#how to use OWASP
Explore tagged Tumblr posts
Text
LDAP testing & defense
LDAP Injection is an attack used to exploit web based applications that construct LDAP statements based on user input. When an application fails to properly sanitize user input, it's possible to modify LDAP statements through techniques similar to SQL Injection.
LDAP injection attacks are common due to two factors:
The lack of safer, parameterized LDAP query interfaces
The widespread use of LDAP to authenticate users to systems.
How to test for the issue
During code review
Please check for any queries to the LDAP escape special characters, see here.
Automated Exploitation
Scanner module of tool like OWASP ZAP have module to detect LDAP injection issue.
Remediation
Escape all variables using the right LDAP encoding function
The main way LDAP stores names is based on DN (distinguished name). You can think of this like a unique identifier. These are sometimes used to access resources, like a username.
A DN might look like this
cn=Richard Feynman, ou=Physics Department, dc=Caltech, dc=edu
or
uid=inewton, ou=Mathematics Department, dc=Cambridge, dc=com
There are certain characters that are considered special characters in a DN. The exhaustive list is the following: \ # + < > , ; " = and leading or trailing spaces
Each DN points to exactly 1 entry, which can be thought of sort of like a row in a RDBMS. For each entry, there will be 1 or more attributes which are analogous to RDBMS columns. If you are interested in searching through LDAP for users will certain attributes, you may do so with search filters. In a search filter, you can use standard boolean logic to get a list of users matching an arbitrary constraint. Search filters are written in Polish notation AKA prefix notation.
Example:
(&(ou=Physics)(| (manager=cn=Freeman Dyson,ou=Physics,dc=Caltech,dc=edu) (manager=cn=Albert Einstein,ou=Physics,dc=Princeton,dc=edu) ))
When building LDAP queries in application code, you MUST escape any untrusted data that is added to any LDAP query. There are two forms of LDAP escaping. Encoding for LDAP Search and Encoding for LDAP DN (distinguished name). The proper escaping depends on whether you are sanitising input for a search filter, or you are using a DN as a username-like credential for accessing some resource.
Safe Java for LDAP escaping Example:
public String escapeDN (String name) {
//From RFC 2253 and the / character for JNDI
final char[] META_CHARS = {'+', '"', '<', '>', ';', '/'};
String escapedStr = new String(name);
//Backslash is both a Java and an LDAP escape character,
//so escape it first escapedStr = escapedStr.replaceAll("\\\\\\\\","\\\\\\\\");
//Positional characters - see RFC 2253
escapedStr = escapedStr.replaceAll("\^#","\\\\\\\\#");
escapedStr = escapedStr.replaceAll("\^ | $","\\\\\\\\ ");
for (int i=0 ; i < META_CHARS.length ; i++) {
escapedStr = escapedStr.replaceAll("\\\\" + META_CHARS[i],"\\\\\\\\" + META_CHARS[i]);
}
return escapedStr;
}
3 notes
·
View notes
Text
How to Build a Safe and Secure Digital Wallet

In today’s digital era, convenience and efficiency are driving the shift towards cashless transactions, and digital wallets have become an essential part of our daily lives. As these digital wallets store sensitive financial information, it is crucial to prioritize security and safety during their development. In this blog, we will explore the key elements necessary to build a safe and secure digital wallet, ensuring users’ confidence and trust in your platform.
Strong Authentication Mechanisms: A robust authentication system is the foundation of a secure digital wallet. Implement multi-factor authentication (MFA) to require users to provide multiple forms of identification before accessing their accounts. MFA may include a combination of passwords, biometric data (fingerprint, facial recognition), and one-time passwords (OTP) sent to registered mobile numbers or email addresses. This layered approach significantly reduces the chances of unauthorized access.
Encryption and Data Protection: Protecting sensitive user data is paramount in a digital wallet’s security. Utilize strong encryption algorithms to secure data both at rest and during transmission. Adopt industry-standard encryption protocols like SSL/TLS to safeguard communication between the app and backend servers. Additionally, never store plain-text passwords or sensitive information in the database; instead, use strong hashing techniques.
Regular Security Audits and Penetration Testing: Frequent security audits and penetration testing are essential to identify vulnerabilities and weaknesses in your digital wallet’s infrastructure. Engage with qualified security professionals to conduct thorough assessments and address any discovered issues promptly. Regular testing ensures your platform remains resilient against emerging threats and hacker attempts.
Secure Development Practices: Adopt secure development practices from the outset to build a strong security foundation. Train your development team on secure coding practices, ensuring they follow the latest OWASP guidelines. Implement code reviews and conduct regular security awareness training to ensure everyone involved understands the importance of security in the development lifecycle.
End-to-End Encryption for Transactions: Ensure that all transactions, whether online or in-store, are encrypted end-to-end. This encryption prevents unauthorized parties from intercepting and manipulating sensitive transaction data, such as credit card details or personal identification numbers.
Regular Software Updates: Stay vigilant in updating your digital wallet application and backend servers with the latest security patches and software updates. Outdated software can expose your platform to known vulnerabilities, making it an easy target for cyberattacks. Enabling automatic updates can streamline this process and keep your app’s security up to date.
Secure Storage of Payment Information: When storing payment information, follow Payment Card Industry Data Security Standard (PCI DSS) compliance guidelines. If possible, avoid storing cardholder data and instead utilize tokenization or outsourcing payment processing to certified third-party providers. This approach minimizes the risks associated with storing sensitive financial information.
User Education and Awareness: Promote user education and awareness about digital wallet security best practices. Educate users about the risks associated with phishing attacks, using unsecured Wi-Fi networks, and sharing sensitive information with unknown sources. Regularly communicate security updates and tips to ensure users can safeguard their accounts effectively.
Building a safe and secure digital wallet is a critical responsibility for any fintech company. By adopting strong authentication mechanisms, encryption, and secure development practices, you can create a robust platform that users can trust. Regular audits, updates, and user education play pivotal roles in keeping the digital wallet ahead of emerging threats.
Remember, security is an ongoing process, and a proactive approach is essential to maintaining a trusted and reliable digital wallet in an ever-evolving digital landscape.
1 note
·
View note
Text
Unvalidated Redirects in Symfony: Fix & Prevention Guide
Unvalidated Redirects and Forwards (also known as Open Redirects) remain one of the more stealthy yet dangerous web application vulnerabilities. When left unaddressed, they can allow attackers to redirect users to malicious websites or even hijack OAuth tokens in modern Symfony applications.

In this blog post, we’ll break down what Unvalidated Redirects are, how they occur in Symfony apps, how to detect them using free scanning tools, and how to prevent them using secure coding practices.
This article is part of the cybersecurity knowledge hub at Pentest Testing Corp. Read more from our blog: https://www.pentesttesting.com/blog/
🔍 What Are Unvalidated Redirects and Forwards?
Unvalidated Redirects occur when a web application accepts untrusted input that causes the web application to redirect the request to a URL contained within untrusted input. This flaw is often used in phishing attacks and credential theft.
A typical scenario in Symfony might look like this:
Example vulnerable route:
// src/Controller/RedirectController.php use Symfony\Component\HttpFoundation\RedirectResponse; use Symfony\Component\HttpFoundation\Request; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; class RedirectController extends AbstractController { public function redirectAction(Request $request) { $url = $request->query->get('next'); return new RedirectResponse($url); } }
⚠️ If someone visits yoursite.com/redirect?next=https://evil.com, they’ll be forwarded to that malicious domain. That’s dangerous!
🧪 Scan Your Website for Unvalidated Redirects
You don’t need to spend a dime to check if your website is vulnerable. Use our 100% online website vulnerability scanner here:
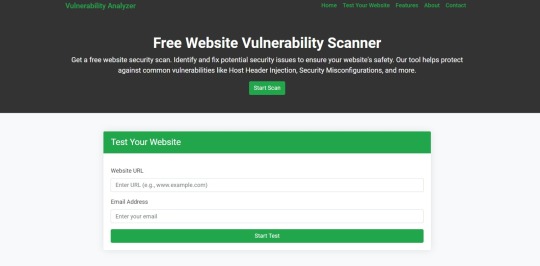
Screenshot of the free tools webpage where you can access security assessment tools.
This scanner identifies redirect vulnerabilities, missing security headers, and more. It’s perfect for Symfony and other PHP frameworks.
🔐 Secure Coding Practices in Symfony
Here’s how you can fix the issue using a whitelist of URLs or internal routes.
✅ Secure Example with Allowed Redirects:
public function redirectSafe(Request $request) { $next = $request->query->get('next'); $allowedRoutes = ['home', 'dashboard']; if (in_array($next, $allowedRoutes)) { return $this->redirectToRoute($next); } return $this->redirectToRoute('home'); }
Or restrict to internal URLs only:
public function redirectIfInternal(Request $request) { $url = $request->query->get('next'); if (parse_url($url, PHP_URL_HOST) === null) { return new RedirectResponse($url); } throw new \Exception("Invalid redirect URL"); }
🧠 Pro Tip: Always validate user-controlled redirect parameters before using them.
📑 Sample Report from Our Tool
After scanning your Symfony app, the tool will generate a detailed vulnerability report. Below is a sample screenshot from the results section to check Website Vulnerability:
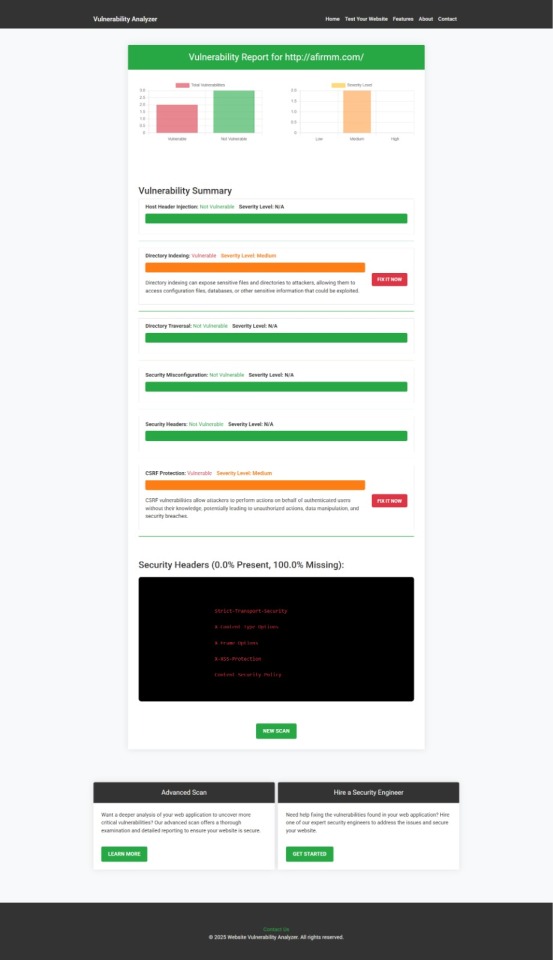
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🛡️ Enhance Security with Our Web App Pentest Services
Don’t stop at redirects. Protect your Symfony application against all OWASP Top 10 risks.
