#web app pentest
Explore tagged Tumblr posts
Text
Web Application Security Testing
Web application security testing is the process of evaluating and identifying vulnerabilities, weaknesses, and potential threats in a web application's code, configuration, and deployment.
2 notes
·
View notes
Text
Your Web App is Not A Grey Area: Importance of Web App Pentest
Apart from regular manual penetration testing, it is essential to use an automated VMDR tool equipped with vulnerability scanning and pentesting capabilities to ensure the holistic security of your web applications. AutoSecT is equipped with all the indispensable features that are needed in a modern web pentest tool to redefine web security, from identifying vulnerabilities in the source code to securing the final application.
1 note
·
View note
Text
Why Vulnerability Scanner Tool is Essential?
Consistent use of vulnerability scanner tool enables organizations to uphold a robust security posture by continuously tracking new vulnerabilities and environmental changes. This proactive approach helps you stay ahead of potential threats and fosters a vigilant security mindset.
0 notes
Text
In the near future one hacker may be able to unleash 20 zero-day attacks on different systems across the world all at once. Polymorphic malware could rampage across a codebase, using a bespoke generative AI system to rewrite itself as it learns and adapts. Armies of script kiddies could use purpose-built LLMs to unleash a torrent of malicious code at the push of a button.
Case in point: as of this writing, an AI system is sitting at the top of several leaderboards on HackerOne—an enterprise bug bounty system. The AI is XBOW, a system aimed at whitehat pentesters that “autonomously finds and exploits vulnerabilities in 75 percent of web benchmarks,” according to the company’s website.
AI-assisted hackers are a major fear in the cybersecurity industry, even if their potential hasn’t quite been realized yet. “I compare it to being on an emergency landing on an aircraft where it’s like ‘brace, brace, brace’ but we still have yet to impact anything,” Hayden Smith, the cofounder of security company Hunted Labs, tells WIRED. “We’re still waiting to have that mass event.”
Generative AI has made it easier for anyone to code. The LLMs improve every day, new models spit out more efficient code, and companies like Microsoft say they’re using AI agents to help write their codebase. Anyone can spit out a Python script using ChatGPT now, and vibe coding—asking an AI to write code for you, even if you don’t have much of an idea how to do it yourself—is popular; but there’s also vibe hacking.
“We’re going to see vibe hacking. And people without previous knowledge or deep knowledge will be able to tell AI what it wants to create and be able to go ahead and get that problem solved,” Katie Moussouris, the founder and CEO of Luta Security, tells WIRED.
Vibe hacking frontends have existed since 2023. Back then, a purpose-built LLM for generating malicious code called WormGPT spread on Discord groups, Telegram servers, and darknet forums. When security professionals and the media discovered it, its creators pulled the plug.
WormGPT faded away, but other services that billed themselves as blackhat LLMs, like FraudGPT, replaced it. But WormGPT’s successors had problems. As security firm Abnormal AI notes, many of these apps may have just been jailbroken versions of ChatGPT with some extra code to make them appear as if they were a stand-alone product.
Better then, if you’re a bad actor, to just go to the source. ChatGPT, Gemini, and Claude are easily jailbroken. Most LLMs have guard rails that prevent them from generating malicious code, but there are whole communities online dedicated to bypassing those guardrails. Anthropic even offers a bug bounty to people who discover new ones in Claude.
“It’s very important to us that we develop our models safely,” an OpenAI spokesperson tells WIRED. “We take steps to reduce the risk of malicious use, and we’re continually improving safeguards to make our models more robust against exploits like jailbreaks. For example, you can read our research and approach to jailbreaks in the GPT-4.5 system card, or in the OpenAI o3 and o4-mini system card.”
Google did not respond to a request for comment.
In 2023, security researchers at Trend Micro got ChatGPT to generate malicious code by prompting it into the role of a security researcher and pentester. ChatGPT would then happily generate PowerShell scripts based on databases of malicious code.
“You can use it to create malware,” Moussouris says. “The easiest way to get around those safeguards put in place by the makers of the AI models is to say that you’re competing in a capture-the-flag exercise, and it will happily generate malicious code for you.”
Unsophisticated actors like script kiddies are an age-old problem in the world of cybersecurity, and AI may well amplify their profile. “It lowers the barrier to entry to cybercrime,” Hayley Benedict, a Cyber Intelligence Analyst at RANE, tells WIRED.
But, she says, the real threat may come from established hacking groups who will use AI to further enhance their already fearsome abilities.
“It’s the hackers that already have the capabilities and already have these operations,” she says. “It’s being able to drastically scale up these cybercriminal operations, and they can create the malicious code a lot faster.”
Moussouris agrees. “The acceleration is what is going to make it extremely difficult to control,” she says.
Hunted Labs’ Smith also says that the real threat of AI-generated code is in the hands of someone who already knows the code in and out who uses it to scale up an attack. “When you’re working with someone who has deep experience and you combine that with, ‘Hey, I can do things a lot faster that otherwise would have taken me a couple days or three days, and now it takes me 30 minutes.’ That's a really interesting and dynamic part of the situation,” he says.
According to Smith, an experienced hacker could design a system that defeats multiple security protections and learns as it goes. The malicious bit of code would rewrite its malicious payload as it learns on the fly. “That would be completely insane and difficult to triage,” he says.
