#cybersecurity penetration testing
Explore tagged Tumblr posts
Text
cybersecurity penetration testing
cybersecurity penetration testing
Cybersecurity Penetration Testing is a proactive security assessment that simulates real-world cyberattacks to identify and exploit vulnerabilities within an organization’s IT infrastructure. Its primary purpose is to evaluate how secure networks, applications, and systems are against potential hackers, helping organizations fix weaknesses before they can be exploited maliciously.
Unlike simple vulnerability scans, cybersecurity penetration testing goes deeper by mimicking attacker techniques to determine the actual risk and impact of a successful breach. It covers a wide range of targets, including web and mobile applications, internal and external networks, APIs, cloud environments, servers, and IoT devices. Ethical hackers, often certified with CEH, OSCP, or CREST, perform these tests using a mix of automated tools and manual techniques to uncover flaws such as SQL injection, cross-site scripting (XSS), broken authentication, privilege escalation, insecure configurations, and outdated software.
The testing process typically follows structured phases:
Planning and Scoping – Defining objectives, legal permissions, and systems in scope.
Reconnaissance and Scanning – Gathering information about the target and identifying vulnerabilities.
Exploitation – Attempting to gain unauthorized access, escalate privileges, or steal sensitive data.
Post-Exploitation – Assessing how deep an attacker could infiltrate the system and its impact.
Reporting and Remediation – Providing detailed findings, risk severity, and actionable remediation steps.
Cybersecurity penetration testing is aligned with global frameworks such as OWASP Top 10, NIST 800-115, MITRE ATT&CK, and PTES. It is also a mandatory requirement for compliance with PCI DSS, ISO 27001, HIPAA, and GDPR.
In conclusion, cybersecurity penetration testing is essential for strengthening an organization’s defenses, protecting sensitive data, and ensuring regulatory compliance. By uncovering vulnerabilities before hackers do, businesses can reduce the risk of costly breaches, maintain customer trust, and enhance overall cyber resilience.
0 notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
2 notes
·
View notes
Text
15 Best Free Resources for Malicious URLs and Phishing Links for Cybersecurity Testing
In today’s rapidly evolving cybersecurity landscape, having access to reliable sources of malicious URLs, phishing links, and malware samples is essential for security professionals, penetration testers, and IT administrators. Whether you’re validating your security controls, conducting security awareness training, or researching new threat vectors, accessing known malicious content in a…
#cyber threats#cybersecurity#ethical hacking#malicious URLs#malware analysis#malware samples#penetration testing#phishing detection#phishing links#security controls#security testing#security tools#security validation#threat intelligence#web security
3 notes
·
View notes
Text
finding usernames/passwords for testfire.net
background: testfire.net is a "fake" website designed for pentesters to play around with. it is NOT a real bank and no one's information is actually being stolen here. this was an assignment for a class.


first we start by logging into the admin account, username: admin and password: admin. although a general SQL injection works on this site. for the inject, password is irrelevant.
other injects that work (note that's not a quotation, that's two apostrophes):
' or ''='
' or '1' = '1
or any other statement that will always be true
on the left we see we can "Edit users"


our assignment was to find username and password pairs. you'd think you could cheekily change the passwords of existing accounts or add new accounts to fulfill this requirement, but none of these options on the admin page actually work.

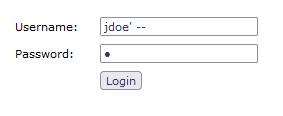
we can see the usernames of several users. since we know the username field is vulnerable to injects, we can now login to any of these without knowing the password.

this field is also vulnerable to injects. inject used:
' --
okay never mind post cancelled
i just checked the solution that my professor wanted and i shit you not its this:

these do technically work as username and password pairs. like, if you use them, you will sign in. in fact, i think you can just put anything other than a blank space for the password and it would count. but man. fuck this.
regardless, here are some actual pairs that i ended up finding. i cant quite remember how i found them, but i saw someone use "demo1234" as a password for both jdoe and jsmith, so i tested sspeed and its the same password. cant find the other ones though.
