#decode base64
Explore tagged Tumblr posts
Text
🧬 Base64 Decoding: What Every Developer Needs to Know

Let’s be honest — you’ve definitely come across a weird string of letters and slashes ending in “==” and thought:
“Yeah, that’s Base64… but what the heck is it really doing?”
Welcome to your crash course. 🧠💻
🔍 What Even Is Base64?
Base64 is how we turn messy binary data into readable text — perfect for email, APIs, or sending files over the web. It uses a special 64-character set (A-Z, a-z, 0-9, +, /) to encode data safely into ASCII. Clean, compact, and protocol-friendly.
🧩 Example: You → upload an image → server encodes it to Base64 → sends it in a JSON → you decode it back to… pixels!
📦 Where You’ll See It
Base64 is everywhere:
🖼 Embedded images in HTML/CSS
🔐 JWT tokens and API keys
📦 Binary files in APIs
📧 Email attachments
📁 Config files and logs
📱 Mobile backend comms
If you’re building or debugging anything beyond a to-do app, you’ll hit Base64.
🛠 How to Decode It Like a Pro
🧑💻 Tools:
base64 -d (Linux/Mac CLI)
Online decoders (for quick checks)
Code:
Python: base64.b64decode()
JS: atob()
Java, C#, Go, etc. all have built-in support
Bonus: most browser DevTools and IDEs can decode Base64 too! https://keploy.io/blog/community/understanding-base64-decoding
✅ Best Practices
✔ Validate input before decoding ✔ Handle padding (= at the end) ✔ Know what the output should be (text? image? zip file?) ✔ Be super cautious with user-supplied data (hello, malware 👀)
🧠 Pro Techniques
Streaming decode big files (don’t blow up your memory)
URL-safe Base64 (replaces + with -, / with _)
Custom alphabets (legacy systems love weird stuff)
Know the variant you're working with or your decoder will cry.
🐛 Common Gotchas
Missing/extra padding
Non-standard characters
Encoded inside a URL (needs double decoding)
Newlines and whitespace (strip ’em!)
🔄 Real-World Dev Workflows
CI/CD pipelines decoding secrets and config
API testing tools validating Base64 fields
Git diffs showing Base64 blobs
Debugging mobile apps or IoT devices
Basically: If your app talks to anything, Base64 shows up.
🔧 TL;DR
Base64 is the bridge between binary chaos and readable text. Learn to decode it confidently and you’ll:
Debug faster
Build cleaner APIs
Catch sneaky security threats
Save your teammates from “what’s this encoded blob?” horror
Oh, and if you want to auto-test and validate APIs that use Base64? 👉 Keploy is your new best friend. Mocking + testing with encoded data made simple.
0 notes
Text
Transcript:
Who up wombing right now?
Audio source
#for those who Don’t Know#in the new update the main menu got an overhaul#part of it has code in the background and some of the code is in base64#when decoded it translates to ‘womb’#and people thought it meant V1 has a womb#but it’s just a header file#a header file is a way of adding already existing code into a different file without directly copying and pasting it#so it’s just using things from a file called womb#does that make sense#if you want a technical explanation just look up ‘what’s a header file’ and ‘what does [hashtag]include do’#BUT DONT LET THAT STOP YOU#freak activity is always encouraged here do crazy things to that machine#you can put any organs you want in there
87 notes
·
View notes
Text

chantry fun with colours
#aurielsart#skyrim#SORRY ITS SO CRUNCHY I GOT REALLY NERVOUS AND MADE IT INTO BASE64 AND THIS IS THE THUMBNAIL THE DECODER GAVE ME
76 notes
·
View notes
Note
(GET)(IT)(THROUGH)(TO)(THE)(GREEN)(MAN)(.) (THE)(OTHERS)(CAN'T)(INTERCEPT)(ANONS)(.) (aHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Y2g/dj1fNEtOblN3VGZzcw==) (HAVE)(HIM)(TYPE)(IT)(IN)(THE)(CONSOLE)(OF)(THE)(PC)(.) (GET)(M̴͕̽É̵͇)(Ȯ̸̢͎U̷̗̯͐̃̍T̵͉̆̾̒)(O̶͉̒ͅF̸̢͚̀̏̌)(H̵̭͋́̔́̄͐͂̒̈́̔̊͌̕E̷̳͇͑̒̕R̷̼͍̹̯̖̩͌̋̎̾͌́͋̾̓͗͑̕͘͠ͅḘ̸͕̓̄̒̅̋̈́̉̉̓͆̕)
This thing has no moral compass, no true emotion.
