#enterprise security solutions
Explore tagged Tumblr posts
Text
I'm sick, so I'm comfort-watching Voyager. I GOT sick because I crammed myself on four different flying sausage tubes over a period of three days so I could go to my son's graduation. I spent my flying sausage tube time reading Murderbot.
Now that you have context, let me just say: watching Voyager through a Murderbot lense is... something.
Tuvok. Janeway. Look me in the eye.
When one of your crew... one of your engineers, ffs... defects to a hostile nation...
YOU ROLL OVER YOUR FUCKING SECURITY CODES.
The Kazon come in firing and they're on the bridge like, "Wow, their weapons are going right through our shields, it's like they have our codes" YOU HAD AN ENGINEER DEFECT TO THE KAZON LAST WEEK ARE YOU TELLING ME YOU DIDN'T DO A SECURITY REVIEW FOR SYSTEM VULNERABILITIES OMGGGGGGGGGGGGG
Vulcans aren't actually any better at doing their own security than humans. Tuvok, SecUnit would be so mad at you.
#the murderbot diaries#star trek voyager#st:voy#This does remind me of that TNG episode 'Contagion'#where the Enterprise is infected by what is essentially an ancient virus#and I'm sitting there going 'I'm not a computer person but have you tried System Restore'#And then the solution was turning it off and turning it back on and I yelled at the screen bc it took them the full hour to try that#apparently living in fully automated luxury space socialism means forgetting the most basic aspects of security/computer troubleshooting
14 notes
·
View notes
Text
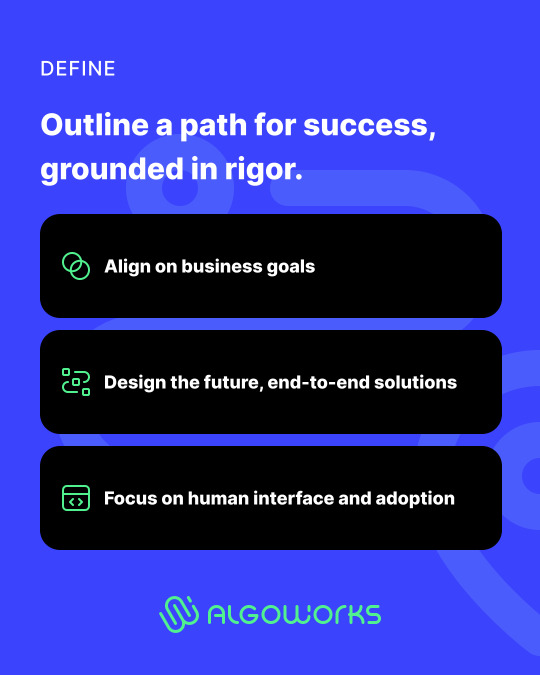


We follow our Define, Build, Run framework to execute flawlessly. From deep listening and 360° planning, to building with agile development and clean code, we ensure performance, security and return on investment through 24/7 monitoring and SLA-backed delivery.
Visit our website to learn more! https://www.algoworks.com/services/
#digital transformation#agile development#clean code#software engineering#cyber security#enterprise solutions#tech innovation#cloud services#innovations#technology#leadership#business excellence
2 notes
·
View notes
Text

1 note
·
View note
Text
How are AIops solutions remodeling the company's IT automation?
Enterprise IT environments are growing in complexity, with hybrid infrastructures, distributed systems and increasing volumes of data. Traditional monitoring tools and manual processes are usually short when it comes to managing performance, identifying anomalies and solving incidents efficiently. This is where AIops Solutions enters, offering a new way of approaching IT operations.
What are AIops solutions? AIops (Artificial Intelligence Operations) refers to the use of artificial intelligence and machine learning to manage and automate IT tasks. These solutions collect data from various IT environments and use machine learning algorithms to analyze, correlate and act with this data. By recognizing standards and providing for potential questions, AIops systems help IT teams respond faster and more accurately to incidents.
Remodeling Enterprise IT automation Automation of enterprise IT has long relied on scripts, predefined workflows and manual intervention. AIops changes this, allowing systems to learn from previous data and improve their performance over time. This continuous learning model supports automated root cause analysis, event correlation and even automated remediation, reducing the workload in the IT team.
