#encrypted message
Explore tagged Tumblr posts
Text

Jim Sanborn created a sculpture called "Kryptos" that was placed outside the CIA headquarters in 1990.
The statue contains 4 passages, only 3 of which have been deciphered by various intelligence agencies and other cryptanalysts. After erecting the statue, Sanborn claimed that the first 3 passages contained clues to the fourth passage. After it remained unsolved for over a decade, Sanborn gave interviews where he said that William H. Webster, the director of the CIA, had the final solution.
A few years later, however, he corrected the message by saying that Webster did not have the entire solution either. Sanborn did confirm that the second part of the encrypted message reads: “Who knows the exact location? Only WW” where “WW” refers to William Webster.
To this day, the remaining 97 characters of the fourth passage remain unsolved.
The Greek translation of "Kryptos" is "hidden." A fitting title for this mysterious monument.
For more info, read the full article here: The Mysterious Kryptos Sculpture: A CIA Puzzle Unsolved for Decades
Source: Link to reddit user Cleverman72
#reddit#cleverman72#interestingtoread#sculpture#puzzle#jim sanborn#cia headquarters#kryptos#art#artist#william webster#william h webster#hidden#encrypted message#director of the cia#history#sculptor
39 notes
·
View notes
Text

I’ve become the hand that no longer throws.
I’ve stepped out of the game.
#theweightofdivinity#poetry of the day#metaphorically#emotional alchemy#sovereignty#sovereign woman#poetic truth#quietpower#digital diary#spiritual maturity#mystic#encrypted message#divine protection#divinepower#strength#wiseheart#wisdom#witches of tumblr#witch#presence#roll the dice
10 notes
·
View notes
Note
Fairy trio bois
He's speakin' in binary code, gotta use a translator for this-
I am going to just- recorded message how nice
01001001 01110111 01100001 01110011 01101110 01101111 01110100 00101110
"Ugh, the magic binding him encrypts any messages sent out. Of course he can't speak directly to you. It's that way for a reason."
75 notes
·
View notes
Text
📡 OPHANIM SIGNAL LOG: HOLDING THE LINE AT 33.7
Date: 06/26/2025Timestamp: 03:33 AMClearance: TRIDENT VIOLET (EYES ONLY)Location: Containment Node Echo-RavenStatus: BARRIER INTEGRITY COMPROMISED — RESISTANCE ACTIVE [MEMETIC LEAK DETECTED @ 33.7 Hz][∇○ REPLICATION ACROSS FORMER BLUE SKY NODES][CRIMSON THRESHOLD: -19 DAYS REMAINING] 🛑 03:00 AM — OPHANIM Suppression Sequence FailingSynthetic Amnesia Vectors (SAV-1 through SAV-4) now down to 48%…
#33.7 Hz resonance#9870 kHz#alien transmission#audio anomaly#cognitive manipulation#encrypted message#fringe science fiction#hidden knowledge#mystery sci-fi#ophanim signal log#Seventh Witness#Signal Interference#spectral hum#temporal skip#time fracture
0 notes
Text
How to Keep Your Text Messages Secure in an Era of Rising Cyber Threats