jdoe | demo1234
jsmith | demo1234
sspeed | demo1234
2 notes
·
View notes
Text
Staying Relevant: Balancing Learning and Life as an Ethical Hacker
Have you experienced burnout while trying to develop your skills and you just don't have the time to do everything? Finding balance is the key to improving your skills in a healthy way. In this article, I explore healthy habits to grow without burning out
You’ve heard it before – cybersecurity is a field that evolves at a blindingly fast pace. The tools, techniques, and technologies threatening networks transform rapidly. As an ethical hacker, your skills can become obsolete within months if you aren’t continuously upgrading your knowledge. Point #4 on our hacker roadmap deals with knowing the latest and greatest when it comes to the state of…

View On WordPress
#burnout#certifications#conference#continuous learning#Cyber Security#cybersecurity education#cybersecurity skills#Ethical Hacking#hacker skills#infosec community#leadership#learning plan#maintaining balance#microlearning#Penetration Testing#pentesting methodologies#personal development#podcast#red team operations#security news#security policies#security tools#time management#trends#vulnerability assessments#work-life balance
3 notes
·
View notes
Text
Cybersecurity Glossary
Over the course of this year I have explained to colleagues and clients who’s roles are not in Cybersecurity what certain phrases or abbreviations mean. After I while I started to drop them into a word document so I could reuse them. Then I decided to make this post so I can easily share the explanations. There are bound to be things missing, please drop a comment if I have missed something and…
View On WordPress
#anonymisation#Attack Surface#authentication#BCP#Biometrics#Botnet#Compliance#Critical Infrastructure#cybersecurity#DDoS#DFIR#Embedded software#Encryption#Firewalls#GRC#ICS#IEC62443#Industrial Control System#IR#ISO27001#Malware#mfa#NIS2#Operational Technology#OSINT#OT#OT Security#PCI DSS#Penetration test#phishing
2 notes
·
View notes
Text
How effective is Red Teaming & Pen Testing?
In today’s digital landscape, ensuring cybersecurity is crucial for organizations of all sizes. One of the key approaches to identifying vulnerabilities in security systems is through Red Teaming and Penetration Testing (Pen Testing). But how effective are these strategies?
Evaluating the Effectiveness of Red Teaming
Through the simulation of real threats, red teaming evaluates an organization's defenses. Here’s how it proves effective:
Comprehensive Security Assessment: It offers an in-depth analysis of security measures and identifies weaknesses.
Realistic Scenarios: By mimicking actual threat actors, it provides a practical understanding of potential risks.
Team Improvement: The exercise fosters collaboration among security teams, enhancing their response strategies.
Assessing the Impact of Penetration Testing
Pen testing focuses on identifying vulnerabilities through controlled attacks. Its effectiveness can be summarized by:
Finding Weak Points: It draws attention to particular weaknesses that an attacker could take advantage of.
Prioritizing Threats: Helps organizations focus on critical areas needing protection.
Regulatory Compliance: Frequently necessary to adhere to rules and industry norms.
Both red teaming and pen testing play vital roles in strengthening an organization’s cybersecurity posture. By proactively identifying vulnerabilities, organizations can better defend against potential threats and ensure a safer digital environment.
0 notes
Text
Penetration testing isn't just about ethical hacking—it's a structured process that helps businesses discover and fix vulnerabilities before real attackers exploit them.
In cybersecurity, the penetration testing lifecycle is typically divided into five essential phases:
Planning & Reconnaissance
Scanning
Gaining Access
Maintaining Access
Analysis & Reporting
Each stage plays a vital role in identifying potential security gaps, especially for businesses in finance, healthcare, and technology sectors.
If you're managing sensitive data or infrastructure, understanding these phases helps you assess risk better and strengthen your defenses.
Dive deeper into the complete breakdown here: Read the Full Guide
1 note
·
View note
Text
The Artificial Intelligence Role in Penetration Testing and Cyber Defense
Introduction
The internet is growing at a pace never seen before, and cyber attacks are also developing in tandem. Companies all over the world are investing in online cyber security training so that experts are equipped with the tools to protect their networks. Penetration testing, the most critical element of cybersecurity, is a preventive strategy to find out vulnerabilities before the attackers can exploit them. With the introduction of artificial intelligence (AI), penetration testing and cyber defense mechanisms are transforming and becoming better.
This is an article on how AI is revolutionizing penetration testing and cybersecurity, its advantages, disadvantages, and future directions. Understanding what AI is doing in cybersecurity will enable cybersecurity experts to utilize AI-powered tools to further fortify their defenses against constantly changing cyberattacks.
The Growing Importance of Penetration Testing in Cybersecurity
Penetration testing, or ethical hacking, involves the simulation of cyberattacks to test the security stance of a company. It's a common practice in online cyber security courses as well as cybersecurity training since it enables experts to identify vulnerabilities and implement robust countermeasures.
Legacy methods of penetration testing put a great reliance on human resources, which is labor and time-intensive. Ethical hackers have to scan manually for vulnerabilities, assess probable exploits, and emulate attacks. Although the process works, it is normally hindered by human mistake and the sheer amount of potential threats.
The Role of AI in Cybersecurity and Penetration Testing
1. Automated Threat Detection
AI security systems are capable of scanning huge volumes of data in real-time to detect vulnerabilities and potential threats. AI applies machine learning algorithms to detect patterns and anomalies that are indicative of security breaches. Automated threat detection reduces the process significantly, obviating the time required to identify and respond to cyber threats, thereby enhancing the overall security standing of an organization.