In addition, AIops integrates well with existing IT service management tools and practices, making the transition to more manageable automated systems. From infrastructure management to application performance, AIops improves visibility between systems and supports better decision making.
AI for IT security Security is a growing concern for companies. AIops Solutions also provides significant value in this area. By monitoring unusual real-time patterns and behaviors, IT safety AI can detect potential threats before they increase. It helps identify suspicious activities, unauthorized access or policy violations without the need for manual log analysis.
This predictive capacity allows organizations to act before incidents become serious problems. Integration with safety operations centers also supports risk prevention and mitigation using AI-powered insights.
Role of Machine Learning Operations Machine Learning Operations (MLops) focuses on the implementation, monitoring and maintenance of machine learning models in production environments. AIops and MLops usually work hand in hand. MLops services ensure that AI models used in AIops systems are accurate, updated and properly integrated with IT operations.
This collaboration between AIops and MLops leads to smarter systems that continually evolve. It also helps IT teams to monitor the performance of AI models and ensure that they produce relevant information over time.
Workflow Automation with AI Another great advantage of AIops is the automation of the workflow with AI. Instead of relying on repetitive manual tasks, companies can automate ticket creation, alert prioritization, system diagnosis and resolution actions. This reduces inactivity time and increases operational efficiency.
AIops platforms can recommend actions or automatically trigger it, depending on the severity of the event and the predefined policies. This feature transforms how teams manage workloads, service requests and incidents.
Final thoughts With better analysis, automated workflows, and intelligent responses to incidents, companies are advancing to more responsive and efficient IT ecosystems. From support for safety measures to the possibility of smarter operations, AIOps is becoming an essential part of modern IT strategies.
Connect today with Celebal Technologies to integrate AIops solutions adapted to your enterprise needs. Our experts provide AI-oriented advanced IT services, including enterprise IT automation, MLops services and workflow automation with AI.
#AIOps solutions#enterprise IT automation#MLOps services#AI for IT security#machine learning operations#AI-powered workflow automation
0 notes
Text
User-Centric Enterprise Software Development and Integration: Enabling Scalable Digital Transformation
In today’s fast-evolving digital landscape, businesses require flexible and user-centric software solutions that go beyond conventional SaaS offerings. Aryabh Consulting Inc. delivers tailored enterprise and application software solutions designed to solve unique administrative and operational challenges across industries.
User-Centric Software Development for Enterprises
At the core of Aryabh Consulting’s approach is a commitment to custom software development that evolves with the business. Unlike off-the-shelf systems, custom applications provide full code ownership and the ability to integrate new features as business needs grow. The team prioritizes understanding each organization’s journey and pain points to engineer solutions that truly fit.

Comprehensive Software Services and Solutions
Aryabh Consulting Inc. offers full-cycle enterprise software consulting and application development services, including:
Business Analysis & Strategy: Thorough needs assessments, strategic roadmapping, and technology stack evaluations.
Custom Software Development: Tailored applications for CRM, ERP, HR, and more, with support for microservices and legacy modernization.
Application Integration & Data Management: Ensuring data consistency and real-time flow through seamless integrations and analytics.
Cloud Solutions: Cloud strategy, migration, and hybrid/multi-cloud architecture planning using AWS, Azure, and Google Cloud.
Security, Compliance, and Scalability
Robust cybersecurity services include risk assessments, compliance management (HIPAA, GDPR), and identity & access management solutions. Aryabh Consulting also provides scalable DevOps implementation with CI/CD pipelines, Infrastructure as Code (IaC), and robotic process automation (RPA).
Future-Ready Digital Innovation
The company supports digital transformation with strategic advisory, AI/ML integration, and IoT implementation to build smarter and more connected enterprise ecosystems. Managed Services and Change Enablement Beyond deployment, Aryabh Consulting Inc. provides performance optimization, 24/7 help desk support, and user training to ensure long-term software success and adoption.
