#sql reporting services
Explore tagged Tumblr posts
Text
A Complete Tutorial on SQL Server Reporting Services (SSRS) with multiple examples on each chart and the Data Sources.
0 notes
Text
SQL Server Reporting Services: Data Analysis Full Course Tutorial (7+ Hours)
SQL Server Reporting Services: Data Analysis Full Course Tutorial (7+ Hours) Get Ad-Free Training by becoming a member … source
0 notes
Text

I was in highschool in the late 1970s, and our "new" computer was a DEC PDP-8, that was five years old or so.
However the school was still largely running on punch cards, and older IBM equipment from the 50s. Attendance for instance, was handled by each home room teacher putting an absent students punch card in an envelope that went down to the computer room, a process that had probably been going on for decades.
There the cards were sorted, and fed into this beast, an IBM 405 alphabetic accounting machine. This is basically a SQL statement implemented in steel, wires, and relays. It would print off a report using fields on the cards fed into it, and could be programmed via a plug board:

I will never forget the IBM service guy coming in to change the oil on this, the whole bottom of it was relays that just kind of sat in an oil bath.
So if you have computer problems, just be happy changing the oil isn't one of them lol.
302 notes
·
View notes
Text
The flood of text messages started arriving early this year. They carried a similar thrust: The United States Postal Service is trying to deliver a parcel but needs more details, including your credit card number. All the messages pointed to websites where the information could be entered.
Like thousands of others, security researcher Grant Smith got a USPS package message. Many of his friends had received similar texts. A couple of days earlier, he says, his wife called him and said she’d inadvertently entered her credit card details. With little going on after the holidays, Smith began a mission: Hunt down the scammers.
Over the course of a few weeks, Smith tracked down the Chinese-language group behind the mass-smishing campaign, hacked into their systems, collected evidence of their activities, and started a months-long process of gathering victim data and handing it to USPS investigators and a US bank, allowing people’s cards to be protected from fraudulent activity.
In total, people entered 438,669 unique credit cards into 1,133 domains used by the scammers, says Smith, a red team engineer and the founder of offensive cybersecurity firm Phantom Security. Many people entered multiple cards each, he says. More than 50,000 email addresses were logged, including hundreds of university email addresses and 20 military or government email domains. The victims were spread across the United States—California, the state with the most, had 141,000 entries—with more than 1.2 million pieces of information being entered in total.
“This shows the mass scale of the problem,” says Smith, who is presenting his findings at the Defcon security conference this weekend and previously published some details of the work. But the scale of the scamming is likely to be much larger, Smith says, as he didn't manage to track down all of the fraudulent USPS websites, and the group behind the efforts have been linked to similar scams in at least half a dozen other countries.
Gone Phishing
Chasing down the group didn’t take long. Smith started investigating the smishing text message he received by the dodgy domain and intercepting traffic from the website. A path traversal vulnerability, coupled with a SQL injection, he says, allowed him to grab files from the website’s server and read data from the database being used.
“I thought there was just one standard site that they all were using,” Smith says. Diving into the data from that initial website, he found the name of a Chinese-language Telegram account and channel, which appeared to be selling a smishing kit scammers could use to easily create the fake websites.
Details of the Telegram username were previously published by cybersecurity company Resecurity, which calls the scammers the “Smishing Triad.” The company had previously found a separate SQL injection in the group’s smishing kits and provided Smith with a copy of the tool. (The Smishing Triad had fixed the previous flaw and started encrypting data, Smith says.)
“I started reverse engineering it, figured out how everything was being encrypted, how I could decrypt it, and figured out a more efficient way of grabbing the data,” Smith says. From there, he says, he was able to break administrator passwords on the websites—many had not been changed from the default “admin” username and “123456” password—and began pulling victim data from the network of smishing websites in a faster, automated way.
Smith trawled Reddit and other online sources to find people reporting the scam and the URLs being used, which he subsequently published. Some of the websites running the Smishing Triad’s tools were collecting thousands of people’s personal information per day, Smith says. Among other details, the websites would request people’s names, addresses, payment card numbers and security codes, phone numbers, dates of birth, and bank websites. This level of information can allow a scammer to make purchases online with the credit cards. Smith says his wife quickly canceled her card, but noticed that the scammers still tried to use it, for instance, with Uber. The researcher says he would collect data from a website and return to it a few hours later, only to find hundreds of new records.
The researcher provided the details to a bank that had contacted him after seeing his initial blog posts. Smith declined to name the bank. He also reported the incidents to the FBI and later provided information to the United States Postal Inspection Service (USPIS).
Michael Martel, a national public information officer at USPIS, says the information provided by Smith is being used as part of an ongoing USPIS investigation and that the agency cannot comment on specific details. “USPIS is already actively pursuing this type of information to protect the American people, identify victims, and serve justice to the malicious actors behind it all,” Martel says, pointing to advice on spotting and reporting USPS package delivery scams.
Initially, Smith says, he was wary about going public with his research, as this kind of “hacking back” falls into a “gray area”: It may be breaking the Computer Fraud and Abuse Act, a sweeping US computer-crimes law, but he’s doing it against foreign-based criminals. Something he is definitely not the first, or last, to do.
Multiple Prongs
The Smishing Triad is prolific. In addition to using postal services as lures for their scams, the Chinese-speaking group has targeted online banking, ecommerce, and payment systems in the US, Europe, India, Pakistan, and the United Arab Emirates, according to Shawn Loveland, the chief operating officer of Resecurity, which has consistently tracked the group.
The Smishing Triad sends between 50,000 and 100,000 messages daily, according to Resecurity’s research. Its scam messages are sent using SMS or Apple’s iMessage, the latter being encrypted. Loveland says the Triad is made up of two distinct groups—a small team led by one Chinese hacker that creates, sells, and maintains the smishing kit, and a second group of people who buy the scamming tool. (A backdoor in the kit allows the creator to access details of administrators using the kit, Smith says in a blog post.)
“It’s very mature,” Loveland says of the operation. The group sells the scamming kit on Telegram for a $200-per month subscription, and this can be customized to show the organization the scammers are trying to impersonate. “The main actor is Chinese communicating in the Chinese language,” Loveland says. “They do not appear to be hacking Chinese language websites or users.” (In communications with the main contact on Telegram, the individual claimed to Smith that they were a computer science student.)