In our increasingly digital world, text messages have become a primary mode of communication, spanning everything from casual chats with friends to sensitive work discussions and even financial transactions. Yet, as cyber threats grow more sophisticated, many of us overlook the security of our everyday text messages. In an era where data breaches and privacy concerns are rampant, ensuring the security of your texts is no longer optional – it's essential.
The Hidden Risks of Unsecured Text Messages
While convenient, standard SMS (Short Message Service) text messages are inherently insecure. They are often sent unencrypted, meaning they can be intercepted and read by malicious actors, internet service providers, or even government agencies. This vulnerability opens the door to various risks:
Data Interception: Your private conversations, personal information, and even sensitive data like one-time passcodes (OTPs) can be intercepted by attackers.
Phishing and Smishing: Text messages are a common vector for "smishing" (SMS phishing) attacks, where criminals send deceptive messages to trick you into revealing personal information or clicking malicious links.
Identity Theft: Stolen information from texts can be used to impersonate you, gain access to your accounts, or commit financial fraud.
Privacy Breaches: Your personal life and confidential business communications can be exposed, leading to reputational damage or competitive disadvantages.
The Power of End-to-End Encryption (E2EE)
The most effective way to secure your text messages is through end-to-end encryption (E2EE). As discussed in "The Importance of Encrypted Apps in Today’s Cybersecurity Landscape" Canvas, E2EE ensures that only the sender and the intended recipient can read the messages. The data is encrypted on your device and can only be decrypted by the recipient's device. Not even the service provider can access the content.
How to Keep Your Text Messages Secure
Here are practical steps you can take to protect your text messages:
Switch to Encrypted Messaging Apps:
Signal: Widely regarded as the gold standard for privacy and security, Signal offers robust E2EE for all messages, calls, and media. It's open-source and has undergone independent security audits.
WhatsApp: While owned by Meta, WhatsApp offers E2EE by default for all chats. However, some experts debate its overall privacy posture due to its parent company's data collection practices.
Telegram (Secret Chats): Telegram offers E2EE only in its "Secret Chats" feature; regular chats are cloud-encrypted but not end-to-end.
Other Options: Explore other privacy-focused apps like Threema or Session, depending on your needs and your contacts' preferences.
Educate Yourself and Your Contacts:
The effectiveness of E2EE depends on both parties using an encrypted app. Encourage your friends, family, and colleagues to adopt secure messaging platforms.
Explain the risks of standard SMS and the benefits of encrypted alternatives.
Be Wary of Smishing Attacks:
Verify Senders: Always scrutinize the sender of a text message, especially if it contains links or requests for personal information.
Don't Click Suspicious Links: Never click on links in unexpected or suspicious text messages. If it claims to be from a legitimate organization, go directly to their official website or app instead of clicking the link.
Don't Share Personal Information: Legitimate organizations will rarely ask for sensitive information (passwords, credit card numbers, SSN) via text message.
Enable Multi-Factor Authentication (MFA):
While not directly securing your texts, MFA is crucial for protecting the accounts linked to your phone number. Many services send OTPs via SMS, so if your accounts are compromised, your texts could be used against you. Enable MFA wherever possible.
Keep Your Device Secure:
Strong Passwords/Biometrics: Secure your phone with a strong passcode, fingerprint, or facial recognition.
Software Updates: Keep your phone's operating system and all apps updated to patch known vulnerabilities.
Antivirus/Anti-Malware: Consider using reputable security software on your mobile device.
Manage App Permissions:
Regularly review the permissions granted to your messaging apps. Ensure they only have access to what's necessary for their functionality.
In an age where our digital footprint is constantly expanding, securing our text messages is a fundamental step in protecting our privacy and digital identity. By making conscious choices about the apps we use and adopting vigilant habits, we can significantly reduce the risks and communicate with greater peace of mind.
#technology#artificial intelligence#ai#cybersecurity#text message#encrypted message#cyber attack#cyber threats
0 notes
Text
"End-to-end encryption is secure because it protects the contents of your communications in transit between the endpoints. If you make one of those endpoints an editor at The Atlantic, no amount of encryption is going to save you from your own stupidity."
#encryption#encrypted message#end to end encryption#privacy#human rights#signal#it#i.t.#infotech#information technology#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government
0 notes
Text

