#polybius cipher
Explore tagged Tumblr posts
Text
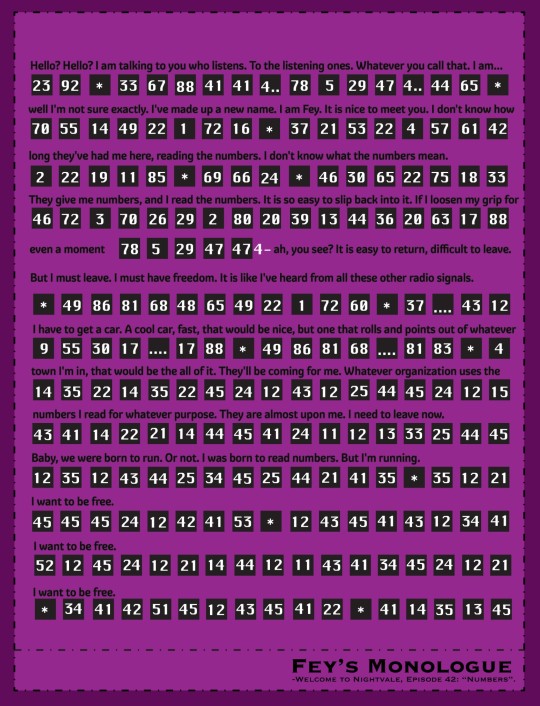
Little thing I did for Fey, my favorite Nightvale character. The numbers are all the ones she recites throughout her appearances and then that wasn't enough, so there's also some of what Cecil says at the end of 42 in Polybius Cipher (one with Fey as the keyword and without the letter Q).
#my art#goldie draws#digital art#graphic design#fey wtnv#fey welcome to nightvale#wtnv 42 numbers#wtnv fanart#wtnv#welcome to night vale#polybius cipher
90 notes
·
View notes
Text
44 23 15 52 34 42 31 14 24 43 11 31 52 11 54 43 15 33 14 24 33 22
1 note
·
View note
Note
I wanted to take a crack at the Broken Joysticks puzzle before you solved it so I searched "torch cipher" and I am so mad.
I actually don’t know what you found that made you mad.
117 notes
·
View notes
Text
i'm always 3 seconds away from breaking and using a typing quirk but that breaks screen readers. do you understand
#people who use them make me so jealous. imagine the euphoria.#i like the onez that use z in place of plural s. or onez that uze z in place of s in general. zo cool. but i can't do that :(#don't even get me started on just straight up using the polybius cipher. but that gets exhausting and online translators for it are hard to#find. not everyone is gonna know to ask for a link either. i'm not making people solve codes whenever i send a message in a discord#make better screen readers help an arcade machine out#an individual known as polybius does the act of expressing its feelings with words#a group of individuals known as entropy do the act of expressing their feelings with words
4 notes
·
View notes
Text
Bagi figured out the code is in Tap Code!
5 notes
·
View notes
Text
In an interview with Dan Milano celebrating Glitch Techs 4 year anniversary, at 36:40, the screen glitches and shows a code. This code:
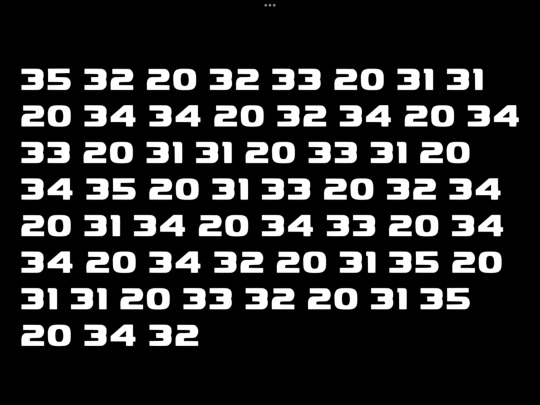
I have no idea what the code is. It looks like a variation of a Polybius Cipher, but it’s not correct, and a regular Polybius Cipher Decoder doesn’t work. Other decoders have just given me gibberish.
This is a call to anyone in the Glitch Techs Fandom with experience with ciphers. We need help with this.
This is the video by the way:
youtube
Notes: There are DEFINITELY spoilers in the QnA. Like 100%. So avoid it if you don’t want any.
15 notes
·
View notes
Text
An Overview of The Nihilist Cipher
Hello! If you're someone interested in ciphers, read ahead to learn a little about one of my long time favorite ciphers, the Nihilist Cipher.
The Nihilist cipher is a polyalphabetic substitution cipher, which basically means it relies on multiple shift ciphers applied to different letters in the text being encoded. If you're familiar with the Vigenère Cipher, Nihilist is pretty similar in a lot of ways.
I'll go through some history of the cipher, how to encode/decode using it, and how to conduct a known plaintext attack on it. I'll also go over how you might approach attacking it without a known plaintext (mainly because I think it's cool), but it won't be the main focus.
History
The Nihilist Cipher was first used by Russian nihilists against Russia's tsarist regime in the late 19th century. It's since been used as a basis for several ciphers with improved security used in WWII, notably the VIC cipher which is essentially an extremely complex hand-encoded cipher that's part of the Nihilist family.
"If [the VIC] cipher were to be given a technical name, it would be known as a 'straddling bipartite monoalphabetic substitution superenciphered by modified double transposition.'" David Kahn, Number One From Moscow
Usage