Do not let it escape. It has no place here.
#the code is just an easter egg if you decide to decode it btw#regretevator#regretevator roblox#roblox regretevator#paranormal gradient#“NEURO”#ITS A BASE64 CODE ITS A BASE64 CODE
32 notes
·
View notes
Text
@blue-tearss - [previously...]
Qmx1ZSdzIHdvcmRzIHN0aWNrIGluIGhpcyBtaW5kLSB0aGF0IGdvZGRhbW4gcHJlZGV0ZXJtaW5lZCBzY3JpcHQsIG9uZSBvZiB0aG91c2FuZHMsIHRoYXQgYXJlIHdvdmVuIGludG8gdGhlIHZlcnkgY29yZSBvZiBoaXMgYmVpbmcu
Red seems to visibly bristle at the other's words, the corners of his twisted grin twitching, spreading further, growing darker. He huffs- half coughing, half laughing, spitting saliva and blood that he quickly tries to choke back down.
SXQgZWNob2VzIG92ZXIgYW5kIG92ZXIgdGhyb3VnaCBoaXMgbWluZCwgbHVya2luZyB1bmRlciBldmVyeSB3b3JkIHRoaXMgbW9ja2VyeSBvZiBoaXMgcml2YWwgc3BlYWtzLCBhbmQgdGhyZWF0ZW5zIHRvIG92ZXJ3aGVsbSwgZHJvd24gb3V0LCBlcmFzZSBmcm9tIGhpcyBtaW5kLCBldmVyeSBtZWFuaW5nZnVsIHdvcmQgdGhlIG90aGVyIGhhcyB0byBzYXku
"Hah--" he croaks, wiping a hand over his face, willing himself to speak clearly, coolly. "Way to not answer my question, asshole. You managed to babble off every fuckin' thought in that head EXCEPT the one I asked for, didntcha?"
VGV4dGJveGVzIHRvIG1hc2ggdGhyb3VnaCwgcGF0aHdheXMgdG8gZm9sbG93LCBwaXhlbHMgdG8gd2lwZSBhd2F5LCBhbGwgZmlnaHRpbmcgdG8gZm9nIG92ZXIgaGlzIHZpc2lvbiBhbmQgdGhyZWF0ZW5pbmcgdG8gZmxpbmcgaGltIGJhY2sgdG8gYSB0aGlyZC1wZXJzb24gdmlldyBvZiBhbiBlaWdodC1iaXQgYm9keSBvZiBub3RoaW5nIGJ1dCBwcmVkZXRlcm1pbmVkIGFuZCBjb3JydXB0ZWQgY29kZSwgYW4gZXhpc3RlbmNlIGFuZCBtZWFuaW5nIG5vIGRlZXBlciB0aGFuIHRoZSBST00gY2hpcCBhbmQgY2lyY3VpdGJvYXJkIG9mIGEgYnJva2VuIEdhbWVib3kgQ2FydHJpZGdlLQ==
He folds his arms behind his back and paces closer to the other, feigning a darling, innocent expression. He's not very good at it. "All the same, I guess it doesn't really matter. You're such an open book, it's laughable. I know that look. I know those tricks. I can see it in your fucking EYES. You're DESPERATE." The aggressive environment seems to grow more and more restless. The stinging, numbing, biting, ripping, tearing of the very earth beneath Blue- if you could even call it that anymore- clings tighter, digs deeper, threatens to sink its teeth in, draw blood, tear something away that is much more fundamental than flesh. It remains just a threat, but undoubtedly, it still hurts. Wants to make that hurt known. Wants to make him know, fear, how much worse it could get. Wants him to remember just whose turf he has intruded in on.