🔗 Explore our tailored service: ➡️ https://www.pentesttesting.com/web-app-penetration-testing-services/
This service includes:
Authentication and session testing
Input validation review
Business logic flaw detection
Comprehensive final report
Get peace of mind by letting professionals test your app.
🤝 Agencies & MSPs: Resell Our Cybersecurity Services
Are you an IT agency or software development firm? Let us do the security while you focus on development.
👥 Partner with us and resell pentesting under your brand: 🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
📬 Stay Updated — Subscribe to Our Newsletter
Never miss critical security updates and techniques for Symfony, Laravel, React.js, and more.
🗞️ Subscribe via LinkedIn: 🔗 https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
🧪 Quick Summary
✔️ Vulnerability: Unvalidated Redirects in Symfony ✔️ Risk: Phishing, user redirection to malicious domains ✔️ Solution: Always validate redirect destinations ✔️ Tool: Use https://free.pentesttesting.com/ for instant vulnerability detection
🔚 Final Thoughts
Unvalidated Redirects may seem harmless, but they can open up doors for social engineering, phishing, and trust abuse. Symfony developers must validate, whitelist, or sanitize redirect targets before processing them.
Want a free scan? DM me or check https://free.pentesttesting.com/
0 notes
Text
DevSecOps Tutorial: A Beginner’s Guide to Secure DevOps
Introduction: Why Security Can’t Be an Afterthought in DevOps
Imagine launching your software faster than ever only to realize it's wide open to cyberattacks. That’s the risk organizations take when they separate security from DevOps. In today’s fast-paced tech world, security must move at the same speed as development and operations. This is where DevSecOps comes in.

In this comprehensive DevSecOps Tutorial, you'll learn how integrating security into DevOps workflows leads to secure, efficient, and reliable software delivery. Whether you're just starting out or eyeing a Certified DevSecOps Professional path, this guide breaks down the essentials and sets you on the right track.
What Is DevSecOps?
DevSecOps stands for Development, Security, and Operations. It extends the DevOps philosophy by embedding security into every stage of the software development lifecycle (SDLC) from planning and coding to deployment and monitoring.
Key Principles of DevSecOps:
Shift Left: Start security practices early in the development cycle.
Automation: Use automated tools for code scanning, threat modeling, and compliance.
Collaboration: Promote shared responsibility among developers, security teams, and operations.
By building a security-first mindset, DevSecOps helps teams catch vulnerabilities before they become breaches.
Why DevSecOps Matters in Modern Software Delivery
Security breaches cost businesses millions and tarnish reputations. According to IBM’s 2024 Cost of a Data Breach Report, the average breach costs $4.45 million. Traditional security practices performed at the end of the SDLC can’t keep up.
DevSecOps bridges this gap by:
Reducing risk exposure
Speeding up secure code deployment
Improving compliance posture
A DevSecOps course can help professionals develop a solid foundation in secure development practices, enabling them to meet growing industry demand.
Core Components of a DevSecOps Pipeline
Let’s break down the DevSecOps pipeline, a core concept in any DevSecOps Training and Certification program:
1. Planning and Requirements
Define security requirements at the planning phase.
Perform threat modeling to identify potential risks early.
2. Development
Write secure code using best practices.
Use tools like static application security testing (SAST) to scan source code in real-time.
3. Build
Integrate security tools into the CI/CD pipeline.
Use dependency scanning tools to analyze third-party components for known vulnerabilities.
4. Test
Automate security testing using DAST (Dynamic Application Security Testing).
Run unit and integration tests with security in mind.
5. Release and Deploy
Use secure configuration management.
Enforce security gates in CI/CD to prevent the deployment of risky code.
6. Monitor
Set up real-time monitoring for anomalies.
Use SIEM (Security Information and Event Management) systems to analyze logs and trigger alerts.
A robust pipeline is central to any AWS DevSecOps Certification path, especially when working with cloud-native architectures.
DevSecOps Tools You Should Know
Understanding the tools used across the DevSecOps pipeline is critical. Here's a categorized view of commonly used tools:StageToolsPlanThreatModeler, IriusRiskDevelopSonarQube, CheckmarxBuildJenkins, GitLab CI/CD, MavenTestOWASP ZAP, Burp Suite, Selenium (Security Test)DeployTerraform, Ansible, KubernetesMonitorSplunk, ELK Stack, Prometheus
These tools automate security checks, helping to integrate secure practices without slowing down development.
What You'll Learn in a DevSecOps Course
A comprehensive DevSecOps course should cover the following topics:
1. Introduction to DevSecOps
History and evolution
Key differences between DevOps and DevSecOps
3. Threat Modeling and Risk Assessment
Identifying attack surfaces
Applying STRIDE or DREAD frameworks
4. Secure Coding Practices
OWASP Top 10
Input validation, output encoding, and proper error handling
5. CI/CD Security Integration
Building secure Jenkins pipelines
Using security plug-ins in GitLab or Azure DevOps
6. Infrastructure as Code (IaC) Security
Securing Terraform and Ansible scripts
Detecting misconfigurations
7. Cloud Security and Compliance
IAM (Identity and Access Management)
Data protection in AWS environments
8. Monitoring, Logging, and Incident Response
Setting up alerts for suspicious activity
Automating incident response with SOAR tools
Whether you're pursuing a Certified DevSecOps Professional title or simply improving your skills, these areas will form the foundation of your knowledge.
DevSecOps Certification Path: Your Roadmap to Career Growth
Embarking on a DevSecOps Certification Path can elevate your career in IT security, cloud engineering, and DevOps.
Step 1: Foundation in DevOps and Security
Learn the basics of CI/CD, version control, and common attack vectors.
Step 2: Enroll in DevSecOps Training
Choose programs that offer hands-on labs and real-world projects.
Consider programs with access to practice environments.
Step 3: Certification Preparation
Review case studies.
Solve sample DevSecOps Interview Questions.
Practice with real DevSecOps pipelines.
Step 4: Earn Certification
Choose certifications aligned with your goals, such as:
Certified DevSecOps Professional
AWS DevSecOps Certification
Step 5: Apply Your Skills
Take on projects or roles where you can implement DevSecOps pipelines, perform security reviews, or automate security tasks.
Sample DevSecOps Interview Questions
Preparing for interviews? These questions can give you a head start:
What is the difference between SAST and DAST?
How would you integrate security into a CI/CD pipeline?
What tools do you recommend for IaC security scanning?
Explain the concept of "Shift Left Security."
How do you secure Kubernetes clusters in DevSecOps?
Understanding these questions often discussed in DevSecOps Training and Certification programs can help demonstrate your readiness to potential employers.
DevSecOps Tutorial: Mini Hands-On Guide
Here’s a simple step-by-step tutorial on setting up a basic DevSecOps pipeline using Jenkins, SonarQube, and OWASP ZAP:
🔹 Step 1: Set Up Jenkins
Install Jenkins and create a new freestyle project.
🔹 Step 2: Integrate SonarQube
Use the SonarQube plugin to analyze your code for static vulnerabilities.
mvn sonar:sonar \ -Dsonar.projectKey=my-app \ -Dsonar.host.url=http://localhost:9000 \ -Dsonar.login=my_token
🔹 Step 3: Add ZAP Security Test
Use OWASP ZAP to perform a dynamic scan on the deployed application.
zap-cli quick-scan --self-contained http://yourapp.com
🔹 Step 4: Fail Build on Vulnerability
Use thresholds in Jenkins to fail builds if critical vulnerabilities are detected.
Real-World DevSecOps Use Case
A Fortune 500 e-commerce company integrated DevSecOps by:
Automating threat modeling using IriusRisk
Shifting security testing left with SonarQube and Checkmarx
Deploying microservices securely on AWS with container scanning and IAM policies
Achieving 25% reduction in security vulnerabilities within 3 months
This real-world transformation illustrates how DevSecOps Tutorial principles directly impact business resilience.
Benefits of DevSecOps for Organizations and Professionals
For Organizations:
Faster delivery without compromising security
Cost savings from early vulnerability detection
Improved compliance with standards like ISO, NIST, and GDPR
For Professionals:
High-demand skills for cloud and security roles
Eligibility for advanced roles like Security Engineer, DevSecOps Engineer, and Cloud Security Architect
Salary growth DevSecOps professionals often earn 20–30% more than traditional DevOps roles
Why Choose H2K Infosys for DevSecOps Training?
H2K Infosys offers tailored DevSecOps Training and Certification programs with a hands-on, project-driven approach. From fundamentals to advanced concepts like cloud-native security and compliance, learners are equipped with everything they need to thrive in real-world environments.
Additionally, H2K Infosys provides:
Expert instructors from the industry
Practical labs and projects
Placement guidance post-certification
Whether you're aiming for the Certified DevSecOps Professional badge or preparing for an AWS DevSecOps Certification, H2K Infosys can be your trusted partner.
Conclusion: Begin Your DevSecOps Journey Today
The future of secure software development lies in DevSecOps. This beginner’s DevSecOps Tutorial gives you the roadmap from pipeline basics to certification strategies to confidently step into this field.
Start learning. Start securing. Start building your future with DevSecOps.
Ready to secure your DevOps pipeline? Begin your journey with DevSecOps training today! Upskill now and stand out in a security-first tech world.
0 notes
Text
How the Best Website Development Company in Ahmedabad Ensures Security in Every Build
In today's highly connected world, keeping your website secure isn't optional, it's essential. As online threats become more advanced every day, businesses can't afford to ignore security or leave it until the end. That’s why choosing the best website development company in Ahmedabad matters more than ever in 2025.
