#backup and recovery
Explore tagged Tumblr posts
Text
Top 8 plugin Backup cho website WordPress uy tín nhất hiện nay
1. UpdraftPlus
2. BackWPup
3. Duplicator
4. All-in-One WP Migration and Backup
5. Jetpack VaultPress Backup (VaultPress)
6. BlogVault
7. Solid Backups (BackupBuddy)
8. WP Time Capsule
Thông tin chi tiết về các tính năng của các plugin trên trong bài viết dưới đây 👇👇👇
#business#design#web series#website#công ty thiết kế website#software#thiết kế web#thiết kế website#web design#userexperience#wordpress web design#wordpress#hosting wordpress#wordpress development#wordpress hosting#wordpress web development services#wordpress website#wordpress web development company#wordpress web development agency#backup#datasecurity#data protection#cybersecurity#backup website#backup website wordpress#backup and recovery#backup account#backup blog#backup power#backup imap emails
1 note
·
View note
Text
Hospitals Are the Target in a New Kind of Cyberwar
New Post has been published on https://thedigitalinsider.com/hospitals-are-the-target-in-a-new-kind-of-cyberwar/
Hospitals Are the Target in a New Kind of Cyberwar


Since the earliest days of cybercrime, healthcare data has been a prime target. Until recently, most cyberattacks on hospitals followed a familiar pattern: ransomware groups would encrypt patient records and demand payment. The motive was clear – and it was all about the money.
But cybersecurity experts are now warning of a shift. A growing number of attacks on health sector systems appear to be driven not by profit, but by politics. These incidents, often traced back to nation state-backed groups, aim to disrupt hospital operations, steal sensitive medical data, and undermine public trust. The United Nations has called cyberattacks on healthcare “a direct and systemic risk to global public health and security.”
This evolution comes at a vulnerable time, as trust in health institutions remains fragile. Cyberattacks deepen that mistrust, strain critical infrastructure, and blur the line between criminal enterprise and geopolitical strategy. As someone working at the intersection of healthcare security and intelligence sharing, I believe this is no longer just a criminal problem – it’s a threat to national security.
The challenge of attribution
As the motives behind cyberattacks on the health sector shift, so too does the complexity of understanding who is behind them – and why.
Unlike the straightforward financial motives of traditional ransomware groups, state-backed campaigns are often hidden behind layers of sophisticated proxies, hacktivist fronts, or loosely affiliated cybercriminals. What may initially appear to be a routine ransomware incident could, upon deeper investigation, reveal signs of a coordinated strategy: targeting critical healthcare infrastructure, maximizing operational disruption, and carefully avoiding attribution to any nation-state.
This pattern has already been seen in high-profile cases. During the COVID-19 pandemic, several European healthcare institutions suffered cyberattacks that officials later suspected were linked to foreign intelligence operations. Although the attacks initially resembled criminal ransomware campaigns, deeper analysis pointed to broader aims – such as stealing vaccine research, disrupting care during a public health emergency, or sowing mistrust in the healthcare system.
This deliberate ambiguity serves the attackers well. By masking strategic sabotage as criminal activity, they sidestep direct political consequences while still inflicting serious harm on institutions providing patient care. For defenders, this blurred line between crime and geopolitics complicates the response at every level: technical, operational, and diplomatic.
In the health sector, patient safety is at immediate risk during a cyber incident, and there is little time or capacity for in-depth forensic analysis. Without a clear understanding of the nature and purpose of an attack, hospitals and healthcare providers may misjudge the threat, miss broader patterns, and fail to coordinate an appropriate defensive strategy.
Importance of intelligence sharing
The key to building an effective defense is collective action, which depends on the free exchange of information. Critical infrastructure organizations are coming together to form Information Sharing and Analysis Centers, or ISACs. Health-ISAC brings together more than 14,000 people through anon-profit industry association designed to facilitate trusted exchanges of cybersecurity threat intelligence, enabling faster, more coordinated responses to emerging risks. Health-ISAC connects hospitals, pharmaceutical companies, insurers, and other stakeholders, creating an ecosystem where knowledge flows more freely and early warnings can be amplified across the global health community.
