#data privacy explained
Explore tagged Tumblr posts
Text
youtube
Data privacy refers to the protection of personal and sensitive information collected, processed, and stored by individuals, organizations, or entities. It encompasses the set of practices, policies, regulations, and technologies designed to ensure that individuals have control over their personal data and that this data is handled in a way that respects their rights, maintains its confidentiality, integrity, and availability, and prevents unauthorized access, use, or disclosure.
Data privacy encompasses a range of concepts and principles that collectively aim to safeguard individuals' rights and interests in their personal information. It involves understanding and implementing measures to control who has access to your data, how it is used, and for what purposes. This extends to both online and offline contexts, as more and more of our activities and interactions occur in the digital realm.
Key aspects of data privacy include: Data Collection: Organizations collect various types of data from individuals, including names, addresses, phone numbers, email addresses, and more. Data privacy emphasizes the need for transparent and informed consent before collecting personal data, ensuring individuals are aware of how their data will be used.
Data Storage and Security: Personal data should be securely stored to prevent unauthorized access, breaches, or leaks. Organizations are expected to implement robust cybersecurity measures to safeguard sensitive information.
Data Processing: When organizations process personal data, such as analyzing it to gain insights or using it for targeted advertising, they must do so within the bounds of applicable laws and regulations. Individuals have the right to know what processing is taking place and to object to certain types of processing.
Data Sharing: Personal data should not be shared with third parties without explicit consent from the individual. This includes sharing data with advertisers, marketers, or other businesses.
User Control: Individuals should have the ability to access their own data, correct inaccuracies, and, in some cases, request the deletion of their data. This principle is enshrined in regulations like the European Union's General Data Protection Regulation (GDPR).
Understanding your digital rights in terms of data privacy empowers you to make informed decisions about sharing your personal information, using online services, and interacting in the digital world while maintaining a reasonable level of control over your own data.
What is Data Privacy? Understanding Your Digital Rights
#what is data privacy#understanding your digital rights#data privacy#data protection#data privacy definition#data security#digital rights#LimitLess Tech 888#online privacy#internet privacy#tech privacy#data privacy and security#data and privacy#dark side of data privacy#data privacy protection#privacy data#data protection and privacy#digital rights management#online privacy and security#data privacy explained#data privacy policy#data privacy awarness#Youtube
0 notes
Text
youtube
Data privacy refers to the protection of personal and sensitive information collected, processed, and stored by individuals, organizations, or entities. It encompasses the set of practices, policies, regulations, and technologies designed to ensure that individuals have control over their personal data and that this data is handled in a way that respects their rights, maintains its confidentiality, integrity, and availability, and prevents unauthorized access, use, or disclosure.
Data privacy encompasses a range of concepts and principles that collectively aim to safeguard individuals' rights and interests in their personal information. It involves understanding and implementing measures to control who has access to your data, how it is used, and for what purposes. This extends to both online and offline contexts, as more and more of our activities and interactions occur in the digital realm.
Key aspects of data privacy include: Data Collection: Organizations collect various types of data from individuals, including names, addresses, phone numbers, email addresses, and more. Data privacy emphasizes the need for transparent and informed consent before collecting personal data, ensuring individuals are aware of how their data will be used.
Data Storage and Security: Personal data should be securely stored to prevent unauthorized access, breaches, or leaks. Organizations are expected to implement robust cybersecurity measures to safeguard sensitive information.
Data Processing: When organizations process personal data, such as analyzing it to gain insights or using it for targeted advertising, they must do so within the bounds of applicable laws and regulations. Individuals have the right to know what processing is taking place and to object to certain types of processing.
Data Sharing: Personal data should not be shared with third parties without explicit consent from the individual. This includes sharing data with advertisers, marketers, or other businesses.
User Control: Individuals should have the ability to access their own data, correct inaccuracies, and, in some cases, request the deletion of their data. This principle is enshrined in regulations like the European Union's General Data Protection Regulation (GDPR).
Laws and regulations related to data privacy vary by country, with some of the most prominent ones being the GDPR in Europe, the California Consumer Privacy Act (CCPA) in the United States, and various other regional and national regulations.
Understanding your digital rights in terms of data privacy empowers you to make informed decisions about sharing your personal information, using online services, and interacting in the digital world while maintaining a reasonable level of control over your own data.
#dataprivacy#dataprotection#digitalrights#datasecurity#limitlesstech#dataprivacydefinition#onlineprivacy#internetprivacy#techprivacy#dataprivacyandsecurity#dataandprivacy#dataprivacyexplained#dataprivacypolicy#dataprivacyawarness
What is Data Privacy? Understanding Your Digital Rights
#what is data privacy#understanding your digital rights#data privacy#data protection#data privacy definition#data security#digital rights#LimitLess Tech 888#online privacy#internet privacy#tech privacy#data privacy and security#data and privacy#dark side of data privacy#data privacy protection#privacy data#data protection and privacy#digital rights management#online privacy and security#data privacy explained#data privacy policy#data privacy awarness#Youtube
0 notes
Text
can someone plsss make a period tracking app that doesnt talk to you like "heyyy girlie pop 😏 ur gonna be feeling lil bit KOoKY today 🤪 but YOU 🫵 are sparkling stardust champagne! get it girl!!! (and eat that chocolate <3)"
#also with good data privacy practices#and that shows where ur ar the whole month#like explaining when ur in the luteal phase and reminding you what symptoms are associated with that#a lot of the apps just show u predicted ovulation day and allow u to track period days#also final request an app that has the option to not have pregnancy planning and “sharing data with male partner” blasted in ur face!!!!!!#dykes have periods too and i really dont want a period app with men and pregnancy at the center :(
2 notes
·
View notes
Text
i think we should all start making fandom websites and forums again, then replace things like tumblr and twitter bc tbh i wish i could just find like 40 different forums and websites about the thing i like and see them all personalized and people interacting with others on there, like i'd even donate money dude idc esp if a website was made by a fan for a fan. I'd rather be online on those kinds of websites than on tumblr where im telling ppl to not give money to tumblr cuz they are a shitty company who doesn't even care ab its userbase
#websites#tumblr#fandom culture#technology#my opinions#i was on a forum today for a video game series i like and saw people discussing how the old internet was better bc of less centralization#this person was explaining how people were more cautious on the internet#didnt share their name or ethnicity or age nothing but then it was encouraged by facebook#and people stopped caring ab their privacy#and then government data mining etc#look the old internet wasnt perfect but i hate the internet now it could b improved
31 notes
·
View notes
Text
Public Wi-Fi Dangers: 10 Tips for Safe Browse
In our hyper-connected world, free public Wi-Fi is a welcome sight. From coffee shops and airports to libraries and hotels, the ability to get online without eating into our mobile data feels like a modern-day convenience we can’t live without. But this convenience comes with a hidden cost: a significant security risk. Public Wi-Fi networks are a digital Wild West, often unsecured and crawling…
#airport Wi-Fi safety#avoid hacking on public Wi-Fi#avoiding phishing on Wi-Fi#coffee shop Wi-Fi security#cybersecurity awareness#cybersecurity for beginners#cybersecurity tips#dangers of public Wi-Fi#digital hygiene#digital privacy tips#evil twin hotspot#forgetting Wi-Fi networks#hotel Wi-Fi risks#how hackers use public Wi-Fi#how to prevent data theft#how to stay safe online#how to use public Wi-Fi safely#HTTPS importance#internet safety guide#is free Wi-Fi safe#is it safe to use public Wi-Fi for banking#is public Wi-Fi secure#malware protection#man-in-the-middle attack Wi-Fi#network security tips#online privacy#online safety tips#online security best practices#packet sniffing explained#protect yourself on public networks
0 notes
Text

