#rclone backup
Explore tagged Tumblr posts
Text
Rclone for Windows
Rclone is a powerful command-line tool for cloud storage management that allows users to sync, copy, move, and mount files across a variety of storage services. Supporting over 70 cloud storage providers, including Google Drive, OneDrive, Dropbox, Amazon S3, and Backblaze B2, Rclone is often referred to as the “Swiss Army knife” of cloud storage due to its versatility and extensive feature…
#cloud backup tool#cloud storage management#rclone#rclone backup#rclone encryption#rclone Google Drive#rclone mount#rclone OneDrive#rclone sync#secure file transfers
0 notes
Text
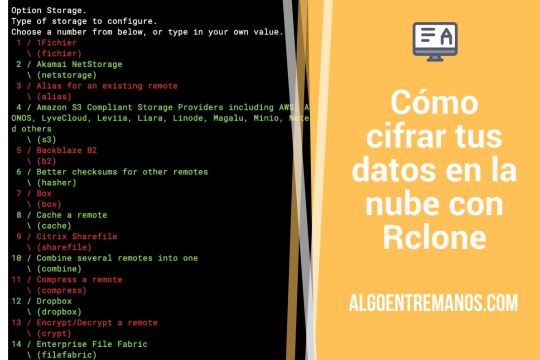
Cómo cifrar tus datos en la nube con Rclone
Ya te he contado cómo instalar Rclone en Rocky Linux para gestionar copias de seguridad, pero en este artículo voy a profundizar más en un aspecto muy interesante de este programa: puede crear copias de seguridad encriptadas en un almacenamiento en la nube que tengas configurado, por ejemplo en Backblaze B2 o Amazon S3. ¡Ojo! Antes de comenzar a crear un espacio remoto cifrado con Rclone, tienes…
View On WordPress
0 notes
Text