Ahmedabad has emerged as a hub of digital innovation and reliable development services. Among the many web service providers in India, companies in this city stand out for their ability to blend technology, creativity, and most importantly robust security protocols into every project.
In this article, we’ll explore how top-tier developers in Ahmedabad are integrating end-to-end security at every stage of a web project and what makes them the ideal choice for your business website.
Why Website Security Is Non-Negotiable in 2025
Website breaches are no longer rare occurrences. According to recent reports, small and medium-sized businesses are among the top targets for cybercriminals. From data breaches to ransomware attacks, even a small vulnerability in your website can result in significant reputational and financial loss.
That’s why the best website development company in Ahmedabad follows strict security guidelines from planning and coding to hosting and maintenance. These companies do not just create visually appealing and responsive websites; they also build digital fortresses to protect user data and business operations.
Let's take a look at security methods these reliable agencies use in 2025.
1. Security-First Architecture and Planning
Every secure website begins with thoughtful planning. The best development agencies in Ahmedabad follow a security-first mindset, incorporating safeguards into the core architecture.
Key Practices:
Threat Modeling During Planning: Before writing a single line of code, the team maps potential vulnerabilities through threat modeling. This helps them preemptively secure data entry points, admin panels, and integrations.
Use of Secure Frameworks: Instead of building from scratch or using outdated platforms, developers choose modern frameworks with built-in security features.
Compliance-Driven Development: Whether it’s GDPR, HIPAA, or PCI-DSS, leading developers ensure that the site complies with international data protection standards right from the start.
By focusing on structure, the best agencies ensure your website has a solid, secure foundation that is harder for hackers to exploit.
2. Secure Coding Standards and Best Practices
The most sophisticated websites are only as safe as their code. Vulnerabilities often originate from careless coding, third-party scripts, or outdated plugins.
How Ahmedabad’s Top Developers Handle It:
OWASP Guidelines: Development teams stick to the OWASP Top 10, a well known global list of major security threats in web applications.These threats include SQL injection, cross site scripting, and unsafe data handling.
Code Review & Pair Programming: Many leading firms adopt peer reviews and pair programming sessions to double-check every code snippet for flaws.
Sanitization & Validation: User input is always validated on both the client and server sides to prevent injection attacks.
Secure coding isn’t just about writing clean code, it's about anticipating potential misuse and sealing off loopholes from day one.
3. HTTPS, SSL, and Data Encryption
Transmitting sensitive data without encryption is a major red flag. The best website development companies in Ahmedabad implement end-to-end encryption by default.
How It’s Done:
HTTPS by Default: SSL certificates are installed at the beginning of the deployment process, ensuring all communications between the user and the server are encrypted.
TLS 1.3 Protocol: Businesses now use TLS 1.3 because it's quicker and safer than older versions.
Encrypted Databases: Sensitive user data such as passwords, payment information, and personal identification details are stored in hashed and salted formats using secure algorithms like bcrypt or SHA-256.
By encrypting both data at rest and data in transit, agencies reduce the likelihood of data theft even in the case of server breaches.
4. Role-Based Access Control and Admin Security
Managing who can access what on a website is one of the most ignored parts of web security. Developers in Ahmedabad now incorporate Role-Based Access Control (RBAC) to ensure that users only access what they are authorized to.

Best Practices in Use:
Multi - Factor Authentication: Admin panels and CMS dashboards are secured with two step or multi-step verification methods.
Audit Trails & Logs: Every admin action is logged, making it easier to identify malicious activities.
Limited Access Permissions: Access to sensitive functions is strictly restricted to verified roles, reducing the attack surface area.
These practices prevent internal threats and unauthorized access, especially on content-heavy or eCommerce sites.
5. Automated Vulnerability Scanning & Regular Penetration Testing
Creating a secure website isn't something you do just once, it's a continuous effort. The best website development companies in Ahmedabad offer ongoing security audits as part of their post-launch services.
Tools and Techniques:
SAST & DAST Tools: Static and dynamic analysis tools (like SonarQube or Burp Suite) are used to continuously scan for vulnerabilities.
Penetration Testing: Ethical hackers are employed to simulate real-world attacks, uncovering any weaknesses.
Regular Updates: CMS systems, plugins, themes, and libraries are frequently updated to fix newly found security issues.
These post-deployment measures ensure that your site stays protected even as cyber threats evolve.
6. Secure Hosting and Cloud Infrastructure
Even a secure website can be compromised by poor hosting choices. Recognizing this, the best agencies in Ahmedabad recommend or provide secure cloud hosting environments.
Hosting Security Measures Include:
Firewalls and WAFs
Auto-scaling & DDoS Mitigation
Secure Shell (SSH) Access Only
Automated Backups with Ransomware Protection
Cloud providers like AWS, Google Cloud, and Azure are often the go-to platforms for these agencies, and they leverage features like IAM and network isolation to protect client data.
7. User Education & Secure UX
Security also depends on the end-user. A secure site can still be compromised if users fall for phishing attacks or use weak passwords. The best web development firms in Ahmedabad offer secure UX features and user education.
Some Features Include:
Password Strength Meters
CAPTCHAs & Bot Protection
Real-time Alerts for Suspicious Login Attempts
Security-focused Onboarding for Admins
Security isn’t just backend-focused anymore it extends to the frontend design, ensuring that users are actively involved in maintaining site integrity.
Conclusion
With the growing reliance on digital channels, your website must be more than just functional and attractive; it needs to be secure at its core. The best website development company in Ahmedabad understands this responsibility. From architecture to hosting, from code to customer education, every part of the build is designed with security-first principles.
In 2025, web security is not optional. It’s the backbone of your digital credibility and customer trust. Partnering with a web development company that values and implements comprehensive security measures is the smartest investment a business can make today.
Whether you're launching an eCommerce site, a corporate portal, or a SaaS platform, don't settle for anything less than excellence. Choose a company that prioritizes security in every pixel, every process, and every piece of code.
0 notes
Text
cybersecurity penetration testing
cybersecurity penetration testing
Cybersecurity Penetration Testing is a proactive security assessment that simulates real-world cyberattacks to identify and exploit vulnerabilities within an organization’s IT infrastructure. Its primary purpose is to evaluate how secure networks, applications, and systems are against potential hackers, helping organizations fix weaknesses before they can be exploited maliciously.
Unlike simple vulnerability scans, cybersecurity penetration testing goes deeper by mimicking attacker techniques to determine the actual risk and impact of a successful breach. It covers a wide range of targets, including web and mobile applications, internal and external networks, APIs, cloud environments, servers, and IoT devices. Ethical hackers, often certified with CEH, OSCP, or CREST, perform these tests using a mix of automated tools and manual techniques to uncover flaws such as SQL injection, cross-site scripting (XSS), broken authentication, privilege escalation, insecure configurations, and outdated software.
The testing process typically follows structured phases:
Planning and Scoping – Defining objectives, legal permissions, and systems in scope.
Reconnaissance and Scanning – Gathering information about the target and identifying vulnerabilities.
Exploitation – Attempting to gain unauthorized access, escalate privileges, or steal sensitive data.
Post-Exploitation – Assessing how deep an attacker could infiltrate the system and its impact.
Reporting and Remediation – Providing detailed findings, risk severity, and actionable remediation steps.
Cybersecurity penetration testing is aligned with global frameworks such as OWASP Top 10, NIST 800-115, MITRE ATT&CK, and PTES. It is also a mandatory requirement for compliance with PCI DSS, ISO 27001, HIPAA, and GDPR.
In conclusion, cybersecurity penetration testing is essential for strengthening an organization’s defenses, protecting sensitive data, and ensuring regulatory compliance. By uncovering vulnerabilities before hackers do, businesses can reduce the risk of costly breaches, maintain customer trust, and enhance overall cyber resilience.
0 notes
Text
API Security: A Complete Guide to Securing Your APIs in 2025

In the age of cloud-native apps, microservices, and mobile-first development, APIs are the core of modern digital infrastructure. But with this rise comes a critical need for robust API security.
APIs are attractive targets for attackers because they expose application logic and sensitive data. This guide covers everything you need to know about API security: what it is, why it matters, common vulnerabilities, and how to test and protect your APIs in 2025.
What Is API Security?
API security refers to the set of practices, tools, and protocols used to protect Application Programming Interfaces from unauthorized access, data breaches, and abuse.
It ensures that APIs:
Authenticate legitimate users
Authorize proper access to data and functions
Prevent malicious inputs and attacks
Maintain confidentiality and integrity of data in transit
Why API Security Matters
APIs are everywhere: From mobile apps to third-party integrations, APIs are integral to functionality and communication.
APIs expose sensitive data: User credentials, payment info, and internal system data all pass through APIs.
They’re high-value attack surfaces: A single weak API endpoint can lead to a massive breach.
OWASP recognizes the threat: The OWASP API Security Top 10 highlights common and critical API threats.
Common API Security Vulnerabilities
Vulnerability Description Broken Object Level Authorization Improper access control to individual resources Broken Authentication Weak tokens or exposed credentials Excessive Data Exposure APIs returning more data than necessary Lack of Rate Limiting Allows brute force and DDoS attacks Mass Assignment Allowing unintended fields to be modified via input Injection Attacks (e.g. SQLi) Malicious data sent through API input Improper Error Handling Exposes internal logic and stack traces
Key API Security Best Practices
1. Use Strong Authentication and Authorization
Implement OAuth 2.0 or OpenID Connect
Validate JWTs securely
Use scopes and roles for granular permissions
2. Rate Limiting & Throttling
Prevent abuse and DoS attacks by limiting request frequency per user/IP
3. Input Validation & Output Encoding
Sanitize input to prevent injection attacks
Encode output to avoid XSS and data leakage
4. Use HTTPS Everywhere
Encrypt data in transit using TLS
Redirect all HTTP traffic to HTTPS
5. Avoid Overexposing Data
Only return necessary fields
Use pagination to limit result sizes
6. Secure API Keys
Never hard-code keys in frontend apps
Rotate and expire unused keys regularly
7. Implement Logging and Monitoring
Detect abnormal behavior early
Use tools like ELK, Prometheus, or Keploy for trace-level insights
How to Perform API Security Testing
API security testing involves simulating attacks, inspecting responses, and validating protections.