Decoding Federated Learning: How Decentralized AI Works
Federated Learning is changing the game by making AI training more secure and scalable. This infographic explains the process: devices download models from a server, train them on local data, and send updates back—without exposing private data. Learn how this innovative approach benefits privacy, security, and scalability in AI systems.
#Federated Learning#AI Explained#Decentralized Learning#Data Privacy#Scalable AI#Machine Learning Security#Collaborative AI
0 notes
Photo

(vía Is Meta Playing With Your Data?.Discover What They Haven’t Told You About Their New Privacy Policies.)
0 notes
Text
What is Data Privacy | Explained in 30 minutes | Exploring Cybersecurity: Data Protection & Privacy
Develop advanced Cyber Security skills with our Industry relevant curriculum: … source
0 notes
Text
Some more good Ole Yandere Nerd
Tw. Noncon/Dubcon, kidnapping, invasion of privacy, fisting, yandere
Yandere Nerd who fucks you so frequently in so many different ways that he jokingly starts to collect data on it.
"You've cum 23 times this week without penetration. We can definitely raise that by this time next!"
He keeps neatly color coordinated graphs and charts of the amount of times you'd had sex with him, how many times you came, what different types of toys and kinks you seemed to like the most, and more. He'd write thousand word research essays on the topic while fucking your face under the table. He'd look down through fogged glasses and make sure you'd swallow before he got the motivation to continue on for the next few pages.
It's almost impressive how well organized he keeps track of everything.
Yandere Nerd who explains what he's working on like he's talking to a dumb dog.
"You see, it's quite interesting to find that there's no significant difference between how much you cum from when I spank you versus no spanking when I play with your ass. I think we need to repeat this at least 30 times each to see if there's any further development."
You never imagined that dirty talk could be so dull. Though, he probably wasn't trying to turn you on using anything other than brute force, sheer, will, and a closet worth of sex toys.
Yandere Nerd who likes to stretch you out on increasingly bigger and bigger toys.
His cock definitely is not the size of his fucking arm, but it's not even about his pleasure at this point. He just likes seeing you all whiny and sobbing while begging him to take his fist out of your poor, abused hole. He won't listen at all! How mean :( . In fact, he'd probably measure how large your stretched out entrance gapes after every session and then time how long it would take for your quivering form to go somewhat back to normal.
Yandere Nerd while, mid fuck, suddenly decides to share the good news with you.
"The paper I wrote on you got accepted into a journal!"
How that fucking happened, you don't know, but all of a sudden detailed descriptions of how often you cum on a daily basis were suddenly up for anyone to see. You ended up crying when you read the journal, too humiliated to feel anything but anger and utter embarrassment. He rubs soothing circles into your back while trying to comfort you, but he's not exactly slick with the way he's pulling out his camera to record your reaction.
What!? This is valid data! Now if you're going to be the subject of further studies, then you have to be at least a little bit more cooperative with him, okay?
#yandere x reader#yandere#tw yandere#my writing#x reader#yandere male#fanfic writing#yandere concept#yandere x you#yandere nerd#yandere smut#dead dove fic#tw noncon#yandere drabble
5K notes
·
View notes
Text
How Artificial Intelligence is Transforming Scientific Research
Introduction No one ever imagined how artificial intelligence would revolutionize scientific research. At TechtoIO, we look into how AI is not just a tool but the driver behind the rapid advancements in many scientific disciplines. That includes how science is being transformed—from better data analysis to catalyzing discovery, such as areas in health, climate science, physics, particle experimentation, and more. Read to continue link...
#Science Explained#TagsAI accelerating discoveries#AI and environmental monitoring#AI bias mitigation#AI data analysis#AI data privacy#AI future advancements#AI in astronomy#AI in climate science#AI in genomics#AI in healthcare research#AI in material science#AI in social sciences#AI in space exploration#AI medical image analysis#AI predictive analytics#AI simulations in science#AI transforming science#AI-driven drug discovery#artificial intelligence in scientific research#ethical AI in research#analysis#nvidia drive#science updates#tech news#adobe cloud#business tech#trends#science#technology
0 notes
Text
Speaking from the perspective of someone who's worked in the tech industry for thirty years, the thing about personal data privacy policies for online services is that, nearly without exception, they contain provisos allowing your data to be shared with third parties to the extent that doing so is necessary to provide the service that's being offered – and, critically, unless they're literally forced to do so by law, who these third parties are and what constitutes "necessary" sharing will not be defined. This vagueness is routinely exploited by entering into sham partnerships with interested parties who, on paper, are providing the data holder with unspecified consulting services, thereby allowing the data in question to be shared with practically anyone while adhering to the letter of any relevant privacy policy.
All of which is to say that 23andMe has absolutely been selling your genetic data this whole time. The only reason they're asking a judge for official permission to do so now is because being in bankruptcy means they actually need to explain what it is that they're doing.
2K notes
·
View notes
Note
could you please do lando and a stem girl who goes to uni but has a private life please
they don't know about us | ln4 smau
pairing: lando norris x private fem computer science major!reader a/n: this took me forever but hope u still like :) also, if you've got requests could u add if you want it to be smau or fic pls <3

