#firewall security service
Explore tagged Tumblr posts
Text
How to Integrate Network Firewall Security into Your Overall IT Strategy

In today’s digital-first business environment, cybersecurity is no longer just an IT concern—it’s a business imperative. As cyber threats become more sophisticated and widespread, organizations must adopt a multi-layered defense strategy. At the heart of this defense lies network firewall security.
Firewalls are no longer simple barriers against unauthorized access. They are intelligent, adaptive, and critical components of a comprehensive IT security strategy. However many businesses still treat firewalls as stand-alone tools, failing to integrate them effectively into their broader IT frameworks.
In this article, we’ll walk you through how to integrate network firewall security into your overall IT strategy—so it works not as an isolated system, but as a powerful enabler of secure and resilient digital operations.
Understanding the Role of Network Firewall Security
A network firewall is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a gatekeeper, allowing legitimate traffic while blocking malicious or unauthorized access.
There are different types of firewalls:
Packet-filtering firewalls
Stateful inspection firewalls
Next-generation firewalls (NGFWs)
Web application firewalls (WAFs)
Cloud-native firewalls
In modern IT environments that include cloud infrastructure, remote workers, SaaS tools, and mobile devices, firewalls need to evolve and integrate seamlessly with your overall IT and cybersecurity strategy.
Why Integration Matters
Integrating firewall security with your IT strategy ensures you’re not just reacting to threats—you’re preventing them. Here’s why integration is essential:
Improved visibility and control over network activity
Faster incident response through centralized management
Reduced risk of security gaps or misconfigurations
Better compliance with data protection regulations
Stronger alignment with business objectives and IT goals
Step 1: Align Firewall Objectives with Business Goals
Before diving into technical details, start your firewall strategy with your overall business objectives.
Ask yourself:
What are your key digital assets?
Where does your business operate (on-prem, cloud, hybrid)?
What industry regulations or compliance standards must you meet?
How much risk are you willing to tolerate?
By understanding the bigger picture, you can tailor firewall policies and configurations that don’t just protect—but also support—your operations.
Step 2: Conduct a Network Security Assessment
To integrate your firewall effectively, you must first understand your current security posture.
Key activities include:
Mapping your network architecture (including remote access points, IoT devices, and cloud environments)
Identifying traffic patterns and sensitive data flows
Assessing existing firewalls, their placement, configurations, and performance
Finding gaps or misalignments between firewall controls and business processes
This step provides a baseline and highlights where improvements or integrations are necessary.
Step 3: Choose the Right Type of Firewall
Not all firewalls are created equal. To support your IT strategy, choose a solution that complements your infrastructure.
On-Premises Business
Opt for stateful inspection firewalls or NGFWs that provide deep packet inspection and intrusion prevention.
Cloud-Based or Hybrid Environment
Integrate cloud-native firewalls that are scalable, auto-configurable, and centrally managed (e.g., AWS Firewall Manager, Azure Firewall).
Web-Heavy Applications
Deploy Web Application Firewalls (WAFs) to protect against web-based attacks like SQL injections and XSS.
Remote Workforce
Use firewalls with VPN integration and Zero Trust Network Access (ZTNA) features.
Matching the right firewall to your IT setup ensures better coverage, performance, and cost-efficiency.
Step 4: Integrate with Centralized Monitoring and SIEM Tools
Standalone firewall logs are useful—but limited. When integrated with your Security Information and Event Management (SIEM) or centralized monitoring systems, firewalls become intelligent sources of threat insight.
Benefits of SIEM Integration:
Real-time alerts for suspicious network activity
Correlated analysis across devices and systems
Automated incident response and threat isolation
Unified dashboard for security and compliance reporting
By feeding firewall logs into your broader monitoring systems, you create a holistic security ecosystem.
Step 5: Define and Enforce Consistent Security Policies
Firewalls are only as effective as the rules they enforce. If you’re managing different firewalls across on-prem and cloud networks, consistency is critical.
Best Practices:
Create role-based access policies that restrict sensitive areas
Implement application-layer filtering to block unwanted software or services
Use geo-blocking or IP whitelisting for location-based controls
Set bandwidth limits for non-critical apps during business hours
Review and update rules regularly to match business changes
Make sure these policies are integrated into your wider IT governance framework and communicated clearly to all stakeholders.