By sharing indicators of compromise, attack techniques, suspicious behaviors, and lessons learned, organizations can turn isolated observations into industry-wide intelligence. A malware signature spotted in a single hospital today could be the early warning that prevents a wave of attacks across the entire globe tomorrow. In this way, intelligence sharing transforms defense from a series of isolated struggles into a coordinated, proactive effort.
However, building and sustaining this kind of collaboration is not without its challenges. Effective sharing depends on trust: trust that sensitive information will be handled responsibly, and trust that participants are committed to mutual defense. Health sector organizations must be willing to report incidents transparently. Fostering this culture of openness remains one of the sector’s greatest challenges, but also one of its most powerful opportunities to strengthen the industry against increasingly sophisticated threats.
Building resilience
While robust cybersecurity controls remain essential, the reality is that preventing every attack is impossible. Therefore, health sector institutions must invest in resilience: the ability to maintain or quickly restore critical services under attack.
That starts with preparation. Organizations should develop and regularly rehearse detailed incident response plans tailored to their specific workflows, facilities, and patient care requirements. These exercises help staff know what to do when systems go down and ensure that decision-making isn’t delayed by confusion or uncertainty during a crisis.
Segmented network architectures are another critical defense. By isolating systems – such as separating medical devices from administrative tools or confining lab networks to their own segment – organizations can prevent malware from moving laterally and causing widespread disruption. This kind of compartmentalization limits damage and buys valuable time for response teams.
Equally important is the strength and accessibility of backup and recovery systems. Backups should be stored securely, tested regularly, and maintained in offline or immutable formats to prevent them from being manipulatedduring an attack. The faster an organization can restore patient records, scheduling tools, and communication systems, the sooner it can return to safe and effective care.
Final thoughts
Too often, cyberattacks reveal that resilience was treated as an afterthought. But in the health sector – in which lives are on the line – it must be a foundational priority. Planning, practice, and coordination are no longer optional. They are the frontline defenses in a cyberwar hospitals can no longer afford to ignore.
What’s needed now is a shift in mindset. Health sectorleaders must view cybersecurity not as an IT issue, but as a core part of patient safety and institutional trust. That means allocating resources, engaging staff at every level, and collaborating beyond organizational boundaries.
No single hospital can stand alone against the forces reshaping the threat landscape. But together – through shared intelligence, coordinated response, and a renewed focus on resilience – the health sector can push back against this rising tide and protect the critical systems millions rely on every day.
#000#Accessibility#Analysis#attackers#backup#backup and recovery#backups#blur#Building#challenge#Collaboration#Collective#communication#Community#Companies#complexity#compromise#covid#crime#critical infrastructure#cyber#Cyberattacks#cybercrime#cybercriminals#cybersecurity#cybersecurity experts#data#defenders#defense#defenses
1 note
·
View note
Text
Top methods for Backup and Recovery you Must Know!

Unfortunately, natural disasters such as fire, earthquake, flood, or even power failures have in the past been the cause of several data loss cases. In this digital transformation era, Data is an invaluable asset for businesses of any type or industry, and losing this precious data can lead to massive damage in more than one way for organizations. According to a report, the average total cost of data breaches in 2022 was about $4.35 million. In fact, India was in the top 45% of cyber-attacks in the year 2022 among other countries. The major brunt of these attacks and targets was the government institutions, resulting in an increase of 95% rise in the year-on-year report for our country.
While backup sounds like a simple process of copying data from one system to another, it has several critical aspects attached to it, such as including application and product data, information of accounts, members, other business records, and employee data among other crucial information that is vital for business operations. Essentially, the backup must be able to help in the regular day-to-day activities without facing any issues internally as well as to the customers. Likewise, recovery ensures utilizing the backup copies in the structure format given, restoring them to their assigned places, and making them back in order to keep the business in continuity. Businesses have realized the importance of having proper backup and recovery plans and have opted for a trusted partner that provides an assured business continuity plan as well.

3 copies of data—which includes original data + two duplicates. That ensures a lost backup or corrupted files do not affect recoverability.
2 different storage types—To reduce the risk of failures if a specific medium does not work out. Internal and external hard drives, removable media, or cloud storage are used generally.
