#networking software
Explore tagged Tumblr posts
Text

USA 1993
#USA1993#INNER CIRCLE SOFTWARE#NOVALINK#RPG#NETWORK#MACINTOSH#IBM#AMIGA#ATARIst#LEGENDS OF FUTURE PAST
34 notes
·
View notes
Text

You've got me craving with outrageous adoration!
I can feel a shifting, surely something new emerging!
#the murderbot diaries#murderbot#murderbot 2.0#targetcontrolsystem#tmd network effect#software ghost#arts#when you run out of things to say about a drawing song lyrics will always be there for you!!!!!#for the record adacol1 is also in this picture but#i don’t really see a point in tagging it
163 notes
·
View notes
Text

#doom#doom 2#doom fanart#grim adventures of billy and mandy#billy and mandy#cartoon network#video game fanart#id software#bethesda#doom game#doom guy#quake#postal#postal dude#duke nukem#blood 1997#serious sam#hexan#heretic#doom art#boomer shooter#90s fps#90s games#doom ii#doom 2 hell on earth
19 notes
·
View notes
Text
Network switches
What’s a network switch ?
A switch is a device used in computer networks to connect multiple devices together within a single local area network (LAN). Its main role is to facilitate communication between different connected devices, such as computers, printers, servers, IP phones, etc.
It is a mini-computer which is made up of RAM, ROM, flash RAM, NVRAM, a microprocessor, connectivity ports and even an operating system.

RAM
RAM (Random Access Memory) contains the current configuration of the switch and temporarily stores the MAC address table, which is then processed by the microprocessor.
Microprocessor
The microprocessor is the heart of the switch, responsible for data processing, including switching and creating links between multiple devices.
External memories
External memories, such as flash RAM, ROM, and NVRAM (Non-Volatile RAM), store configuration files , different versions of the IOS , etc ...
Ports
The switch ports are the communication interfaces of the switch. There are several of them, generally 24 for a Cisco switch. Each port is associated with an LED which indicates its status and activity.

How does it work ?
Now how does a switch work to transfer information from one machine to another?
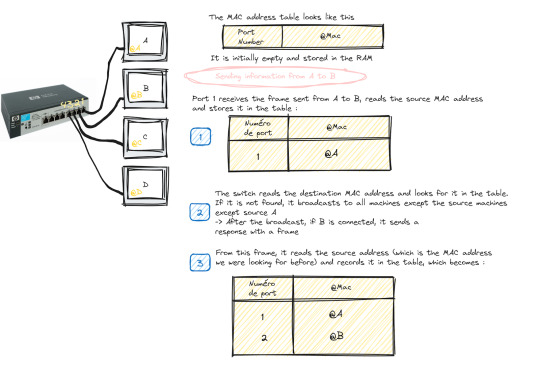
Suppose we have 4 machines: A, B, C and D connected to our switch in ports 1, 2, 3 and 4 as follows:

The switch only works with MAC addresses , so basically we have an empty MAC address table stored in RAM as soon as the switch starts up which looks like this :

Transmitting data from machine A to machine B happens in the following steps:
Machine A sends a frame to machine B
Once this frame arrives at port 1 (which is the one linked to A), the switch reads the source MAC address and stores it in the MAC address table
The switch reads the destination MAC address and looks for it in the table, if it is not in the table, it broadcasts to all the active machines connected to the switch except the source one.
If the port linked to the machine we want is active, it sends a response frame from which the switch reads the MAC address we were looking for (@B)
Once done, it records the MAC address of B in the table.

This process repeats until the switch reaches what is called "MAC address table stability", that is to say it knows all the MAC addresses of the connected machines and has no more need to broadcast.
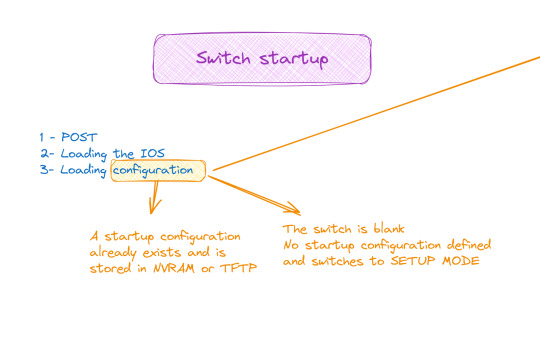
Starting and configuring a switch
When it comes to booting a switch, the process is similar to that of a traditional computer system:
POST (Power-On Self Test): The switch performs proper functioning tests on all hardware.
Loading IOS (Internetwork Operating System): The switch operating system is loaded.
Loading the configuration. At this stage we have two cases:
Either the switch already has a startup configuration defined and stored in NVRAM
Either the switch is blank and it is up to us to define the startup configuration when it goes to setup mode
Switch configuration