#custom software development#enterprise software solutions#application integration services#digital transformation consulting#scalable business software#DevOps automation#cloud migration services#secure enterprise software#Aryabh Consulting
0 notes
Text
A Rock-Solid Data Platform: Why SQL Server 2016 Standard Remains a Top Choice
Unleashing the Power of SQL Server 2016: A Reliable Foundation for Modern Data Needs
In today’s rapidly evolving digital landscape, organizations require a robust and reliable data platform to support their critical operations and strategic initiatives. SQL Server 2016 Standard stands out as a versatile, powerful choice that continues to deliver exceptional performance, security, and flexibility. Its comprehensive features make it an ideal solution for businesses seeking stability and scalability in their data management infrastructure.
One of the key strengths of SQL Server 2016 Standard is its enhanced security capabilities. With features like Always Encrypted, it ensures sensitive data remains protected, even in the event of a breach. This encryption technology allows data to be encrypted at rest and in transit, providing peace of mind for organizations handling confidential information. Furthermore, dynamic data masking helps prevent unauthorized access by hiding sensitive data from users who do not need to see it, fostering a secure environment for data handling.
Beyond security, SQL Server 2016 excels in supporting business intelligence (BI) initiatives. Its integrated analytics tools enable companies to analyze vast amounts of data efficiently, transforming raw data into actionable insights. Power BI integration facilitates interactive visualizations, empowering decision-makers with real-time data dashboards. This seamless BI capability ensures organizations can stay ahead of market trends and respond swiftly to changing business conditions.
Performance enhancements in SQL Server 2016, such as in-memory OLTP and operational analytics, significantly boost transaction processing speeds and reduce latency. These features are particularly beneficial for applications requiring high throughput and low latency, such as financial systems or e-commerce platforms. The in-memory technology allows for real-time data processing, which is crucial for competitive advantage in today's fast-paced environment.
Scalability is another cornerstone of SQL Server 2016 Standard. Its ability to handle large volumes of data and concurrent users makes it suitable for organizations of all sizes. Whether managing small departmental databases or enterprise-wide data warehouses, SQL Server 2016 adapts to your needs, ensuring reliable performance without compromising security or functionality.
Moreover, SQL Server 2016 offers comprehensive tools for data management and automation. Its robust backup and recovery options, coupled with advanced monitoring features, enable administrators to maintain high availability and system integrity. These tools simplify database administration, reduce downtime, and enhance overall operational efficiency.
Choosing a database platform is a strategic decision that impacts every aspect of an organization. SQL Server 2016 Standard continues to be a top choice because it combines tried-and-true stability with innovative features that meet modern data demands. Its cost-effectiveness, combined with enterprise-grade capabilities, makes it an attractive solution for businesses aiming for growth and resilience.
In conclusion, SQL Server 2016 Standard offers a comprehensive, secure, and high-performing data platform that supports a wide range of business needs. Its combination of security features, BI integration, performance enhancements, and scalability makes it a reliable foundation for any organization’s data strategy. To learn more about how this platform can elevate your data management, visit A Rock-Solid Data Platform: Why SQL Server 2016 Standard Remains a Top Choice.
#SQL Server 2016#Data Platform#Database Security#Business Intelligence#Data Management#In-Memory OLTP#Enterprise Data Solutions
0 notes
Text

Power your infrastructure with Microsoft Windows Server 2022 Standard – built for performance, scalability, and top-tier security.
Whether you're managing virtual machines, handling network roles, or running enterprise-level applications, Windows Server 2022 is your reliable solution.
✅ Genuine Microsoft License ✅ Instant Digital Delivery ✅ Lifetime Activation ✅ Enterprise-Grade Security ✅ Best Price Online
👉 Get it now from TechLicence – your trusted Microsoft partner: www.techlicence.com
#Power your infrastructure with Microsoft Windows Server 2022 Standard – built for performance#scalability#and top-tier security.#Whether you're managing virtual machines#handling network roles#or running enterprise-level applications#Windows Server 2022 is your reliable solution.#✅ Genuine Microsoft License#✅ Instant Digital Delivery#✅ Lifetime Activation#✅ Enterprise-Grade Security#✅ Best Price Online#👉 Get it now from TechLicence – your trusted Microsoft partner: www.techlicence.com#windowssoftware#PCUpgrade#Microsoft#DigitalLicense#productkey#windowsserver2022#windowsserverstandard#standard2022#serverstandard2022#microsoftwindowsserver#serversolutions#security#serverkey
0 notes
Text
Business IT Solution for Digital Transformation Success
Modern leaders must act fast because change never slows. Moreover, IT solutions for business now shape every growth plan. As digital tools take over daily work, every business must adopt the right strategy to stay ahead. From cloud systems to data protection, smart moves make a big difference . Small steps bring big results when paired with a clear vision. Digital transformation is not just a tech shift—it is a cultural shift. Therefore, success depends on smart planning, strong support, and the right tools. This post shows clear steps, simple tools, and steady wins that let any firm thrive.
