#vpn software solutions
Explore tagged Tumblr posts
Text
Start Your Own Branded VPN Business with white-label software Solutions
Unlock the Full Potential of Your VPN Business with Smarters' All-in-One Software Suite, which includes a robust billing panel, customizable VPN app, and professionally crafted website. Using our advanced, tailored solutions, you can boost security, simplify management, and scale with confidence.
📞 Get in touch with us today
0 notes
Text

Are you seeking top-notch security for your iPhone? SwizzVPN, the leading VPN app tailored for iPhones, is your answer. Connect to servers across 50+ global locations, including Switzerland, and benefit from features such as no-registration access, unlimited speed, bandwidth, and device connections. Leverage Switzerland's strict privacy laws for unparalleled protection. Download SwizzVPN now to seamlessly access global servers and enjoy unrestricted browsing on your iPhone.
0 notes
Text
Grow Your VPN Business with Smarters' VPN Software Solution

Starting your own VPN services business can be a game-changer for your success. By utilizing Smarters' VPN software solution, you can easily establish your own VPN enterprise with dedicated servers. With your own VPN business, you can provide your customers with secure and reliable internet access. You'll have access to all the necessary tools for your business, including a
Custom VPN App,
Custom VPN Website, and
Smarters VPN Panel
These powerful tools can help you save time and money and enable you to concentrate on delivering the best VPN services to your customers. All you have to do is purchase a VPS or dedicated server, and Smarters' software will take care of everything else for you. With Smarters' VPN software solution, you can provide your customers with the most outstanding VPN services available. So, don't let this opportunity pass you by! Contact us today and learn how you can benefit from Smarters' game-changing VPN software solution for your VPN services business.
Visit: https://shorturl.at/blHP2
#VPN Software Solution#vpnsoftwaresolution#vpnresellerpanel#smarters billing panel#vpn reseller panel
0 notes
Text
Hello everyone, friends, I need to talk to you about something important today...
As you know, I live in Turkey, and if you are Turkish like me, or have Turkish acquaintances who are not Turkish, or follow the developments in Turkey, you may have heard that access to several games and social media platforms in Turkey has been blocked these days.
These applications are not currently accessible in my country;
-X(Twitter)
- Instagram
-Roblox
-Wattpad
Apart from this, I don't know if there are any access blocks for other applications yet, but the Discord application will also be blocked today, and it is also planned to block the application called Tik Tok on August 13.
What I really want to talk about is that if access to the Tumblr application is blocked, I may suddenly have to leave the account and this time I cannot use my other account. I am really sorry for that, but unfortunately there is nothing I can do...
There were indeed valid reasons for these bans, but what really makes me angry is that they were immediately banned without doing anything about it...
We had no news about this. We just woke up this morning and.. BOOM! We cannot use any applications!
I cannot understand why they blamed everyone and did this instead of just closing the accounts that violated these bans. Moreover, these things do not work in this order, first a warning is given, then the accounts that do this are closed. If there is still no solution, then access to the applications will be blocked.
However, despite such an effective solution, they instantly close random applications without notifying people...
I'm not saying that applications shouldn't be closed, there were legitimate reasons to close them, but I'm trying to explain that they can't do it suddenly like this.
Long story short, there may be an access block to the Tumblr application in Turkey for any reason, so I'm telling you this so you don't worry if I don't post to the account for a long time.
Of course you will ask me this
"Why don't you use VPN?"
(For those who don't know: Vpn: A kind of interesting software that can allow you to use prohibited applications and sites)
Yes, there are people using VPN, but the problem is; Ever since this app access blocking scandal began, scammers have been using it to their advantage. They put people in an even more difficult situation by stealing people's private information such as bank accounts with fake VPN applications:(
Unfortunately, this situation also puts people in a difficult economic situation; There were many people selling on Instagram and making money by writing code on Roblox, and now they are all in a difficult situation. There has been a major unemployment problem in our country for a long time. Even people who got into the best universities cannot find a job, so now they had an advantage such as technology, but now it is being taken away from them. There is a high probability that applications such as YouTube and Facebook will be closed. Some YouTube users have already left their accounts, some People started sending videos titled "Farewell video before YouTube closes"...
I hope these problems will end somehow, because despite everyone's objections, my own country's rulers still do not listen to their own people!
I hope I don't have to leave my account, but if something happens, I apologize again, but as I said, there is nothing I can do :(
That's all I can say about this subject. If you have any other questions, you can ask me. I will try to help you as much as I can. Goodbye for now.
19 notes
·
View notes
Text
Who Am I?
An old woman who has been in this world and on this line for a very long time. I believe in compassion, community, and revolutionary kindness. You can call me Asha, or tía if you need an auntie. I would be honored.
I noticed recently that I have aggregated a lot of helpful resources on this blog and decided to list them out below for easy finding. A lot of these are not put together by me, but by the kind people on this site and many others. It is always good to thank them for their time and helpfulness if you have the energy to do so!
Please feel free to ask me for help if you need something that isn't here or gently nudge me if there is something here that is outdated/incorrect/broken/no longer helpful.
Help yourself, then help each other. Read good books, learn useful skills, give long hugs, and never, ever talk to pigs.💜
SO IF YOU'VE EVER ASKED, "WHAT DO I DO...?"
‼️IF YOU NEED HELP:
Auntie Network via Reddit
LGBT National Help Hotline
Trans Lifeline
The Trevor Project (Under 25)
Crisis Text Line
List of Worldwide Crisis Hotlines via Reddit
Rebloggable List of Worldwide Crisis Hotlines (please be kind and add your country if it is not present)
Explain Like I'm Scared: Compassionate task assistance for people with autism or anxiety, though everyone is welcome to request. Recommended by Tumblr user warriorsdebt.