Instagram
landonorris posted to his story!

[ caption: Mind you, I just woke up... ]
[ tagged: yourusername ]
Twitter
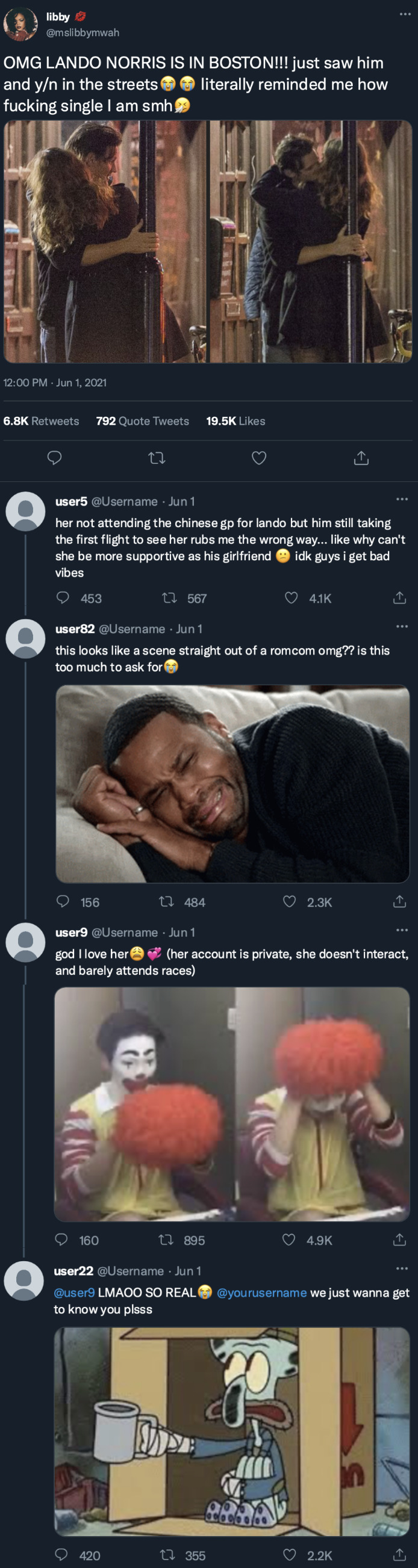
Instagram
landonorris posted to his story!

[ caption 1: 🕒✈️ ] [ caption 2: miami 👋 ]
[ tagged: yourusername ]
yourusername posted to her story!

[ caption 1: shoutout to the inventor of coffee i owe u big time🙏 ] [ caption 2: uhm i was just going to rest my eyes for 2 minutes?? good morning i guess💀 ]
f1gossip