The relatively low monthly subscription cost for the smishing kit means it’s highly likely, with the number of credit card details scammers are collecting, that those using it are making significant profits. Loveland says using text messages that immediately send people a notification is a more direct and more successful way of phishing, compared to sending emails with malicious links included.
As a result, smishing has been on the rise in recent years. But there are some tell-tale signs: If you receive a message from a number or email you don't recognize, if it contains a link to click on, or if it wants you to do something urgently, you should be suspicious.
30 notes
·
View notes
Text
Build Powerful Web Applications with Oracle APEX – Fast, Responsive, and Scalable

In today’s digital world, businesses need custom web applications that are not only powerful but also fast, user-friendly, and mobile-responsive. That’s where Oracle APEX (Application Express) comes in — and that’s where I come in.
With over 15 years of experience in Oracle technologies, I specialize in designing and developing robust Oracle APEX applications tailored to your business needs.
✅ What I Offer:
Fully customized Oracle APEX application development
Beautiful and responsive UI designs for desktop & mobile
Data entry forms, interactive reports, and dashboards
Complex PL/SQL logic, validations, and dynamic actions
Migration from Oracle Forms to APEX
Web service integrations and scalable architectures
Whether you're building a tool for internal use or deploying a full-scale enterprise app, I can bring your project to life with precision and quality.
👉 Hire me on Fiverr to get started: 🔗 https://www.fiverr.com/s/e6xxreg
2 notes
·
View notes
Text
Symfony Clickjacking Prevention Guide
Clickjacking is a deceptive technique where attackers trick users into clicking on hidden elements, potentially leading to unauthorized actions. As a Symfony developer, it's crucial to implement measures to prevent such vulnerabilities.

🔍 Understanding Clickjacking
Clickjacking involves embedding a transparent iframe over a legitimate webpage, deceiving users into interacting with hidden content. This can lead to unauthorized actions, such as changing account settings or initiating transactions.
🛠️ Implementing X-Frame-Options in Symfony
The X-Frame-Options HTTP header is a primary defense against clickjacking. It controls whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object> tag.
Method 1: Using an Event Subscriber
Create an event subscriber to add the X-Frame-Options header to all responses:
// src/EventSubscriber/ClickjackingProtectionSubscriber.php namespace App\EventSubscriber; use Symfony\Component\EventDispatcher\EventSubscriberInterface; use Symfony\Component\HttpKernel\Event\ResponseEvent; use Symfony\Component\HttpKernel\KernelEvents; class ClickjackingProtectionSubscriber implements EventSubscriberInterface { public static function getSubscribedEvents() { return [ KernelEvents::RESPONSE => 'onKernelResponse', ]; } public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $response->headers->set('X-Frame-Options', 'DENY'); } }
This approach ensures that all responses include the X-Frame-Options header, preventing the page from being embedded in frames or iframes.
Method 2: Using NelmioSecurityBundle
The NelmioSecurityBundle provides additional security features for Symfony applications, including clickjacking protection.
Install the bundle:
composer require nelmio/security-bundle
Configure the bundle in config/packages/nelmio_security.yaml:
nelmio_security: clickjacking: paths: '^/.*': DENY
This configuration adds the X-Frame-Options: DENY header to all responses, preventing the site from being embedded in frames or iframes.
🧪 Testing Your Application
To ensure your application is protected against clickjacking, use our Website Vulnerability Scanner. This tool scans your website for common vulnerabilities, including missing or misconfigured X-Frame-Options headers.

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning for a Website Security check, you'll receive a detailed report highlighting any security issues:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🔒 Enhancing Security with Content Security Policy (CSP)
While X-Frame-Options is effective, modern browsers support the more flexible Content-Security-Policy (CSP) header, which provides granular control over framing.
Add the following header to your responses:
$response->headers->set('Content-Security-Policy', "frame-ancestors 'none';");
This directive prevents any domain from embedding your content, offering robust protection against clickjacking.
🧰 Additional Security Measures
CSRF Protection: Ensure that all forms include CSRF tokens to prevent cross-site request forgery attacks.
Regular Updates: Keep Symfony and all dependencies up to date to patch known vulnerabilities.
Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
📢 Explore More on Our Blog
For more insights into securing your Symfony applications, visit our Pentest Testing Blog. We cover a range of topics, including:
Preventing clickjacking in Laravel
Securing API endpoints
Mitigating SQL injection attacks
🛡️ Our Web Application Penetration Testing Services
Looking for a comprehensive security assessment? Our Web Application Penetration Testing Services offer:
Manual Testing: In-depth analysis by security experts.
Affordable Pricing: Services starting at $25/hr.
Detailed Reports: Actionable insights with remediation steps.
Contact us today for a free consultation and enhance your application's security posture.
3 notes
·
View notes
Text
What is Lead Generation? A Complete Guide for Beginners in 2025
In the ever-evolving world of digital marketing and sales, lead generation remains a foundational strategy for business growth. Whether you’re running a small startup or a large enterprise, understanding what lead generation is—and how to do it effectively—can make or break your customer acquisition efforts.
In this post, we’ll break down what lead generation means, how it works, why it’s important in 2025, and how you can start implementing a successful lead generation strategy today.
What is Lead Generation?
Lead generation is the process of attracting and converting strangers into someone who has indicated interest in your product or service. These individuals are called "leads" and are typically the first step in the sales funnel.
A lead can be anyone who has shared their contact information with your business—whether by filling out a form, subscribing to a newsletter, downloading an eBook, or booking a demo.
The goal of lead generation is simple: build a pipeline of potential customers and nurture them into becoming paying clients.

Why Lead Generation is Crucial in 2025
With buyers becoming more informed and self-directed, the way businesses generate leads has shifted significantly. According to Demand Gen Report (source), 71% of B2B buyers start their journey with a generic search. This makes it more important than ever for businesses to have a strong online presence and provide value from the very first interaction.
Here’s why lead generation is essential in today’s landscape:
It drives business growth: Without leads, you have no sales. And without sales, you have no business.
It builds relationships: Lead generation introduces people to your brand in a helpful, non-intrusive way.