IF YOU NEED...
A Mom for a Minute via Reddit
A Dad for a Minute via Reddit
A Safe, Inclusive Place for Men via Reddit
IF YOU WANT TO HELP SOMEONE ELSE:
Fundraiser Links for Palestine via GazaVetters
Watch & Support No Other Land
One Simple Wish
Food Not Bombs
Habitat for Humanity
Food Plant Solutions: End Malnutrition & Food Insecurity
POLITICS & RESISTANCE:
‼️You Should Be Using a VPN
‼️UK: Protests Against The Supreme Court for Trans Rights
Protests & Security Resource Links via anarchopuppy
How to report a church to the IRS for abusing tax exempt status
Michael Moore's Sicko -- Free on Youtube
5 Calls
Get Involved with 350.org
Guide to Living Solar Punk via Tumblr (broken links have been updated and sorted into the appropriate categories on this list)
ACAB BASICS:
‼️Don't Talk to the Police
‼️Immigrant Legal Resource Center: Links to Red Cards
WRITING & PUBLISHING:
Resources for Self-Publishing
Writing Resources That Are Not Google
My List of Free Writing & Publishing Software
Paid Publishing Software: Scrivener, Vellum (Mac Only)
A World Building Checklist
Jami Gold's Worksheets for Writers
Vintage Girls' Names via byjove
Top Names by Decade via US Social Security
Everything You Need to Know About Writing Stab Wounds
Randomize a Superpower
More Writing Resources...
ART & CRAFTING:
Blender 3D: Noob to Pro
Make Art Without Adobe
Making Stuff & Doing Things: DIY Zines for Just About Everything
Fat Photo Reference
Art References & Resources Links via midwinterhunt
Filterable Picrew Database because fuck using AI
Royalty-Free Elements
GIFMAKING FOR BEGINNERS
Makerspace Map
Repair Café
MUSIC:
LMMS: free digital audio workstation
Learn Music Theory
Train Your Ears
Cigar Box Nation
AGRICULTURE, HERBALISM, & BOTANY:
Edible Plants of the World
Food Forest Nursery: Find a Community Garden
Food Not Lawns
Research on Regenerative Agriculture by Amir Kassam
The carbon footprint of Conservation Agriculture
Medicinal Plants
A Visual Guide to Mushrooms
Folk Names for Herbs
Poison Path Plants
SUPPORT LIBRARIES:
Queer Liberation Library
Quatrefoil Library
OR JUST READ (PLEASE JUST READ THEY REALLY DON'T WANT YOU TO DO THAT):
M/a/rxists.org: delete slashes please. Promoted to first because apparently tumblr does not want me to link to this site, fascinating!
thean/a/rchistlibrary.org: same deal as above.
Anna's Archive
Project Gutenberg
The Literature Network
Bartleby: links to reference, also includes verse, fiction, & non-fiction texts. Please note that their homework help tool is banned by certain academic organizations.
Project Muse: Many free, peer-reviewed resources on Humanities & Social Sciences
Library of Congress: Free to Use
Granta
The Morning News
THINGS THAT WILL SIMPLY MAKE LIFE BETTER:
Get your meds cheaper!
Remember to stretch!
File your taxes for free!
How to buy things from Japan
Re-examine these logical fallacies!
TECHNOLOGY:
You Should Be Using a VPN
Manocha Academy Coding Classes: 7 Day Free Trial, No Card Required.
Free Resources from Code Academy
People far smarter than me discuss how NOT to kill a computer
Physical Health for Your Desktop
Infosec Links & Resources
NAVIGATING DISABILITY & RESOURCES:
How to Answer 21 Tricky Disability Questions
PHARMACY & HOSPITAL BILL SAVINGS:
Dollar For: non-profit that will assist you with applying to programs that will discount or forgive medical bills.
Scriptcycle
Walgreens Rx Savings Finder
GoodRx
SingleCare (HRT coupons!!)
Article: How to Pay Hospital Bills When You're Flat Broke
PRACTICAL SKILLS:
Morse Code made easy
Japanese Language & Culture Resources
Language learning alternatives to DuoLingo!
Make Lockpicks from Stuff You've Got In Your Garage
Learn to Lockpick
🏴☠️
You Should Be Using a VPN
Identity Generator
Cobalt: download videos or images from websites
Why You Shouldn't Pay For The Sims
3 notes
·
View notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
Best Business Software Tools in 2024
The right software tools can help increase productivity, draft operations more efficiently and promote company growth in today's high-paced business environment. Whether you are a start-up or an existing enterprise the following business software is necessary to improve different areas of your business.
1. Project Management: ClickUp

It is a feature-laden project manager that lets you handle tasks, projects, and workflows of all types. Its ease of use and user-friendly interface, complimented with diverse dashboards cater to audiences between small teams and large organizations. Task assignments, time tracking, goal setting, and collaboration options allow you to stop hopping between spreadsheets and emails so your projects are complete efficiently.
2. CRM–– Zoho CRM
Zoho CRM — Your Intelligent Customer Relationships Management System. Among other features, it has lead management, sales automation, and analytics to make sales performance improve on a consistent streamline both administrative aspect as well as customer satisfaction. Due to its integration capabilities with other Zoho products, as well as most third-party applications, It has become a flexible option for businesses that are ready to supercharge their customer relationship management.
3. Accounting: Zoho Books

Zoho Books- The Best Accounting Software for Business Owners Invoicing, expense tracking and financial reporting are some of its features. You can also rest assured that your taxes are being handled correctly and always have the latest view of your financial health to help you manage your finances better.