Step 6: Automate Where Possible
Manual configurations are error-prone. Automating firewall rule management and threat response can boost efficiency and consistency.
Automation opportunities:
Auto-deployment of firewall configurations across branches or cloud regions
Real-time threat detection and blocking using AI or machine learning
Scheduled audits and compliance checks
Self-healing security systems that adapt to new vulnerabilities
Many modern firewall platforms offer APIs and integrations that support Infrastructure as Code (IaC), helping you embed firewall logic into your DevOps pipelines.
Step 7: Train Your Team and Foster Collaboration
Even the best firewall won’t protect you if your team doesn’t know how to use it. Integration is not just technical—it’s also about culture and communication.
Key focus areas:
Train IT and security teams on firewall management, policy enforcement, and monitoring tools
Include firewall strategies in IT planning sessions
Encourage collaboration between cybersecurity, cloud, networking, and application teams
Document all configurations and decisions to ensure transparency and knowledge transfer
Integrated firewall security requires cross-functional alignment to be truly effective.
Step 8: Monitor, Audit, and Optimize Continuously
Integration isn’t a one-time task. Your network evolves, new threats emerge, and your business shifts. A successful integration includes ongoing refinement.
Establish a routine for:
Firewall performance monitoring
Traffic analysis to detect bottlenecks or malicious patterns
Security audits to check for rule misconfigurations or outdated settings
Policy optimization based on current risk levels or industry benchmarks
Incident reporting and post-mortems for continuous improvement
Make this part of your larger IT and cybersecurity lifecycle management.
Conclusion
Firewalls are foundational to modern cybersecurity—but only when fully integrated into your IT strategy. When treated as isolated tools, they offer limited value. But when woven into the fabric of your infrastructure, processes, and people—they become powerful assets that drive resilience, agility, and trust.
As you build your IT roadmap, don’t think of firewall security as a checkbox. Think of it as a dynamic, evolving part of your digital ecosystem—one that protects your future as much as your present.
#firewall service#firewall security#network firewall security#Firewall Solutions#firewall protection#firewall security service#cloud based firewall#next generation firewalls#fortinet firewalls#palo alto firewall
0 notes
Text

Best Cyber Security Services- NewGig Secure Solutions
#firewall#security#network security services#network security solutions#network security market#antivirus
2 notes
·
View notes
Text
High‑Speed and Secure Access Network Solutions – Esconet Technologies
Esconet Technologies offers comprehensive Access Network solutions tailored for enterprise environments. Their network infrastructure suite features high-speed copper and optical fiber connectivity (1 Gbps–100 Gbps), a multilayered design following core/distribution/access best practices, IPv6 readiness, Wi‑Fi 6/6E wireless, cloud-managed systems, advanced security (firewalls, IPS, VPNs), and deployable satellite broadband for remote locations. Partnered with top OEMs (Cisco, Arista, Juniper, Dell, HPE), Esconet ensures scalable, secure, future-ready digital transformation networks. For more details, Visit: Esconet's Access Network solution Page .
#access network solutions#enterprise networking#fiber optic connectivity#high-speed internet infrastructure#Wi-Fi 6 deployment#Wi-Fi 6E network#IPv6 network architecture#cloud-managed networking#enterprise wireless solutions#secure network infrastructure#network security solutions#VPN and firewall services#satellite broadband connectivity#digital transformation infrastructure#Esconet Technologies#copper and fiber network design#scalable network solutions#IT infrastructure services#enterprise IT solutions#smart campus networking
0 notes
Text
Enhancing SASE with Network Sandboxing: A Modern Cybersecurity Approach
In the rapidly evolving world of cybersecurity, businesses must adopt robust strategies to defend against increasingly sophisticated threats. One of the most comprehensive and modern approaches is Secure Access Service Edge (SASE), which combines wide area networking (WAN) with cloud-delivered security services. To further strengthen this architecture, integrating network sandboxing can provide…
#automated threat detection#business cybersecurity#Cloud-Based Security#Cybersecurity#Fiber Internet#firewall as a service#IT security#malware prevention#network sandbox#real-time security#SASE#secure web gateway#SolveForce#Threat Detection#Zero Trust#zero-day threats
0 notes
Text
Choosing Radiant Info Solutions for SonicWall TZ Firewall Renewal Services
Learn why Radiant Info Solutions is your best choice for SonicWall TZ firewall renewal services. Contact us today for expert support and seamless renewal services.