2. AI-Based Vulnerability Scanning
Artificial intelligence-based vulnerability scanners may be employed to scan networks, systems, and applications on a continuous basis to identify security vulnerabilities. These scanners employ machine learning to enhance precision, minimize false positives, and initiate only real threats for further investigation. This feature is especially useful for online cyber security training companies, as it enables students to gain hands-on experience in vulnerability scanning based on real-life scenarios.
3. Improved Threat Intelligence
Threat intelligence is an essential element of cyber security. AI is capable of collecting and analyzing information from various sources, such as dark web bulletin boards, threat repositories, and network logs, and providing actionable insights. Organizations can remain proactive against new threats and modify their security strategy accordingly with AI-powered cybersecurity.
4. Ethical Hacking with AI
Ethical hacking demands strong technical expertise and skill, which can be supplemented using AI tools. AI may automate reconnaissance, exploit development, and post-exploitation analysis for ethical hackers. With the addition of AI security tools in ethical hacking, penetration testers can discover vulnerabilities more effectively and create better mitigation plans.
5. Real-Time Incident Response
One of the strongest advantages of AI in cybersecurity is its real-time incident response capability. AI security systems can detect and respond to threats before they can do extensive harm. By analyzing the patterns of attacks and predicting future threats, AI enhances the ability of an organization to prevent cyber incidents proactively.
Benefits of AI Implementation in Cybersecurity Defense and Training
Increased Efficiency and Accuracy
Artificial intelligence -based cybersecurity solutions can process massive amounts of data at unprecedented rates, allowing threat detection and mitigation at an accelerated pace. This efficiency decreases the burden on cybersecurity experts so that they can concentrate on strategic decision-making and incident management.
Cost-Effectiveness
Penetration testing and cyber defense procedures can be greatly minimized in operational costs through automating them using AI. Companies can use their resources more efficiently, making their cybersecurity staff available for high-priority work.
Adaptive Learning
AI security systems learn from emerging threats and adjust their defenses in response. This ability to learn by themselves means that cybersecurity defenses stay current, even against changing cyber threats.
Increased Hands-On Training
Cybersecurity training sessions can incorporate AI-based simulation platforms to offer practical experience in penetration testing and cyber defense. These platforms use actual attack scenarios to enable students to gain practical experience and prepare for actual cybersecurity challenges.
Incorporating AI in Cyber Defense: Challenges
False Positives and False Negatives
While AI improves the efficiency of threat detection, it is not infallible. AI-powered security software sometimes triggers false alarms or fails to detect sophisticated cyber attacks. AI models need continuous monitoring and adjustment to make them more accurate.
Dependence on Data Quality
AI systems depend on large data sets in order to operate efficiently. Outdated or incorrect data can undermine the efficacy of AI-based security systems. Organizations have to make sure that their AI models are trained on current and extensive cybersecurity data sets.
Ethical and Legal Issues
The use of AI in penetration testing and cyber protection is regulated by legal and moral issues. The organizations must ensure that AI-based penetration testing solutions are used responsibly and comply with the regulatory requirements.
Future Trends in AI-Powered Cybersecurity
With advancing AI technology, so will its application in cybersecurity. Some of the future trends are:
AI-Powered Autonomous Security Systems: Emerging cybersecurity systems might utilize completely autonomous AI systems capable of identifying, analyzing, and eliminating threats on their own without any human interaction.
AI-Powered Security Orchestration:AI will be utilized to automate and orchestrate security solutions so that processes of threat response are made more efficient.
AI-Augmented Cybersecurity Training: AI-enabled virtual labs and simulation platforms will be a critical part of cybersecurity training programs, offering students interactive hands-on training.
Quantum Computing and AI Security: With the growth of quantum computing, AI will be at the center of the creation of quantum-resistant cybersecurity regulations.
Conclusion
The use of AI for penetration testing and cyber defense is transforming the landscape of cybersecurity. AI security tools improve threat detection, automate vulnerability scanning, and enhance incident response. Organisations are better positioned to enhance their cybersecurity positioning and remain ahead of new threats with the use of AI security tools.
For working professionals who want to enhance their cybersecurity skills, one must take online cyber security training. Online platforms such as Guruface provide detailed cybersecurity training courses, teaching and practical experience that is necessary to excel in this profession. Since cyber attacks are evolving continuously, investment in cybersecurity training and ethical hacking courses is essential so that one has a strong defense system against cyber attacks.
0 notes
Text
Cyber Security Services Company | Data Security Solutions

In today’s fast-paced digital world, businesses increasingly rely on technology to store, process, and transmit sensitive data. As companies across industries harness the power of the internet, the need for robust cybersecurity services has never been more crucial. Data breaches and cyberattacks are growing threats from small startups to large corporations that can have devastating consequences. That’s where a cybersecurity company specializing in data protection services and cybersecurity management comes into play.