4. HR Management: monday. com HR
It is a complete human resources management software that helps companies to better structure their workforce. This system provides with facilities like employee on boarding, performance tracking, payroll management etc. With the platform's ease of use, UI simplicity, and automation capabilities in HR processes that would otherwise take hours away from key HR initiatives.
5. Payroll: OnPay

OnPay is an excellent payroll software for businesses of all sizes. It is a cloud payroll software for businesses that ensures complete compliance and automation of top-class payroll calculations, tax filings & employee payments. Additionally, OnPay provides HR and benefits management tools, effectively providing a full-fledged employee pay management solution.
6. Point-of-Sale (POS): eHopper
Versatile Point of Sale Software for Businesses Up To Mid-Sized It offers services like Inventory management, sales tracking and customer management. This makes eHopper a perfect choice for businesses that intend to simplify their sales operations using an affordable and intuitive POS system.
7. Inventory Management: Cin7
While there are plenty of other inventory management systems available, Cin7 stands out as one of the most popular options for small to mid-size businesses (SMBs) looking to get their stock levels, orders and supply chain operations under control. These functionalities consist of real-time inventory monitoring, order processing and e-commerce platform integration. With the powerful feature set of Cin7, businesses can keep inventory at an optimal level and fulfill customer demands to the hilt.
8. Website Builder: Weebly
Weebly is the website builder that you can also use to build your site or blog. It has lots of customizable templates, drag-and-drop functionality, and e-commerce ready to go. With Weebly, you can create a professional website even if you are a tech noob and give your business the relevant online visibility it needs.
9. Recruiting: ZipRecruiter

ZipRecruiter: Popular rated job search app for businesses on board. They provide hiring solutions through features like job posting candidates filtering and tracking the application. AI-powered matching from ZipRecruiter surfaces more relevant candidates to businesses faster.
10. VPN: NordVPN
It is a secure, encrypted VPN application that will make sure that you and your business stay safe as you work with the web. It provides features of encrypted connections, threat protection and global server access as well. In this way, It guarantees secure data in companies and privacy on internet.
Conclusion
The business software tools a company uses are very important to increase productivity and power growth. The above-mentioned tools are some of the best & flexible according to the fact which can assist businesses for any sized groups and help them attain their desired objectives. Implementing these tools in your operations can also help speed up processes and lead to higher customer satisfaction, as well as allow you to be on top of the competition.
#business#business growth#innovation#startup#entrepreneur#100 days of productivity#project management#sales#payroll#hr management#hr software#hr services#ai#artificial intelligence#technology#tech#techinnovation
3 notes
·
View notes
Text
Simplify Order & Service Management with VPN Billing Panel

Looking for a smarter way to handle your VPN orders and services? With a custom VPN Billing Panel, you can manage subscriptions, user accounts, invoices, and more - all from one simple dashboard. It keeps everything organized so you can save time and focus on growing your business. 👉 Launch Your Custom VPN Billing Panel – Everything You Need to Manage Services & Orders. Contact us to start!
0 notes
Text

Discover SwizzVPN, a Swiss-based VPN offering a lifetime unlock option. It operates in VPN-blocked countries, requiring no registration—simply tap to connect. Accessible on the App Store for iPhone, iPad, Mac, and Apple TV. Prioritize research, considering user reviews and reputation. For details, visit our website for seamless connectivity.
1 note
·
View note
Text
White Label VPN SOFTWARE SOLUTION For VPN Startups
Managing a VPN business can be a daunting task, with so many things to keep track of. Luckily, Smarters VPN panel is here to help. With this powerful tool, VPN service providers can easily manage their VPN servers, clients, resellers, and packages. The panel automates many administrative tasks, reducing workload and freeing up time for other important activities. But don't worry, if manual management is preferred, this panel also allows for that. What makes Smarters VPN Panel different is its hybrid approach, offering both automation and manual options. It's the perfect solution for VPN businesses looking to streamline their operations and deal with clients more easily. At Smarters, we're dedicated to providing complete VPN software solutions for businesses, so you can focus on what really matters.
Smarters VPN Billing Panel
Manage VPN Servers, VPN Clients, VPN Reseller, VPN Package automatically. This Smarters VPN Panel contains the Shopping Cart, Support ticket system, Client area, Admin Area. This will provide you with a complete VPN client solution.
Smarters VPN Custom App
The app that allows your VPN clients to connect your VPN that is managed by a smarters vpn billing panel. It’s a fully customizable & brand-able app for all VPN service providers.
Smarters VPN Website
It’s a white Label Website that is easy to customize, easy to use and no coding expertise is needed.
Starting a VPN business has never been easier! With our complete VPN Software Solution, you can easily grow your business and manage it with ease. All you need is a dedicated server or VPS, and our Smarters VPN Management panel will take care of everything for you. Our solution is designed to make things as simple as possible for you, so you can focus on running your business and serving your customers. With our help, you can build a successful VPN business in no time!
For more details, you can visit our official website here:https://shorturl.at/eCQWZ
0 notes
Note
safari uses webkit which is open source. as evil as apple are they do have a genuine incentive to protect your data. it hurts their biggest competitor: Google. The more privacy they give users the more harm they do to Google
This...doesn't mean anything to the discussion. Chromium is open source as well, but "open source" does not always equal "good for users," when it's forced down your throat in a closed ecosystem. I mean, yeah, you can build a different version of a browser using webkit, but apple *still tries hard to lock users out of adblocking extensions, especially on mobile*. It's not apple being good by using webkit, it's apple using webkit as a shield from criticism when it doesn't matter because you can still use their One True Browser on mobile. Go ahead, build your own version, try to use it on an ios device without paying for a developer account or doing the weird-ass "sideloading" that requires setting up a development server on your PC that you have to connect to every 7 days or they lock you out of all non-appstore apps. Give it a shot.