It improves ROI: Targeted lead gen strategies ensure you’re attracting the right audience, not wasting resources.
It supports long-term success: A consistent lead pipeline means predictable revenue and scalable growth.
Types of Leads
Not all leads are the same. Understanding the different types can help you tailor your messaging and approach.
1. Marketing Qualified Lead (MQL)
Someone who has shown interest through content interaction but isn’t ready to buy yet.
2. Sales Qualified Lead (SQL)
A lead who has taken action suggesting they’re ready to talk to your sales team (like booking a call).
3. Product Qualified Lead (PQL)
Typically relevant for SaaS—someone who has used your product (like a free trial) and shows buying intent.
How Lead Generation Works
The lead generation process usually includes these key steps:
1. Attract Visitors
Use SEO, social media, content marketing, and paid ads to bring people to your website or landing pages.
2. Offer Value
Create lead magnets like guides, webinars, checklists, or free tools that your target audience wants.
3. Capture Information
Use forms, chatbots, or popups to collect user details in exchange for your lead magnet.
4. Nurture and Convert
Send follow-up emails, offer more content, or schedule calls to move leads further down the funnel.
Watch: What is Lead Generation?
📹 This beginner-friendly YouTube video explains it well: "7 Keys to Lead Generation & Sales Prospecting for Business Development and B2B Sales"
youtube
Popular Lead Generation Strategies in 2025
✍️ Content Marketing
Publishing helpful blog posts, whitepapers, or videos to attract and educate potential customers.
🔍 Search Engine Optimization (SEO)
Optimizing your site and content to rank high on Google so your target audience can find you.
📧 Email Marketing
Sending personalized, value-packed messages to nurture leads and keep them engaged.
💼 LinkedIn Outreach
Great for B2B businesses—use it to connect with decision-makers and share valuable resources.
📣 Paid Advertising
Run targeted ads on Google, Facebook, or LinkedIn to bring traffic directly to high-converting landing pages.
Tools to Help with Lead Generation
Here are some must-have tools to streamline your lead generation efforts:
HubSpot – CRM and marketing automation for capturing and nurturing leads.
Mailchimp – For sending and automating email campaigns.
OptinMonster – Great for creating popups and opt-in forms.
SEMrush – For keyword research and SEO optimization.
LinkedIn Sales Navigator – Ideal for identifying and connecting with B2B leads.
How Businesses Use Lead Generation Services
Many companies choose to outsource their efforts to experts who specialize in attracting and converting high-quality leads. These lead generation services offer tailored strategies that align with your industry, audience, and growth goals—saving time while maximizing ROI.
Final Thoughts
Lead generation is the lifeblood of any successful business. Whether you’re a marketer trying to fill your sales funnel or an entrepreneur looking to grow your client base, understanding how to attract and convert leads is essential.
By combining valuable content, smart targeting, and nurturing tools, you can build a lead gen system that works for you 24/7. In 2025, the businesses that thrive will be the ones that focus not just on selling—but on providing value from the very first click.
2 notes
·
View notes
Text
I'd rather have been asleep at 1:40am instead of laying there thinking about how uncertain and scared I feel right now, but I was laying there feeling uncertain and scared and realized I have no idea what people that work in offices DO.
I've only worked retail/customer service outside of the military and even while working in an office in the military, I had nothing to do.
At first I was put in one office that didn't need me so they just said "Here... Manage these files." and I was like "..... how, exactly??" and ended up retyping the labels for all of them because some were wrong and there was nothing else for me to do.
Then they gave me the personnel database. I rebuilt it and made it accessible in two days, and that was it. After that, I filled out orders for one person once. The only way I had anything to DO was by becoming the mail clerk which is another customer-facing, cyclically repetitive task that is never done and needs redone in the same way every day. After the mail was done, which took about two hours, I would leave or go sit in my office with nothing to do because the database was my whole job and it was DONE. It wouldn't need changed until the software was updated and that wouldn't be for years.
I had a once-a-week task of making a physical copy of the server which meant going into a closet, popping a tape into a machine, and waiting. I had to sit there with it. There was nothing else to do. I got in trouble for coloring in a coloring book while waiting for the backups to write and I was like "........ What am I SUPPOSED to do, then?????" "Work on the database!" "It's DONE........"
If it's SQL stuff do people sit around until the boss says "Hey, I need to know how much we spent on avocado toast this month." and then whip up a report real quick and wait for the boss to want a report on something else? What about when the boss doesn't need a report?
What do IT people do when things are working smoothly?
I can understand data entry, that would be like "Here we have all these waivers that were signed for the indoor trampoline business and these need plugged into the database manually because the online one was down so they're on paper." or something like that but what about when the online waivers do work what do they do then?
?????
It's like that episode of Seinfeld where George gets an office job but just sits there all day because he has no idea what he's supposed to be doing, no one tells him, and he eventually gets fired because he didn't do anything.
13 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Maximizing Business Insights with Power BI: A Comprehensive Guide for Small Businesses
Maximizing Business Insights Small businesses often face the challenge of making data-driven decisions without the resources of larger enterprises. Power BI, Microsoft's powerful analytics tool, can transform how small businesses use data, turning raw numbers into actionable insights. Here's a comprehensive guide to maximizing business insights with Power BI.
Introduction to Power BI
Power BI is a business analytics service by Microsoft that provides interactive visualizations and business intelligence capabilities. With an interface simple enough for end users to create their own reports and dashboards, it connects to a wide range of data sources.
Benefits for Small Businesses
1. User-Friendly Interface: Power BI's drag-and-drop functionality makes it accessible for users without technical expertise.
2. Cost-Effective: Power BI offers a free version with substantial features and a scalable pricing model for additional needs.
3. Real-Time Data: Businesses can monitor their operations with real-time data, enabling quicker and more informed decision-making.
Setting Up Power BI
1. Data Sources: Power BI can connect to various data sources such as Excel, SQL databases, and cloud services like Azure.
2. Data Modeling: Use Power BI to clean and transform data, creating a cohesive data model that forms the foundation of your reports.
3. Visualizations: Choose from a wide array of visualizations to represent your data. Customize these visuals to highlight the most critical insights.
