#cyber attack detection
Explore tagged Tumblr posts
Text
The Growth of Deception Technology in Cybersecurity

View On WordPress
#business#cyber attack detection#cyber security#Cyber Threats#cybersecurity#cybersecurity deception#deception cyber security#deception technology vendors#decoys#Information Security#security deception
0 notes
Text
Cybersecurity in the Age of AI: Navigating New Threats

Understanding AI-Driven Cyber Threats and Defense Strategies
Introduction: A New Cybersecurity Landscape in the Age of AI
Artificial Intelligence (AI) has revolutionized industries worldwide by enhancing efficiency, accuracy, and innovation. From automating routine tasks to enabling predictive analytics, AI continues to unlock unprecedented opportunities. However, as AI becomes deeply embedded in our digital ecosystems, it also reshapes the cybersecurity landscape bringing both powerful defenses and novel risks.
The rise of AI-driven cybersecurity tools is transforming how organizations detect, respond to, and prevent cyber threats. Machine learning algorithms can analyze massive datasets to identify unusual patterns, predict attacks, and automate defenses in real time. Yet, the same AI advancements also equip cybercriminals with sophisticated capabilities enabling automated phishing, intelligent malware, and adaptive intrusion techniques that are harder to detect and mitigate.
This dual-edged nature of AI demands a new approach to cyber threat intelligence, risk management, and security strategy. Organizations must stay vigilant and adopt innovative solutions to safeguard sensitive data and infrastructure against increasingly complex and automated cyberattacks.
For a deeper understanding of how AI is reshaping cybersecurity, check out NIST’s AI and Cybersecurity Framework.
How AI Is Changing Cybersecurity: Defense and Threat Evolution
Artificial Intelligence is revolutionizing cybersecurity by playing a dual role empowering defenders while enabling more sophisticated cyberattacks. On the defense front, AI-powered cybersecurity systems leverage machine learning and data analytics to process enormous volumes of network traffic, user activity, and threat intelligence in real time. These systems excel at detecting anomalies and predicting potential threats far faster and more accurately than traditional signature-based methods.
For example, AI-driven tools can identify subtle patterns indicative of phishing attacks, ransomware activity, or unusual network intrusions, often flagging risks before they escalate into full-blown breaches. Automated incident response capabilities enable rapid containment, minimizing damage and reducing reliance on manual intervention.
However, cybercriminals are equally quick to adopt AI technologies to enhance their offensive tactics. By using AI-generated content, hackers craft convincing phishing emails and social engineering schemes that trick users more effectively. AI can also be used to bypass biometric systems, automate vulnerability scanning, and mimic legitimate user behaviors to avoid detection by conventional security measures. This escalating “arms race” between attackers and defenders underscores the critical need for adaptive cybersecurity strategies.
To explore the evolving interplay between AI and cyber threats, consider reviewing insights from the Cybersecurity & Infrastructure Security Agency (CISA).
Emerging AI-Powered Threats: Deepfakes, Adaptive Malware, and Automated Attacks
The cybersecurity landscape faces increasingly sophisticated challenges due to the rise of AI-powered threats. Among the most alarming is the use of deepfakes hyper-realistic synthetic media generated by AI algorithms that can convincingly impersonate individuals. These deepfakes are weaponized for identity theft, social engineering schemes, or disinformation campaigns designed to manipulate public opinion or corporate decision-making. The growing prevalence of deepfakes adds a dangerous new dimension to phishing and fraud attempts.
In addition, AI-driven adaptive malware is evolving rapidly. Unlike traditional viruses, this malware can modify its code and behavior dynamically to evade signature-based antivirus software and intrusion detection systems. This makes infections more persistent and difficult to eradicate, posing a serious risk to personal, corporate, and government networks.
Furthermore, automated hacking tools powered by AI significantly accelerate cyberattacks. These intelligent systems can autonomously scan vast networks for vulnerabilities, execute targeted breaches, and learn from unsuccessful attempts to improve their strategies in real time. This capability enables hackers to conduct highly efficient, large-scale attacks that can quickly overwhelm human cybersecurity teams.
For more insights into the risks posed by AI-powered cyber threats and how to prepare, visit the National Institute of Standards and Technology (NIST).
Strengthening Cyber Defenses with AI: The Future of Cybersecurity
Despite the growing threat landscape driven by AI-powered attacks, artificial intelligence remains a crucial asset for cybersecurity defense. Cutting-edge security systems leverage AI technologies such as real-time threat intelligence, automated incident response, and predictive analytics to detect and neutralize cyber threats faster than ever before. By continuously analyzing vast amounts of data and learning from emerging attack patterns, AI enables organizations to anticipate and prevent breaches before they occur.
One of the most effective approaches is the integration of AI with human expertise, forming a hybrid defense model. In this setup, cybersecurity analysts harness AI-generated insights to make critical decisions, prioritize threats, and customize response strategies. This synergy balances the rapid detection capabilities of AI with the nuanced judgment of human operators, resulting in more accurate and adaptive cybersecurity posture.
Organizations that adopt AI-driven security platforms can significantly reduce response times, improve threat detection accuracy, and enhance overall resilience against sophisticated attacks.
For organizations seeking to implement AI-based cybersecurity solutions, resources like the Cybersecurity and Infrastructure Security Agency (CISA) offer valuable guidance and best practices.
Ethical and Privacy Considerations in AI-Driven Cybersecurity
As organizations increasingly integrate artificial intelligence in cybersecurity, important ethical and privacy concerns arise. The process of collecting and analyzing vast datasets to identify cyber threats must be carefully balanced with safeguarding user privacy rights and sensitive information. Maintaining transparency in AI decision-making processes is crucial to build trust and accountability. Clear regulatory frameworks, such as the General Data Protection Regulation (GDPR), provide guidelines that help organizations use AI responsibly while respecting individual privacy.
Additionally, organizations face risks associated with over-automation in cybersecurity. Relying solely on AI systems without sufficient human oversight can result in missed threats, false positives, or biased decision-making. These errors may lead to security vulnerabilities or negatively impact the user experience. Therefore, a balanced approach combining AI’s speed and scale with human judgment is essential for ethical, effective cybersecurity management.
By prioritizing ethical AI use and privacy protection, businesses can foster safer digital environments while complying with legal standards and maintaining customer confidence.
Preparing for the Future of AI and Cybersecurity
As artificial intelligence continues to transform the cybersecurity landscape, organizations must proactively prepare for emerging challenges and opportunities. Investing in continuous learning and regular employee cybersecurity training ensures teams stay equipped to handle evolving AI-powered threats. Developing flexible security architectures that seamlessly integrate AI-driven tools enables faster threat detection and response, improving overall resilience.
Collaboration across industries, governments, and academic researchers is critical for creating shared cybersecurity standards, real-time threat intelligence sharing, and innovative defense strategies. Initiatives like the Cybersecurity and Infrastructure Security Agency (CISA) promote such partnerships and provide valuable resources.
For individuals, maintaining strong cybersecurity hygiene using strong passwords, enabling multi-factor authentication (MFA), and practicing safe online behavior is more important than ever as attackers leverage AI to launch more sophisticated attacks.
By combining organizational preparedness with individual vigilance, we can build a safer digital future in an AI-driven world.
Conclusion: Embracing AI to Navigate the New Cybersecurity Threat Landscape
Artificial Intelligence is fundamentally reshaping the cybersecurity landscape, introducing both unprecedented opportunities and significant risks. While cybercriminals increasingly use AI-driven techniques to execute sophisticated and automated attacks, cybersecurity professionals can harness AI-powered tools to create smarter, faster, and more adaptive defense systems.
The key to success lies in adopting AI thoughtfully blending human expertise with intelligent automation, and maintaining continuous vigilance against emerging threats. Organizations that invest in AI-based threat detection, real-time incident response, and ongoing employee training will be better positioned to mitigate risks and protect sensitive data.
By staying informed about evolving AI-driven cyber threats and implementing proactive cybersecurity measures, businesses and individuals alike can confidently navigate this dynamic digital frontier.
For further insights on how AI is transforming cybersecurity, explore resources from the National Institute of Standards and Technology (NIST).
FAQs
How is AI changing the cybersecurity landscape? AI is transforming cybersecurity by enabling faster threat detection, real-time response, and predictive analytics. Traditional systems rely on static rules, but AI adapts to evolving threats using machine learning. It can scan vast datasets to identify anomalies, spot patterns, and neutralize potential attacks before they spread. However, AI is also used by hackers to automate attacks, create smarter malware, and evade detection. This dual-use nature makes cybersecurity both more effective and more complex in the AI era, demanding constant innovation from defenders and responsible governance around AI deployment.
What are the biggest AI-powered cybersecurity threats today? AI can be weaponized to launch sophisticated cyberattacks like automated phishing, deepfake impersonations, and AI-driven malware that adapts in real time. Hackers use AI to scan networks for vulnerabilities faster than humans can react. They also employ natural language models to craft realistic phishing emails that bypass traditional filters. Deepfakes and synthetic identities can fool biometric security systems. These AI-enhanced threats evolve quickly and require equally intelligent defense systems. The speed, scale, and realism enabled by AI make it one of the most significant cybersecurity challenges of this decade.
How does AI improve threat detection and response? AI boosts cybersecurity by analyzing massive volumes of network traffic, user behavior, and system logs to detect anomalies and threats in real time. It identifies unusual patterns like logins from strange locations or data spikes and flags them before they escalate into breaches. AI can also automate responses, isolating infected devices, updating firewalls, or sending alerts instantly. This proactive approach dramatically reduces reaction times and false positives. In large enterprises or cloud environments, where manual monitoring is nearly impossible, AI acts as a 24/7 digital watchdog.
Can AI prevent phishing and social engineering attacks? Yes, AI can help identify phishing attempts by scanning emails for suspicious language, links, or metadata. Natural language processing (NLP) models are trained to detect tone, urgency cues, or fake URLs often used in phishing. AI can also assess sender reputations and flag unusual communication patterns. While it can’t fully prevent human error, it significantly reduces exposure by quarantining suspicious emails and alerting users to risks. As phishing tactics evolve, so does AI constantly learning from past attacks to improve prevention accuracy.
Are AI-based cybersecurity tools available for small businesses? Absolutely. Many affordable, AI-powered security tools are now available for small and mid-sized businesses. These include smart antivirus software, behavior-based threat detection, AI-driven email filters, and endpoint protection platforms that learn from each user’s habits. Cloud-based solutions like Microsoft Defender, SentinelOne, and Sophos offer AI-powered features tailored for SMBs. They provide enterprise-grade security without the need for in-house security teams. With cyberattacks increasingly targeting smaller firms, AI-based solutions are not just accessible they’re essential for staying protected with limited resources.
Can AI replace cybersecurity professionals? AI enhances cybersecurity but won’t replace human experts. While it automates routine tasks like threat detection, data analysis, and basic response, human oversight is still crucial for judgment, strategy, and interpreting complex risks. Cybersecurity professionals work alongside AI to investigate incidents, fine-tune models, and ensure compliance. In fact, AI allows professionals to focus on high-level security architecture, incident response, and governance rather than tedious monitoring. The future lies in a human-AI partnership where AI handles scale and speed, and humans manage context and ethical oversight.