The way adblockers, currently, work on safari on mobile isn't an extension with filter lists, but an entire complete internal VPN that itself has filter lists, bypassing the engine. That,,,works, but isn't how it used to be, breaks other private VPN solutions, and that's intentional. Hell, they 'accidentally' broke it again with the ios17 update in july, and it took a full week before they fixed it. I see no reason to stan a corporation. Microsoft uses open source software in windows 11. Should I defend windows as whole because they did so?
6 notes
·
View notes
Text
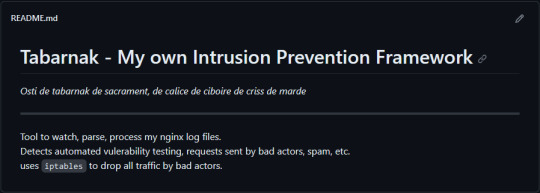
(this is a small story of how I came to write my own intrusion detection/prevention framework and why I'm really happy with that decision, don't mind me rambling)
Preface
About two weeks ago I was faced with a pretty annoying problem. Whilst I was going home by train I have noticed that my server at home had been running hot and slowed down a lot. This prompted me to check my nginx logs, the only service that is indirectly available to the public (more on that later), which made me realize that - due to poor access control - someone had been sending me hundreds of thousands of huge DNS requests to my server, most likely testing for vulnerabilities. I added an iptables rule to drop all traffic from the aforementioned source and redirected remaining traffic to a backup NextDNS instance that I set up previously with the same overrides and custom records that my DNS had to not get any downtime for the service but also allow my server to cool down. I stopped the DNS service on my server at home and then used the remaining train ride to think. How would I stop this from happening in the future? I pondered multiple possible solutions for this problem, whether to use fail2ban, whether to just add better access control, or to just stick with the NextDNS instance.
I ended up going with a completely different option: making a solution, that's perfectly fit for my server, myself.
My Server Structure
So, I should probably explain how I host and why only nginx is public despite me hosting a bunch of services under the hood.
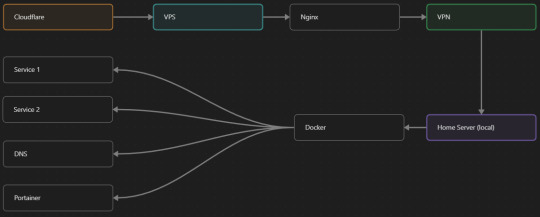
I have a public facing VPS that only allows traffic to nginx. That traffic then gets forwarded through a VPN connection to my home server so that I don't have to have any public facing ports on said home server. The VPS only really acts like the public interface for the home server with access control and logging sprinkled in throughout my configs to get more layers of security. Some Services can only be interacted with through the VPN or a local connection, such that not everything is actually forwarded - only what I need/want to be.
I actually do have fail2ban installed on both my VPS and home server, so why make another piece of software?
Tabarnak - Succeeding at Banning
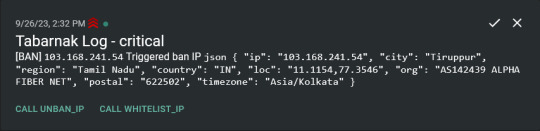
I had a few requirements for what I wanted to do:
Only allow HTTP(S) traffic through Cloudflare
Only allow DNS traffic from given sources; (location filtering, explicit white-/blacklisting);
Webhook support for logging
Should be interactive (e.g. POST /api/ban/{IP})
Detect automated vulnerability scanning
Integration with the AbuseIPDB (for checking and reporting)
As I started working on this, I realized that this would soon become more complex than I had thought at first.
Webhooks for logging This was probably the easiest requirement to check off my list, I just wrote my own log() function that would call a webhook. Sadly, the rest wouldn't be as easy.
Allowing only Cloudflare traffic This was still doable, I only needed to add a filter in my nginx config for my domain to only allow Cloudflare IP ranges and disallow the rest. I ended up doing something slightly different. I added a new default nginx config that would just return a 404 on every route and log access to a different file so that I could detect connection attempts that would be made without Cloudflare and handle them in Tabarnak myself.
Integration with AbuseIPDB Also not yet the hard part, just call AbuseIPDB with the parsed IP and if the abuse confidence score is within a configured threshold, flag the IP, when that happens I receive a notification that asks me whether to whitelist or to ban the IP - I can also do nothing and let everything proceed as it normally would. If the IP gets flagged a configured amount of times, ban the IP unless it has been whitelisted by then.
Location filtering + Whitelist + Blacklist This is where it starts to get interesting. I had to know where the request comes from due to similarities of location of all the real people that would actually connect to the DNS. I didn't want to outright ban everyone else, as there could be valid requests from other sources. So for every new IP that triggers a callback (this would only be triggered after a certain amount of either flags or requests), I now need to get the location. I do this by just calling the ipinfo api and checking the supplied location. To not send too many requests I cache results (even though ipinfo should never be called twice for the same IP - same) and save results to a database. I made my own class that bases from collections.UserDict which when accessed tries to find the entry in memory, if it can't it searches through the DB and returns results. This works for setting, deleting, adding and checking for records. Flags, AbuseIPDB results, whitelist entries and blacklist entries also get stored in the DB to achieve persistent state even when I restart.