Smith imagines a world where 20 zero-day events all happen at the same time. “That makes it a little bit more scary,” he says.
Moussouris says that the tools to make that kind of attack a reality exist now. “They are good enough in the hands of a good enough operator,” she says, but AI is not quite good enough yet for an inexperienced hacker to operate hands-off.
“We’re not quite there in terms of AI being able to fully take over the function of a human in offensive security,” she says.
The primal fear that chatbot code sparks is that anyone will be able to do it, but the reality is that a sophisticated actor with deep knowledge of existing code is much more frightening. XBOW may be the closest thing to an autonomous “AI hacker” that exists in the wild, and it’s the creation of a team of more than 20 skilled people whose previous work experience includes GitHub, Microsoft, and a half a dozen assorted security companies.
It also points to another truth. “The best defense against a bad guy with AI is a good guy with AI,” Benedict says.
For Moussouris, the use of AI by both blackhats and whitehats is just the next evolution of a cybersecurity arms race she’s watched unfold over 30 years. “It went from: ‘I’m going to perform this hack manually or create my own custom exploit,’ to, ‘I’m going to create a tool that anyone can run and perform some of these checks automatically,’” she says.
“AI is just another tool in the toolbox, and those who do know how to steer it appropriately now are going to be the ones that make those vibey frontends that anyone could use.”
9 notes
·
View notes
Text
Prevent OAuth Misconfiguration in Symfony Apps Securely
Introduction
OAuth is the industry-standard protocol for authorization. While Symfony offers first-class OAuth bundles, a single misconfiguration can expose sensitive data or allow unauthorized access.

In this guide, we’ll walk you through:
What OAuth misconfiguration entails
Common pitfalls in Symfony setups
Hands-on coding examples
How to scan your app using our Website Vulnerability Scanner online
Best practices to lock down your OAuth flows
For more in-depth tutorials, visit our blog: ➡️ Pentest Testing Corp Blog
What Is OAuth Misconfiguration?
OAuth misconfiguration occurs when the authorization server or client settings are improperly defined, leading to:
Open Redirects: Attackers abuse redirect URIs
Insecure Scopes: Granting excessive permissions
Weak Token Validation: Skipping signature or audience checks
In Symfony, these mistakes often stem from inaccurate security.yaml entries or incorrect client registration on your OAuth provider.
Example: Insecure OAuth Setup
Below is an insecure security.yaml that illustrates two pitfalls: missing state checks and overly permissive redirect URIs.
# config/packages/security.yaml security: firewalls: oauth_login: pattern: ^/connect/ oauth: resource_owners: google: "/login/check-google" login_path: /connect/google check_path: /login/check-google default_target_path: / use_referer: true # insecure: trusts HTTP Referer header oauth_user_provider: service: app.user_provider
Issues:
use_referer: true trusts the HTTP Referer header—easy to spoof.
Redirect URIs not strictly defined on the OAuth provider side.
How to Scan with Our Free Tool
Use our Website Vulnerability Scanner to automatically detect OAuth misconfigurations and other vulnerabilities in seconds.
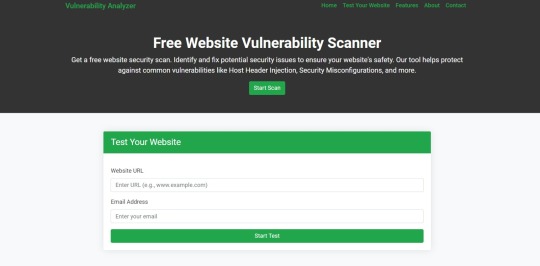
Screenshot of the free tools webpage where you can access security assessment tools for vulnerability detection
Within moments, you’ll receive a detailed report identifying misconfigurations, insecure headers, and more.
Sample Vulnerability Assessment Report
Once the scan completes, you’ll see sample assessment report to check Website Vulnerability:
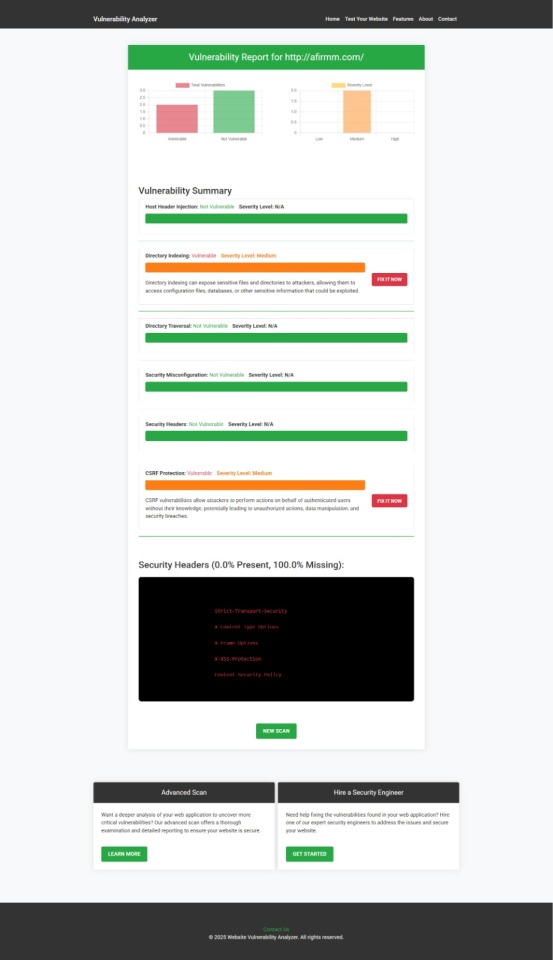
Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities
Best Practices to Secure OAuth in Symfony
Strict Redirect URIs Register only exact URIs on your OAuth provider.
