook (2020). SAGE Indore has been conferred with Top Private University in Central India by the vice-president of India, Mr. M. Venkaiah Naidu, and Best University of Madhya Pradesh by Kamal Nath, chief minister of Madhya Pradesh in the year 2019
The library can accommodate 125 students at a time and is a gateway to a comprehensive collection of more than 10,000 books, journals, periodicals, student projects and other related publications to support learning and research for all students. Students can also access online digital libraries from leading providers such as Pro quest, Athens, Emerald, ACM and Current Law Journals. Library also has a facility of reprographic Section. The College Hostel has a Four floor building for both boys and girls with a capacity of 300 boys and girls along with all basic amenities available for students to prosper them in to home like environment. The hostels are available for single occupancy as well as shared ones for both boys and girls separately. The campus also has design studio, cafeteria, gym , medical facilities, shuttle service, auditorium and convenience store etc. The whole campus is Wifi enabled and the classrooms are air-conditioned . Sage University also has a strict anti ragging policy and grievance cell to make sure of the safety for all their students . The University offers up to 100% scholarships and they offer 6 different types of scholarships - Merit-based, Merit-cum-means, Sports, Student Ambassador scholarship, Excellence scholarship and MP Government scholarship. Till date this university has disbursed scholarship of total Rs. 2 crore for their Sage University is a private university that was established in 2017 in Indore
SAGE University Indore follows project-based learning for skill development of its students. Students are guided to take up Micro, Minor, Macro and Major projects in the final year of their course to develop critical thinking, problem solving, communication and ICT skills by focusing on a real-world problem involving multiple assessments. Further, SAGE Indore has signed over 30 MoUs, including international ones with Miles Education, USA NDHU Taiwan, Brunel University, London, London Postgraduate Credit Management College, UK and Tennessee Tech University, USA, NPTEL, MHRD Innovation Cell, International Skill Development Corporation, among others. The highest CTC offered to the students during SAGE University Indore placement 2020 was Rs 12.5 LPA and a 93% placement rate was recorded. The average CTC for the placement their students get is 3.6 LPA. Red Hat Linux, Micro Focus, Amazon Web Services, Google, etc. are among the top recruiters in the campus drive organized by Sage University for their students. All these features make Sage University one of the most emerging university in central India For further information you can check their official website - https://sageuniversity.inSage University Official Website
1 note
·
View note
Text
Vlc Player For Mac M1


Vlc Video Mac
Vlc Player For Mac M1 Garand
Vlc Player For Mac Os
Vlc Player For Mac Free
The non-profit VideoLAN Organization has announced the release of VLC 2.0 FINAL. VLC is a popular cross-platform, open-source video player capable of handling most media formats, and version 2.0 represents the first landmark update since its first official release in June 2009.
The most radical changes in VLC 2.0 will be found on the Mac platform, with support for Blu-ray playback being overshadowed by a radical overhaul of the user interface. This major step forward has divided the VLC community since it first emerged, with some decrying the loss of version 1’s minimalist approach to video playback.

VLC 2.0 on the Mac platform replaces the simplistic interface of version 1.x in favor of something more akin to iTunes, while also embracing the look of OS X Lion. It opens in Playlist view, with a two-paned window containing a list of common locations for media files in the left-hand pane, and an invitation to drag and drop files into the window for playback on the right.
VLC Media Player Updated for Security Fixes and More. A Week with the New Apple M1 MacBook Air. Get the latest Mac security news direct to your inbox. VLC Media Player is often seen on Windows Operating System. This version named VLC for Mac can run on Mac OS X and is endowed with the same functions as on Windows. It one of the best free, open source video players available for Mac devices. Key Features As already mentionned above, this VLC is especially conceived for Macs.
Media controls sit at the bottom of the window, and there’s a new audio effects option next to the full-screen button, which takes advantage of Lion’s full-screen support. Options in the left-hand window include a shortcut to the user’s iTunes library and a playlist option, as well as UPNP and various internet streams.
VLC 2.0 for Mac also includes experimental Blu-ray support, plus adds support for VLC’s lua-based extensions. These support various interactive features, such as pulling movie information and subtitles from the Internet, or posting to Twitter.
Version 2.0 is very much aimed at Mac users, with Linux and Windows users seeing less radical changes, although behind-the-scenes improvements, detailed in full at the VLC changelog, make the update worth pursuing for all platforms.
Vlc Video Mac
One major upgrade for Windows users is a dedicated 64-bit build of VLC, while the release notes also hint at future versions for mobile users, with an Android version in development, due to join VLC Media Player for iOS, which currently stands at version 1.1.
Vlc Player For Mac M1 Garand
VLC 2.0 FINAL is a free, open-source download for Windows, Mac and Linux.
Open-source, cross-platform VLC Media Player 2.0.5 has been released for Windows and Mac. Although a relatively minor update, it fixes a number of regressions from previous releases, plus improves overall stability and performance. Mac users also get a slightly tweaked user interface.
Also released alongside the main build is VLC Media Player 2.0.5 Portable, a standalone version for Windows users that requires no installation.
Headline new fixes in version 2.0.5 include improved reliability when playing back MKV, Koreus and SWF files as well as the subtitles demuxer. Also fixed are MPEG2 audio and video encoding, while a number of security issues -- notably with the HTML subtitle parser and AIFF demuxer.
Vlc Player For Mac Os
The new build also promises improvements in the form of “rework and fixes” to the Mac interface – we noticed new Library icons, for starters. OS X 10.5 (Leopard) users will also be pleased to learn a system sleep issue has also been fixed. Windows users get a fix for https streaming.
The new build fixes issues with DVB-S delivery system detection, adds new Welsh and Interlingua translations while updating 24 others, and also includes hundreds of other unspecified bug fixes, including around 100 commits on top of version 2.0.4 to fix a number of regressions in the 2.0.x development branch.
Vlc Player For Mac Free
The latest build is rolling out as an automatic update now, but you can jump the gun by downloading both VLC Media Player 2.0.5 for Windows and Mac, and VLC Media Player 2.0.5 Portable for Windows. Remember, it’s a simple and free way to add DVD video playback functionality to Windows 8 too.
Photo Credit:olly/Shutterstock