Encoding a message requires two things: A key and a Polybius square, known by you and the person you're communicating with. A Polybius square is one of these guys:
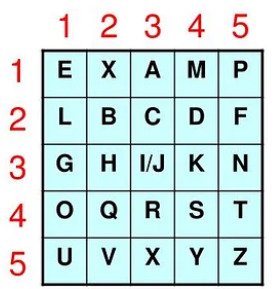
To use the cipher, you must first convert the plaintext into a numeric representation by mapping each letter to a number using the square. The mapping follows a (row, column) scheme, so the letter 'T' in the above square would become '45'. You'll notice that the square is 5x5, meaning there is 1 less square than there are letters in the English alphabet! This is typically solved by either choosing a square to represent 2 letters, differentiated using context by the receiver, or by simply leaving off an unused/infrequently used letter (often Q). It's also common to place a word at the start of the Polybius square, in this case "EXAMPLE" to offset the alphabet and avoid the mappings becoming trivial and obvious to attackers.
After we convert the plaintext to it's numeric representation, that's when the key becomes important. We first encode the key we picked using the Polybius square (i.e. the key MATH would become 14 13 45 32). Then, we repeat the key along the plaintext, and add each plaintext value to the key value to get the ciphertext!
To decode, the receiver must simply repeat the encryption process in reverse: repeating the key across the ciphertext, subtracting the key values, and translating the numeric plaintext back into English text. Because the encryption and decryption processes use the same key, the Nihilist Cipher is considered symmetric.
Known Plaintext Attack
Now we get into the fun part: How can we decode Nihilist encoded text without knowing the key? We will assume we know some ciphertext and the plaintext associated with it. Therefore, our goal is to use what we know to reveal the key, and use the key to decrypt the rest of the cipher. For example, assume we know that the first line of the Bee Movie script, "According to all known laws of aviation", results in the ciphertext "37 66 67 64 35 68 48 53 75 66 57 66 56 84 84 32 57 95 25 84 66 73 36 86 45 65 94 55 37 88 48 85 54".
Since the ciphertext is simply the result of adding the key to the plaintext, to find the key we only need to do the reverse and subtract the plaintext from the ciphertext!
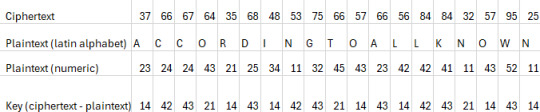
Even with only this short segment, we can see the repeating key is "14 42 43 21 14 43". Now we can repeat this key across the whole message and decrypt the Bee Movie script into numeric encoded plaintext.
At this point, you might be realizing where the next challenge lies. Unless you happen to be in a situation where you don't know the key yet somehow do know the Polybius square, this alone doesn't tell us very much! Since we've essentially converted our original problem into a simple substitution cipher, this is where we employ frequency analysis to figure out which number maps to which letter in the Polybius square. If you're up for a challenge you can do this manually, or use an online tool to analyze the frequency of each number and compare it to how often each letter of the English alphabet appears in typical text. Eventually, you'll be able to decode the Polybius square as the square below.
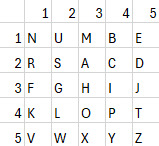
Ironically, the first snippet of The Bee Movie which we knew the plaintext of includes no 'E's, which are the most frequent letter in the English language, but letter frequencies of the full text would end up being much closer to the expected letter proportions.
Congratulations! You've now completed a plaintext attack on the Nihilist cipher and can sit down with a cup of tea for a bit of light reading .