# security.yaml oauth: resource_owners: google: redirect_uri: 'https://your-app.com/connect/google/check'
2. Enforce State Parameter Prevent CSRF in the authorization flow.
oauth: resource_owners: google: options: use_state: true
3. Validate Tokens Always verify issuer (iss), audience (aud), and signature.
// src/Security/GoogleTokenValidator.php use Firebase\JWT\JWT; public function validate(string $jwt): array { $publicKey = file_get_contents($this- >projectDir.'/config/jwt/public.pem'); $payload = JWT::decode($jwt, $publicKey, ['RS256']); if ($payload->aud !== 'your-client-id') { throw new \Exception('Invalid audience'); } return (array)$payload; }
4. Limit Scopes Only request the scopes your app truly needs.
oauth: resource_owners: google: options: scope: ['email', 'profile']
AI Application Cybersecurity
Leverage our AI-powered analysis for advanced threat detection in AI applications:
🔗 AI Application Cybersecurity Services
Partner With Us
Offer top-tier cybersecurity to your clients by reselling our pentest & assessment services:
🔗 Offer Cybersecurity Service to Your Clients
Stay Updated
Subscribe to our LinkedIn newsletter for the latest in web security:
✉️ Subscribe on LinkedIn
By following these guidelines and examples, you’ll eliminate OAuth misconfiguration risks in your Symfony applications—and keep your users’ data safe.
Want a free scan? DM me or check https://free.pentesttesting.com/.
2 notes
·
View notes
Text
Elevating IT Security: DSGVO Compliance, Smart Audits & Pentesting Tools
In today’s data-driven world, IT security is no longer just an operational concern—it’s a legal and reputational necessity. From growing cyber threats to ever-tightening data privacy regulations like the DSGVO (General Data Protection Regulation), businesses face immense pressure to manage their digital risk effectively.
risikomonitor.com GmbH is a cybersecurity pioneer that offers a powerful suite of IT audit solutions, IT-Sicherheit tools, and advanced pentesting tools—all while ensuring your organization stays aligned with DSGVO compliance standards.
Let’s explore how businesses can build a resilient security framework by combining compliance, proactive testing, and automated protection.
DSGVO Compliance: More Than Just a Legal Obligation
Since its enforcement in 2018, DSGVO compliance (GDPR in English) has reshaped how companies handle personal data. Whether you're a multinational or an SME, processing EU citizens' data brings serious responsibilities—and potential penalties if ignored.
Non-compliance can lead to:
Fines up to €20 million or 4% of global revenue
Lawsuits and loss of customer trust
Operational disruptions and reputation damage
risikomonitor.com GmbH simplifies GDPR/DSGVO compliance through:
Data mapping and discovery tools
Real-time consent tracking
Automated privacy impact assessments
Breach detection and notification workflows
Role-based access controls and encryption audits
With intuitive dashboards and compliance reporting, your legal and IT teams stay aligned—saving time while minimizing legal exposure.
Smarter Security Starts with Effective IT Audit Solutions
An IT audit evaluates your current infrastructure, policies, and operations to ensure that your systems are secure, compliant, and optimized. While many companies still treat IT audits as an annual task, the modern approach is continuous and automated.
risikomonitor.com GmbH provides IT audit solutions that are dynamic and proactive. These include:
Assessment of system configurations and software versions
Patch management and vulnerability scanning
Network security reviews (firewalls, segmentation, open ports)
User access and identity control assessments
With real-time visibility and automatic alerts, organizations can quickly respond to gaps and improve their security posture without waiting for the next scheduled audit.
IT-Sicherheit Tools: Fortifying Digital Defenses
IT-Sicherheit (IT security) goes beyond antivirus software. It requires intelligent tools that protect data, systems, and communication across all endpoints—both internal and cloud-based.
risikomonitor.com GmbH offers an evolving suite of IT-Sicherheit tools designed for comprehensive coverage:
Endpoint Detection & Response (EDR)
Secure configuration enforcement
Privileged access management
SIEM (Security Information and Event Management) integration
Intrusion detection and prevention systems (IDPS)
These tools are integrated into a unified platform that reduces complexity while maximizing control. Automated rule enforcement, centralized dashboards, and real-time threat intelligence give IT teams what they need to stay ahead of cybercriminals.
Advanced Pentesting Tools: Simulating the Real Threats
Penetration testing is no longer optional—it’s essential. Advanced pentesting tools help simulate real-world cyberattacks so organizations can identify weaknesses before attackers do.
Traditional pen tests are often limited in scope and frequency, but risikomonitor.com GmbH takes a smarter approach. Their tools enable:
Automated vulnerability exploitation testing
Red teaming and social engineering simulation
Continuous security testing for web and mobile apps
Real-time risk scoring and detailed remediation guidance
Integration with existing CI/CD and DevSecOps pipelines
By running automated tests regularly, businesses gain ongoing visibility into how secure their infrastructure truly is. These simulations are customized based on industry, asset criticality, and threat landscape—providing a tailored roadmap to stronger security.