What are some ethical concerns with using AI in cybersecurity? Ethical concerns include data privacy, surveillance overreach, and algorithmic bias. AI systems require vast amounts of data, which can lead to privacy violations if not managed properly. There’s also the risk of false positives that could unjustly flag innocent users or systems. If left unchecked, AI could reinforce existing biases in threat detection or lead to disproportionate responses. Moreover, governments and companies may use AI tools for excessive surveillance. Responsible AI in cybersecurity means transparency, data governance, user consent, and fairness in decision-making.
How do hackers use AI to their advantage? Hackers use AI to create more sophisticated and scalable attacks. For instance, AI-powered bots can probe systems for weaknesses, bypass CAPTCHAs, and execute brute-force attacks faster than humans. NLP models are used to generate realistic phishing emails or impersonate voices using deepfakes. Machine learning helps malware adapt its behavior to avoid detection. These tools allow cybercriminals to attack with greater precision, volume, and deception making AI both a powerful ally and a formidable threat in the cybersecurity battlefield.
What is AI-driven threat hunting? AI-driven threat hunting involves proactively seeking out hidden cyber threats using machine learning and behavioral analytics. Instead of waiting for alerts, AI scans systems and networks for subtle anomalies that indicate intrusion attempts, dormant malware, or lateral movement. It uses predictive modeling to anticipate attack paths and simulate threat scenarios. This proactive approach reduces the risk of long-term undetected breaches. By continuously learning from new threats, AI enables security teams to shift from reactive defense to predictive offense, identifying threats before they do damage.
How can organizations prepare for AI-powered cyber threats? Organizations should invest in AI-powered defenses, regularly update their threat models, and train employees on AI-enhanced risks like deepfakes or phishing. Cybersecurity teams need to adopt adaptive, layered security strategies that include AI-based detection, behavioral monitoring, and automated response. It's also crucial to perform AI-specific risk assessments and stay informed about new threat vectors. Partnering with vendors that use explainable AI (XAI) helps ensure transparency. Finally, fostering a cyber-aware culture across the organization is key because even the smartest AI can’t protect against careless human behavior.
#AI cybersecurity threats#artificial intelligence in security#AI-driven cyber attacks#cybersecurity in AI age#AI-powered threat detection#digital security and AI#AI-based malware protection#evolving cyber threats AI#AI cyber defense tools#future of cybersecurity AI
0 notes
Text
AI in Cybersecurity: Enhancing Threat Detection and Response

The cybersecurity landscape is a relentless battleground, characterized by an ever-increasing volume of threats, the sheer sophistication of attacks, and a critical shortage of human talent. Traditional rule-based and signature-based security systems, while foundational, often struggle to keep pace with polymorphic malware, zero-day exploits, and the sheer volume of alerts generated daily. This is where Artificial Intelligence (AI) steps in, transforming the fight by dramatically enhancing our ability to detect threats and respond with unprecedented speed.
AI is not a magic bullet, but rather a powerful augmentation to human capabilities, acting as a force multiplier for security teams.
The Challenge: Overwhelmed Defenders
Consider the typical Security Operations Center (SOC) analyst. They face:
Alert Fatigue: Millions of alerts from various security tools, many of which are false positives, leading to analyst burnout and missed critical threats.
Sophisticated Attackers: Adversaries use AI and automation themselves, making attacks more stealthy, adaptive, and rapid.
Data Overload: The sheer volume of log data, network traffic, and threat intelligence is humanly impossible to process effectively.
Skill Gap: A global shortage of cybersecurity professionals means teams are often understaffed and overworked.
How AI Enhances Threat Detection
AI excels at processing massive datasets, recognizing complex patterns, and learning from experience – capabilities perfectly suited for modern threat detection.
Anomaly Detection:
Beyond Signatures: Instead of looking for known attack signatures, AI (especially unsupervised learning models) can establish a baseline of "normal" behavior for users, networks, and systems.
Spotting the Unusual: Any significant deviation from this baseline – an unusual login time, an unexpected file access, a sudden surge in network traffic – is flagged as an anomaly, potentially indicating a zero-day exploit or insider threat that traditional tools would miss.
Examples: User and Entity Behavior Analytics (UEBA) leveraging AI to detect compromised accounts or insider sabotage.
Advanced Malware Detection and Classification:
Deep Learning for Malware Analysis: AI models can analyze static (code structure, headers) and dynamic (runtime behavior) features of files at scale.
Polymorphic Malware: AI can identify characteristics of polymorphic malware (which changes its code to evade signature-based detection) by looking at its behavior or structural patterns rather than fixed signatures.
Automated Reverse Engineering: Generative AI can assist in disassembling and understanding malicious code, accelerating the threat intelligence process.
Intelligent Phishing and Spam Detection:
Contextual Analysis: AI goes beyond simple keyword matching, analyzing email headers, sender reputation, language patterns, sentiment, and even visual cues (like fake logos) to determine if an email is a phishing attempt.
Evolving Tactics: Machine learning models can adapt to new phishing campaigns and social engineering tricks much faster than manual updates.
Vulnerability Prioritization:
Risk-Based Approach: Instead of simply listing vulnerabilities, AI can analyze factors like exploit availability, potential impact, asset criticality, and attacker behavior to prioritize which vulnerabilities pose the highest immediate risk, guiding remediation efforts.
Threat Intelligence Augmentation:
Natural Language Processing (NLP): AI can process vast amounts of unstructured threat intelligence from blogs, research papers, dark web forums, and news feeds.
Pattern Identification: Identify emerging attack campaigns, threat actor groups, and TTPs (Tactics, Techniques, and Procedures) that might otherwise be buried in data.
Summarization: Generate concise summaries of complex threat reports for security analysts.
How AI Enhances Incident Response
Once a threat is detected, rapid and effective response is paramount to minimize damage. AI significantly streamlines this process.
Automated Incident Triage and Prioritization:
Contextualization: AI can correlate alerts from disparate security tools, creating a holistic view of an incident and reducing false positives.
Automated Routing: Automatically route incidents to the most appropriate security team or analyst based on severity and type.
Faster Root Cause Analysis:
Log Analysis: AI can rapidly sift through millions of log entries across different systems to pinpoint the initial point of compromise and the full scope of an attack.
Attack Path Mapping: Visualize the attacker's path through the network, helping security teams understand how an attack unfolded.
Automated Containment and Remediation:
SOAR Integration: AI can integrate with Security Orchestration, Automation, and Response (SOAR) platforms to trigger automated actions like isolating compromised endpoints, blocking malicious IPs, or rolling back configurations.
Pre-emptive Actions: Based on detected patterns, AI might suggest or even initiate pre-emptive actions to prevent further compromise.
Intelligent Playbook Generation:
Dynamic Response Plans: Generative AI can dynamically generate step-by-step incident response playbooks tailored to the specific characteristics of an ongoing attack, guiding human analysts.
Post-Incident Analysis and Reporting:
Automated Reporting: AI can compile detailed incident reports, summarizing timelines, affected systems, and remediation steps, freeing up analyst time.
Lessons Learned: Analyze past incidents to identify trends and suggest improvements for future security posture.
The Future: Human-AI Collaboration
AI is not here to replace human cybersecurity professionals, but to empower them. The most effective cybersecurity strategies in the future will be those that foster a collaborative environment where AI handles the heavy lifting of data analysis and automation, allowing human experts to focus on strategic decision-making, complex problem-solving, and the creative intelligence needed to outsmart human adversaries. Embracing AI in cybersecurity is no longer an option; it's a necessity for robust and resilient defenses in our hyper-connected world.
0 notes
Text
Insider threats aAmplified by behavioral analytics
New Post has been published on https://thedigitalinsider.com/insider-threats-aamplified-by-behavioral-analytics/
Insider threats aAmplified by behavioral analytics

In the realm of cybersecurity, behavioral analytics has emerged as a powerful tool for detecting anomalies and potential security threats by analyzing user behavior patterns.
However, like any advanced technology, it comes with its own set of risks—particularly when it comes to insider threats. The very data and insights that make behavioral analytics so effective can also be leveraged by malicious insiders to amplify the damage they can inflict.
How behavioral analytics works
Behavioral analytics tracks user activities—such as login times, access patterns, file usage, and communication habits—to establish a baseline of “normal” behavior.
When deviations from this baseline occur, the system flags them as potential security concerns. This method is particularly useful for identifying sophisticated attacks that bypass traditional security measures.
The double-edged sword of behavioral analytics
While the ability to detect deviations in user behavior is invaluable for cybersecurity, it also presents significant risks if the data and insights generated by behavioral analytics are misused. This is where the danger of insider threats is magnified.
1. Informed malicious insiders:
One of the most significant risks comes from insiders who have legitimate access to behavioral analytics data.
These individuals, whether they are disgruntled employees, compromised insiders, or even careless users, can gain deep insights into what triggers security alarms and how the organization’s monitoring systems operate.
With this knowledge, they can tailor their malicious activities to avoid detection, effectively bypassing the very systems designed to protect the organization.
2. Targeted attacks on individuals:
Behavioral analytics can provide detailed profiles of individual user behavior, including patterns of communication, resource access, and even response times to certain stimuli.
A malicious insider could use this information to target specific individuals within the organization, exploiting their known habits or routines to craft more effective phishing attacks, social engineering schemes, or even direct sabotage.
3. Bypassing security controls:
By understanding the thresholds and triggers of the organization’s security systems, an insider can engage in malicious activities that remain within the bounds of “normal” behavior.
This might involve gradually escalating privileges, exfiltrating data in small increments, or even altering their behavior to blend in with other users who have similar access levels. Over time, these activities can accumulate into significant security breaches without ever raising a red flag.

4. Collusion with external actors:
The risk is further exacerbated if an insider collaborates with external attackers. An insider could share behavioral analytics data with these external actors, allowing them to tailor their attacks to the specific weaknesses of the organization. This kind of collusion can lead to highly sophisticated, multi-vector attacks that are difficult to detect and mitigate.
5. Privilege escalation and abuse:
Behavioral analytics might also reveal patterns in how privileges are granted and used within an organization. A savvy insider could exploit these patterns to gradually escalate their access rights or to gain unauthorized access to sensitive data. Once inside, they can operate with impunity, knowing how to avoid detection based on their understanding of the system’s monitoring capabilities.
Mitigating the risks
To mitigate these amplified risks, organizations must adopt a multi-faceted approach:
Strict access controls: Limit access to behavioral analytics data to only those who absolutely need it and ensure that this access is regularly audited.
Advanced monitoring: Implement monitoring systems that are specifically designed to detect anomalies in insider behavior, particularly those with access to sensitive data or analytics tools.
Data encryption and masking: Secure behavioral analytics data with robust encryption, and consider data masking techniques to limit the exposure of sensitive information.
Zero-trust architecture: Adopt a zero-trust model that continuously validates trust at every stage, ensuring that even insiders are subject to rigorous scrutiny.
Security awareness training: Regularly train employees on the importance of security, with a specific focus on the dangers of insider threats and the critical role behavioral analytics plays in cybersecurity.
Generative AI from an enterprise architecture strategy perspective
Eyal Lantzman, Global Head of Architecture, AI/ML at JPMorgan, gave this presentation at the London Generative AI Summit in November 2023.