1 copy off-site— Eliminating the risk associated with a single setup. These Offsite duplicates are required during a robust disaster and data backup recovery strategies and failure of local outages.
While following the general industry practices, cloud solutions have been of great help to not only store the data but also back it up regularly and recover swiftly when needed along with the ongoing business operations. Now that we have understood the importance and need for backup and recovery, let’s learn about the different methods of backup and recovery.
Full backup: This involves copying all the data on a system or device to a backup location, such as an external hard drive, cloud storage, or tape drive. This method is time-consuming and requires a lot of storage space, but it ensures that all your data is backed up.
Incremental backup: Incremental backup involves copying only the data that has changed since the last backup. This method is faster and requires less storage space than a full backup, but it requires multiple backups to restore all the data.
Cloud backup: Cloud backup involves storing your data on remote servers maintained by a cloud service provider. This method provides off-site storage and protects your data against physical disasters and theft.
Virtualization: Virtualization involves creating virtual machines that can be backed up and restored independently of the underlying hardware. This method provides flexibility and simplifies backup and recovery
Disaster Recovery: Disaster recovery involves planning and preparing for the worst-case scenario, such as a natural disaster, cyber-attack, or hardware failure. This method includes creating a disaster recovery plan, testing the plan, and ensuring that the necessary resources and tools are available.

As per the business need, the method of data backup can be chosen for action. These backup methods vary in quality and quantity of the data as well. It’s essential to choose a backup and recovery method that provides the right level of protection and meets your budget and time constraints.
Some of the best practices for a full-proof disaster recovery or business continuity include both backup and recovery as 2 sets of approaches. A regular and consistent backup solution and a well-defined recovery plan put together in place can ensure data protection and save you from unplanned data loss. It is only wise to be prepared for the worst-case scenario while being able to run the daily operations uninterrupted. Cloud solutions provide the relief of daily operations along with regular backup and recovery process which is achieved automatically. For businesses seeking an off-site data storage backup cloud becomes a safe option.
0 notes
Text
Install Splunk and Veeam App on Windows Server to monitor VBR
Splunk Enterprise is a powerful platform that automates the collection, indexing, monitoring, and alerting of data. This enables you to aggregate and analyze events efficiently. With Splunk, you can gain full control over your data flow and leverage it to drive business insights and decisions. Kindly read about data management and governance. n this acticle, we shall discuss how to install Splunk…
#Backup#Backup and Recovery#Backup Data#Backup Files and Folders#Linux#MacOS#Microsoft Windows#monitor#Monitor Backup#Monitor VBR with Splunk#Monitor Veeam Backup And Replication [VBR] with Splunk#Splunk#Splunk Enterprise#Veeam App for Splunk#Veeam App for Splunk Setup#Windows 10#Windows 11#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022
0 notes
Text
NAKIVO Backup Solutions: Protecting Your Data with Radiant Info Solutions
Discover how NAKIVO Backup Solutions and Radiant Info Solutions ensure comprehensive data protection and recovery for businesses in India.

0 notes
Text
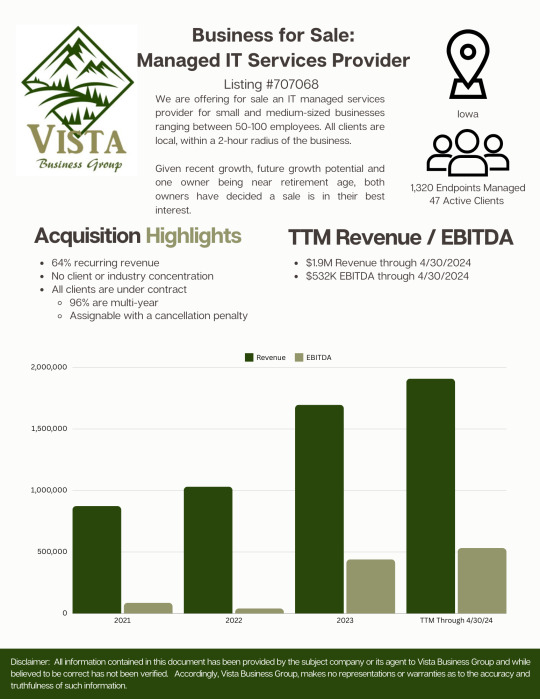
🔥NEW LISTING🔥 ***MANAGED IT SERVICES PROVIDER FOR SALE*** We are offering for sale an IT managed services provider for small and medium-sized businesses ranging between 50-100 employees. All clients are local, within a 2-hour radius of the business. Given recent growth, future growth potential and one owner being near retirement age, both owners have decided a sale is in their best interest. Location - Iowa Acquisition Highlights: ▪ 64% recurring revenue ▪ No client or industry concentration ▪ All clients are under contract ▫ 96% are multi-year ▫ Assignable with a cancellation penalty TTM Revenue / EBITDA: ▪ $1.9M Revenue through 4/30/2024 ▪ $532K EBITDA through 4/30/2024 If you would be interested in learning more about this opportunity please contact Scott Blackwood at [email protected] for more information.