#SonicWall TZ#firewall renewal services#SonicWall partner#network security solutions#IT services#Radiant Info Solutions
0 notes
Text
10 web application firewall benefits to keep top of mind - CyberTalk
New Post has been published on https://thedigitalinsider.com/10-web-application-firewall-benefits-to-keep-top-of-mind-cybertalk/
10 web application firewall benefits to keep top of mind - CyberTalk


EXECUTIVE SUMMARY:
These days, web-based applications handle everything from customer data to financial transactions. As a result, for cyber criminals, they represent attractive targets.
This is where Web Application Firewalls (or WAFs) come into play. A WAF functions as a private security guard for a web-based application or site; always on-guard, in search of suspicious activity, and capable of blocking potential attacks. But the scope of WAF protection tends to span beyond what most leaders are aware of.
In this article, discover 10 benefits of WAFs that cyber security decision-makers should keep top-of-mind, as to align WAF functions with the overarching cyber security strategy.
1. Protection against OWASP Top 10 threats. A WAF can stop application layer attacks, including the OWASP Top 10 (with minimal tuning and no false positives). WAFs continuously update rule sets to align with the latest OWASP guidelines, reducing the probability of successful attacks.
2. API protection. WAFs offer specialized protection against API-specific threats, ensuring the integrity of data exchanges. WAFs can block threats like parameter tampering and can find abnormal behavioral patterns that could be indicative of API abuse.
Advanced WAFs can understand and validate complex API calls, ensuring that only legitimate requests are processed. They can also enforce rate limiting and access controls specific to different API endpoints.
3. Bot & DDoS protection. WAFs can distinguish between malicious and legitimate bot traffic, preventing DDoS threats, credential stuffing, content scraping and more. This area of WAF capability is taking on increasing importance, as bots are blazing across the web like never before, negatively impacting the bottom line and customer experiences.
4. Real-time intelligence. Modern WAFs leverage machine learning to analyze traffic patterns and to provide up-to-the-minute protection against emerging threats, enabling businesses to mitigate malicious instances before exploitation-at-scale can occur.
5. Compliance adherence. WAFs enable organizations to meet regulatory requirements, as they implement much-needed security controls and can provide detailed audit logs.
The granular logging and reporting capabilities available via WAF allow organizations to demonstrate due diligence in protecting sensitive data.
Many WAFs come with pre-configured rule sets designed to address specific compliance requirements, rendering it easier to maintain a compliant posture as regulations continue to evolve.
6. Reduced burden on development teams. Stopping vulnerabilities at the application layer enables development or IT team to focus on core functionalities, rather than the constant patching of security issues.
This “shift-left” approach to security can significantly accelerate development cycles and improve overall application quality. Additionally, the insights offered by WAFs can help developers understand common attack patterns, informing better security practices as everyone moves forward.
7. Customizable rule sets. Advanced WAFs offer the flexibility to create and fine-tune rules that are specific to an organization’s needs. This customization allows for the adaptation to unique application architecture and traffic patterns, minimizing false positives, while maintaining robust protection.
Organizations can create rules to address specific threats to their business, such as protecting against business logic attacks unique to their application.
And the ability to gradually implement and test new rules in monitoring mode before enforcing them ensures that security measures will not inadvertently disrupt legitimate business operations.
8. Performance optimization. Many WAFs include content delivery network (CDN) capabilities, improving application performance and UX while maintaining security.
Caching content and distributing it globally can significantly reduce latency and improve load times for users worldwide. This dual functionality of security and performance optimization offers a compelling value proposition. Organizations can upgrade both their security posture and user satisfaction via a single cyber security solution.
9. Operational insights. WAFs present actionable operational insights pertaining to traffic patterns, attack trends and application behavior. These insights can drive continuous security posture improvement, inform risk assessments and help cyber security staff better allocate security resources.
10. Cloud-native security. As organizations migrate to the cloud, WAFs intended for cloud environments ensure consistent protection across both hybrid and multi-cloud infrastructure. Cloud-native WAFs can scale automatically with applications, offering uncompromising protection amidst traffic spikes or rapid cloud expansions.