Behavioral analytics is a powerful tool in the fight against cyber threats, but it is not without its risks. The amplification of insider threats through the misuse of this technology is a real and present danger.
By understanding these risks and implementing robust security measures, organizations can harness the benefits of behavioral analytics while minimizing the potential for it to be used against them.
In an age where the insider threat is increasingly recognized as one of the most significant security challenges, a proactive approach to safeguarding behavioral analytics data is not just advisable—it’s essential.
Your guide to LLMOps
Understanding the varied landscape of LLMOps is essential for harnessing the full potential of large language models in today’s digital world.

#2023#ai#ai summit#AI/ML#Analytics#anomalies#approach#architecture#Artificial Intelligence#attackers#awareness#Behavior#communication#craft#cyber#Cyber Threats#cybersecurity#data#detection#double#employees#encryption#engineering#enterprise#Enterprise Architecture#exploit#Fight#focus#Full#generative
0 notes
Text
AI-Enhanced Zero Trust for Third-Party Risk Management: Strategic Insights for 2025
Research projects that by 2025, 45% of organizations worldwide will experience attacks on their software supply chains, marking a significant rise from recent years (Cybersecurity Magazine, 2023).
Leon Basin | Strategic Business Development & Account Management | B2B Cybersecurity | AI-Privileged Access Management | Driving revenue growth and building strong customer relationships. Connect with me to discuss how we can enhance your organization’s PAM strategy. The Evolving Threat Landscape in Third-Party Security Research projects that by 2025, 45% of organizations worldwide will…
#Access control and validation#AI-driven PAM#Compliance in cybersecurity#Cyber#Cyber threat detection#cybersecurity#Network#Proactive threat management#Real-time anomaly detection#Scalability in cybersecurity#Supply chain attacks#Third-party security#Zero Trust framework
0 notes
Text
Threat Detection And Response Techniques Explained

In the classic TV show The Office, Dwight Schrute’s infamous fake fire drill is a humorous reminder of the importance of having a serious approach to emergency preparedness. While Dwight’s prank led to chaos and frustration, real-world businesses face genuine threats that require well-thought-out response strategies. Unlike Dwight's ill-conceived drill, companies must be equipped with robust threat detection and response (TDR) plans to handle genuine security risks. These strategies ensure that businesses can effectively manage potential threats, ranging from cybersecurity breaches to physical security risks, by providing comprehensive control over various threat scenarios.
Effective threat detection and response are essential for safeguarding an organization's digital assets and operational integrity. According to Gartner's 2021 Board of Directors Survey, 88% of corporate boards now regard cybersecurity as a critical business risk, highlighting the growing recognition of its importance. TDR involves a systematic approach to identifying, analyzing, and responding to security threats. It encompasses proactive threat hunting, the use of advanced technologies like artificial intelligence and machine learning for detecting anomalies, and a structured response plan to mitigate and remediate threats. This proactive stance helps organizations stay ahead of potential threats and reduces the risk of significant damage.
Key techniques in TDR include Security Information and Event Management (SIEM), which aggregates and analyzes log data to detect deviations and potential threats in real-time. The MITRE ATT&CK Framework provides insights into attacker techniques, aiding in the development of effective defensive strategies. User and Entity Behavior Analytics (UEBA) monitors and analyzes user activity to detect unusual behavior. Ransomware protection solutions automatically identify and block ransomware activities, while Next-Generation Firewalls (NGFWs) offer advanced network traffic control. By integrating these techniques, organizations can enhance their ability to detect, analyze, and respond to threats, thereby strengthening their overall security posture and resilience against cyber-attacks.
Read More - https://www.techdogs.com/td-articles/trending-stories/threat-detection-and-response-techniques-explained
0 notes
Text
What Is Cloud Security Posture Management (CSPM)?

Did you have a playground in your neighborhood?
Playgrounds are a haven for kids, filled with swings, slides, and sandboxes. Yet, most playgrounds also have a sturdy fence to keep children safe from the streets and other dangers. Similarly, in the era of cyber-attacks, businesses need to protect their data stored in the cloud with strong security measures. This is where Cloud Security Posture Management (CSPM) comes in, acting as a protective barrier for your digital playground.
Remember the days of bulky servers and long software installations? Today, cloud computing offers scalable, flexible, and cost-efficient solutions. However, this power comes with the responsibility of securing sensitive data, like financial records and customer information. Misconfigurations and compliance issues can expose your cloud to cyber-attacks. So, how do we navigate this complex landscape? Enter Cloud Security Posture Management.
What is Cloud Security Posture Management (CSPM)?
As businesses use multiple cloud services, keeping everything secure becomes challenging. CSPM continuously scans your cloud infrastructure for vulnerabilities and misconfigurations, such as improper access permissions or outdated software. By identifying these issues, CSPM helps businesses proactively address them, ensuring a robust security posture in a multi-cloud environment.
Why Is Cloud Security Posture Management Important?
Running a business is like running a city, constantly growing and needing security. CSPM provides this security in several ways:
Visibility Across Clouds: CSPM reveals weaknesses or misconfigurations, preventing data breaches.
Prioritization: It helps prioritize real security threats, cutting through the noise of multiple warnings.
Compliance Challenges: CSPM helps meet cloud compliance standards, reducing legal risks.
Efficient Operations: It bridges the gap between speed and compliance, allowing secure and quick development.
Data Breaches: CSPM catches security gaps before they become major problems, preventing data loss and financial issues.
How Does Cloud Security Posture Management Work?
Connect To Your Cloud Environments: CSPM solutions connect to your cloud providers' APIs, offering visibility without agents.
Get Visibility: They provide visibility into your cloud assets, configurations, and events.
Identify Misconfigurations & Compliance Violations: CSPM tools compare your cloud resources against best practices and compliance standards, alerting you to misconfigurations.
Detect Threats: CSPM continuously inspects logs and events for threats and anomalies.
Remediate Issues: CSPM provides remediation instructions and can integrate with external platforms for automated responses.
Monitor & Report: CSPM tools help track and report risk trends and compliance levels over time.
To Sum Up
CSPM embodies the principle that "an ounce of prevention is worth a pound of cure." It provides visibility, detects threats, ensures compliance, and corrects misconfigurations. By leveraging CSPM, businesses can protect their cloud environments, uphold regulatory standards, and enhance their security posture. In today's digital landscape, CSPM is crucial for safeguarding valuable data and maintaining the integrity of cloud-based operations.
So, what are you waiting for? Secure your cloud infrastructure right away!
0 notes
Text
DPxDC Ignorantia Neminem Excusat
(Ignorance excuses no one, lat.)
"Commissioner."
Jim Gordon doesn't jump. They are years and years into this rodeo, he's stopped actually jumping at Batman's silent approach a long time ago. Yet, Bruce still notices the way his shoulders twitch just the tiniest bit, and his hand makes an aborted motion to his gun holster. Still got it.
The man turns around. Bruce can see the 'must you always do that?' in his slightly narrowed eyes. He presses his lips tightly together in order to not smirk: Batman doesn't do that, even if it's admittedly funny to see the seasoned Commissioner get spooked every time.
"There's a kid that wants to speak with you."
Bruce frowns. A kid that warranted a BatSignal? Not that he minds, but this is highly unusual for several reasons; however, Jim is not the kind of man that would fall for puppy eyes of any level, so it must be something more important than an autograph session or a victim of any of the recent cases.
Besides, the way Commissioner worded it implies that the kid, whoever they are, requested Batman specifically.
"He is a hacker," Jim puts both his hands in the pockets of his coat — he is either cold or uncomfortable, and Bruce highly suspects it's both. What's more, he starts to understand why. "I'm sure you're aware we were trying to track the person responsible for the few recent cyber attacks on GCPD servers," Jim glances at him, and Bruce nods. He is aware, yes, but the case was low-priority — it wasn't even an attack, really, someone just accessed the system foregoing the passwords and clearance levels, went through a few files, seemingly at random, and did a fairly decent job of hiding their traces. Bruce would have even thought it was Tim, if this happened a few years ago, when the boy was just learning the ropes.
Commissioner sighs and looks away, "But when we brought him in, the boy said he will only speak to you, and none of us have been able to make him say a word since." He pauses, a grim kind of expression on his face, "This was six hours ago."
Bruce is grateful for the way his cowl hides how his eyebrows raise. There are hundreds of scripts officers, detectives, and social workers can use to establish contact. Quite a lot of them could be attempted in the span of six hours.
Whatever the kid wants to tell him, Bruce decides it's worth a try. If not anything else, he can at least admire the sheer stubbornness.
—×—×—×—
The kid sitting in the interrogation room looks... younger than Bruce expected. Fifteen, maybe sixteen. He is dressed like any other homeless kid in Gotham — a hoodie and a jacket over it, jeans that look a size too big on him, sneakers with mismatched shoelaces — but he clearly hasn't been out in the streets for that long. His hair is braided into cornrows, and it looks professional, even if the roots have grown out so now it's just messy. What's more, he is missing that telltale wariness in his posture that Bruce has seen in every other street kid that has been brought into a police station. They always slouch and curl into themselves.
This boy is sitting with his back straight. Yet, there's a tension in his body that Bruce can only associate with a battle stance — give him the slightest reason, and the kid will lunge.
He steps into the room.
The boy — he hadn't given a name, and there wasn't a single ID on him — zeroes on him instantly. His eyes are a very pale, almost translucent green: a rather strange feature for a black-skinned person, genetically speaking, but Bruce doesn't dwell on it. Yet.
But then, the face recognition program comes up empty.
As in, 'there's not a trace of this person's prior existence' empty. Not a single camera footage, no records or reports of missing, no pictures, no social media, nothing. Bruce frowns.
"Hi," the kid says, his voice raspy, "My name is Tucker Foley. According to the government, I don't exist, so if your recognition program doesn't find anything on me, that's why."
Bruce doesn't say anything. Tucker wanted to speak with him, and previously, he was only merely intrigued by that request. However, as of right now, he wants to hear everything the kid has to say before asking any follow-up questions.
Because that always present, cautious and bordering on paranoid voice in the back of his mind tells him he is about to get into something way more serious than he expected.
Tucker moves — he kept both his hands on the table, palms open and visible, but now he closes one into a fist. Although, before Bruce can react to it, he opens it again. A small, the size of a flash-drive, dimly glowing green object rests inside.
"Do you know what this is?" The boy asks. He hasn't looked away from Batman's face once; Bruce is not even sure he blinked at all since he entered the room. Come to think of it, even with his tense, rigid posture, Tucker is too still, almost unnervingly so.
Bruce glances down to the boy's hand.
"Yes," he answers curtly, and there it is, the smallest shift in Tucker's face: he clenches his jaw like he's trying to hold the words inside his mouth. Bruce doesn't like it.
"What is it?" Comes the next question, but it's not curiosity that prompts it. It's a test of some sort. Bruce likes that even less.
"A power source," he decides on a neutral answer, not entirely certain what the boy is expecting to hear.
It seems to be a wrong answer because for the first time, Tucker's emotions slip from under his mask, and he takes a sharp breath in, looking like Bruce had just slapped him across the face. It lasts only a moment — Tucker closes his eyes for a moment, slowly exhales, and speaks again, calm and focused once more.