Customizing Dashboards
1. Tailor to Needs: Customize dashboards to reflect the unique needs of your business, focusing on key performance indicators (KPIs) relevant to your goals.
2. Interactive Reports:Create interactive reports that allow users to explore data more deeply, providing a clearer understanding of underlying trends.
Real-World Examples
Several small businesses have successfully implemented Power BI to gain a competitive edge:
1. Retail: A small retail store used Power BI to track sales trends, optimize inventory, and identify peak shopping times.
2. Finance:A small financial advisory firm employed Power BI to analyze client portfolios, improving investment strategies and client satisfaction.
Integration with Existing Tools
Power BI seamlessly integrates with other Microsoft products such as Excel and Azure, as well as third-party applications, ensuring a smooth workflow and enhanced productivity.
Best Practices
1. Data Accuracy: Ensure data accuracy by regularly updating your data sources.
2. Training: Invest in training your team to use Power BI effectively.
3. Security: Implement robust security measures to protect sensitive data.
Future Trends
Power BI continues to evolve, with future updates likely to include more advanced AI features and enhanced data processing capabilities, keeping businesses at the forefront of technology.
Conclusion
Power BI offers small businesses a powerful tool to transform their data into meaningful insights. By adopting Power BI, businesses can improve decision-making, enhance operational efficiency, and gain a competitive advantage. Partnering with Vbeyond Digital ensures a smooth and successful implementation, maximizing the benefits of Power BI for your business. with Power BI: A Comprehensive Guide for Small Businesses
3 notes
·
View notes
Text
Top 5 Selling Odoo Modules.
In the dynamic world of business, having the right tools can make all the difference. For Odoo users, certain modules stand out for their ability to enhance data management and operations. To optimize your Odoo implementation and leverage its full potential.
That's where Odoo ERP can be a life savior for your business. This comprehensive solution integrates various functions into one centralized platform, tailor-made for the digital economy.
Let’s drive into 5 top selling module that can revolutionize your Odoo experience:
Dashboard Ninja with AI, Odoo Power BI connector, Looker studio connector, Google sheets connector, and Odoo data model.
1. Dashboard Ninja with AI:
Using this module, Create amazing reports with the powerful and smart Odoo Dashboard ninja app for Odoo. See your business from a 360-degree angle with an interactive, and beautiful dashboard.
Some Key Features:
Real-time streaming Dashboard
Advanced data filter
Create charts from Excel and CSV file
Fluid and flexible layout
Download Dashboards items
This module gives you AI suggestions for improving your operational efficiencies.
2. Odoo Power BI Connector:
This module provides a direct connection between Odoo and Power BI Desktop, a Powerful data visualization tool.
Some Key features:
Secure token-based connection.
Proper schema and data type handling.
Fetch custom tables from Odoo.
Real-time data updates.
With Power BI, you can make informed decisions based on real-time data analysis and visualization.
3. Odoo Data Model:
The Odoo Data Model is the backbone of the entire system. It defines how your data is stored, structured, and related within the application.
Key Features:
Relations & fields: Developers can easily find relations ( one-to-many, many-to-many and many-to-one) and defining fields (columns) between data tables.
Object Relational mapping: Odoo ORM allows developers to define models (classes) that map to database tables.
The module allows you to use SQL query extensions and download data in Excel Sheets.
4. Google Sheet Connector:
This connector bridges the gap between Odoo and Google Sheets.
Some Key features:
Real-time data synchronization and transfer between Odoo and Spreadsheet.
One-time setup, No need to wrestle with API’s.
Transfer multiple tables swiftly.
Helped your team’s workflow by making Odoo data accessible in a sheet format.
5. Odoo Looker Studio Connector:
Looker studio connector by Techfinna easily integrates Odoo data with Looker, a powerful data analytics and visualization platform.
Some Key Features:
Directly integrate Odoo data to Looker Studio with just a few clicks.
The connector automatically retrieves and maps Odoo table schemas in their native data types.
Manual and scheduled data refresh.
Execute custom SQL queries for selective data fetching.
The Module helped you build detailed reports, and provide deeper business intelligence.
These Modules will improve analytics, customization, and reporting. Module setup can significantly enhance your operational efficiency. Let’s embrace these modules and take your Odoo experience to the next level.
Need Help?
I hope you find the blog helpful. Please share your feedback and suggestions.
For flawless Odoo Connectors, implementation, and services contact us at
[email protected] Or www.techneith.com
#odoo#powerbi#connector#looker#studio#google#microsoft#techfinna#ksolves#odooerp#developer#web developers#integration#odooimplementation#crm#odoointegration#odooconnector
4 notes
·
View notes
Text
The Ultimate Guide to Mastering Power BI: A Comprehensive Course by Zabeel Institute
In today's data-driven world, businesses are constantly seeking ways to leverage data for better decision-making. One of the most powerful tools to achieve this is Microsoft Power BI, a business analytics solution that empowers organizations to visualize their data, share insights, and make data-driven decisions in real time. If you're looking to gain expertise in this powerful tool, Zabeel Institute's Power BI course in Dubai is the perfect starting point.
What is Power BI?
Power BI is a suite of business analytics tools that allows users to analyze data and share insights. With its user-friendly interface and robust capabilities, Power BI enables both beginners and seasoned professionals to create interactive dashboards and reports. Whether you're dealing with simple data sets or complex analytics, Power BI makes data visualization intuitive and accessible.
Why Learn Power BI?
Learning Power BI opens up a world of opportunities. As businesses increasingly rely on data to drive their decisions, professionals skilled in Power BI are in high demand. Here are some compelling reasons why you should consider enrolling in a Power BI course:
High Demand for Power BI Skills: With the rise of data-driven decision-making, there is a growing demand for professionals who can interpret and visualize data effectively.
Career Advancement: Mastering Power BI can significantly enhance your career prospects, especially in fields such as data analysis, business intelligence, and management.
Versatility: Power BI is versatile and can be applied across various industries, including finance, healthcare, marketing, and more.
Improved Decision-Making: By learning how to create detailed and interactive reports, you can help your organization make informed decisions based on real-time data.
Course Overview: Analyzing Data with Microsoft Power BI
At Zabeel Institute, the Analyzing Data with Microsoft Power BI course is designed to equip you with the skills needed to harness the full potential of Power BI. This comprehensive course covers everything from the basics to advanced data visualization techniques.