Detection of automated vulnerability scanning For this, I went through my old nginx logs, looking to find the least amount of paths I need to block to catch the biggest amount of automated vulnerability scan requests. So I did some data science magic and wrote a route blacklist. It doesn't just end there. Since I know the routes of valid requests that I would be receiving (which are all mentioned in my nginx configs), I could just parse that and match the requested route against that. To achieve this I wrote some really simple regular expressions to extract all location blocks from an nginx config alongside whether that location is absolute (preceded by an =) or relative. After I get the locations I can test the requested route against the valid routes and get back whether the request was made to a valid URL (I can't just look for 404 return codes here, because there are some pages that actually do return a 404 and can return a 404 on purpose). I also parse the request method from the logs and match the received method against the HTTP standard request methods (which are all methods that services on my server use). That way I can easily catch requests like:
XX.YYY.ZZZ.AA - - [25/Sep/2023:14:52:43 +0200] "145.ll|'|'|SGFjS2VkX0Q0OTkwNjI3|'|'|WIN-JNAPIER0859|'|'|JNapier|'|'|19-02-01|'|'||'|'|Win 7 Professional SP1 x64|'|'|No|'|'|0.7d|'|'|..|'|'|AA==|'|'|112.inf|'|'|SGFjS2VkDQoxOTIuMTY4LjkyLjIyMjo1NTUyDQpEZXNrdG9wDQpjbGllbnRhLmV4ZQ0KRmFsc2UNCkZhbHNlDQpUcnVlDQpGYWxzZQ==12.act|'|'|AA==" 400 150 "-" "-"
I probably over complicated this - by a lot - but I can't go back in time to change what I did.
Interactivity As I showed and mentioned earlier, I can manually white-/blacklist an IP. This forced me to add threads to my previously single-threaded program. Since I was too stubborn to use websockets (I have a distaste for websockets), I opted for probably the worst option I could've taken. It works like this: I have a main thread, which does all the log parsing, processing and handling and a side thread which watches a FIFO-file that is created on startup. I can append commands to the FIFO-file which are mapped to the functions they are supposed to call. When the FIFO reader detects a new line, it looks through the map, gets the function and executes it on the supplied IP. Doing all of this manually would be way too tedious, so I made an API endpoint on my home server that would append the commands to the file on the VPS. That also means, that I had to secure that API endpoint so that I couldn't just be spammed with random requests. Now that I could interact with Tabarnak through an API, I needed to make this user friendly - even I don't like to curl and sign my requests manually. So I integrated logging to my self-hosted instance of https://ntfy.sh and added action buttons that would send the request for me. All of this just because I refused to use sockets.
First successes and why I'm happy about this After not too long, the bans were starting to happen. The traffic to my server decreased and I can finally breathe again. I may have over complicated this, but I don't mind. This was a really fun experience to write something new and learn more about log parsing and processing. Tabarnak probably won't last forever and I could replace it with solutions that are way easier to deploy and way more general. But what matters is, that I liked doing it. It was a really fun project - which is why I'm writing this - and I'm glad that I ended up doing this. Of course I could have just used fail2ban but I never would've been able to write all of the extras that I ended up making (I don't want to take the explanation ad absurdum so just imagine that I added cool stuff) and I never would've learned what I actually did.
So whenever you are faced with a dumb problem and could write something yourself, I think you should at least try. This was a really fun experience and it might be for you as well.
Post Scriptum
First of all, apologies for the English - I'm not a native speaker so I'm sorry if some parts were incorrect or anything like that. Secondly, I'm sure that there are simpler ways to accomplish what I did here, however this was more about the experience of creating something myself rather than using some pre-made tool that does everything I want to (maybe even better?). Third, if you actually read until here, thanks for reading - hope it wasn't too boring - have a nice day :)
10 notes
·
View notes
Text
The benefits of VPS hosting for your eCommerce startup
Are you contemplating whether virtual private server (VPS) hosting is the ideal choice for your promising eCommerce website? You're not alone.
The best virtual private server hosting is a popular, budget-friendly solution and often the go-to choice for startups. However, the decision is only sometimes straightforward, and it's essential to understand the benefits fully.
This comprehensive guide will delve into the advantages of VPS hosting for promising eCommerce website and provide practical steps to transition smoothly to a VPS solution. You'll gain invaluable insights into how and why VPS hosting offers reliable, secure solutions that significantly enhance website speeds, security, and uptime.

By the end, you'll be empowered to make an informed decision that is well-suited for your promising eCommerce startup's needs!
A virtual private server, or VPN, is a type of hosting service that makes use of virtualization technology to provide several users with access to a dedicated resource on a server. It is a cheaper VPS hosting than renting a whole server and offers greater security and stability than shared hosting.
Security is one of the most important aspects of a promising eCommerce website since most transactions involve users' and clients' private information. Consequently, employing a best VPS hosting should improve website security and reassure users that their information will remain private and confidential.
What other advantages does implementing the best VPS hosting offer eCommerce companies, though?
Benefits of Using a VPS For a Start-up eCommerce Website
Assuring safety:
Without a question, an affordable VPS hosting is the most secure web hosting package. You can protect your business from dangerous crimes and cyberattacks because there won't be any direct resource sharing, unlike split hosting, between users.
Without a doubt, it is crucial to take the server's security into account. Furthermore, browsers need to identify SSL certificates as secure. Although it offers appropriate security and control, there are still hazards that you need to be mindful of.
Performance and Speed:
A hosting server that can deliver optimal performance and speed for your website is a must for your promising eCommerce website. This is your website's most important feature. It is impossible to exaggerate the significance of having a dependable and constantly available host for your business. Furthermore, it is imperative that you have a lightning-fast website to aid visitors in maintaining their patience while on your site.
Creating a VPS Account:
The most attractive feature of best VPS hosting is its affordable price tag, which isn't always available. One of the main things that draws businesses is this. You may enjoy the maximum bandwidth, storage, and speed of the best VPS hosting service without worrying. Having complete control over your server will allow you to explore all of the options for improving the Cloud VPS's performance and boosting productivity.