Cloud-native WAFs also offer centralized management. This simplifies administration and ensures consistent policy enforcement. By virtue of the features available, these WAFs can provide enhanced protection against evolving threats.
Further thoughts
WAFs afford organizations comprehensive protection. When viewed not only as a security solution, but also as a business enablement tool, it becomes clear that WAFs are an integral component of an advanced cyber security strategy. To explore WAF products, click here.
For more cloud security insights, click here. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#10 web application firewall benefits to keep top of mind#Administration#amp#analyses#API#application layer#applications#approach#architecture#Article#Articles#audit#Behavior#bot#bot traffic#bots#Business#cdn#Cloud#cloud infrastructure#Cloud Security#cloud services#Cloud-Native#compliance#comprehensive#content#continuous#credential#credential stuffing#customer data
0 notes
Text

On this holy occasion of Bakrid, may your sacrifices be rewarded with eternal peace and blessings.
#eeka#eekaconsultancyservices#consultancyservices#consultancy#services#EidAlAdha2024.#EidMubarak.#FestivalOfSacrifice.#Qurbani.#EidUlAdha.#BakraEid.#MuslimFestival.#IslamicHoliday.#bangalore#networking#security#firewall#happy#jobs#ecs
0 notes
Text
Firewall Security
🔐💼 Strengthen Your Human Firewall with Employee Security Awareness Training from Century Solutions Group! 💻🛡️
In today's cyber landscape, your employees are your first line of defense against digital threats. That's why we offer comprehensive security awareness training and testing to empower your team with the knowledge and skills needed to recognize and thwart cyber-attacks. Why is employee security awareness crucial? Well, imagine your workforce as the gatekeepers of your digital kingdom 🏰🔒. With proper training, they become your human firewall, protecting your organization from phishing scams, malware, and social engineering tactics. Don't leave your organization vulnerable to cyber threats – trust Century Solutions Group to arm your employees with the tools they need to defend against evolving dangers. Your security is our priority! 💼💻🚀 #EmployeeSecurityAwareness #CyberDefense #CenturySolutionsGroup 🔐💡

#Firewall Security#Employee Security Training#cybersecurity#cyberattack#it services#cloud technology services#phishing#data backup
1 note
·
View note
Text
Safeguarding Your Online Presence: The Necessity of Firewall as a Service
In today's digital landscape, businesses and websites face an ever-increasing array of cyber threats. From malicious hackers to sophisticated malware, the risks of falling victim to a cyber attack are higher than ever before. This is where firewall as a service (FWaaS) emerges as a critical solution, offering robust protection and peace of mind for organizations of all sizes.
The Evolving Threat Landscape Traditional on-premises firewalls, while effective, often struggle to keep pace with the rapid evolution of cyber threats. FWaaS, on the other hand, is a cloud-based solution that leverages the latest in security technologies and real-time threat intelligence. By outsourcing firewall management to a specialized provider, businesses can benefit from continuous updates, ensuring their defenses are always up-to-date and fortified against the latest threats.
Cost-Effective Scalability Implementing and maintaining a traditional firewall solution can be a costly endeavor, particularly for small and medium-sized businesses. FWaaS eliminates the need for expensive hardware and dedicated IT resources, allowing organizations to scale their firewall protection as their business grows seamlessly. Additionally, the subscription-based pricing model of FWaaS ensures predictable and manageable costs, making it an attractive option for businesses of all sizes.
Comprehensive Multi-Location Protection In today's distributed business environment, organizations often operate across multiple locations, each with its own unique set of security requirements. FWaaS provides consistent and centralized protection across all locations, ensuring that every branch office, remote employee, and cloud resource enjoys the same level of robust security. This streamlined approach simplifies security management and reduces the risk of vulnerabilities arising from inconsistent or outdated policies.
Simplified Management and Reduced Overhead Managing and maintaining an on-premises firewall solution can be a complex and time-consuming task, requiring dedicated IT resources and expertise. By leveraging FWaaS, businesses can offload the burden of firewall management to their service provider, freeing up valuable time and resources for core business activities. This simplified approach also reduces the risk of human error and ensures consistent application of security policies across the entire organization.