#information technology#it#msp#it managed services#managedservices#managed it services#managed service provider#itcompany#it services#backup and recovery#procurement#it consulting#tech#technology#business#business for sale#forsale#opportunity#privateequity#mergersandacquisitions
0 notes
Text
Revolutionizing Backup and Recovery: VergeIO Unveils ioGuardian for Unprecedented Data Integrity @VergeIO_Inc
Revolutionizing Backup and Recovery: VergeIO Unveils ioGuardian for Unprecedented Data Integrity @VergeIO_Inc #VergeIO #ioGuardian #DataResilience #BackupRecovery #BusinessContinuity #ITsolutions #DataProtection #Innovation #VergeOS #DisasterRecovery
Revolutionizing Backup and Recovery: VergeIO Introduces ioGuardian In the ever-evolving landscape of data management and protection, businesses are constantly seeking innovative solutions to ensure the integrity and accessibility of their critical data. Addressing this imperative, VergeIO, a trailblazer in cutting-edge software solutions, proudly unveils ioGuardian for VergeOS. This…

View On WordPress
#Backup and Recovery#Business Continuity#Data protection#Data Resilience#Disaster Recovery#innovation#ioGuardian#IT Solutions#VergeIO#VergeOS
0 notes
Text
5 Essential Tips for Maintaining Top-Notch Salesforce Org Health
Introduction: Salesforce has become an indispensable tool for businesses to manage customer relationships, streamline operations, and drive growth. However, just like any other complex system, your Salesforce organization requires regular attention and care to ensure it remains efficient, effective, and aligned with your business objectives.
In this blog, we'll explore five essential suggestions to maintain a top-notch Salesforce Org health, helping you get the most out of your investment.
Best Tips for Managing Salesforce Org Health
Regular Data Cleanup and Maintenance: A cluttered and disorganized Salesforce Org can lead to decreased user productivity, slower system performance, and inaccurate reporting. Regularly conduct data cleanup exercises to eliminate duplicate records, outdated information, and irrelevant data. Implement validation rules, workflows, and data governance processes to ensure that data entered into the system is accurate and consistent. Consider archiving or purging old records that are no longer needed, which can significantly improve system responsiveness.
Optimize User Training and Adoption: Even the most powerful tools are only as effective as the users who operate them. Invest in comprehensive user training programs to ensure that your team fully understands the features and functionalities of Salesforce. Regularly assess user adoption rates and address any issues or challenges they might face. Encourage the use of best practices and provide ongoing training as Salesforce releases updates and new features
Govern Customization and Configuration: Salesforce offers an array of customization options to tailor the platform to your specific business needs. While customization is valuable, an excessive amount can lead to complexity, slow performance, and difficulties during upgrades. Establish a clear governance framework for customization and configuration. This includes guidelines for when to use declarative tools (like Process Builder) versus custom code, as well as regular reviews of custom objects, fields, and processes to ensure they remain relevant and effective
Implement Robust Security Practices: Data security and privacy are paramount in today's business landscape. Regularly review and update your Salesforce security settings to ensure that only authorized personnel have access to sensitive information. Implement strong password policies, multi-factor authentication (MFA), and role-based access controls to minimize the risk of data breaches. Regularly audit user permissions and deactivate accounts for employees who no longer require access to the system
Stay Informed About Salesforce Updates: Salesforce continuously releases updates, enhancements, and new features to improve the platform's functionality and security. It's crucial to stay informed about these updates and assess their potential impact on your organization. Create a process for reviewing and testing new releases in a sandbox environment before rolling them out to your production Org. This practice helps identify any potential compatibility issues with your existing customizations and allows for adjustments before affecting users.
