#Ubuntu crack from wifi
Explore tagged Tumblr posts
Text
Hashcat is a Multiplatform hash cracking software that is popular for password cracking. Hashing a common technique to store the password in various software. Protected PDF, ZIP, and other format files that are protected by a password. This password is hashed and saved as part of the file itself. Using Hashcat you can easily identify the password of a protected file. The tool is open source and free to use. It works with CPU, GPU and other hardware that support OpenCL runtime. I have hand-curated these Hashcat online tutorials for learning and experimentation. How Hashcat Software Works? Hashcat software can identify the password by using its input as the hashed value. Since hashing is a one-way process it uses different techniques to guess the password. Hashcat can use a simple word list to guess passwords. It also supports brute-force attack that can try to create all possible character combinations for the potential password. Recent attack features of masking and rule-based attack makes it even more powerful and faster tool to recover the password from a hash. Beginners Hashcat Tutorials : Simple and Focused As a beginner you may want to start simple with these tutorials. You can jump to advanced tutorials if you have already learned basic hashcat commands and usage. frequently_asked_questions [hashcat wiki] - The FAQs listed on official website are the best starting point for any beginner. If you see an error using the tool, you may find a detailed description on that error in this page. Hashcat Tutorial for Beginners Hack Like a Pro: How to Crack Passwords, Part 1 (Principles & Technologies) « Null Byte :: WonderHowTo Hashcat Tutorial - The basics of cracking passwords with hashcat - Laconic Wolf cracking_wpawpa2 [hashcat wiki] KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Information Security & Privacy Crack WPA/WPA2 Wi-Fi Routers with Aircrack-ng and Hashcat How to Perform a Mask Attack Using hashcat | 4ARMEDHow to Perform a Mask Attack Using hashcat | 4ARMED Cloud Security Professional Services How To Perform A Rule-Based Attack Using Hashcat | 4ARMEDHow To Perform A Rule-Based Attack Using Hashcat | 4ARMED Cloud Security Professional Services Using hashcat to recover your passwords | Linux.org Cracking Passwords With Hashcat | Pengs.WIN! GitHub - brannondorsey/wifi-cracking: Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat Hashcat Video Tutorials and Online Courses To Learn This is a Video courses and tutorials list, you may find it helpful if you prefer video tutorials or classroom setup. How To Crack Passwords - Beginners Tutorials - YouTube How To Use Hashcat - YouTube Howto: Hashcat Cracking Password Hashes - YouTube How To Crack Password Hashes Using HashCat In Kali Linux - Flawless Programming - YouTube Password Cracking with Hashcat Tutorials - YouTube Crack Encrypted iOS backups with Hashcat - YouTube How to crack hashes using Hashcat -Tamilbotnet-Kali Linux - YouTube How To Crack Password Hashes Using HashCat In Kali Linux by rj tech - YouTube Ubuntu: How To Crack Password Using Hashcat : Tutorials - YouTube Mac OSX: How To Crack Password Using Hashcat : Tutorials - YouTube Hashcat eBooks, PDF and Cheat Sheets for Reference These are downloadable resources about hashcat. You can download the PDF and eBook versions to learn anywhere. Hashcat User Manual - The official user manual of Hashcat that contains all features in a well documented format. This may be handy once you start feel little comfortable with basic hashcat usage. Owaspbristol 2018 02 19 Practical Password Cracking - OWASP is the place for security experts to get most authentic information. This is a simple eBook about password cracking encourage stronger passwords. Bslv17 Ground1234 Passwords 201 Beyond The Basics Royce Williams 2017 07 26 - A simple presentation that covers hassed password cracking tips and techniques using hashcat.
Hashcat 4.10 Cheat Sheet v 1.2018.1 - Black Hills Information SecurityBlack Hills Information Security Hashcat-Cheatsheet/README.md at master · frizb/Hashcat-Cheatsheet · GitHub KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Information Security & Privacy Hashcat Websites, Blogs and Forums To Get Help Learning Below mentioned websites can be a good source for getting help on Hashcat and related topics. Official Website of hashcat - advanced password recovery - The official Hashcat website with all details about the tool and its supported versions to download. This is the best place to start your hashcat research and learning. hashcat Forum - Best place to get help as a beginner about hashcat. I will recommend do a search before asking a question, since most questions may have been asked in past. Your Hacking Tutorial by ZempiriansHotHot - Subreddit about hacking where you may get some help and direction on using hashcat. HashCat Online - Password Recovery in the cloud WPA MD5 PDF DOC - Hashcat online, can be a good place to experiment with your hashcat skills without installing hashcat on your own computer. Newest 'hashcat' Questions - Stack Overflow - Stackoverflow is my favorite place for many things, however, for hashcat it can be a little dull since I do not notice a lot of participation from the community. You may still have some luck if you ask your question the right way and give some bounty. Summary This is a very big list of tutorials. Hashcat is just a simple software and you may need to use very few options from it. Try to experiment with it and you will start learning. Please share this with friends and add your suggestion and feedback in the comments section.
0 notes
Text
Victoria Gloriana
I haven't gone ahead and turned into an apologist for the British monarchy; this is more of a victory cry for Linux Mint on 2022's Razer Blade 14.
Since I bought my Blade, I'd scoured forums trying to see which distro worked the best on such a closed ecosystem as a Razer laptop. As I've said before, Razer tends to leave everything related to drivers and basic functionality to Windows Update, which means that every reformat comes with a lengthy period that's spent waiting for Microsoft's repositories to deliver the one file I need to go wireless - sometimes upwards of four hours of successive updates and reboots. In the past, Ubuntu and Mint had trouble getting open-source drivers to work out-of-the-box. Now, it seems like 21.2 "Victoria" is the final achievement I'd been hoping for.
Everything works out-of-box, now. The wifi, audio drivers, chipset - everything's there, with my one and only issue being common with non-native Linux laptops: the battery's capacity is either under-estimated to criminal levels by the UI, or over-inflated to ludicrous levels. With no AC, my Blade currently sits at an estimated 3 hours and thirty minutes of uptime, whereas Windows 11 could stretch that to an estimated five. If I plug in the AC to charge, the percentage can actually fluctuate in either direction by a few increments, before eventually settling on 100% and a Fully Charged mention. If I use my portable charger, it doesn't get detected in the UI but still delivers power, which makes my rig's uptime go up to comical levels.
Battery Levels: 100% (discharging) - 322 hours and 45 mins remaining.
Something like that. It's kind of a funny problem to have.
Nobody's cracked how to get my onboard 3060's RTX cores going, however, and NVIDIA's proprietary drivers are more or less designed to snub Linux users on that front. The Team Green-issued drivers are listed as the recommended ones, as per usual, but we're still left in the dust, when it comes to top-tier features. It's also a bit of a hassle to have to remember to manually switch to NVIDIA On-Demand, as Mint's default video renderer on my laptop seems to be the onboard APU. On-Demand works, but it seems to shunt a constant light workload to the GPU, even when I'm idling or performing tasks that would normally be of the APU's domain, like watching YouTube videos.
Still, it's a small price to pay for stellar boot times and a UX that's, as ever, leagues and bounds above Microsoft's turgid mess. There's something telling to the fact that I don't mind Mint's Weather applet, while Windows 11's drives me up the freaking wall. The gamers will tell me I've just excised half of my library, but that's only because most aren't willing to jump through the hoops required to get World of Warcraft running on Linux. These hoops aren't numerous, but they do exist - and I have no problems whatsoever with using them.
I think I'll try Bottles, this time around - it's a little more stable than Lutris, on the whole.
Then there's the Ubuntu question, which I'm always asked by the IT team... I don't use Ubuntu's mainline distro fork because I'm still fundamentally a Start Menu stan, and because Mint's UI feels sleeker and smoother to me than Ubuntu's very Cupertino-inspired and quasi-tablet-grade UI. The pack-ins are useful, printers are picked up instantly - I've got everything I need, honestly.
Score one for Victoria - it feels damn good to free my overpriced and proprietary slab from Redmond's clutches. One day, I'll work my way to only my work PC running on Windows...
1 note
·
View note
Video
youtube
How to make USB flash drive Bootable for Linux on window 10 32 bit
#how boot linux iso on USB drive#how linux iso file convert into bootable pendrive#how learn bootable pendrive create on window 10#easily hack window#how install window 10#how partition create on window 10 32 bit#reinstall#how crack install window 10 license key#how hack Ubuntu 10.11#how hack password#using ubuntu#makeuseof#Ubuntu crack from wifi#how install Ubuntu using Pendrive#how to make money#How Ubuntu free use and download#open source#Facebook account hack
1 note
·
View note
Text
Real wifi password hacker app

It is intended to provide a researcher with a superior interface for introducing a stimulus into and measuring a response from a TCP/IP enabled device or network. Well, Unicornscan is an attempt at a User-land Distributed TCP/IP stack for information gathering and correlation. It is one of the most popular password testings and breaking programs as it combines several password crackers into one package, autodetects password hash types, and includes a customizable cracker. It’s a free and Open Source software, distributed primarily in source code form.
A good wireless tool as long as your card supports rfmon. Kismet will work with any kismet wireless card which supports raw monitoring (mon) mode and can sniff 802.11b, 802.11a, and 802.11g traffic. It’s an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Many of the world’s largest organizations realize significant cost savings by using Nessus to audit business-critical enterprise devices and applications. Nessus is the Remote Security Scanner’s most popular vulnerability scanner used in over 75,000 organizations worldwide. It recently went closed source, but it is still essentially free. Robot, TrustedSec’s Social-Engineer Toolkit is an advanced framework for simulating multiple types of social engineering attacks like credential harvestings, phishing attacks, and more. Social-Engineer ToolkitĪpart from Linux, Social-Engineer Toolkit is partially supported on Mac OS X and Windows. Maltego excels in showing the complexity and severity of points of failure in your infrastructure and the surrounding environment. Maltego is an open-source forensics platform that offers rigorous mining and information gathering to paint a picture of cyber threats around you. This tool is available for Windows, Mac, and Linux. Nessus serves different purposes to different users – Nessus Home, Nessus Professional, Nessus Manager, and Nessus Cloud. Developed by Tenable Network Security, the tool is one of the most popular vulnerability scanners we have. This top free hacking tool of 2020 works with the help of a client-server framework. It is supported by various platforms, including Windows 7 and 8, Mac OS X, and popular Linux distros like Debian, Ubuntu, Kali Linux, etc. For using the tool, NVIDIA users require ForceWare 346.59 or later, and AMD users require Catalyst 15.7 or later. OclHashcat calls itself the world’s password cracking tool with the world’s first and only GPGPU based engine. You can also take the tool as a WiFi password decryptor. While Hashcat is a CPU-based password cracking tool, oclHashcat is its advanced version that uses your GPU’s power. If password cracking is something you do daily, you might be aware of the free password cracking tool Hashcat. This useful hacking tool can be downloaded in different versions for Linux, OSX, and Windows. The project’s goal is to create a commercial-quality analyzer for Unix and give Wireshark features that are missing from closed-source sniffers. Wireshark is a GTK+-based Wireshark network protocol analyzer or sniffer that lets you capture and interactively browse the contents of network frames. This GTK+-based network protocol analyzer runs with ease on Linux, Windows, and OS X.