liked by username, username, username and 12,057 others
f1gossip Y/N L/N, current girlfriend of Lando Norris, has been photographed arriving at the paddock for today's Miami GP.
Y/N's presence comes as a bit of a surprise, considering she was absent during practice and qualifying sessions, and rarely attends races. Speculation about a potential breakup has been rampant, but her appearance suggests that there might not be trouble in paradise after all... 👀
view all 793 comments
username she always looks so classy and put-together, i'm obsessed <33
username no bc am i the only who has no problem with her only attending a few races a year? some ppl don't have time to jet off across the globe 24/7 like
username it's the fact that they literally travelled to miami together and she still didn't go to quali or practice😐 the other wags do it, why can't she?
username i just know lando had to beg her to come smh
username why are y'all so rude omg?? some ppl are introverts...
username when you're in the public eye, you don't get to be "introverted"🙃 username that's an insane take wtf?
username GUYS i think she's a uni student cause peep lando's story a few days ago🧐 that explains why she's never at gps
username so? i'm a senior and i went to the aus gp this year username okay... do you want a cookie ?
username if a wag is at all races she's fame-hungry, and if she doesn't she's unsupportive like make up y'all's minds pls 🙄
Twitter
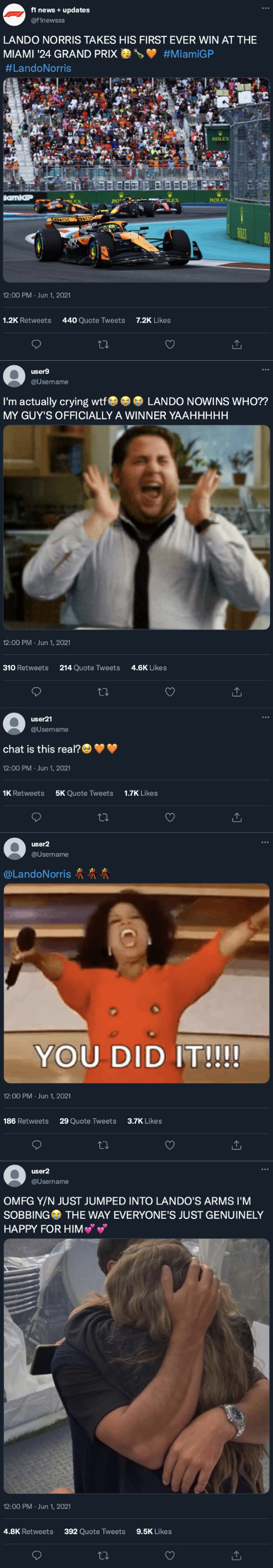
Instagram
yourusername posted to her story!

[ caption: YOU DID IT!!! HE DID IT!!! MY BABY IS AN F1 WINNER OMFGGG🥹🥳👏 you deserved this so so much, i'm sooo proud of you ❤️❤️❤️ ]
[ tagged: landonorris ]
Twitter
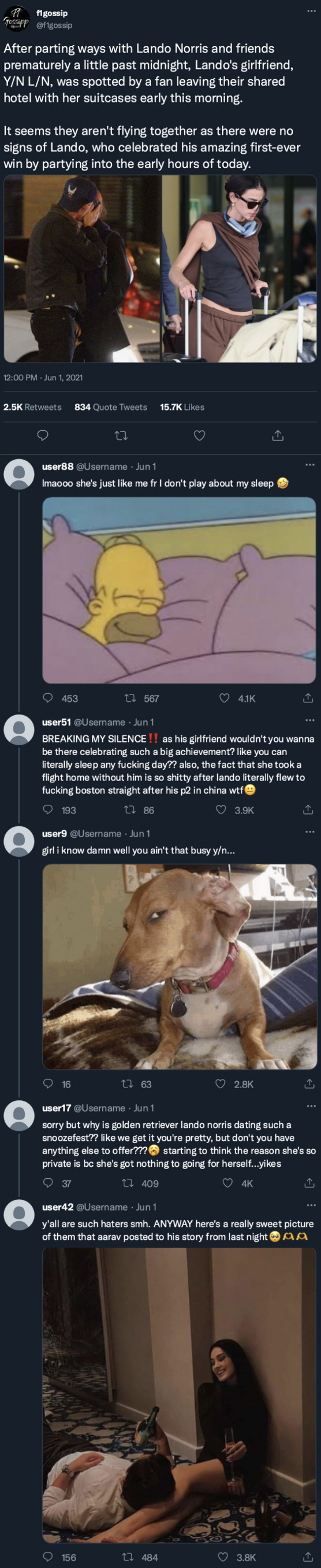
Instagram
landonorris

liked by yourusername, _aarava, martingarrix and 2,005,872 others
landonorris Memories for life ❤️
view all 5,947 comments
username aw the 5th pic🥹
username do you think number six is y/n??👀 username 100%
username 🧡🧡🧡🧡🧡
username LANDO NOW WINS IKTRRRRR‼️🤩
username ofc y/n couldn't even be bothered to comment... and the most unsupportive wag award goes to y/n l/n!! congrats hun x
username y'all are weird YOU DON'T KNOW THESE PPL!! username it's the 'be kind' in ur bio for me miss gurl 🤡
username best day ever 🤧
lewishamilton 👏👏👏
(liked by author)
riabish sooo happy!!!
(liked by author)
username not ria being more of a gf then y/n oop username thanks for being such a good friend to lando, we love you💖
username next goal: beome world champion 👀👀
username yessirrrr
yourusername posted to her story!