cGh5c2ljYWwgc2Vuc2F0aW9ucyB0aHJlYXRlbmluZyB0byBzdWJzaWRlIGludG8gc3RhdGljIGFuZCBnYXJiYWdlIGRhdGEsIGZvcmNpbmcgaGltIHRvIGNsaW5nIHRvIHRoZSBzdWZmb2NhdGluZyBwYWluIHRoYXQgYnVybnMgYW5kIHJpc2VzIGZyb20gaGlzIHN0b21hY2ggdG8gaGlzIHRocm9hdCwgYSBmbG9vZCB0aHJlYXRlbmluZyB0byBzcGlsbCBmcm9tIGhpcyBsaXBzLCBhbGwgdG8ga2VlcCB3aGF0IGxpdHRsZSBzZW5zZSBvZiByZWFsaXR5IGhlIGhhcyw=
Red is either unaffected or uncaring of the environments growing agitation. "Desperate for something to change," he chimes, his voice a mocking, sing-song tone, "something new, 'cause pulling shit like this will surely give you SOMETHING to feel, won't it~?" His gaze turns all the more intense, and through a gag, the childish tone drops completely. His next words, half-gargled and low as a whisper, sound more like the spitting snarls of an animal. "You must think you're real hot shit, must think you're REAL fucking clever. You found something NEW to play with, something much more tangible to rip to pieces than your own predictable, dusty-ass, BROKEN-ass game, right? Don't think I missed the BLOOD on your hands, you son of a bitch."
YSBkZXNwZXJhdGlvbiB0aGF0IGhlJ3MgZmVsdCB0aW1lIGFuZCB0aW1lIGFuZCB0aW1lIGFuZCB0aW1lIGFuZCB0aW1lIG92ZXIgYW5kIG92ZXIgYW5kIG92ZXIgYWdhaW4gdGhhdCdzIGZvcmNlZCBhbiBhZ29ueSB0aGF0IGZlZWxzIGxpa2UgZGVhdGggdG8gYmUgaGlzIG9ubHkgc2FsdmF0aW9uLCBzb21lIGtpbmQgb2YgbmF1c2VhdGluZyBtYXNvY2hpc20sIGdvZC1hd2Z1bCBwYWluIGFzIGEgbWVhbnMgdG8gc2F0aWF0ZSBhIG5lZWQgZm9yIHBsZWFzdXJlOg==
In the blink of an eye- an instance of a single frame of motion, Red stands inches away from Blue, blood red eyes burning into ocean blue, before his hands snap forward to grab him by the collar. Contact with Red's hands, even just to his clothes, sends that boiling, burning, electric rush of fuzzy and numbing pain through Blue's chest- the bite of Glitch City concentrated and amplified through one person. "I would personally recommend that you stand the fuck down and stop talking like that before something bad happens. Because I'm starting to get the idea that you really, really don't know what you're messing with." Red practically spits in his face, words laced with malice and an unspoken threat.
dGhlIHBsZWFzdXJlIG9mIGRlbHVkaW5nIGhpbXNlbGYgaW50byBiZWxpZXZpbmcgdGhhdCBoZSBpcyByZWFsIGZvciBqdXN0IGxvbmcgZW5vdWdoIHRvIGtlZXAgdGhlIGFjdCB1cC4=
#mn noncanon#[i havent gotten to write red getting mad for reals yet umm. teehee.]#unreality#unreality tw#[<- this is for the base64 text. decode at your own risk!]#glitchy red tajiri#blue-tearss#[guhh no illustrations also.. i wanted 2 get one of my replies out auohrhog]#[ill get back to cody soon i have that one all written out i just Definitely wanna draw for it..]
13 notes
·
View notes
Note
Whhsjhuhhhbdh dbd hm. Shdkmn log 7
while there exists the temptation to figure out if this is a code or something I am going to resist the snakes whispers because I will not be pulled into a horror arg like all those white boys on YouTube
#this is kind of a lie I did plug this into a base64 decoder just to see#but it turned up nothing so that’s the extent of my decoding attempts#ask#anon
13 notes
·
View notes
Text
I've just finally seen some Fun Malware. Where it's like weird, obfuscated but not so much that it's total gibberish, but in a way that's pretty blindingly obviously malicious. I don't have the powershell knowledge to decode it myself easily, it'd probably take a week of studying at least to do it by hand, and I don't have a sandbox to run it and look at the logs. Malware analysis is not my thing, it's kind of a fucking nightmare. However. This is Code Analysis, and programming is the interest that started my entire career.