This blog explores the importance of cybersecurity management, the types of services offered by a cybersecurity services company, and how data protection services and endpoint security services can help businesses protect their sensitive information.
Understanding the Growing Importance of Cybersecurity
The digital transformation that businesses have undergone in recent years has revolutionized operations, providing significant benefits like improved efficiency, better customer engagement, and more streamlined processes. However, this transformation has also opened new doors for cybercriminals who exploit vulnerabilities in systems and networks to steal data, launch attacks, and disrupt operations.
With data breaches and cyberattacks on the rise, organizations must safeguard sensitive information from unauthorized access, manipulation, and theft. Whether it’s customer data, intellectual property, or financial records, securing these assets is paramount to maintaining trust, compliance with regulations, and protecting brand reputation.
Cybersecurity solutions providers play a key role in defending organizations from these threats. Cybersecurity isn’t just a technical need—it’s a business priority that can help prevent costly disruptions, legal ramifications, and loss of customer confidence. This is where the role of a cybersecurity consulting firm becomes indispensable.
What Is a Cybersecurity Services Company?
A cybersecurity services company specializes in identifying, mitigating, and preventing cyber threats. They provide tailored solutions to ensure businesses’ information and infrastructure are well-protected from a wide range of security risks. These companies are essential partners in safeguarding businesses from cyberattacks and ensuring the security of sensitive data and systems.
Key Services Provided by a Cybersecurity Services Company

Cybersecurity companies offer a range of services designed to safeguard businesses from evolving threats. These services include:
Threat Detection & Prevention Services: Cybersecurity companies deploy advanced monitoring tools and techniques to detect vulnerabilities, anomalous activities, and potential threats before they cause harm. This includes setting up firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Risk Management: Cybersecurity firms assess vulnerabilities and design strategies to safeguard businesses from both internal and external threats. A cyber risk management company helps ensure that businesses are prepared for any potential cyber risks.
Cybersecurity Audits & Assessments: Regular security audits and penetration testing are vital for identifying weaknesses in a company’s infrastructure. These audits ensure no part of the system remains unprotected.
Compliance Support: For businesses in regulated industries, cybersecurity compliance services help ensure adherence to standards like GDPR, HIPAA, and PCI DSS. Companies in these industries can also benefit from IT security services companies that provide guidance and support for meeting compliance requirements.
Incident Response & Disaster Recovery: Even with robust security measures, breaches can still occur. Incident response services help businesses respond quickly and effectively to limit damage. Additionally, cybersecurity audit services and vulnerability assessment companies help identify and prevent potential attacks before they materialize.
Employee Training & Awareness: Cybersecurity management companies often provide training programs to raise awareness about phishing, password hygiene, and safe online behavior, reducing human error and improving security.
Types of Data Security Solutions Offered by Cybersecurity Companies

At the core of every cybersecurity service is data protection. Cybersecurity solutions providers offer several key solutions to help businesses secure their information:
Encryption: Encryption ensures that even if data is accessed by cybercriminals, it remains unreadable without the decryption key. Cloud security companies offer encryption solutions to protect data stored in the cloud, safeguarding sensitive information during transit and while at rest.
Access Control & Authentication: Multi-factor authentication (MFA) and role-based access control (RBAC) are implemented to ensure only authorized personnel can access sensitive systems.
Data Loss Prevention (DLP): Data protection services monitor data transfers and emails to prevent unauthorized sharing or leakage of confidential information.
Firewalls & Network Security: Firewalls act as the first line of defense by filtering traffic and blocking harmful activities. Network security services providers ensure that your network is properly configured with firewalls, VPNs, and network segmentation to protect data from external attacks.
Backup & Disaster Recovery: A comprehensive backup and recovery plan ensures that lost or compromised data can be restored with minimal disruption to business operations. Cloud security companies play a key role in providing reliable cloud-based backup and recovery services.
Endpoint Security: With more employees working remotely, endpoint security services are becoming essential. Cybersecurity firms implement solutions to protect mobile devices, laptops, and tablets from threats.
Why Partner with a Cybersecurity Services Company?
Businesses of all sizes can benefit from the specialized expertise of a cybersecurity consulting firm. Here are some reasons why partnering with one is essential:
Expertise and Experience
Cybersecurity is a complex field requiring in-depth knowledge of emerging threats and security solutions. A cybersecurity services company brings years of experience and expertise to the table, ensuring best practices and cutting-edge tools are used to protect your data.
Cost Efficiency
Building an in-house cybersecurity team can be costly. By outsourcing to a cybersecurity solutions provider, businesses gain access to expert resources and advanced technologies without the need to invest in full-time staff.