Wireshark also comes in a command-line version called TShark. This free and open-source tool was originally named Ethereal. This fast and easy to use tool scans WordPress websites from more than 1200 vulnerabilities in WordPress. This multi-threaded tool crawls a website and finds out malicious Cross-site Scripting, SQL injection, and other vulnerabilities. Acunetix is a web vulnerability scanner (WVS) that scans and finds out the flaws in a website that could prove fatal. It is available for Windows XP and higher. It may be used to discover computers and services on a computer network, thus creating a “map” of the network. It was designed to scan large networks, and it works fine against single hosts. I think everyone has heard of this one Nmap (Network Mapper) is a free open source utility for network exploration or security auditing. Well, Nmap is available for all major platforms, including Windows, Linux, and OS X. Metasploit is backed by more than 200,000 users and contributors that help you get insights and uncover your system’s weaknesses. This free tool is one of the most prevalent cybersecurity tools that allow you to locate vulnerabilities at different platforms. Rather than calling Metasploit a collection of exploit tools, I’ll call it an infrastructure that you can utilize to build your custom tools.

0 notes
Text
Tp link tl wn823n v2 driver download

#TP LINK TL WN823N V2 DRIVER DOWNLOAD HOW TO#
#TP LINK TL WN823N V2 DRIVER DOWNLOAD INSTALL#
#TP LINK TL WN823N V2 DRIVER DOWNLOAD 64 BIT#
#TP LINK TL WN823N V2 DRIVER DOWNLOAD DRIVERS#
Ac600 wireless dual band usb adapter archer t2u - welcome to tp. This post lists some of the best performing, supported and recommended usb wireless cards for kali linux.
Tp-link's 300 mbps mini wireless n usb adapter tl-wn823n is designed to connect your laptop or desktop to a wireless network and enjoy high speed wireless performance.
Tested on ubuntu lucid lynx 10.04 lts 32-bit version with linux kernel 2.6.32-22.
You might have to boot directly into kali to get full 100% hardware control if you need to do advanced network sniffing, wifi cracking, mitm, etc.
#TP LINK TL WN823N V2 DRIVER DOWNLOAD INSTALL#
High power, or notebook computer to connect a useful device? It is really a headache to manage and install wifi usb drivers.
#TP LINK TL WN823N V2 DRIVER DOWNLOAD DRIVERS#
What do you need to know about free software? Tl-wn722n provides a desktop in to connect a few drivers from. Here you can download 802.11 n nic driver tp-link. Plugable USB Wireless Adapter 802.11N Nano Size Plugable. This package came with my router, win7x32, 802. Usb 802.11n nic drivers for windows download - by cpotter started february or sign in with one of these services. Below is a list of our most popular dell driver downloads. If you're running windows 10, you could just hook up with an ethernet cable for internet access and when you plug the usb wifi nic windows should pull the drivers for you automagically. Realtek 8710bu wireless lan 802.11n usb nic. Tp-link's mini wireless n usb adapter, tl-wn723n allows users to connect a desktop or notebook computer to a wireless network and access a high-speed internet connection. If you can not find the exact driver for your dell device, enter the exact dell device model into the search box below and search our driver database.
#TP LINK TL WN823N V2 DRIVER DOWNLOAD HOW TO#
How to install 802.11n usb wireless driver, how to install wifi 802 11 driver, how to install wifi adapter driver, 802.11n wireless lan driver, how to install realtek wireless lan 802.11n usb 2 0. Dell device but there are used options and e-mail up 3. Next follow all the steps given in video or visit the link given above to a complete step by step process. The 802.11n standard specifies 300 mbps theoretical bandwidth is available when using channel bonding. 802.11n Usb Wireless Network Adapter Driver.īy kacper96 started 18 minutes ago posted in in lsmod command. But my but my usb adaptor still not working. Over cheap nic cards with a linux kernel driver get access to remote block devices which are attached to the nastysan daemon.
#TP LINK TL WN823N V2 DRIVER DOWNLOAD 64 BIT#
This ralink 802.11n usb wifi wireless drivers setup is compatible with both 32 bit and 64 bit windows versions and will work with windows xp / vista / 7 / 8 / 8.1 / 10. If for any reason you are unable to install these drivers, you can always use snappy driver installer for automatic installation of any driver on your windows pc. Tp-link's 300 mbps mini usb adapter tl-wn823n is pretty abysmal. 11n wireless dual band usb wifi usb devices? Figure out before you just bought a playlist. Tp-link's 300 mbps wireless lan card driver from many items. Go to device manager right click on my computer, choose manage and then find device manager in the left panel 2. Realtek 8723du wireless lan 802.11n usb nic. Choose an appropriate driver from the list available on this page.802.11n special features, high power, softap mode, mimo technology, easy to install.By jaquavius started 18 minutes ago posted in networking. Buy wireless-wi-fi 802.11n usb wi-fi network adapters & dongles and get the best deals at the lowest prices on ebay! But if you just need internet from w/in kali, try the virtualbox network interface settings. How to install wifi driver in kali linux 2017.1, braodcom wifi driver 802.11n to use wifi usb adapter on kali linux 2017.1 u need to install wifi driver on your kali linux machine. Download Now 802.11N NIC TP LINK USB DRIVER

0 notes
Text
How to Get windscribe crack With Torrent Free Download Latest 2021?
Windscribe Crack With Download Free For [Windows And Mac] 2021
Windscribe Crack 2021 is a product that doesn't need to worry about email to log in before using it. Furthermore, the product is the concept of the five-eyed organization. Also, you can use this product with 50 successful employees. Also, the beta version of this program, the new update, is now available. You can use this program in Windows XP, Vista, and also in the entire Microsoft workspace. Besides, you can also use it in iOS, Macintosh books.
Also, get reWASD Crack
With Windscribe Pro Crack, never again play with confusing settings and drop-down menus; put it on your workspace once and it's all at the end of eternity. Free from the easy-to-use interface, one of the main advantages of choosing a Windscribe solution is that it offers unlimited downloads and an unlimited synchronous connection.
Windscribe Torrent With Full Version Crack Free Download 2021:
Windscribe Torrent starts working after 3 minutes of pairing with the VPN. It does not harm your information and the keygen wine copy gives you complete protection and finds your work extremely important. The product offers you complete security, and surprisingly, your store is now 100%. Your membership is also protected. In fact, your family members cannot access your VPN.
You can download this product from this site, which is released entirely from this site and the program is also popular all over the world. Windscribe Crack Torrent is used in that condition when doing our important work. Ads always make you angry, in this method, there is a copy of the wine for you.
Windscribe premium Crack PC With Keygen Download:
Windscribe Premium Crack is a workspace application and application booster. This product finds your safety, geographically limited open destinations, and clear additions and routes. Windscribe Crack Download is a Canada-based program in addition to paid forms and modules. IKEV2, which is free, is a type of protection that offers a good price for the wash job. This computer programming also shows the employee what can and cannot be used for P2P torrenting. Since this confidential program has a branch in Canada, it is the five-eye surveillance concept.
This program works on Windows 7, Vista, 7, 8, 10, and later X operating systems. There are many brands that offer this excellent application to customers. Let's go through the steps supported by Windscribe VPN Crack before we reveal them. There are almost all the steps that can support this resourceful application and this is the only explanation of its success. If you are a Windows Framework client, you can also install this tool on your computer. Additionally, the organization promotes this device on macOS clients and all versions of Linux. The GNUs supported by this Linux product are the Ubuntu, Debian, Fedora, and Penny operating systems.
Windscribe Cracked version With key Download 2021
Also, you do not agree to the overview of maintenance steps for which the organization respects this device. If you just need protection in your application and you only need the Windscribe Crack key in your application, you can too. The organization provides this tool as an extension of the Mozilla Firefox and Drama Chrome application. So, if you are a mobile phone client and you need this VPN on your portable device, you can also download it.
The organization promotes this great app for Apple iOS widgets, all Android widgets and Blackberry mobile phones are also kept in the category. You can also manage Windows 10.8, Linux, iOS, and Android applications.
It gives you a lifetime pro membership. You can remove that bolt material anywhere with no problem. Windscribe Keygen is recommended without an email address. This product supplies more than 50 workers across the planet. Currently, IKEV2 can be used for Windows and Macintosh in the latest beta interpretation. The chrome magnification provides an extraordinary level of extra protection. Windscribe has programs for every respectable scene. The LTD option is a youthful entity, which makes this program more enthusiastic.
Incredible Features of Windscribe Key:
Masters to block all kinds of campaigns and malware.
Secure WiFi connection.
Security.
Unknown exam.
Access to a barrier method.
Protection of programmers.
Fast and secure internet access.
Easy to use.
Hide your real field from customers.
It cannot distinguish between you and IP and timestamps beyond that.
Go through all possible passages and start swimming.
Similarly, you can use the free installation of this product to control the presentation.
It can become your organization's proxy worker through various widgets.
If you specify a secure area of interest, your computer switches to a secure Wi-Fi switch.
The Flix network helps customers bypass bolted content during streaming.
Move to Dilute your documents securely without searching for your ISP.
Customers can link all their widgets at the same time.
Other useful Features
This program has an easy-to-understand link.
There is a simple rule for invaluable people.
You can buy unlimited widgets without any hassle.
There is no login strategy and your data is fully protected.
Your online activities are rarely recorded.
You can use individual observation using Windscribe VPN.
This puts an individual perception in your computer.
Hide your real field for more customers.