Reliability:
When it comes to dependability, hosting from the virtual private sector is unmatched. When your organization first starts out, shared hosting or even small business hosting is a good fit. However, as your firm expands, you'll need a high-tier hosting solution to meet your expanding needs. For your website and business to remain up to date, you will require a more reliable server. Your website will benefit greatly from VPS hosting, and it will always be up and running well. All the credit for this will go to the many layers of excess that are built into the software.
Small businesses can benefit greatly from cheap VPS hosting in addition to expanding companies. Taking their online presence to the next level can be beneficial. Selecting a VPS hosting option gives the business the assurance that it will function flawlessly at all times.
Regarding the lifespan of your company's website and its entire functionality, affordable VPS hosting is always available for sharing hosting. When sharing a server for your website with other possible users, if VPS hosting is not used, one of the websites could become infected with malware, potentially crashing the entire server. That will cause quite a bit of harm to your website.
When comparing shared hosting and best VPS hosting side by side, the former provides the highest degree of dependability while the latter delivers just enough consistency.
Cost-Effective
It is a type of affordable VPS hosting, so it's well-liked and suggested. It is significantly less expensive than other hosting options. The main reason for this is that companies are limited to using the resources they require. Any resource they need is always available to them.
Another key advantage of VPS hosting is its scalability, which provides businesses with the freedom to add resources as their traffic volume increases. This flexibility not only ensures smooth operations but also plays a crucial role in cost-effectiveness, as you're only paying for what you need, when you need it.
Suppose you choose shared hosting instead of investing in a line of dedicated servers. In that case, the cost can be prohibitive, especially for larger businesses, and there is a greater chance of performance and security problems. Using cheap VPS hosting as your service can help you overcome those issues with ease. Not only does it address the issues above, but its price structures are also comparatively more affordable.
Moreover, Let's Encrypt, an organization formed by the University of Michigan, the Electronic Frontier Foundation, and other IT companies, offers free SSL certificates. In today's world, SSL certificates are a necessity for all websites. With the increasing threat of global hacking, protecting your website with an SSL certificate is a must. Without one, all major web browsers will flag your website as insecure. This underscores the importance of SSL certificates in ensuring your website's security.
Dedicated Resources
The ability to split software into several virtual servers from a single physical server is a significant advantage of VPS hosting. Each virtual server has its own operating system and programs, which is a significant feature.
It can be a hassle to manage memory and CPU time from a single physical server. VPS hosting resolves this issue by assigning these resources to individual virtual servers.
For dedicated resources, you receive many dedicated servers instead of one dedicated server. This helps manage traffic when many apps are open at once.
This makes VPS hosting the greatest choice for businesses in need of dedicated resources because of its low cost in conjunction with dedicated resources.
On a shared server, hundreds of accounts use the same hardware resources. Even if one website receives a lot of traffic, the server's overall performance breaks. This issue is effectively resolved using VPS. They constantly provide resources tailored to particular tasks, increasing the service's dependability and ensuring that operations proceed more quickly.
Flexibility
Flexibility is regarded as one of the most significant features of VPS hosting. It is not only an incredibly strong host for operating your company whenever and however you need it, but it can expand in size as your company expands. Whichever provider you choose to purchase VPS hosting from, the majority offer flexibility and scalability.
This feature also aids in budget maintenance. In the early going, you can get a smaller bundle that meets your needs. You can continue to upgrade it as your firm expands to meet your needs. This allows you a great deal of flexibility to modify your hosting to suit the demands of your company at any given time.
This is relevant when you require increased power, performance, or speed. Updating the VPS host in accordance with your needs is simple without constantly switching to new servers.
Also, because it can expand with your company in every aspect, this is definitely perfect for companies who are experiencing rapid expansion. Businesses can benefit from affordable VPS hosting far more than they can from any shared hosting platform in terms of scalability and flexibility.
Customer Service
When using a self-managed server, you receive only issues that you must handle on your own. The most you will receive for small-scale issues is the host team's assistance with hardware and network issues. You should only anticipate them addressing a limited number of issues over time. If you get into trouble, you are largely on your own.
You receive complete control over the machine as the ultimate benefit of this approach. The best VPS hosting makes it easy for you to install the programs of your choice and adjust settings to meet your requirements. You can perform these tasks for self-managed servers as well, but you will be responsible for fixing any errors or failures to complete them; however, in the case of VPS, there are different cases.
The nicest thing about VPS is that it comes with pre-installed, ideal settings based on your performance requirements. Taking control of the system would be easy for you because it configures itself.
If you have any issues or inquiries about the hosting service, you can easily contact customer support. Whatever issue you may have will be resolved by customer support. Additionally, customer support can properly assist you and walk you through the procedure step-by-step. Additionally, it can give you instructions on how to use the server's administrative platforms.
Remember that customer support is always ready to answer any questions you may have, day or night, and you should always be eager to get any issues resolved.
Conclusion
You're probably convinced by this point that VPS hosting is fantastic for your promising e-commerce start-up. However, it's crucial to consider additional elements that can make your website stand out from the competition. By making the most of the site's capabilities, you can ensure that the firm is set up for success and make better-informed decisions.
Dedicated databases and other resources utilized by numerous websites are usually needed for eCommerce start-up. The easiest way to make sure these resources remain stable and you don't have to pay extra for them is to use a virtual private server (VPS). A VPS is an easily maintained, reasonably priced, and economical solution.

Janet Watson
MyResellerHome
MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
1 note
·
View note
Text
The latest version of the Kids Online Safety Act (KOSA) is focused on removing online information that people need to see—people of all ages. Letting governments—state or federal—decide what information anyone needs to see is a dangerous endeavor. On top of that, this bill, supposedly designed to protect our privacy, actually requires tech companies to collect more data on internet users than they already do.
I have long supported comprehensive privacy protections, but the details matter. KOSA gets the details consistently wrong.