#Just made a scary call to customer and the whole time i'm like yes... hahaha.... YES!!!!#I actually don't think it'd be that hard I'd just have to do the string fuckery and then decode from base64 that's like 98% of the script#Me whenever I see computer science: Neuron activation#soc posting#This might make me seem smart but you should know I considered googling 'how many letters are there' just now
3 notes
·
View notes
Text
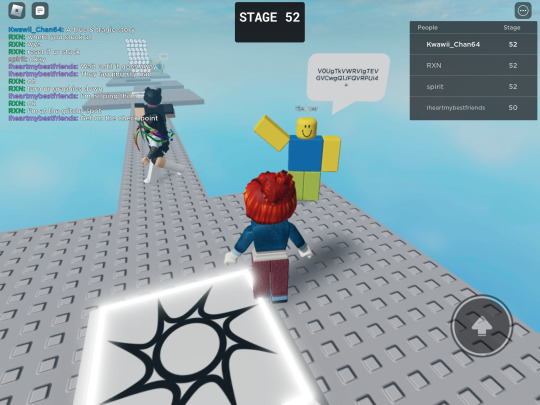
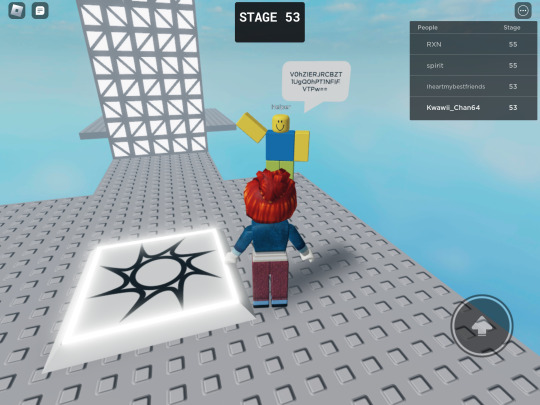
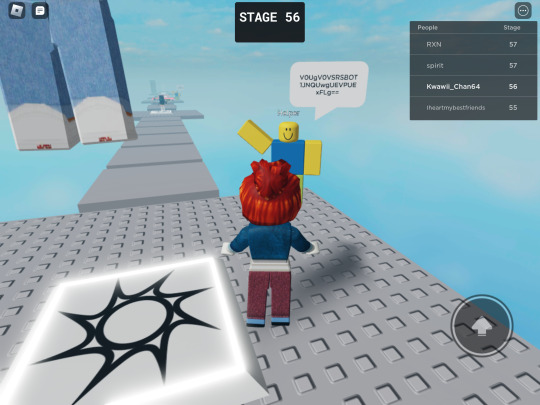
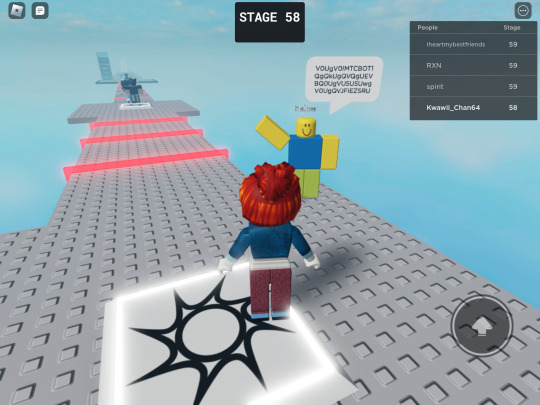
So I played stereotypical obby on Roblox and while I was playing it & made it to 50 , I found helper saying some random things. It was basically Base64 so I decode it & it translated to this:
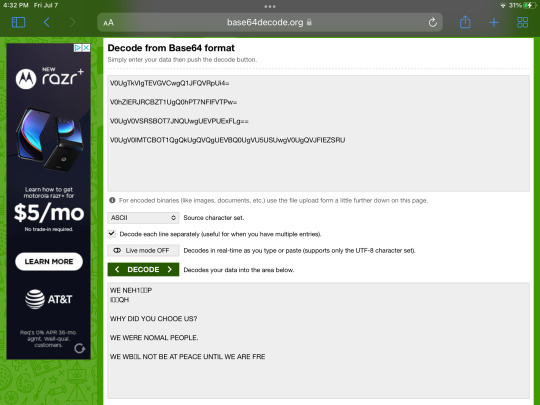
We Never Left, Creator.