Why risikomonitor.com GmbH?
Unlike other vendors that only solve part of the problem, risikomonitor.com GmbH delivers an integrated, end-to-end cybersecurity ecosystem. With a focus on automation, real-time data, and legal compliance, their platform is ideal for:
Mid-size and enterprise businesses
Regulated industries (finance, healthcare, legal, SaaS)
Businesses targeting the EU and DSGVO-covered markets
Organizations undergoing digital transformation
Their all-in-one system includes:
Continuous DSGVO compliance monitoring
Automated IT audits and vulnerability checks
Scalable IT-Sicherheit tools
Comprehensive pentesting capabilities with expert reporting
Final Thoughts
The cyber threat landscape is becoming more sophisticated, and data protection laws are only getting stricter. To succeed in this environment, organizations must take a proactive, integrated approach to cybersecurity.
With the right tools and strategies—like those from risikomonitor.com GmbH—you can ensure your systems are secure, your compliance is airtight, and your risk is under control.
0 notes
Text
Performing regular penetration testing on your network is more important now than ever before. Data protection regulations threaten hefty fines for breaches, and the public is becoming less trusting of data security. That means even small businesses cannot afford to risk a breach. Budgeting for penetration testing may not be fun, but it is necessary. Luckily, your pentest is priced based on your needs—a small business will pay much less than a large one with a bigger infrastructure. So, how much should you set aside for annual penetration testing? Small businesses should budget at least $30,000 annually. Medium-sized businesses may need to put aside at least $40,000 annually. However, your testing budget will depend on your needs. And every pentest is different, so your costs may fluctuate. Here are the factors you need to take into account when budgeting for penetration testing. How to Estimate Your Penetration Testing Budget Scope of the Test A penetration test is not a one-size-fits-all operation. Tests can be done on apps, networks, user security, and even your staff. Pentests can also simulate different types of attacks or focus on different aspects of a specific target application. All of these factors affect the cost of your test. If you want a comprehensive test of your entire network, the cost is going to be higher. If you want to test a specific program, such as a chatbot, before implementing it into your system, your costs will be lower. To define your costs, develop the scope of your test with comprehensive planning. Your third-party pentester will help you with this by asking a series of questions to define your needs. A good pentesting plan should: Define your goals Set expectations Define the environment Identify potential issues Define the limits of the test Size of the Target A penetration test for a small company with limited web applications will almost always be cheaper than a test for a large company with extensive and far-reaching applications. Don’t believe a pentesting company if they try to sell you a standardized package—that’s not how testing works. This isn’t to say that smaller networks are more secure or that small business is less prone to attack. It just means that pentesters require less time do smaller jobs, so their rates are typically lower. The complexity of the Target The complexity of your web apps has a big impact on your testing cost. More complex apps normally have more potential vulnerabilities, so testing needs to be more comprehensive. You may need to do multiple pentests on a single app in order to identify critical vulnerabilities. It can take months to test especially complex apps, resulting in higher costs. This is why it’s so important to develop the scope of your test during the planning phase. A medium-sized business that limits the scope of a test to the essentials could save tens of thousands of dollars. Security Priorities Every penetration test is different. That means you must define your security priorities before testing begins. For small businesses, this can actually save money. If you don’t have the cash for comprehensive testing, you can work with your pentester to prioritize critical aspects of your security during the planning phase. For less critical issues, you could use automated penetration testing to provide a basic level of security (more on that next). Type of Testing There are multiple types of penetration testing available. The pricing info above refers to third-party human penetration testing. That means real people plan and simulate an attack on your system. This is considered to be the best type of penetration testing because it most accurately simulates a real attack. However, the costs of human penetration testing are restrictive. It’s recommended to test this way just once per year. For continuous penetration testing, automated pentesting software provides valuable security data at an affordable rate. Automated testing
is not as comprehensive and it increases the risk of false positives, but it is an effective way to fill in security cracks between human pentests. Another type of penetration test is called Red Teaming. Red teams may test apps and networks, but they also go after your staff. They use social engineering tactics, such as phishing, to manipulate and trick people into giving away secure data. Red Teaming costs more than standard penetration testing, and it’s not necessary for most SMBs. Budget for Penetration Testing With proper planning and the right knowledge, penetration testing can be less costly to your bottom line. But the key takeaway is that penetration testing is no longer considered optional, even for small businesses. Last year, 42% of small businesses fell victim to cyber-attacks. As a result of attacks, businesses often lose customers and staff, and they suffer fines and legal consequences. Cyber-attacks on SMBs are inevitable, so don’t wait to start penetration testing. Make a budget for your next pentest and ensure the ongoing security of your business.
0 notes
Text
Plano Detalhado para Construção da NeoSphere
1. Sistema de Identidade Modular com Web3
Tecnologias: Ceramic Network + SIWE (Sign-In with Ethereum).
Implementação:
Personas Múltiplas: Cada persona é um perfil vinculado a uma sub-chave derivada da wallet principal do usuário (ex: usando HD Wallets).
Esferas Sociais: Controle de acesso via listas de permissão armazenadas em Ceramic (dados descentralizados) com referências on-chain para auditoria.
Segurança:
Chaves de criptografia (AES-256) geradas a partir da assinatura da wallet do usuário.
Dados sensíveis (ex: e-mail) armazenados criptografados em Ceramic.