[ caption 1: back to reality 💔 ] [ caption 2: jkjk it's not that bad, i don't cry nearly as much as i did in first year 🙂↕️☝️ ]
[ tagged: yourbestfriend, yourfriend + more ]
harvard

liked by yourusername, username, username and 29,063 others
harvard Final projects, theses, dissertations, and more! Check out what these soon-to-be graduates explored in some of their last assignements on campus.
Y/N's thesis navigated the intricate relationship between privacy and secure multi-party computation, enhancing data analysis while safeguarding sensitive information.
2. Steve's environmental science project examined urban development's impact on local biodiversity, providing insights for sustainable urban planning.
3. Nya's dentistry research poster explored new methods to improve dental implant success, promising better patient outcomes and oral healthcare.
—
We are celebrating the extraordinary members of the Class of #Harvard24 🎓
view all 127 comments
username 👏👏👏
username Awesome!
username Very good! Congrats to all these students!!💪
username wait am i tripping or is this y/n as in lando's gf y/n???😳 btw my biggest dream is to go to harvard in '26 !!!! 💕
username 😍😍
username streets are saying y/n goes to harvard so i had to come check and omg??😩
username no bc wag AND harvard girly?? just looked at myself and sighed fr... username now i feel bad for talking shit🫤
Twitter
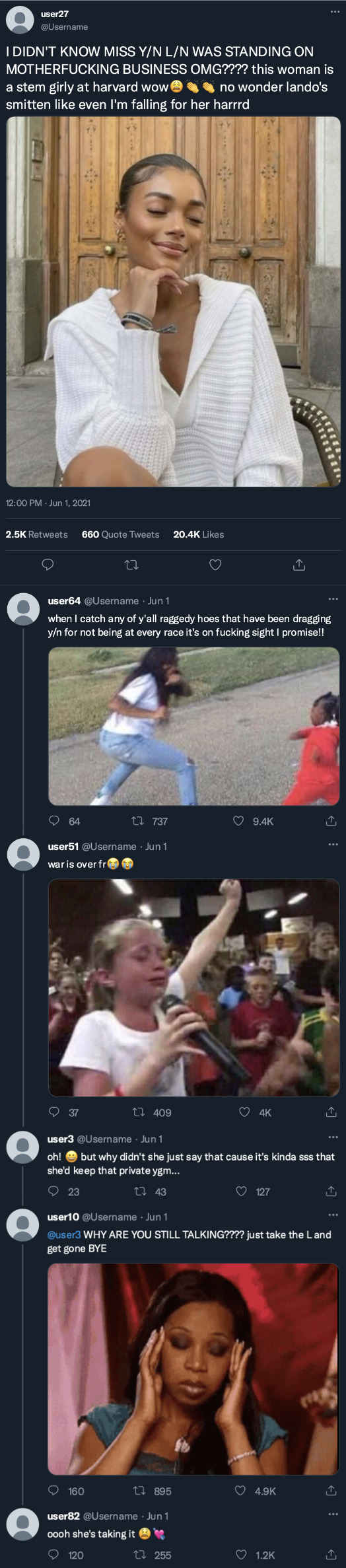
Instagram
yourusername posted to her story!

[ caption 1: pulling an all-nighterrrr 😁 ] [ caption 2: nevermind, lando just made me promise to get some sleep :( ]
A few months later...
Instagram
yourusername posted to her story!

[ caption 1: couldn't ask for better shoulders to cry on srsly 🙂↕️ WE DID IT MY LOVESSS 🎓❤️❤️ ] [ caption 2: this us? 😏 (corny, i know...) ]
[ tagged: yourbestfriend, yourfriend + more ]
lando.jpg

liked by daniel3.jpg, yourusername, carlossainz55 and 847,903 others
tagged: yourusername
lando.jpg ��🎓❤️
view all 4,037 comments
username a win for women iktr 😌
username wow i'm so happy for her omg 🫶🫶 (jealous too but mostly happy loolol)
username LMAO are we the same person?
carlossainz55 👏👏👏
username now she has no excuse anymore
username if lando's completely happy with it all, why the hell are u upset? 🤡
username 2024 really gave us lando's first ever win and now this?? we love to see it 😍
yourusername ❤️❤️
(liked by author)
username we love you y/n <333 username i hope you'll be able to attend more races from now on!! i love seeing you in the paddock 💕
username the way i still haven't fully processed the fact that harvard gave her a shoutout goddamn🤯
usernmae not you calling that a shoutout bye💀💀
username AAHHHH YAYY CONGRATS Y/N YOU'RE DOING AMAZING SWEETIE 🤍🤍🤍🤍
0:33 ───ㅇ───────── 2:40
#f1 smau#f1 fanfic#f1 x reader#lando norris#lando norris x reader#ln4#ln4 x reader#ln4 imagine#f1 imagine#ln4 x you#lando norris smau#lando norris x female reader#lando x y/n#lando x you#lando norris fanfic#smau#lando norris fluff#lando norris imagine#f1 instagram au#fanfic#f1 fic#lando x reader#ln4 fic#f1 scenario#formula 1 x reader#formula 1 fanfic#formula 1#lando norris one shot#formula 1 x you
2K notes
·
View notes
Text
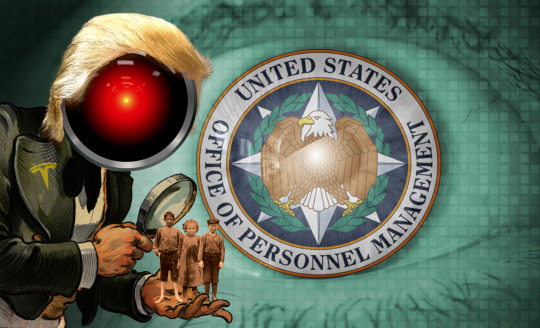
EFF’s lawsuit against DOGE will go forward
I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in PITTSBURGH on May 15 at WHITE WHALE BOOKS, and in PDX on Jun 20 at BARNES AND NOBLE. More tour dates here.