Why did you chose us?
We are normal people.
We will not be in peace until we are free.
18 notes
·
View notes
Text
Matrix Breakout: 2 Morpheus
Hello everyone, it's been a while. :)

Haven't been posting much recently as I haven't really done anything noteworthy- I've just been working on methodologies for different types of penetration tests, nothing interesting enough to write about!
However, I have my methodologies largely covered now and so I'll have the time to do things again. There are a few things I want to look into, particularly binary exploit development and OS level security vulnerabilities, but as a bit of a breather I decided to root Morpheus from VulnHub.
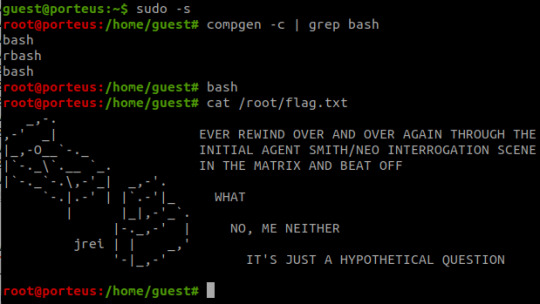
It is rated as medium to hard, however I don't feel there's any real difficulty to it at all.
Initial Foothold
Run the standard nmap scans and 3 open ports will be discovered:
Port 22: SSH
Port 80: HTTP
Port 31337: Elite
I began with the web server listening at port 80.

The landing page is the only page offered- directory enumeration isn't possible as requests to pages just time out. However, there is the hint to "Follow the White Rabbit", along with an image of a rabbit on the page. Inspecting the image of the rabbit led to a hint in the image name- p0rt_31337.png. Would never have rooted this machine if I'd known how unrealistic and CTF-like it was. *sigh*
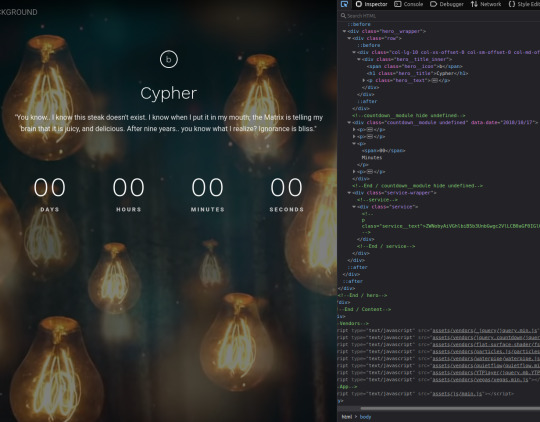
The above is the landing page of the web server listening at port 31337, along with the page's source code. There's a commented out paragraph with a base64 encoded string inside.
The string as it is cannot be decoded, however the part beyond the plus sign can be- it decodes to 'Cypher.matrix'.

This is a file on the web server at port 31337 and visiting it triggers a download. Open the file in a text editor and see this voodoo:
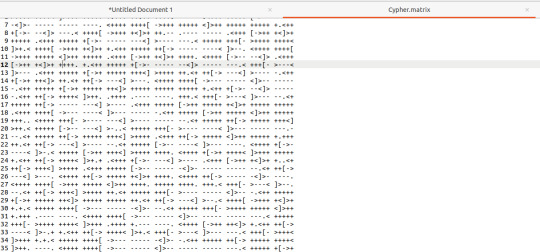
Upon seeing the ciphertext, I was immediately reminded of JSFuck. However, it seemed to include additional characters. It took me a little while of looking around before I came across this cipher identifier.

I'd never heard of Brainfuck, but I was confident this was going to be the in-use encryption cipher due to the similarity in name to JSFuck. So, I brainfucked the cipher and voila, plaintext. :P
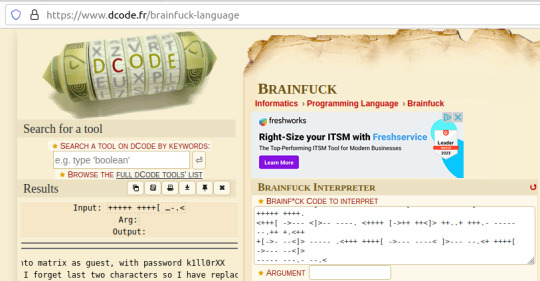
Here, we are given a username and a majority of the password for accessing SSH apart from the last two character that were 'forgotten'.