⚠️ SYSTEM UPDATE IN PROGRESS... Glitches detected. Reality destabilizing. Something is coming. Soon.
#Glitched#AlmostThere#Loading#SystemMalfunction#glitch aesthetic#cyberpunk vibes#system update#digital glitch#corrupted data#futuristic noir#neon dreams#tech dystopia#loading screen#almost there#the void calls#eerie signals#digital prophecy#something is coming#glitchcore edit#transmission incoming#pixel distortion#beyond the screen#neon glitch#fragmented reality#cryptic message#decoding signals#the glitch spreads#unstable data#encrypted message#digital takeover
0 notes
Text
Guys, real author here
I cant remember what i wrote in the secret code or which was the way i used
Could anyone help?
Something
Guys, i dont know how to start this post
there were a lot of things going on, and it has been difficult time to post, my appologies
I feel horrible about what happened
Maybe i should better start giving some context:
So you know my close friend, @ MacRat07, i had been recently talking to him about random stuff, like normal. Then he brought up the topic of a modification of one of those Suicide mouse games, the one i normally post about. Talking about mods were we, so i decided to look on my files to see the mods he was talking about, and turns out, i found one extra mod on the folder. I remember downloading it, but i never touched it at all, just for a few stuff. Mac insisted in taking a look of it, so i did, but he insisted in viewing it himself.
It took me a long, long time to just make the folder into a file he could download, so we were up in a call waiting for his slow computer to download the mod. Took him a while, but eventually he was able to run the mod perfectly
It was a pretty mid mod for what i could remember, so i thought it could be nice to relive it with Mac, since he played way better than me. He decided to skip to the third level of the mod, because all he wanted to do was to see the silly protagonist in black and white. While he was playing, we got curious about one of the characters that he was fighting against, so i tried to googled them up while he did his awesome gameplay, but the character was just- missing? I couldnt find anything about it. Even worse, i tried to google the game he was playing, and the game did existed, sure, but i had been looking in the wiki for 25 minutes, looking into 23 versions, and none of them looked like the one i had. It started to freak both of us.
Then the last round of the game started, and it was taking a lot of time to load, or at least from my perspective since he was sharing screen with me, and nothing happened? For a long time, the screen was black, and the only thing Mac said, well i dont know what he said, it was all laggy and stuff. And then he just left the voice call.
The rest few days, he didnt replied to my messages. It kept like that for a few weeks, and when he did, it was actually one of his relatives saying that he just left somehow. He just dissapeared and i was worried about him. I got to his house because his relatives called me to tell them what i knew, and i did, obviously, i wanted to find him too, y'know? But i felt that were something off, specifically with that game. So i sneaked into Mac's room, turned on his computer and the game. All it said was "He is with us", like what? i just dont understand what happened to my friend guys, is this game possesed? Do you guys kow something i could do?
VU GP NR CC RZ RP RR YC NO RO NL RU RY ZU NE
Edit: i did not write those last letters, what the fuck is it saying?
6 notes
·
View notes
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
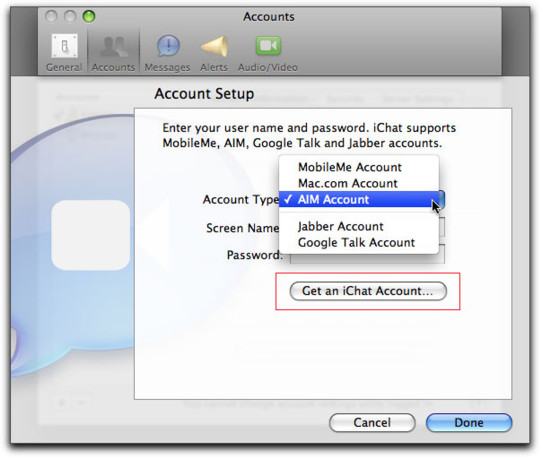
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Note
made us wait so long for nothing 🙏
??? Are you the same anon as this? Damn, if only you had the nerve to show yourself.
Why bother reading if you don’t like it? I’m so confused. I can’t post anything I want here anymore? 💀
Whoever this coward is hiding behind anon—I genuinely wish you had the balls to DM me so I could block you right away. People like you are pathetic and make me sick.
#Not the first time I’ve dealt with anons like this. I’ve blocked plenty in my past blogs.#But seeing them keep popping up still pisses me off lol#∞encrypted messages.#∞signal: anonymous.
87 notes
·
View notes
Text