Conclusion:
Maintaining a top-notch Salesforce Org health requires a proactive approach that involves regular cleanup, user engagement, customization governance, security measures, and staying updated on platform developments. By following these five essential tips, your organization can ensure that Salesforce remains a powerful tool that contributes to your business success, helping you drive growth, streamline processes, and deliver exceptional customer experiences.
#Salesforce Org Health#Org maintenance#CRM optimization#Data integrity#Performance tuning#System health check#Data hygiene#Configuration management#Best practices#User adoption#Customization management#Security audit#Data governance#Automation tools#Regular updates#User training#Scalability#Backup and recovery#Compliance measures#Analytics and reporting
0 notes
Text
my 8 year old macbook just crashed and wouldnt restart and if recovery move doesn’t fix things i think i really will crawl into a cave and sleep for 10000 years fuck me
#i have a backup from a few weeks ago that’s Fine#but i cannot emotionally or financially handle getting another macbook right now#like i can use the windows laptop to get by but my data and papers and all that shit is on the ios#GREEM.JPG#oh update recovery mode just failed well#time to try pram and smc aaaaaa#ramblings#wharglbargle
27 notes
·
View notes
Text
gonna kill clip paint
#getting through the sketch and 70% of the linework when the power went out on a really good drawing on hancock#and its just gone#not even in my recovery files#they never fucking are#im so mad#IM SO MADDDDDD#LIKE its set to auto save backup every 15 mins#i was workin on it for half an hour at LEAST#not even a LIL BIT of it saved????#it was turning out so good#i dont wanna draw it again#but i want it to exist
30 notes
·
View notes
Text
HD Tech
Founded in 1995 and headquartered in Seal Beach, California, HD Tech has been a trusted partner for businesses seeking dependable and forward-thinking IT solutions. With decades of hands-on experience, we’ve built our reputation by delivering exceptional service and results across industries. Our approach combines technical excellence with a strong commitment to customer satisfaction.

At HD Tech, our mission isn't to be perfect—it’s to be exceptional. As President Tom Hermstad puts it, “Exceptional performance comes from exceptional people. And the foundation for exceptional people is exceptional culture.” This belief guides everything we do, from our hiring and training to how we support our clients. Our cultural fundamentals define us, shaping a team that leads by example in the ever-evolving world of technology.
Contact Details: HD Tech 📍 Address: Seal Beach, CA 90740 📞 Phone: 562-343-8756 🌐 Website: https://www.hdtech.com/
Find Us Online Facebook: https://www.facebook.com/hdtechnologies Instagram: https://www.instagram.com/hdtechoc/ Pinterest: https://www.pinterest.com/hdtechitservices/ Youtube: https://www.youtube.com/channel/UCVd32h5n2oEglVdX18UJp1Q Linkedin: https://www.linkedin.com/company/h&d-technologies/
2 notes
·
View notes
Text
The Most Dangerous Data Blind Spots in Healthcare and How to Successfully Fix Them
New Post has been published on https://thedigitalinsider.com/the-most-dangerous-data-blind-spots-in-healthcare-and-how-to-successfully-fix-them/
The Most Dangerous Data Blind Spots in Healthcare and How to Successfully Fix Them


Data continues to be a significant sore spot for the healthcare industry, with increasing security breaches, cumbersome systems, and data redundancies undermining the quality of care delivered.
Adding to the pressure, the US Department of Health and Human Services (HSS) is set to introduce more stringent regulations around interoperability and handling of electronic health records (EHRs), with transparency a top priority.
However, it’s clear that technology has played a crucial role in streamlining and organizing information-sharing in the industry, which is a significant advantage when outstanding services heavily rely on speed and accuracy.