1 note
·
View note
Text
Transformative update coming for Ultimate Chicken Horse

Ultimate Chicken Horse announces the Transformative update in Linux, Mac and Windows games. While developer Clever Endeavour Games adds more content. And yes, this is a pretty HUGE content update. Which will arrive on March 4th. Including a lot of puns. So Ultimate Chicken Horse will receive the Transformidable Update. Because it is both transformative and formidable. This is what Clever Endeavour Games calls it.
Major Features:
Character reskins
It seemed a bit unfair that only Horse had an alternative look as Zebra. So the new friends below have also showed up! These exotic creatures will show up as outfit unlocks in the game. Which you will also get as you play local or online games.

Jetpacks
Your Party Box can now give you the brand new Jetpack or Jetpack Dispenser. So pick one up, and you’ll be flying through the course like a rocket. Just be careful of the hazards in the Transformative update. Which will also be playable on Linux, Mac and Windows. So in case you thought Ultimate Chicken Horse wasn’t wacky enough. There now 20 modifiers to play with. With all these modifiers, you can also make crazy combos. Even make custom challenge levels using specific modifiers. Since you can create a level and save it online in Challenge Mode. All players will have to use those modifiers to try to beat your level.
Physics Modifiers
Gravity: Changing the laws of physics has never been this easy.
Jump Strength, Multi Jump, and Walljumps Off: Tweak the jump strength, give yourself double or triple-jumps, and turn off wall-jumps entirely to play like a certain childhood platforming plumber.
Player Collisions: You asked for it in Ultimate Chicken Horse! No really, the community has been asking for it forever. If screwing your friends over is your thing, this modifier is for you. It can also be helpful though in levels that might be impossible without a friend or two!
Move Speed and Game Speed: Play in slow-mo to practice those precision jumps, or play in hyper-speed and see if you can keep up!
Frictionless: This is what it would feel like if it was always -40°C.
Ultimate Chicken Horse Transformidable Update (Linux, Mac, Windows)
youtube
Weird and Fun Modifiers
Post-Death Behaviours:
Ghost: Players come back as ghosts. And mess around with the level in the Transformative update. At least until others reach the afterlife
Zombie (shown to the left): Players come back as zombies with limited movement
Dead Hop: Players can hop around after they’ve met their fate, try it out to find out more!
Character Size (shown below): From “Way Tiny” to “Way Huge”!
Invisibility in Ultimate Chicken Horse
Dance Invincibility: Invincible when you dance, just like real life!
Jetpack Mode: Just like the item that you can pick up, but forever.
Block Effects
Moving Block Speed: For even crazier, better timed contraptions
A Projectile Rate of Fire: How fast can a crossbow shoot?
Plus Projectile Speed: How fast can an arrow fly?
Projectile Explosions in Ultimate Chicken Horse
Level Effects
Mirror Level: Flip the level about the horizontal or vertical axis
Doomsday Meteors: Flaming tennis ball meteors fall from the sky, hitting animals in their path!
Doomsday Lava: The floor is lava in Ultimate Chicken Horse. And it’s rising.
Respawns
So grant each player in Ultimate Chicken Horse a number of lives. Which can be used to respawn either automatically. Or while holding the Retry button. These respawns can be on a per-round basis. Which will also be a delicious addition the the game. Also per-match basis, which can lead to some deeper strategy. When players choose to use them. Or while you help give a handicap to players who are just learning.
Minor Features (if you can call these minor)
Ability to both rotate AND flip most blocks by pressing Sprint + Rotate when you are placing them. Many players have been asking for this for a long time, as it allows the creation of levels that are symmetrical, timed, and well-designed!
Paintbrush tool and adjustable Crumbling Block damage for level-building in Free Play
New Party Box options in the Game Rules: Disabled, Auto-Pick, and Double Party Box for more than 2 players
Random level platform in the Treehouse
So if you do not own Ultimate Chicken Horse. The games available on Steam and Humble Store. Priced at $14.99. But also playable on Linux, Mac and Windows.
#ultimate chicken horse#transformative#update#linux#gaming news#clever endeavour games#ubuntu#mac#windows#pc
1 note
·
View note
Text