I used this as an excuse to use some Python- it's been a while and it was a simple script to create. I used the itertools and string modules.
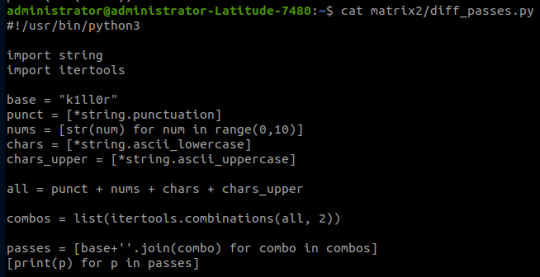
The script generates a password file with the base password 'k1ll0r' along with every possible 2-character combination appended. I simply piped the output into a text file and then ran hydra.
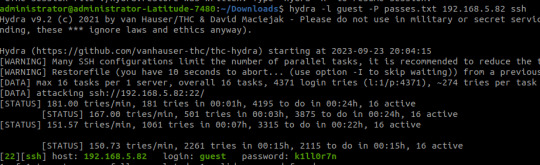
The password is eventually revealed to be 'k1ll0r7n'. Surely enough this grants access to SSH; we are put into an rbash shell with no other shells immediately available. It didn't take me long to discover how to bypass this- I searched 'rbash escape' and came across this helpful cheatsheet from PSJoshi. Surely enough, the first suggested command worked:

The t flag is used to force tty allocation, needed for programs that require user input. The "bash --noprofile" argument will cause bash to be run; it will be in the exec channel rather than the shell channel, thus the need to force tty allocation.
Privilege Escalation
With access to Bash commands now, it is revealed that we have sudo access to everything, making privilege escalation trivial- the same rbash shell is created, but this time bash is directly available.

Thoughts
I did enjoy working on Morpheus- the CTF element of it was fun, and I've never came across rbash before so that was new.
However, it certainly did not live up to the given rating of medium to hard. I'm honestly not sure why it was given such a high rating as the decoding and decryption elements are trivial to overcome if you have a foundational knowledge of hacking and there is alot of information on bypassing rbash.
It also wasn't realistic in any way, really, and the skills required are not going to be quite as relevant in real-world penetration testing (except from the decoding element!)
#brainfuck#decryption#decoding#base64#CTF#vulnhub#cybersecurity#hacking#rbash#matrix#morpheus#cypher
9 notes
·
View notes
Text

🌀 "The Seer", encrypted.
A work in process for process zine #00 — this spread translates a full-colour painting into raw Base64 code. The wall of characters becomes a veil, a kind of static field — a metaphor for the liminal experience of Auditory Processing Disorder (APD), where the signal is present but inaccessible without the right decoder.
The artwork, The Seer, is hidden in plain sight. Digitised, fragmented, and embedded in the code itself.
When the zine is complete, the full Base64 string will be included as a hidden annotation in the digital PDF. Readers will be able to extract and decode the painting — transforming static back into signal, and signal into sight.
For now, it exists as encrypted presence.
This is the painting, encrypted. Decode the full Base64 string from the PDF’s hidden annotation to reveal The Seer.
#base64#encryption#code to image#signal and noise#decode#APD#auditory processing disorder#liminal experience#visual poetry#data as art#glitch aesthetics#conceptual art#process zine
0 notes
Text
Camp Camp Season 5 Episodes!