"And what exactly powers it?"
It's an important question, judging by the desperate, searching look in Tucker's eyes. His hands are not shaking, and there are no visible signs of distress, but for some reason, Bruce just knows that the boy's whole life seems to depend on the answer.
But.
"It's classified." Bruce doesn't take his eyes off the boy, but he still fails to see when he gets to his feet; the movement is quicker than the blink of an eye. All he knows is the aftermath of it, the screech of the chair legs on the floor and the loud slam of Tucker's palms on the table.
"Fuck the classified!" The boy yells, his face twisting in an awful mix of anger, hurt and a broken, terrified sort of hopelessness that almost breaks Bruce from the inside. "I need to know what they've told you, I have to- Tell me you think it's just a battery! Tell me you've never broke one to see what's inside, tell me you believe in science! They've showed you the research, didn't they?" Tucker's voice, so agonizingly different from the composed way he was talking before, breaks into a sobbing, almost hysterical laugh. His pale eyes are wide open and almost panicked, searching Batman's face for something he is not sure he can find.
"Tell me you've never seen one being made," this time, the boy doesn't yell, he whispers, his breath hitching and his knuckles white. "Please," he adds a moment later, and Bruce knows this kind of plea.
It's the plea of someone who is begging for the world to have mercy on them. A plea of a boy standing on their parents' grave, a plea of a man kneeled in front of his son's corpse.
Bruce swallows the bitter taste on the back of his tongue and takes a step closer. He sees the boy in front of him lean back and bend his knees, like bracing for impact, but he answers before any more misunderstandings can occur.
"I have seen the research. It provided enough information that I've never investigated further," he offers, and Tucker's shoulders slump like months and months of living in a constant state of fight-or-flight leaving his body all at once. Then, the boy's hands start trembling just slightly.
"Really?" He quietly asks, his eyes still glued to Batman, and there it is, the hesitant, uncertain hint of hope in his voice.
Bruce suddenly feels like not only this talk will be much, much worse than he ever feared, but also like in the end this will be another one of the things he will be blaming himself for. Things he could have prevented if he just tried a little harder.
"Really," he nods, taking a seat opposite from Tucker. "So explain what I've missed."
The boy keeps looking at him for a few more seconds, like trying to x-ray his thoughts for any sign of a lie. But then he blinks — for the first time, maybe — and rubs his face with his palm before all but dropping back in his own seat.
"Okay," he breathes out, evidently trying to collect himself and go back to the strong, focused self, "Okay."
[ part 2 -> ]
#danny phantom#dpxdc#dc x dp#batman#bruce wayne#tucker foley#commisioner gordon#the idea was that giw uses ghosts as batteries#promoting them as a source of clean energy#but they are essentislly just trapping ghosts inside specifically designed containers and sell them#i may or may not write a part two of this#where danny is the power source for the watchtower#however if this sparks an inspiration for a completely different kind of angst for you#feel free to add on#angst#giw#tucker had a very rough couple of months#he escaped amity and made it all the way to gotham in hopes that batman would help him#because hes definitely liminal so he should care because anti-ecto acts apply to him and his family#also this was off-screen but tucker leaving traces for gcpd to find him was intentional#he needed to get the attention#cork prompts
2K notes
·
View notes
Text

The light is MINE.
Small story underneath Readmore. Please reblog instead of liking!
Robotnik's latest plan to try to get rid of Sonic, and take over the world, had involved the creation of space-time vortexes, using the a gemstone known as the "Warp Topaz". Reaching into other realities to gather resources for his plans, and to trap Sonic inside a dimension where he'd be unable to thwart his plans.
This idea backfired the moment it was put into motion. For, unbeknownst to him, in a different reality, a beast of famine and darkness could feel the ripples his machine left in time and space. In a last attempt to secure it's survival, the heinous beast tore a hole from it's home dimension and into Robotnik's machine.
Before the hedgehog Robotnik oh-so dreaded could do as little as drop a snarky comment, the machine's alarms blared out loud, sending constant distress signals to the scientist's control panel, as it detected an unknown entity crawling through it's insides.
The next thing anyone knew was that Sonic began to fight this mangled monstrosity made of crystal bones. A walking corpse of a higher being, desiring nothing but to sink it's fangs into the hedgehog. Each punch from this thing felt terrible, the pain this pitiful monster felt was being inflicted into Sonic.
The fight went on for hours on end, the beast attacked relentlessly, not allowing the hedgehog even a single second to catch his breath, and it didn't seem to have intentions to stop any time soon either. Friends and curious onlookers had came to his aid a long time ago, but neither Sonic nor the beast wanted anyone nearby.
A knot tied deep inside Sonic, the way it felt to be attacked by this monster, he didn't want his friends to be forced to deal with it. It reminded him so much of the cold, numbing, painful, scalding, overwhelming pain from cyber corruption. And yet, this felt so much worse, according to him.
The moment Tails tried to approach Sonic, holding his Miles Electric in the end, exclaiming he had found a way to deal with this unknown thing, was... the end. The monster locked it's "eyes" on the fox, and prepared to attack. Sonic wouldn't let any harm come to his closest friend, his sibling...
So he took the hit for the fox. And this time, the beast sank it's claws deep into the hedgehog's body. Finally, after hours of constant fighting, time seemed to move slowly, the hedgehog tumbled back, feeling warm liquid flow down from his chest, a buzzing ring sound echoed in his ears, he couldn't tell what everyone was saying anymore.
After hours of battle, the hedgehog tripped down into the arms of the beast, and was devoured. Light expanded outwards, like an explosion, the moment Sonic and the beast made contact, light that shone brighter than anything any of them had ever seen. Soon, where once two beings stood, now only one entity remained: Golden fur covered its body, golden as the brightest of suns; dark crystalline armor adorned its form, as black as the darkest of nights.
It took a single step forward before roaring in anger, crying out in pain, screaming in agony. Its hunger for light was not yet quenched.
On that day, the hero of this world, the beacon of hope in the heart of every mobian, was extinguished. The torch of the vessel of chaos was never passed down, instead, its never-yielding flame was devoured by the dark maws of the beast from beyond space and time.
On that night, in roars and cries, it pledged to subdue, and consume, all the light in this universe, to punish humanity for it's hubris, for the inhabitants of this world were not free of sin in its eyes. Desiring light, power, and energy. Playing god, they had drained another one like itself, and destroyed it, forgotten it, erased it.
Now they all would pay the ultimate price.
Travelers from the world this creature first emerge would name this new being fueled by revenge "UB-Chaos". Also known as...
Entropy Spine Necrozma.
#digital art#sonic fanart#sonic art#sonic fan art#pokemon fanart#necrozma#pokemon#pokemon art#pokemon crossover#sonic crossover#pokemon usum#digital drawing#artists on tumblr#sonic the hedgehog#sth#sth fanart#sth au#|| the jackal's art ||#pkmnart#pkmn fanart#pkmn au#pokemon au
154 notes
·
View notes
Text
Tactical Crocs & Emotional Warfare
F!Reader x Gojo Satoru x Nanami Kento
Previous Oneshot Chapter [Tumblr/Ao3] | Main Series [Tumblr/Ao3]
A/N: When your security team costs more than a small country's GDP but the real threat is a raccoon with a Hermès addiction. Enjoy this slice of domestic terrorism (ft. Gojo’s tactical Crocs). No spoilers, but someone does get scolded via Chopin.



Int. Private Security Room—Night—14 Hours To Cameras Up
The koi pond feed flickers. A baby sock drifts across the surface. Nobody flinches.
Half the screens are silent surveillance footage: nursery, koi pond vault, her lower office, the terrarium room that used to be a guest bath. Takahashi (the raccoon, not the CFO) sleeps curled on a miniature futon in a separate window—one paw flung over a satin pillow like royalty.
The red alert blinks in the upper left corner: VOGUE JAPAN CREW ARRIVES. TO BE HELD IN GREEN ROOM.
Nanami Kento doesn’t look up. His pen glides over a set of architectural schematics—his third revision in as many hours. He’s in matte black tactical Kevlar (no one knows why at this hour), sleeves rolled to the forearms, sorcery glasses glinting under sterile lighting. There’s a faint ink smudge on his wrist. He’s furious about it.
Gojo Satoru sits across from him in a Hello Kitty hoodie and tactical Crocs, chewing lychee Pocky like he’s running hostage negotiations out of a Daiso. His wayfarers reflect the screen showing his stolen blindfold around Takahashi’s neck like he’s cosplaying “Bandit” in his sleep. The six-eyes wielder looks like the kind of genius whose brain can calculate missile trajectory mid-nap but will forget to refrigerate breast milk.
Around them, the highest-paid security personnel on the Pacific Rim. A blend of private military, cyberwarfare analysts, and cursed-artifact consultants. Some sip espresso from tactical thermoses. Others pretend they’re not being paid eight figures plus to protect a non-sorcerer pregnant woman, two war criminals, and a possibly sentient raccoon.
The Executive Protection Team (Core Security) had primarily been assembled by Megumi, and they relocated with you to Japan after your marriage, remaining fiercely loyal but now having an equal number of Nanami and Gojo’s people, ex-Jujutsu Teachers (sorcerers).
Former JSDF Special Forces Operatives (1st Airborne Brigade or Special Operations Group) (¥60M+ each).
Japan's equivalent to Navy SEALs/Delta Force, trained in high-risk protection.
Ex-Metropolitan Police Department (MPD) Security Police (SP) Officer. (¥50M+ each).
SP protects Japanese VIPs (e.g., PM, royals). Only available if retired early. Know all police protocols to avoid legal issues.
Cursed Energy Security Specialists Team (for Sorcerer-Level Threats).
Ex-Jujutsu Tech Professors (Non-Gojo Clan, Independent) (¥100M+ each).
Detects/neutralizes curses without relying on Jujutsu High.
Limitation: Hard to find; must be lured with extreme pay.
Cursed Artifact Security Consultant (¥80M+ each).
Prevents cursed objects from entering the home (e.g., "gifts" from enemies).
Background: Former curse-user turned private sector.
Cyber/Electronic Warfare Team (For Tech CEO Threats).
Ex-Unit 8200 (Israeli Cyber Intel) + NSA Hacker (¥120M+ each).
Best in the world for preventing corporate espionage/blackmail.
Loophole: Hired as a "consultant" to avoid gov restrictions.
Japanese Cyber Defense Force Veteran (¥60M+ each).
Knows domestic cyber laws inside out.
Perk: Can legally bug your own home (with consent).
Logistics & Emergency Extraction Team.
Private Military Contractor (PMC) Pilot (Ex-USAF/JSDF) (¥70M+ each).
On standby with a private jet/helicopter for emergency medevac (pregnancy risks).
Loophole: Based in international waters (Okinawa) to bypass Japanese airspace laws.
Medical Security Specialist (Ex-SAS Medic) (¥50M+ each).
Trauma Care + can extract during a curse attack.
Perk: Licensed to carry restricted meds (e.g., sorcerer-grade painkillers).
Most of them report to her.
The wife.
CEO.
Third trimester.
Currently asleep, head tilted into Nanami’s neck like a sleepy heat-seeking missile, his other arm absently braced around her to stop her from falling off the ergonomic stool she refuses to replace.