Backups with restic and rclone
Encrypted local and cloud backups
0 notes
Text
rcloned my homedir to the storage server installing Fedora presently. I have real homedir backups but they require a somewhat arcane interface to access so this sucks less. Fedora does BTRFS by default now!
I might end up not actually using all of this because I'll probably incorporate a lot of my new Work config like fish shell. Also moving to Plasma at least for now. There's a script called Krohnkite which implements i3-esque tiling on top of Plasma.
23 notes
·
View notes
Text
What Is a Storage VPS and Why You Might Need One
In a world drowning in data — from high-resolution images and massive video libraries to backup files and system logs — it’s more important than ever to find smart, scalable, and cost-effective storage solutions.
Enter: the Storage VPS.
If you’ve ever asked yourself, “How can I store huge amounts of data affordably?” or “What’s the difference between a regular VPS and a Storage VPS?” — this guide is for you.
We’re going to break down what a Storage VPS is, how it works, who it’s for, and how you can use it to supercharge your data storage strategy — all without overpaying or overcomplicating your tech stack.
What Is a Storage VPS?
A Storage VPS (Virtual Private Server) is a virtual server that’s optimized for massive disk space rather than high CPU or RAM. It gives you a private, scalable environment with large storage capacity, usually in the range of hundreds of gigabytes to multiple terabytes.
Unlike standard VPS plans — which focus on a balanced mix of computing power and storage — a Storage VPS leans heavily on providing as much space as possible at the lowest price per terabyte.
You can think of it as your own personal data warehouse. It’s ideal for situations where you don’t need intensive computing power but need a place to store a large amount of files, backups, media, or logs.
Why Use a Storage VPS Instead of Traditional Cloud Storage?
You may be wondering why someone would choose a Storage VPS over platforms like Google Drive, Dropbox, or Amazon S3. The answer comes down to control, cost, and flexibility.
Here’s a comparison to help clarify: FeatureStorage VPSTraditional Cloud StorageCost per TBLowerHigherControlFull root accessLimited to provider’s toolsFlexibilityInstall any softwareRestricted by provider featuresScalabilityEasily scalable via VPS upgradesCan get expensive or complexData privacyYou manage the dataProvider-managed servers
With a Storage VPS, you get full access to your server. You can install anything you want, encrypt your data, schedule automated backups, and control how and when your storage is used.
Plus, you’re typically paying a fraction of the cost compared to mainstream cloud platforms — especially when you need multiple terabytes of space.
Common Use Cases for a Storage VPS
Let’s look at some real-world ways people and businesses are using Storage VPS hosting to their advantage.
1. Offsite Backups for Websites or Apps
If you’re running a WordPress agency or managing multiple websites, a Storage VPS can act as a low-cost, secure location to store your offsite backups. You can automate backups using tools like rsync, Rclone, or SFTP, and store them encrypted on your VPS.
This ensures that even if your main server goes down, you have a reliable offsite recovery option.
2. Hosting a Personal Media Server
Want to stream your personal movie, music, or photo collection without relying on third-party platforms? A Storage VPS can be used to run media servers like Plex, Jellyfin, or Emby.
All you need is a basic VPS plan with high storage, and you can stream your media remotely — all under your control, without subscriptions or limits.
3. Cold Storage for Logs and Archives
Developers and IT teams often need to store large volumes of logs, analytics data, snapshots, and backups — data that doesn’t need to be accessed daily but must be available when required.
A Storage VPS provides a perfect solution for this kind of “cold” storage. It’s affordable, accessible on demand, and keeps your primary servers from getting overloaded.
What to Look for in a Good Storage VPS
Not all VPS plans are created equal, especially when it comes to storage. Here’s what to consider when choosing a Storage VPS:
Key Factors
Storage Type: HDD offers the most space for the lowest cost, while SSD is faster but more expensive. Choose based on your access needs.
Data Redundancy: Look for providers that offer RAID storage or at least some level of redundancy and backup.
Network Bandwidth: If you’re uploading or syncing large files, make sure the VPS has at least 1 Gbps network speed.
Root Access: Make sure the provider gives you full root access so you can configure the server however you want.
Location Options: Choose a data center location that matches your needs — whether it's for speed, compliance, or geo-redundancy.
Also, look at the provider’s policies on bandwidth limits and fair use. Some budget VPS plans have hidden limits that can impact performance if you transfer large volumes of data.
How to Set Up Your Storage VPS in 5 Steps
Setting up a Storage VPS doesn’t require advanced server knowledge. Here’s a basic setup roadmap:
Choose a reputable provider offering high-storage VPS plans.
Deploy your preferred OS (Ubuntu or Debian are beginner-friendly).
Secure your server by updating packages, creating secure passwords, and setting up a firewall (e.g., UFW).
Install file transfer tools like SFTP, rsync, or Rclone.
Automate backups or syncs using cron jobs or simple scripts.
In under an hour, you can be up and running with your own remote storage server.
Top Storage VPS Providers in 2025
If you're looking for reliable Storage VPS options, here are a few providers worth considering:
Hetzner
Based in Germany, Hetzner offers high-storage VPS solutions at some of the lowest price points in the industry. Their hardware is robust, and their support is developer-friendly.
Contabo
Contabo has long been a go-to for affordable VPS hosting. Their storage-optimized VPS plans include generous storage along with decent CPU and RAM.
GreenCloud VPS
GreenCloud offers specialized storage VPS plans in multiple global locations. They are especially popular for backup and media storage use cases.
Can a Storage VPS Help With SEO?
Indirectly, yes. Here’s how:
Faster page loads: Offloading large media (images, videos, PDFs) to a subdomain on your Storage VPS can reduce your main site’s load times.
Higher reliability: Storing backups separately means you can recover faster in case of downtime or corruption.
Better scalability: You can store and serve static files from a Storage VPS, reducing the load on your primary web server.
While it’s not a direct ranking factor, improved speed, uptime, and performance can positively influence your search engine visibility.
Final Thoughts: Is a Storage VPS Worth It?
Absolutely — especially if you’re dealing with large amounts of data or need more control over your storage infrastructure.
Let’s recap why a Storage VPS is a smart move:
Lower cost per terabyte than traditional cloud platforms
Full control over your server environment
Easily scalable and customizable
Ideal for backups, media hosting, and file storage
Great for developers, small businesses, and tech-savvy users
Whether you’re a solo creator, an IT admin, or a growing business, a Storage VPS gives you the tools to store, manage, and access data on your terms.
Ready to Get Started?
If you’re ready to take control of your data — and stop overpaying for cloud storage — a Storage VPS might be the perfect fit. Look for a provider that matches your storage and budget needs, and get started today.
Still have questions? Let me know — I’d be happy to help you choose the right setup.
0 notes
Text
Hướng dẫn tạo crontab tự động backup với rclone với wasabi
💖👉🍀 Ok mình làm gọn cho bạn luôn nè, tạo crontab tự động backup với rclone rất dễ nhé! 🌟 Kế hoạch: Mỗi 1 tiếng tự động chạy lệnh rclone sync folder /home2/pickyour/public_html/wp-content/uploads/ lên Wasabi. Log kết quả ra file /var/log/rclone_wasabi.log để kiểm tra sau. ✅ Bước 1: Mở crontab crontab -e ✅ Bước 2: Thêm dòng sau vào cuối file: 0 * * * * /usr/bin/rclone sync…
0 notes
Link
0 notes
Text
Akira ransomware prevention and defense 2024
New Post has been published on https://thedigitalinsider.com/akira-ransomware-prevention-and-defense-2024/
Akira ransomware prevention and defense 2024