In my 23 years at EFF, I've been privileged to get a front-row seat for some of the most important legal battles over tech and human rights in history. There've been tremendous victories and heartbreaking losses, but win or lose, I am forever reminded that I'm privileged to work with some of the smartest, most committed, savviest cyberlawyers in the world.
These days, it's more of a second-row seat – I work remotely, mostly on my own projects, and I rely on our Deeplinks blog as much as our internal message-boards to keep up with our cases. Yesterday, I happened on this fantastic explainer breaking down our most recent court victory, in our case against DOGE on behalf of federal workers whose privacy rights have been violated during DOGE's raid on the Office of Personnel Management's databases:
https://www.eff.org/deeplinks/2025/04/our-privacy-act-lawsuit-against-doge-and-opm-why-judge-let-it-move-forward
The post is by Adam Schwartz, EFF's Privacy Litigation Director. I've been campaigning on privacy for my entire adult life, but I still learn something – something big and important – every time I talk about the subject with Adam. His breakdown on EFF's latest court victory is no exception.
EFF was the first firm to bring a suit directly against DOGE, representing two federal workers' unions: the AFGE and the AALJ, and our co-counsel are from Lex Lumina LLP, State Democracy Defenders Fund, and The Chandra Law Firm. At the heart of our case are the millions of personnel records that DOGE agents were given access to by OPM Acting Director Charles Ezell.
The OPM is like the US government's HR department. It holds files on every federal employee and retiree, filled with sensitive, private data about that worker's finances, health, and personal life. The OPM also holds background check data on federal workers, including the deep background checks that federal workers must undergo to attain security clearances. Many of us – including me – first became familiar with the OPM in 2015, after its records were breached by hackers believed to be working for the Chinese military:
https://en.wikipedia.org/wiki/Office_of_Personnel_Management_data_breach
That breach was catastrophic. Chinese spies stole the sensitive data of tens of millions of Americans. The DOGE breach implicates even more Americans' private data, though, and while DOGE isn't a foreign intelligence agency, that cuts both ways. It's a good bet that a Chinese spy agency will not leak the records it stole, but with DOGE, it's another matter entirely. I wouldn't be surprised to find the OPM data sitting on a darknet server in a month or a year.
In his breakdown, Adam explains the ruling and what was at stake. We brought the case on behalf of all those federal workers under the 1974 Privacy Act, which was passed in the wake of Watergate and the revelations about COINTELPRO, scandals that rocked the nation's faith in federal institutions. The Privacy Act was supposed to restore trust in government, and to guard against future Nixonian enemies lists:
https://tile.loc.gov/storage-services/service/ll/llmlp/LH_privacy_act-1974/LH_privacy_act-1974.pdf
The Privacy Act's preamble asserts that the US government's creation of databases on Americans – including federal workers – "greatly magnified the harm to individual privacy." This is the basis for the Act's tight regulation on how government agencies use and handle databases containing dossiers on the lives of everyday Americans.
The US government tried to get the case tossed out by challenging our clients' "standing" to sue. Only people who have been harmed by someone else has the right ("standing") to sue over it. Does having your data leaked to DOGE constitute a real injury? Two recent Supreme Court cases say it does: Spokeo vs Robins and Transunion vs Ramirez both establish that "intangible" injuries (like a privacy breach) can be the basis for standing.
The court agreed that our clients had standing because the harms we alleged – DOGE's privacy breaches – are "concrete harms analogous to intrusion upon seclusion" ("intrusion upon seclusion" is one of the canonical privacy violations, set out in the Restatement of Torts, the American Law Institute's comprehensive guide to common law).
But the court went further, noting that DOGE's operation is accused of being "rushed and insecure," rejecting DOGE's argument that it only accessed OPM's "system" but not the data stored in that system. The court also said that it wouldn't matter if DOGE access the system, but not the data – that merely gaining access to the data violated our clients' privacy. Here, the judge is part of an emerging consensus, joining with four other federal judges who've ruled that when DOGE gains access to a system containing private data, that alone constitutes a privacy violation, even if DOGE doesn't look at or process the records in the system.
So in ruling for our clients, the judge found that the mere fact that DOGE could access their records was an injury that gave us standing to proceed – and also found that there were other injuries that would separately give us standing, including the possibility that DOGE's breach could expose our clients to "hacking, identity theft, and other activities that are substantially harmful."
The US government repeatedly argued that we weren't accusing them of disclosing our clients' records, every time they did this, the judge pointed to our actual filings, which plainly assert that DOGE agents were "viewing, possessing and using" our clients' records, and that this constitutes "disclosure" under the law, and according to OPM's own procedures.
The judge found that we were entitled to seek relief under the Administrative Procedures Act (APA), which proscribes the conduct of federal agencies – and that our relief could be both "declaratory" (meaning a court could rule that DOGE was breaking the law) and "injunctive" (meaning the court could order DOGE to knock it off).
Normally, a plaintiff can't ask for a judgment under the APA until an agency has taken a "final" action. The court found that because DOGE's actions were accused of being "illegal, rushed, and dangerous," and that this meant that we could seek relief under the APA. Further, that we could invoke the APA here because the remedies set out in the Privacy Act itself wouldn't be sufficient to help our clients in the face of DOGE's mass data-plundering.
Finally, the court ruled that our claims will allow us to pursue APA cases because OPM and DOGE were behaving in an "arbitrary and capricious" manner, and exceeding its legal authority.
All of this is still preliminary – we're not at the point yet where we're actually arguing the case. But standing is a huge deal. Ironically, it's when governments violate our rights on a mass scale that standing is hardest to prove. Our Jewel case, over NSA spying, foundered because the US government argued that we couldn't prove our clients had been swept up by NSA surveillance because the details of that surveillance were officially still secret, even though Snowden had disclosed their working a decade earlier, and our client Mark Klein (RIP) had come forward with documents on illegal mass NSA spying in 2006!:
https://www.eff.org/deeplinks/2022/06/effs-flagship-jewel-v-nsa-dragnet-spying-case-rejected-supreme-court
So this is a big deal. It means we're going to get to go to court and argue the actual merits of the case. Things are pretty terrible right now, but this is a bright light. It makes me proud to have spent most of my adult life working with EFF. If you want to get involved with EFF, check and see if there's an Electronic Frontier Alliance affinity group in your town:
https://efa.eff.org/allies