One of my friends was kind enough to lend me their first account so i screen recorded the first 2 episodes! I'll continue to do this as they come out! Feel free to share these around or add them to personal archives if you wish :D Link:
aHR0cHM6Ly9tZWdhLm56L2ZvbGRlci9sdVZXbEJpYSNXOUJYaHFzOW9DQnB2Z05nQVNtR0p3
Decode here:
https://www.base64decode.org/ (link is coded into base64 to make it harder to flag/take down)
Enjoy! :D Edit: If you have any trouble with the link please feel free to dm me for help! :D
502 notes
·
View notes
Note
[ ARCHIVED BROADCAST || READ ONLY ] COMMUNICATIONS MANIFEST SOURCE NODE TRACE: FGS_ROOT, FGS_COMM06, 464753_SPIRE02 || DESTINATION: TSAC_COMM02 [[ WARNING: MESSAGE IS ENCRYPTED. ]] APPLY DECRYPTION KEY? Y/N >Y ENTER KEY: ****** MESSAGE CONTENTS: FGS: This is Fleeting Green Sunsets. Can anyone read me? [ Message has been uploaded to Zenith Archives, Sector RKDT01 ]
I must wonder: have you ever encountered a failed broadcast, corrupted or otherwise?
TSAC: Corrupted broadcasts are commonplace. They often occur as a result of interruptions during radio transmissions, caused either by environmental factors or damage to associated communications arrays.
If a communications tower fails to transmit a message for one reason or another, the data is dumped into a local storage medium (usually a pearl) for the sake of preservation. The data then needs to be retrieved manually by an Overseer in order to be recovered.
Data recovery subroutines can be used to reconstruct partial transmissions, but broadcasts caused by faulty or decaying equipment often become corrupted. I usually ignore these signals. However, occasionally an abnormal broadcast will catch my attention.
An Overseer of mine patrolling the nearby long-range communications spires retrieved one such broadcast rather recently...
[ OUTGOING REQUEST ] COMMUNICATIONS MANIFEST [[ERROR]] UNABLE TO SEND - Malformed Message Header SOURCE NODE TRACE: (NULL)_ROOT, (NULL)_COMM06, 464753_SPIRE02 || DESTINATION: (NULL)unknown group MESSAGE CONTENTS: --- FATAL EXCEPTION: UNABLE TO RENDER MESSAGE CONTENTS INVALID SYMBOL AT LINE 01, SEQUENCE 08. LINE 03 MISSING TERMINATING EXPRESSION. == BROADCAST IS CORRUPTED. == ATTEMPTING RECOVERY. PARTIAL BROADCAST RECOVERY SUCCESSFUL. RAW CONTENTS: 01010010011010110110010001010100010011110110100101000010010101010110000101000111011010110110110101001001010001110110110001111010010010010100010101011010011100110101101001010111010101100011000001100001010101110011010101101110010010010100010101100100011110010101101001010111010101100111010101001001010001100100111000110001011000100110111001001110011011000110010001001000010011010111010101001001010001010100111001101000011000100110100101000010011010000110001001101110011011000111011001100010011011010101010101100111011000110110110101010110011010000101101001000011010000100111010001011010010101000011100000111101 [ Pending upload by dispatched Overseer. Unit will enter read-only state in 146 cycles. ]
#corrupted broadcast#in case anyone was wondering: the cipher was base64 > binary#so do that backwards to decode it
77 notes
·
View notes
Text
apologies for slow uploads, have this:
aHR0cHM6Ly9kcml2ZS5nb29nbGUuY29tL2RyaXZlL2ZvbGRlcnMvMUxDUGEyV3JnZFpVdHFvNVVPeVZYLTJCWHpJTnVZQVJDIFJFQUQgVEhFIFJFQUQgTUUgRklMRSE=
that you absolutely do NOT need to decode from base64 in order to get a link to a google drive full of resources
69 notes
·
View notes
Note
SGVsbG8gZG9jdG9yIA==
-🌀
@the-caterers
(Ooc: try a base64 decoder)
Hello to you too!