1. Introduction to Power BI
The course begins with an introduction to the Power BI environment. You'll learn about the Power BI service, Power BI Desktop, and how to navigate through these tools efficiently. Understanding the interface is crucial for leveraging the full capabilities of Power BI.
2. Connecting to Data Sources
Power BI allows you to connect to a wide range of data sources, including Excel, SQL Server, Azure, and many more. In this module, you'll learn how to import data from various sources and prepare it for analysis.
3. Data Transformation and Cleaning
Before you can visualize your data, it often needs to be cleaned and transformed. This section of the course will teach you how to use Power Query to shape and clean your data, ensuring it's ready for analysis.
4. Creating Data Models
Data modeling is a crucial step in the data analysis process. In this module, you'll learn how to create relationships between different data sets and build a robust data model that supports your analysis.
5. Building Interactive Dashboards
One of Power BI's strengths is its ability to create interactive dashboards. You'll learn how to design visually appealing dashboards that provide meaningful insights at a glance.
6. Advanced Data Visualizations
Once you're comfortable with the basics, the course delves into more advanced visualizations. You'll explore custom visuals, R and Python integration, and how to create sophisticated reports that stand out.
7. DAX (Data Analysis Expressions)
DAX is a powerful formula language in Power BI. This section covers the fundamentals of DAX, enabling you to perform complex calculations and create dynamic reports.
8. Power BI Service and Collaboration
Power BI is not just about creating reports—it's also about sharing and collaborating on those reports. You'll learn how to publish your reports to the Power BI service, set up security, and collaborate with your team.
9. Power BI Mobile App
In today's mobile world, being able to access your reports on the go is essential. The course will show you how to use the Power BI Mobile App to view and interact with your dashboards from anywhere.
10. Best Practices for Power BI
To ensure you're getting the most out of Power BI, the course concludes with a module on best practices. This includes tips on performance optimization, report design, and maintaining data security.
Why Choose Zabeel Institute?
When it comes to learning Power BI, choosing the right institute is crucial. Zabeel Institute stands out for several reasons:
Experienced Instructors: Zabeel Institute's instructors are industry experts with years of experience in data analysis and business intelligence.
Hands-On Training: The course is designed to be highly practical, with plenty of hands-on exercises to reinforce your learning.
Industry-Recognized Certification: Upon completion, you'll receive a certification that is recognized by employers globally, giving you an edge in the job market.
Flexible Learning Options: Whether you prefer in-person classes or online learning, Zabeel Institute offers flexible options to suit your schedule.
Real-World Applications of Power BI
Understanding Power BI is one thing, but knowing how to apply it in the real world is what truly matters. Here are some examples of how Power BI can be used across various industries:
Finance: Create detailed financial reports and dashboards that track key metrics such as revenue, expenses, and profitability.
Healthcare: Analyze patient data to improve healthcare delivery and outcomes.
Retail: Track sales data, customer trends, and inventory levels in real time.
Marketing: Measure the effectiveness of marketing campaigns by analyzing data from multiple channels.
Human Resources: Monitor employee performance, track recruitment metrics, and analyze workforce trends.
Success Stories: How Power BI Transformed Businesses
To illustrate the impact of Power BI, let's look at a few success stories:
Company A: This retail giant used Power BI to analyze customer purchasing behavior, resulting in a 15% increase in sales.
Company B: A financial services firm leveraged Power BI to streamline its reporting process, reducing the time spent on report generation by 50%.
Company C: A healthcare provider used Power BI to track patient outcomes, leading to improved patient care and reduced readmission rates.
Mastering Power BI is not just about learning a tool—it's about acquiring a skill that can transform the way you work with data. Whether you're looking to advance your career, enhance your business's decision-making capabilities, or simply stay ahead in today's data-driven world, Zabeel Institute's Power BI course is the perfect choice.
Don't miss out on the opportunity to learn from the best. Enroll in Zabeel Institute's Power BI course today and take the first step towards becoming a Power BI expert.
Ready to transform your career with Power BI? Enroll in Zabeel Institute's Power BI course now and start your journey towards mastering data analysis and visualization. Visit Zabeel Institut for more information.
2 notes
·
View notes
Text
Power of Data Visualization: A Deep Dive into Microsoft Power BI Services
In today’s data-driven world, the ability to transform raw data into actionable insights is a crucial asset for businesses. As organizations accumulate vast amounts of data from various sources, the challenge lies not just in storing and managing this data but in making sense of it. This is where Microsoft Power BI Services comes into play—a powerful tool designed to bring data to life through intuitive and dynamic visualizations.
What is Microsoft Power BI?
Microsoft Power BI is a suite of business analytics tools that enables organizations to analyze data and share insights. It provides interactive visualizations and business intelligence capabilities with a simple interface, making it accessible to both technical and non-technical users. Whether you are analyzing sales performance, tracking customer behavior, or monitoring operational efficiency, Power BI empowers you to create dashboards and reports that highlight the key metrics driving your business.
Key Features of Microsoft Power BI Services
User-Friendly Interface: One of the standout features of Power BI is its user-friendly interface. Even those with minimal technical expertise can quickly learn to create reports and dashboards. The drag-and-drop functionality allows users to effortlessly build visualizations, while pre-built templates and AI-powered insights help accelerate the decision-making process.
Data Connectivity: Power BI supports a wide range of data sources, including Excel, SQL Server, cloud-based data warehouses, and even social media platforms. This extensive connectivity ensures that users can pull in data from various systems and consolidate it into a single, coherent view. The ability to connect to both on-premises and cloud-based data sources provides flexibility and scalability as your data needs evolve.
Real-Time Analytics: In today’s fast-paced business environment, real-time data is critical. Power BI’s real-time analytics capabilities allow users to monitor data as it’s collected, providing up-to-the-minute insights. Whether tracking website traffic, monitoring social media engagement, or analyzing sales figures, Power BI ensures that you are always equipped with the latest information.
Custom Visualizations: While Power BI comes with a robust library of standard visualizations, it also supports custom visuals. Organizations can create unique visualizations that cater to specific business needs, ensuring that the data is presented in the most effective way possible. These custom visuals can be developed in-house or sourced from the Power BI community, offering endless possibilities for data representation.