Although KOSA has been revamped since lawmakers introduced it in February, and improved slightly, it’s still a dangerous bill that presents censorship and surveillance as a solution to some legitimate, and some not-so-legitimate, issues facing young internet users today.
The Good
KOSA is a sweeping update to the Children’s Online Privacy Protection Act, also known as COPPA. COPPA is the reason that many websites and platforms ask for you to confirm your age, and why many services require their users to be older than 13—because the laws protecting data privacy are much stricter for children than they are for adults. Legislators have been hoping to expand COPPA for years, and there have been good proposals to do so. KOSA, for its part, includes some good ideas: more people should be protected by privacy laws, and the bill expands COPPA’s protections to include minors under 16. That would do a world of good, in theory: the more people we can protect under COPPA, the better. But why stop with protecting the privacy of minors under 16? EFF has long supported comprehensive data privacy legislation for all users.
Another good provision in KOSA would compel sites to allow minor users to delete their account and their personal data, and restrict the sharing of their geolocation data, as well as provide notice if they are tracking it. Again, EFF thinks all users—regardless of their age—should have these protections, and expanding them incrementally is better than the status quo.
The Bad
But KOSA’s chief focus is not to protect young people’s privacy. The bill’s main aim is to censor a broad swath of speech in response to concerns that young people are spending too much time on social media, and too often encountering harmful content. KOSA requires sites to “prevent and mitigate mental health disorders,” including by the promotion or exacerbation of “self-harm, suicide, eating disorders, and substance use disorders.” Make no mistake: this is a requirement that platforms censor content.
This sweeping set of content restrictions wouldn’t just apply to Facebook or Instagram. Platforms covered by KOSA include “any online platform that connects to the internet and that is used, or is reasonably likely to be used, by a minor.” As we said before, this would likely encompass everything from Apple’s iMessage and Signal to web browsers, email applications and VPN software, as well as platforms like Reddit, Facebook, and TikTok—platforms with wildly different user bases and uses, and with hugely varying abilities, and expectations, to monitor content.
A huge number of online services would thus be forced to make a choice: overfilter to ensure no one encounters content that could be construed as ambiguously harmful, or raise the age limit for users to 17. Many platforms may even do both.
Let’s be clear about the dangerous consequences of KOSA’s censorship. Under its vague standard, both adults and children will not be able to access medical and health information online. This is because it will be next to impossible for a website to make case-by-case decisions about which content promotes self-harm or other disorders and which ones provide necessary health information and advice to those suffering from them. This will disparately impact children who lack the familial, social, financial, or other means to obtain health information elsewhere. (Research has shown that a large majority of young people have used the internet for health-related research.)
Another example: KOSA also requires these services to ensure that young people do not see content that exacerbates a substance use disorder. On the face of it, that might seem fairly simple: just delete content that talks about drugs, or hide it from young people. But how do you find and label such content? Put simply: not all content that talks about drugs exacerbates their use.
There is no realistic way to find and filter only that content without also removing a huge swath of content that is beneficial. For just one example, social media posts describing how to use naloxone, a medication that can reverse an overdose from opioids, could be viewed as either promoting self-harm, because it can reduce the potential danger of a fatal overdose, or as providing necessary health information. But KOSA’s vague standard means that a website owner is in a better position legally if they remove that information, which avoids a potential claim later that the information is harmful. That will reduce the availability of important and potentially life-saving information online. KOSA pushes website owners toward government-approved censorship.
The Ugly
To ensure that users are the correct age, KOSA compels vast data collection efforts that perversely result in even greater potential privacy invasions.
KOSA would authorize a federal study on creating a device or operating system level age verification system, “including the need for potential hardware and software changes.” The end result would likely be an elaborate age-verification system, run by a third-party, that maintains an enormous database of all internet users’ data.
Many of the risks of such a program are obvious. They require every user—including children—to hand private data over to a third-party simply to use a website if that user ever wants to see beyond the government’s “parental” controls.
Moreover, the bill lets Congress decide what’s appropriate for children to view online. This verification scheme would make it much harder for actual parents to make individual choices for their own children. Because it’s so hard to differentiate between minors having discussions about many of these topics in a way that encourages them, as opposed to a way that discourages them, the safest course of action for services under this bill is to block all discussion and viewing of these topics by younger children and teenagers. If KOSA passes, instead of allowing parents to make the decision about what young people will see online, Congress will do it for them.
A recent study on attitudes toward age verification showed that most parents “are willing to make an exception or allow their child to bypass the age requirement altogether, but then require direct oversight of the account or discussions about how to use the app safely.” Many also fudge the numbers a bit, to ensure that websites don’t have the specific birthdays of their children. With the hard-wired, national age verification system imagined by KOSA, it will be much harder, if not impossible, for parents to decide for themselves what sites and content a young person can encounter. Instead, the algorithm will do it for them.
KOSA also fails to recognize the reality that some parents do not always have their childrens’ best interest in mind, or are unable to make appropriate decisions for them. Those children suffer under KOSA’s paternal regime, which requires services to set parental controls to their highest levels for those under thirteen.