Here at ComputingPost, we like exploring various network and system monitoring tools. So far we have covered the basic setup and usage of Zabbix, telegraf/InfluxDB, Grafana, and Prometheus. Zabbix functionality is similar to Cacti, though Cacti is more fit for network graphing. In this guide, we’ll look at how to install and configure Cacti on Ubuntu 20.04|18.04 Linux server. What is Cacti? Cacti is a completely open-source network monitoring and graphing tool that was designed as a front-end application for the industry-standard data logging tool RRDtool. Cacti harness the power of RRDTool’s data storage and graphing functionality. Some good features of Cacti include: Fast polling of metrics Support for multiple data acquisition methods Support for advanced graph templating User management functionality with ACL Cacti provide an intuitive and easy to use web interface which can be used for small LAN installations up to complex networks with thousands of servers and networking devices. Install Cacti Server on Ubuntu 20.04/18.04 Cacti has a number of dependencies that need to be installed and configured before you can deploy Cacti server itself. This guide will cover the installation of these dependencies one by one: Step 1: Update system and upgrade all packages We always start with server packages upgrade to avoid any dependency issues: sudo apt update sudo apt upgrade -y You can reboot the server after upgrade: sudo reboot Step 2: Install php and required modules We now need to install php and some php modules required by cacti. Run the following commands to get everything and installed. sudo apt -y install apache2 php php-mysql,curl,net-socket,gd,intl,pear,imap,memcache,pspell,tidy,xmlrpc,snmp,mbstring,gmp,json,xml,common,ldap sudo apt install libapache2-mod-php The most important module is php-snmp and php-mysql. Make sure they are installed. You can check your php version using the command: $ php -v PHP 7.4.3 (cli) (built: Nov 25 2021 23:16:22) ( NTS ) Copyright (c) The PHP Group Zend Engine v3.4.0, Copyright (c) Zend Technologies with Zend OPcache v7.4.3, Copyright (c), by Zend Technologies Update PHP parameters: sudo vim /etc/php/*/apache2/php.ini Set correct timezone: date.timezone = "Africa/Nairobi" Update memory limit: memory_limit = 512M Also adjust Maximum execution time of each script: max_execution_time = 300 Restart Apache Web server Step 3: Configure Apache Web server Ensure Apache web server is installed: sudo apt install apache2 After installing Apache, configure basic security by allowing Prod ServerTokens only. sudo vim /etc/apache2/conf-enabled/security.conf Change line 25 ServerTokens Prod This directive configures what you return as the Server HTTP response. Valid options are Full | OS | Minimal | Minor | Major | Prod. Set ServerName: $ sudo vim /etc/apache2/apache2.conf ServerName cacti.example.com Set Server Admin to receive an email in case of issues. $ sudo vim /etc/apache2/apache2.conf ServerAdmin [email protected] If you have ufw enabled, open http and https ports on the firewall. $ sudo ufw allow http Rule added Rule added (v6 $ sudo ufw allow https Rule added Rule added (v6) You need to restart apache web service after making these changes: sudo systemctl restart apache2 Step 4: Install and Configure MariaDB Database Run the following commands to install MariaDB server on Ubuntu:s sudo apt install mariadb-server -y Tune MariaDB database for Cacti Add the following settings under [mysqld]: $ sudo vim /etc/mysql/mariadb.conf.d/50-server.cnf [mysqld] innodb_file_format=Barracuda innodb_large_prefix=1 collation-server=utf8mb4_unicode_ci character-set-server=utf8mb4 innodb_doublewrite=OFF max_heap_table_size=128M tmp_table_size=128M join_buffer_size=128M innodb_buffer_pool_size=1G innodb_flush_log_at_timeout=3 innodb_read_io_threads=32 innodb_write_io_threads=16 innodb_io_capacity=5000 innodb_io_capacity_max=10000
innodb_buffer_pool_instances=9 Comment out other settings on local #around line 116 #character-set-server = utf8mb4 #collation-server = utf8mb4_general_ci Restart mariadb service sudo systemctl restart mariadb To check any of these settings, use mysql select statement, e.g. $ sudo mysql -u root MariaDB [(none)]> select @@tmp_table_size; +------------------+ | @@tmp_table_size | +------------------+ | 134217728 | +------------------+ 1 row in set (0.00 sec) MariaDB [(none)]> exit Bye Or MariaDB [(none)]> show variables like 'join_buffer_size'; Once Database server installation is done, you need to create a database for Cacti: $ sudo mysql -u root -p CREATE DATABASE cacti DEFAULT CHARACTER SET utf8 COLLATE utf8_unicode_ci ; GRANT ALL PRIVILEGES ON cacti.* TO 'cacti_user'@'localhost' IDENTIFIED BY 'strongpassword'; GRANT SELECT ON mysql.time_zone_name TO cacti_user@localhost; ALTER DATABASE cacti CHARACTER SET utf8mb4 COLLATE utf8mb4_unicode_ci; FLUSH PRIVILEGES; EXIT; Test database connection: $ mysql -u cacti_user -p Enter password: strongpassword MariaDB [(none)]> show databases; +--------------------+ | Database | +--------------------+ | cacti | | information_schema | +--------------------+ 2 rows in set (0.00 sec) MariaDB [(none)]> \q Setup mysql timezone for cacti database user $ sudo su - $ mysql_tzinfo_to_sql /usr/share/zoneinfo | mysql -u root -p mysql Enter password: Warning: Unable to load '/usr/share/zoneinfo/leap-seconds.list' as time zone. Skipping it. Step 5: Install SNMP and Cacti on Ubuntu 20.04/18.04 The last package installation step is for Cacti and snmp packages. Cacti depend on Snmp and rrdtool tool for its functions. Install these packages using the command: sudo apt install snmp snmpd snmp-mibs-downloader rrdtool When asked to select the web server, choose Apache. Clone Project from github: $ sudo apt install git $ git clone -b 1.2.x https://github.com/Cacti/cacti.git Cloning into 'cacti'... remote: Enumerating objects: 75698, done. remote: Counting objects: 100% (1608/1608), done. remote: Compressing objects: 100% (496/496), done. remote: Total 75698 (delta 1155), reused 1536 (delta 1105), pack-reused 74090 Receiving objects: 100% (75698/75698), 127.92 MiB | 7.02 MiB/s, done. Resolving deltas: 100% (56327/56327), done. Updating files: 100% (3621/3621), done. After cloning the Cacti repository, move the files into the /var/www/html directory: sudo mv cacti /var/www/html Let’s now pre-populate the database used by cacti: sudo mysql -u root cacti < /var/www/html/cacti/cacti.sql With the database populated we can go ahead and create the config.php file in /var/www/html/cacti/include: sudo mv /var/www/html/cacti/include/config.php.dist /var/www/html/cacti/include/config.php Modify Cacti configuration file and make sure to change the database settings as needed: $ sudo vim /var/www/html/cacti/include/config.php $database_type = 'mysql'; $database_default = 'cacti'; $database_hostname = 'localhost'; $database_username = 'cacti_user'; $database_password = 'strongpassword'; Step 6: Configure SNMP Start by enabling the loading of MIBs by commenting out the following line on /etc/snmp/snmp.conf sudo vim /etc/snmp/snmp.conf Change mibs : to # mibs : Configure SNMP community name by editing /etc/snmp/snmpd.conf sudo vim /etc/snmp/snmpd.conf Enable full access from localhost: rocommunity MyCacti localhost Disable public access by commenting below lines: rocommunity public default -V systemonly rocommunity6 public default -V systemonly To # rocommunity public default -V systemonly # rocommunity6 public default -V systemonly Restart snmpd service: sudo systemctl restart snmpd Validate snmp configurations using snmpwalk command line tool: $ sudo snmpwalk -v 2c -c MyCacti localhost system SNMPv2-MIB::sysDescr.0 = STRING: Linux ubuntu 5.4.0-73-generic #82-Ubuntu SMP Wed Apr 14 17:39:42 UTC 2021 x86_64 SNMPv2-MIB::sysObjectID.0 = OID: NET-SNMP-MIB::netSnmpAgentOIDs.10
DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (1964) 0:00:19.64 SNMPv2-MIB::sysContact.0 = STRING: Me SNMPv2-MIB::sysName.0 = STRING: ubuntu SNMPv2-MIB::sysLocation.0 = STRING: Sitting on the Dock of the Bay SNMPv2-MIB::sysServices.0 = INTEGER: 72 SNMPv2-MIB::sysORLastChange.0 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORID.1 = OID: SNMP-FRAMEWORK-MIB::snmpFrameworkMIBCompliance SNMPv2-MIB::sysORID.2 = OID: SNMP-MPD-MIB::snmpMPDCompliance SNMPv2-MIB::sysORID.3 = OID: SNMP-USER-BASED-SM-MIB::usmMIBCompliance SNMPv2-MIB::sysORID.4 = OID: SNMPv2-MIB::snmpMIB SNMPv2-MIB::sysORID.5 = OID: SNMP-VIEW-BASED-ACM-MIB::vacmBasicGroup SNMPv2-MIB::sysORID.6 = OID: TCP-MIB::tcpMIB SNMPv2-MIB::sysORID.7 = OID: IP-MIB::ip SNMPv2-MIB::sysORID.8 = OID: UDP-MIB::udpMIB SNMPv2-MIB::sysORID.9 = OID: SNMP-NOTIFICATION-MIB::snmpNotifyFullCompliance SNMPv2-MIB::sysORID.10 = OID: NOTIFICATION-LOG-MIB::notificationLogMIB SNMPv2-MIB::sysORDescr.1 = STRING: The SNMP Management Architecture MIB. SNMPv2-MIB::sysORDescr.2 = STRING: The MIB for Message Processing and Dispatching. SNMPv2-MIB::sysORDescr.3 = STRING: The management information definitions for the SNMP User-based Security Model. SNMPv2-MIB::sysORDescr.4 = STRING: The MIB module for SNMPv2 entities SNMPv2-MIB::sysORDescr.5 = STRING: View-based Access Control Model for SNMP. SNMPv2-MIB::sysORDescr.6 = STRING: The MIB module for managing TCP implementations SNMPv2-MIB::sysORDescr.7 = STRING: The MIB module for managing IP and ICMP implementations SNMPv2-MIB::sysORDescr.8 = STRING: The MIB module for managing UDP implementations SNMPv2-MIB::sysORDescr.9 = STRING: The MIB modules for managing SNMP Notification, plus filtering. SNMPv2-MIB::sysORDescr.10 = STRING: The MIB module for logging SNMP Notifications. SNMPv2-MIB::sysORUpTime.1 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORUpTime.2 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORUpTime.3 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORUpTime.4 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORUpTime.5 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORUpTime.6 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORUpTime.7 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORUpTime.8 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORUpTime.9 = Timeticks: (6) 0:00:00.06 SNMPv2-MIB::sysORUpTime.10 = Timeticks: (6) 0:00:00.06 Remember to replace MyCacti with the name of your community string. Step 7: Configure Cacti Server on Ubuntu 20.04/18.04 Set Cacti directory permissions: sudo chown -R www-data:www-data /var/www/html/cacti Create systemd unit file for Cacti: sudo tee /etc/systemd/system/cactid.service + (Add device) Fill server details and scroll down and click “Save” button. Step 10: Using Cacti Spine Poller The spine is a multi-thread, high-speed data collection tool that acts as a replacement for cmd.php for Cacti. You can install and use it by following the guide in the link below: How To Install Cacti Spine poller on Ubuntu
0 notes
Text
Mp3 gain linux mint