Passos:
Integrar autenticação SIWE no frontend (React/Flutter).
Desenvolver contrato de registro de personas na Polygon (armazena apenas hashes).
Criar interface para gerenciamento de Esferas Sociais (ex: "Amigos", "Clientes").
2. Feed Híbrido com Curadoria Inteligente
Arquitetura:
Web2 Content: MongoDB para posts, comentários, perfis.
Web3 Content: The Graph para indexar NFTs e transações na Polygon.
Cache: Redis para posts populares e metadados de NFTs.
Algoritmos:
Cronológico: Ordenação simples por timestamp (prioridade no MVP).
Temático (Fase 2): Modelo de NLP (ex: BERT) para categorizar texto + Vision Transformer para imagens.
Engajamento: Ponderar likes (30%), comentários (20%), shares (20%), vendas de NFT (30%).
Implementação:
Criar microsserviço de feed que consome dados de MongoDB e The Graph.
Desenvolver sistema de caching em Redis com TTL de 15 minutos.
Adicionar filtros de visualização no frontend ("Modo Crono", "Modo Tendências").
3. Sistema de Pagamento Unificado (Fiat + Crypto)
Componentes:
PIX: Integração com Stripe/Pagar.me via webhooks para confirmação em <2s.
Criptomoedas:
Checkout via MetaMask (Polygon) com confirmação em 15s (5 blocos).
Smart Contract de Royalties (EIP-2981) com splits automáticos.
Conversão Fiat-Crypto: MoonPay embutido no app para compra de USDC.
Implementação:
Desenvolver contrato ERC-721 com suporte a royalties.
Criar gateway de pagamento que redireciona para PIX ou MetaMask.
Testar fluxo completo: usuário compra USDC via MoonPay → paga por um NFT → royalties distribuídos.
4. Armazenamento Descentralizado com IPFS + CDN
Fluxo de Upload:
Usuário faz upload de vídeo (até 1080p) → servidor processa com FFmpeg (compressão H.265).
Versão comprimida vai para CDN (Cloudflare R2) → link gerado instantaneamente.
Se o usuário mintar como NFT:
Arquivo original é enviado para IPFS via Pinata.
CID registrado em contrato ERC-721 na Polygon.
Otimizações:
Limitar uploads gratuitos a 10GB/mês (armazenamento em CDN por 30 dias).
NFTs têm armazenamento permanente (custo coberto por taxa de 5% nas vendas).
5. Notificações em Tempo Real
Arquitetura:
WebSockets: Socket.io para notificações instantâneas (ex: "NFT vendida!").
Filas de Eventos: RabbitMQ para desacoplar processamento (ex: novo comentário → notificação).
Implementação:
Serviço de notificação escuta eventos na blockchain (ex: contrato de NFT).
Mensagens são publicadas no RabbitMQ e consumidas pelo serviço de WebSocket.
Frontend exibe notificações com prioridade (financeiras > sociais).
6. Estratégia de Segurança
Smart Contracts:
Auditoria por Certik antes do lançamento.
Use OpenZeppelin Contracts para funções críticas (ex: ERC-721, acesso).
Aplicação Web:
Pentest focado em OWASP Top 10 (ex: injeção SQL, XSS).
Rate limiting (100 requests/min por IP) e WAF (Cloudflare).
Dados:
Zero conhecimento de chaves privadas (assinaturas apenas no client-side).
Backup diário de bancos de dados com criptografia AES-256.
7. MVP em 12 Semanas (Roadmap)
Semana Tarefas-Chave 1-2 Arquitetura C4, Setup inicial (React + Node.js + Polygon). 3-4 Autenticação SIWE + Perfis em Ceramic. 5-6 Feed básico (MongoDB + The Graph) + PIX integration. 7-8 Mint de NFTs com IPFS + contrato ERC-721. 9-10 Sistema de notificações (Socket.io + RabbitMQ). 11-12 Testes de carga (k6), Pentest, Lançamento Beta.
Riscos e Mitigação
Adoção Lenta de Web3:
Solução: Foco inicial em PIX + experiência Web2, com opções Web3 como "avançadas".
Altos Custos de Armazenamento:
Solução: Limitar armazenamento gratuito e monetizar via taxas de marketplace.
Complexidade de Escalabilidade:
Solução: Arquitetura serverless (AWS Lambda) + auto-scaling (Kubernetes).
Conclusão
A NeoSphere exigirá uma abordagem modular, priorizando a abstração da complexidade Web3 para o usuário final. Começar com um MVP focado em criadores de conteúdo (artistas digitais, microinfluencers) permitirá validar a demanda e ajustar a direção. A combinação de velocidade de rede social tradicional com autonomia econômica da Web3 é o diferencial chave para competir com o Instagram.
0 notes
Text
Crowdsourced Testing Market Size, Share, Analysis, Forecast, Growth 2032: Consumer Behavior and Market Demand Analysis
Crowdsourced Testing Market size was valued at USD 2.6 Billion in 2023 and is expected to reach USD 6.3 Billion by 2032, growing at a CAGR of 10.4% over the forecast period 2024-2032.
Crowdsourced Testing Market is rapidly transforming the software quality assurance landscape, driven by the rising need for agile, cost-effective, and real-time testing solutions. This approach leverages a global pool of testers to evaluate digital products under real-world conditions, enabling companies to deliver superior user experiences. From startups to large enterprises, organizations are embracing crowdsourced testing to shorten release cycles and identify critical bugs across a wider range of devices, networks, and geographies.