Collaboration and Sharing: Collaboration is key to making data-driven decisions. Power BI makes it easy to share insights with colleagues, whether through interactive reports or shared dashboards. Reports can be published to the Power BI service, embedded in websites, or shared via email, ensuring that stakeholders have access to the information they need, when they need it.
Integration with Microsoft Ecosystem: As part of the Microsoft ecosystem, Power BI seamlessly integrates with other Microsoft products like Excel, Azure, and SharePoint. This integration enhances productivity by allowing users to leverage familiar tools and workflows. For example, users can import Excel data directly into Power BI, or embed Power BI reports in SharePoint for easy access.
The Benefits of Microsoft Power BI Services for Businesses
The adoption of Microsoft Power BI Services offers numerous benefits for businesses looking to harness the power of their data:
Enhanced Decision-Making: By providing real-time, data-driven insights, Power BI enables businesses to make informed decisions faster. The ability to visualize data through dashboards and reports ensures that critical information is easily accessible, allowing decision-makers to respond to trends and challenges with agility.
Cost-Effective Solution: Power BI offers a cost-effective solution for businesses of all sizes. With a range of pricing options, including a free version, Power BI is accessible to small businesses and large enterprises alike. The cloud-based service model also reduces the need for expensive hardware and IT infrastructure, making it a scalable option as your business grows.
Improved Data Governance: Data governance is a growing concern for many organizations. Power BI helps address this by providing centralized control over data access and usage. Administrators can set permissions and define data access policies, ensuring that sensitive information is protected and that users only have access to the data they need.
Scalability and Flexibility: As businesses grow and their data needs evolve, Power BI scales effortlessly to accommodate new data sources, users, and reporting requirements. Whether expanding to new markets, launching new products, or adapting to regulatory changes, Power BI provides the flexibility to adapt and thrive in a dynamic business environment.
Streamlined Reporting: Traditional reporting processes can be time-consuming and prone to errors. Power BI automates many of these processes, reducing the time spent on report creation and ensuring accuracy. With Power BI, reports are not only generated faster but are also more insightful, helping businesses to stay ahead of the competition.
Empowering Non-Technical Users: One of Power BI’s greatest strengths is its accessibility. Non-technical users can easily create and share reports without relying on IT departments. This democratization of data empowers teams across the organization to take ownership of their data and contribute to data-driven decision-making.
Use Cases of Microsoft Power BI Services
Power BI’s versatility makes it suitable for a wide range of industries and use cases:
Retail: Retailers use Power BI to analyze sales data, track inventory levels, and understand customer behavior. Real-time dashboards help retail managers make quick decisions on pricing, promotions, and stock replenishment.
Finance: Financial institutions rely on Power BI to monitor key performance indicators (KPIs), analyze risk, and ensure compliance with regulatory requirements. Power BI’s robust data security features make it an ideal choice for handling sensitive financial data.
Healthcare: In healthcare, Power BI is used to track patient outcomes, monitor resource utilization, and analyze population health trends. The ability to visualize complex data sets helps healthcare providers deliver better care and improve operational efficiency.
Manufacturing: Manufacturers leverage Power BI to monitor production processes, optimize supply chains, and manage quality control. Real-time analytics enable manufacturers to identify bottlenecks and make data-driven adjustments on the fly.
Conclusion
In an era where data is a key driver of business success, Microsoft Power BI Services offers a powerful, flexible, and cost-effective solution for transforming raw data into actionable insights. Its user-friendly interface, extensive data connectivity, and real-time analytics capabilities make it an invaluable tool for organizations across industries. By adopting Power BI, businesses can unlock the full potential of their data, making informed decisions that drive growth, efficiency, and innovation.
5 notes
·
View notes
Text
As a Cyber Security Expert, I will provide penetration Testing and WordPress Malware Removal services. Those are my best and strongest skills. I can combine the power of manual and automated penetration tests to remove all types of malware and viruses from any WordPress website.
My Services on penetration testing:
✅I will test File Uploads, SQL injection, XSS, CSRF, Authentication, Access Control, Information Disclosure, RFI, RCE, LFI, Brute Force, SSRF, and many more Bugs.
✅I will test your website and give you a professional and premium testing report that help you fix this vulnerability.
✅Network devices (Servers, switches, routers) Penetration Testing services.
✅I will test manual and automated both.
✅Mobile Application Penetration Testing.
My services for WordPress Malware Removal:
✅I will remove all types of malware and viruses from hacked WordPress websites
✅fix redirect issues where the website redirects to another website and URLs.
✅remove malware from the server of C-Panel
✅Reactive suspended hosting account.
✅Remove Japanese or Chinese Spam Links.
✅Remove all backdoors and phishing scripts.
✅Install many security plugins.
✅Updates all Plugins and Themes on your website.
Why work with me:
⭐️I will use multiple vulnerability scanners.
⭐️Provide unlimited modifications and retesting for the issues that have been fixed.
⭐️No false Positives on the Report and give the recommendations.
⭐️On-time delivery.
Me on Fiverr: https://www.fiverr.com/safety_hub?up_rollout
Let me work with you. I am a professional cybersecurity specialist with 3years of experience. I will give you the best service. I hope you will be satisfied.
Thank You.