EXECUTIVE SUMMARY:
In March of 2023, the first Akira ransomware strain was observed in the wild. Since then, the group has compromised over 100 different organizations, targeting those in the financial, manufacturing, real-estate, healthcare and medical sectors.
Akira operates on a Ransomware-as-a-Service (RaaS) model and typically deploys a double-extortion scheme. This involves exfiltrating sensitive data prior to device encryption and insisting on a ransom in exchange for withholding the data from the group’s TOR leak site.
Most recently, Akira interrupted a U.S. emergency dispatch system, causing a nine-day operational outage. During the outage, dispatchers relied on backup systems. As of the present writing, full system restoration is still a work-in-progress.
About Akira
The group is believed to have taken its name from the 1988 cult anime film of the same name, which depicts biker gangs in a dystopian Tokyo. The Akira ransomware gang is known for use of a retro aesthetic on victims’ sites, reminiscent of the 1980’s green screen consoles.
Cyber security researchers have uncovered evidence linking the Akira group to the notorious Conti ransomware operation. In at least three separate cryptocurrency transactions, Akira criminals appear to have sent the full amount of the ransom payment to Conti-affiliated addresses.
The overlap of cryptocurrency wallets indicates that the individual controlling the address or wallet has either splintered off from the original group, or is working with two different groups simultaneously.
How Akira operates
Akira commonly breaches systems by obtaining unauthorized access to the target organization’s VPNs, as through a compromised username/password combination.
After sneaking in through an endpoint, Akira typically uses any of several methods to acquire permissions that enable lateral network movement.
These methods include orchestrating a mini-dump of the LSASS (Local Security Authority Subsystem Service) process memory, obtaining credentials stored in the Active Directory database and exploiting known vulnerabilities in backup software.
Advanced persistence mechanisms
Akira ordinarily deploys tools and techniques like Remote Desktop Protocol (RDP), Server Message Block (SMB), impacket module wmiexec, and a service manager tool known as nssm.exe, in order to gain persistence within systems.
As is the case among many cyber criminal groups, Akira also attempts to uninstall or disable security defenses, including anti-malware and network monitoring tools.
Beyond that, the group tends to use the runas command (a Windows command-line tool that allows for the execution of scripts, apps…etc., with different user permissions from the currently logged-in user) in order to execute commands.
This, in turn, makes tracking hacker activities more difficult for defenders.
Akira and C2 mechanisms
Most ransomware attackers weaponize a command and control (C2) mechanism to execute activities. The C2 system establishes communication with and exerts control over a compromised machine or network.
The C2 server can potentially be used to manage the ransomware deployment and to initiate the encryption of data on targeted systems. For the purpose of establishing persistent remote access to multiple systems within the network, Akira seems to prefer AnyDesk.
Akira and data exfiltration
Akira uses a number of different tools when it comes to data exfiltration. These include WinRAR, WinSCP, rclone, and MEGA.
After data exfiltration, Akira demands a ransom from victims. In the event that the ransom goes unpaid, the group will leak stolen data on its TOR site, as previously mentioned.
Akira’s encryption tactic
To encrypt a given target’s data, Akira relies on a combination of AES and RSA algorithms. The group will also purge Windows Shadow Volume Copies from devices by running a PowerShell command. For victims, this massively complicates the process of independently restoring systems and recovering encrypted data.
Recommended means of preventing and defending against Akira’s ransomware
1. Address identity and access management.
Enhance access controls. Implement multi-factor authentication (MFA). Akira can gain initial access via unauthorized logins to VPNs through accounts that lack MFA. This seemingly simplistic safeguard can significantly limit the risk of unauthorized access.
2. Store credentials securely.
As noted earlier, Akira deploys a variety of tactics to obtain credentials. These tactics include execution of a mini-dump of the LSASS process memory, retrieving credentials stored in the Active Directory database and leveraging vulnerabilities in backup services.
To that effect, organizations need to take care when it comes to credential management. Credentials should be stored securely, and regularly updated. Backup services must also be appropriately secured.
3. Elevate your patch management protocol.
Akira commonly exploits vulnerabilities in VPN software. Thus, regular patching and updating of software can proactively prevent Akira attacks.
4. Monitor your network like a ninja.
Akira relies on built-in commands and tools to identify an environment’s systems and to learn about the status of target devices. Detect duplicitous behavior by monitoring for unusual network activity.
Your organization should also monitor for data exfiltration. Look for substantial data transfers and unusual network patterns.
5. Secure C2 channels.
Akira uses widely recognized dual-use agents, such as AnyDesk, to establish persistent remote access. Remain vigilant in regards to abnormal remote access activities and fortify Command and Control (C2) channels. This can be of tremendous assistance when it comes to thwarting potential attacks.
6. Secure remote desktop protocol.
Akira frequently employes Remote Desktop Protocol (RDP), using legitimate local administrator user accounts to facilitate lateral movement. Enhancing the security of RDP and staying vigilant for atypical RDP activity can be effective in preventing lateral movement.
7. Implement endpoint protection.
Akira usually attempts to uninstall endpoint protections as a means of evading detection. Deploying robust endpoint protection measures and consistently monitoring for efforts to disable or uninstall such safeguards can also assist with attack prevention and detection.
Related resources
The 10 most dangerous ransomware groups right now – Read article
Secure your data. Explore endpoint security solutions – Learn more
Identity and access management solution free trial – Click here
#2023#2024#access management#Accounts#active directory#Akira#Akira ransomware#Algorithms#anti-malware#apps#Article#attackers#authentication#backup#Behavior#C2#CISO#command#communication#Conti#Conti ransomware#credential#credentials#cryptocurrency#cyber#cyber security#data#data exfiltration#Database#defenders
0 notes
Video
youtube
Cloud Backup with Data Encryption using Google Drive, rClone, and Docker
0 notes
Text