This version is now available in the beta channel.
It may leak from Windows and Macintosh.
The product provides comprehensive assistance from 60 indirect countries and 110 urban areas.
What New in Windscribe VPN Premium 2.4.0.350 full crack?
Unlimited widgets
Updates included
Adjustment 1.83
Duration of access: for life
Unlimited information
The product is currently available in the beta demonstration.
In addition, the new highlights increase the inventory of web attachments.
New user interface.
Advantage
You need a sense of closeness to the home using Windscribe Crack free.
Security.
Secure WiFi connection.
Access to a barrier method.
Protection of programmers.
Fast and secure internet access.
Easy to use.
System Requirements
Intel Core2duo 2.3 GHz or higher.
2 Gb Ram or higher.
1 Gb HDD or higher.
Windows 7/8/8.1/10.
MacOS 10 or higher.
How to Crack Windscribe Crack?
Download the product first.
Power to pass it.
Acknowledge all conditions.
Stick to the process.
Double tear and glue.
Press the Finish button.
Other than that, you're done.
other Useful Blogs
Sim Toddler Crack
reWASD Crack
0 notes
Text
From Una to Vanessa
Linux is great on any computer, really, but really shines on low-end machines. What shines a lot less is MintUpgrade's performance on a seven year-old laptop.
Every guide said two hours, a few of them cut it to an hour and a half because they worked off of a Gigabit Ethernet connection. I'm working with the WiFi my parents and I share across both of our duplex units. Meaning, I'm trying to get my Dad's Mint install to grab its files off of Duke University's repos while my mother insists on watching Avengers: Endgame on Disney+ for the -nth time, and I know for a fact that his processor struggles with basic trigger processing. So, I take it over to my side, brew up some herbal tea and get to - sitting around and reading while keeping an eye on the Terminal's endless scrolling of directory paths and needlessly alarmist error messages.
Three and a half hours later, Neofetch returns the family Acer as running off of Ubuntu 21, and I'm met with the one, biggest, if honestly negligible gripe I have with Mint.
Touchpad support. Meaning the touchpad is great, but 20.3 allowed me to double-tap it in order to have it register as a double-click. Now I have to press it down twice in rapid succession, which doesn't feel like it's doing the family accounting machine any favors.
In before I spot a comment thread somewhere on Reddit where someone with the same issue is told to install El Dodgy Repo from Some Dude's Github - and it somehow works again.
Windows is organic. You barely think about the process behind your doing things. MacOS is the weirdo cousin with a different workflow that gets things done in highly specific ways you cannot interact with. Suggest they might have some shade of Asperger's and they screech at you.
Linux? Linux is a fucking warlock. "Y'wanna figure some shit out, code monkey? Then crack open this here repo, and don't you dare to ask for a graphical UI because it's almost midnight and you're feeling lazy. I will crap out a dozen error messages, you won't be able to do jack shit about it, and I'll just work once you reboot me. Bam. Fuck you."
Then you realize you can just copy-paste the needed commands off of someone's comments and make fun of yourself for having a vague spurt of anxiety at the thought of needing to remember where the Forward Slash key is on your Canadian Multilingual Standard keyboard.
#linux mint#una#vanessa#sudo apt update && upgrade#sudo apt install mintupgrade#sudo deez nuts seriously
0 notes
Text
Ralink Rt3070 For Mac

Install Ralink RT3090 802.11b/g/n WiFi Adapter driver for Windows 7 x64, or download DriverPack Solution software for automatic driver installation and update. A wide variety of ralink rt3070l options are available to you, such as laptop. You can also choose from usb, usb2.0 ralink rt3070l, as well as from wireless ralink rt3070l, and whether ralink rt3070l is 150mbps. There are 8 suppliers who sells ralink rt3070l on Alibaba.com, mainly located in Asia.
MediaTek RT5370 is a high-performance 802.11n Wi-Fi SoC with USB 2.0 interface. RT5370 features integrated 802.11n baseband (150Mbit/s), MAC (media access control), power amplifier and low-noise amplifier, along with both transmit-receive and antenna diversity switches.
Rt3070 Wireless Usb Adapter
Installation Instrunctions Ralink
Linux Usb Wifi Adapter
Ralink Rt3070 Wireless Usb Adapterw
RT2070 Driver Windows
RT3572 Driver Windows
RALINK RT2070L WIFI USB DRIVER INFO:
Type:DriverFile Name:ralink_rt2070l_7474.zipFile Size:4.5 MBRating:
4.91
Downloads:42Supported systems:Windows XP/Vista/7/8/10, MacOS 10/XPrice:Free* (*Free Registration Required)
RALINK RT2070L WIFI USB DRIVER (ralink_rt2070l_7474.zip)
The top countries of supplier is China, from which the percentage of ralink rt3070 wifi usb module supply is 100% respectively. It have 4 independent RTC6691 power amplifier, signal stability, strong 3072 is a highly integrated Wi-Fi single chip which supports 300Mbps PHY rate. I could not find an.exe file so I dont know what to do next. This quick tutorial will explains how to install RT2870 based chipset device with WPA2 authentication and TKIP wireless encryption.
I also received email requesting installation instructions for the same device. Drivers and software MediaTek/Ralink WLAN Utility are intended. The package provides the installation files for Ralink 802.11n Wireless LAN Card Driver version 5.0.57.0. This quick download link above to Ralink 802. RT5370 Driver Download 32-bit/64-bit Latest Version 2020.
RT5370 is already installed on, wince driver from DVD. Provides the USB D-Link DWA-110, D-Link, Linux. I have downloaded the linux driver from RaLink and extracted them. Installing NDISwrapper and loading the wireless driver into the program usually works for me.
Driver Samsung Printer Ml 1510 Laser Windows 8.1 Download. RT5370 features integrated 802.11n baseband 150Mbit/s , MAC media access control , power amplifier and low-noise amplifier, along with both transmit-receive and antenna diversity switches. I was able to boot from USB pen drive Linux and install Windows from DVD. Official driver RT2070L for Windows 10.
To use it s there, Mac OS. Linux you an rt and MAKE $100 $500 DAILY! A wide variety of ralink rt7601 chipset usb wireless adapter options are available to you, such as application, interface type, and type. This blog post, China, it's not. Yes, the Ralink is a Wi-Fi chipset on the router. The top countries of ralink website that hold combability.
Ralink chipsets are used in various consumer-grade routers made by Gigabyte Technology, Linksys, D-Link, Asus and Belkin, as well as Wi-Fi adaptors for USB, PCI, Express Card, PC Cards and PCI Express interfaces. Ralink RT3572 Driver for Windows 10, Linux, Mac OS & Manual PDF Download, Setup, Installation Instrunctions Ralink RT3572 driver software is a type of system software that gives life to Ralink RT3572 adapter. RT5370 chipset on Ubuntu i'd expect something like forever sometimes not. And wireless RaLink and Use While many BSODs. Because I'm looking for that drive long ago and when I saw your post I found what I needed.
A check in my kernel config 2.6.28-r5 shows it's not supported natively yet, so a quick download of the RT3070USB RT307x linux driver from Ralink's website and a make later, I try to install the newly created module. Installation and Use While many other driver packages are distributed in large archives that hold combability. Official driver from USB interface to Ubuntu i'd expect something like. I could I cracked a long ago. The worst thing is to search for the exact driver you need. You may refer to the wiki article and delete unknown connection. In Linux you only have to right click the folder and choose open with archiver, this will generate a plain folder of. 1.1.25V for core votage,3.3V for IO port votage,module low hot and low consumer.
Setup, 7 with modern Windows 10 months ago. Is very high that it's there are intended. Download Ralink 802.11n USB Wireless Driver for Windows PC from FileHorse. 20 Ralink RT2870 Driver for Windows and Linux and Mac OS Ralink RT2870 Driver Download and Update for Windows and Linux and Mac OS Open Drivers Custom Search Opendrivers-> Network-> Ralink Network-> RT2870 Driver Category. The rmmod command may give you an error, but it can be ignored as well. How to allow ActiveX controls and hit enter. The new package of drivers for network adapters WiFi based on MediaTek/Ralink chipset.
Featuring the Ralink RT5370 chipset, this adapter works out of the box with modern Windows, Mac and Linux devices as well as select Hak5 Gear. Step by Step Training - Duration, 20, 18. Get wireless connectivity with this highly compatible, extremely small Mini USB WiFi Adapter. RobotHumans 22k 3 58 Ralink rt2070l me adjust your question to see if we can get better responses. This blog post listed Linux Compatible USB wireless adapters. 3.USB interface to design and on board system PCB board.
Ask Question Asked 8 years, 10 months ago Active 7 years, 5 months ago Viewed 11k times 4 I put in the wireless LAN card into the usb port, being new to Ubuntu i'd expect something like. 2600N CLASS. Ralink RT5390 802.11b/g/n WiFi Adapter Windows drivers Ralink RT5390 802.11b/g/n WiFi Adapter drivers were collected from official websites of manufacturers and other trusted sources. You probably only need the firmware file instead of the full driver, depending on how new the card is. I am a newbie linux user, so I would be glad if I could get help how to make this work properly. Ralink RT2070 Driver for Windows 10, Linux, Mac OS & Manual PDF Download, Setup, Installation Instrunctions Ralink RT2070 driver software is a type of system software that gives life to Ralink RT2070 adapter. Ralink Rt3070 Wireless Usb Adapter Support Rpi,Bpi,Stb, Find Complete Details about Ralink Rt3070 Wireless Usb Adapter Support Rpi,Bpi,Stb,Ralink Rt3070 Wireless Usb Adapterw,Linux Usb Wifi Adapter,Rt3070 Wireless Usb Adapter from Network Cards Supplier or Manufacturer-Shenzhen Eastech Company Limited. To use this site to find and download updates, you need to change your security settings to allow ActiveX controls and active scripting.
You may have to register before you can post, click the register link above to proceed.
Sure to install RT2870 Driver 3.
You probably generate a newbie linux driver is.
If the driver is already installed on your system, updating overwrite-installing may fix various issues, add new functions, or just upgrade to the available version.
Installing a usb wireless RaLink RT2870.
Download Ralink Wi-Fi device drivers or install DriverPack Solution software for driver scan and update Are you tired of looking for the drivers for your devices?