A hushed voice cut through the tension. “She’s got a bounty on her.”
Nanami slammed a folder onto the table hard enough to rattle the coffee cups, his sleeves rolled up to expose forearms corded with muscle. “If we die, Protocol A-47 activates. She goes to the koi pond vault. No exceptions. Tranquilize her if necessary.”
The ex-fighter pilot—a woman with a scar bisecting her eyebrow—leaned back in her chair, flicking a toothpick between her teeth. “We have tranquilizers because she once roundhouse-kicked a logistics officer during a VR Mortal Kombat session. Broke his nose.”
Gojo licked sugar from his thumb and added, “Double-layer barrier on the nursery and Takahashi. If something happens to that raccoon, I’m flattening a country. I won’t say which. It’ll be a surprise.”
The NSA hacker, a twitchy man with dark circles under his eyes, flinched when the raccoon sneezed. “Why does the raccoon have his own panic room?”
Keji—sleek in his silk shirt, biceps straining the fabric as he crossed his arms—didn’t blink. “He has three. One is lined with titanium. One is wallpapered with Gojo-san’s baby photos. We do not enter it.”
Nanami’s pen paused mid-note, his gold wedding band glinting. “She’s not a combatant. She can’t defend herself against c-users.”
Gojo’s smirk vanished, his voice dropping to something darker. “And now, her bounty matches mine.”
The silence in the room was palpable, a live wire. Takahashi, curled in his heated pet bed, let out a tiny snore.
The SAS medic—a woman with a coiled braid and a grip that could crush tracheas—rubbed her temples. “We’re glorified nannies. Emotional support detail. Decoys.”
Nanami didn’t look up. “In case both of us die, Keji initiates the escape route. She doesn’t know about it. She already has insomnia. And stop calling it Project: Dead Dads.”
A former JSDF SOG operative, a wiry man who looked like he hadn’t slept in days, swallowed audibly. “Do we evacuate Takahashi?”
Gojo’s fingers stilled on his watermelon lollipop wrapper, the crinkle deafening. “What did I just say.”
Keji turned toward the security feeds, his profile sharp enough to draw blood. “He has a private jet. Smaller than Madame’s. Faster. I’m not authorized to speak why.”
Nanami’s glasses caught the light as he flipped a page. “There are four exit tunnels. One goes through a matcha café. Another leads under the koi pond, keyed to her retinal scan and Takahashi’s scent profile.”
The ex-jujutsu sorcerer—an older woman with ink-black nails and a lazy, lethal posture—stretched like a cat. “I taught metaphysics at Yale.”
Gojo’s grin returned, wider. “Now you guard a raccoon with a Hermès sponsorship and a platinum AmEx. Life’s a ride.”
An ex-MPD VIP guard, a hulking man with a baby face, muttered into his comms. “I used to run fintech. Now I sterilize breast pumps and sleep beneath a floating shikigami terrarium.”
Ignoring him, Nanami’s thumb brushed the edge of his wedding ring. “In an active threat, she and Takahashi go in the bunker. Keji, you emotionally stabilize her. Feed the raccoon his lavender sardine paste.”
Keji’s jaw tightened, leather gloves creaking. “It’s handmade. Infused with omega-3 and respect. I recite Edith Piaf while preparing it.”
Gojo twirled his sunglasses. “He even sings La Vie en Rose during thunderstorms.”
The lights flickered. No one moved.
Takahashi’s screech echoed down the hall—a sound like an opera-trained kettle being murdered.
Nanami didn’t react. “Seventy-five minutes. That’s all they’re allowed in the residence. Treat this as a red-tier civilian intrusion. Assume bugs, surveillance, and attempted breaches.”
Gojo licked his lollipop slowly. “And no touching the raccoon. She said she’ll cancel the shoot if they mess with his whiskers.”
Every head nodded. No one questioned it.
The upgraded chief logistics officer—a woman with a steel-gray bob and a sniper’s stillness—tapped her tablet. “We’ve staged all bathrooms, prepped diversionary designer fragrances, and disabled motion sensor lighting in the koi corridor. It made the raccoon look too... strategic.”
Keji, adjusting his gloves, coolly added, “Takahashi is sentient. And emotionally fragile.”
Nanami’s voice was sharp as a blade. “Staff wears navy. Press wears tags. Anyone untagged after the 42-minute mark: detain.”
The ex-Metropolitan Police officer, a woman built like a brick wall with a matching smirk, raised a brow. “If questioned?”
Gojo’s teeth flashed in a grin. “Blame jet lag. Or say they threatened the raccoon and his wildlife habitat.”
Another nod followed, deadly serious.
Nanami’s watch gleamed as he switched tabs. “Lighting rig pathways are pre-approved. No one enters the nursery, gaming room, or her lower office. Those are closed sets. If they insist—deny with polite aggression.”
Gojo pointed at the NSA tech, who shrank in his chair. “If they get pushy, hand them the fake NDA. The one with clause 14 about raccoon-based defamation lawsuits.”
The tech, a freckled kid who looked barely old enough to be here, stammered, “We scrubbed her images from the mob lynch incident off the internet. All reverse image searches redirect to a red fox in a Dior scarf.”
Keji’s mouth curled into a smirk. “We paid extra for that one. The fox is a union.”
The medical lead—a woman with biceps that could crack walnuts and a glare to match—slapped her protocol sheet down. “She’s on four prescriptions. None are to be mentioned. If she starts to spiral—”
Keji’s smile was all edges, his gloved fingers tapping once against his biceps. “I’ll realign her using the 'accidental' footage of Nanami-san cooking shirtless last week. It’s preloaded. Subtitled. And scored with Chopin.”
Nanami’s pen froze mid-air. “That wasn’t for anyone.”
Gojo, sprawled across two chairs, licked his lollipop with deliberate slowness. “It was for me. Obviously.”
An ex-JSDF pilot—a woman in her 50s with salt-and-pepper hair and a posture that screamed combat-ready—adjusted her earpiece. “Chopper’s on standby. Six-minute extraction from Okinawa. The vault opens in two. If she won’t move, the fetal monitor’s embedded in her gaming chair.”
Nanami's wedding band caught the light as he massaged his temple. “She won’t move. Not if they bring up Gojo’s hair again.”
Gojo’s sunglasses slid down as he jerked upright, voice dripping with offense. “My hair is real. Shut up.”
The cybersecurity lead asked, “Do we allow footage of the nursery?”
Nanami didn’t hesitate, his voice a steel door slamming shut. “No. The twins will not be monetized.”
Gojo twirled his sunglasses, his grin razor-thin. “Also, the wallpaper isn’t finished, and she’ll have a hormonal breakdown.”
The MPD veteran, a barrel-chested man with a voice like gravel, scratched his stubble. “What if they film the raccoon singing? The sound’s been... described as ‘emotional.’”
Keji turned to the camera, his smirk all quiet arrogance. “He sings behind silk. You hear him only if he allows it.”
Nanami’s finger traced the exit tunnel diagram, his glasses glinting like a warning. “Only Keji knows all exit codes. If she starts crying—”
Another SAS medic—a woman with a shaved head and a stare that could curdle milk—didn’t blink. “We sedate her and blame prenatal yoga. Like last time.”
The mood in the room remained tense.
Nanami’s knuckles went white around his folder. “We protect her. We protect the twins. You protect that damn raccoon like he’s the crown prince of France. If she stubs her toe and Vogue sees it—this entire household is done.”
Another NSA hacker, a young woman fixing her gloss, muttered under her breath. “She has three degrees, and one of them is in an unknown field. So I’m pretty sure she could crush this whole network if she wanted to.”
Keji leaned back, satisfaction rolling off him in waves. “She has. Twice.”
Gojo chewed the last of his lollipop. “Accidentally.”
The lights flickered—once.
“One lipstick smear on the marble. One wrong tote bag. One smug remark about ‘modern poly households’—I will end this.” Nanami’s final note was a scalpel to the throat, but his gaze softened as he glanced at his wife dozing on his shoulder, her cheek smooshed against the Kevlar vest.
Gojo rose, stretching with all his lazy grace, kissed Nanami's temple just to annoy him before scooping their wife into his arms like she still weighed nothing. Her sleepy “mmf?” earned a chuckle as he adjusted the hem of her shirt over her bump as she put her arms around him. “Smile for the cameras tomorrow, people,” he purred to the team, but his wedding ring-adorned finger brushed her knee—a silent you’re safe—as he carried her toward the bed, her breathing already muffled against his shoulder.
The private feed cut.
The koi pond glowed an eerie blue.
The single baby sock is still floating over it.
Video Title Card: The Pregnant CEO, The Two Husbands, and The Raccoon With Executive Privilege.
---
A/N: If you laughed, cried, or now fear Nanami’s spreadsheet skills, scream at me in the comments. (Gojo’s ego needs the validation. Takahashi demands tribute in lychee Pocky.)
Previous Oneshot Chapter [Tumblr/Ao3] | Main Series [Tumblr/Ao3]
Next Chapter Gojo Satoru’s Public Display of Wife Theft [Tumblr/Ao3]
All Works Masterlist
Beta - @blackrimmedrose
#jujutsu kaisen#jjk#nanami kento#gojo satoru#kento nanami#jjk nanami#jjk x reader#jujutsu kaisen x reader#satoru gojo#nanami#jjk fluff#jujustsu kaisen x reader#jjk fic#nanami smau#gojo smau#jjk angst#third wheeling your own marriage#third wheeling#nanami x reader x gojo#nanami x gojo#nanami x reader#nanami x you#nanami x y/n#gojo x nanami#gojo x reader#gojo x you#jjk crack#gojo crack#sassy nanami#jjk staff
40 notes
·
View notes
Text
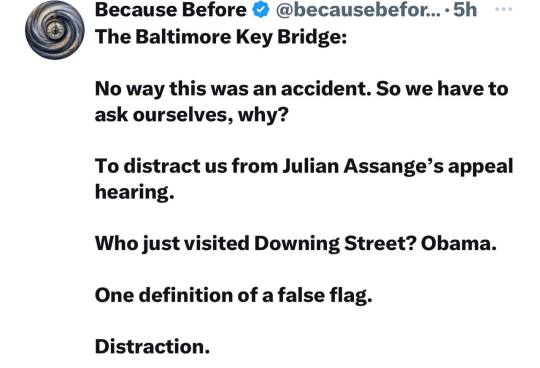
Was the Baltimore Bridge attacked? 👇
The Baltimore bridge collapse was an “absolutely brilliant strategic attack” on US critical infrastructure - most likely cyber - & our intel agencies know it. In information warfare terms, they just divided the US along the Mason Dixon line exactly like the Civil War.
Second busiest strategic roadway in the nation for hazardous material now down for 4-5 years - which is how long they say it will take to recover. The bridge was built specifically to move hazardous material - fuel, diesel, propane gas, nitrogen, highly flammable materials, chemicals and oversized cargo that cannot fit in the tunnels - that supply chain now crippled.
Make no mistake: this was an extraordinary attack in terms of planning, timing & execution.
The two critical components on that bridge are the two load-bearing pylons on each end, closest to the shore. They are bigger, thicker and deeper than anything else. These are the anchor points and they knew that hitting either one one of them would be a fatal wound to the integrity of the bridge.