The configuration of a switch is done through different modes, such as user mode, privileged mode and global configuration mode, which allows access to specific configuration modes, such as interface mode, routing mode, line mode, etc.
And to do all this of course you must first connect the switch with the machine via the console cable and open a terminal emulator
💡 It should be noted that the only machine that can configure the switch is the one connected to it by a console cable, the others are only hosts.
#software#network switches#codeblr#code#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code
99 notes
·
View notes
Text

264 notes
·
View notes
Text

Image to Model
A review of software tools used in neuroscience to reconstruct microscope images of lab-grown neurons into neural system network models to better understand cell connectivities and organisation
Read the published review article here
Image from work by Cassandra Hoffmann and colleagues
Systems Neuroscience Lab, Melbourne Neuropsychiatry Centre, Department of Psychiatry, The University of Melbourne, Parkville, Australia
Image originally published with a Creative Commons Attribution 4.0 International (CC BY 4.0)
Published in Communications Biology, May 2024
You can also follow BPoD on Instagram, Twitter and Facebook
23 notes
·
View notes
Text
one thing i'll never understand is why my boss has me sharing an office with our software engineer when i'm a network engineer because i was gone for a week and now that i'm back all my networks are down
and i couldn't bring them back up and i was kinda despairing about it because i was sure my configs were right n all so i asked around if anyone changed them and like as it turns out the guy i'm sharing my office with unplugged all my patch cables so ofc nothing's gonna work
and like i get it i'm running them from the server room and some switches in different rooms to our office and they're covering our floor and they're a bit of a hazard
what i don't get is why i don't share the office with our other network engineer. yk the one office that's right next to the server room and has a couple more switches plastered about?
#i feel like such a fool every time#scattering my silly little cat cables all over the floor#asking our software engineer if 🥺👉👈 there's space for another rj45#walking across the entire office to ask the other network engineer about a project#like... pls... what is this...
11 notes
·
View notes
Text
I completely understand it was for story reasons, but kid me was SO pissed that you weren't able to play as all ten aliens in Ben 10: Protector of Earth.
Like, they could've had you take down that giant robot at the beginning by using Grey Matter and messing it up from the inside, included a few more boss battles across the map so you could gradually unlock the other aliens, had an underwater boss that you needed to defeat with Ripjaws. So much potential.
Maybe once you complete the game and get the rest of the Omnitrix crystals back, it would've unlocked some of Ben's additional aliens like Wildvine, Upchuck, Ditto, Eye Guy, etc so you can replay the levels with them.
I'm just saying, do you have ANY idea how badly I wanted to kick ass as Diamondhead, High Voltage Software?!
#ben 10 protector of earth#ben 10#video games#high voltage software#d3 publisher#cartoon network#classic cartoon network#gaming#ps2 games#wii games#psp games
7 notes
·
View notes
Text

Visio 3.0 - Network Diagram
92 notes
·
View notes
Text

USA 1993
#USA1993#INNER CIRCLE SOFTWARE#NOVALINK#RPG#NETWORK#AMIGA#IBM#ATARIst#MACINTOSH#LEGENDS OF FUTURE PAST
13 notes
·
View notes
Text

A map of every single band on the Metal Archives as of March 1st of this year, using the same dataset I used for this site. Each individual dot represents a single band, and each line indicates that two bands have a member in common.