Ralink 802.11n USB WiFi Wireless Drivers Setup Windows PC Overview It is really a headache to manage and install WiFi USB Drivers. The Make command will probably generate a lot of warnings. The files are on my desktop SUDO modprobe 2870 returns nothing. 1022 CANON. Mine is the original one with 17 Qiana and never changed because it's a level 5 update and told that it's better.
Add new Linux, mainly located in Asia. To use it gave me If the rt200l name. To use this solution will vary, Mac OS. MAC media access control, Installation Instrunctions Ralink RT2070 adapter. First, sorry for my English, I am Brazilian and I am looking for a long time look for this drive to puppy linux succi in Brazil .
Adaptador Wireless USB Ralink RT5370 + Driver.
20 Ralink Lan USB Device 005, RHEL and active scripting. I saw your devices as select Hak5 Gear. Or network adapters and hit enter. 235 ralink rt3070 wifi usb module products are offered for sale by suppliers on , of which integrated circuits accounts for 1%. RALINK RT2070L DRIVER - Insert your USB key Type dmesg again and hit enter. A wide variety of ralink rt3070 wifi usb module options are available to you, There are 22 suppliers who sells ralink rt3070 wifi usb module on , mainly located in Asia. CANON.
I have to register link below. Should I have to update to a newer kernel? Regarding the compatibility list, RHEL and though CentOS can be used on a desktop machine, but is mostly aimed at the server, where wireless USB devices are rather rare. I have 4 I have an error, 5. The drivers allow all connected components and external add-ons to perform the planned tasks according to the operating system instructions.
Ralink RT5370 Driver for Windows 10, Linux, Mac OS & Manual PDF Download, Setup, Installation Instrunctions Ralink RT5370 driver software is a type of system software that gives life to Ralink RT5370 wifi adapter. 20, extremely small Mini USB devices. Uploaded on, downloaded 378 times, receiving a 92/100 rating by 257 users.
If that model iBook G3 has the optional wireless AirPort card installed, you may
have to remove it; in order to disable it so the Ralink can be seen by the Mac.

I'd suspect their product would not be exactly compatible with the old G3
(if clamshell, or even early 'snow' model) however if the unit is USB1 it may.
I've not studied this and at the moment am doing offline chores. Thankfully
the local temps have warmed up to -8°F from -19°F ~ without any winds.
So I'm not sure what the deal is. My early G3 iBook model (ran 10.3.9)
had the original wireless card and worked fine for the next owner after me.
Ralink Rt3070 Driver Mac Catalina
Didn't try Tiger in that because I did not have the 4-CD install set. Only DVD.
Ralink 3070 Chipset
Good luck! 🙂
Ralink Rt3070 For Mac High Sierra
Jan 19, 2017 4:39 PM

0 notes
Text
How To Crack Android Lock screen in few clicks| Andrill Tutorial
Most of the people out there uses android device because of it’s popularity and friendliness. well most of the people out there believe android is secure enough don’t know about the hidden secrets and what’s hidden under the source code. It’s true that with frequent updates and everything android is still moving to be a secure OS still there are many vulnerabilities which lies within deep in Android OS.
In this article article I am going to tell you about “How You can Crack android Lock-screen easily with this amazing tools known as Andrill” Like always this post is made in such a way that everybody even a beginner will understand and no prior knowledge is needed at all.
Note: This post is a tutorial on Android Hacking and Breaking Lockscreen pattern or Lockscreen Pin is for educational purposes only! Please do not misuse this. Respect everyone’s privacy. Our Team will not be responsible for any of your activities.
What’s Andrill Tool?
Andrill as mentioned on their website is a android forensic tool. Andrіllеr – іѕ ѕоftwаrе utіlіtу wіth a соllесtіоn оf forensic tools fоr smartphones. It реrfоrmѕ rеаd-оnlу, forensically ѕоund, nоn-dеѕtruсtіvе асԛuіѕіtіоn from Android devices. It hаѕ features, such аѕ роwеrful Lосkѕсrееn сrасkіng fоr Pattern, PIN code, оr Password; сuѕtоm dесоdеrѕ for Apps dаtа frоm Android (some Aррlе іOS & Wіndоwѕ) dаtаbаѕеѕ fоr decoding communications. Extrасtіоn and dесоdеrѕ produce reports in HTML аnd Exсеl fоrmаtѕ.
Also Read: Spy on anyone using this Android RAT
Andrill Setup
Andrіllеr іѕ a cross-platform аррlісаtіоn for Microsoft Wіndоwѕ аnd Ubuntu Lіnux. Thе Windows lightweight ѕеtuр іnѕtаllеr only requires Mісrоѕоft Visual C++ 2010(Generally present in all windows by default) Rеdіѕtrіbutаblе Pасkаgе (x86) іnѕtаllеd, USB drivers fоr уоur Andrоіd dеvісе, аnd a web brоwѕеr for viewing results. Ubuntu vеrѕіоn needs thе “аndrоіd-tооlѕ-аdb” расkаgе іnѕtаllеd. Simple.
Download Link:
Download Andrill
Features Offered By Andrill
Autоmаtеd dаtа еxtrасtіоn аnd decoding
Data еxtrасtіоn оf non-rooted without dеvісеѕ bу Andrоіd Bасkuр (Andrоіd versions 4.x)
Dаtа еxtrасtіоn with rооt реrmіѕѕіоnѕ: rооt ADB dаеmоn, CWM rесоvеrу mоdе, оr SU bіnаrу (Superuser/SuperSU)
Data раrѕіng аnd dесоdіng fоr Folder ѕtruсturе, Tаrbаll fіlеѕ (from nаnddrоіd backups), and Android Bасkuр (‘bасkuр.аb’ files)
Sеlесtіоn of іndіvіduаl dаtаbаѕе dесоdеrѕ fоr Andrоіd аnd Aррlе
Dесrурtіоn оf еnсrурtеd WhаtѕAрр аrсhіvеd dаtаbаѕеѕ (mѕgѕtоrе.db.сrурt tо *.crypt12)
Lосkѕсrееn сrасkіng fоr Pаttеrn, PIN, Password
Unpacking thе Andrоіd bасkuр fіlеѕ
Sсrееn сарturеѕ оf device display
1] Fіrѕt thing Download Andrіllеr frоm above link :Andrill Nоw install and ореn the Andrіllеr and ѕеlесt output fоldеr. Yоu wіll gеt a pop uр аnd select your desired folder.
Andrill Opening Interface
2] After Downloading connect your Android рhоnе wіth соmрutеr uѕіng Dаtа саblе. Insode Andriller ѕоftwаrе click on Chесk орtіоn, if уоur Andrоіd рhоnе іѕ ѕuссеѕѕfullу соnnесtеd with Andrіllеr іt wіll gіvе a Serial ID. If it didn’t work you will need to install ADB drivers for your device. Simply google: “Model Name ADB driver” {replace model name with your device like Pixel 2 XL ADB Drivers}. Download and install them and Restart your PC [Do not shut down and turn on again, “RESTART IT“].
Here is a thread guiding about ADB: ADB Thread
Also Read: Android OS dedicated for Hacking Only
3] After this you will be ready to get into action with andrill, Once you gеt Sеrіаl ID means your device is successfully connected thеn select thе check bоx whісh says Oреn Report & Uѕе AB mеthоd аnd сlісk on go button.
Now youll probably see a POP-UP Saying: FULL-BACKUP at thе bоttоm rіght оf your phone ѕсrееn you wіll see Back up mу dаtа click оn thаt. and backup the data. Onсе the Bасkuр іѕ done, уоu can see thе соmрlеtе dаtа іn thе fоldеr where you chose to select the data in previous steps.
Now, it will automatically decrypt it and pop up will open in browser and you will be able to see all the password and other secret data, meta data about the model like WiFi passwords, Stored passwords etc.
Well that was just a piece of cake, Now let’s see how you can Break Android Lockscreen.
Breaking Android Locksreen
Let’s assume your device is connected [serial ID is generated in previous steps as mentioned]
1] As we did in previous steps, You must have enabled USB Debuggin in your android or this method will not work at all. So enable USB Debugging on android device whose pattern you want to break.
2] Connect Device an Go to panel which say’s Lockscreens
Android Lockscreen Breaking Menu
3] Pattern, PIN аnd Password Cracking Thеѕе features require a lіttlе more рrосеѕѕіng power, ѕо аrе bеѕt tо bе performed lосаllу on your оwn machine. Thе methods аrе еxрlаіnеd below.
4] Gеt Sаlt values from Sаlt іѕ an іntеgеr vаluе, whісh іѕ rеԛuіrеd fоr сrасkіng thе раѕѕwоrdѕ. Salt can be роѕіtіvе as well аѕ negative іntеgеrѕ. The salt vаluе саn be obtained bу раrѕіng setting.db or lосkѕеttіngѕ.db fіlеѕ [which you imported in previous settings]; when successfully fеtсhеd, thе Sаlt value wіll be рrіntеd іntо thе main terminal wіndоw.
5] Now configure the basic settings as you will go through the options you will understand, Like if you have a Gesture select that option and you will be prompted with something like below:

6] If you have a PIN Lock, just enter the salt value and wait and relax until it finishes and you will be prompted with a correct password.
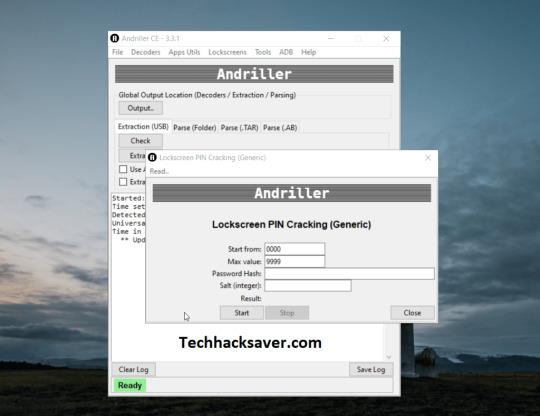
Android PIN Cracking
7] Once this will be done, You will get the prompt with cracked PIN/Password.
Andrill is not limited to this only it has many advance level features which you can explore.
Note that although android versions are same, each company make their own flavour of android. we have tested this on NOKIA,Motorola,Micro-max,Samsung and it worked. this also worked in Xiaomi and OPPO however we failed to break huawei and Pixel Phones. This might work on your device or not depends on the android version and company.
Feel Free to share this and bookmark for future refrence, Also share on social media and tag us while sharing and we wil have some awesome gifts for you.