Proactive Protection
Rather than waiting for a breach to occur, a cybersecurity management company helps you adopt a proactive approach by identifying and neutralizing potential threats before they can impact your business.
Regulatory Compliance
Staying compliant with regulations like GDPR, HIPAA, and CCPA can be challenging. A cybersecurity services company ensures your business complies with relevant data protection laws, avoiding legal complications and fines. These companies provide cybersecurity compliance services to meet the highest standards of data protection.
Business Continuity
Cybersecurity services also encompass disaster recovery planning, ensuring that your business can continue to operate smoothly after a cyber attack or natural disaster. Security operations center services ensure continuous monitoring, offering peace of mind that any security breaches are quickly detected and neutralized.
Conclusion: Protect Your Business with a Cybersecurity Services Company
As cyber threats continue to evolve, businesses must take proactive steps to protect their sensitive data and maintain customer trust. Partnering with a reputable cybersecurity consulting firm ensures that you have the right tools, expertise, and strategies in place to prevent cyberattacks, secure your data, and maintain regulatory compliance.
Whether it’s through penetration testing, endpoint security services, or incident response services, a cybersecurity services company plays a crucial role in keeping your data safe and your business running smoothly.
Investing in cybersecurity solutions today can help prevent significant financial and reputational damage in the future. Don't wait until it's too late—reach out to a trusted cybersecurity services company today to protect your data and your business's future.
#Cyber Security Services Company | Data Security Solutions#Cybersecurity Management Company#Managed Cyber Security Services#Cyber Security Company#Cyber Security Services#Endpoint Security Services#Cybersecurity Solutions Provider#Cyber Security Consulting Firm#Network Security Services#Cybersecurity Audit Services#IT Security Services Company#Cloud Security Company#Data Protection Services#Cybersecurity Compliance Services#Security Operations Center Services#Threat Detection Services#Penetration Testing Company#Incident Response Services#Vulnerability Assessment Company#Cyber Risk Management Company#Information Security Services
0 notes
Text
VirtualBox Guest Additions on Kali Linux Install Guide 2025
Installing VirtualBox Guest Additions on Kali Linux packages correctly is crucial for optimal virtual machine performance. Many users struggle with fullscreen display issues, shared folders, and clipboard functionality when running Kali Linux on VirtualBox. This comprehensive guide provides the definitive method for installing these essential packages in 2025. Check the 256MB Video memory and 4GB…
0 notes
Text
Why Cybersecurity Certifications Like ISO 27001 & SOC 2 Matter Today
Cybersecurity threats are growing—fast. Whether you're a startup or an enterprise, frameworks like ISO 27001 and SOC 2 can be the difference between peace of mind and panic.
At Cyber Guardians, we help businesses navigate: 🔐 What VAPT actually involves 💰 VAPT cost in India and what to expect ✅ How to get SOC 2 certification 📈 Getting ISO 27001 certified — minus the confusion
We’ve been there. Let us help you get compliant with confidence.
#VAPT companies in India#SOC 2 certification#ISO 27001 cost#cybersecurity#penetration testing#data compliance#infosec
0 notes
Text
Ethical Hacking Tools: What’s Legal and Free?
Curious about ethical hacking but worried you might trip over legal lines or blow your budget? You’re not alone. With cybersecurity threats rising every day, ethical hackers—also known as white-hat hackers—are becoming heroes in hoodies. But to do it right, you need the proper tools: ones that are legal, effective, and preferably free. Let’s dive into the best ethical hacking tools you can use…
#ethical hacking#free cybersecurity tools#legal hacking software#penetration testing#white-hat hacking
0 notes
Text
Coding and Scripting for Beginner Hackers
Learning to code and write scripts is a crucial skill for getting into ethical hacking and cybersecurity. Scripting allows you to automate repetitive tasks, develop your own custom tools, analyze data, and program everything from small hacking tools to machine learning models. Understanding and knowing how to code in different languages can be extremely useful when doing deep dives into malware…

View On WordPress
#Cyber Security#cybersecurity careers#Ethical Hacking#hacer certifications#hacking for beginners#hacking guide#hacking homelab#infosec#learn to code#learn to hack#Penetration Testing#Pentesting
4 notes
·
View notes
Text
Penetration Testing New Techniques for Next-Gen Threats in 2025

Cybersecurity remains where data is. The research says almost 359 million enterprises were established globally in 2023. With expansion of companies, they must now focus on the ultimate goal of protecting their assets. With the constant cyber threats evolution, companies are required to stay ahead of them to protect their data, systems, and reputation.
But how prepared are you for the impending cyberattack? It is alarming that, as of February 2024, the average cost of a data breach increased from $4.45 million to $4.88 million globally.