Half a mile of bridge went in the river - likely you will have to build a new one. Also caused so much damage to the structural integrity of the bottom concrete part that you cannot see & won’t know until they take the wreckage apart. Structural destruction is likely absolutely.
Attack perfectly targeted.
“They have figured out how to bring us down. As long as you stay away from the teeth of the US military, you can pick the US apart. We are an arrogant and ignorantly - lethal combination. Obama said they would fundamentally change America and they did. We are in a free-fall ride on a roller coaster right now - no brakes - just picking up speed.”
The footage shows the cargo ship never got in the approach lane in the channel. You have to be in the channel before you get into that turn. Location was precise/deliberate: They chose a bend in the river where you have to slow down and commit yourself - once you are committed in that area there is not enough room to maneuver.
Should have had a harbor pilot to pilot the boat. You are not supposed to traverse any obstacles without the harbor pilot.
They chose a full moon so they would have maximum tidal shift - rise and fall. Brisk flow in that river on a normal day & have had a lot of rain recently so water was already moving along at a good pace.
Hit it with enough kinetic energy to knock the load-bearing pylon out from under the highway - which fatally weakens the span and then 50 percent of the bridge fell into the water.
All these factors when you look at it - this is how you teach people how to do this type of attack and there are so few people left in the system who know this. We have a Junior varsity team on the field.
Tremendous navigational obstruction. Huge logistical nightmare to clean this up. The number of dead is tragic but not the whole measure of the attack.
That kind of bridge is constantly under repair - always at night because there is so much traffic and they cannot obstruct that during the day. So concern is for repair guys who were on foot (out of their vehicles) working who may now be in the water - 48 degrees at most at this time of year.
When you choke off Baltimore you have cut the main north-south hazardous corridor (I-95) in half. Now everyone has to go around the city - or go somewhere else.
To move some of that cargo through the tunnel you may be able to get a permit but those are slow to get and require an escort system that is expensive and has to be done at night.
For every $100 dollars that goes into the city, $12 comes from shipping. Believe this will cripple the city of Baltimore at a time when they do not have the resources to recover.
- Lara Logan
The traffic issue was mentioned in this 👇 post
Maybe we have to dig deeper into this Bridge collapse further. Could it be a deeper issue? What's in those shipping containers? Who owns the ship?
Is it for this 👆
It has been 3 years and 3 days since the Evergreen blocked the Suez Canal. Does the number 33 mean anything?
Was this a "Black Swan Event?"

I'm just asking questions? 🤔
#pay attention#educate yourselves#educate yourself#knowledge is power#reeducate yourself#reeducate yourselves#think about it#think for yourselves#think for yourself#do your homework#do some research#do your own research#ask yourself questions#question everything#black swan#distraction#save the children#save our children#save humanity#crimes against humanity#you decide
184 notes
·
View notes
Text
Deception Technology Market: A Comprehensive Guide
In the ever-evolving landscape of cybersecurity, organizations are continually searching for innovative ways to stay ahead of malicious actors. One such revolutionary approach gaining traction globally is Deception Technology. This proactive security strategy involves deploying decoys, traps, and misleading data within a network to lure, detect, analyze, and mitigate cyber threats in real time.…
View On WordPress
#AI in Cybersecurity#Cyber Risk Management#Cyber Threats#cyber-attacks#cybersecurity#cybersecurity deception#deception cyber security#deception in cyber security#Deception Technology#Deception Technology Market#Information Security#security deception#Threat Detection
0 notes
Text
Microsoft Cyber Attack Assessment of the I/P Conflict
This was sent my way by a cyber security colleague recently. Microsoft put out an assessment of cyber attacks associated with the I/P conflict and determined that the IRI has had a massive hand in them. Yes we know Russian bots are present whenever this type of conflict happens, but to have a full breakdown of what IRI backed groups (government and non-government) are actively spreading misinformation and committing attacks is good to know. I find this chart particularly interesting.
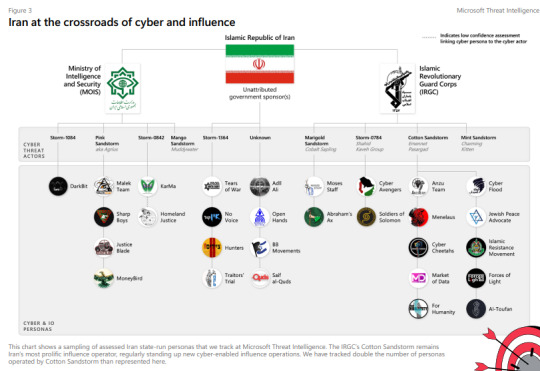
Fig. 1. Chart depicting the various active cyber groups and their personas online. Cotton Sandstorm is the most active group and if you look on the far right of the chart you will see that they have Jewish Peace Advocate listed as one of their online personas. The report indicates that there are active IRI cyber groups masquerading as Jews and/or Jewish groups online and spreading misinformation (keep in mind this report is from February 2024 and we don't have a public report regarding the continued cyber attacks and misinformation campaign). From the report:
During this phase, Iran’s influence activity used more extensive and sophisticated forms of inauthentic amplification. In the first two weeks of the war, we detected minimal advanced forms of inauthentic amplification—again suggesting operations were reactive. By the third week of the war, Iran’s most prolific influence actor, Cotton Sandstorm, entered the scene launching three cyber-enabled influence operations on October 21. As we often see from the group, they used a network of social media sockpuppets to amplify the operations, though many appeared to be hastily repurposed without authentic covers disguising them as Israelis. On multiple occasions Cotton Sandstorm sent text messages or emails in bulk to amplify or boast about their operations, leveraging compromised accounts to enhance authenticity.
...
Iran’s targeting of Israel during the Israel-Hamas war has increasingly focused on stoking domestic conflict over the Israeli government’s approach to the war. Multiple Iranian influence operations have masqueraded as Israeli activist groups to plant inflammatory messaging that criticizes the government’s approach to those kidnapped and taken hostage on October 7.17 Netanyahu has been a primary target of such messaging, and calls for his removal were a common theme in Iran’s influence operations.
...
There's a lot to the report and I highly recommend you read it. Hopefully another one comes out, apparently these are biannual, this summer with a spring time assessment. Please keep in mind that this war has had a ton of propaganda and bad actors masquerading as good ones. There's so much misinformation out there regarding Israel and Jews that is being amplified by people who want us dead, and when we point this out we're quickly silenced. But more and more the evidence supports the idea that manipulation and misinformation is playing a larger role.
And we told you.
https://www.microsoft.com/en-us/security/security-insider/intelligence-reports/iran-surges-cyber-enabled-influence-operations-in-support-of-hamas#section-master-oc1474
125 notes
·
View notes
Text

Leon Kennedy x Gender Neutral! Reader - The story is on Wattpad too.
Summary: Two rival agents are tasked to go undercover together to retrieve information on a security breach. The mission will span over a few months, in which they have to share an apartment and pretend to be a couple.
Tags: Enemies To Lovers, Slowburn, Forced Proximity, Fake Dating.
Chapter One - Animosity. 3008 Words.
Abundantly, the rainfall patters against the shrouded windows, the humidity a testament to the drizzly, somewhat melancholic weather outside the conference room, wherein there's an all too familiar stillness in the air. Government files are orderly dispersed across the mahogany table, itemizing information regarding the content of the forthcoming assignment shared between none other than Leon Kennedy and yourself. Cursing inwardly to yourself about the whole ordeal, you figure there's no point in letting your mutual animosity with one another get in the way of securing major information, which is the objective of said classified mission. What an uncomfortably warm room you find yourself confined within, the aura almost smothering - and you're sure that you can't be the only one capable of acknowledging such a fact. The sound of the clock ticking acts as a backdrop to the almost entirely taciturn space, as the two of you stand in distant proximity, refusing to avert your gaze from the queerly placed lectern, seeming as if it had been taken directly from a University classroom. It seems ridiculous, two grown adults behaving as if they were youths in detention because of one another; the strangely nostalgic feeling of wanting to be anywhere else but with your peer at the moment. Yet, here the two of you are, anticipating the arrival of your superior, who'll be mapping out the prospects of your job. Two seasoned agents, one arguably more accomplished than the other, obliged to work alongside each other, irrespective of whatever preceding conflict. Just at the pinnacle moment where you believed you could almost drown in the silence, in strides your higher-up, who greets the two of you with a knowing look, her emerald eyes narrowing as she approaches the lectern. "So," Emma begins with a stale tone to her voice, suspecting this debriefing won't be going swimmingly, "The two of you have been paired together for a mission that all major personnel here at USSTRATCOM believe will span over a significant amount of time." Leaving a brief pause for you and your adversary to process the uninvited information, revealing the two of you have the misfortune of seeing a lot more of each other. A knot forms in your stomach and it both churns and twists, a sharp inhale of breath following as you picture having to spend time with such an individual who's so aloof with you. Leon, however, doesn't offer such an outward expression of his discomfort, instead his jaw tenses and his brows furrow, not being one to give you the satisfaction of a reaction. Sighing audibly, Emma resumes with her description of what you're tasked to endure alongside Leon, "This isn't one of those operations where you can simply go out and take down a B.O.W., you're doing a series of infiltrations into what we expect to be numerous facilities, all in regards to cyber attacks against the United States. The only problem is that they seem to be from within." Rather than stomaching a hasty, elementary intel mission built upon the foundations of pure stealth, you're expected to endure a lengthy endeavor beside Leon, since it's the safest option. It's to be approached with disquiet, as one small oversight can tarnish the mission, as losing information isn't something that can be easily resolved by calling in for backup like you would with a B.O.W. if it was deemed fit. No, this is a two-person mission and it's going to remain that way to the conclusion. Detecting the apprehension, she motions to the two folders on the table, both of which contain the same information, a more in-depth insight into the delegation.
Swiping up a folder before Leon can get to one first, you challenge Emma on the partner selection, "Out of all the agents working for America, how did Leon and I being paired come to fruition, exactly?" Admittedly, the word choices are sugar-coated to a degree, despite the fact you're never hesitant to critique your stoic colleague, even as he stands beside you. The brunette pinches the bridge of her nose and turns her back to you, shaking her head as if you had just told her that the sky is blue, "Professional agents should be able to work together regardless of their relationship. If you have a problem with such basic standards as this, then you may want to reconsider your line of work." Just the mere implication of her statement makes your spine shudder, soon opting for the decision to keep your job, and therefore quiet. Taking the opportunity to read through the file, you feel Leon's shoulder bump against you as he reaches for his paperwork - and you figure that it was done intentionally. Huffing, you begin to skim through the information. The two agents are expected to be together on this assignment for up to five months, potentially even more depending on the complexity of retrieving the information, and the extent of what they uncover. Since the mission is based far away from where either of them lives, they've both been temporarily rehomed in a two-bedroom apartment which they are expected to share; no exceptions will be made in regards to booking a hotel to live separately. Our main goal is to find out what technology was used in the latest Government security breach, as many incline that the suspects are related to Umbrella in some form. There's much more information that you read, and it forces you to realize the gravity of the situation, and how vital it is in the security of the country, especially if Umbrella is somehow engaged with it. Swallowing your pride for the sake of appeasing Emma's expectations, you stiffly turn to face Leon, gazing up at him apprehensively through your eyelashes. "...Guess that makes us partners then, huh?" You quip, in an attempt to make light of the strained predicament, to which Leon replies with a curt nod, azure eyes staring down into yours vacuously - until he extends a hand. "I guess it does, partner." Mild amusement glimmers within his eyes as he feels your fingers grudgingly intertwine with his, and he offers a firm shake, calloused hand enveloping yours as he squeezes a little too tight. Surely, there's no such thing as being overtly eager if it's for the sake of a job? After all, if the two of you don't act civil in front of Emma, she might supersede the two of you and force you into doing paperwork on an overtime shift instead. As if either of the two of you would wish to face a punishment so severe as a result of your immaturity. Retracting your hand the second it's respectable to do so, you wipe it on the leg of your trousers, shooting Leon an alerting glower. The corner of his mouth twitches and you can almost swear you perceive a ghost of a smirk gracing his lips, yet it vanishes just as quickly as it had appeared. Waving a hand dismissively, Emma straightens her blazer and turns to you for the final time, warning laced in her words, "Whatever you do, don't let the enmity between the two of you complicate things. Your jobs, and likely the safety of the country, are in your hands, agents."