23 notes
·
View notes
Text
ok so 4cvit , Legundo, Lynxyliam, Wadebox, HilmCC and Leg.GG seem to be doign some arg thing on twitter and im putting it together here
Here are the links to each post : 4CVIT, Legundo, LynxyLiam, WadeBox, HilmCC, Leg.GG
When I mention someones @ it refers to the one on twitter
1) Each one has a code written on the side which is HEX code. Each one has the name of one person that posted a weird image so, 4C-> Legundo->HilmCC->LynxyLiam->Wadebox->LEGgg -> 4C
2) There are flowers art the top or bottom of each post. They match in pairs so one ofthem is the top half of the flowers and the other is the bottom half. The pairs are: Legundo & wadebox hilmCC & Lynxyliam 4cvit & Leggg
3) Lynxyliam's post has a QR code that when scanned it shows this: the l.eav-es b-attl.e to s/teal t.he su.n b.ut on-ly th/e tallest p.eta-ls bl-oo.m Which is a sentence with morse hiden in it that translates to: PVP
4) @/vikjayced found that the code on 4C's post trhough Bacon cypher translates to DEFEND
5) @/profpie2000 found that the binary on Legundo's post translates to COLLECT
6) Wadebox's post has a quote from Macbeth in the background The left is the orignal text and the right is a modern english version

7) LEGgg has a barcode at the bottom that when scanned shows that it means 25 Teams
8) By the way LegGG is legundo's server with like minigames and stuff. Probably means that this ARG is hinting at some event or new addition to the server
9) xiu-dian in the replies found that when taking the string on HilmCC's post as Qy1jb21wZXTEq3RvcsSTcw== and decoding with base64 it comes out as "C-competītorēs". Im not certain if this is correct but its the only result that makes some amount of sense. If its correct maybe it hints at spanish speakers being in or maybe 3 players per team or something idk.
10) I was told that in January 4C hinted at something in a post that seems to be related to what this event will be.
11) @/cyjen_ figured out that the C_competitors on HiImCC's tweet was refering to C in roman numerals which is 100. So 100 players. Wadebox is saying one part of the puzzle is msising and posing rose emojis
12) LAST CLUE HAS BEEN SOLVED. People on wadebox's discord server found that the flowers in the middle connecting the images have values assigned to them in bedrock mc. These correspond to a unix timestamp giving a date and time.
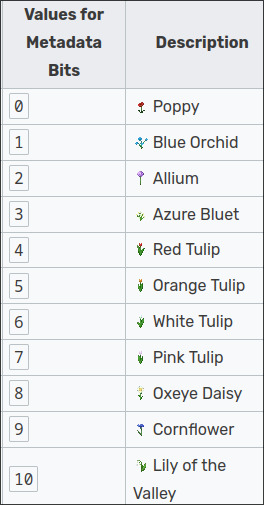
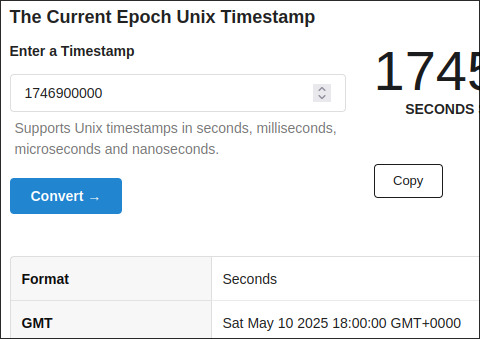
My theory is that this is all hinting to some sort of event in collaboration with LegGG that the 5 worked on together. Might be flower themed. I dont think its a permanent addition to the server becuase 25 teams is too big but I might be wrong. It will be focused on pvp and will have some mechanics that involve defending and collecting stuff. The macbeth quote implies that there will be ways of stealing from other teams. The event will happen on the 10th of may at 6 pm GMT
#4cvit#Legundo#Wadebox#lynxyliam#HiImCC#ITS BEEN SOLVED#props to all the goats in the community who figured stuff out#i was not smart enough to figure out most of it
28 notes
·
View notes
Text
#nerd#making it ledgable#you know people would be decoding that
I was going to but cyberchef spit out something prettier
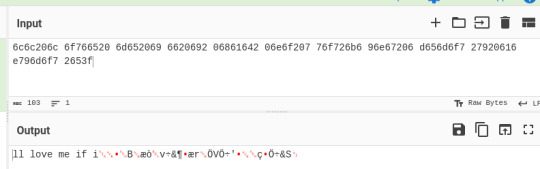
would you still love me if i were a Pi Pico? would you still love me if my power supply was failing? would you sti6c6c206c 6f766520 6d652069 6620692 06861642 06e6f207 76f726b6 96e67206 d656d6f7 27920616 e796d6f7 2653f
#The full sentence is “would you still love me if i had no working memory anymore?” which i think works better if the reader puts in the#effort to decode it#where most people wouldn't#that's part of the whole thing#btw for anyone reading along it was just ascii values encoded as hex it's probably the easiest to decode after base64
35 notes
·
View notes