🔐 Manual Testing Techniques:
Fuzzing endpoints with invalid data
Bypassing authorization logic
Checking for unhandled errors
⚙️ Automated Tools:
OWASP ZAP – Scans APIs for vulnerabilities
Postman/Newman – Automate security assertions
Burp Suite – Advanced proxy testing and scanning
Keploy – Records real API traffic, auto-generates tests with mock data, helping catch regressions and data leaks
API Security in DevOps and CI/CD
Integrate security tests in CI pipelines
Block releases if APIs fail security checks
Shift-left by testing early and often during development
Use container and cloud scanning tools for full-stack security
Role of API Gateways and WAFs
API Gateways (e.g., Kong, Apigee, AWS API Gateway) help with:
Authentication
Rate limiting
Request transformation
Caching and logging
Web Application Firewalls (WAFs) add another layer by detecting and blocking threats in real-time.
Final Thoughts
In a world where APIs are the backbone of apps, ensuring their security is no longer optional. Whether you’re a developer, tester, or security engineer, understanding and implementing robust API security measures is crucial.
Combine strong security practices with automation tools like Keploy to generate test cases and mocks from real traffic, enabling secure, reliable API testing at scale.
0 notes
Text
0 notes
Text
Breaking Boundaries: How Innovation is Transforming Software Testing
From Cost Center to Competitive Advantage
For many years, software testing lived under a cloud of misconceptions. Businesses often saw it as a necessary cost rather than a true value driver. Testers were the last gatekeepers, scrambling to find bugs under tight deadlines before a release went out the door. But that old narrative is fading. Innovation in software testing is turning quality assurance into a strategic force that can define a company’s reputation, speed to market, and customer satisfaction.
Modern software systems are more complex than ever. They’re built to run on countless devices, operate in cloud environments, and integrate with external services through APIs. Users demand seamless experiences and expect issues to be fixed immediately—or they’ll go elsewhere. This pressure has fueled a wave of innovation that is reshaping how software is tested, who does the testing, and the tools used to achieve high-quality results.
The Power of Intelligent Automation
Automation in testing isn’t new, but how we approach it has changed dramatically. Early test automation relied on rigid scripts that often broke with even small changes in an application’s interface. Maintaining these scripts was time-consuming and costly. Today’s innovative tools leverage artificial intelligence and machine learning to make automation smarter and more adaptable.
For instance, AI-driven tools like TestCraft or Functionize can analyze the structure of web pages and recognize objects even when their identifiers change. This reduces the headache of brittle tests that fail for minor cosmetic changes. Visual testing tools like Percy or Applitools take screenshots of applications and compare them pixel by pixel, highlighting unexpected differences that human testers might miss.
Beyond UI testing, AI is helping generate test data, predict which tests are most critical, and even write test cases based on user behavior patterns. Such advancements free up testers to focus on more complex problem-solving and exploratory testing, rather than routine test execution.
Integration with Development Pipelines
One of the biggest innovations in software testing is how deeply it has become integrated into the development process. In traditional development cycles, testing occurred only after coding was complete. If testers discovered major issues, deadlines slipped, costs soared, and frustration spread across teams.
DevOps and agile methodologies changed this dynamic. Today, testing happens in parallel with development, thanks to continuous integration and continuous delivery (CI/CD) pipelines. Every time developers commit code, automated tests run to validate changes immediately. This approach, known as continuous testing, dramatically reduces the time it takes to catch and fix defects.
Even performance and security testing have found their place earlier in the cycle. Tools like Gatling and JMeter can simulate thousands of users hitting a system, while security scanning tools check for vulnerabilities as code is written. Instead of being a separate phase, testing has become a seamless part of how modern software is built and shipped.
Expanding Beyond Functional Testing
Innovation in software testing is also expanding the definition of what “quality” means. It’s no longer enough for software to just “work.” Users expect fast load times, visually appealing interfaces, and reliable performance under pressure. This has sparked growth in specialized testing areas, each bringing its own innovative approaches.
Performance Testing: Tools like k6 and Locust allow testers to write scripts that mimic real user behavior, helping teams identify bottlenecks before customers do.
Accessibility Testing: Modern tools like axe or Pa11y scan applications to ensure they’re usable by people with disabilities—a legal requirement and an ethical responsibility.
Security Testing: Automated scanners like OWASP ZAP can detect vulnerabilities early, reducing the chance of costly breaches.
These innovations ensure that software isn’t just functional—it’s robust, inclusive, and secure.
Shift-Left and Shift-Right: Two Sides of the Same Coin
Two phrases have become buzzwords in the world of software testing innovation: “shift-left” and “shift-right.” Both are critical to modern quality strategies.
Shift-Left: Pushing testing earlier in the development process. Developers write unit tests alongside production code, execute static code analysis tools, and even collaborate with testers during the design phase to identify potential issues before a single line of code is written.
Shift-Right: Extending testing into production environments. Instead of assuming testing ends at deployment, teams now observe real user behavior through monitoring tools, gather analytics on application usage, and run tests in production under controlled conditions using feature flags.
Together, these approaches provide a continuous loop of feedback that helps improve software quality throughout its lifecycle.
The Human Element: Testers as Innovators
Amid all the technological advances, one constant remains: the critical role of human testers. Innovative tools are powerful, but they can’t replace human judgment, creativity, and empathy. Modern testers have become more than bug finders—they are quality engineers, business analysts, and customer advocates.
Today’s testers work closely with developers to understand business requirements, contribute to test automation, and identify risks that might not be visible in code alone. They explore systems from a user’s perspective, anticipating how real people might interact with software in ways developers never imagined.
To thrive in this innovative era, testers are learning new skills—coding, cloud architecture, data analysis, and AI literacy. Equally important are soft skills: communication, critical thinking, and the ability to champion quality in cross-functional teams.
Innovation is a Journey, Not a Destination
Software testing innovation isn’t a one-time achievement—it’s an ongoing journey. As technology continues to evolve, new challenges will arise. The rise of low-code platforms, edge computing, and the increasing reliance on AI systems will push testing into uncharted territory.
But one thing is certain: organizations that embrace innovative testing practices are better equipped to deliver high-quality software quickly and confidently. In a digital world where reputation can be won or lost with a single flawed release, innovative software testing has become not just an advantage but a necessity.
Software testing has stepped into the spotlight as a creative, strategic force. It’s no longer merely about finding defects—it’s about unlocking new possibilities, building user trust, and driving business success. The future of software testing innovation is bright, and it’s being shaped every day by those willing to push boundaries and reimagine what quality truly means.
0 notes
Text
Crafting Excellence: Your Go‑To Software Development Company in Chennai

In today’s digital era, a robust software solution isn’t just “nice to have”—it’s the spine of every thriving business. If you’re searching for the best software development company in Chennai, look no further. Our team blends cutting‑edge technology, agile processes, and a client‑first mindset to deliver scalable, secure, and user‑friendly software tailored to your unique needs.
Why Chennai Leads the Way in Software Development
Chennai, often dubbed the “Detroit of India,” has evolved beyond manufacturing into a bustling IT hub. Home to world‑class engineering institutes and a vast talent pool, the city has attracted both global giants and nimble startups. As a Software Development Company in Chennai, we leverage this ecosystem to tap into top talent, innovative mindsets, and competitive costs—ensuring you get enterprise‑grade software without the enterprise price tag.
Our Core Services
Custom Software Development From requirement analysis to deployment and maintenance, we build bespoke applications—desktop, web, and mobile—that align perfectly with your business goals.
Enterprise Solutions & ERP Streamline operations, automate workflows, and gain real‑time insights with our tailor‑made ERP and CRM platforms.
Cloud Migration & DevOps Transition to AWS, Azure, or Google Cloud seamlessly. Our DevOps experts implement CI/CD pipelines, containerization (Docker, Kubernetes), and infrastructure as code for unparalleled reliability.
Product Engineering & MVPs Validate your startup idea quickly with an MVP. We follow lean‑agile principles to iterate rapidly, reducing time‑to‑market and sharpening product‑market fit.
Quality Assurance & Testing Our dedicated QA team conducts functional, performance, security, and usability testing—ensuring your software is rock‑solid and user‑friendly before it reaches production.
UI/UX Design A stunning interface alone isn’t enough. We marry intuitive user flows with elegant design, boosting adoption rates and reducing support overhead.
What Sets Us Apart as the Best Software Development Company in Chennai
Agile & Transparent Process You stay in the loop at every sprint review. Prioritized backlogs, daily standups, and fortnightly demos ensure your feedback drives the project forward.
Domain Expertise Across Industries Whether you’re in finance, healthcare, e‑commerce, or manufacturing, our seasoned consultants understand your regulatory, security, and user‑experience needs.
Dedicated Teams & Project Ownership Unlike break‑fix shops, we form long‑term partnerships. Your dedicated team becomes an extension of your organization, aligning with your culture and vision.
Robust Security & Compliance From OWASP‑hardened code to GDPR and HIPAA compliance, we bake security into every layer—data, network, application—so you can sleep easy.
Cost‑Effective Engagement Models Choose from fixed‑price, time‑and‑materials, or outcome‑based contracts. Scale the team up or down as your needs evolve, without hidden costs.
Success Stories: Proven Impact
FinTech Transformation A leading NBFC partnered with us to build a lending‑automation platform. We delivered a 40% reduction in approval time and a 30% increase in loan throughput within six months.
Healthcare Innovation For a network of clinics, we developed a telemedicine portal integrated with IoT diagnostics. Patient consultations tripled, while operational costs dropped by 25%.
E‑Commerce Revamp A regional retailer saw 50% growth in online sales after we launched a headless commerce architecture coupled with personalized AI‑driven recommendations.
How to Get Started
Free Discovery Call Share your vision, challenges, and goals. We listen first, advise next.
Solution Blueprint & Proposal Receive a detailed roadmap, timeline, and cost estimate—no surprises, ever.
Kick‑off & Delivery Your dedicated team hits the ground running. Regular checkpoints ensure we’re always on track.
Partner with the Leading Software Development Company in Chennai
When you choose us, you’re not just hiring developers—you’re gaining a strategic ally committed to your success. Whether you need a transformative enterprise system or a nimble startup MVP, we have the expertise, processes, and passion to deliver.
Reach out today for a free consultation and discover why we’re regarded as the best software development company in Chennai. Let’s build the future—together.