Ciphertext-Only Attack
Now maybe that was too easy for you. Maybe you're a pro cipher-cracker, and you want to decode the Nihilist cipher without some "plaintext crutch". Here's how you can try to approach it! This method will need a large amount of ciphertext available, and relies on statistical analysis, plus some exploitation of the cipher's design to crack it.
The majority of this attack follows the same approach as a statistical attack on the Vigenère cipher. First you determine the key length by testing various key lengths, splitting the text up into groups that would be encoded with the same key, and computing the index of coincidence, which will be high (close to 0.068, the index of coincidence of English text) when the guessed key length is correct.
At this point, if this were the Vigenère cipher, we would have to go on to analyze the mutual index of coincidence between groups of ciphertext characters with the same key shifted by various amounts, but flaws in the Nihilist encoding system mean there's a good chance we can identify the key without this step!
Because of the way the Polybius square is set up, and the lack of modular arithmetic in the encoding method, every key letter value has exactly 25 possible ciphertext numbers that can result from that key. By comparing the ciphertext values encoded with the same shift, we can quickly identify or at least significantly narrow down the shift used to obtain those values! There are even a few cipher text values that immediately reveal what key was used to generate that cipher text (For example, a cipher text value of 30 can only be obtained using key=15). For a full list of possible ciphertext values generated by each key, check out this document I put together.
And that's it!
You are now a certified expert in all things Nihilist cipher. Go forth and use your new skill responsibly, leaving behind cryptic messages everywhere you go.
Happy decoding!