In the ever-evolving landscape of cyber threats, firewall as a service has emerged as a vital and indispensable solution for businesses and websites of all sizes. By providing robust security, scalability, comprehensive protection, and simplified management, FWaaS empowers organizations to focus on their core operations while entrusting their online presence to the experts. Embrace this powerful solution and safeguard your digital assets with confidence.
1 note
·
View note
Text
Understanding the Firewall: Your First Line of Defense in Cybersecurity
Introduction -
It is critical to protect your network from cyber dangers in the connected digital world of today. Strong cybersecurity measures are becoming essential due to the constant risk of malware infections, data breaches, and unwanted access attempts. The firewall, a vital element that creates a barrier between your reliable network and the unpredictably vast internet, is at the vanguard of this protection.
Let me tell you What exactly a Firewall is :
Consider your network as a stronghold, with the firewall acting as the gatekeeper regulating access and departure. A firewall is essentially a software or hardware security system that keeps an eye on and regulates all incoming and outgoing network traffic by pre-established security standards. These rules serve as the first line of protection against potential threats by dictating which data packets are allowed to flow through and which are blocked.
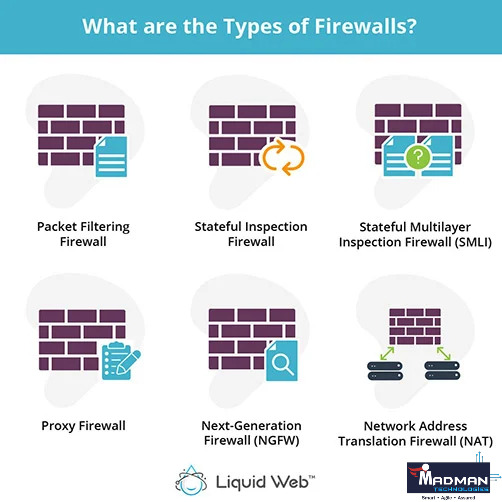
Types of Firewalls -
Firewalls come in various forms, each with its own set of functionalities tailored to meet specific security needs:
Packet-Filtering Firewalls: These inspect individual packets of data as they traverse the network, making decisions based on predetermined criteria such as IP addresses, ports, and protocols.
Stateful Inspection Firewalls: Building upon packet filtering, stateful inspection firewalls maintain a record of active connections and use this contextual information to make more informed decisions about allowing or blocking traffic.
Proxy Firewalls: Proxy firewalls operate as middlemen between internal and external network traffic, thoroughly inspecting data packets and enhancing security by masking internal IP addresses and adding more recording and analytic features.
Next-Generation Firewalls (NGFW): NGFWs offer complete security by fusing classic firewall functions with cutting-edge technologies. These characteristics include intrusion detection, application awareness, and enhanced threat protection.
The Role of Firewall in Cybersecurity -
A firewall's main function is to safeguard your network against the harmful activity, illegal access, and online threats. Firewalls assist in preventing intrusions, blocking malware infections, and reducing the dangers connected with a range of cyberattacks by enforcing security policies and filtering traffic by preset rules. These assaults include:
Denial-of-Service (DoS) Attacks: Firewalls can detect and block suspicious traffic patterns associated with DoS attacks, preventing them from overwhelming your network resources.
Malware infections: Firewalls can prevent efforts by viruses, worms, or other malware to infiltrate your network by screening incoming traffic for known malware signatures and dangerous behaviours.
Unauthorized Access Attempts: Firewalls can prevent efforts by viruses, worms, or other malware to infiltrate your network by screening incoming traffic for known malware signatures and dangerous behaviours.
Data Leakage: Firewalls help protect against data breaches and information leaks by granting granular control over outgoing traffic. This prevents sensitive data from leaving your network without the required authorization.
Best Practices for Firewall Implementation -
Firewalls are an essential part of cybersecurity, but how well they work depends on how well they are configured, maintained, and adhered to :
Define Clear Security Policies: Establish comprehensive security policies that outline the acceptable use of your network and the rules governing traffic flow.
Regularly Update Rulesets: Stay vigilant by updating firewall rulesets to address emerging threats and vulnerabilities, ensuring that your network remains protected against the latest cyber risks.