For storage, get a NAS. Either prebuilt (e.g synology) or build something yourself using truenad.
Prebuilt has the advantage that they most likely use very energy efficient parts that are hard to aquire or hard to work with for DYI builds.
For offsite backup, the cheapest would be to have a friend with some storage and use each others systems as offsite storage.
If that is not an option, try to get some cheap hosted S3 storage. Amazon has the lowest running cost with their longterm/archival solutions, but they come with the downside of steep transfer costs once you need to get to your data. Other people recommend backblaze. I'm personally using Wasabi.
Software wise, there is a lot good software to choose from. What exactly you want to use depends on your usecase.
Dirvish if you want to let a backup server pull the data instead of pushing from the source
duplicity is what I'm currently using to backup my VPS to S3 Storage
restic as an alternative for duplicity
Déjà Dup for a nice GUI app for the desktop (based on duplicity or restic)
If you backup windows and don't mind the software not being open source, I really recommend veeam free. Just works rock solidly.
honorable mentions: rclone, syncthing (not really a backup), whatever is built in to what you use (e.g. proxmox backup settings, Synology Hyperbackup, etc.)
Most importantly, remember the 3-2-1 Principle
you should have 3 copies of your data (your production data and 2 backup copies) on two different media with one copy off-site for disaster recovery.