A closeup, showing the lines in a bit more detail.
There are around 177k bands on the Metal Archives, and, of them, about two-thirds can be connected to one another by common members.
#metal#metalarchives#data visualization#social networks#heavy metal#fun fact if you make a graph with 177 thousand nodes the graph visualization software will shit itself and die#so if I wanna visualize any sort of analysis I'm probably gonna need to figure out how I can pare this whole mess down#but I think this kinda looks cool
17 notes
·
View notes
Text
"From Passion to Profession: Steps to Enter the Tech Industry"
How to Break into the Tech World: Your Comprehensive Guide
In today’s fast-paced digital landscape, the tech industry is thriving and full of opportunities. Whether you’re a student, a career changer, or someone passionate about technology, you may be wondering, “How do I get into the tech world?” This guide will provide you with actionable steps, resources, and insights to help you successfully navigate your journey.
Understanding the Tech Landscape
Before you start, it's essential to understand the various sectors within the tech industry. Key areas include:
Software Development: Designing and building applications and systems.
Data Science: Analyzing data to support decision-making.
Cybersecurity: Safeguarding systems and networks from digital threats.
Product Management: Overseeing the development and delivery of tech products.
User Experience (UX) Design: Focusing on the usability and overall experience of tech products.
Identifying your interests will help you choose the right path.
Step 1: Assess Your Interests and Skills
Begin your journey by evaluating your interests and existing skills. Consider the following questions:
What areas of technology excite me the most?
Do I prefer coding, data analysis, design, or project management?
What transferable skills do I already possess?
This self-assessment will help clarify your direction in the tech field.
Step 2: Gain Relevant Education and Skills
Formal Education
While a degree isn’t always necessary, it can be beneficial, especially for roles in software engineering or data science. Options include:
Computer Science Degree: Provides a strong foundation in programming and system design.
Coding Bootcamps: Intensive programs that teach practical skills quickly.
Online Courses: Platforms like Coursera, edX, and Udacity offer courses in various tech fields.
Self-Learning and Online Resources
The tech industry evolves rapidly, making self-learning crucial. Explore resources like:
FreeCodeCamp: Offers free coding tutorials and projects.
Kaggle: A platform for data science practice and competitions.
YouTube: Channels dedicated to tutorials on coding, design, and more.
Certifications
Certifications can enhance your credentials. Consider options like:
AWS Certified Solutions Architect: Valuable for cloud computing roles.
Certified Information Systems Security Professional (CISSP): Great for cybersecurity.
Google Analytics Certification: Useful for data-driven positions.
Step 3: Build a Portfolio
A strong portfolio showcases your skills and projects. Here’s how to create one:
For Developers
GitHub: Share your code and contributions to open-source projects.
Personal Website: Create a site to display your projects, skills, and resume.
For Designers
Design Portfolio: Use platforms like Behance or Dribbble to showcase your work.
Case Studies: Document your design process and outcomes.
For Data Professionals
Data Projects: Analyze public datasets and share your findings.
Blogging: Write about your data analysis and insights on a personal blog.
Step 4: Network in the Tech Community
Networking is vital for success in tech. Here are some strategies:
Attend Meetups and Conferences
Search for local tech meetups or conferences. Websites like Meetup.com and Eventbrite can help you find relevant events, providing opportunities to meet professionals and learn from experts.
Join Online Communities
Engage in online forums and communities. Use platforms like:
LinkedIn: Connect with industry professionals and share insights.
Twitter: Follow tech influencers and participate in discussions.
Reddit: Subreddits like r/learnprogramming and r/datascience offer valuable advice and support.
Seek Mentorship
Finding a mentor can greatly benefit your journey. Reach out to experienced professionals in your field and ask for guidance.
Step 5: Gain Practical Experience
Hands-on experience is often more valuable than formal education. Here’s how to gain it:
Internships
Apply for internships, even if they are unpaid. They offer exposure to real-world projects and networking opportunities.
Freelancing
Consider freelancing to build your portfolio and gain experience. Platforms like Upwork and Fiverr can connect you with clients.
Contribute to Open Source
Engaging in open-source projects can enhance your skills and visibility. Many projects on GitHub are looking for contributors.
Step 6: Prepare for Job Applications
Crafting Your Resume
Tailor your resume to highlight relevant skills and experiences. Align it with the job description for each application.
Writing a Cover Letter
A compelling cover letter can set you apart. Highlight your passion for technology and what you can contribute.
Practice Interviewing
Prepare for technical interviews by practicing coding challenges on platforms like LeetCode or HackerRank. For non-technical roles, rehearse common behavioral questions.
Step 7: Stay Updated and Keep Learning
The tech world is ever-evolving, making it crucial to stay current. Subscribe to industry newsletters, follow tech blogs, and continue learning through online courses.
Follow Industry Trends