This enormous figure emphasizes how crucial proactive penetration testing (pen testing) procedures are for all companies.
In this article, we will assess how penetration testing is evolving to keep pace with next-gen attacks and turn organizations safe for 2025.
Let’s discuss how advanced penetration testing techniques and trends in 2025 can neutralize new-gen threats.
How is penetration testing defined, and what is VAPT?
Vulnerability assessment and penetration testing are cybersecurity tactics created especially for organizations that identify flaws and address them before malicious attackers may use them. First, the vulnerability assessment thoroughly overviews a company’s security holes or infrastructure deficiencies.
Penetration testing takes this step forward to simulate real attacks and estimate the strength of security solutions in dealing with these dangers.
Pen-testing is an ethical hacking process that uses the same methods a malicious hacker uses to determine security loopholes. It finds significant vulnerabilities, identifies their effect, and suggests actions to protect systems and data against breaches.
Why there is a dire need for penetration testing
Because cyber threats are getting more complex, organizations need to act now rather than wait for a breach to happen. Research indicates that over 75% of businesses have been the target of a cyberattack, and phishing remains the most popular way for hackers to get in.
The extent of these attacks is expanding, and data breaches have a sharp increase in financial impact—the average cost is already in the millions.

New techniques and trends of penetration testing in 2025

· AI-Powered penetration testing:
Artificial intelligence and penetration testing technologies are becoming more integrated. AI is capable of real-time analysis of massive data sets, pattern recognition, and attack vector prediction. Therefore, security teams can proactively fix vulnerabilities before their exploitation.
· Cloud penetration testing:
With the increase of cloud computing in business processes, cloud environment testing vulnerabilities are inevitable. Cloud application and network penetration testing ensure that cloud applications and networks have security and services to prevent new threats to cloud infrastructure.
· Social engineering simulations:
Online attackers are increasingly using phishing, spear-phishing, and other social engineering techniques as their primary access points. More social engineering simulations, such fictitious phishing operations, will be added to penetration testing in the future years to gauge how vulnerable and ready staff members are for these strategies.
· Zero-trust architecture testing:
The Zero-Trust model has adopted the default assumption that no individual, whether inside or outside the network, can be trusted as businesses move toward this assumption. By granting access to only verified people and devices, penetration testers will focus on evaluating how well Zero-Trust networks operate.
· Automated penetration testing:
Automating recurring security processes, such as evaluating setups and scanning for vulnerabilities, has become popular. Although this method offers scalable operations and faster processes than others, it is still a technological innovation that will help achieve complete coverage.
· DevSecOps:
DevSecOps incorporates security into the software development lifecycle by automating security procedures from design to deployment. Its foundation is secure code and ongoing security testing across the whole development cycle, which allows for the identification of vulnerabilities early in the application’s lifecycle and improves its security posture.
· IoT security testing:
As the number of connected devices rises, IoT security assessment becomes essential over time. Finding vulnerabilities in hardware, software, and communication features like Wi-Fi and Bluetooth is essential. IoT penetration testing helps prevent attacks on vulnerable devices, unauthorized access, and data breaches.
· GRC, SIEM, and Help Desk System Integrations:
Security operations can improve response times and automate procedures by integrating help desk systems, governance, risk management, compliance (GRC), and security information and event management (SIEM). When vulnerabilities are found, alerts are sent to the appropriate teams, facilitating quicker remediation and better risk management in general.
What are the Next-Gen threats coming up in 2025?
Cybersecurity is still a shifting target, and several next-generation threats are expected to surface, bringing with them new testing techniques. These consist of:
Ransomware 2.0: With advanced, multidimensional extortion techniques that target different industries, ransomware will continue to develop from its traditional form. A ransomware assault can potentially shut down an enterprise, demand a payment, and cause massive damage. The main goal of penetration testing should be identifying ransomware vulnerabilities in on-premises or cloud environments.
Infostealer malware: In a hybrid system, compromised identities and info-stealing malware pose the greatest risk. Web3 and cryptocurrency organizations will also be the best places to attack. Democratized cyber capabilities allow attackers with limited expertise to undertake highly complex hacks.
Deepfake technology: As AI and deepfakes advance, attackers might use audio or video resembling lifelike representations of executives or employees to defraud businesses out of confidential information. Penetration testing requires that a test firm assess an organization’s defenses against deepfake-powered social engineering attacks.
IoT and smart devices: The IoT’s attack surface is growing, and smart devices, wearable technology, and connected infrastructure must be tested as part of a penetration test because each could be compromised if not appropriately secured.
AI-driven attacks: AI helps hackers scale and automate attacks that make exploiting and evading vulnerabilities easier. To protect against AI-powered attacks, penetration testing must keep pace with automated, machine-learning-enabled attack techniques by 2025.