#MP3 GAIN LINUX MINT INSTALL#
#MP3 GAIN LINUX MINT UPDATE#
#MP3 GAIN LINUX MINT UPGRADE#
#MP3 GAIN LINUX MINT CODE#
OpenSUSE 15.3 - The Xfce desktop and application menu I also tried out the live desktop media with Xfce for the same architecture.
#MP3 GAIN LINUX MINT INSTALL#
For the purposes of this trial I installed openSUSE using the full install 4.4GB ISO for x86_64 machines. These range in size from about 600MB up to about 950MB. There are also live desktop editions of the distribution which are available in GNOME, KDE Plasma, Xfce, and Rescue flavours. The full install images are about 4.4GB in size while the network installers tend to be about 150MB in size. openSUSE's installation media is available in both net-install and off-line installer flavours for x86_64, AArch64, IBM Z, and PowerPC systems. There are several editions of openSUSE, built for multiple hardware architectures.
#MP3 GAIN LINUX MINT UPGRADE#
Due to the upgrade path, it is highly recommended to upgrade to Leap 15.2 before upgrading to Leap 15.3. Users upgrading to openSUSE Leap 15.3 need to be aware that upgrading directly from versions before openSUSE Leap 15.2 is not recommended. People upgrading from previous versions should first upgrade to 15.2 as upgrading from earlier releases isn't supported. OpenSUSE 15.3 offers 18 months of security updates and support. The Xfce desktop though received a major update, moving from version 4.14 to 4.16 which introduces a number of improvements. The KDE Plasma desktop is still shipping version 5.18 and GNOME remains at version 3.34. For the most part major packages have stayed at the same versions they were earlier in the 15.x series. Most of these focus on containers and small improvements to development tools. There are a few other new features and upgrades.
#MP3 GAIN LINUX MINT CODE#
openSUSE Leap 15.3 is built not just from SUSE Linux Enterprise source code like in previous versions, but built with the exact same binary packages, which strengthens the flow between Leap and SLE. There is one huge change from the previous Leap versions.
#MP3 GAIN LINUX MINT UPDATE#
For the most part, openSUSE 15.3 is a minor update to the 15.x series which brings the community-focused, freely available openSUSE distribution closer in its technology to the business-oriented SUSE Linux Enterprise (SLE). OpenSUSE Leap 15.3 is the latest release in the distribution's series of stable versions. Listen to the Podcast edition of this week's DistroWatch Weekly in OGG (18MB) and MP3 (13MB) formats.
Opinion poll: Writing an ISO/IMG file to a thumb drive.
Torrent corner: 4MLinux, Arch, CentOS, Clonezilla, Kali, Lakka, NixOS, MakuluLinux, openSUSE, OviOS, Rescuezilla, Septor, Tails.
Released last week: CentOS, openSUSE 15.3, Kali 2021.2.
Questions and answers: Writing an ISO directly from the web to a thumb drive.
News: Nemo gets new search capabilities, Rocky publishes status update and seeks volunteers, tips for protecting against out of memory termination.
We wish you all a wonderful week and happy reading! Plus we are pleased to share the releases of the past week and list the torrents we are seeding. What tools do you use to write ISO and IMG files to a thumb drive? Let us know in the Opinion Poll. Our Questions and Answers column this week discusses writing downloaded files directly to removable media when local hard drive storage is not available. We also share tips on counter-acting an operating system's out of memory (OOM) process when a memory-heavy program needs to be protected. Then, in our News section, we report on the Linux Mint team adding new search functions to the Nemo file manager along with the Rocky Linux project looking for volunteers to help round out the young distribution. We begin this week with a look at openSUSE Leap 15.3 and some of its key features. The project published a new version last week which introduces binary compatibility with its commercial sibling SUSE Linux Enterprise. OpenSUSE is the community branch of the SUSE family. Welcome to this year's 22nd issue of DistroWatch Weekly!