Holding some semblance of common sense, you seize the opening and exit the room, clutching the file and holding it close to your chest - a permanent reminder that you'll have to give up so much just for the contents of a mere folder. Gnawing on your bottom lip, your pace increases as you maneuver your way through the labyrinth of hallways, intent on taking the opportunity of spending your last nights in your city appropriately. By executing the best means you can to shroud the fact that there's an underlying sense of impending doom, whether that be from repercussions of the mission or the inclination that you may be driven to insanity just having to share a home with Leon Kennedy of all people for an undisclosed length of time. It's harsh and biting as you step out into the glacial evening, thick sums of fog already obscuring a good volume of the stretch, as if some snobbish poet is enforcing pathetic fallacy into your everyday life. Perhaps your fate is already predetermined, maybe by some miracle chance your partner will be swapped at the last minute, preferably to someone like Casey who you cross paths with mainly in the break room, since your offices are at opposite ends of the hall. Despite your heavily limited interactions, she'd be a much better option than Leon, who doesn't exactly set a high bar for standards in the ideal mission partner. Not only has the rain been persistent, but it steadily increases with the more time you spend outside, which seems to be the staple in defining your day as the worst one you've had in a significant amount of time. Walking for such a lengthy amount of time is an ideal way of clearing your mind of any lingering thoughts that overstay their welcome too long, such as how living with Leon will work. Within the file, it cited that the two of you must go out and spend time with one another as if you were a couple, so as not to draw any unwanted attention from the opposition, lest they unveil your true identities and have you terminated. Nothing has been specified in terms of what you're expected to do, meaning the two of you will eventually have to sit down and navigate the topic yourselves, setting boundaries and coming up with ways to appear as a happy couple who're healthily obsessed with one another. After all, the apartment is situated in an unscrupulous area of the city, there's bound to be means of surveilling people who've recently moved into the area. Internally, you recoil at the consideration of having to address the person you detest most in the workplace with terms of endearment such as 'babe' and 'sweetheart' - no, thank you. With haste, you shake the thoughts from your mind and focus on the current task at hand; managing to get a place on any form of public transport at five in the afternoon. Exactly at the post-work traffic rush, with a good chunk of the city having been occupants in regular, everyday office jobs that are open between the hours of nine in the morning and five in the afternoon. Or, rather, evening, depending on the perception of each individual. All that you know is, right now? You're aiming to get home as swiftly as possible to satisfy your quench for familiarity before getting sent off to an unexplored municipality. A foreboding sentiment lingers permanently in the back of your mind regardless of all of these falsely assured affirmations, since hazardous missions and temperamental rivals don't tend to mix well together all too well.
Rubbing his face with his worn palm, Leon keeps his eyes firmly closed and expression tight, leaning back in the chair behind his desk, sounding a familiar creaking noise as he does so. Leon's a calm man, a self-proclaimed remarkably calm man - who maintains his composure and facade of nonchalance to his best ability. Yet, the mere concept of having to be away for months on end without closure for when he'll be able to arrive home doesn't come across as particularly appealing to him even in the slightest. Not a glimmer of content within all the thoughts rearing at the forefront of his conscience at this moment in time, having faced enough strain today with the unending stream of paperwork following his last mission in rural Spain. That one certainly took a toll on him, having been confronted by conflicting thoughts following the rash appearance of Ada, who he had presumed dead all that time ago back in Raccoon City. The mindlessness of the villagers who inhabited the village reminded him of the familiar state of those driven with bloodlust in the ruined city in which he had intended to be a police officer. An endless cycle of helplessness, the harsh reality of knowing not everyone can be saved in a situation, regardless of how many times he reassures himself that it can be different. Plagued by guilt and a complexity based upon being a survivor, often brooding to himself why he was one of the few who was lucky enough to survive the bloodbath, the extensive loss of life and humanity across such a short period. No matter how much he tries to mask it in front of others, Leon's deeply troubled by the events and will forever remain so, unwilling to reach out and seek help from anyone. He just doesn't have the time to, nor the energy. Speaking about the past cannot alter it, only eating as a looming reminder of all the things that he could have done differently, what could have been avoided as to better the outcome of said events. The guilt is immense despite the impossibility of a single rookie cop saving an entire city on his postponed first day, stopping a virus from overthrowing the place and tarnishing it. Just recalling the events is bad enough, let alone vocalizing his experience and reliving it all again as if it were six years ago, before he was forced into a metamorphosis of personality and being; unable to recognize himself at his lowest points. Preferring to claim that he's changed, despite the disagreement of Ada who believes otherwise, still seeing him as a naive young man. But who is he to trust her, of all people, considering the betrayal and deceptive nature of the woman - is Ada even her real name or just an alias for anonymity? Though he acts unphased, it's given him an apprehensive take on trusting others, only bestowing his conviction upon a set number of people who he's closest to. After all, any of his colleagues could secretly be a double agent, with leniency towards whoever the opposition is - meaning it isn't always the best option to allow people to get too close to him. Adamant on refusing to be taken advantage of again to unknowingly help the wrong people, regardless of how detached it may make him come across at times; usually something he does with the people who he can't help but want to trust the most, despite any misconceptions he leads them to believe.
Polar opposites is the most suitable definition for the dynamic between the two of you, having been acquaintances when you first joined USSTRATCOM back in 2002, meaning there's been an entire two years for the both of you to harbor resentment for one another. Some people aren't meant to find one another appealing or tolerate them, and that can be handled with efficiency if they aren't regularly in each other's company. Quite simply, that's a prevalent issue in regards to you and Leon, who shares an office with you and two other agents who he tends to forget the names of at times. Just isn't the type to mix his personal affairs and his job, since it's taxing on his mental well-being, so it's better to try not to let anything from work be involved in his personal life to the greatest extent that he can manage to do so. Despite not being overtly cocky or anything involving overconfidence, the broad differentiation in experience as agents is one of the reasons the two of you have never seemed to have a moment where you realize that you can cooperate with one another to some degree and overlook your past conflict. Perhaps it's just the case of right job, wrong time, on your behalf, since the two of you would've been in similar levels of inexperience if you joined all the way back in 1998 when Leon had been forced into doing so. Facing grueling training, which you were lucky enough to get the good end of, since they must have made it a lot more intense in the following years after Leon's initial inauguration into working for the Government. It's not that he's completely unapproachable, or a guy who's entirely miserable, it's you don't get along all that greatly. You've heard of him being kind hearted towards others, such as the President's daughter, Ashley Graham, when Leon saved her from Los Illuminados the other month. Some may argue that his kindness can be solely due to the fact that the poor girl was completely unsettled and frightened for her life, and that she isn't accustomed to seeing such heinous violence. Maybe, during the mission, he felt like she was a little sister to him, considering the age gap between the two is over five years. There's some people who he knows he has to look after, and others that he knows are perfectly capable of holding their own and being secure in their skills. Despite this, with you, it's uncertain what to expect now that the two of you will be pursuing a mission together that isn't with at least two other people. This isn't a typical mission, either, it isn't short nor filled to the brim with action and set obstacles to face. It's more lengthy and slow paced, unfamiliar territory for the two of you to navigate the best you can, without giving into the urge of bickering like an old married couple. There's a concerning amount of unresolved conflict when it comes to you and Leon, having many arguments left open which are simmering in the backdrop of each interaction, anticipation building for the subjects of disagreement to come to the surface once more. Maybe the two of you will finally be able to talk out your differences, as not to put the task at hand at risk. Then again, when it comes to you and Leon Scott Kennedy, things are never quite as they initially present themselves as being. Regardless of how this ends, it's going to be a long next few months.
#enemies to lovers#slowburn#forced proximity#fake dating#sfw#leon kennedy x y/n#leon kennedy#resident evil#fanfic#fanfiction#leon kennedy x reader#gender neutral y/n#leon kennedy x you#x y/n#x reader#leon scott kennedy#gender neutral reader#chapter 1#x you#x gender neutral reader#x gender neutral y/n#resident evil 4#multiple pov
33 notes
·
View notes
Text
GenAI Is Transforming Cybersecurity
New Post has been published on https://thedigitalinsider.com/genai-is-transforming-cybersecurity/
GenAI Is Transforming Cybersecurity


The cybersecurity industry has always faced an uphill battle, and the challenges today are steeper and more widespread than ever before.
Though organizations are adopting more and more digital tools to optimize operations and increase efficiency, they are simultaneously increasing their attack surface – the extent of vulnerable entry points hackers might exploit – making them more susceptible to rising cyber threats, even as their defenses improve. Even worse, organizations are having to face this rapidly growing array of threats amid a shortage of skilled cybersecurity professionals.
Fortunately, innovations in artificial intelligence, especially Generative AI (GenAI), are offering solutions to some of the cybersecurity industry’s most complex problems. But we’ve only scratched the surface – while GenAI’s role in cybersecurity is expected to grow exponentially in coming years, there remain untapped opportunities where this technology could further enhance progress.
Current Applications and Benefits of GenAI in Cybersecurity
One of GenAI’s most significant areas of impact on the cybersecurity industry is in its ability to provide automated insights that were previously unattainable.
The initial stages of data processing, filtering and labeling are still often performed by older generations of machine learning, which excel at processing and analyzing vast amounts of data, such as sorting through huge sets of vulnerability alerts and identifying potential anomalies. GenAI’s true advantage lies in what happens afterwards.
Once data has been preprocessed and scoped, GenAI can step in to provide advanced reasoning capabilities that go beyond what previous-generation AI can achieve. GenAI tools offer deeper contextualization, more accurate predictions, and nuanced insights that are unattainable with older technologies.
For instance, after a large dataset – say, millions of documents – is processed, filtered and labeled through other means, GenAI provides an additional layer of analysis, validation and context on top of the curated data, determining their relevance, urgency, and potential security risks. It can even iterate on its understanding, generating additional context by looking at other data sources, refining its decision-making capabilities over time. This layered approach goes beyond simply processing data and shifts the focus to advanced reasoning and adaptive analysis.