Pulled a sneaky on my co-worker today :p
493 notes
·
View notes
Link
#rclone et docker#backup volume docker avec Rclone#Utiliser Rclone avec Pcloud#Rclone et les containers docker
0 notes
Text
Backup files to Google Drive with Rclone
Backup files to Google Drive with Rclone
Backup files with rclone Backup files to google drive using rclone. Before we get right to this, let us break down the keywords first. Backup In information technology, a backup, or data backup is a copy of computer data taken and stored elsewhere. That way, it may be used to restore the original after a data loss event. The verb form referring to the process is known as “back up”. Whereas the…

View On WordPress
0 notes
Text
Google photos backup linux

#Google photos backup linux update
That way, if you need to change a value, you know which parameter to adjust. Some of these values are the defaults, but we’ve included them here so that we can discuss them. If the destination directory does not exist, it will be created. Subdirectories are separated by the usual “/” forward slash. Also note the colon “:” that is used as a separator between the remote storage name and the directory name. Note the use of “google-drive”, which is the name we gave to this remote connection during the the rclone config sequence.
“google-drive:LinuxDocs”: The destination directory in the remote storage.
“/home/dave/Documents”: The local directory to we’re going to copy to the remote storage.
#Google photos backup linux update
This sets the frequency of update of the statistics to one second. –stats 1s: rclone can provide statistics on the transferred files.This value sets the limit for the number of retries. –low-level-retries 10: A low-level retry tries to repeat one failing operation, such as a single HTTP request.–retries 3: If there are this many errors, the entire copy action will be restarted.–timeout 300s: If a transfer becomes idle for this amount of time, it is considered broken and is disconnected.It sets the time that rclone will try to make a connection to the remote storage. –contimeout 60s: The connection timeout.Checkers monitor the transfers that are in progress., –checkers 8: How many “checkers” to run in parallel.–transfers 30: This sets the number of files to copy in parallel.–verbose: Gives information about every file that is transferred.–update: Skip any files that are on the remote storage that have a modified time that is newer than the file on the local computer.copy: Copy the files from the local computer to the remote storage, skipping over files that are already present on the remote storage.usr/bin/rclone copy -update -verbose -transfers 30 -checkers 8 -contimeout 60s -timeout 300s -retries 3 -low-level-retries 10 -stats 1s "/home/dave/Documents" "google-drive:LinuxDocs" You can call it whatever makes sense to you. Type (or copy and paste) this into a text editor and save it to your computer. We’re using this as a basic form of off-site backup. This is a one-way copy to the cloud it isn’t a two-way synchronization between your Google Drive and your local computer-although rclone can do that. The command we’re going to look at below copies files from your local computer to your Google Drive. That’s great, but it does mean there are a lot of options. The rclone application is very feature-rich. At the “Yes, Edit, Delete” menu type “y” and then press “Enter.”Īt the final menu, type “q” and press “Enter.”

1 note
·
View note
Link

Rclone can efficiently manage files on 40+ cloud storage providers, such as AWS, Backblaze, Google Drive, Dropbox, Mega, NextCloud, ownCloud, Rackspace and many.
Rclone was purely a command line program in the earlier days. Fortunately, it does have an experimental Web based GUI now. So if you’re not comfortable with CLI, you can perform many Rclone operations graphically via a Web browser.
Its features include: mounting filesystems as a disk, is secure and safe, can sync files (or migrate) between different cloud providers, can avoid copying duplicate files, reduces bandwidth and time, can compress and split files (to overcome cloud provider limitations), verifies data integrity, and more.
But it is not a backup solution for version control, however some 3rd party developers, such as HashBackup and Kopia, do create innovative backup solutions using rclone CLI or API. It also does uni-sync and not bidirectional sync.
See https://ostechnix.com/install-rclone-in-linux/
#technology #cloudstorage #clouddrive #rclone #opensource
0 notes
Text
docker-rclone-google-drive-cron-backup/guide at master · negati-ve/docker-rclone-google-drive-cron-backup · GitHub
0 notes
Text
Free Dropbox Clone

Download latest version of RealDownloader for Windows. Safe and Virus Free. Downloading videos with this software is so simple, in fact, that, once installed, the software automatically displays a download button next to all web videos. With one click, the video is downloaded and saved onto your hard disk. Real Downloader can also launch multiple downloads at the time no matter the size or format of the videos. Download realplayer downloader for windows 10. RealPlayer® 20/20 is the fastest, easiest, and fun new way to download and experience video Download the latest version of RealPlayer or RealTimes and get the latest features! Video downloader Download video Video grabber Download Downloader Grabber Grab. RealDownloader was reviewed by Bogdan Popa. Windows 10 32/64 bit Windows 8 32/64 bit Windows 7 32/64 bit.