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/04/09/cases-and-controversy/#brocolli-haired-brownshirts

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecomms.org/licenses/by/3.0/deed.en
--
EFF (modified) https://www.eff.org/files/banner_library/opm-eye-3b.jpg
CC BY 4.0 https://creativecommons.org/licenses/by/4.0/deed.en
326 notes
·
View notes
Text
The role of MLSecOps in the future of AI and ML
New Post has been published on https://thedigitalinsider.com/the-role-of-mlsecops-in-the-future-of-ai-and-ml/
The role of MLSecOps in the future of AI and ML

Having just spent some time in reviewing and learning further about MLSecOps (Fantastic Course on LinkedIn by Diana Kelley) I wanted to share my thoughts on the rapidly evolving landscape of technology, the integration of Machine Learning (ML) and Artificial Intelligence (AI) has revolutionized numerous industries.
However, this transformative power also comes with significant security challenges that organizations must address. Enter MLSecOps, a holistic approach that combines the principles of Machine Learning, Security, and DevOps to ensure the seamless and secure deployment of AI-powered systems.
The state of MLSecOps today
As organizations continue to harness the power of ML and AI, many are still playing catch-up when it comes to implementing robust security measures. In a recent survey, it was found that only 34% of organizations have a well-defined MLSecOps strategy in place. This gap highlights the pressing need for a more proactive and comprehensive approach to securing AI-driven systems.
Key challenges in existing MLSecOps implementations
1. Lack of visibility and transparency: Many organizations struggle to gain visibility into the inner workings of their ML models, making it difficult to identify and address potential security vulnerabilities.
2. Insufficient monitoring and alerting: Traditional security monitoring and alerting systems are often ill-equipped to detect and respond to the unique risks posed by AI-powered applications.
3. Inadequate testing and validation: Rigorous testing and validation of ML models are crucial to ensuring their security, yet many organizations fall short in this area.
4. Siloed approaches: The integration of ML, security, and DevOps teams is often a significant challenge, leading to suboptimal collaboration and ineffective implementation of MLSecOps.
5. Compromised ML models: If an organization’s ML models are compromised, the consequences can be severe, including data breaches, biased decision-making, and even physical harm.
6. Securing the supply chain: Ensuring the security and integrity of the supply chain that supports the development and deployment of ML models is a critical, yet often overlooked, aspect of MLSecOps.

The imperative for embracing MLSecOps
The importance of MLSecOps cannot be overstated. As AI and ML continue to drive innovation and transformation, the need to secure these technologies has become paramount. Adopting a comprehensive MLSecOps approach offers several key benefits:
1. Enhanced security posture: MLSecOps enables organizations to proactively identify and mitigate security risks inherent in ML-based systems, reducing the likelihood of successful attacks and data breaches.
2. Improved model resilience: By incorporating security testing and validation into the ML model development lifecycle, organizations can ensure the robustness and reliability of their AI-powered applications.
3. Streamlined deployment and maintenance: The integration of DevOps principles in MLSecOps facilitates the continuous monitoring, testing, and deployment of ML models, ensuring they remain secure and up-to-date.
4. Increased regulatory compliance: With growing data privacy and security regulations, a robust MLSecOps strategy can help organizations maintain compliance and avoid costly penalties.
Potential reputational and legal implications
The failure to implement effective MLSecOps can have severe reputational and legal consequences for organizations:
1. Reputational damage: A high-profile security breach or incident involving compromised ML models can severely damage an organization’s reputation, leading to loss of customer trust and market share.
2. Legal and regulatory penalties: Noncompliance with data privacy and security regulations can result in substantial fines and legal liabilities, further compounding the financial impact of security incidents.
3. Liability concerns: If an organization’s AI-powered systems cause harm due to security vulnerabilities, the organization may face legal liabilities and costly lawsuits from affected parties.
Key steps to implementing effective MLSecOps
1. Establish cross-functional collaboration: Foster a culture of collaboration between ML, security, and DevOps teams to ensure a holistic approach to securing AI-powered systems.
2. Implement comprehensive monitoring and alerting: Deploy advanced monitoring and alerting systems that can detect and respond to security threats specific to ML models and AI-driven applications.
3. Integrate security testing into the ML lifecycle: Incorporate security testing, including adversarial attacks and model integrity checks, into the development and deployment of ML models.
4. Leverage automated deployment and remediation: Automate the deployment, testing, and remediation of ML models to ensure they remain secure and up-to-date.
5. Embrace explainable AI: Prioritize the development of interpretable and explainable ML models to enhance visibility and transparency, making it easier to identify and address security vulnerabilities.
6. Stay ahead of emerging threats: Continuously monitor the evolving landscape of AI-related security threats and adapt your MLSecOps strategy accordingly.
7. Implement robust incident response and recovery: Develop and regularly test incident response and recovery plans to ensure organizations can quickly and effectively respond to compromised ML models.
8. Educate and train employees: Provide comprehensive training to all relevant stakeholders, including developers, security personnel, and end-users, to ensure a unified understanding of MLSecOps principles and best practices.
9. Secure the supply chain: Implement robust security measures to ensure the integrity of the supply chain that supports the development and deployment of ML models, including third-party dependencies and data sources.
10. Form violet teams: Establish dedicated “violet teams” (a combination of red and blue teams) to proactively search for and address vulnerabilities in ML-based systems, further strengthening the organization’s security posture.