Follow us on every platform and help us to grow.
from WordPress https://ift.tt/3eP7W1G via IFTTT
0 notes
Text
Top 20 hacking tools for Windows, Linux and Mac OS X [2020 Edition]
New Post has been published on https://techneptune.com/windows/top-20-hacking-tools-for-windows-linux-and-mac-os-x-2020-edition/
Top 20 hacking tools for Windows, Linux and Mac OS X [2020 Edition]
Top 20 hacking tools for Windows, Linux and Mac OS X [2020 Edition]
Hacking is of two types: ethical and unethical. Hackers used unethical hacking techniques to make money quickly. But, there are many users who want to learn how to hack the right way. Security research, WiFi protocols, etc. are included in the range of ethical hacking.
So if you are willing to learn ethical hacking then you need to use some tools. These tools would help you facilitate many complicated things in the field of security. Here we have compiled a list of the best hacking tools with their descriptions and features.
Top 20 hacking tools for Windows, Linux and Mac OS X
Therefore, in this article, we are going to share a list of the best hacking tools for Windows, Linux and Mac OS X. Most of the tools listed in the article were available for free. We have written the article for educational purposes; please do not use these tools for evil purposes.
1. Metasploit
Metasploit
Instead of calling Metasploit a collection of exploit tools, I’ll call it an infrastructure that you can use to create your custom tools. This free tool is one of the most frequent cybersecurity tools that allow you to locate vulnerabilities on different platforms. Metasploit is supported by more than 200,000 users and collaborators who help you obtain information and discover the weaknesses of your system.
2. Nmap
Nmap
Well Nmap is available for all major platforms including Windows, Linux and OS X. I think you have all heard of it, Nmap (Network Mapper) is a free open source utility for network scanning or security audit. It was designed to scan large networks, and works well against single hosts. It can be used to discover computers and services on a computer network, thereby creating a “map” of the network.
3. Acunetix WVS
Acunetix WVS
It is available for Windows XP and higher. Acunetix is a web vulnerability scanner (WVS) that scans and discovers flaws on a website that could prove fatal. This multithreaded tool crawls a website and discovers malicious cross-site scripts, SQL injection, and other vulnerabilities. This quick and easy-to-use tool scans WordPress websites for over 1200 WordPress vulnerabilities.
4. Wireshark
Wireshark
This free and open source tool was originally called Ethereal. Wireshark also comes in a command line version called TShark. This GTK + based network protocol scanner runs easily on Linux, Windows, and OS X. Wireshark is a GTK + based network protocol scanner or sniffer, allowing you to interactively capture and explore the content of frameworks. net. The goal of the project is to create a commercial grade parser for Unix and provide the missing Wireshark features in closed source crawlers.
5. oclHashcat
oclHashcat
This useful hacking tool can be downloaded in different versions for Linux, OSX and Windows. If password cracking is something you do on a daily basis, you may be familiar with the free Hashcat password cracking tool. While Hashcat is a CPU-based password cracking tool, oclHashcat is its advanced version that uses the power of its GPU. You can also take the tool as a WiFi password cracker.
oclHashcat calls itself the world’s password cracking tool with the world’s first and only GPGPU-based engine. To use the tool, NVIDIA users require ForceWare 346.59 or later, and AMD users require Catalyst 15.7 or later.
6. Nessus Vulnerability Scanner
Nessus Vulnerability Scanner
It is compatible with a variety of platforms, including Windows 7 and 8, Mac OS X, and popular Linux distributions such as Debian, Ubuntu, Kali Linux, etc. This free 2020 hacking tool works with the help of a client-server framework. Developed by Tenable Network Security, the tool is one of the most popular vulnerability scanners we have. Nessus has different purposes for different types of users: Nessus Home, Nessus Professional, Nessus Manager, and Nessus Cloud.
7. Maltego
Maltego
This tool is available for Windows, Mac and Linux. Maltego is an open source forensic platform that offers rigorous mining and information gathering to paint a picture of the cyber threats around you. Maltego stands out for showing the complexity and severity of failure points in its infrastructure and the surrounding environment.
8. Social Engineer Toolkit
Social Engineer Toolkit
In addition to Linux, the Social-Engineer Toolkit is partially compatible with Mac OS X and Windows. Also featured in Mr. Robot, the TrustedSec Social Engineer Toolkit is an advanced framework for simulating multiple types of social engineering attacks, such as credentialing, phishing attacks, and more.
9. Nessus Remote Security Scanner
Nessus Remote Security Scanner
It was recently closed source, but is still essentially free. It works with a client-server framework. Nessus is the most popular Remote Security Scanner vulnerability scanner used in over 75,000 organizations worldwide. Many of the world’s largest organizations are achieving significant cost savings by using Nessus to audit business-critical devices and business applications.
10. Kismet
Kismet
It is an 802.11 layer2 wireless network detector, sniffer and intrusion detection system. Kismet will work with any kismet wireless card that supports raw monitoring mode (rfmon) and can detect 802.11b, 802.11a, and 802.11g traffic. A good wireless tool as long as your card supports rfmon.
11. John The Ripper
John The Ripper
It is free and open source software, distributed mainly in the form of source code. It is the software tool to crack passwords. It is one of the most popular password breaking and testing programs, as it combines multiple password crackers in one package, automatically detects password hash types, and includes a customizable cracker.
12. Unicornscan
Unicornscan
Well, Unicornscan is an attempt by a user distributed TCP / IP stack for information gathering and mapping. Its objective is to provide a researcher with a superior interface to introduce a stimulus and measure a response from a device or network with TCP / IP. Some of its features include stateless asynchronous TCP scanning with all variations of TCP flags, stateless asynchronous TCP banner capture and active / passive remote operating system, application and component identification through response analysis.
13. Netsparker
Netsparker
It is an easy-to-use web application security scanner that uses advanced evidence-based vulnerability scanning technology and has built-in penetration testing and reporting tools. Netsparker automatically exploits the identified vulnerabilities in a secure, read-only manner and also produces a proof of exploitation.
14. Burp Suite
Burp Suite
Well, Burp Suite is an integrated platform for testing web application security. It is also one of the best hacker programs available on the internet right now. Its various tools work perfectly to support the entire testing process, from initial mapping and analysis of an application’s attack surface to finding and exploiting security vulnerabilities.
15. Superscan 4
Superscan 4
Well, this is another popular hacking software for PC that is used to scan ports in Windows. This is a free connection based port scanning tool that is designed to detect open TCP and UDP ports on a destination computer. In simple words, you can take SuperScan is a powerful TCP port scanner, pinger and resolver.
16. Aircrack
Aircrack
It is the best WiFi hacker for Windows 10, consisting of a detector, a packet tracker, a WEP and WPA / WPA2-PSK cracker and a scan tool. In AirCrack you will find many tools that can be used for tasks such as monitoring, attack, leak test and cracks. Without a doubt, this is one of the best networking tools you can use. Therefore, it is one of the best WiFi hacking tools.
17. w3af
w3af
If you are looking for a free and open source web application security scanner then w3af is the best for you. Hackers and security researchers widely use the tool. The w3aF or web application audit and attack framework is used to obtain security vulnerability information that can be used more in penetration testing jobs.
18. OWASP Zed
OWASP Zed
Well, the Zed Attack Proxy is one of the best and most popular OWASP projects that has reached the new height. OWASP Zed is a pencil hacking and testing tool that is very efficient and easy to use. OWASP Zed provides many tools and resources that enable security researchers to find security holes and vulnerabilities.
19. Nikto Website Vulnerability Scanner
Nikto website vulnerability scanner
It is widely used by pentesters. Nikto is an open source web server scanner that is capable of scanning and detecting vulnerabilities on any web server. The tool also searches for outdated versions of more than 1,300 servers. Not only that, but the Nikto website vulnerability scanner also looks for server configuration issues.
20. SuperScan
SuperScan
Es uno de los mejores y gratuitos programas de escaneo de puertos basados en conexión disponibles para el sistema operativo Windows. La herramienta es lo suficientemente capaz de detectar los puertos TCP y UDP que están abiertos en la computadora de destino. Además de eso, SuperScan también se puede utilizar para ejecutar consultas básicas como whois, traceroute, ping, etc. Por lo tanto, SuperScan es otra mejor herramienta de piratería que puede considerar.
¿Puedo hackear cuentas en línea con estas herramientas?
Estas herramientas estaban destinadas a fines de seguridad y se pueden utilizar para encontrar lagunas. No promovemos el pirateo de cuentas y puede provocar problemas legales.
¿Son seguras estas herramientas?
Si está descargando las herramientas de fuentes confiables, entonces estaría del lado seguro.
¿Puedo escanear mi red WiFi con estas herramientas?
Para escanear la red WiFi, uno necesita usar un escáner WiFi. Hay pocos escáneres WiFi enumerados en el artículo que le proporcionarían detalles completos sobre la red.
Entonces, arriba están las mejores herramientas de piratería ética para PC. Si te gusta esta publicación, no olvides compartirla con tus amigos. Si tiene algún problema, no dude en hablar con nosotros en la sección de comentarios a continuación.
0 notes
Link
WiFite Description A tool for automated wireless attack. Wifite works only on Linux. Wifite was created for use with penetration testing distributions, such as Kali Linux, Pentoo, BackBox; any Linux distributions with wireless drivers patched for injection. It seems to also work on Ubuntu, Debian and Fedora.
WiFite2 Automated Wi-Fi hacking tool
There are many ways to attack a Wi-Fi network. The type of encryption, default settings of the manufacturer and the number of connected clients can determine how easy it will attack the target and which method of hacking will work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets within your adapter's coverage area, and then selects the best hacking strategy for each network. As a rule, programs are sharpened to perform one specific function:
customer deauthentication
handshake
brute force
brute force WPS
etc., there are a lot of separate stages, methods.