Monitor and Analyze Traffic: Implement logging and monitoring mechanisms to track network activity, detect anomalies, and identify potential security incidents in real time.
Combine with Additional Security Measures: Enhance your network security posture by complementing firewalls with intrusion detection systems (IDS), antivirus software, and other security measures.
Regular Audits and Assessments: Conduct periodic audits and security assessments to evaluate the effectiveness of your firewall configuration and identify areas for improvement.
Conclusion -
The firewall is the mainstay of network security in a time of ubiquitous cyber threats and digital connection. Firewalls are essential for protecting sensitive data, important assets, and the cybersecurity posture of your company because they efficiently manage traffic flow and enforce security standards. Accept the strength of firewalls as your first line of defence against the always-changing cyber threat landscape and provide your network the defence it needs.
One of the best sellers and service providers of firewalls is MADMAN TECHNOLOGIES, where A product must meet the following criteria to be eligible for the Firewall category:
Evaluate and filter user access;
Build barriers between networks and the internet; and
Notify administrators when unauthorized access is attempted.
Establish and uphold security and identification regulations.
Automate testing and monitoring-related duties
For any queries, you can google our website -
Contact details — 9625468776
#information technology#it products#it services#technology#itservices#it technology#application of firewall#it solutions#firewall#networking#secuity#network security
0 notes
Text
How Firewall Services Protect Your Network from Cyber Threats

Introduction
In today’s digital landscape, cyber threats are more sophisticated and prevalent than ever. Businesses, regardless of their size, are prime targets for cybercriminals aiming to steal data, disrupt operations, or demand ransom. One of the most critical components of any cybersecurity strategy is a robust firewall service. Firewalls serve as the first defense against cyberattacks, filtering out malicious traffic while allowing legitimate data to pass through. This article explores how firewall services protect your network from cyber threats, ensuring business continuity and data security.
What is a Firewall?
A firewall is a security system that monitors and controls incoming and outgoing network traffic based on predefined security rules. It is a barrier between a trusted internal network and untrusted external networks, such as the Internet. Firewalls come in different types, including hardware-based, software-based, and cloud-based solutions, each providing unique security benefits.
Key Functions of Firewall Services
Firewall services offer multiple layers of protection to safeguard businesses from cyber threats. Here are some of their key functions:
1. Traffic Monitoring and Filtering
Firewalls inspect every packet of data that enters or leaves your network. They analyze data for potential threats and block unauthorized access while allowing legitimate traffic. This ensures that only safe and relevant communication is permitted.
2. Preventing Unauthorized Access
By implementing strict access control policies, firewalls prevent unauthorized users from accessing sensitive company data. They help enforce role-based access, ensuring that employees and third parties can only access information necessary for their responsibilities.
3. Protection Against Malware and Viruses
Many advanced firewalls include Intrusion Prevention Systems (IPS) that detect and block malicious software, such as viruses, worms, and trojans, before they can infiltrate your network. Firewalls can also integrate with antivirus programs to provide an additional layer of protection.
4. Blocking Malicious Websites
Firewalls can restrict access to dangerous or inappropriate websites known to host malware, phishing attacks, or other cyber threats. This helps prevent employees from visiting harmful websites that could compromise the organization’s security.
5. Preventing Distributed Denial-of-Service (DDoS) Attacks
A DDoS attack aims to overwhelm a network or server with excessive traffic, rendering it inoperable. Firewalls detect and mitigate DDoS attacks by filtering out suspicious traffic patterns and blocking sources of attack before they cause harm.
6. Enhancing Network Performance
By filtering out unnecessary and malicious traffic, firewalls optimize bandwidth usage and improve overall network performance. They help prioritize business-critical applications while preventing congestion caused by unauthorized data consumption.
7. Logging and Reporting for Compliance
Firewall services provide detailed logs and reports that help organizations monitor network activity, detect potential threats, and ensure compliance with cybersecurity regulations such as GDPR, HIPAA, and PCI DSS.
Types of Firewalls
Different types of firewalls provide varying levels of protection. Choosing the right firewall service depends on the specific needs of your business. The most common types include:
1. Packet-Filtering Firewalls
These firewalls analyze data packets based on predefined security rules, allowing or blocking them based on source and destination IP addresses, ports, and protocols. While simple and efficient, they lack deep inspection capabilities.