4 notes
·
View notes
Text
Client Work(Android)|CST2335_Final_GroupProject_F22 2022Soccer match highlights part Output Video|Algonquin College
youtube
Programming Assignment Helper For International Students 𝐖𝐞 𝐚𝐫𝐞 𝐡𝐞𝐥𝐩𝐢𝐧𝐠 𝐬𝐭𝐮𝐝𝐞𝐧𝐭𝐬 𝐨𝐮𝐭! 𝐏𝐫𝐨𝐯𝐢𝐝𝐢𝐧𝐠 𝐬𝐞𝐫𝐯𝐢𝐜𝐞𝐬 𝐟𝐨𝐫 𝐬𝐜𝐡𝐨𝐨𝐥/𝐜𝐨𝐥𝐥𝐞𝐠𝐞/𝐮𝐧𝐢𝐯𝐞𝐫𝐬𝐢𝐭𝐲 𝐚𝐬𝐬𝐢𝐠𝐧𝐦𝐞𝐧𝐭𝐬, 💻 𝐜𝐨𝐮𝐫𝐬𝐞𝐰𝐨𝐫𝐤,𝐥𝐚𝐛 𝐩𝐫𝐨𝐣𝐞𝐜𝐭𝐬/𝐫𝐞𝐩𝐨𝐫𝐭𝐬, 𝐞𝐱𝐚𝐦𝐬, 𝐪𝐮𝐢𝐳𝐳𝐞𝐬, 𝐝𝐢𝐬𝐬𝐞𝐫𝐭𝐚𝐭𝐢𝐨𝐧𝐬,𝐭𝐡𝐞𝐬𝐢𝐬; 𝐚𝐬 𝐰𝐞𝐥𝐥 𝐚𝐬 𝐩𝐫𝐨𝐨𝐟𝐫𝐞𝐚𝐝𝐢𝐧𝐠, 𝐞𝐫𝐫𝐨𝐫 𝐜𝐨𝐫𝐫𝐞𝐜𝐭𝐢𝐨𝐧, 𝐚𝐧𝐝 𝐛𝐮𝐠-𝐟𝐢𝐱𝐢𝐧𝐠. 𝐀𝐥𝐬𝐨 𝐝𝐨𝐢𝐧𝐠 𝐬𝐨𝐟𝐭𝐰𝐚𝐫𝐞 𝐜𝐨𝐦𝐩𝐚𝐧𝐲, 𝐚𝐠𝐞𝐧𝐜𝐢𝐞𝐬 𝐩𝐫𝐨𝐟𝐞𝐬𝐬𝐢𝐨𝐧𝐚𝐥 𝐩𝐫𝐨𝐣𝐞𝐜𝐭𝐬📊
We specialize in the following fields: 📘 Computer Science🔖Programming: 🔖 Python 🔖 Java 🔖 C 🔖 C++ 🔖 C# 🔖 Ruby 🔖 Matlab 🔖 HTML | CSS | JavaScript 🔖 PHP 🔖 CSS 🔖 Databases | SQL 🔖 Android Development 🔖 Algorithms 🔖 Swift 🔖 Networks | CCNA 🔖All kinds of IT work 📘EEE 📘Mechanical Engineering 📘Civil📘ALL type of academic services 📘 Mathematics 📘 Statistics 📘 Marketing 📘 Management 📘 Accounting 📘 Psychology 📘 Business 📘 Economics 📘 Pharmacology 📘 Engineering 📘 Finance 📘 Nursing 📘 Sociology 📘 Literature 📘 Health & Social Care 📘Writing 📘Thesis 📘Report
we provide all type of academic services 🟩Assignments 🟩Projects 🟩Exams 🟩Quizz 🟩Lab 🟩Thesis 🟩Dissertation 🟩Reports 🟩Final year projects 🟩Programming 🟩Coursework 🟩Proposal Writing 🟩Essay writing 🟩Article writing 🟩LSAT exam 🟩Research paper writing 🟩Term paper 🟩Conference Paper 🟩Case study 🟩Proofreading 🟩DATA Analysis 🟩Stata Analysis 🟩Spss 🟩Review articles 🟩Referencing 🟩Correction 🟩Questionnaries 🟩Formatting 🟩Presentation 🟩Synopsis 🟩Ai Removal 🟩Paraphrasing
For take our services contact with us Whatsapp/Telegram:+8801772432396 whatsapp profile link: https://wa.me/+8801772432396 https://wa.me/message/PYHN7PIZEHNQO1 Email 1:[email protected] Email 2:[email protected] Discord username:programmingassignmenthelperbd or Discord username:academiccourseworkservices Discord Server profile link:https://discord.com/invite/C6DQUbgH2w Instagram:https://www.instagram.com/programmingassignmenthelperbd/ Instagram Username:programmingassignmenthelperbd Telegram Account: https://t.me/programmingassignmenthelperbd Telegram Username:@programmingassignmenthelperbd Telegram Phone Number:+8801772432396 skype profile link: https://join.skype.com/invite/w0k4c2of6ts3 skype name:live:.cid.e36c1f8fe9b0bbfd Printerest Account:https://www.pinterest.com/programmingassignmenthelperbd/ Printerest Username:programmingassignmenthelperbd Twitter Account:https://twitter.com/assignmentintl Twitter Username:assignmentintl Tiktok Account:https://www.tiktok.com/@assignmenthelperbd Tiktok Username:assignmenthelperbd Linkedin Company Page: https://www.linkedin.com/showcase/assignment-writing-for-students https://www.linkedin.com/company/programming-assignment-exam-quiz-project-report-helper-for-international-students Facebook Compnay Page: https://www.facebook.com/programmingassignmenthelperforinternationalstudent/ Website:https://academiccourseworkservices.com/
Our Student Review /Client Feedback:https://drive.google.com/file/d/16Ametl8UY-RehW3Q4jYZmM1DxioCG3J8/view?usp=sharing
𝐎𝐮𝐫 𝐰𝐨𝐫𝐤 𝐩𝐨𝐫𝐭𝐟𝐨𝐥𝐢𝐨 𝐥𝐢𝐧𝐤: https://www.youtube.com/channel/UCyOlJCraJuVs6oBUIYOoz0Q?sub_confirmation=1
𝗔𝗹𝗴𝗼𝗻𝗾𝘂𝗶𝗻 𝗰𝗼𝗹𝗹𝗲𝗴𝗲 𝗮𝗽𝗽𝗹𝗶𝗲𝗱 𝗮𝗿𝘁𝘀 𝗮𝗻𝗱 𝘁𝗲𝗰𝗵𝗻𝗼𝗹𝗼𝗴𝘆 𝘄𝗼𝗿𝗸 𝗽𝗼𝗿𝘁𝗳𝗼𝗹𝗶𝗼 𝗹𝗶𝗻𝗸:https://www.youtube.com/playlist?list=PL16VzvGeViA0g1ql7OVnoaNCGgZCZG0Lx
Regards Assignment Helper [Programming Assignment Helper For International Students]
#CST8227#CST2335#CST8333#CST8288#AlgonquinCollege#Android#Java#Python#Enterprise_Application_Programming#Graphical_Interface_Programming#Programming_Language_Research#students_work_output_video#client_work_output_video#cobol#Network_Programming#System_Analysis_and_Design#canaduniversity#canada#internationalstudents#students#computersciencestudents#assignmenthelper#labhelper#academichelper#thesishelper#dissertationhelper#essayhelper#reporthelper#ottawastudents#torontostudents
1 note
·
View note
Text
Decoding Data Roles: A Comprehensive Guide to Data Analysts and Data Scientists
In today's data-driven landscape, the roles of data analysts and data scientists share some similarities but differ significantly in terms of their focus, skill sets, and the scope of their work. As organizations increasingly recognize the importance of these roles, the demand for skilled professionals has led to the emergence of various data science institutes. Let's explore the nuances that differentiate a data analyst from a data scientist, while also considering the importance of choosing the best Data Science institute for a comprehensive education in this field.