The future of MLSecOps: Towards a proactive and intelligent approach
As the field of MLSecOps continues to evolve, we can expect to see the emergence of more sophisticated and intelligent security solutions. These may include:
1. Autonomous security systems: AI-powered security systems that can autonomously detect, respond, and remediate security threats in ML-based applications.
2. Federated learning and secure multi-party computation: Techniques that enable secure model training and deployment across distributed environments, enhancing the privacy and security of ML systems.
3. Adversarial machine learning: The development of advanced techniques to harden ML models against adversarial attacks, ensuring their resilience in the face of malicious attempts to compromise their integrity.
4. Continuous security validation: The integration of security validation as a continuous process, with real-time monitoring and feedback loops to ensure the ongoing security of ML models.
By embracing the power of MLSecOps, organizations can navigate the complex and rapidly evolving landscape of AI-powered technologies with confidence, ensuring the security and resilience of their most critical systems, while mitigating the potential reputational and legal risks associated with security breaches.
Have access to hundreds of hours of talks by AI experts OnDemand.
Sign up for our Pro+ membership today.
AI Accelerator Institute Pro+ membership
Unlock the world of AI with the AI Accelerator Institute Pro Membership. Tailored for beginners, this plan offers essential learning resources, expert mentorship, and a vibrant community to help you grow your AI skills and network. Begin your path to AI mastery and innovation now.

#Adversarial attacks#ai#ai skills#AI-powered#applications#approach#artificial#Artificial Intelligence#autonomous#Blue#breach#challenge#Collaboration#Community#compliance#comprehensive#compromise#computation#continuous#course#data#Data Breaches#data privacy#data privacy and security#deployment#developers#development#Devops#employees#Explainable AI
0 notes
Text
STOP KOSA CALL IN DAY THE 16TH APRIL 2024

• There will be a hearing on Wednesday (17th April) where KOSA, along with some other bad internet bills, like the Protecting Kids on Social Media Act could be pushed.
• We will be having a calling day on TUESDAY (16 th April) to make clear to Congress that there is still a ton of opposition to these bills. https://energycommerce.house.gov/posts/chair-rodgers-and-ranking-member-pallone-announce-legislative-hearing-on-data-privacy-proposals-1 •We need to contact Congress and urge people to use this site for this https://www.stopkosa.com/
• House Energy and Commerce is holding the hearing so they are the best offices to call this week !! https://energycommerce.house.gov/representatives (the link doesnt work properly so you'll need to head to the site and select "Members" to find them)
• You can use http://badinternetbills.com/ to contact your congresspeople !
• And https://www.house.gov/representatives/find-your-representative to find all of the phone numbers of your House Representative ! •Don't forget to use faxzero.com to send up to 5 free faxes a day ! If you get a response talking about the changes made to the bills, please dont forget to point out it still makes it dangerous as explained here https://www.eff.org/deeplinks/2024/02/dont-fall-latest-changes-dangerous-kids-online-safety-act Here are scripts you can use when contacting reps !

Please make sure to not mention how LGBT people will be affected by KOSA if your rep is republican, they don't care. Use freedom of speech instead like shown above !!! ^^^

Here is the Democrat version ! You may also tell your reps to support privacy legislations instead of the dangerous KOSA bill, as this will actually protect kids and anyone. Check my masterpost for more info And dont forget to join our discord server for the latest news and steps to take ! https://discord.com/invite/pwTSXZMxnH REBLOGS ENCOURAGED ! Making tweets, tiktoks, anything you want to spread awareness against KOSA is welcomed as well !!
#kosa#internet censorship#censorship#kids online safety act#tumblr#discord server#supreme court#us politics
1K notes
·
View notes
Text
Two Harvard students recently revealed that it's possible to combine Meta smart glasses with face image search technology to "reveal anyone's personal details," including their name, address, and phone number, "just from looking at them."
In a Google document, AnhPhu Nguyen and Caine Ardayfio explained how they linked a pair of Meta Ray Bans 2 to an invasive face search engine called PimEyes to help identify strangers by cross-searching their information on various people-search databases. They then used a large language model (LLM) to rapidly combine all that data, making it possible to dox someone in a glance or surface information to scam someone in seconds—or other nefarious uses, such as "some dude could just find some girl’s home address on the train and just follow them home,” Nguyen told 404 Media.
This is all possible thanks to recent progress with LLMs, the students said.
"This synergy between LLMs and reverse face search allows for fully automatic and comprehensive data extraction that was previously not possible with traditional methods alone," their Google document said.
Where previously someone could spend substantial time conducting their own search of public databases to find information based on someone's image alone, their dystopian smart glasses do that job in a few seconds, their demo video said.
The co-creators said that they altered a pair of Meta Ray Bans 2 to create I-XRAY to raise awareness of "significant privacy concerns" online as technology rapidly advances.
572 notes
·
View notes