2. Stateful Inspection Firewalls
Unlike packet-filtering firewalls, stateful inspection firewalls track the state of active connections. They analyze the entire context of traffic to make more informed security decisions, providing stronger protection against unauthorized access.
3. Proxy Firewalls
Proxy firewalls act as intermediaries between users and the internet. Instead of direct communication, data passes through the proxy firewall, which inspects and filters requests, ensuring that malicious content never reaches the network.
4. Next-Generation Firewalls (NGFWs)
NGFWs combine traditional firewall functions with advanced security features such as deep packet inspection, intrusion prevention, and application control. They offer superior protection against modern cyber threats.
5. Cloud-Based Firewalls (Firewall-as-a-Service)
Cloud firewalls provide security without the need for on-premises hardware. These services offer scalability, automatic updates, and global threat intelligence, making them ideal for businesses with remote workforces and cloud-based applications.
Benefits of Firewall Services
Investing in firewall services provides businesses with multiple security and operational benefits, including:
1. Comprehensive Cyber Threat Protection
Firewalls serve as a robust defense mechanism against cyber threats, preventing unauthorized access, malware infections, and data breaches.
2. Regulatory Compliance
Many industries have strict cybersecurity regulations. Firewalls help businesses meet compliance requirements by enforcing security policies and providing audit logs.
3. Enhanced Productivity
By blocking access to non-business-related websites and applications, firewalls prevent distractions and enhance employee productivity.
4. Cost Savings
A data breach can be extremely costly due to financial losses, legal fines, and reputational damage. Investing in firewall services helps prevent these incidents and reduces long-term security costs.
5. Scalability and Flexibility
Modern firewall services offer scalable solutions that grow with your business. Whether you operate a small startup or a large enterprise, firewalls can be customized to meet your security needs.
Firewall Services vs. Cyber Threats: A Cost Analysis
Cybersecurity breaches can be financially devastating. Here’s a comparison of the cost of a cyberattack versus the investment in firewall services:
Scenario 1: Cost of a Cyberattack
Legal fines and penalties: $500,000
Data recovery and forensic investigation: $250,000
Downtime and lost business: $1 million
Reputation damage and customer loss: $750,000
Total estimated cost: $2.5 million
Scenario 2: Cost of Firewall Services Investment
Firewall installation and setup: $50,000
Annual firewall maintenance and monitoring: $30,000
Employee security training: $20,000
Total estimated cost: $100,000
The contrast is clear—investing in firewall services is significantly more cost-effective than dealing with the aftermath of a cyberattack.
Conclusion
Cyber threats continue to evolve, making network security more critical than ever. Firewall services act as the first and most essential layer of defense, protecting businesses from unauthorized access, malware, data breaches, and DDoS attacks. By investing in firewall services, organizations not only secure their sensitive data but also enhance productivity, ensure compliance, and save on long-term security costs.
The choice is clear: proactive protection with a reliable firewall service is the best defense against the ever-growing landscape of cyber threats.
#firewall service#firewall security#network firewall security#Firewall Solutions#firewall protection#firewall security service#cloud based firewall#next generation firewalls#fortinet firewalls#palo alto firewall
0 notes
Text
Endpoint Security: Safeguarding the Digital Perimeter in an Evolving Landscape

In the dynamic landscape of cybersecurity, where threats are ever-evolving and the attack surface is expanding, ensuring the security of endpoints has become a mission-critical aspect for organizations. Endpoint security, a comprehensive approach to protecting devices connected to a network, has become increasingly vital as the number of remote workers and connected devices continues to rise. This blog post delves into the key components of endpoint security, its importance in the current digital ecosystem, and the evolving strategies to address emerging threats.
Understanding Endpoint Security:
Endpoint security encompasses a suite of measures designed to secure individual devices – or endpoints – that connect to an organization's network. These endpoints can range from traditional desktops and laptops to smartphones, tablets, servers, and other internet-enabled devices. The goal is to create a robust defense that safeguards these endpoints against a multitude of cyber threats.
Key Components of Endpoint Security:
1. Antivirus and Anti-malware Solutions:
Fundamental to endpoint security, antivirus and anti-malware solutions provide real-time protection against malicious software. These tools detect and eliminate viruses, Trojans, and other malware, preventing them from compromising the integrity of endpoints and spreading throughout the network.