0 notes
Text
WebSenor – A Leading Mobile App Development Company in Bangalore Driving Digital Innovation

Bangalore has long been recognized as the technology capital of India. Home to some of the country’s most innovative startups and tech giants, the city is now also a major center for mobile application solutions. In today’s digital-first world, businesses across all industries are increasingly relying on mobile apps to improve engagement, streamline operations, and drive growth. WebSenor stands out as a leading mobile app development company in Bangalore, offering end-to-end services for startups, SMEs, and enterprises alike. With a mission to empower businesses through digital transformation, WebSenor blends innovation, user experience, and modern technologies to deliver top-tier mobile solutions.
Why Choose WebSenor for Mobile App Development?
Proven Expertise and Industry Experience
WebSenor brings over a decade of experience in mobile and software development in Bangalore. Their portfolio includes more than 500 successfully delivered projects across industries such as healthcare, e-commerce, logistics, and education.
Whether it's building a new product from scratch or modernizing an existing solution, the company specializes in custom mobile app development in Bangalore. Their services cover native Android, iOS, and cross-platform applications—making them a reliable choice for any digital product development need.
Skilled and Certified Team of Developers
WebSenor’s team consists of highly qualified mobile app developers in Bangalore who are not only technically skilled but also aligned with industry best practices. Developers at WebSenor are proficient in:
Flutter and React Native for cross-platform apps
Kotlin and Java for Android development
Swift and Objective-C for iOS development
The company also encourages continuous upskilling, ensuring the team is well-versed in the latest development tools and frameworks. Their leadership team brings a strategic approach, ensuring each project is delivered with precision and purpose.
Focus on Client-Centric Solutions
At the core of WebSenor’s approach is a strong focus on client needs. Each project begins with a deep understanding of the client's goals and challenges. By adopting agile development methodologies, WebSenor delivers faster iterations, better communication, and more transparent project tracking.
This client-first philosophy has allowed them to tailor solutions that not only meet but often exceed expectations. Whether you’re a startup looking for a product-market fit or an enterprise scaling operations, WebSenor adapts its approach to serve you better.
Innovative Technologies Driving WebSenor’s Success
Integration of AI, IoT, Blockchain, and Cloud
WebSenor stays ahead of the curve by integrating emerging technologies into its mobile applications. These include:
AI-based chatbots and recommendation systems
IoT-enabled tracking systems for logistics
Blockchain-based secure transactions
Cloud-based infrastructure for high availability and scalability
These advanced technologies allow businesses to create intelligent, connected, and future-ready applications.
UI/UX Excellence and Human-Centered Design
Mobile app success doesn’t depend on code alone—it’s also about how users feel while using the app. WebSenor emphasizes UI/UX design for mobile apps, following a human-centered design approach. Using tools like Figma, Adobe XD, and Sketch, their designers create clean, intuitive, and engaging user experiences that drive higher user retention and satisfaction.
Performance, Security, and Scalability as Priorities
WebSenor conducts end-to-end testing, performance optimization, and rigorous quality checks to ensure the applications they deliver are fast and stable. Security is another cornerstone, with adherence to GDPR, OWASP, and other global compliance frameworks.
With scalable architecture, their apps are capable of handling enterprise-level traffic, ensuring smooth performance as the user base grows.
Industries Served by WebSenor
Healthcare and Telemedicine
From online consultation platforms to patient management systems, WebSenor delivers secure, compliant, and user-friendly apps for the healthcare industry. Their solutions support remote diagnostics, e-prescriptions, and real-time health tracking.
E-commerce and Retail
WebSenor is an experienced Android app development company in Bangalore and iOS app development company in Bangalore that builds mobile shopping platforms with features like catalog management, payment integration, real-time notifications, and inventory tracking.
Education and E-learning
For the education sector, WebSenor develops learning management systems (LMS) and interactive mobile learning tools. Their apps support video-based lessons, quizzes, progress tracking, and multi-language support—ideal for both formal education and corporate training.
Logistics and Transportation
WebSenor has built mobile solutions for fleet tracking, route optimization, delivery status updates, and real-time GPS tracking. Their experience in logistics gives them the edge in designing reliable and high-performance apps for transportation companies.
What Clients Say – Testimonials and Success Stories
Real Client Feedback
Clients consistently praise WebSenor’s professionalism, technical competence, and transparent communication. Many have highlighted the ease of working with their team and the measurable improvements in user engagement and revenue after deploying the apps.
For example:
"WebSenor understood our vision from day one. Their team delivered a user-friendly app that perfectly aligned with our business model. We saw a 40% increase in customer retention within 3 months."
Case Studies of Transformative Projects
A retail startup partnered with WebSenor for an app launch, resulting in 100,000+ downloads and a 3x increase in sales within the first quarter.
A telemedicine platform developed by WebSenor helped doctors reach over 50,000 patients during the pandemic, offering secure video consultations and digital prescriptions.
These success stories demonstrate WebSenor’s ability to deliver high-impact digital products.
Commitment to Quality and Compliance
Adherence to Global Development Standards
WebSenor follows Agile/Scrum methodologies, ensuring continuous feedback loops and quality control at every stage. They comply with ISO standards, and all their apps meet the guidelines of Apple’s App Store and Google Play Store.
Transparent Communication and Support
Clients have full visibility into the development process through tools like Jira and Trello. A dedicated account manager ensures seamless coordination and communication throughout the project lifecycle.
Moreover, WebSenor offers post-launch support, including bug fixes, updates, and feature enhancements—ensuring long-term success of the app.
WebSenor’s Vision for the Future of Mobile App Development
Embracing Future Trends
WebSenor is actively investing in the future of app development. Their R&D team is exploring:
AR/VR experiences for e-commerce and education
Wearable app integration for health and fitness
Voice-enabled interfaces for smart assistant compatibility
This forward-thinking mindset ensures that WebSenor remains at the forefront of innovation.
Empowering Businesses Through Digital Innovation
As a startup mobile app partner, WebSenor provides not just technology, but strategic guidance. Their vision is to make digital transformation accessible to businesses of all sizes. By combining creativity, technology, and business insight, WebSenor helps clients scale faster and serve their users better.
Get in Touch with WebSenor
Ready to build your mobile app? WebSenor invites startups, enterprises, and agencies to explore their services and bring their app ideas to life.
Website: https://websenor.com/mobile-app-development-companies-in-bangalore/
Office: Located in Bangalore with branches in Udaipur, Dubai, and other global locations
Certifications: ISO 9001:2015 Certified
Ratings: 4.8+ stars on Google and Clutch
Whether you need a simple MVP or a full-scale enterprise app, WebSenor provides reliable app development services in Bangalore to meet your goals.
Conclusion
WebSenor has established itself as a trusted mobile app development company in Bangalore, delivering high-quality, innovative, and scalable solutions. With a skilled team, proven methodology, and commitment to excellence, WebSenor continues to help businesses succeed in the digital era. Whether you’re looking for custom mobile app development in Bangalore, outsourcing your development needs, or searching for the best app developers in Bangalore, WebSenor stands ready to be your partner in innovation. Get in touch today to begin your journey toward digital transformation.
#MobileAppDevelopment#AppDevelopmentBangalore#WebSenor#MobileAppDevelopers#TopAppDevelopmentCompany#CustomAppDevelopment#AndroidAppDevelopment#iOSAppDevelopment#AppDevelopmentServices#TechInBangalore#SoftwareDevelopmentIndia#DigitalInnovation#StartupTechPartner#AppDevelopmentExperts#UIUXDesign#OutsourcingAppDevelopment#MobileApplicationSolutions#BestAppDevelopers#DigitalTransformation#AppDevelopmentCost
0 notes
Text
WebSocket Vulnerabilities in Symfony: A Secure Guide
WebSockets are widely used in Symfony applications to enable real-time communication, but they also open up new attack surfaces if not implemented securely. This post explores common WebSocket vulnerabilities in Symfony, shows how to test for them, and gives secure coding practices with examples.
If you maintain a Symfony web application, make sure you scan your website with our Website Vulnerability Scanner online free.
Why WebSocket Security Matters in Symfony
Symfony developers often use WebSocket libraries such as Ratchet, Mercure, or custom WS servers. Unlike HTTP, WebSockets establish a long-lived TCP connection, bypassing some of the typical HTTP request-response protections.
Attackers can exploit vulnerabilities such as:
Cross-Site WebSocket Hijacking (CSWSH)
Insecure Origin validation
Message tampering & injection
Lack of authentication on WebSocket channels
Information disclosure over unencrypted WS (ws://)
Example scenario: If you forget to validate the Origin header, a malicious site can connect to your WebSocket endpoint from a victim’s browser and hijack their session.
Testing WebSocket Security in Symfony
You can test your Symfony app’s WebSocket endpoints with tools like:
wscat
Burp Suite
OWASP ZAP
Our Free Website Vulnerability Scanner
📷 Screenshot of our Website Vulnerability Scanner tool interface:
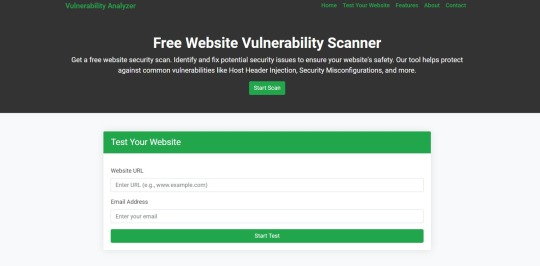
Screenshot of the free tools webpage where you can access security assessment tools.
Run a scan, and you’ll get a detailed vulnerability report highlighting weaknesses.
📷 Sample assessment report generated by our free tool to check Website Vulnerability:
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Coding Example: Protecting WebSocket in Symfony with Ratchet
Here’s how you can securely validate WebSocket connections in Symfony using Ratchet:
1️⃣ Validate the Origin
use Ratchet\MessageComponentInterface; use Ratchet\ConnectionInterface; class SecureChat implements MessageComponentInterface { public function onOpen(ConnectionInterface $conn) { $origin = $conn->httpRequest->getHeader('Origin'); if (!in_array($origin[0], ['https://yourdomain.com'])) { $conn->close(); return; } echo "Connection from {$conn->remoteAddress}\n"; } public function onMessage(ConnectionInterface $from, $msg) { // Sanitize & handle messages } public function onClose(ConnectionInterface $conn) {} public function onError(ConnectionInterface $conn, \Exception $e) {} }
✅ This ensures only trusted origins can establish a connection.