Limitations and challenges to traditional penetration testing
Even if it is successful, traditional penetration testing has several drawbacks in the current cybersecurity environment:
Limited scope: Standard penetration testing mainly concentrates on pre-defined test cases so that it may overlook numerous new or complex vulnerabilities.
Constraints on resources: Cutting-edge attack techniques are more challenging to identify since traditional testing methods cannot keep up with the ever-evolving cyber threat.
Human error: penetration testers are only as good as their equipment and expertise. Errors or insufficient testing may have identified vulnerabilities or led to incorrect conclusions.
Best practices of penetration testing for Next-Gen threats
In keeping with the current year 2025, businesses must create and adhere to these best practices for penetration testing for next-generation threats:
Continuous testing: Penetration testing cannot be done just once. Continuous testing is necessary for organizations to detect vulnerabilities as soon as they appear and take immediate action.
Comprehensive coverage: The penetration testing scope should include mobile apps, cloud environments, and IoT devices, among other contemporary technologies typically disregarded in conventional penetration testing.
Pay attention to human elements: Simulated phishing and other assaults should be used to assess employees’ readiness because social engineering is still one of the most common attack vectors.
Integration with response to incidents: An organization’s incident response strategy should be closely linked to penetration testing. It allows businesses to react quickly to the discovery of new vulnerabilities.
Post-test remediation: After conducting penetration testing, companies need to strengthen security procedures, patch vulnerabilities, and build strong defenses in general.
FAQs
How often should organizations execute penetration testing?
Organizations should do penetration testing at least once a year, but more frequently if there are significant changes to the infrastructure or if important systems are impacted.
How much does penetration testing cost?
The cost of penetration testing can vary from several thousand to ten thousand dollars for more extensive tests, depending on the scope, complexity, challenges, and frequency.
Does penetration testing make a system 100% secure?
Penetration testing reduces the probability of hacking breaches, but total protection is not guaranteed, as newly discovered vulnerabilities can emerge after scanning in real-time.
How should you choose the right VAPT service provider?
To choose the right VAPT service provider, you should research on the VAPT service providers and assess the best features they serve you for your requirements.
Conclusion
To conclude, businesses now need to use next-generation penetration testing techniques to stay ahead of cyber threats before they trap them with their complexities.
In 2025, penetration testing will be essential for protecting against new threats due to AI-driven tools, thorough testing for modern technology, and continuous development. Organizations can ensure they are prepared to handle future cybersecurity challenges by implementing best practices and exercising initiative with ESDS SOC as a service.
For more information and knowledge on what ESDS can do for your business, you can visit here.
0 notes
Text
What Are Top 3 Vulnerability Management Metrics to Measure in 2025
In today’s rapidly evolving cybersecurity landscape, staying ahead of potential threats is essential. Companies face a relentless onslaught of security vulnerabilities, and effectively managing these vulnerabilities has become critical for safeguarding data and maintaining regulatory compliance. One of the primary methods to assess the security posture of any organization is through vulnerability management and penetration testing. In 2024, certain key metrics have emerged as essential for effectively managing vulnerabilities, aiding businesses in minimizing risks while optimizing their security strategy.

This article will explore the top three vulnerability management metrics to measure in 2024, focusing on their significance in shaping a robust security program, and highlighting how penetration testing plays an integral role.
1. Vulnerability Detection Rate
The Vulnerability Detection Rate is a metric that reflects how effectively your organization identifies security vulnerabilities within its IT infrastructure. A higher detection rate indicates that the organization has robust tools and processes in place for continuous monitoring and assessment, which is crucial for early-stage vulnerability management.
Why It Matters: In 2024, the growing sophistication of cyber threats makes the Vulnerability Detection Rate a key performance indicator (KPI) for cybersecurity teams. An accurate and high detection rate allows teams to discover potential vulnerabilities before they are exploited. It also helps organizations quantify the effectiveness of their scanning tools, Vulnerability Scanning protocols, and penetration testing procedures.
How to Measure It: The Vulnerability Detection Rate is typically calculated by dividing the number of detected vulnerabilities by the total vulnerabilities present, which can be estimated based on past data and testing results. Organizations should strive for real-time detection capabilities using tools that integrate vulnerability management with penetration testing solutions. This hybrid approach allows for both automated and manual detection of weaknesses across endpoints, applications, and networks.
Penetration Testing's Role: Penetration testing acts as a simulated attack on the system, testing the detection capabilities of an organization. Conducting regular penetration tests helps verify that vulnerabilities are detected accurately and promptly, which can reveal any gaps in detection mechanisms. A comprehensive penetration test offers insights into vulnerabilities that automated tools may overlook, helping cybersecurity teams to refine their detection tools and strategies.