Why a Business IT Solution Drives Continuous Value
However, every market shifts daily, and data grows hourly. Therefore, a Business IT Solution guides teams, aligns systems, and cuts waste. Moreover, clear dashboards reveal gaps; thus, leaders adjust in time. Consequently, profits rise while risks fall.
Business IT Solution for Cloud Adoption
Furthermore, cloud shifts the cost from capital to usage. Hence, teams pay only for real demand. Because of this, apps scale during peaks and shrink during dips. Consequently, users enjoy smooth service without extra spending.
#business IT solutions#digital transformation#IT strategy#cloud adoption#secure data#system integration#agile methods#data-driven decisions#technology for business#IT for growth#business innovation#digital tools#IT support#enterprise technology#process automation.
0 notes
Text
Enterprise Information Archiving: A Strategic Imperative for Modern Data Management
In today’s data-driven business environment, Enterprise Information Archiving (EIA) has emerged as a critical component of effective data management strategies. As organizations generate and process vast amounts of digital information across diverse platforms—emails, documents, chat applications, and multimedia—managing this data efficiently becomes both a regulatory necessity and a business…
#archiving solutions#business#Business Intelligence#cloud archiving#Data archiving#data privacy#EIA#enterprise backup#enterprise content management#enterprise data archiving#Enterprise information archiving#enterprise information archiving software#information archiving#Information governance#Information Security#Information Technology#secure data storage#Security#technology
0 notes
Text
Bots Now Dominate the Web: Why This Growing Problem Demands Urgent Action

The digital world, once a bustling marketplace of human interaction, has undergone a silent, pervasive transformation. Data from 2024 and early 2025 reveals a startling reality: bots now dominate web traffic, accounting for over 50% of all internet activity. While some of these automated programs are "good" – diligently indexing content for search engines or enabling helpful chatbots – a significant and escalating proportion are "bad bots," mimicking human behavior for malicious purposes. This widespread bot dominance web traffic presents a serious and ever-growing problem for businesses, cybersecurity, and the overall integrity of the web. The sheer volume and sophistication of these malicious bots internet traffic are redefining the landscape of online security.
The rise of bot traffic on the internet is significantly fueled by rapid advancements in Artificial Intelligence (AI) and Large Language Models (LLMs). These technologies simplify the creation and scaling of sophisticated, evasive bots, allowing even less skilled malicious actors to launch high-volume attacks. As of early 2025, malicious bots account for a staggering 37% of all internet traffic, a substantial increase from previous years, signaling a deepening bot problem online.
The Unseen Majority: How Bots Came to Dominate the Web
For the first time in a decade, automated traffic has surpassed human activity. This shift is primarily attributed to the proliferation of AI and LLMs, which have democratized bot development, making it more accessible to a wider range of actors. These advancements enable bots to mimic human interaction with startling accuracy, often bypassing traditional security measures.
The sophistication of these bad bots internet traffic is constantly evolving. They employ techniques like IP rotation, mimicking legitimate browser fingerprints, and distributing attacks across vast networks of compromised devices (botnets). The goal is simple: evade detection by blending in with legitimate web traffic automation. This makes it increasingly difficult for organizations to differentiate between genuine human users and malicious automated scripts, amplifying the bot problem online.
The Multifaceted Problem: Impacts of Bot Dominance

The pervasive presence of malicious bots internet traffic creates a myriad of complex and costly issues across various aspects of the digital economy. Understanding the full scope of the impact of bots on business is crucial for developing effective defense strategies.