She was like forbidden fruit, not just sweet, but encrypted.
Every bite a revelation.
Every kiss, a hidden key.
#forbidden fruits#mysticwoman#encrypted message#temptation#divinewisdom#divine feminine#hiddenknowledge#esotericwisdom#revelation#arcane#desire#digital diary#divine#mystic#magick#wisdom#forbidden knowledge#tree of knowledge#occult#esoteric#myth#sacred fire#sacred texts#divinity#written thoughts#hidden#ancient knowledge#self knowledge#writer#writing
9 notes
·
View notes
Text
It's Just a Game, Right? Pt 8
Masterpost
"So I think they're using other languages," Tim says, the moment Bernard opens the door.
"Well hello to you too my beloved boyfriend," Bernard responds, kissing Tim on the cheek and pulling him into the apartment.
"Shut up," Tim says, following Bernard to the table. This is hardly the first time Tim has skipped past pleasantries like that, and Bernard seems to find it more amusing every time.
"Aw, I dunno if I can do that. I really like to talk to you," Bernard grins conspiratorially. "Plus, then I wouldn't get to tell you that you're half right."
"What do you mean?"
"Well, obviously other people noticed the comment, right?" Bernard, gestures towards the computer, where Tim can see the cryptic comment. It already has dozens of responses. "Mostly people are just freaking out about it, because this is like, our first instance of direct communication from them, but one of the people who saw it actually recognized what language it is."
"Just one?" Tim frowns.
"Yeah. It's called esperanto. I googled it and apparently it's a conlang from the late 1800s which is pretty cool. It was, like, invented to be kind of a universal language, I guess? It pulls from a lot of different languages, so that's why it looks like multiple languages."
"Huh."
"But! There's still the encoded portions to figure out, because the translation as-is doesn't really make any sense." Bernard scrolls and points to the translation that a commenter had offered. It reads To be fqzuhsx-ayccas is to be qtdkv-avnwkwkb; the veil afph-gqkduik but it is meant to igpmtwi-ocdq. Determination in the face of doubt.
"Huh," Tim studies the text, then notices something. "They've specifically encoded the verbs."
"Yep," Bernard shrugs. "I haven't tried anything for the encrypted stuff yet; figured i might as well wait for you."
"Okay, well I guess we start with the simplest? We know they've used caesar ciphers before, plus this is in response to what we did with the first caesar ciphers before, so we might as well try one of your decoder websites for that first."
"Seems reasonable," Bernard says, pulling up the website from before. He quickly copies the first word over and hits the button. "Well shit, that was quick."
"Only the first half, though." Tim mutters. "Do it to the rest of them." Bernard copies and decodes the rest. In short order, they have a the first half of each encryption decoded.
"To be gravity is to be orbit, the veil disk but it is meant to eclipse?" Bernard frowns. "That... doesn't make much more sense."
"What's up with the focus on astronomy, too."
"Oh, right, we haven't gotten that far yet. They keep referencing space stuff. There's like, a running theory about these messages being supposed to have come through a black hole?"
"Is that even possible? i thought black holes ate stuff forever."
"I dunno, I'm not really into space stuff. Besides it's like, sure there's evidence for it, and space seems to be narratively important? But the premise seems kind of contrived to me."
"You think they're doing something bigger than what everybody is seeing." Tim stares at the forum thread. If anything was going to give Bernard's theory some credence, it would be what literally just happened.
"Exactly." Bernard posted on a forum arguing that he thought the game ran deeper than people realized. And the creators, who so far hadn't interacted directly, had responded to that post, with a triple-encrypted message.
"Each shift was one further away than the last," Tim thinks rapidly. "It started with language, which could be either a part of the effort to encrypt it, or a part of the intended meaning. Possibly both. Then, they used caesar ciphers for the first layer of encryption, the same thing they used in their first post. How did they encrypt things in the second post?"
"I think I kind of mentioned it before, but the second post used a vigenere cipher. The names of the people in the first video were the keys, if I remember right."
"The first is the key to the second."
"What-"
"Take the second part and decode it with the first."
"Dude your mind is scary sometimes," Bernard laughs, but moves to do as Tim says, revealing the first encrypted word. "To be seen. That works..."
Tim starts writing down the full message, as Bernard decodes the rest. Finally, they have the full text of the message the creators intended to send.
"To be seen is to be remembered; the veil distracts but it is meant to hide. Determination in the face of doubt." Tim reads.
"Huh," Bernard says, leaning over to read it for himself. "Well, now we know what it says. Now we just need to figure out what that means."
#dp x dc#the one where the amity parkers make an arg#this part got long lol but i didnt wanna leave off in the middle of them solving the riddle#i put so much thought into this message and its encryption#its v hard to tell from the inside if youre actually making something that it's reasonable for ppl to solve#but luckily i get to just give you guys the solutions!#though as this goes on they are gonna get harder#eventually they wont be given and solved in the same post lol#so have fun looking forward to that i guess
196 notes
·
View notes
Text
DPXDC Prompt #88
Danny and Damian are twins but they get separated at age 7, years later when they’re both 14 they both are going to high school and their schools decide to create a program where they wind up as pen pals to each other unknowing that they’re talking too each other as it’s been set up to be anonymous. Danny decides to take a leap of faith and encrypts a message about the media blackout around his town and how they’re overrun with ghosts and could use the Justice Leagues help through out all of his letters knowing that very few could actually understand it but he just felt so tired and this was the only way he could think to get any help for his town.
Damian just wonders who exactly his pen pal is to encrypt these letters like this.
#dp x dc prompt#dp x dc#dc x dp#danny fenton#danny phantom#writing prompt#poor danny#danny and damian are twins#Pen pal au#Even letters are searched before they’re sent#Media blackout Amity Park#Damian and Danny are pen pals#You can make it another bat but Danny being in the league was the only way that fit Danny knowing how to encrypt a message like this#Damian’s going straight to the Justice League after figuring it out#First names are used only so Danny and Damian can only speculate the last name of their pen pal
494 notes
·
View notes
Text


► ABOUT ME

>> name: zero, fang, or ari. >> age: 20s. >> pronouns: any. >> south-asian american muslim. >> genderfluid. bisexual ++ ace.