Let's delve into the nuances that differentiate a data analyst from a data scientist.
1. The Scope of Work:
Data analysts and data scientists play distinct roles when it comes to the scope of their work.
Data Analyst:
Data analysts are the interpreters of historical data. Their primary focus lies in uncovering trends, generating reports, and providing insights that aid day-to-day operations within an organization. They work with structured data, employing tools such as Excel, SQL, and visualization tools like Tableau or Power BI. The problems they address are typically well-defined and pertain to specific queries.
Data Scientist:
Data scientists, on the other hand, have a broader scope. While data analysis is a part of their work, they are also deeply involved in more complex tasks. This includes developing machine learning models, engaging in predictive modeling, and conducting advanced analytics. Data scientists deal with unstructured or semi-structured data, addressing more intricate and less defined problems. Their role extends beyond routine data interpretation to include exploratory data analysis, hypothesis testing, and the development of algorithms.
2. Skill Sets:
The skill sets required for data analysts and data scientists highlight the differences in their roles.
Data Analyst:
Data analysts need a strong foundation in statistical analysis, data cleaning, and proficiency in tools like Excel and SQL. While they may have some programming skills, they typically do not require the same level of expertise in machine learning. Visualization tools are a key part of their toolkit, enabling them to communicate insights effectively.
Data Scientist:
Data scientists require a more comprehensive skill set. They need a deep understanding of statistics, machine learning, and programming languages such as Python or R. Proficiency in data preprocessing, feature engineering, model selection, and evaluation is essential. Data scientists often work with big data technologies and possess advanced knowledge of analytical techniques, enabling them to create and implement complex algorithms.
3. Problem Complexity:
The complexity of problems tackled by data analysts and data scientists varies significantly.
Data Analyst:
Data analysts generally deal with well-defined problems and questions. Their focus is on providing answers to specific queries based on structured data. The insights they provide contribute to the day-to-day decision-making processes within an organization.
Data Scientist:
Data scientists thrive on addressing more complex and less structured problems. They engage in exploratory data analysis, hypothesis testing, and the creation of models capable of handling unstructured or semi-structured data. The solutions they develop often contribute to strategic decision-making, driving innovation, process optimization, and the creation of new products or services.
4. Business Impact:
The impact of data analysts and data scientists on an organization's decision-making processes is another area of distinction.
Data Analyst:
The insights provided by data analysts are integral to operational improvements and day-to-day decision-making. Their work contributes to the efficiency and effectiveness of ongoing processes within the organization.
Data Scientist:
Data scientists play a more strategic role in decision-making. Their insights have a broader impact on the organization, driving innovation, shaping long-term strategies, and contributing to the development of new products or services. The impact of a data scientist's work extends beyond routine operations, influencing the overall direction of the organization.
5. Educational Background:
The educational backgrounds of data analysts and data scientists reflect the differences in the complexity of their roles.
Data Analyst:
Data analysts may have a background in fields such as statistics, mathematics, economics, or business. While a bachelor's degree is often sufficient, some roles may require a master's degree.
Data Scientist:
Data scientists typically hold more advanced degrees, such as a master's or Ph.D., in fields like computer science, statistics, or data science. The nature of their work demands a deeper understanding of advanced mathematical and statistical concepts, as well as expertise in machine learning.
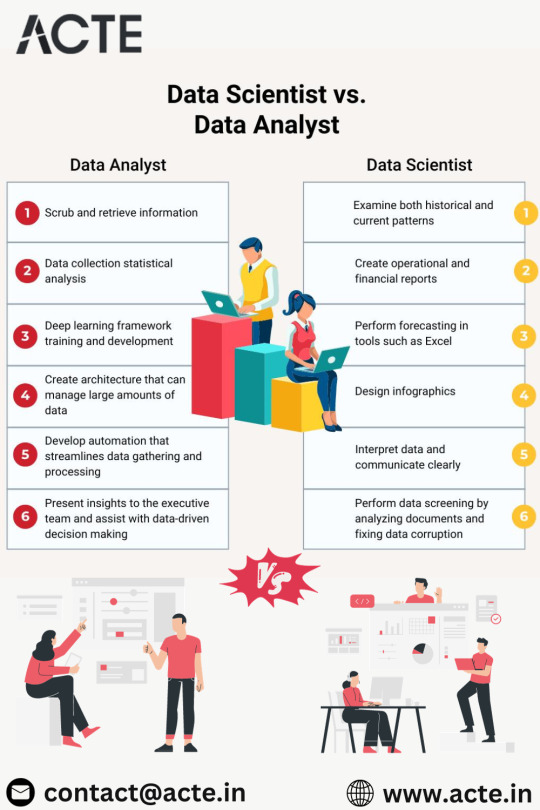
In conclusion, the divergence between data analysts and data scientists is profound, marked by distinctions in complexity, skill prerequisites, and organizational impact. Data analysts concentrate on offering actionable insights from existing data, enhancing day-to-day decision-making processes. In contrast, data scientists embark on tackling intricate issues, employing advanced analytics and machine learning to derive predictive and prescriptive insights that play a pivotal role in shaping an organization's strategic direction.As the demand for skilled professionals in these domains grows, the relevance of quality education becomes paramount. Choosing the best Data Science courses in Chennai is a crucial step in acquiring the necessary expertise for a successful career in the evolving landscape of data science.
3 notes
·
View notes