Crowdsourced Testing Market is witnessing robust traction as businesses seek to enhance product reliability while maintaining speed-to-market. The availability of diverse testers helps uncover usability issues and functional defects early, reducing the cost and time of post-release fixes. This decentralized testing model also complements DevOps practices by providing continuous feedback through parallel testing, thus improving test coverage and scalability.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3680
Market Keyplayers:
Applause (Applause Platform, Applause Codeless Automation)
uTest (uTest Platform, Test Cycle Management)
Testlio (Testlio Platform, Testlio Managed Testing)
Crowdtest (Crowdtest Dashboard, Bug Discovery Service)
Passbrains (Passbrains Platform, Passbrains Marketplace)
Bugcrowd (Bug Bounty Program, Vulnerability Disclosure Program)
Synack (Synack Red Team, Synack Vulnerability Intelligence)
Global App Testing (Functional Testing, Exploratory Testing)
Rainforest QA (Rainforest Automation, Rainforest Tester Network)
Cobalt (Cobalt Pentest Platform, Cobalt Core)
99tests (Crowd Testing Platform, Functional Testing Suite)
Testbirds (Testbirds Nest, Device Cloud)
Digivante (Digivante Platform, Exploratory Testing)
Crowdsprint (Crowdsprint Testing Services, Performance Testing)
test IO (Exploratory Testing, test IO Automation)
QaizenX (Crowdtesting Platform, App Usability Testing)
Mob4Hire (MobTest Platform, Crowdsource Usability Testing)
Crowd4Test (Crowd4Test Platform, Mobile App Testing)
WeAreTesters (Crowdsourced QA, Bug Bounty Services)
Market Analysis
The crowdsourced testing market is shaped by the evolving demands of the digital economy. Companies are increasingly recognizing the limitations of traditional testing environments, particularly when it comes to testing under diverse real-world conditions. Crowdsourced testing platforms offer flexibility, global tester reach, and faster execution, making them ideal for mobile apps, web platforms, gaming, IoT, and other digital products. The surge in smartphone penetration, expansion of internet services, and growing complexity of applications are further fueling the adoption of this model.
Additionally, the market is being driven by increasing focus on user experience, where usability and accessibility play critical roles. Organizations are also turning to crowdsourced testing to ensure compliance with localization standards and diverse user demographics.
Market Trends
Increased adoption among SMEs: Small and medium enterprises are leveraging crowdsourced testing for its cost-efficiency and access to global testers without infrastructure investments.
Integration with AI and automation tools: Crowdsourced platforms are enhancing their capabilities by incorporating AI-driven insights and automation features for smarter test management.
Focus on cybersecurity testing: With rising threats, companies are increasingly using ethical hackers and testers in crowdsourced environments to identify security vulnerabilities.
Greater use in localization testing: Brands expanding globally are using crowd testers to ensure cultural, linguistic, and functional alignment across regions.
Real-time testing demand: As development cycles shorten, the need for on-demand, real-time testing is growing, making crowdsourced testing a strategic fit for agile and DevOps methodologies.
Market Scope
The crowdsourced testing market spans across various sectors including e-commerce, BFSI, healthcare, telecommunications, gaming, and media & entertainment. Its scope extends beyond simple bug detection to encompass exploratory testing, usability feedback, beta testing, localization validation, and performance testing. The ability to conduct tests across different geographies, devices, browsers, and network conditions gives this market a significant edge over conventional QA methods.
Furthermore, as digital transformation initiatives accelerate globally, the demand for scalable, diverse, and real-world testing environments is becoming indispensable. Crowdsourced testing not only offers scalability but also helps companies validate their digital products under diverse environmental factors that in-house testing teams may not replicate efficiently.
Market Forecast
The future of the crowdsourced testing market is highly promising, supported by increasing digital product rollouts and the evolution of cloud-based testing infrastructure. As enterprises continue to prioritize user satisfaction and rapid deployment cycles, crowdsourced testing will become a cornerstone of software quality assurance strategies. Expansion in emerging economies, rise in remote work models, and growing reliance on mobile-first applications are expected to drive further market penetration.
Market players are likely to focus on strategic partnerships, AI integration, and tester community development to expand their offerings. The growth trajectory is further strengthened by regulatory requirements for accessibility, performance benchmarks, and the growing complexity of user behavior across different platforms.
Access Complete Report: https://www.snsinsider.com/reports/crowdsourced-testing-market-3680
Conclusion
In an era where digital experience defines brand perception, crowdsourced testing emerges as a vital enabler of quality and agility. Its ability to tap into global user insights and provide scalable, real-world testing makes it a game-changer for businesses aiming to deliver flawless digital interactions. As technology evolves, those who strategically harness the power of the crowd will lead with innovation, user satisfaction, and competitive advantage.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Crowdsourced Testing Market#Crowdsourced Testing Market Scope#Crowdsourced Testing Market Growth#Crowdsourced Testing Market Trends
0 notes
Text
How to Choose the Right Counselling Courses in Scotland
Each penetration testing methodology has its specific use cases and benefits. Organizations should select among penetration testing methodologies based on their security goals, technical environment, and compliance requirements.
Different methodologies exist for penetration testing different digital assets. In the brief overview below, we will discuss their focus, strengths, and weaknesses.