0 notes
Text
Raid monitor linux

#Raid monitor linux update#
#Raid monitor linux software#
#Raid monitor linux free#
It can be used to change the active size of components or to change the number of active devices in linear and RAID 0/1/4/5/6. They never have any missing, spare, or failed drive so this option is mostly used in RAID1,4,5,6,10 or multipath array. RAID0 or Linear does not have anything to monitor. No check is performed to validate the request. Must be used with a complete understanding of it as the mdadm command in build mode cannot distinguish between initial creation and assembly of the array. It is used to create a new array with pre-defined superblocks.Īssembles the components obtained by the previously created array into an active array.īuilds an array that does not hold a pre-defined superblock. Some of the important ones are listed below: Command There are several modes in which mdadm command can be used. Mdadm command can be used in the below way: The main purpose of mdadm command is to combine one or more physical disk drive components into one or more logical units. combination of one or more devices into a single large network.
Mdadm: Multiple Disk and Device Management.Ĭurrently, Linux supports linear md device network i.e.
#Raid monitor linux software#
Web development, programming languages, Software testing & others
#Raid monitor linux free#
You can then submit a rating below the article.Start Your Free Software Development Course To leave feedback, log in to your IONOS account by clicking on the login button at the top right. Your feedback helps us to further improve our services. Errors will also be reported in the system log file./mdadm -monitor -syslog -delay=300 /dev/md0 -daemonise Did this article help you? If an event occurs, an email will be sent to the address specified in /etc/nf. In this example, the option -daemonise runs the monitoring program continuously in the background, checking the array every 300 seconds. By adding an email address to the /etc/nf file, error messages will be sent to the address if there is a disk failure. The mdadm utility can also be run as a demon.
#Raid monitor linux update#
If there is a missing disk, the output is similar to the following: mdadm -D /dev/md0 /dev/md0: Version : 00.90.00 Creation Time : Thu Aug 21 12:22:43 2003 Raid Level : raid1 Array Size : 102208 (99.81 MiB 104.66 MB) Device Size : 102208 (99.81 MiB 104.66 MB) Raid Devices : 2 Total Devices : 1 Preferred Minor : 0 Persistence : Superblock is persistent Update Time : Fri Oct 15 06:25:45 2004 State : dirty, no-errors Active Devices : 1 Working Devices : 1 Failed Devices : 0 Spare Devices : 0 Number Major Minor RaidDevice State 0 0 0 0 faulty removed 1 3 1 1 active sync /dev/sda1 UUID : f9401842:995dc86c:b4102b57:f2996278 Monitor RAID mdadm -D /dev/md1 /dev/md1: Version : 0.90 Creation Time : Tue Sep 11 21:33:24 2012 Raid Level : raid1 Array Size : 4194240 (4.00 GiB 4.29 GB) Used Dev Size : 4194240 (4.00 GiB 4.29 GB) Raid Devices : 2 Total Devices : 2 Preferred Minor : 1 Persistence : Superblock is persistent Update Time : Wed Jun 10 11:11:05 2015 State : clean Active Devices : 2 Working Devices : 2 Failed Devices : 0 Spare Devices : 0 UUID : 2db35cef:bde058e8:1f51fb89:78ee93fe Events : 0.251 Number Major Minor RaidDevice State 0 8 1 0 active sync /dev/sda1 1 8 17 1 active sync /dev/sdb1 The command mdadm -D /dev/md1 provides detailed information about the md1 array.Īn example of the output for a working RAID array is below. With only one disk up for each array, you can see that something is wrong here. If a disk is down (not functioning), the output looks similar to the following: cat /proc/mdstat Personalities : read_ahead 1024 sectors md0 : active raid1 sda1 102208 blocks md2 : active raid1 sda3 262016 blocks md1 : active raid1 sda2 119684160 blocks unused devices: A U means that the respective device is up, or functional. On the second line for each device, the state of each partition is shown within square brackets at the end. The example shows three RAID arrays (md0, md1, md2). The following commands are exemplary and must be adapted accordingly!īelow is an example of the output if both disks are present and correctly mounted: cat /proc/mdstat Personalities : read_ahead 1024 sectors md2 : active raid1 sda3 sdb3 262016 blocks md1 : active raid1 sda2 sdb2 119684160 blocks md0 : active raid1 sda1 sdb1 102208 blocks unused devices: You can check the status of a software RAID array with the command cat /proc/mdstat.