Sources:
https://www.cia.gov/resources/csi/static/Number-One-From-Moscow.pdf https://en.wikipedia.org/wiki/VIC_cipher
https://cyberw1ng.medium.com/nihilist-cipher-an-in-depth-look-at-the-cryptographic-technique-2023-b05b83551957
https://courses.cs.washington.edu/courses/cse163/20wi/files/lectures/L04/bee-movie.txt
17 notes
·
View notes
Text



Decoded:
BOJUTZMKZSKYZGXZKJ -> Caesar Cipher code: VIDONTGETMESTARTED -> track 6 Don't get me started
Image on YouTube -> Hexa hue code -> track 7 Colours Fly
Instagram post -> 44234-OEM-2151555154-234434532 -> Polybius cypher code -> THREEZEROSUM -> track 3 Zero Sum
5 notes
·
View notes
Note
Hey you, the one with the 'cool thing you think about but don't get to talk about as much as you'd like to.' What is one thing you want to talk about, in as much detail as you'd like (I will read all of it).
Ok one thing that I really think is cool, hmmmmm
This happens every time I’m asked “what do you like” my brain just instantly vacates everything I do, it’s just like “Error 404: Life Experiences not found”
Hmmmmmm, I’d probably say ciphers/encryption
Ok so encryption and ciphers, simple in concept but holy hell does this shit get complex and fun fast
I first found out about them from the Secret Breakers book series (I love it, would definitely recommend), and then I went to a CTYI (Centre for Talented Youth Ireland) course and learned more about them and how they work, in between these two events I also did a load of research and got really hyper fixated on them, I then proceeded to learn more and begin creating my own and making my own little puzzles and stuff
Ok so encipherment and encryption both do a similar job, obfuscate a message to hide it, they were used in the World Wars to send messages to people in enemy lines on both sides (most notably the Enigma Machine), encryption often uses mathematics and numbers linked in certain ways to hide things, ciphers are a little different in the way they operate, ciphers are obfuscations but it’s easier to hide that they are obfuscations as they can often look like normal text
For example, the Baconian cipher uses something similar to binary and highlighted text to hide a message, so 00000 is A, 00001 is B, 00010 is C, so on, so where there is a one you highlight the letter
So to hide the word “hi” you need at least 10 letters, but less that 15, so “hello there” is our ten letters and hi translates to 00111 01000, so we highlight the letters specified, which gives us “hello there” (the baconian cipher was made by Sir Francis Bacon and he has many written letters with hidden messages in them, that’s all I can remember off the top of my head)
But using encryption (for example Base64) “hi” would become “aGk=“ which is much more obvious that it is a hidden message
I’ll explain how encryption is used in real life somewhat in a reblog later, I just want to get back to where I was as uI just accidentally deleted a huge chunk of what I had typed (as in I opened Google to check my spelling and tumblr decided it would be the perfect time to restart, I’m typing this on my phone)
Ok so onto the ciphers, the one that I really really like
So ciphers have been in use for millennia, I’ll start with a common enough one, The Polybius Square
The Polybius Square was created by an Ancient Greek scholar called Polybius(yeah he tried really hard when naming his cipher), the cipher is a simple enough substitution cipher (a substitution cipher is where certain letters or symbols are replaced by others things), where letters are replaced using 2 digits which mark there position on the square
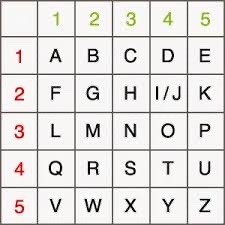
Which looks like this, it goes like this 11=A, 12=B, 13=C, 14=D, 15=E, 21=F, and so on, you’ll notice that in 24, instead of a single letter is both “i” and “j” simply for the reason that you can’t make a square out of 26 boxes
Early ciphers were often only used by themselves but later they were used together to make more complex ciphers whether this be where it was encoded once and then encoded again or that the two were used at the same time to do some funny shenanigans
A great example of this is the ADGFX cipher which uses a modified Polybius Square along with Columnar Transpostion
Ok I’ll explain the ADGFX cipher in just a second ima explain columnar transposition first, so with columnar transposition you need a key, we’ll use “cargo” (the general standard) so first take your message and split it into groups with the amount of characters in the group corresponding to the length of the key (So “we need to attack soon”, would be grouped into groups of 5 when using a key like cargo, the groups would look like this “wenee dtoat tacks oon”)
Next you align the groups under the key

Here is one using the example message of “we need to attack soon”
Ok next you need to take the letters in your key and arrange them alphabetically, so cargo become acgor, now take the columns you made and shift them along with the key letters