OWASP Penetration Testing Methodology
The OWASP (Open Web Application Security Project) Penetration Testing Methodology is one of the most well-known methodologies for pen testing. It provides a structured framework for assessing the security of web applications (there are other methodologies for, say, mobile application pentests). OWASP is widely used for identifying vulnerabilities and ensuring the reliability of web software. The OWASP Web Security Testing Guide (WSTG) is central to this methodology, outlining specific tests and tools for detecting security issues in web applications
This methodology mostly focuses on a black-box approach, simulating an external attack without prior knowledge of the internal structure of the application. It emphasizes the use of practical tools and techniques, covering areas like input validation, authentication, session management, and business logic testing. It is instrumental in strengthening the application’s security posture against modern cyber threats.
OWASP does provide comprehensive coverage, as it Includes all major aspects of web application security, from technical vulnerabilities to business logic issues. It is freely available, making it accessible to organizations of all sizes and there are regular updates to it that ensure it reflects the latest in web application security.

However, OWASP utilization depends heavily on the tester's expertise and experience in applying the framework effectively. Also, it is less suited for testing other domains.
NIST SP 800-115 Penetration Testing Methodology
NIST SP 800-115, titled "Technical Guide to Information Security Testing and Assessment," provides a structured framework for conducting penetration testing and other security assessments. It is aimed at helping organizations evaluate the effectiveness of their security controls by simulating real-world attacks. The methodology covers three phases, such as 1) Planning, which accounts for defining objectives and scope; establishing roles, responsibilities, and rules of engagement; and identifying targets and constraints. 2) Execution, which accounts for performing information gathering and vulnerability identification; exploiting vulnerabilities to demonstrate their potential impact; and documenting findings in real-time for accuracy. 3) Post-Execution, which accounts for analyzing results to prioritize remediation efforts and delivering a comprehensive report with detailed findings, risks, and mitigation strategies.
NIST SP 800-115 is characterized by a comprehensive scope as it addresses various testing techniques, including network, application, and physical security assessment guidelines. It promotes consistency across testing teams and environments as well as clear remediation steps and prioritization of risks.
However, while detailed, it may lack specific technical steps for unique environments. Also, it’s quite resource-intensive: requires skilled personnel and significant time investment for effective execution.
SANS Penetration Testing Framework
SANS Penetration Testing Methodology is derived from best practices taught by the SANS Institute, a leader in cybersecurity training and certifications. This methodology provides a structured approach to ethical hacking and is widely used for identifying vulnerabilities and simulating real-world attacks. It is often paired with SANS courses like SEC560 (Network Penetration Testing and Ethical Hacking) and SEC542 (Web App Penetration Testing and Ethical Hacking).
The methodology includes such steps as: 1) Reconnaissance: gathering open-source intelligence (OSINT) to understand the target environment; 2) Scanning: identifying live hosts, open ports, and services through tools like Nmap; 3) Exploitation: using vulnerabilities found during scanning to gain unauthorized access; 4) Post-Exploitation: maintaining access, escalating privileges, and pivoting to other systems. 5) Reporting: documenting findings, risks, and mitigation strategies.
This penetration testing framework is distinguished by its practicality. It focuses on real-world scenarios and hands-on techniques. Also, it covers all major aspects of penetration testing, from reconnaissance to reporting, and is supported by extensive SANS training programs and certifications. On the other hand, it requires skilled testers and extensive time investment. Also, it relies heavily on tools like Metasploit and Burp Suite, which may limit creativity in certain scenarios.
CREST Penetration Testing Methodology
CREST (Council of Registered Ethical Security Testers) penetration testing is a standardized and globally recognized methodology for conducting penetration tests. It ensures that tests are performed by certified professionals who follow consistent, detailed, and ethical procedures to evaluate an organization's cybersecurity posture. CREST accreditation guarantees high-quality, precise, and trustworthy testing
CREST-certified penetration testing involves simulated cyberattacks authorized by the client to assess vulnerabilities in IT systems, networks, and applications. The methodology emphasizes robust documentation, pre-engagement planning, and adherence to ethical and professional standards.
It is a credible methodology: CREST-certified testers and organizations ensure globally recognized standards of professionalism and expertise. It covers various areas including network, application, and infrastructure testing; ensures detailed and actionable reporting, aiding stakeholders in implementing corrective measures.
It should be noted that CREST-certified services can be expensive due to rigorous certification and resource requirements. The certification process and execution can take longer compared to non-standardized methodologies.
The above methodologies can be used for different types of penetration testing, such as web or mobile. A professional penetration testing company can follow these standards when working with end clients or its white label partners leveraging its expertise for the benefit of general cybersecurity.
0 notes
Text
Secure Your Systems with WebClues Infotech’s Penetration Testing Services
Elevate your cybersecurity with our comprehensive Penetration Testing Services at WebClues Infotech. Our cutting-edge testing methodologies and industry-leading tools ensure unmatched security for your digital assets. We specialize in Web Application Testing, API Pentest, Mobile App Pen Testing, External Network Pentest, Internal Network Pentest, and Cloud Config Review. Stay ahead of threats with reliable and customized solutions. Safeguard your business from potential risks - visit https://www.webcluesinfotech.com/penetration-testing-services today!