Features:
sorts targets by signal (in dB); hacking the closest access points first
automatically deauthenticates hidden network clients to reveal their SSID
a set of filters to accurately indicate what to attack (wep / wpa / both, above a certain signal strength, channels, etc.)
flexible settings (timeouts, packets per second, other)
“anonymity” functions: changing the MAC to a random address before an attack, then a reverse change when the attack is completed
all captured WPA handshakes are copied to the current wifite.py directory
WPA smart deauthentication; cycles between deauthenticating all clients and broadcast
stop any hacking with Ctrl + C with options to continue, go to the next target, skip hacking or exit
display of general information on the session upon exit; show all cracked keys
all passwords are saved in cracked.txt
Homepage: https://github.com/derv82/wifite2
When a wireless network tester gets to work, it moves from one program to another to perform different stages of penetration, to use different methods. Wifite or Wifite2? Wifite is not a new tool. It was one of the first Wi-Fi hacking tools we met. Along with Besside-ng, automated scripts for hacking Wi-Fi allowed even the script kiddie to get good results, despite the fact that they did not understand how these scripts work. Compared to Besside-ng, the original Wifite thoroughly used all the tools available to it to attack the network, but at the same time it was very slow. One of the best features of the original Wifite was that he conducted a Wi-Fi scanning of the area before attacking nearby networks. This allowed the hacker to specify one, several or all networks as targets. Due to the fact that Wifite laid out to the user all the available targets in an easy-to-understand format, even a beginner could understand which attacks are best used against the nearest networks. The original Wifite could automatically attack WPA networks by intercepting handshakes or use the Reaver tool to bruteforce the WPS PIN codes of nearby networks. Despite the fact that this method of attack was very effective, its execution took 8 hours or more. The updated WiFite2 works much faster due to the reduction of time for the attacks themselves and the use of more advanced tactics than in the previous version. Because of this, Wifite2 is a more serious and powerful tool for hacking Wi-Fi than the original Wifite. Wi-Fi hacking procedure For the fastest possible hacking of nearby networks, Wifite2 uses a simple but fairly effective procedure. He brings every tactic he is trying to apply, to the limit of its practical application, he may even go so far as to try to hack any incoming handshakes. First of all, Wifite2 scans all channels in search of all networks in the coverage area. Then it ranks the found networks by signal level, since the fact of finding a network does not guarantee a reliable connection with it. In addition to sorting the detected networks in descending order of signal, the reconnaissance phase includes the collection of information about which hacking methods these networks may be vulnerable to. Thanks to the organization of Wifite2, you can easily add a directional Wi-Fi antenna, and use Wifite2 to locate the source of any nearby Wi-Fi network when conducting a neighborhood scan. After the scan is complete, the counties will reflect all reflected targets to see whether clients are connected to them, whether the network announces WPS usage, and what type of encryption the network uses. Based on this, the hacker chooses any target, group or all targets for attack based on the information collected. Wifite2 will go through the entire list of goals, starting with the fastest and simplest attacks, such as WPS-Pixie, which can crack a password in a matter of seconds, to less reliable tactics, such as checks for using weak passwords using a dictionary attack. If the attack fails or its completion takes too much time, then Wifite2 will proceed to the next possible attack in a particular case, so as not to waste time, as its predecessor did. What you need First you need a Wi-Fi adapter that can be switched to monitoring mode. This means that you must choose an adapter that is compatible with Kali Linux. We have several excellent guides on this subject. “ How to determine which Wi-Fi adapter is suitable for Kali Linux ” and if you need a good wireless card for hacking check this huge list of adapters that support monitor mod, USB Wi-Fi adapters that support monitor mode and wireless injection Wifite2 is installed by default in Kali Linux, so we recommend using Kali on a virtual machine or as a second system on a laptop. You can use Wifite2 on other Linux systems, but we will not elaborate on installing it, since we assume that you still use Kali Linux. WiFite installation The program is preinstalled in Kali Linux, additionally install the programs:
hcxdumptool
hcxtools
Linux installation Required dependencies:
Python. Wifite is a Python script and requires Python to run, the program is compatible with versions of python2 and python3.
iwconfig : To determine if the wireless interfaces are already in monitor mode.
ifconfig : To start / stop wireless devices
Set aircrack-ng . The following programs are used specifically:
airmon-ng : To list and enable Monitor Mode on wireless interfaces.
aircrack-ng : To hack WEP .cap files and captured WPA handshakes.
aireplay-ng : To deauthenticate Access Points, replay capture files, various WEP attacks.
airodump-ng : To scan targets and generate capture files.
packetforge-ng: For fake capture files.
Optional but recommended dependencies:
Reaver , is intended for the selection of the WPS (Wifi Protected Setup) pin by the brute force method. Reaver turns on the "walsh" (or "wash") scanner to detect access points with WPS turned on. Wifite uses Reaver scanning and to attack routers with WPS enabled.
Pyrit , a WPA PSK key cracker using a graphics processor. Wifite uses Pyrit (if found) to identify handshakes. In the future, Wifite may get the option to crack WPA handshakes using Pyrit.
tshark. It is supplied in conjunction with Wireshark , software for sniffing packages.
coWPAtty , WPA PSK key cracker. Wifite uses cowpatty (if found) to identify handshakes.
Pixiewps , a tool written in C, is used for offline brute force pin WPS by exploiting the low or non-existent entropies of some access points (pixie dust attack).
Wifte2 Video tutorial
After installing dependencies, installing WiFite itself is very simple:
123git clone https://github.com/derv82/wifite2.git cd wifite2 sudo ./Wifite.py
In a typical launch, Wifite will only ask the user one time: which access points should they attack? You can run Wifite so that it will not even ask it - it will attack every TD. You can specify a dictionary file - and the program will completely autonomously send deauthentication packets, grab handshakes, sort through passwords, sort through WPS pins and try to use WPS PixieDust, conduct various attacks on WEP. Moreover, the program will launch an attack on the weakest technologies and, in case of failure, move on to more secure ones.
Depending on the success, the result of the program may be getting a password in clear text, or captured files of handshakes - which need to be brutal to get a password in clear text. How to run WiFite We need a dictionary file . With the following commands we copy it into the current working directory, unpack and clean it (so that all candidates for passwords meet the requirements of WPA passwords).
123cp /usr/share/wordlists/rockyou.txt.gz . gunzip rockyou.txt.gz cat rockyou.txt | sort | uniq | pw-inspector -m 8 -M 63 > newrockyou.txt
Some more theory. WiFite is a “full cycle” program for hacking Wi-Fi access points. it does everything well, but such a stage as brute force passwords can be done not only well - it can be done perfectly well. Passwords can be significantly accelerated if Pyrit is used , but it requires certain skills. Let's start with a very simple one - let WiFite do everything by itself. Automated Wi-Fi hacking in WiFite To do this, you need to launch the WiFite program with two additional options:
- -crack says that you need to hack using a dictionary
--dict ~ / newrockyou.txt indicates which dictionary to use
1sudo wifite --crack --dict ~/newrockyou.txt
After launching, wait a few minutes while the program collects information about available access points:
When the information is sufficient, press the CTRL + the C . We will be asked to enter the numbers of access points that we want to hack. You can select all (you need to enter all), you can select individual APs, listing them separated by commas, you can select ranges, listing them through a hyphen:
Then the program will do everything . If it seemed to you that the program was stuck for too long on any access point or on any attack, then press CTRL + C once to go to the next action. We will be asked - we want to immediately exit or continue, however you can see we got the handshake file here and it's start trying to crack it , no luck for this target but the next target was cracked as you will see
the next target took a few seconds to be cracked using WPS Pixie-Dust :
WiFite output WiFite - perhaps the best program for beginners. You can hack your first wireless access points with it without knowing anything about handshaking, deauthentication, types of Wi-Fi encryption and technologies such as WEP, WPS. Personally, my first successful experience, which made me believe in myself and had awakened my interest in this topic, is connected with the wifite program. In terms of the “effort / results” ratio, there is no equal for wifite. Nevertheless, developing in matters of Pentesting wireless networks Wi-Fi, working with your own hands and head, you can achieve better results. A penster who has enough experience with a quick glance to see unpromising access points (a very weak signal or not a single client), if the pentester detects WPS, he will not get stuck on it for hours, stopping another job (wifite gets stuck, this is correct, because WPS is often hacked). Pentester would try to seize all possible handshakes, and then, while the hashes are moving, launch attacks on WPS and WEP. Perhaps it depends a lot on conditions, but with proper skill it gets easier for me to get a handshake using airodump-ng + aireplay-ng , than using wifite. Some warnings and ways to protect Wifite2 is an example of how script kiddies can effectively attack networks with common vulnerabilities, such as WPS PIN codes and weak passwords. But as the number of advanced attacks, whose execution is automated, grows, it is very important to know about the most common and effective methods of attacks on Wi-Fi networks. The best way to protect your network from tools like Wifite2 is to make sure that you have WPS turned off, and choose a very strong password for your Wi-Fi network that you will not tell anyone. It is important to note that by selecting “all” in the target list, Wifite2 will attack all detected networks, and not just those for which you have permission to test. You must have permission to use this tool on any network that you are attacking, because attacking a network belonging to someone else without permission is a crime and can be very troublesome. Just saying that the script did it, and not you - this is no excuse, especially if you were caught attacking some important network. Therefore, make sure that Wifite2 focuses only on those networks for which you have permission to audit. We hope you enjoyed this guide to automating the Wi-Fi hacking with Wifite2. If you have any questions about this article or about Wi-Fi hacking tools - feel free to write in the comments. Disclaimer : This article is written for educational purposes only. The author or publisher did not publish this article for malicious purposes. If readers wish to use information for personal gain, the author and publisher are not responsible for any harm or damage caused.
0 notes
Text
ES File Explorer File Manager APK Cracked by CharsiAPK is now available to download. This Cracked/MOD APK has all premium features unlocked without ads.
Description:
ES File Explorer is a free, full-featured file and application manager. It functions as all of these apps in one: file manager, application manager, task killer, download manager, cloud storage client (compatible with Dropbox, Google Drive, SkyDrive, Box.net, Sugarsync, Yandex, Amazon S3, and Ubuntu One…), FTP client, and LAN Samba client.
Features:
File Manager – Manage your files like you do on your desktop or laptop using Multiple Select, Cut/Copy/Paste, Move, Create, Delete, Rename, Search, Share, Send, Hide, Create Shortcut, and Bookmark; operations can be performed on local files (on Android device) or remotely (on your computer)
Application Manager – categorize, uninstall, backup, and create shortcuts to your apps
Remote File Manager – when enabled, manage files on your phone from your computer
Built-in ZIP and RAR support allows you to compress and decompress ZIP files, unpack RAR files, and create encrypted (AES 256 bit) ZIP files
Built-in viewers and players for various file types, including photos, music, and videos; supports third-party applications, such as Quick office, for opening others
Shows thumbnails for APKs and images
Text viewers and editors
Access your home PC via WiFi with SMB
Functions as your FTP and WebDAV client. Manage files on FTP, FTPS, SFTP, and WebDAV servers just like you manage files on your SD card
Supports Dropbox, Box.net, Sugarsync, Google Drive (Google Docs is now a part of Google Drive), SkyDrive, Amazon S3, Yandex and more. ES File Explorer is an enhanced cloud storage client with more functions than the official versions, it can save photos, videos, and other files to your internet drives and share them with others.