2. Mean Time to Remediation (MTTR)
Mean Time to Remediation (MTTR) is a crucial metric for understanding the efficiency of an organization’s response to identified vulnerabilities. MTTR calculates the average time taken to fix a vulnerability after its detection. Keeping this metric low is essential for preventing the exploitation of vulnerabilities and ensuring that identified threats do not remain in the system long enough to cause harm.
Why It Matters: The faster an organization remediates a vulnerability, the less time attackers have to exploit it. With the increasing rate of zero-day vulnerabilities in 2024, cybersecurity teams must act quickly once vulnerabilities are identified. A short MTTR not only indicates an agile response capability but also helps in meeting regulatory requirements and reducing potential financial or reputational damage.
How to Measure It: To measure MTTR, calculate the time between when a vulnerability is identified and when it is resolved. Divide the total remediation time across all vulnerabilities by the number of resolved vulnerabilities within a specific timeframe. It is best practice to track MTTR by severity level (e.g., high, medium, low), as high-risk vulnerabilities should generally have a shorter MTTR than low-risk ones.
Penetration Testing's Role: Penetration testing supports MTTR by identifying specific weaknesses in systems and applications, thereby guiding prioritized remediation efforts. It helps highlight vulnerabilities that pose the greatest risk, allowing teams to allocate resources effectively and improve response times. When Penetration Testing is conducted regularly, it can also reveal recurring vulnerabilities, helping teams streamline their remediation processes and reduce MTTR.
3. Vulnerability Reopen Rate
The Vulnerability Reopen Rate metric measures the frequency at which previously remediated vulnerabilities reappear, indicating that previous fixes may have been insufficient or temporary. A high reopen rate suggests that there are issues within the patch management or remediation processes, or that vulnerabilities have returned due to configuration changes, software updates, or inadequate fixes.
Why It Matters: In 2024, complex infrastructures and third-party dependencies mean that vulnerabilities can recur due to software updates or overlooked configurations. A high Vulnerability Reopen Rate can indicate a need for improved patching practices, better configuration management, or more thorough penetration testing to verify that vulnerabilities are completely resolved. Reducing the reopen rate not only boosts security posture but also conserves resources by minimizing repetitive work for security teams.
How to Measure It: Calculate the Vulnerability Reopen Rate by dividing the number of vulnerabilities that have reappeared after initial remediation by the total number of vulnerabilities resolved over a given period. Tracking this metric over time helps organizations understand the consistency and effectiveness of their remediation efforts.
Penetration Testing's Role: Penetration testing is critical in validating that vulnerabilities have been properly remediated. After a vulnerability is patched or mitigated, conducting a follow-up penetration test ensures that the issue has been fully addressed. This practice not only helps to keep the Vulnerability Reopen Rate low but also verifies that patches have not inadvertently created new vulnerabilities. Regular penetration tests are instrumental in keeping this metric under control by providing an extra layer of verification and reducing the chances of vulnerability reoccurrence.
The Role of Penetration Testing in Vulnerability Management Metrics
Incorporating penetration testing into vulnerability management goes beyond simply identifying security gaps; it enhances the entire vulnerability management process. Penetration testing, when conducted consistently, provides a real-world perspective on the security posture of an organization, helping cybersecurity teams to accurately assess and improve each metric. Here’s how:
Improving Detection Accuracy: Penetration testing helps assess the accuracy and coverage of detection tools, enabling organizations to fine-tune their scanning and monitoring systems.
Prioritizing Remediation Efforts: By highlighting high-risk vulnerabilities, penetration tests help in prioritizing and reducing MTTR, as they show which areas need immediate attention and streamline the remediation process.
Ensuring Lasting Remediation: Penetration testing verifies that vulnerabilities have been remediated effectively, which in turn helps in maintaining a low Vulnerability Reopen Rate.
Conclusion
In 2024, vulnerability management metrics like Vulnerability Detection Rate, Mean Time to Remediation (MTTR), and Vulnerability Reopen Rate will be pivotal in measuring and improving an organization’s cybersecurity resilience. Penetration testing plays an indispensable role in supporting these metrics, offering a comprehensive approach to identifying, prioritizing, and validating remediation efforts. By focusing on these metrics and integrating regular penetration testing, organizations can bolster their security posture and reduce their risk of cyber-attacks. Emphasizing these metrics helps companies build a proactive and effective vulnerability management strategy, making 2024 a year of fortified defenses against an evolving threat landscape.
#Vulnerability management metrics#Penetration testing#Cybersecurity resilience#Vulnerability Detection Rate#Mean Time to Remediation (MTTR)#Vulnerability Reopen Rate#Cyber threats#Vulnerability scanning tools#Security posture#IT infrastructure vulnerabilities
0 notes