2. Firewall Protection:
Firewalls act as a barrier between an endpoint and the external network, monitoring and controlling incoming and outgoing traffic. By blocking unauthorized access and potential threats, firewalls play a crucial role in securing endpoints and preventing malicious activities.
3. Email Security:
Given the prevalence of phishing attacks and email-based threats, endpoint security often includes robust email security features. These capabilities help detect and block phishing attempts, malicious attachments, and other email-borne threats, reducing the risk of compromise through social engineering.
4. Device Control:
Endpoint security solutions often incorporate device control features, allowing organizations to manage and control the use of peripheral devices connected to endpoints. This helps mitigate the risk of data leakage and unauthorized access through USB drives and other external devices.
5. Behavioral Analysis:
Modern endpoint security solutions leverage advanced behavioral analysis to detect anomalies in endpoint behavior. By establishing a baseline of normal activities, these tools can identify deviations that may indicate a security threat, enabling proactive responses to potential risks.
The Importance of Endpoint Security:
1. Data Protection:
Endpoints serve as gateways to an organization's sensitive data. Strengthening endpoint security is crucial for preventing unauthorized access, data breaches, and the compromise of critical information. Robust endpoint security ensures the confidentiality and integrity of data.
2. Threat Mitigation:
Endpoints are frequent targets for a variety of cyber threats, including ransomware, malware, and advanced persistent threats. Endpoint security acts as the first line of defense, detecting and neutralizing these threats before they can infiltrate the network and cause harm.
3. Adaptation to Remote Work:
The rise of remote work has expanded the attack surface, making endpoint security even more critical. With employees accessing corporate networks from various locations and devices, organizations must implement robust endpoint security measures to protect against potential vulnerabilities and cyber threats.
4. Regulatory Compliance:
Endpoint security is vital for maintaining compliance with industry regulations and data protection laws. Failure to secure endpoints adequately can result in legal consequences, financial penalties, and reputational damage for organizations.
The Future of Endpoint Security:
As cyber threats continue to evolve, so must endpoint security strategies. The integration of artificial intelligence and machine learning into endpoint security platforms enhances their ability to detect and respond to emerging threats in real-time. Additionally, the adoption of zero-trust security models assumes that no device or user should be automatically trusted, providing a more proactive and adaptive approach to endpoint security.
In conclusion, as the digital landscape evolves, organizations must recognize the critical role of endpoint security in safeguarding their networks and data. Investing in robust endpoint security solutions not only protects against current threats but also ensures a proactive defense against emerging cyber risks. In this era of constant connectivity, endpoint security stands as the frontline defense, securing the gateways to the digital realm and fortifying organizations against the ever-evolving cybersecurity challenges.
0 notes
Text
#WordPress Security#WordPress development services#Web Application Firewalls#Content Security Policies#hosting services
0 notes
Text
1)Who is Ionix?
We are a full-service MSP (Managed Service Provider) based in Elk City, OK.
2)What does an MSP do?
If your school or business uses technology, we can help streamline your operations and protect you from security threats and equipment failure. We can do all of this for a fixed rate, so you don't have to worry about your system stability or your budget.
3)What can Ionix provide?
This is a hard question to answer because every business is different, and we customize our solutions to fit your needs. Small list of what we can provide:
Network Solutions: Firewall, Switches, Cabling and Wireless Access Points
Hardware for each user: Computer, Monitor, battery backup
Security Awareness Training
PCI Compliance/Consulting
Security Cameras
Data backup solutions
#WIRING#technology#Switch#smartboard#security cameras#network#MONITOR#Managed Services#laptop#firewall#desktop#cloud#cabling#backup
1 note
·
View note
Text
#artificial intelligence#marketing#whatsapp#search engine optimization#social media#tumblr tv#web application development#web application security#web application firewall#web application services#web application testing#next generation
0 notes
Text
How to Optimize Your SonicWall Firewall with Radiant Info Solutions
Maximize your network security with expert optimization services from Radiant Info Solutions. Ensure your SonicWall Firewall performs at its best.
#SonicWall Firewall optimization#network security#firewall services#Radiant Info Solutions#SonicWall partner
0 notes