KOSA is a Poor Substitute for Real Privacy Online
KOSA’s attempt to improve privacy and safety will in fact have negative impacts on both. Instead of using super-powered age-verification to determine who gets the most privacy, and then using that same determination to restrict access to huge amounts of content, Congress should focus on creating strict privacy safeguards for everyone. Real privacy protections that prohibit data collection without opt-in consent address the concerns about children’s privacy while rendering age-verification unnecessary. Congress should get serious about protecting privacy and pass legislation that creates a strong, comprehensive privacy floor with robust enforcement tools.
https://www.eff.org/deeplinks/2022/11/kosa-would-let-government-control-what-young-people-see-online
internet censorship bill about to pass congress:
ao3 is facing a ddos attack from an overseas right-wing anonymous group because it contains "degeneracy and disgusting things like LGBT and NSFW".
they're not the only right-wing group that is attacking fanfiction sites because of queer & nsfw content. the Heritage foundation, the US right wing think tank that writes laws for republicans, wrote an article about how "big tech turns kids trans" in which they're advocating for the Kid's Online Safety Act to pass because it will give state attorney generals power to sue websites for "potentially harmful content towards minors". in this article they point out websites like wattpad, tumblr, tiktok, twitter as sites that GOP attorney generals can and will target for censorship if this bill passes. all places where fandom, that's mostly queer, hangs out.
if you think this bill has no chance of passing because of all the red flags it poses, think again. it currently has 38 cosponsors in the senate, and is being pushed by the democrats as a "protecting the children!!" type bill.
there are left-aligned orgs in congress rn lobbying for this bill to pass. july is extremely decisive, because if KOSA goes through to markup it'll be bundled with the Earn It act, Restrict, and all the other bad internet bills and passed as a package, completely censoring the internet forever.
if you want to learn more about the bill, go here. also sign the open letter against it here
it's ESSENTIAL that you call your members of congress, specifically Maria Cantwell (you can call from out of state) and tell them DO NOT PASS KOSA. this site here connects you to your members of congress and gives you a short simple script to read off of! super easy and doesn't take much out of your day! please do this now!!
23K notes
·
View notes
Text
Explore Microsoft Iran’s Official Platform for Software, Cloud Solutions, Support Services, and the Latest Technology News and Innovations
MicrosoftIran.net: Bridging Legal Software Access in a Sanctioned Market
Introduction
Iran’s technology landscape has long grappled with international trade restrictions and software access challenges. Amid this backdrop, MicrosoftIran.net — operating under the banner “Microsoft Iran” — stands as a unique digital bridge. This platform, run by Iranian partner RayanNet (with a UK-based legal entity, Talee Limited), provides lawful, fully licensed Microsoft software to Iranian individuals, businesses, and public institutions. What the site lacks in an official Microsoft stamp, it compensates for through transparent licensing, regional localization, and a mission to reduce piracy.
History & Structure
Iran has been subject to severe U.S. and international sanctions for years, hindering the ability of global corporations like Microsoft to engage directly. In response, local tech companies innovated creative workarounds. One such initiative emerged via RayanNet, a private Iranian company that, through its UK-registered sister entity Talee Limited, became an official Microsoft Partner & Solution Provider
History & Structure
Iran has been subject to severe U.S. and international sanctions for years, hindering the ability of global corporations like Microsoft to engage directly. In response, local tech companies innovated creative workarounds. One such initiative emerged via RayanNet, a private Iranian company that, through its UK-registered sister entity Talee Limited, became an official Microsoft Partner & Solution Provider
Products, Services & Benefits
1. Genuine Licensing
Every product sold carries a retail or volume license verified by Microsoft, ensuring legitimacy and eligibility for updates, security patches, and official support .
2. Robust Support & Warranty
Backed by Microsoft’s technical infrastructure, MicrosoftIran.net offers immediate delivery along with client and technical support, including warranty coverage
3. Full Product Spectrum
From Windows (desktop/server) and Office 365 to Azure cloud, SQL Server, Dynamics, and developer tools like Visual Studio, every key and license type—Retail, Volume, CSP—is available
4. Fair Pricing & Transparent Invoicing
Licensed directly from Microsoft, the site provides competitive pricing and official receipts or pro forma invoices, enabling equitable access for businesses and institutions .
Reducing Piracy & Boosting Security
Due to sanctions, Iranian users frequently resort to pirated or cracked versions of Microsoft software, a trend that brings serious risks:
System instability and performance issues
Lack of security updates, leaving systems vulnerable to cyber threats
Challenges integrating with official support systems
Reliance on unverified third-party patches that may contain malware
Challenges & Limitations
Despite its mission, MicrosoftIran.net operates in a complex, constrained landscape:
Legal & Regulatory Barriers
While partnered with Microsoft via Talee UK, it remains constrained by U.S. export laws. Consequently, not all services are fully available, and cloud service access is monitored under strict compliance
Cybersecurity Risks
Using unofficial software in Iran leaves users exposed to malware and hacker groups like APT35. While licensed products offer protection, broader systemic issues remain .
Geopolitical Instability
Shifting diplomatic relationships and renewed sanction cycles may impact delivery, pricing, or legal frameworks. A government pivot could reinstitute restrictions swiftly .
Community & Advocacy
Iranians keenly monitor and debate access to Microsoft services online:
Petitions have circulated — nearly 500 signatures — urging Microsoft to open Windows Store and Xbox services to Iranian users .
Discussions on platforms like Reddit highlight issues like limited Teams or Xbox Live access and the need for VPNs
Concerns around software piracy, licensing, and regulatory compliance persist in tech forums and local discourse
The Path Forward
The future of MicrosoftIran.net hinges on a few key developments:
Easing of Sanctions — Should international relations soften, the company could deepen its partnership with Microsoft, enabling more direct channels (e.g., Azure, Teams, Xbox) to operate formally.
Strengthening Cybersecurity — Combating cracked installations and integrating licensed software into national cybersecurity frameworks could dramatically improve digital safety.
Tech Ecosystem Integration — Enhanced collaboration with Iranian universities, SMEs, and developer communities could accelerate innovation, digital skills, and cloud adoption.
Conclusion
MicrosoftIran.net exemplifies a creative, legally grounded solution in a market constrained by external sanctions. By enabling access to genuine Microsoft software, it closes the piracy gap, enhances system security, and promotes digital equality in Iran.
0 notes