Dropbox Download
Free Dropbox Clone Free
You must agree to the terms laid down here in order to use the software on your PC. Scriptcase 9 full crack. You agree to abide by the copyrights and intellectual property rights laws as a trial or premium user of Clone Files Checker software.

Dropbox supports modified times, but the only way to set a modification time is to re-upload the file. This means that if you uploaded your data with an older version of rclone which didn't support the v2 API and modified times, rclone will decide to upload all your old data to fix the modification times.
Today we review all the methods and ways to get more free space in Dropbox and have enough space for photos, files or videos. You can buy space in Dropbox if you do not have enough with the free gigas offered by the cloud service but you can also bet on ways and methods to get more free space in Dropbox before paying.
To download and install this software on your computer you must
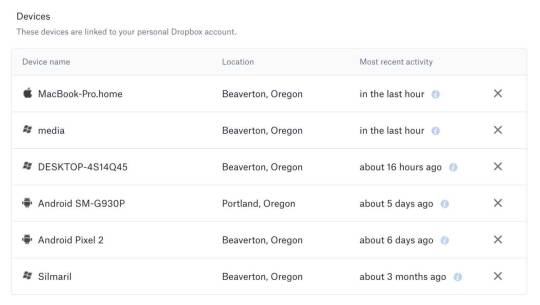
Dropbox Download
For years now, Dropbox has been the gold standard and a trustworthy provider for file syncing and data backup. Dropbox was one of the first early companies to understand and deliver on cloud storage and syncing. It is a reliable and straightforward file-synching with a storage service that has now been enhanced with collaboration features. (more) How to Get A Free Dropbox With 16GB of Space.
Free Dropbox Clone Free
not try to change the software code
unless you have taken written permissions from Sorcim Technologies, not use our brand name, images and trademarks elsewhere. If you are given permission to use these materials, you agree to follow the terms laid down.
agree that the software you are downloading may ask you to install updates that are meant to improve software functionality
not sell the software to other people without our consent
not remove the EULA text from software
not distribute software to illegal websites
adhere to the terms laid down here and you agree that your software license can be suspended in case you are found to be violating these terms of service conditions.
The software Clone Files Checker is published by Sorcim Technologies (pvt) Ltd or Sorcim. It comes with a 'LIMITED FIX' option whereby you can delete up to 10 duplicate files groups from the files scanned and reported by the software.
not held us responsible for claims provided about our software by third-parties like affiliates and partners
agree to retain the right to stop using software distributed by Sorcim Technologies (pvt) Ltd.
check out the privacy policy for our company http://www.sorcim.com/privacy.html and the software http://www.clonefileschecker.com/privacy-policy.html
agree to use the software and content as it is and at your sole risk, and Sorcim Technologies is not held responsible for any loss incurred that is not applicable by law
agree that Sorcim Technologies do not warrant to you that the content and software will meet all your requirements or will be free from error and you agree that any loss caused to your computer or any other electronic device will not be the responsibility of Sorcim.
keep your license code saved yourself and company will not be responsible if you accidentally lose access to it
understand and agree that there may be links to third-party websites in www.clonefileschecker.com website and Sorcim is not questionable or liable to any information provided by these external websites which are not directly affiliated with Sorcim.
agree that the transactions carried out through our merchant are done at your own risk
allow us to send infrequent emails to you to inform you about updates and changes to our privacy policies and Terms of Use.
The Cloud Scan (in Clone Files Checker for Mac) is performed by Sorcim Technologies’ Cloud Duplicate Finder web-app. Its Terms of Service can be viewed at https://www.cloudduplicatefinder.com/tems-of-service

0 notes