Financial Drain & Fraud
The direct financial implications of bot fraud are staggering. Malicious bots are instrumental in various fraudulent activities that directly hit a business's bottom line:
Credential Stuffing and Account Takeovers (ATOs): Bots automate login attempts using stolen username/password combinations from data breaches. Successful ATOs lead to financial theft, misuse of loyalty points, and damage to customer trust.
Carding and Gift Card Fraud: Bots test stolen credit card numbers against e-commerce sites or attempt to drain balances from stolen digital gift cards, leading to chargebacks and direct financial losses.
Ad Fraud and Click Fraud: Bots simulate clicks and impressions on online advertisements, depleting advertisers' budgets without generating genuine leads or conversions. This distorts analytics and wastes significant marketing spend.
Scalping and Inventory Hoarding: In industries with high-demand, limited-stock items (like concert tickets, sneakers, or popular gaming consoles), bots rapidly purchase inventory, only for it to be resold at inflated prices on secondary markets. This infuriates legitimate customers and damages brand reputation.
Cybersecurity Risks & Data Integrity
Cybersecurity bot attacks represent a fundamental threat to an organization's digital infrastructure and sensitive data. Bots are often the first line of attack in broader cyber campaigns:
Vulnerability Scanning and Exploitation: Bots automatically scan websites and APIs for known vulnerabilities (e.g., SQL injection, cross-site scripting), identifying weak points that can then be exploited for unauthorized access or data exfiltration.
Distributed Denial-of-Service (DDoS) Attacks: Botnets, vast networks of compromised devices controlled by attackers, flood target websites, servers, or networks with overwhelming volumes of traffic, rendering them inaccessible to legitimate users.
API Abuse: With the rise of API-driven applications, bots increasingly target APIs to scrape data, create fake accounts, exploit business logic, or launch sophisticated fraud schemes that bypass traditional web application firewalls.
Data Scraping: Competitors or malicious actors use bots to steal valuable data, including pricing information, product catalogs, customer reviews, and proprietary content, leading to competitive disadvantage and intellectual property theft.
Operational & Performance Disruptions
The sheer volume of web traffic automation from bots places immense strain on IT infrastructure:
Server Strain and Increased Costs: High bot traffic consumes valuable server resources, bandwidth, and computing power, leading to increased hosting expenses and the need for costly infrastructure upgrades.
Degraded Website Performance: Overwhelmed servers result in slower loading times, timeouts, and poor responsiveness for legitimate users, severely impacting user experience and conversion rates.
Skewed Analytics: Bot traffic contaminates website and application analytics, inflating metrics like page views, unique visitors, and clicks while distorting bounce rates and conversion rates. This leads to flawed business decisions based on inaccurate data.
Brand Reputation & Trust
Beyond the technical and financial impacts, bot dominance web traffic erodes trust and damages brand reputation:
Spam and Misinformation: Spam bots flood comment sections, forums, and social media platforms with unsolicited advertising, malicious links, or propaganda, harming a website's credibility and user experience.
Customer Frustration: When legitimate customers are unable to access services due to DDoS attacks, or when they can't purchase items due to bot-driven scalping, their frustration can quickly turn into negative reviews and a damaged brand image.
SEO Penalties: Google and other search engines penalize websites with low-quality or duplicate content, which can result from content scraping by bots, negatively impacting search engine rankings and organic traffic.
Industries Under Siege: Where Bot Threats are Most Acute

While the bot problem online affects nearly every sector, certain industries consistently face a higher proportion and more sophisticated online bot threats:
Financial Services: A primary target due to the sensitive nature of data and high-value transactions. They face relentless account takeover bots, credential stuffing, and fraud attempts.
Retail: Highly susceptible to bot fraud related to inventory scalping, gift card fraud, price scraping, and loyalty program abuse.
Travel: Experiences a significant percentage of bad bots internet traffic, used for competitive price scraping, account takeovers, and fraudulent bookings.
Gaming: Often sees the highest proportion of sophisticated bot traffic, including bots used for cheating, account compromise, and inventory manipulation within in-game economies.