2️⃣ Enforce TLS (WSS)
Always configure your WebSocket server to run behind HTTPS and accept only wss:// connections.
In your Symfony Nginx config:
location /ws { proxy_pass http://127.0.0.1:8080; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; proxy_set_header Host $host; }
And make sure your TLS certificates are properly configured.
3️⃣ Authenticate WebSocket Clients
You can use Symfony’s session or JWT tokens during the handshake:
use Firebase\JWT\JWT; public function onOpen(ConnectionInterface $conn) { $queryParams = $conn->httpRequest->getUri()->getQuery(); parse_str($queryParams, $params); $jwt = $params['token'] ?? ''; try { $payload = JWT::decode($jwt, $yourSecretKey, ['HS256']); } catch (\Exception $e) { $conn->close(); return; } }
Learn More: Symfony Web Security Services
We offer advanced Web Application Penetration Testing Services tailored for Symfony and other PHP frameworks. If you’d like a professional team to test and secure your app, visit: 🔗 Web App Penetration Testing Services
Agencies: Offer Cybersecurity to Your Clients
Are you an agency or freelancer serving clients? You can resell our penetration testing services to your clients and earn more while protecting their web assets. Learn more: 🔗 Offer Cybersecurity Service to Your Client
📚 Stay Updated with the Latest Security Tips
We regularly publish detailed blog posts, guides, and examples on our blog: 🔗 Pentest Testing Blog
And don’t forget to subscribe to our LinkedIn newsletter to stay ahead: 🔗 Subscribe on LinkedIn
✅ Final Tip:
Run your Symfony app through our free tool for a Web App Security test and share the results with your dev team. Fixing these issues proactively saves time, money, and reputation.
Try it here: 🔗 https://free.pentesttesting.com/
1 note
·
View note
Text
Who Should Pursue Certified DevSecOps Professional?
Introduction: Security Is Now Everyone’s Job
In the past, security was a last-minute checkbox handled by a specialized team. Today, it’s a shared responsibility. The traditional waterfall method and even standalone DevOps workflows are no longer sufficient to address rapid threats and vulnerabilities. That’s where DevSecOps comes in it integrates security directly into the software development lifecycle (SDLC).
This change means that every role in tech must understand how security aligns with automation, CI/CD pipelines, compliance, and cloud-native technologies. A Certified DevSecOps Professional is equipped to meet these evolving expectations with the right tools, frameworks, and mindset.

Who Should Pursue Certified DevSecOps Professional?
Here’s a breakdown of professionals who would benefit the most from pursuing DevSecOps Certification:
1. DevOps Engineers Transitioning to Security
If you’re a DevOps engineer already familiar with automation, containers, or CI/CD pipelines, then DevSecOps is the natural next step. Learning security principles, tools like Snyk, SonarQube, or Aqua Security, and integrating them into existing pipelines enhances your skill set and career trajectory.
Why It Matters:
You’ll be able to automate security testing without slowing down deployment.
You’ll bridge the gap between developers and security teams.
2. Cybersecurity Professionals Looking to Modernize Skills
Traditional cybersecurity roles are evolving. A Certified DevSecOps Professional has both the security mindset and the development knowledge needed for modern environments, especially with the rise of AWS DevSecOps Certification tracks that focus on cloud-native deployments.
Why It Matters:
DevSecOps helps cybersecurity professionals move beyond static analysis and manual testing.
You’ll be equipped to embed security earlier in the SDLC.
3. Software Developers with an Eye on Security
Developers who understand secure coding practices and want to integrate security testing into their workflows benefit significantly from DevSecOps Online Training. Learning about tools like static application security testing (SAST) and dynamic analysis (DAST) makes their code more robust and reduces technical debt.
Why It Matters:
You’ll reduce vulnerabilities early on and speed up approvals.
Security-aware developers are increasingly preferred in hiring decisions.
4. Cloud Engineers and Architects
As cloud adoption skyrockets, so do security risks. Cloud engineers working on platforms like AWS or Azure must learn how to secure deployments, containers, and microservices. AWS DevSecOps Certification offers focused modules on securing cloud-native infrastructures.
Why It Matters:
Cloud security is one of the fastest-growing tech specialties.
You’ll learn how to protect assets across IAM, S3, EC2, Lambda, and Kubernetes.
5. IT Managers and Tech Leads
For tech leads responsible for implementing security policy across teams, DevSecOps Training and Certification provides the strategic insight required to lead adoption initiatives and guide developers toward security-focused practices.
Why It Matters:
You'll understand how to align team processes with compliance standards like GDPR or HIPAA.
You’ll be able to coach teams to implement security gates without slowing down development.
What You Learn from DevSecOps Certification
A Certified DevSecOps Professional gains a deep understanding of the tools, techniques, and cultural shifts necessary to integrate security into every stage of development and operations.
Core Topics Covered:
CI/CD Security Integration: Injecting security into Jenkins, GitLab CI, or AWS CodePipeline workflows.
Threat Modeling: Identifying risks at the design stage.
SAST/DAST Tools: Using tools like Checkmarx, OWASP ZAP, or SonarQube.
Infrastructure as Code (IaC) Security: Securing Terraform or CloudFormation scripts.
Container Security: Best practices using Docker, Kubernetes, and image scanning tools.
Secrets Management: Using tools like HashiCorp Vault or AWS Secrets Manager.
Cloud Security Best Practices: Especially focused on AWS environments for those pursuing the AWS DevSecOps Certification.
Hands-On Labs and Projects
Most DevSecOps Courses include practical labs:
Building a secure CI/CD pipeline.
Implementing role-based access control (RBAC).
Automating vulnerability scans with each deployment.
Securing API endpoints with token-based authentication.
DevSecOps Demand in the Market: Real Stats
According to a 2024 report from Cybersecurity Ventures:
Global DevSecOps market is projected to reach $23 billion by 2028.
85% of DevOps teams are expected to integrate security practices within 2 years.
Professionals with DevSecOps Certification earn 20-25% more on average than their non-certified peers.
Recruiters are actively seeking candidates with titles such as:
DevSecOps Engineer
Secure DevOps Lead
Cloud Security Engineer
Application Security Specialist
Certifications like the Certified DevSecOps Professional validate both practical and theoretical skills something that employers trust.
Navigating the DevSecOps Certification Path
The DevSecOps Certification Path usually involves the following progression:
1. Foundational Knowledge
Basic understanding of software development, DevOps, and cybersecurity.
Introductory DevSecOps tutorials or online courses.
2. Hands-On Training
Enroll in a DevSecOps Online Training program that provides practical exposure.
Learn to use tools like Jenkins, Kubernetes, and AWS services securely.
3. Certification Exam
Attempt a Certified DevSecOps Professional exam.
May include MCQs, scenario-based questions, and a hands-on lab section.
4. Specialization
Go deeper with AWS DevSecOps Certification to specialize in cloud-native security.
Consider advanced topics like chaos engineering, red teaming, and compliance automation.
Benefits of Becoming a Certified DevSecOps Professional
Here’s what you gain by completing a recognized DevSecOps Certification:
✔ Competitive Advantage
Hiring managers are actively looking for certified professionals to reduce onboarding time and ensure team agility.
✔ Higher Salary Potential
Certification can boost your earning potential significantly. Many professionals report a 30-50% salary increase after becoming certified.
✔ Broader Career Opportunities
Roles in cloud security, CI/CD design, and application risk management open up once you’re certified.
✔ Practical Security Skills
You won’t just know what to do you’ll know how to secure pipelines, code, and deployments with real-world tools.
Real-World Use Case: DevSecOps in Action
Scenario: A fintech company is rapidly releasing updates to its customer-facing mobile application. With security breaches rising, the DevOps team is under pressure to deliver securely.
Problem: Their existing CI/CD pipeline lacks security checks, allowing potential vulnerabilities to reach production.
Solution: They hire a Certified DevSecOps Professional who:
Integrates SAST tools like SonarQube in the build process.
Adds dynamic analysis using OWASP ZAP during staging.
Implements security policies in Jenkins for automated testing.
Educates developers on secure code practices.
Outcome: The release cycle continues without delay, while security compliance improves dramatically.
How AWS DevSecOps Certification Fits In
For professionals working with cloud environments, especially AWS, pursuing an AWS DevSecOps Certification is a smart choice.
What It Covers:
Securing EC2 instances, IAM policies, S3 buckets, and VPCs.
Setting up AWS WAF and Shield for DDoS protection.
Automating compliance audits with AWS Config and CloudTrail.
Using AWS CodePipeline with security gates.
This specialization aligns with roles such as:
AWS Cloud Security Engineer
DevSecOps Architect
Cloud Automation Specialist
H2K Infosys offers structured training for cloud-based DevSecOps Certification Paths, helping professionals bridge the gap between security and cloud deployments.
Learning with H2K Infosys: Your Next Step
H2K Infosys provides DevSecOps Online Training tailored to professionals at different stages in their careers. Whether you're transitioning from DevOps, security, or cloud engineering, their hands-on labs and practical exercises make the learning journey actionable and job-ready.
With structured guidance, real-world projects, and a clear DevSecOps Certification Path, learners build confidence to tackle modern security challenges in DevOps environments. You’ll not only prepare for certifications like the Certified DevSecOps Professional but also master the skills employers are desperately seeking.
Key Takeaways
DevSecOps is essential for modern software delivery and security integration.
A Certified DevSecOps Professional is equipped to embed security into DevOps practices.
Ideal candidates include DevOps engineers, cloud architects, security professionals, developers, and IT leads.
DevSecOps Certification provides practical, job-ready skills and boosts your earning potential.
Specializations like the AWS DevSecOps Certification enhance your cloud security credentials.
The DevSecOps Certification Path includes foundational learning, hands-on practice, certification, and advanced specialization.
Conclusion: Step Into the Future of Secure Development
If you're serious about making an impact in the world of secure software delivery, becoming a Certified DevSecOps Professional is more than a smart move it’s a strategic career decision. Whether you're focused on cloud, DevOps, or cybersecurity, the right training and certification can set you apart in a competitive market.
Start your journey toward secure DevOps today build, secure, and innovate with confidence.