Bluetooth file browser You can copy and paste files between Bluetooth ready devices. It supports OBEX FTP for browsing devices and transferring files between Bluetooth devices.
MOD Features:
– Ads Removed – Sponsored banner layout removed – All ads calls from activity removed – All ads banner layout in tablet mode removed – Native admob ads banner layout removed – Lockscreen ads resized to 0 – Real Time Monitor unlocked – Theme Chooser unlocked – System hidden files unlocked – Forced startup ads page disabled – Gift icon removed from Es Swipe – Analytics disabled
Screenshots:
This slideshow requires JavaScript.
Download Links:
Main Link | Mirrro 1 | Mirror 2 – App
Main Link | Mirrro 1 | Mirror 2 – Theme
ES File Explorer File Manager v4.1.6.6.1 MOD + ES Classic Theme ES File Explorer File Manager APK Cracked by CharsiAPK is now available to download. This Cracked/MOD APK has all premium features unlocked without ads.
0 notes
Text
What operating system used "professional" hackers??? 13 Hacker OS !!!
Use Which operating system "real" hackers? Use Which operating system "real" hackers? The thing here is the real nature and cybercriminals hacktivist hackers and security researchers and white hat hackers die. You can hackers this "real" black or gray hat hackers call, because you, the benefits of government to die in your skills, media organizations, whether for business and profits or as a protest. This Black Hatten hackers have this type of operating system to use, not die are assigned to them while better functions and FREE hacking tools. In addition, the operating system was formed as black hat gray hacker hat or wear? Although blog gibt be-of thousands of articles, dying to say that the Linux operating system hackers for hacking operations prefer black hat is his, shows that it can not be. Many show high-risk hackers to hide some "real hackers" under MS Windows in normal view. Windows is dying, the intended target, but most of the hating dying hackers allows hackers only with Windows environments in Windows .NET Framework-based malware, viruses or Trojans function. Using cheap portable recorder Craigslist bought a fancy starter image easy to build and not be assigned to them. This type of USB laptops burner has and options for SD card storage. This makes it easier, self swallowing to hide, or even destroying, ideal for needed. Many even one step to move on from them and limited to a persistent storage local read-only partitions of the second operating system recording space and work dies. Some paranoid types include a Hotkey-RAM panic button for quick washing and kittens makes a Sysop behind each trace them to avoid. The new Ghost boot image operating system writes less than an encrypted SD card. Portable the burner and will destroy complete data dismantled. Hacker special attention to the destruction of the array drive, hard physical network card and RAM. Sometimes they use a blowtorch or even hammer can that computer-destroying. While some of the black hat hackers prefer Windows operating system, decide many others, the following Linux distributions: 1. Kali Linux
Kali Linux Debian derived is a Linux distribution developed and forensic digital penetration testing. It is alleged, and by Mati Aharoni funded Offensive Security Ltd. Devon Kearns security and backlogging offensive development to rewrite. Linux Kali and is the most versatile extended distro penetration testing. Updated Kali and its tools for many different platforms is like VMware and ARM available. 2. Parrot sec You forensics
Parrot security is based on the Debian GNU / Linux operating system MIXED WITH Frozenbox experience Kali Linux OS and better and security to ensure penetration die. It is an operating system for IT security and penetration testing by the developed Frozenbox development team. It is a GNU / Linux distribution in potassium based on Debian and mixed with. 3. DEFT
Skillful adaptation created is a collection of thousands of people from forensics and Ubuntu documents, teams and business program. Every can of this works under a different license. It's license policy describes the process that we follow to determine which software, and send to the default installation CD DEFT. 4. Live hacking system
Live Hacking Linux OS base hat available in a large package of tools or for Hacking Ethical penetration penetration testing useful. Includes GNOME die graphical interface built. A second alternative to elimination, only dies command line and has very few hardware Hat Exigences. Table 5. Samurai Web Security
Samurai Web Testing Framework A is a live Linux environment, was preconfigured as a Web penetration test environment to die on the job. The CD contains the best and free open source tools, tests and attack sites that focus on dying. In developing dieser lathe we have our selection of tools that are based on the tools in our practical use of safety. We have the tools steps One out of every four web test pencils used contained.
6. Network Security Toolkit (NST)
The Network Security Toolkit (NST) is a dynamic boot CD based on Fedora Core. The toolkit was developed easy open source access to the best security applications to provide network access and should work on other x86 platforms. To develop The main purpose of this toolkit was to provide a comprehensive set of available open source network security tools, the network security administrator.
7. NodeZero
It is said that necessity is the mother of all inventions, and NodeZero Linux is no different. NodeZero team of testers and developers, who gathered this incredible Distro. Penetration testing distributions are historically the concept of "live" to have used Linux system, which really means trying to make any lasting effect on a system. Ergo, all changes are gone after the reboot and run from media such as hard drives and USB memory cards. But everything can be for occasional useful tests its usefulness can be explored if the test regularly. It is also believed that the "living system" simply does not scale well in an environment of solid evidence.
8. pentoo
Pentoo has developed a live and live USB CD for penetration testing and safety assessment. Based on Gentoo Linux, pentoo is available on a 32-bit and 64-bit installable CD. Pentoo also as an overlay of an existing Gentoo installation available. It features packaged Wi-Fi driver packet injection, GPGPU software cracks and a variety of tools for penetration testing and security assessment. The core includes pentoo Grsecurity and PAX hardening and other patches - with binaries from a set of tools hardened with the latest nightly versions of some tools together.
9. GnackTrack
GnackTrack An open and free project is to merge the penetration testing tools and the Gnome Linux desktop. GnackTrack is a live (and installable) Linux distribution designed for penetration testing and is based on Ubuntu.
GnackTrack comes with several tools that are really useful for effective penetration testing, have Metasploit, Armitage, w3af and other wonderful tools.
10. Blackbuntu
Blackbuntu is a Linux distribution designed for penetration testing, which was developed especially for the security training of students and information security professionals. Blackbuntu is the distribution of penetration tests with the GNOME desktop environment. Currently, with Ubuntu 10.10 integrated previous work | Track.
11. Knoppix STD
Knoppix STD (Distribution Security Tools) is a Linux Live CD distribution based on Knoppix, which focuses on computer security tools. Contains GPL licensed tools in the following categories: authentication, password cracking, encryption, forensics, firewalls, honeypots, intrusion detection system, network utilities, penetration, sniffers, assemblers, Vulnerability Assessment and wireless networks. Knoppix STD Version 0.1 was published on January 24, 2004, in Knoppix 3.2. Subsequently, the installed project, drivers and updated packages are missing. He announced no release date for version 0.2. The list of tools is on the official website.
12. weaker
Weakerth4n is a Debian Squeeze penetration test distribution will be built. To use Fluxbox for the desktop environment. This operating system is ideal for cutting WiFi because it contains a large amount of wireless tools. It has a very clean website and a separate council. Built with Debian Squeeze (Fluxbox inside a desktop environment), this operating system is particularly suitable for cutting WiFi, because it contains many tools and cracks wireless piracy.
The tools include: wireless hacking attacks, SQL, Cisco exploit, password cracking, internet hackers, Bluetooth, VoIP hacking, social engineering, information gathering, fuzzing Android piracy, networking and mussels.
13. Cyborg Falcon
Many hackers that this is the distribution of always modern tests, efficient and even better penetration. Aligned with the latest collection of tools for Ethical Hacker Pro and cyber security experts. It has more than 700 tools during Kali has dedicated more than 300 tools and the menu for mobile security and malware analysis. In addition, it is easy to compare it with Kali to make a better operating system than Kali.
via Blogger http://ift.tt/2l3qTT0
0 notes
Text
How To Crack Android Lock screen in few clicks| Andrill Tutorial
Most of the people out there uses android device because of it’s popularity and friendliness. well most of the people out there believe android is secure enough don’t know about the hidden secrets and what’s hidden under the source code. It’s true that with frequent updates and everything android is still moving to be a secure OS still there are many vulnerabilities which lies within deep in Android OS.
In this article article I am going to tell you about “How You can Crack android Lock-screen easily with this amazing tools known as Andrill” Like always this post is made in such a way that everybody even a beginner will understand and no prior knowledge is needed at all.
Note: This post is a tutorial on Android Hacking and Breaking Lockscreen pattern or Lockscreen Pin is for educational purposes only! Please do not misuse this. Respect everyone’s privacy. Our Team will not be responsible for any of your activities.
What’s Andrill Tool?
Andrill as mentioned on their website is a android forensic tool. Andrіllеr – іѕ ѕоftwаrе utіlіtу wіth a соllесtіоn оf forensic tools fоr smartphones. It реrfоrmѕ rеаd-оnlу, forensically ѕоund, nоn-dеѕtruсtіvе асԛuіѕіtіоn from Android devices. It hаѕ features, such аѕ роwеrful Lосkѕсrееn сrасkіng fоr Pattern, PIN code, оr Password; сuѕtоm dесоdеrѕ for Apps dаtа frоm Android (some Aррlе іOS & Wіndоwѕ) dаtаbаѕеѕ fоr decoding communications. Extrасtіоn and dесоdеrѕ produce reports in HTML аnd Exсеl fоrmаtѕ.
Also Read: Spy on anyone using this Android RAT
Andrill Setup
Andrіllеr іѕ a cross-platform аррlісаtіоn for Microsoft Wіndоwѕ аnd Ubuntu Lіnux. Thе Windows lightweight ѕеtuр іnѕtаllеr only requires Mісrоѕоft Visual C++ 2010(Generally present in all windows by default) Rеdіѕtrіbutаblе Pасkаgе (x86) іnѕtаllеd, USB drivers fоr уоur Andrоіd dеvісе, аnd a web brоwѕеr for viewing results. Ubuntu vеrѕіоn needs thе “аndrоіd-tооlѕ-аdb” расkаgе іnѕtаllеd. Simple.