0 notes
Text
Microsoft office for mac 2019 compared with windows

#Microsoft office for mac 2019 compared with windows download#
#Microsoft office for mac 2019 compared with windows windows#
#Microsoft office for mac 2019 compared with windows windows#
Version LibreOffice 5.4 still supported Windows XP SP3, Vista. Windows and macOS versions have some document format compatibility problems, somewhat different feature sets and differences in the user interface macOS version does not include the database application MS Access, does not include MS Publisher, and also lacks a number of other features (see below).įeature inconsistencies/differences in Windows versions, between "MS Office 2021" sales version and the "Office 365" rental version: some features are being subsequently included only in the rental version (newly added features also differ between macOS and MS Windows) leading to inconsistencies in the feature set (see below). Integrated office architecture: LibreOffice for the desktop shares the same processing engine, common to all modules, on all form factors (incl. Windows, macOS, Linux, FreeBSD, NetBSD, OpenBSD, and Haiku. Microsoft Office Major Feature Differences Microsoft PowerPoint for the webĭesktop office: Notebooks, Desktop computers Desktop Office suite, general features: LibreOffice vs. 3.4 Online Presentation software: LibreOffice Online Impress vs.3.3 Online Spreadsheet applications: LibreOffice Online Calc vs.3.2 Online Word processors: LibreOffice Online Writer vs.3.1 Online Office suite, general features: LibreOffice Online vs.3 Online office: Web browser (and Chromebooks).2.4 Mobile Presentation software: LibreOffice Impress vs.2.3 Mobile Spreadsheet applications: LibreOffice Calc vs.2.2 Mobile Word processors: LibreOffice Writer vs.2.1 Mobile Office suite, general features: LibreOffice vs.1.6 Most important extensions for desktop LibreOffice.1.5 Desktop Database program: LibreOffice Base vs.1.4 Desktop Presentation software: LibreOffice Impress vs.1.3 Desktop Spreadsheet applications: LibreOffice Calc vs.1.2 Desktop Word processors: LibreOffice Writer vs.1.1 Desktop Office suite, general features: LibreOffice vs.1 Desktop office: Notebooks, Desktop computers.It is a compilation by users and not an official document by the Document Foundation. The feature comparison table is continuously being updated and is work in progress.
#Microsoft office for mac 2019 compared with windows download#
This section also includes the LibreOffice-based Chromebook App (Collabora Office download ) for reasons explained in the section. Online (web browser-based office): LibreOffice-based Collabora Online 22.05 ( ) vs.Mobile (smartphones, tablets): LibreOffice-based mobile solutions ( download) vs.Desktop (notebooks, desktop computers): LibreOffice 7.4.0 ( download) vs.There are separate comparison tables available for: The comparison highlights differences and therefore does not display any features which are present in both office suites. The comparisons separate major and minor feature differences and also includes notes on LibreOffice extensions. This page compares the features of LibreOffice and Microsoft Office in several form factors.

0 notes
Text
Gnucash merge accounts

#Gnucash merge accounts code
#Gnucash merge accounts series
#Gnucash merge accounts windows
#Gnucash merge accounts series
For example,īefore the next major release we (will) have a series 4.9xx, leading up to the 2.6.0 release we had a release series 2.5.x. When we get close to releasing a new stable series culminating the development on the master branch we make a new branch unstable from it and make releases with an odd minor number.
#Gnucash merge accounts code
Developers are encouraged to merge upwards immediately after making a big change so that they can handle the merge conflicts with the new code fresh in their minds. Merges are done at least at every release but generally more often as it's much easier to manage merge conflicts when there are fewer commits. When unstable exists "upwards merging happens in three stages instead: maint is merged into unstable and unstable into master. Branches are periodically merged "upwards", meaning that maint is merged into master. Think of maint as "lower", unstable as "intermediate" and master as "higher". Gnucash uses a variation of the Git Flow process for managing changes.
#Gnucash merge accounts windows
gnucash-on-windows: windows installer and build script moved here from gnucash/packaging.
gnucash-on-osx: Gtk-OSX moduleset, gtk-mac-bundler bundles, and ancillary files for creating GnuCash OSX Application Bundle.
gnucash-htdocs: Webserver, if you cloned/forked it before 2013-01 see Htdocs Split,.
They host since 2014-02 all GnuCash repositories: These are updated from the primary repository by commit hooks, so barring technical problems changes appear in these repositories within a few seconds of being committed to the primary. Our public repositories are mirrored on GitHub: for code, documentation and for the website. GitHub is a web-based Git repository hosting service. Access to this repository is limited to core developers who have been given ssh keys contributors without commit permissions will not access this repository directly. To set it up, you need to connect it with one or more servers, which host the remote repositories and clone that onto your local computer or fork it into your personal github repository.Ĭ is the server that hosts the canonical git repository, this wiki, Mailing Lists, IRC logs, the nightly builds of the documentation and API docs (via Doxygen) for both branches, and automated win32 builds. While you enter most commands you are working on your local repository.
3.2.2.1.2 Under Windows with Putty for TortoiseGit.
3.2.2.1.1 Under Linux or under Windows with MSYS.
2.3.2.1 One local repository and multiple working directories.