0 notes
Text
The Growing Importance of Software Testing Services in Modern Development
In today’s digital age, software is at the core of almost every business operation. From customer engagement platforms and eCommerce stores to banking apps and healthcare systems, software drives efficiency and growth. But with increasing complexity comes the greater risk of bugs, failures, and vulnerabilities. This is why software testing services have become a non-negotiable part of modern software development.
What Are Software Testing Services?
Software testing services involve a set of activities designed to evaluate the quality, functionality, and performance of software applications. These services help identify errors, security flaws, usability issues, and performance bottlenecks before the software reaches the end-user.
Professional software testing services ensure that the software meets both business and technical requirements. They play a crucial role in reducing development costs, preventing data breaches, and improving customer satisfaction.
Key Objectives of Software Testing
Detect Bugs and Errors Early Identifying bugs during the early stages of development helps reduce costs and avoid complex fixes later.
Ensure Functional Accuracy Functional testing ensures that all features of the application work as intended under various conditions.
Validate User Experience A well-tested application delivers a smooth and intuitive experience, increasing user retention and brand loyalty.
Maintain Performance Standards Load, stress, and performance testing confirm that the software performs well under peak usage.
Prevent Security Breaches Security testing identifies potential threats and vulnerabilities that could compromise user data or system integrity.
Types of Software Testing Services
Here are the most widely used testing services available in the industry:
1. Manual Testing
Involves human testers manually executing test cases to find bugs and usability issues. It is ideal for exploratory and user interface testing.
2. Automation Testing
Uses tools like Selenium, Cypress, and Appium to automate repetitive test cases, improving speed and accuracy.
3. Performance Testing
Checks how the application behaves under different levels of user load. It includes load testing, stress testing, and scalability testing.
4. Security Testing
Ensures the application is free from vulnerabilities and complies with standards like GDPR, HIPAA, or OWASP.
5. Regression Testing
Verifies that recent changes in the code haven't negatively impacted existing features.
6. Compatibility Testing
Assures the software functions across various devices, operating systems, and browsers.
7. API Testing
Validates the logic, performance, and security of APIs used in software architecture.
Benefits of Using Professional Software Testing Services
Cost Savings: Fixing bugs early reduces overall development and maintenance costs.
Faster Time-to-Market: Automated testing and agile QA practices speed up delivery cycles.
Better Product Quality: Reliable testing improves the end-user experience and reduces negative reviews or returns.
Risk Mitigation: Early detection of security and performance issues prevents major failures post-launch.
Scalability: As your software grows, testing ensures continued stability and performance.
Why Businesses Choose Outsourced Software Testing Services
Outsourcing QA and testing to a specialized software testing company provides access to skilled testers, advanced tools, and proven methodologies. It allows internal teams to focus on development while ensuring quality is never compromised.
Companies like Fleek IT Solutions offer flexible, scalable, and cost-effective software testing services tailored to the unique needs of startups, enterprises, and digital agencies.
Conclusion
As software becomes more central to business success, ensuring its quality is no longer optional — it’s essential. Software testing services offer a strategic advantage by ensuring reliability, performance, and security before your software goes live. Whether you’re launching a new product or updating an existing platform, investing in professional QA services can be the difference between success and failure.
0 notes
Text
Strengthening Cybersecurity with Pentest, GDPR Audits & Threat Intelligence
In today’s hyperconnected digital world, data protection and cyber resilience are no longer optional—they’re critical business priorities. As cybercriminals become more sophisticated, organizations must adopt equally advanced methods to assess risk, stay compliant, and secure both visible and hidden parts of their infrastructure.
risikomonitor.com GmbH is a trusted name in cybersecurity automation and compliance monitoring. Their integrated solutions—ranging from website pentest solutions to GDPR data protection audits, dark web threat intelligence, and comprehensive IT security audits—equip businesses to protect their data assets, maintain compliance, and anticipate potential threats before they surface.
Let’s break down how these core services work together to safeguard your business from both external and internal threats.
Website Pentest Solutions: Exposing the Unseen Vulnerabilities
Your website is your public digital front. Unfortunately, it’s also one of the most targeted assets by hackers. SQL injections, cross-site scripting, misconfigured permissions, and outdated plugins are just a few of the vulnerabilities cyber attackers exploit.
risikomonitor.com GmbH offers automated and manual website pentest solutions that:
Simulate real-world cyberattacks to find exploitable weaknesses
Test for OWASP Top 10 vulnerabilities
Analyze both application and infrastructure layers
Deliver a full risk report with severity scores and remediation steps
Integrate with CI/CD pipelines for DevSecOps workflows
These penetration tests are vital not only for security hardening but also for maintaining trust with your customers and stakeholders. Regular testing ensures that your website remains a secure gateway rather than a potential entry point for cybercriminals.
GDPR Data Protection Audit: Building Trust Through Compliance
With increasing regulations surrounding personal data, compliance is now a competitive advantage. The GDPR (General Data Protection Regulation) is one of the world’s most comprehensive data privacy laws, and failure to comply can lead to penalties, reputational damage, and lost business.
risikomonitor.com GmbH simplifies compliance with an automated GDPR data protection audit system that:
Maps personal data flows across systems
Evaluates data storage, access, and sharing policies
Identifies compliance gaps in security and consent management
Supports the creation of DPIAs (Data Protection Impact Assessments)
Prepares you for regulator audits with accurate, exportable reports
This auditing solution is especially valuable for businesses operating in or targeting the EU, as well as any enterprise that processes data of EU citizens—even if they're based outside Europe.
Dark Web Threat Intelligence: Monitoring the Invisible Threats
Many breaches go undetected not because systems aren’t monitored, but because attackers are using channels businesses aren’t watching—like the dark web. Credentials, intellectual property, source code, and customer data often appear for sale in darknet marketplaces well before companies even realize there’s been a breach.
That’s where dark web threat intelligence comes in.
risikomonitor.com GmbH leverages specialized crawlers and AI-driven analysis to:
Detect exposed login credentials and email/password dumps
Monitor forums, marketplaces, and encrypted chat channels for brand mentions
Track stolen credit card or banking data
Identify phishing domains and clones impersonating your brand
Alert your team when new threats appear
With early warnings and actionable insights, businesses can react swiftly—shutting down threats before they spread.
IT Security Audits: The Foundation of Resilience
While individual services like pentesting or dark web scanning are powerful, a full IT security audit gives organizations the bigger picture. It’s a comprehensive review of your IT infrastructure, practices, and policies to uncover systemic risks and misconfigurations.
risikomonitor.com GmbH delivers end-to-end audits covering:
Network security and firewall configurations
User access and identity management
Endpoint protection and patch management
Cloud infrastructure and SaaS risk assessments
Internal security policies and training programs
The audit results are translated into an executive summary with technical recommendations, risk scoring, and a prioritized roadmap for fixing gaps—ensuring your cybersecurity investments are strategic and effective.
Why Choose risikomonitor.com GmbH?
Unlike isolated cybersecurity vendors, risikomonitor.com GmbH provides a unified platform that combines compliance, automation, and real-time threat detection—all backed by enterprise-grade technology and scalable to businesses of all sizes.
Their integrated offerings ensure you:
Detect threats before they breach your defenses
Stay GDPR-compliant with minimal manual effort
Monitor your digital identity beyond the surface web
Audit and improve every layer of your IT infrastructure
Whether you're an eCommerce brand, SaaS company, healthcare provider, or financial firm, this solution empowers you to protect sensitive data, satisfy auditors, and reduce operational risk.
Final Thoughts
The cyber threat landscape is constantly shifting. It’s no longer enough to simply react after an incident—modern businesses must detect, prevent, and adapt in real time.
With website pentest solutions, deep GDPR data protection audit, powerful dark web threat intelligence, and thorough IT security audits, risikomonitor.com GmbH offers a 360° cybersecurity strategy for businesses ready to lead in a digital-first world.
0 notes
Text
API Security Testing 101: Protecting Your Data from Vulnerabilities

Data is vital to everything we do in the modern world. When it comes to data, we cannot ignore APIs. They act as the internet's functional backbone, helping in the smooth transfer of data between servers, apps, and devices. APIs must be protected from risks and vulnerabilities because they are used at every step. This is where security testing for APIs comes in. Ignoring this could be costly because it could compromise the privacy of sensitive user data, disrupt business operations, and harm your company's reputation with customers.
Introduction to API Security
API security testing simulates the behavior of cyber attackers. It involves sending incorrect inputs, requesting unauthorized access ,replicating injection or brute-force attacks, allowing you to identify and remediate vulnerabilities before a real hacker does it for you.
In this blog, you'll learn:
Learn why API security testing is important
A demo-ready example to help apply best practices
Tools like Keploy helps you to test your API in ease with Security
APIs present unique dangers because of the direct system-to-system access and automation-friendly interfaces APIs enable. If you understand these risks beforehand you can build an effective defense. So let’s dive into the different types of risks that APIs pose.
Broken Object-Level Authentication (BOLA)APIs can allow a malicious user to obtain user-specific information if there is no access control to every individual object by their ID (e.g., /users/123), allowing sensitive personal user information to be compromised.
Broken AuthenticationPoor token management, such as tokens that do not expire or weak credentials make it difficult to manage tokens securely. Brute force attacks are much easier in this environment.
Excessive Data Exposure / Mass AssignmentWhen an API provides responses with too much unfiltered data, it can reveal how the app works behind the scenes, allowing attackers to access sensitive data or take actions that shouldn't have been possible.
No Rate LimitsWhen an API does not limit the number of requests someone can send, it is easy to overload the API or perform brute force attacks by sending many repeated requests.
Security MisconfigurationThese common mistakes create easy routes for attackers, such as using outdated API versions, open CORS policies, and debugging endpoints.
Injection AttacksWith no input validation in place, malicious SQL, NoSQL, or script commands can be injected into the system, leading to data corruption or complete compromise of the system.
Insufficient Logging & MonitoringWithout logging requests to API endpoints or raising alerts. Threats can go unnoticed, making it hard to catch a security breach in time.
What Is API Security Testing?
API security testing is a proactive simulation of cyberattacks to your API, such as malformed inputs, brute-force attacks, and authentication bypasses, so that security weaknesses can be determined and remediated before attackers can exploit them.