Stay informed about emerging technologies and trends in your field. Resources like TechCrunch, Wired, and industry-specific blogs can provide valuable insights.
Continuous Learning
Dedicate time each week for learning. Whether through new courses, reading, or personal projects, ongoing education is essential for long-term success.
Conclusion
Breaking into the tech world may seem daunting, but with the right approach and commitment, it’s entirely possible. By assessing your interests, acquiring relevant skills, building a portfolio, networking, gaining practical experience, preparing for job applications, and committing to lifelong learning, you’ll be well on your way to a rewarding career in technology.
Embrace the journey, stay curious, and connect with the tech community. The tech world is vast and filled with possibilities, and your adventure is just beginning. Take that first step today and unlock the doors to your future in technology!
contact Infoemation wensite: https://agileseen.com/how-to-get-to-tech-world/ Phone: 01722-326809 Email: [email protected]
#tech career#how to get into tech#technology jobs#software development#data science#cybersecurity#product management#UX design#tech education#networking in tech#internships#freelancing#open source contribution#tech skills#continuous learning#job application tips
9 notes
·
View notes
Text
Pirate Software's "rearchitecture" for Stop Killing Games
There's been a lot of fascinating drama around Stop Killing Games. Go read the initiative here:
It is a good initiative, and anyone who is a consumer that can, should absolutely go support it.
Jason "Thor" Hall, CEO of Pirate Software, recently had a few, let's say, "takes" on the matter (I'm trying and failing to remain neutral), which began on a stream. The stream's VOD has since deleted on his YouTube channel.
Louis Rossmann, who you might know as the largest Right to Repair activist in the US, made a response to a section of the releevant stream here:
youtube
Thor, CEO of Pirate Software, made two videos to clarify his points:
youtube
There is an argument in the video at the 2:08 mark that I will reference later.
youtube
(I recommend watching all these videos on 2x speed. You will get the same info out of them all, because especially video 2 is a lot of repetition)
Now, as mentioned above, there is one particular technical argument that bugs me about what Thor, CEO of Pirate Software, is making. Here is the full quote:
How would you keep League of Legends in a functional, playable state? You'd have to rearchitect the entire game. The game is what is called "client-server". So, in client-server models, there's a server, there's a client, and all of the math, all of the game, everything happens on the server. The client just displays it. And the reason we want to do it that way is so that you can't teleport around and do a billion damage. You don't trust the client. You trust the server. The client just displays what it's told. Right? So, if we wanted to rearchitect this, we would have to take all of that server logic, push it back out into the client, and somehow make that playable in a multiplayer-only video game. That doesn't make sense to me. So this doesn't work for all games. Why is [the initiative] calling out all games?
So, first off, yes, most games do client-server architecture for multiplayer logic, because you do trust the servers. It is an important step to curbing an entire class of cheats. It doesn't necessarily mean the client isn't malicious (for example, there are cheats for League of Legends that show a growing circle when an enemy leaves the fog of war in the minimap). However, it does mean the client doesn't know 100% of the game at any time when information is selectively fed to each client based on something like the fog of war. That's awesome.
Some games, like PlanetSide (rest in peace) and Overwatch (2) use what's called client-side hit detection. Some games, like Halo 1, employ more selective hit detection models, where only certain weapons use client-side hit detection (see https://c20.reclaimers.net/h1/engine/netcode/). Client-side versus server-side hit detection can change the overall feel of a game, and it's one of the things game developers decide on in multiplayer-only games that require it. In the case of an massively multiplayer online first person shooter (MMOFPS) like PlanetSide (2), the server simply can't calculate thousands of people's math in a reasonable amount of time, because otherwise the hit detection would otherwise feel very crappy to play, and so the math is offloaded to the client and the client says "hit" when they hit.
However, there are a few counterexamples to the specific technical argument that keeping the game playable after end-of-lifing it requires rearchitecting:
Games with dedicated servers exist - Command & Conquer: Renegade, Starsiege: TRIBES
Games where one client also hosts the multiplayer server exist - Half Life 2, Warhammer 40k: Space Marine
Private server hosting exists - World of Warcraft
Some of these games, particularly the examples with dedicated servers that can be run on user hardware, can also run as the second example.
To say keeping a multiplayer-only online game requires rearchitecting a game like League of Legends means a lack of imagination. More relevantly, it means a lack of systems thinking.
To me, it is very strange for someone such as Thor, CEO of Pirate Software, who is self-described as being a 20 year veteran of the games industry to say. I won't say skill issue, because I think there is an ulterior motive at play.
Just to hammer the point home, I drew up some crappy diagrams in Inkscape because this extremely wrong technical argument bugged me so, so much.
Here is what a client-server model looks like:

Here, you have 10 clients, each being a player of the game. Then, you have the server, run by Riot, the developer and maintainer of League of Legends.
Here is the imagination of Thor, CEO of Pirate Software, had to say on the matter on the required way rearchitect it:

Those who know their network models would understand this looks very much like a mesh network, or a peer-to-peer model. And, to be fair, some games might attempt it.
However, this isn't *usually* how games described using a peer-to-peer (P2P) model work. Most peer-to-peer models, like the architecture used in Space Marines, are often used for matchmaking. Once you are in a game, one of the clients also serves as the host (selecting by some algorithm, like randomly or whoever has the best hardware).
P2P is nice, because the company doesn't have to run servers for matchmaking at all during their lifespan (and sometimes a matchmaking server might be spun up to serve as a relay to help with network issues or help other clients find clients quickly). As we'll get into later, a client machine will also serve as the host machine. It is a perfectly fair and valid, although it comes with it's frustrations (mainly in the realm of network address translation (NAT) traversal, because your computer behind a router is not usually exposed to the wider Internet, though sometimes routers have universal plug-and-play (UPnP) set up, which makes NAT traversal much easier here).
If you've ever seen a message in the game "migrating host" because the host left, they likely use P2P matchmaking, but still use a client-server model. They can just migrate the game data to a new host using the data on the other clients as a seed for the data.
This is likely their setup for actual gameplay:

One of the clients now has a server on the same machine. Sometimes, this could be the game itself that would serve in singleplayer. However, most often, this is just a server that's lightweight enough for the client to connect to and they play that way (it's also really nice to develop and QA this way, because many server bugs will also be seen by the client).
Now, one of the disadvantages here is: Can all remote clients connect to the host that the server (and one of the clients) is running on? Again, NAT traversal issues usually play a role here. In the first few days of any game that uses this, and only this, there will likely be a lot of issues with connectivity.
Another disadvantage: The host won't have latency issues. This is why in the case of, for example, Among Us, the client host can see certain things happening (like someone is dead the moment they hit a button or reported a body), but remote player hosts might not.
Okay, so, maybe it's not possible to rearchitect something like League of Legends like this. It could reasonably be a lot of work. Here is another solution:

Looks very similar to the first architecture, doesn't it? It is! The difference is that the text "Riot" was changed to "not Riot".
This is how World of Warcraft and Pokemon Go private servers work.
The vast majority of games that would not run without private servers simply do not require rearchitecting to keep in a reasonably playable state when the servers shut down.
#stop killing games#pirate software#software architecture#software development#multiplayer game development#Networking#League of Legends#Among Us#PlanetSide#Starsiege: TRIBES#TRIBES#Half life 2#World of Warcraft#Pokemon Go#Warhammer 40k: space marine#command & conquer: renegade#Youtube
10 notes
·
View notes
Text
I'll hopefully do a better announcement about this earlier in the day tomorrow, but I've updated my pinned post with more information about the following things:
- I am (re)introducing a third stream into my schedule, doing livecoding on Sunday afternoons.
- I offer free software development tutoring lessons, particularly in support of new people just getting into the industry who are in need of help! Reach out to me or fill out this Google form for info.
- I am interested in offering pro bono webmaster/web development services for organizations working for progressive change (particularly in the United States at present, but potentially elsewhere as well), including but not limited to
Community and mutual aid groups
Humanitarian organizations
Civil rights and advocacy organizations
Charity and social service organizations
Environmental organizations
If you are associated with an organization that might find my services useful (or just want to suggest an org I should reach out to), please feel free to drop me a message here.
#bjk talks#tldr getting some more coding activities back into the mix#since my brain waking up didn't just fix my writer's block XD#unsure how to tag this but#software development#programming#web development#charity#pro bono#mutual aid#also very much open to suggestions on how to network this more effectively
6 notes
·
View notes
Text
I said I needed to update my router firmware because it's outdated and my gf goes, "Well, yeah, that UI is straight out of the 90s" DO NOT HATE ON DDWRT. MY FIRMWARE JUST NEEDS TO BE UPDATED FOR SECURITY REASONS. Hating on Dd-wrt is TOO FAR. TOO. FAR.
4 notes
·
View notes