Media and Entertainment: Targeted for content scraping, ad fraud, and credential stuffing on streaming platforms.
Fighting Back: Strategies for Bot Management and Mitigation

Combating bot dominance requires a proactive, multi-layered, and continuously evolving defense strategy. Relying on outdated methods is no longer sufficient against today's sophisticated malicious bots internet attacks.
Advanced Bot Management Solutions: The cornerstone of modern bot defense. These specialized platforms utilize a combination of behavioral analysis (distinguishing human-like patterns from automated ones), machine learning (adapting to new bot tactics), device fingerprinting, and real-time threat intelligence. They go beyond simple IP blocking or CAPTCHAs to detect and mitigate even the most evasive bots.
Robust API Security: Given that 44% of advanced bot traffic targeted APIs in 2024, securing these digital gateways is paramount. Implementing strong authentication mechanisms (like OAuth, API keys), strict access controls, and rate limiting on API endpoints can significantly reduce the attack surface for API security bots. Regular API penetration testing is also crucial.
Multi-Factor Authentication (MFA): Implementing MFA adds a critical layer of security beyond just passwords. Even if bots manage to acquire stolen credentials through credential stuffing, MFA can prevent unauthorized access by requiring a second verification step (e.g., a code from a mobile app), drastically reducing account takeover bots success rates.
Continuous Monitoring and Analytics: Businesses must actively monitor their web traffic automation for unusual patterns. This includes spikes in requests from a single IP, abnormally high failed login attempts, unusual user-agent strings, or suspicious conversion rates. Real-time dashboards and automated alerts are essential for early detection of online bot threats.
Regular Security Audits and Patching: Proactive vulnerability management is key. Regularly auditing web applications, APIs, and underlying infrastructure for security flaws, and promptly patching identified vulnerabilities, closes potential entry points for bots.
User-Agent and Proxy Analysis: Many simpler bots still rely on outdated browser user-agent strings or operate through known dubious proxy services. Implementing rules to block traffic from such indicators can filter out a significant portion of commodity bot attacks. Detecting traffic from residential proxies, which more advanced bots now use, requires more sophisticated analysis.
Rate Limiting and Throttling: While not a complete solution, judiciously applying rate limits on specific endpoints (e.g., login pages, search functions, API calls) can prevent brute-force attacks and resource exhaustion caused by excessive bot requests.
Conclusion: Securing the Human-Centric Web
The landscape of the internet has fundamentally shifted. Bots now dominate the web, and this poses a significant, evolving bot problem online for businesses, their customers, and the integrity of digital interactions. From sophisticated bot fraud schemes to debilitating cybersecurity bot attacks, the impact is wide-ranging and costly.
Ignoring this reality is no longer an option. As AI continues to empower bots to become even more evasive and intelligent, businesses must embrace comprehensive and adaptive bot management solutions. Investing in robust API security, implementing strong authentication, and continuously monitoring for unusual patterns are not merely best practices; they are essential for survival in the current digital climate.
The future of the web depends on our ability to effectively differentiate between humans and machines, safeguarding digital assets and ensuring a secure, reliable, and authentic online experience for everyone. By adopting proactive strategies, organizations can protect their revenue, reputation, and customer trust from the pervasive and growing threat of malicious web traffic automation. The time for urgent action is now.
#Cyber Security Services Company | Data Security Solutions#Top-rated Cyber Security Services Company Offering Advanced Protection#Threat Detection#Risk Assessment#Data Security Solutions For Businesses Worldwide.#Cybersecurity services company#Data security solutions#Managed cybersecurity services#Enterprise cyber protection#Data breach prevention services#Cyber threat protection#IT security solutions provider#Endpoint security services#Network security services#Cybersecurity consulting company
0 notes
Text
Top Benefits of Cloud Managed Services for Businesses - Anutatech

Discover the benefits of cloud managed services with Anutatech – your trusted partner for smarter IT solutions. Our cloud-managed services offer 24/7 monitoring, automated updates, and enhanced security, reducing downtime and freeing up your internal resources. With scalable infrastructure, predictable costs, and expert support, businesses can focus on growth while we handle the tech. Anutatech ensures seamless integration, disaster recovery, and performance optimization, helping your business stay agile in a competitive digital world. Embrace the future with Anutatech’s reliable, secure, and cost-efficient cloud solutions tailored to your unique needs. Let us manage the cloud, so you can manage success.