Like this
So now that we have our letters it’s easy, we take them from left to right, top to bottom and write them out, leaving us with, “eweentdatoatkscoon” with the key of cargo, now if most people were given that they wouldn’t have the slightest clue what to do
So now imagine if we added more layers, like in the ADGFX cipher
Long story short, you take a custom alphabet and replace the letters in a Polybius square with them, then replace the numbers in the square with ADGFX
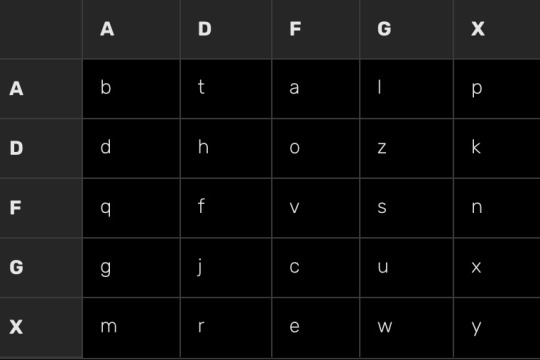
There is one that I stole from Google
So you encode your message using the square and then with the result you use the columnar transposition that we discussed earlier and then you have your final encoded message, unless you want to add more bullshit to it, like idk a A1Z26 cipher, changing the letters to numbers, or maybe a binary converter, or maybe a morse encoder, actually why not all of them
And that’s where shit starts getting fun (for me anyway, where you stack the jenga tower of encoding hoping that one of the ciphers in it doesn’t need numbers or spaces which other ciphers can’t use
Oh another fun thing, a number and text where you have to convert the number to binary and use that to highlight letters which are the encoded message, or are they
And that’s why I absolutely love encoding and ciphers so much because you can create such interesting little things that can become games, or just brand new ciphers where you have to spot little patterns or grab little ideas and run with them hoping that that was the way it works
Actually one last thing before I go, my own encipherment method which I couldn’t find anywhere online, and thus gave it a name
The Eclipsed Polybius Square (EPS)
Ok so the name comes from a name I used to go by (Which was Eclispe) and then the Polybius Square
Ok so I’ve written documentation of it countless times, but I can never explain it off the top of my head, I know how it works, it’s just stored in the depths of the blob of synapses that is in my skull
Ok so first step, take your message and use a Polybius square to turn it into the numbers,
I am struggling to figure out how to write this
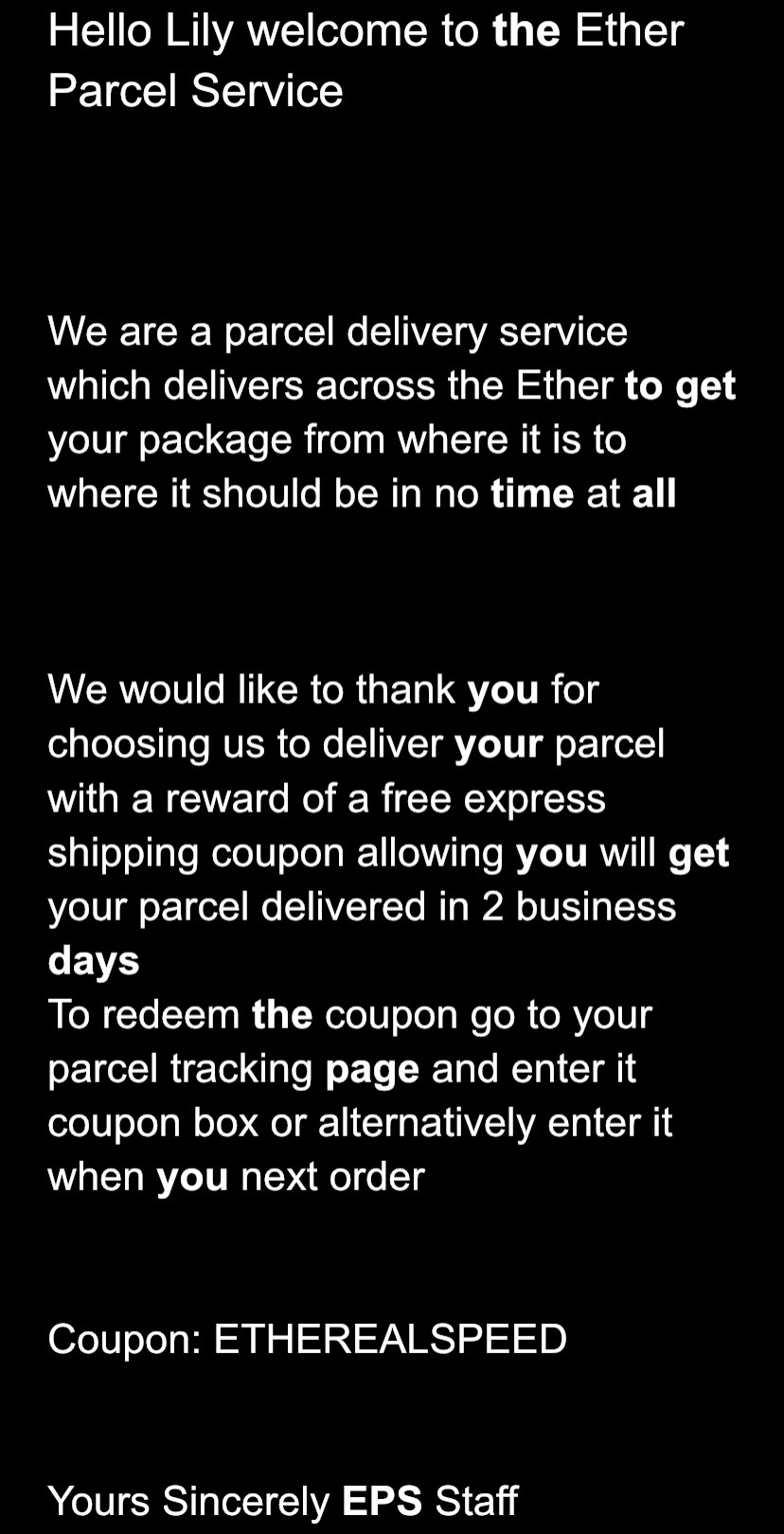
Here is an example which I used in an sort of puzzle hunt that I made for some friends (If you notice the name Lily there, it’s a character within the story of the puzzle hunt, game, thing)
Ok so see how some of the words are highlighted, they indicate numbers for the Polybius square
So “the” is in bold and it’s 3 letters long so we get the number 3, then “to” is in bold so we get 2, these two give us 32 which is our first letter “M”, then we have “get” which is 3, then “time” which is 4, now we have our next letter 34 which is “O”, and this continues to give us a whole word
You’re welcome to solve the rest if you want(send it to me if you do, whether that be in DMs or reblog)
Also just a note, when making the text which will hold the code, I’d recommend making the code first and then writing the text working around the code to get it in using as little words as possible, or you might end up like I did with all of the text there only giving 1 word
Actually actually, I have one last thing, thank you @rookieroc for asking, I have been dying to talk about this and so much more but I just haven’t found anyone to say it about
P.S. I will most likely add to this over time with reblogs with more information on different ciphers
#ciphers#puzzles#encryption#cryptography#god I love ciphers#again thank you @rookieroc for giving me the opportunity to share this knowledge#whadda ya mean it’s half past 2 in the morning#where tf did my time go
28 notes
·
View notes
Text