Healthcare organizations have been turning to emerging technologies to alleviate growing pressures, which could possibly save them $360 billion annually. In fact, 85% of companies are investing or planning to invest in AI to streamline operations and reduce delays in patient care. Technology is cited as a top strategic priority in healthcare for 56% of companies versus 34% in 2022, according to insights from Bain & Company and KLAS Research.
Yet there are a number of factors healthcare providers should be mindful of when looking to deploy advanced technology, especially considering that AI solutions are only as good as the information used to train them.
Let’s take a look at the biggest data pain points in healthcare and technology’s role in alleviating them.
Enormous Amounts of Data
It’s no secret that healthcare organizations have to deal with a massive amount of data, and it’s only growing in size: By next year, healthcare data is expected to hit 10 trillion gigabytes.
The sheer volume of data that needs to be stored is a driving force behind cloud storage popularity, although this isn’t a problem-free answer, especially when it comes to security and interoperability. That’s why 69% of healthcare organizations prefer localized cloud storage (i.e., private clouds on-premises).
However, this can easily become challenging to manage for a number of reasons. In particular, this huge amount of data has to be stored for years in order to be HHS-compliant.
AI is helping providers tackle this challenge by automating processes that are otherwise resource-exhaustive in terms of manpower and time. There are a plethora of solutions on the market designed to ease data management, whether that’s in the form of tracking patient data via machine learning integrations with big data analytics or utilizing generative AI to speed up diagnostics.
For AI to do its job well, organizations must ensure they’re keeping their digital ecosystems as interoperable as possible to minimize disruptions in data exchanges that have devastating repercussions for their patients’ well-being.
Moreover, it’s crucial that these solutions are scalable according to an organization’s fluctuating needs in terms of performance and processing capabilities. Upgrading and replacing solutions because they fail to scale is a time-consuming and expensive process that few healthcare providers can afford. That’s because it means further training, realigning processes, and ensuring interoperability hasn’t been compromised with the introduction of a new technology.
Data Redundancies
With all that data to manage and track, it’s no surprise that things slip through the cracks, and in an industry where lives are on the line, data redundancies are a worst-case scenario that only serves to undermine the quality of patient care. Shockingly, 24% of patient records are duplicates, and this challenge is worsened when consolidating information across multiple electronic medical records (EMR).
AI has a big role to play in handling data redundancies, helping companies streamline operations and minimize data errors. Automation solutions are especially useful in this context, speeding up data entry processes in Health Information Management Systems (HIMS), lowering the risk of human error in creating and maintaining more accurate EHRs, and slashing risks of duplicated or incorrect information.
However, these solutions aren’t always flawless, and organizations need to prioritize fault tolerance when integrating them into their systems. It’s vital to have certain measures in place so that when a component fails, the software can continue functioning properly.
Key mechanisms of fault tolerance include guaranteed delivery of data and information in instances of system failure, data backup and recovery, load balancing across multiple workflows, and redundancy management.
This essentially ensures that the wheels keep turning until a system administrator is available to manually address the problem and prevent disruptions from bringing the entire system to a screeching halt. Fault tolerance is a great feature to look out for when selecting a solution, so it can help narrow down the product search for healthcare organizations.
Additionally, it’s crucial for organizations to make sure they’ve got the right framework in place for redundancy and error occurrences. That’s where data modeling comes in as it helps organizations map out requirements and data processes to maximize success.
A word of caution though: building the best data models entails analyzing all the optional information derived from pre-existing data. That’s because this enables the accurate identification of a patient and delivers timely and relevant information about them for swift, insight-driven intervention. An added bonus of data modeling is that it’s easier to pinpoint APIs and curate these for automatically filtering and addressing redundancies like data duplications.
Fragmented and Siloed Data
We know there are a lot of moving parts in data management, but compound this with the high-paced nature of healthcare and it’s easily a recipe for disaster. Data silos are among the most dangerous blind spots in this industry, and in life-or-death situations where practitioners aren’t able to access a complete picture of a patient’s record, the consequences are beyond catastrophic.