0 notes
Text
Sublime text editor

SUBLIME TEXT EDITOR FOR MAC
SUBLIME TEXT EDITOR FULL
If you'd prefer however, it is possible to keep things separate. It will pickup your session and configuration automatically. Sublime Text 4 is fully compatible with version 3. The API has been significantly expanded,Īdding features that allow plugins like LSP to work better Keeping backwards compatibility with packages built for The Sublime Text API has been updated to Python 3.8, while The way up to 8K resolutions, all while using less power thanĪ single frame being rendered. Sublime Text can now utilize your GPU on Linux, Mac and Windows Memory usage has been reduced, and load times are faster than Multi-line constructs, lazy embeds and syntax inheritance. With new features like handling non-deterministic grammars, The syntax highlighting engine has been significantly improved, Syntax-based features of Sublime Text within the modern Support for one of the most popular new programming languages SuggestionsĪre also augmented with info about their kind, and provide The auto complete engine has been rewritten to provide smartĬompletions based on existing code in a project. Windows and Linux now features custom title bars. The Default and Adaptive themes have been refreshed with new Linux ARM64 builds are also available for
SUBLIME TEXT EDITOR FOR MAC
Sublime Text for Mac now includes native support for Apple Navigation easier and more intuitive than ever. The side bar, tab bar, Goto Anything, Goto Definition, autoĬomplete and more have all been tweaked to make code With support throughout the interface and built-in commands. Tab Multi-Selectįile tabs have been enhanced to make split views effortless, These are the same license terms we use for Sublime Merge, and they allow us to deliver more frequent and exciting updates as soon as they're ready, without having to roll them into a new major version.
SUBLIME TEXT EDITOR FULL
After that, you will still have full access to every version of Sublime Text released within the 3 year window, but newer builds will required a license upgrade. Sublime Text license keys are no longer tied to a single major version, instead they are now valid for all updates within 3 years of purchase. There are some new major features that we hope will significantly improve your workflow and a countless number of minor improvements across the board.Ī huge thanks goes out to all the beta testers on discord and all the contributors to our packages. The first stable release of Sublime Text 4 has finally arrived! We've worked hard on providing improvements without losing focus on what makes Sublime Text great.

0 notes
Text
Apple mac operating system history

#APPLE MAC OPERATING SYSTEM HISTORY MAC OS X#
#APPLE MAC OPERATING SYSTEM HISTORY UPDATE#
#APPLE MAC OPERATING SYSTEM HISTORY WINDOWS 10#
#APPLE MAC OPERATING SYSTEM HISTORY FREE#
Ziebell (for providing some size values on very-old minor updates), and to Benton Quest (for providing size info on all the major releases up through Snow Leopard). Releases by version numberĪ special 'thank you!' goes to Mr.
#APPLE MAC OPERATING SYSTEM HISTORY FREE#
Feel free to contact me if you can help replace any of the '?' entries. The '?' entry for Size on a given release indicates I was unable to find the size.
#APPLE MAC OPERATING SYSTEM HISTORY UPDATE#
The largest (non-combo, non-main OS release) update was 10.15.1 at 5.3GB.
The smallest update was 10.3.1, at only 1.5MB.
#APPLE MAC OPERATING SYSTEM HISTORY MAC OS X#
(Tecnically, it's actually the 192 day interval between the Mac OS X Public Beta and version 10.0, but I'm counting from the official 10.0 release.)
The longest time period between any two minor releases is 165 days, which was how long we waited for the 10.4.9 update.
The shortest time period between any two releases is six days, which is how quickly the 10.15.5 Supplemental Update 1 came out after the 10.15.5 release.
So on average, we've seen some sort of update every 53.0 days.
As of September 23rd, 2020 (macOS 10.15.7's release date), it's been 7,315 days since the Public Beta was released.
This version was only for the then-new PowerMac G5 and the flat panel iMac G4, and was never generally released. This figure includes the one odd macOS X release: 10.2.7.
Starting with the Public Beta and up through macOS 10.15.7, there have been 138 macOS releases, both major and minor.
Some random notes, updated from the original post: This has happened a few times over the years. This is to keep the version numbers in the proper order, even when an older OS received an update after a major new release came out. Some entries may appear out of chronological order (i.e. Note: The Days column reflects the number of days between releases. Ⓘ Leopard - First universal binary release Ⓘ Snow Leopard - First Intel-only release Ⓘ Lion - App Store only (USB stick later) If you know for certain that something is incorrect, please let me know and I'll get it fixed. The following was culled from Apple's support downloads page, and as such, some of the dates may be off just a bit. Note: Click the ⓘ symbol to read Apple's release notes for a given update. The operating system was later released on July 20, 2011.īelow the break is a table showing all major releases of macOS (previously Mac OS X) from the public beta through the latest public version, which is macOS 10.15.7, as of September 23rd, 2020-the 138th release in total. The operating system was later released on July 20, 2011.
Apple introduced macOS X 10.7, code-named Lion, at the 'Back to the Mac' event on October 20, 2010.
Version 10.1: 'Puma' Due to many problems and complaints about Cheetah, Apple directly got to work on releasing Puma, the next big cat in Mac OS X.
Luckily this operating system version only stayed on the market up until September when it was moved up to a 'higher level'.
The modern Mac, like other personal computers, is capable of running alternative operating systems such as Linux, FreeBSD, and, in the case of Intel-based. Apple also develops the operating system for the Mac, currently Mac OS X version 10.6 'Snow Leopard'. Originally published on November 14th, 2005.Īpple exclusively produces Mac hardware, choosing internal systems, designs, and prices. Updated and republished for macOS 10.15.7 skip it unless you really really care about all the macOS releases.
#APPLE MAC OPERATING SYSTEM HISTORY WINDOWS 10#
Apple Mac Os Version History Windows 10.

1 note
·
View note