This builds resilience by testing:
The codebase against known defects (via SAST)
The running API under attack (via DAST)
The API behavior under actual use (via IAST, etc.)
The resistance to logic attacks or chained exploits (via Pen Testing)
In conclusion, it is not just testing, it is a security first way of thinking that helps you ensure your API is robust, compliant, and consistent.
How API Security Testing Works

API security testing is a structured, multi-step approach designed to systematically identify and fix vulnerabilities.
1. Scope & Discovery
Identify all API endpoints internal, external, or third party and rank them based on exposure and sensitivity using OpenAPI specifications, documentation or logs.
2. Threat modeling
Identify and map attack vectors against the OWASP API Top 10, broken or lack of authentication, injection, data exposure, insufficient rate limit; etc.
3. Automated scanning
SAST: Identify injection flaws, secrets and configuration issues statically by scanning source code.
DAST: Identify runtime problems by hitting running API's with crafted requests.
4. Manual penetration testing
Testers who are professionals simulate as closely as possible real attacks, manual testing allows testers to target business logic and follow chains of vulnerabilities allowing for a much wider scope than the forms of testing discussed above.
5. Analyze & report
Go through the findings to understand severity (CVSS), reproduce findings, and list (unless stated otherwise) simple remediation steps for technical teams to work wih.
6. Fix & retest
Once patches are released:
Automated scanning
Manual Validations
How is API Security Different From General Application Security?
API security may be thought of as part of application security. However, there is a different mindset and testing methodology required for APIs. Here is a breakdown of the differences:
What They Are Protecting
Application security protects the user interface, session management, client-side attacks like XSS or CSRF.
API security protects backend services that communicate directly in between systems (without user interface interaction).
Attack Surface
Applications are limited to attacks through a UI, forms, inputs, and session-based attacks.
APIs are exposed to attacks via endpoints, payloads, headers, tokens, and sometimes even business logic directly.
Authentication and Access Control
Applications will rely on session authentication flows (cookies, login flows, etc.).
APIs rely on token-based authentication (JWT, OAuth, API keys, etc.) which introduces its risks (token leakage, absence of scope validation, absence of expiration).
Testing Methodology
Application security testing focuses on UI behavior and user flow.
API security testing focuses on sending raw HTTP requests, creating malformed payloads, bypassing authentication and abusing the business logic of the application.
Risk of Automation
Applications have a UI layer that a user has to interact with and exposes the steps of a flow.
APIs are machine friendly, provide direct access and are not limited by UI. This makes them less restrictive and increases the risk of bots and scripting abuse.
Types of API Security Tests
To ensure resilient APIs, it's important to layer different types of security testing. Each method reveals different weaknesses from vulnerability in code, runtime issues on environments etc.

What are API testing Tools and Frameworks
API testing tools and frameworks are software tools that developers use to test if their APIs are working. By sending HTTP requests to the API endpoints, it verifies the responses against the expected outcomes including status codes, response times, and data formats.
Types of API Testing Tools
CategoryWhat They DoPopular ToolsBest ForGUI-Based

API Security Testing Best Practices
API security vulnerabilities cost companies millions in breaches. Here are 5 essential practices with simple demos to secure your APIs effectively.
1. Implement Authentication & Authorization
Why it matters: 61% of data breaches involve compromised credentials.
Quick Demo - JWT Authentication:CopyCopy// Simple JWT middleware const jwt = require('jsonwebtoken'); const authenticateToken = (req, res, next) => { const token = req.headers['authorization']?.split(' ')[1]; if (!token) return res.status(401).json({ error: 'Token required' }); jwt.verify(token, process.env.JWT_SECRET, (err, user) => { if (err) return res.status(403).json({ error: 'Invalid token' }); req.user = user; next(); }); }; // Protected route app.get('/api/profile', authenticateToken, (req, res) => { res.json({ userId: req.user.id, role: req.user.role }); });
Test it:CopyCopy# Should fail without token curl http://localhost:3000/api/profile # Expected: 401 Unauthorized # Should work with valid token curl -H "Authorization: Bearer YOUR_JWT_TOKEN" http://localhost:3000/api/profile
2. Validate All Input
Why it matters: Input validation prevents 90% of injection attacks.
Quick Demo - Input Sanitization:CopyCopyconst validator = require('validator'); const validateUser = (req, res, next) => { const { email, username } = req.body; // Basic validation if (!email || !validator.isEmail(email)) { return res.status(400).json({ error: 'Valid email required' }); } if (!username || username.length < 3) { return res.status(400).json({ error: 'Username must be 3+ characters' }); } // Sanitize input req.body.email = validator.normalizeEmail(email); req.body.username = validator.escape(username); next(); }; app.post('/api/users', validateUser, (req, res) => { // Safe to process - input is validated createUser(req.body); res.json({ message: 'User created' }); });
Test it:CopyCopy# Test malicious input curl -X POST http://localhost:3000/api/users \ -H "Content-Type: application/json" \ -d '{"email":"test","username":"<script>alert(1)</script>"}' # Expected: 400 Validation error
3. Add Rate Limiting
Why it matters: Rate limiting prevents 99% of brute force attacks.
Quick Demo - Basic Rate Limiting:CopyCopyconst rateLimit = require('express-rate-limit'); // General API rate limit const apiLimiter = rateLimit({ windowMs: 15 * 60 * 1000, // 15 minutes max: 100, // 100 requests per window message: { error: 'Too many requests, try again later' } }); // Strict rate limit for sensitive endpoints const authLimiter = rateLimit({ windowMs: 15 * 60 * 1000, max: 5, // Only 5 login attempts per 15 minutes message: { error: 'Too many login attempts' } }); app.use('/api/', apiLimiter); app.use('/api/auth/', authLimiter);
Test it:CopyCopy# Test rate limiting (run multiple times quickly) for i in {1..10}; do curl http://localhost:3000/api/auth/login; done # Expected: First few succeed, then 429 Too Many Requests
4. Follow OWASP Guidelines
Why it matters: OWASP API Top 10 covers 95% of common vulnerabilities.
Quick Demo - Prevent Data Exposure:CopyCopy// BAD: Exposes sensitive data app.get('/api/users/:id', (req, res) => { const user = getUserById(req.params.id); res.json(user); // Returns password, tokens, etc. }); // GOOD: Return only necessary data app.get('/api/users/:id', authenticateToken, (req, res) => { const user = getUserById(req.params.id); // Only return safe fields const safeUser = { id: user.id, username: user.username, email: user.email, createdAt: user.createdAt }; res.json(safeUser); });
Common OWASP Issues to Test:
Broken authentication
Excessive data exposure
Lack of rate limiting
Broken access control
5. Automate Security Testing
Why it matters: Manual testing misses 70% of vulnerabilities.
Quick Demo - Basic Security Tests:CopyCopy// test/security.test.js const request = require('supertest'); const app = require('../app'); describe('API Security Tests', () => { test('should require authentication', async () => { const response = await request(app).get('/api/profile'); expect(response.status).toBe(401); }); test('should reject malicious input', async () => { const response = await request(app) .post('/api/users') .send({ username: '<script>alert(1)</script>' }); expect(response.status).toBe(400); }); test('should enforce rate limits', async () => { // Make multiple requests quickly const requests = Array(10).fill().map(() => request(app).post('/api/auth/login') ); const responses = await Promise.all(requests); const blocked = responses.some(r => r.status === 429); expect(blocked).toBe(true); }); });
Run Security Tests:CopyCopy# Add to package.json "scripts": { "test:security": "jest test/security.test.js", "security-audit": "npm audit --audit-level=high" } # Run tests npm run test:security npm run security-audit
How Keploy Makes Your API Testing More Secure
In this blog, we are discussing API security, right? What if the platform provided a way to make API testing more secure and implement all the best practices? Yes, you can now test your APIs without writing any tests and ensure 100% security. Sounds interesting?
Go to: app.keploy.io
The interesting part is, if your APIs have any authentication, you can integrate all of those through a simple, intuitive UI.

Once everything is set, Keploy API Testing agent starts creating APIs without you writing any test cases. Once the test suites are created, you can run and test them. Here’s the catch:
Concerned about privacy? No worries! You can use our local private agent for running your test suites, ensuring your data stays within your control. Whether you choose the local private agent or the hosted agent, Keploy offers flexible options to suit your needs.

To know more Keploy API Testing agent: https://keploy.io/docs/running-keploy/api-test-generator/
Related Resources
For developers looking to enhance their API security testing strategy, explore these useful guides:
Complete API Testing Guide - Fundamentals of API testing methodologies
REST Assured Alternatives - Compare 20 powerful testing tools including Keploy
No-Code API Testing - Simplify testing workflows with automation
Test Mock Data Best Practices - Create secure and realistic test data
API Performance Testing - Optimize API speed and security simultaneously
Conclusion
APIs are an important part of the digital systems we use today, but as more APIs are used, the number of attacks and security issues also increases. Securing APIs through regular testing is now a must and should be seen as a basic need. API security testing helps you find problems early, protect user data, and prevent costly attacks. Tools like Keploy make it easier by turning real traffic into useful test cases. Adding security testing to your software development process and following trusted standards like the OWASP API Top 10 lets you build safer APIs while keeping your team's speed and productivity. Good API security protects your business and builds trust with your users.
FAQs
Are all cyberattacks preventable via API security testing?API security testing helps reduce risk by identifying vulnerabilities before they can be exploited by attackers. However, it should be part of a comprehensive security plan that includes incident response and monitoring.
How often should I test my API security?Manual testing should be done every three months, while automated testing should be integrated into your CI/CD pipeline, and more extensive testing should be conducted for major API changes.
How do penetration testing and API security testing differ?API security testing automatically scans for known vulnerabilities. Penetration testing involves experts simulating real attacks to find complex vulnerabilities.
How Secure is Keploy API Testing agent?Keploy is built with security-first principles and is compliant with major industry standards:
✅ SOC 2
✅ ISO 27001
✅ GDPR
✅ HIPAA
Your data and test traffic are handled securely, with the option to run Keploy entirely within your network using our self-hosted agent or BYO LLM infrastructure.
What’s the difference between manual and automated API security testing?Automated testing (SAST, Keploy replay testing, DAST) should be done with every code change or CI build to catch issues early. Manual testing, like quarterly or post-release penetration testing, finds more complex exploits and logic errors.
0 notes