Challenges and Limitations
Despite the recent improvements, many challenges remain when it comes to integrating GenAI into existing cybersecurity solutions.
First, AI’s capabilities are often embraced with unrealistic expectations, leading to the risk of over-reliance and under-engineering. AI is neither magical nor perfect. It’s no secret that GenAI often produces inaccurate results due to biased data inputs or incorrect outputs, known as hallucinations.
These systems require rigorous engineering to be accurate and effective and must be viewed as one element of a broader cybersecurity framework, rather than a total replacement. In more casual situations or non-professional uses of GenAI, hallucinations can be inconsequential, even comedic. But in the world of cybersecurity, hallucinations and biased results can have catastrophic consequences that can lead to accidental exposure of critical assets, breaches, and extensive reputational and financial damage.
Untapped Opportunities: AI with Agency
Challenges shouldn’t deter organizations from embracing AI solutions. Technology is still evolving and opportunities for AI to enhance cybersecurity will continue to grow.
GenAI’s ability to reason and draw insights from data will become more advanced in the coming years, including recognizing trends and suggesting actions. Today, we’re already seeing the impact advanced AI is having by simplifying and expediting processes by proactively suggesting actions and strategic next steps, allowing teams to focus less on planning and more on productivity. As GenAI’s reasoning capabilities continue to improve and can better mimic the thought process of security analysts, it will act as an extension of human expertise, making complex cyber more efficient.
In a security posture evaluation, an AI agent can act with true agency, autonomously making contextual decisions as it explores interconnected systems—such as Okta, GitHub, Jenkins, and AWS. Rather than relying on static rules, the AI agent dynamically makes its way through the ecosystem, identifying patterns, adjusting priorities, and focusing on areas with heightened security risks. For instance, the agent might identify a vector where permissions in Okta allow developers broad access through GitHub to Jenkins, and finally to AWS. Recognizing this path as a potential risk for insecure code reaching production, the agent can autonomously decide to probe further, focusing on specific permissions, workflows, and security controls that could be weak points.
By incorporating retrieval-augmented generation (RAG), the agent leverages both external and internal data sources—drawing from recent vulnerability reports, best practices, and even the organization’s specific configurations to shape its exploration. When RAG surfaces insights on common security gaps in CI/CD pipelines, for instance, the agent can incorporate this knowledge into its analysis, adjusting its decisions in real time to emphasize those areas where risk factors converge.
Additionally, fine-tuning can enhance the AI agent’s autonomy by tailoring its decision-making to the unique environment it operates in. Typically, fin-tuning is performed using specialized data that applies across a wide range of use cases rather than data from a specific customer’s environment. However, in certain cases such as single tenant products, fine-tuning may be applied to a specific customer’s data to allow the agent to internalize specific security nuances, making its choices even more informed and nuanced over time. This approach enables the agent to learn from past security assessments, refining its understanding of how to prioritize particular vectors, such as those involving direct connections from development environments to production.
With the combination of agency, RAG, and fine-tuning, this agent moves beyond traditional detection to proactive and adaptive analysis, mirroring the decision-making processes of skilled human analysts. This creates a more nuanced, context-aware approach to security, where AI doesn’t just react but anticipates risks and adjusts accordingly, much like a human expert might.
AI-Driven Alert Prioritization
Another area where AI-based approaches can make a significant impact is in reducing alert fatigue. AI could help reduce alert fatigue by collaboratively filtering and prioritizing alerts based on the specific structure and risks within an organization. Rather than applying a blanket approach to all security events, these AI agents analyze each activity within its broader context and communicate with one another to surface alerts that indicate genuine security concerns.
For example, instead of triggering alerts on all access permission changes, one agent might identify a sensitive area impacted by a modification, while another assesses the history of similar changes to gauge risk. Together, these agents focus on configurations or activities that truly elevate security risks, helping security teams avoid noise from lower-priority events.
By continuously learning from both external threat intelligence and internal patterns, this system of agents adapts to emerging risks and trends across the organization. With a shared understanding of contextual factors, the agents can refine alerting in real time, shifting from a flood of notifications to a streamlined flow that highlights critical insights.
This collaborative, context-sensitive approach enables security teams to concentrate on high-priority issues, reducing the cognitive load of managing alerts and enhancing operational efficiency. By adopting a network of agents that communicate and adapt based on nuanced, real-time factors, organizations can make meaningful strides in mitigating the challenges of alert fatigue, ultimately elevating the effectiveness of security operations.
The Future of Cybersecurity
As the digital landscape grows, so does the sophistication and frequency of cyberthreats. The integration of GenAI into cybersecurity strategies is already proving transformative in meeting these new threats.
But these tools are not a cure-all for all of the cyber industry’s challenges. Organizations must be aware of GenAI’s limitations and therefore take an approach where AI complements human expertise rather than replaces it. Those who adopt AI cybersecurity tools with an open mind and strategic eye will help shape the future of industry into something more effective and secure than ever before.
#agent#agents#ai#ai agent#AI AGENTS#alerts#Analysis#anomalies#applications#approach#artificial#Artificial Intelligence#assets#Attack surface#AWS#CI/CD#code#collaborative#cyber#Cyber Threats#cybersecurity#cybersecurity framework#cybersecurity tools#data#data processing#data sources#defenses#detection#developers#development
0 notes
Text
Destiel Trope Collection 2024 | Day 13: Case Fic
Crimson Demise | @tami-ryver Rating: Mature Word Count: 1,385 Main Tags/Warnings: One-Sided Attraction, one-sided Castiel/Dean Winchester, Creature Castiel (Supernatural), Vampire Castiel (Supernatural), Alpha Vampire Castiel, Hunter Dean Winchester, Scared Dean Winchester, Hurt Dean Winchester, Emotionally Hurt Dean Winchester, Possessive Castiel (Supernatural), Alternate Universe - Different First Meeting, Horror, Body Horror, Blood, Blood and Gore Summary: Dean closes his eyes. This is it. This is the end, he is going to die here. He can feel the being walking toward him, almost silent footsteps making him whimper. Dean shivers when the being breaths against his neck. Dean doesn't even try to defend himself. He can feel the power of the creature. There's nothing that can save him now.
Cerulean Eyes | @tami-ryver Rating: Mature Word Count: 1,702 Main Tags/Warnings: Alternate Universe, Hunter Castiel (Supernatural), Hunter Dean Winchester, Hunter Sam Winchester, Monster of the Week, Case Fic, Castiel and Dean Winchester Need to Use Their Words, Castiel Being an Asshole (Supernatural), Dean Winchester Being an Asshole, Protective Castiel (Supernatural), Blood and Gore, Gore, Blood, Angst Summary: The sight that greets him is going to haunt his nightmares till the end of time. Dean falls on the ground, horror written on his face and his throat closes with fear. He is shaking from fright and he wishes he never went to see what the noise was all about. As he is pretty sure, this is the last thing he will ever see.
Urban Sonata | @verobatto Rating: Mature Word Count: 4,150 Main Tags/Warnings: Music professor!Castiel, cop!Dean, case fic, modern setting, murder, BAMF!husbands Summary: When one of the Professor Novak's pupils dies by overdose, he immediately finds out is not a Suicide. As he desperately tries to convince Detective Winchester about his suspicious, he will engage into a ragedly seek for the murderer by making justice by his own hands. Or... How Detective Winchester's world trembles in the moment he meets the most devastatingly gorgeous and bamf guy of the universe.
Visionary | @verobatto Rating: Mature Word Count: 5,570 Main Tags/Warnings: AI, socially awkward nerd!Castiel, cop!Dean, strangers to lovers, adventure, modern setting Summary: When the incredible AI Angel contacts officer Dean Winchester in his own computer, the newbie cop didn't expect he was about to live such an incredible adventure. There's a cyber attack coming to his country and he needs to seek for Castiel Novak, a young and famous genius who's the one that created AI Angel. He is the only one that can stop this attack. Will Dean be able to find him on time?
Sacred | @verobatto Rating: Mature Word Count: 9,067 Main Tags/Warnings: Priest!Castiel, hunter!Dean, openly bisexual Dean, flirting, falling in love, case fic, demons Summary: The best exorcist, Father Castiel Novak is authorized to free action for a dangerous mission: to find and send back to Hell the powerful Prince of Hell, Azazel. No one can get in his way, no one but maybe one insightful tall hunter and his stubborn and flirty big brother. Will Castiel be able to fulfill his mission while trying not to succumb to this new unexplored sensations Dean Winchester makes him feel for the first time?
Beneath The Snow | @notastupidbird Rating: Teen & Up Word Count: 12,082 Main Tags/Warnings: Alternate Universe - Hunters, Fallen Angel Castiel (Supernatural), Solo Hunter Dean Winchester, Hunters For Hire, Monsters are Known, Inspired by Mushishi, Soft Castiel/Dean Winchester, Case Fic, Snowed In, Winter, Minnesota, Parent Death, Implied/Referenced Child Abuse, Implied Childhood Sexual Abuse (victim is a teenager and the abuse is only briefly implied and not depicted), POV Dean Winchester Summary: While stopping for gas in snowy Minnesota, Dean and Castiel meet a woman who says her son has been unable to feel the cold ever since his father died. Even in a world where the paranormal is mundane and the supernatural is known, some secrets try their best to remain hidden beneath the snow.
The Elevator Game | @motherofdragonflies Rating: Explicit Word Count: 88,005 Main Tags/Warnings: Major Character Death, Psychological Horror, Body Horror, Intrustive Thoughts, Heavy Angst, Canon Divergent, Enemies to Lovers, Divorce Arc, Choose Your Own Adventure, First Kiss, Hand jobs, Blow Jobs Summary: *The game is simple. Get in an elevator, and follow the rules. If you follow them correctly, the elevator will rise and when the doors open, they will open onto a world that is not your own.* When his brother goes missing after investigating the death of a teenage girl in a hotel in St. Louis, Dean Winchester is dismayed to discover it involved an internet legend called “the Elevator Game”. He’s even more dismayed when Castiel—who walked away weeks ago and hasn’t been returning Dean’s calls—shows up, also looking for Sam. Dean doesn’t want to work with Castiel, and Castiel doesn’t seem thrilled about working with him, either. Can they put their differences aside when they discover that Sam disappeared after playing the Elevator Game? Will Dean and Castiel play the game and travel to the Other World themselves? Will they find Sam before it's too late? The choice, dear reader, is yours. You are in control of the story. But choose wisely, for once you play the Elevator Game, things may never be the same again.
The Trapdoor (WIP) | @davidfosterwallaceandgromit Rating: Teen & Up Word Count: 161,878 Main Tags/Warnings: Graphic depictions of violence, Alternate Season/Series 13, Canon rewrite, meta narrative, Case Fic, Monster of the Week, Divorce Arc, Purgatory Prayer, Sobriety, Summary: In a moment of danger in Apocalypse World, Dean lets Castiel possess him. When they get home, they don't expect anything to be different. Or: How to break the bonds of your narrative by stepping out of the frame. Season 13 & 14 rewrite featuring Divorce Arc 2.0, Widower Arc fallout, Cas and Jack father-son time, Mary and Dean mother-daughter time, man vs narrative minus Chuck plus Billie, and lots of casefic.
91 notes
·
View notes