While AI and technology are helping organizations manage and process data, integrating a bunch of APIs and new software isn’t always smooth sailing, particularly if it requires outsourcing help whenever a new change or update is made. Interoperability and usability are at the crux of maximizing technology’s role in healthcare data handling and should be prioritized by organizations.
Most platforms are developer-centric, involving high levels of coding with complex tools that are beyond most people’s skill sets. This limits the changes that can be made within a system and means that every time an organization wants to make an update, they have to outsource a trained developer.
That’s a significant headache for people operating in an industry that really can’t sacrifice more time and energy to needlessly complicated processes. Technology should facilitate instant action, not hinder it, which is why healthcare providers and organizations need to opt for solutions that can be rapidly and seamlessly integrated into their existing digital ecosystem.
What to Look for in a Solution
Opt for platforms that can be templatized so they can be imported and implemented easily without having to build and write complex code from scratch, like Enterprise Integration Platform as a Service (EiPaaS) solutions. Specifically, these services use drag-and-drop features that are user-friendly so that changes can be made without the need to code.
This means that because they’re so easy to use, they democratize access for continuous efficiency so team members from across departments can implement changes without fear of causing massive disruptions.
Another vital consideration is auditing, which helps providers ensure they’re maintaining accountability and consistently connecting the dots so data doesn’t go missing. Actions like tracking transactions, logging data transformations, documenting system interactions, monitoring security controls, measuring performance, and flagging failure points should be non-negotiable for tackling these data challenges.
In fact, audit trails serve to set organizations up for continuous success in data management. Not only do they strengthen the safety of a system to ensure better data handling, but they are also valuable for enhancing business logic so operations and process workflows are as airtight as possible.
Audit trails also empower teams to be as proactive and alert as possible and to keep abreast of data in terms of where it comes from, when it was logged, and where it is sent. This bolsters the bottom line of accountability in the entire processing stage to minimize the risk of errors in data handling as much as possible.
The best healthcare solutions are designed to cover all bases in data management, so no stone is left unturned. AI isn’t perfect, but keeping these risks and opportunities in mind will help providers make the most of it in the healthcare landscape.
#2022#ai#amp#Analytics#APIs#as a service#audit#automation#backup#backup and recovery#bases#Big Data#big data analytics#billion#Building#Business#challenge#change#Cloud#cloud storage#clouds#code#coding#Companies#continuous#data#data analytics#data backup#Data Management#data modeling
0 notes
Text
How to Configure Object First OOTBI Appliance
Undoubtedly, Object First Out-of-the-Box Immutability (OOTBI) storage ranks among the best storage appliances on the market today, specifically designed for the Veeam Backup solution. The same brilliant minds who developed and founded Veeam are behind the creation of OOTBI. In this article, we shall discuss how to Configure Object First OOTBI Appliance. Please see Set up Veeam Backup for…

View On WordPress
#Backup#Backup and Recovery#Local Storage#Object First Ootbi#Object Storage#Ootbi#s3#s3 Compatible Storage#s3 Storage#storage
0 notes
Text
.
#other people had worse days than i did yesterday#but yesterday I managed to fry both backups of all my digital writing for my entire life#along with all the other file detritus I've collected since I was 15#but it's the loss of my writing that's doing me in#I had so many projects I wanted to come back to that I can't ever see again#I don't even remember half of them#I'm looking into data recovery for the damaged drives but. god. what if it doesn't work#what if it's all gone forever?#improving#anyway if anyone knows anything about data recovery for damaged drives hmu i guess
2 notes
·
View notes
Text
tell me how in the hell csp, once upon crashing doesnt have my data for the past few hours my file has been up despite autosaving being turned on for every /40/ minutes. i swear it somehow lost 6 hours of history (that i admittedly barely did anything on, so its not like i lost a ton of stuff but ! is this not false advertising? if it cannot remember despite autosaving every supposed 40 min, how am i meant to trust this thang)
#legitimately upset my shit had a good vibe that is hard to redo because now my jimmies are in a twist :(#and yes every recovery and backup file show nothing past 12:10 pm which was 8 hours ago but i know i drew well past to 3pm#this is such fucking bullshit they lie to me#not the first time this has happened btw lol
10 notes
·
View notes