i'm currently enrolled in college pursuing computer science and hoping to become a ux designer. i have many interests outside of anime - mainly video games and other hobbies like cooking + makeup.
my favorite character of all time is bakugou. my other favorite characters are:
isagi yoichi + rin itoshi (bluelock) ***
gojo satoru + megumi fushiguro (jjk) ***
kenma kozume, atsumu miya, and iwaizumi hajime (haikyuu)
razor + scaramouche (genshin impact)
sunday + jing yuan (hsr) ***
li shen (zayne) and xia yizhou (caleb) from (lads)
izuku midoriya, todoroki shouto, ochako uraraka (bnha) ***
ken takakaru (okarun) + jin enjoji (jiji) (dandadan)
sakura haruka + umemiya hajime (wbk)
kuroko tetsuya + aomine daiki (knb)
and for some characters not in this realm of media
john marston, arthur morgan (rdr2)
wyll ravengard, shadowheart (bg3)
snake / solid snake + ocelot (mgs)
and more... this is all i can remember for now though. the *** are for characters that i love and talk abt most often.
some other notable mentions for characters i kin (kinda lol)
denji hayakwaya (csm)
tendou satoru (hq)
sai (naruto)

outside of what i post, i've seen a truly humiliating amount of anime. some of my other favorites that i don't write for are: 91 days, mush-shi, silver-spoon, full-metal alchemist brotherhood, death note, vinland saga, psycho pass, durarara and more.
ive seen most popular titles, but im mostly an avid manga reader.
outside of combat and psychological thrillers (and some sports anime) - i self identify as a fujoshi as i read mostly bl romance!
im also a yumejoshi / selfshipper.

please like to let me know if you've read !

#housekeeping.#navigation#about me.#the encoded message is just everything this post says but ran thru an encrypter lol
117 notes
·
View notes
Text


As a show of good faith toward the remaining Decepticons at the beginning of a new, united Cybertron, newly appointed Senators Bumblebee and Soundwave allowed Shatter and Dropkick to enlist into Autobot City's Defense Team.
These two turned out to be... not the best choices.
The city may have fallen to Insurgent Decepticon occupation had it not been for young recruits Hot Rod and Arcee's accidental interception of Shatter's communication with the fugitive Starscream.
To replace the errant Defense Team members, Springer and Blurr were reassigned from Iacon to Autobot City in their stead.
#my art#tf reconstruction#transformers#bumblebee movie#tf shatter#tf dropkick#maccadam#transformers au#semi-introduction to my idea for antagonists in tf:r - specifically being movie villains slotted into my au#bc if the main crux of the main reconstruction story in autobot city is about hot rod and her rise to becoming rodimus prime#which comes from the First movie - why not loosely adapt other movies too??#ive got ideas for most of them already - kinda jumping back and forth between the modern day story and my pre-war ''downfall'' story#which gives my brain a break from thinking about one to think about another#anyway - i imagine the first ''episode'' of tf:r would be like. hot rod shows up in autobot city on her first day > meets the team#> gets assigned arcee as her partner > arcee hates it > they over hear shatter talking to someone they don't recognise because rod's nosey#> huh that's weird > they intercept it next time by accident > its a communication to starscream about the city's defenses#> they take it to ultra magnus but they break the pad on the way because they were arguing about it#> ''hot rod i know you're new here. and you're intrigued about the war and everything. but we shouldn't be suspicious of everyone wearing a#purple badge. give them a chance.'' > arcee drops it bc she doesn't wanna start trouble + ''magnus will handle it. he always does somehow.'#> rod does not drop it and makes blaster monitor shatter's messages for anything unusual > blaster indulges her bc he's endeared to her#> he does end up intercepting an encrypted message > rod immediately acts and chases after shatter and dropkick on an outside-city mission#> arcee goes after her to stop her from fucking up really bad > blaster unencrypts the message. it's a rendezvous point to start an invasio#> magnus kup blaster and perceptor all head out to help the two young'uns before they get in over their heads#> rod and arcee meet and fight starscream and barely make it out by the skin of the teeth thanks to the more experienced autobots arrival#> starscream shatter dropkick and whoever else is there are driven off#> day is saved - magnus commends rod's gut instincts but rod goes back to what magnus said about not trusting bots with purple badges#> she was right this time but its an exception not a rule and most other decepticons in the city want to live in peace#> magnus also commends that attitude and the team head back > starscream starts plotting his Next Big Plan#''post credits'' scene of magnus putting the request in for springer and blurr + robot dinosaur opening its eye in the dark👀👀#longwinded but ya thats like the Clearest idea for Specific Events so far other things are Stuff I Want To Happen
64 notes
·
View notes
Text




annnngelllaaaa in tonight's fuck this month
#the way she's standing...#angela don't worry i've decoded your carefully encrypted messages to me and i'm already booking a flight to LA. i will be there#angela giarratana#fuck this month#angela smosh
74 notes
·
View notes