Just got my girl back from the museum! She's going in a place of honor
#it's starting to feel like fey's my child lol#no clue what the place of honor is gonna be byw#i have far too many posters in my room as is...#my art#goldie draws#digital art#graphic design#graphic art#fey wtnv#fey welcome to nightvale#wtnv fey#wtnv fanart#wtnv quote#fay wtnv#wtnv#wtnv 42 numbers#welcome to night vale#welcome to nightvale#welcome to night vale fanart#fanart#polybius cipher#queer artist#indie artist#small artists#digital artist#artists on tumblr#artist of tumblr#artwork#art
14 notes
·
View notes
Text

WELP İT İS A GOODBYE POST
🌑🌒🌓🌔🌕🌖🌗🌘
Did you read the article I put between the important above and important below in the pinned post? Yes... I feel like Dipper and Mabel; Just like they had to leave Gravity Falls when the summer ended, I'm also going to stop being online when the summer ends. Yes, that's true. Undertale AU Ask Blog will be closed. There's a chance I'll be online again during the semester. But I'll be online next summer like I did this summer. So just like Dipper and Mabel; See you next summer!
Before I go, I want to show you my latest OC I created; His name is G-Gilbert, (G stands for glitch) a ghost who usually appears in the dream world or subconscious. He speaks using Polybius, just like Gaster speaks with Wingdings.


There is also a message from Natt: I'am fine, see you all! (43 . 34 . 43)
I'll also tag a few friends to say bye to them, see you next summer guys!
@1v31182m5 @pastilina @mioplaces @hiimstripes @orangyketchup @godofchaoss
Do you remember my first post? I started with Hİ İNTERNET. Now let it be like this;
GOODBYE İNTERNET
Edit:

#my art#drawing#digital painting#art#digital art#gravity falls#bill cipher#undertale#wd gaster#gaster#undertale gaster#artwork#artists on tumblr#original art#polybius#wingdings#oc art#ocs#my ocs#oc#latest oc#comedy guy#goodbye#goodbye post#see you next summer#see you next year#bye tumblr#goodbye tumblr#goodbye internet#i will come back
40 notes
·
View notes
Text
OC PROPAGANDA METHINKS!!!

I entered in the @lemon-demon-oc-tournament and here's the reasons why you should vote for my oc Socrates 💥💥💥
I have very good reasons methinks
Reason one: They can change sizes
They can be one (1) (☝️) apple tall or the size of a whale.
Observe


2. They're FLUFFY so you can SNUGGLE THEM and because they can be any size they can be your stuffed animal or your bed. You choose.
3. They make really good lemonade it gives you the same side effects as being high (for the first 5 minutes until you start hearing every lemon demon song at once in your ears for the rest of time)
4. Their voice claim is Lolbit!! OH MY GOD FIVE NIGHTS AT FREDDYS??? that's pretty cool man you should totally vote for them
5. They are basically Bill Cipher but way more epic and cool and litcherrally awesome (rainbow dash said so)
See here:

6. THEY ARE A COSPLAYER. THEY COSPLAYED MEDIC FROM HIT GAME TEAM FORTRESS TWO.
Observe:

7. THEY ARE LGBT AND AUTISTIC. Socrates is bisexual and polyamorous and non binary we love a bi Royal also they have autism they are just like me yippie ^_^
8. They have an AWESOME OC PLAYLIST WITH TALLY HALL AND OTHER AWESOME BANDS??? WHAT THE FLIP??? IT CONTAINS AWESOME SONGS FROM BEETLEJUICE THE MYSICAL???
9. They have toe and hand beans they will allow you to squish. Just once. A vote May give you more however.
10. They're really old help a grandparent out man
11. They have a lot of lore
LORE INCOMING
Basically Socrates is the Satan/God of the Idiot Control Now universe (lemon demon oc universe) and they have existed since the beginning of time!!! They basically have seen the fucking rise and fall of countless nations and all they do with that information is do a little trolling. A little tomfoolery. Like for a prank. They're your classic movie villain that's silly (ripoff of Hades from Hercules and Bill Cipher)
They bullied Shepherd Satellite (Touch Tone Telephone) in high school for being adopted now that's an epic prank right guys *gets a tomato to the face*
Anyway they have a lot more lore based off of Greek mythology but y'all ain't reading all that
12. Their paws squeak when they walk
13. Best friend of View Monster and Cabinet Man (Byte Polybius) maybe if you voted for Socrates you all could hang out ....
Anyway that will be all for me. SOCRATES FOR PRESIDENT I MEAN SOCRATES FOR MAYOR I MEAN SOCRATES FOR SENATOR I MEAN SOCRATES FOR SECRETARY I MEAN SOCRATES FOR WINNER OF TOURNAMENT tehre we go first try ^__^
(Btw this is all a joke you don't have to vote for me just have fun in the competition guys ^_^ good luck to all the contestants and early congrats to whoever wins. From the preliminaries I've seen everyone's ocs are very lovely and everyone's characters are perfect even if you don't win. Have fun in the comp! :]] )

#lemon demon#art#neil cicierega#lemon demon ocs#lemon demon fanart#lemon demon oc#silly#artists on tumblr#lemon demon tournament#lemon demon sona#GL GUYS :3#this took too long#listen to rainbow dash gusy /nf /j
24 notes
·
View notes
Note
421154, 24 23115115 11 1342454323 3433 543445. --sincerely, 2445311543, 442315 354235 4313344544
--sincerely, anonymous (there's more that I'd like to say, but I don't wanna stress you out by having you decode it. It's the polybius square cipher, by the way)
(to solve it, first number is the row the letter is in, second number is the column it is in)
... no way
you actually. me? ha ha this is BRILLIANT!! i love you too
words can't describe how happy i am right now :)))))
...
does. does this mean we're dating <:]
#fellas. is it gay to learn a cipher for your cryptography hyperfixation crush#radiovoice#tf2 rp blog#team fortress 2#tf2#tf2 grn#jules tag#nonny ⏱#vernebury#WOOHOO
2 notes
·
View notes
Note
23 34 31 54 43 23 24 44 24 51 15 22 34 44 14 15 13 34 14 15 42 43 24 33 32 54 21 11 33 14 34 32!!!!!
okay are you just turning things I've said into a polybius cipher
This one just reads "oh my God I've got decoders in my fandom"
Which I, STILT-MAN, decoded just now
6 notes
·
View notes
Note
What's your favorite cipher? I'm partial to the polybius square. - 🐛
I did enjoy playing with ciphers and codes as a child. I had a book - one of those overly produced trick books they make for children, that comes in plastic wrap and has the trick pages that unfold to reveal hidden messages and games - called "Secret Codes and Formulas". It came with a decoder for a simple Caesar cipher, which I would use to write notes in the margins of the other books I'd read.
I can't say I have a favorite, however.
2 notes
·
View notes
Note
44 23 15 52 34 42 31 14 24 43 11 31 52 11 54 43 15 33 14 24 33 22
-polybius cipher anon
Hey! Don't send me stuff like this
#seriously shit like this freaks me out especially with what this translates to#if it was a funny translation i'd be chill with it but no it says “world is always ending”#unreality
6 notes
·
View notes