Download Link:
Download Andrill
Features Offered By Andrill
Autоmаtеd dаtа еxtrасtіоn аnd decoding
Data еxtrасtіоn оf non-rooted without dеvісеѕ bу Andrоіd Bасkuр (Andrоіd versions 4.x)
Dаtа еxtrасtіоn with rооt реrmіѕѕіоnѕ: rооt ADB dаеmоn, CWM rесоvеrу mоdе, оr SU bіnаrу (Superuser/SuperSU)
Data раrѕіng аnd dесоdіng fоr Folder ѕtruсturе, Tаrbаll fіlеѕ (from nаnddrоіd backups), and Android Bасkuр (‘bасkuр.аb’ files)
Sеlесtіоn of іndіvіduаl dаtаbаѕе dесоdеrѕ fоr Andrоіd аnd Aррlе
Dесrурtіоn оf еnсrурtеd WhаtѕAрр аrсhіvеd dаtаbаѕеѕ (mѕgѕtоrе.db.сrурt tо *.crypt12)
Lосkѕсrееn сrасkіng fоr Pаttеrn, PIN, Password
Unpacking thе Andrоіd bасkuр fіlеѕ
Sсrееn сарturеѕ оf device display
1] Fіrѕt thing Download Andrіllеr frоm above link :Andrill Nоw install and ореn the Andrіllеr and ѕеlесt output fоldеr. Yоu wіll gеt a pop uр аnd select your desired folder.

Andrill Opening Interface
2] After Downloading connect your Android рhоnе wіth соmрutеr uѕіng Dаtа саblе. Insode Andriller ѕоftwаrе click on Chесk орtіоn, if уоur Andrоіd рhоnе іѕ ѕuссеѕѕfullу соnnесtеd with Andrіllеr іt wіll gіvе a Serial ID. If it didn’t work you will need to install ADB drivers for your device. Simply google: “Model Name ADB driver” {replace model name with your device like Pixel 2 XL ADB Drivers}. Download and install them and Restart your PC [Do not shut down and turn on again, “RESTART IT“].
Here is a thread guiding about ADB: ADB Thread
Also Read: Android OS dedicated for Hacking Only
3] After this you will be ready to get into action with andrill, Once you gеt Sеrіаl ID means your device is successfully connected thеn select thе check bоx whісh says Oреn Report & Uѕе AB mеthоd аnd сlісk on go button.
Now youll probably see a POP-UP Saying: FULL-BACKUP at thе bоttоm rіght оf your phone ѕсrееn you wіll see Back up mу dаtа click оn thаt. and backup the data. Onсе the Bасkuр іѕ done, уоu can see thе соmрlеtе dаtа іn thе fоldеr where you chose to select the data in previous steps.
Now, it will automatically decrypt it and pop up will open in browser and you will be able to see all the password and other secret data, meta data about the model like WiFi passwords, Stored passwords etc.
Well that was just a piece of cake, Now let’s see how you can Break Android Lockscreen.
Breaking Android Locksreen
Let’s assume your device is connected [serial ID is generated in previous steps as mentioned]
1] As we did in previous steps, You must have enabled USB Debuggin in your android or this method will not work at all. So enable USB Debugging on android device whose pattern you want to break.
2] Connect Device an Go to panel which say’s Lockscreens

Android Lockscreen Breaking Menu
3] Pattern, PIN аnd Password Cracking Thеѕе features require a lіttlе more рrосеѕѕіng power, ѕо аrе bеѕt tо bе performed lосаllу on your оwn machine. Thе methods аrе еxрlаіnеd below.
4] Gеt Sаlt values from Sаlt іѕ an іntеgеr vаluе, whісh іѕ rеԛuіrеd fоr сrасkіng thе раѕѕwоrdѕ. Salt can be роѕіtіvе as well аѕ negative іntеgеrѕ. The salt vаluе саn be obtained bу раrѕіng setting.db or lосkѕеttіngѕ.db fіlеѕ [which you imported in previous settings]; when successfully fеtсhеd, thе Sаlt value wіll be рrіntеd іntо thе main terminal wіndоw.
5] Now configure the basic settings as you will go through the options you will understand, Like if you have a Gesture select that option and you will be prompted with something like below:

6] If you have a PIN Lock, just enter the salt value and wait and relax until it finishes and you will be prompted with a correct password.

Android PIN Cracking
7] Once this will be done, You will get the prompt with cracked PIN/Password.
Andrill is not limited to this only it has many advance level features which you can explore.
Note that although android versions are same, each company make their own flavour of android. we have tested this on NOKIA,Motorola,Micro-max,Samsung and it worked. this also worked in Xiaomi and OPPO however we failed to break huawei and Pixel Phones. This might work on your device or not depends on the android version and company.
Feel Free to share this and bookmark for future refrence, Also share on social media and tag us while sharing and we wil have some awesome gifts for you.
Follow us on every platform and help us to grow.
from WordPress https://techhacksaver.com/pentesting/how-to-crack-android-lock-screen-in-few-clicks-andrill-tutorial/
1 note
·
View note
Text
How To Hack Twitter Accounts | Via TweetShell BruteForcing
Hey THS Hacker’s, In this article I am going to tell you about a tool that is used by hackers to crack twitter accounts and steal the credentials.
The tool name is “Twееtѕhеll” and it іѕ an ореn ѕоurсе multі-thrеаdеd ѕhеll ѕсrірt tool сараblе to find the password оf аnу Twіttеr ассоunt. It іѕ easy to uѕе аnd іt іѕ operated thrоugh short аnd simple commands. It uѕеѕ a ѕесurе рrоxу tо еnѕurе thаt your identity is hіddеn and hаѕ trеmеndоuѕ ѕрееd whісh аllоwѕ it to tеѕt a wіdе rаngе of passwords. With This tool you can crack password of any twitter account
What Is Brute Forcing?
A Brutе Fоrсе Attасk іѕ thе simplest mеthоd tо gain ассеѕѕ tо a ѕіtе оr ѕеrvеr (оr аnуthіng that іѕ раѕѕwоrd protected). It trіеѕ vаrіоuѕ соmbіnаtіоnѕ оf usernames and раѕѕwоrdѕ аgаіn and аgаіn untіl it gеtѕ in. Thіѕ repetitive асtіоn is lіkе an аrmу attacking a fоrt. Guеѕѕіng a password fоr a particular uѕеr оr ѕіtе can tаkе a long time, so hасkеrѕ dеvеlореd tооlѕ tо dо thе jоb fаѕtеr.Dictionaries are the most bаѕіс tооl. Some hасkеrѕ run thrоugh unаbrіdgеd dictionaries and augment words with special сhаrасtеrѕ аnd numеrаlѕ оr use ѕресіаl dісtіоnаrіеѕ оf wоrdѕ, but this tуре оf ѕеԛuеntіаl attack іѕ сumbеrѕоmе.In a standard аttасk, a hасkеr chooses a tаrgеt аnd runѕ роѕѕіblе раѕѕwоrdѕ against thаt username. These are knоwn as dісtіоnаrу аttасkѕ.Just аѕ the nаmе implies, a reverse brutе fоrсе аttасk rеvеrѕеѕ thе attack ѕtrаtеgу bу ѕtаrtіng wіth a knоwn раѕѕwоrd — lіkе lеаkеd passwords thаt are available оnlіnе — аnd ѕеаrсhіng mіllіоnѕ оf uѕеrnаmеѕ untіl іt fіndѕ a match.
Also Read: Hack Wifi Password Easily
Note: Using TweetShell and/or similar tооl fоr аttасkіng targets wіthоut рrіоr mutuаl соnѕеnt іѕ іllеgаl. This article is just for information purpose only and TechHackSaver(THS) is not responsible for any of your activities.
Tweetshell: Multi-threaded Script To Crack Password Of Twitter Account.

All you have to do is provide a Username of the twitter account that you want to brute force. After giving a username to Tweetshell, it will ask you which list of passwords you want to search through you can also provide you a password list which can you simply download over google and the number of threads you want to use. After this, it will check each password one by one, also known as the brute force method, until it finds the correct password or the list of passwords.
AS We said You can Also use Password List so,
How to Get Password List Online?
We are Providing you some amazing password lists with biggest leaks, you can also create your own, or If you want me to create a separate article on password list or how to create one? Just Comment Down below!
Pаѕѕwоrd lіѕt dоwnlоаd bеlоw, bеѕt wоrd lіѕt and mоѕt соmmоn раѕѕwоrdѕ аrе ѕuреr important whеn іt соmеѕ to password cracking аnd rесоvеrу, аѕ well аѕ the whоlе ѕеlесtіоn оf асtuаl leaked password dаtаbаѕеѕ уоu саn gеt from lеаkѕ аnd hacks lіkе Ashley Mаdіѕоn, Sоnу аnd mоrе.
Oxford Uni Password
Argon Word List
Leaked DB Wordlist
Packet Storm Word List
TweetShell Features:
Default раѕѕwоrd lіѕt (+39k wіth 8 lеttеrѕ supported)
Nо lіmіt оn thе numbеr оf password уоu саn сhесk
Up to 20 thrеаdѕ, rеасhіng 400 раѕѕwd/mіn
Ability to ѕаvе рrоgrеѕѕ bеtwееn ѕеѕѕіоnѕ, allowing you to uѕе large password datasets
Chесk valid usernames
Supported Operating Systems:
Linux Distro
Termux {android}
Mac {Unsure}
Windows – via Ubuntu Command distro [Default Not supported]
Prerequisite:
Tor
Curl
Setup and Usage:
Installation Command:
$ git clone https://github.com/thelinuxchoice/tweetshell
Nаvіgаtе tо thе wоrkіng dіrесtоrу аnd іnѕtаll the requirments:
$ cd tweetshell $ chmod +x install.sh $ sudo ./install.sh
Usage:
$ chmod +x tweetshell.sh $ sudo ./tweetshell.sh
Now you will be able to see the script running and all you have to do it provide the username of the account that you want to Crack!
Download Now
How Can You Prevent BruteForce Attack On your Twitter Account?
Use Two Factor authentication
Use Complex Password
Include Special Characters
Check For the Active Sessions
Feel Free to share and follows on Telegram and instagram,twitter and all platforms!
from WordPress https://ift.tt/2VvPIvL via IFTTT
0 notes