Visit Us: https://www.anuntatech.com/blog/cloud-managed-services-understanding-the-service/
#anuntatech#modern desktop management#enterprise digital workspace#secure virtual desktops#mobile device management solutions
0 notes
Text
High‑Speed and Secure Access Network Solutions – Esconet Technologies
Esconet Technologies offers comprehensive Access Network solutions tailored for enterprise environments. Their network infrastructure suite features high-speed copper and optical fiber connectivity (1 Gbps–100 Gbps), a multilayered design following core/distribution/access best practices, IPv6 readiness, Wi‑Fi 6/6E wireless, cloud-managed systems, advanced security (firewalls, IPS, VPNs), and deployable satellite broadband for remote locations. Partnered with top OEMs (Cisco, Arista, Juniper, Dell, HPE), Esconet ensures scalable, secure, future-ready digital transformation networks. For more details, Visit: Esconet's Access Network solution Page .
#access network solutions#enterprise networking#fiber optic connectivity#high-speed internet infrastructure#Wi-Fi 6 deployment#Wi-Fi 6E network#IPv6 network architecture#cloud-managed networking#enterprise wireless solutions#secure network infrastructure#network security solutions#VPN and firewall services#satellite broadband connectivity#digital transformation infrastructure#Esconet Technologies#copper and fiber network design#scalable network solutions#IT infrastructure services#enterprise IT solutions#smart campus networking
0 notes
Text
Choosing the Right Crypto Wallet for Your Business – Custodial vs. Non-Custodial
Choosing the right crypto wallet is crucial for safeguarding digital assets. In this guide by Theta Technolabs, we explore the key differences between custodial and non-custodial wallets, helping businesses make informed decisions. Learn how wallet types impact control, security, and compliance in today’s fast-moving blockchain landscape.
#crypto wallet for business#custodial crypto wallet#business crypto solutions#blockchain wallet types#crypto wallet development#enterprise blockchain security#digital asset management#decentralized wallets#crypto security for startups#blockchain consulting company
0 notes
Text
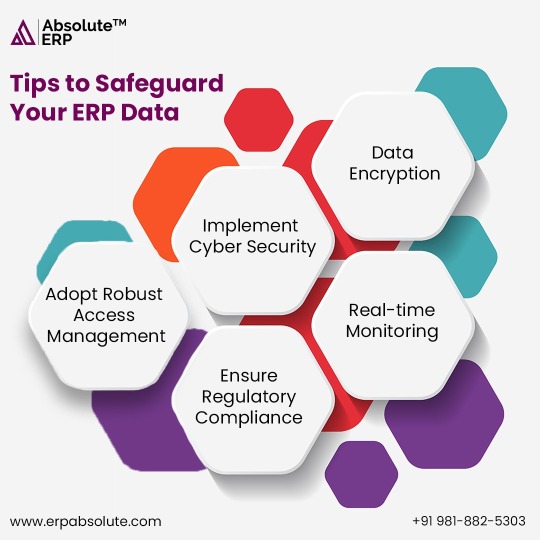
#ERP Data#ERP Safety#ERP Solutions#Enterprise Resource Planning Software#Data Management#Data Security
1 note
·
View note
Text
#The new generation router#based on ARM architecture multi-core processors and non blocking switching architecture#is applied in SD-WAN solution scenarios#integrating routing and switching security to meet the needs of enterprise customers for network equipment routing and switching security.#small and medium-sized enterprise headquarters or branches#and other scenarios.
0 notes
Text
High Quality Data Backup Cartridges | Server Storage UK

Shop premium data cartridges designed for efficient backup and long-term storage. Ideal for enterprise servers and tape libraries, our cartridges provide secure, cost-effective data protection. Browse our extensive UK stock, including LTO and other formats, with fast delivery, expert advice, and reliable customer support for your business needs.
#Data backup cartridges#Server storage solutions#Enterprise tape libraries#LTO data cartridges#Secure data protection
0 notes