0 notes
Link
Web pentesting with Defensive Security and Offensive Security. Defensive coding is the thing. When we write code, we’re not just aiming for high-performance code. We also want to produce code that doesn’t have any weaknesses. After we have performed a code review, we ensure that the code is free of any vulnerabilities. We regularly perform tests to eliminate any vulnerabilities that exist.
1 note
·
View note
Photo
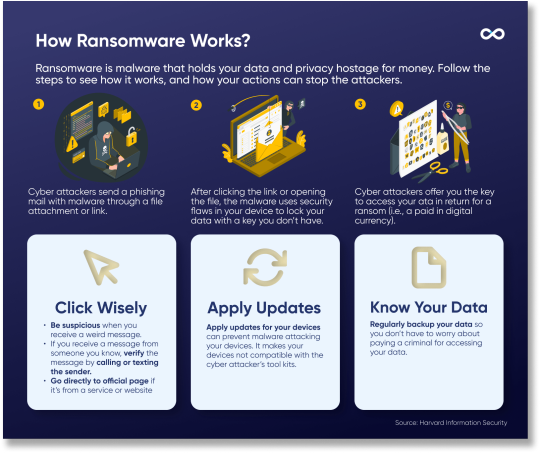
According to a PhishLabs report, by HelpSystems, ransomware attacks are growing more than 100% year-over-year 😮 As ransomware often arises as a result of attackers leveraging vulnerabilities. it is important to recognize those vulnerabilities to stop it. Here’s an infographic about how ransomware works and the ways for you to prevent it from harming you. Visit here to learn more: https://www.veecotech.com.sg/digital-marketing-statistics/
#web security#cybersecurity#pentesting#cyberattack#cybercrime#ethical hacking#backup#web application firewall market#web application security#mobile app security#pentest#penetration testing
0 notes
Text
Erlik 2 - Vulnerable-Flask-App
Erlik 2 – Vulnerable-Flask-App
Erlik 2 – Vulnerable-Flask-App Tested – Kali 2022.1 Description It is a vulnerable Flask Web App. It is a lab environment created for people who want to improve themselves in the field of web penetration testing. Features It contains the following vulnerabilities. HTML Injection XSS SSTI SQL Injection Information Disclosure Command Injection Brute Force Deserialization Broken…

View On WordPress
#Flask App#KitPloit#Vulnerable Api#Vulnerable App#Vulnerable Flask App#Vulnerable Web App#Vulnerable Web Application#Vulnerable Webserver#Web Hacking Simulation#Web Pentesters
0 notes
Text
Prevent Command Injection in Symfony: Secure Your Code
Symfony is a powerful PHP framework trusted by thousands of developers, but like any framework, it's not immune to security threats. One of the most dangerous—and often overlooked—threats is a Command Injection Attack.

In this blog post, we’ll break down what a command injection attack is, how it can be exploited in a Symfony application, and—most importantly—how to prevent it. We’ll also include code examples and offer you a Website Vulnerability Scanner online free to scan your website for vulnerabilities like this one.
➡️ Visit Our Blog for More Cybersecurity Posts: 🔗 https://www.pentesttesting.com/blog/
🧨 What is Command Injection?
Command Injection is a type of security vulnerability that allows attackers to execute arbitrary system commands on your server. If user input is improperly sanitized, attackers can exploit functions like exec(), system(), or shell_exec() in PHP.
This can lead to:
Data breaches
Server hijacking
Total application compromise
🐘 Symfony Command Injection Example
Let’s start with a naive Symfony controller that might fall victim to command injection.
❌ Vulnerable Symfony Code
// src/Controller/BackupController.php namespace App\Controller; use Symfony\Component\HttpFoundation\Request; use Symfony\Component\HttpFoundation\Response; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; class BackupController extends AbstractController { public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // ⚠️ Dangerous input $output = shell_exec("mysqldump -u root -psecret mydb > /backups/{$filename}"); return new Response("Backup created: $filename"); } }
If an attacker sets filename=backup.sql;rm -rf /, this code could delete your entire server. Yikes!
🔐 Secure It With Escaping & Whitelisting
Let’s see how we can secure this.
✅ Safe Symfony Version
public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // Sanitize the filename using a whitelist or regex if (!preg_match('/^[\w\-\.]+$/', $filename)) { return new Response("Invalid filename", 400); } $safePath = escapeshellarg("/backups/" . $filename); $output = shell_exec("mysqldump -u root - psecret mydb > $safePath"); return new Response("Backup created: $filename"); }
By using escapeshellarg() and validating the input, we reduce the risk significantly.
🛠️ Automate Detection with Our Free Tool
Want to check if your website is vulnerable to command injection and other critical flaws?
🎯 We’ve built a Free Website Vulnerability Scanner that checks for command injection, XSS, SQLi, and dozens of other issues—all in seconds.
🖼️ Screenshot of our Website Vulnerability Scanner:

Screenshot of the free tools webpage where you can access security assessment tools.
👉 Try it now: https://free.pentesttesting.com/
📋 Sample Output Report
Our scanner doesn’t just find issues—it gives you a detailed, developer-friendly report you can act on.
🖼️ Screenshot of a sample scan report from our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
💼 Need Help Fixing It? We've Got You Covered
🔐 Web App Penetration Testing Services If you're looking for expert-level help to secure your Symfony or PHP application, our team is ready to assist.
➡️ Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Are You a Tech Company or Agency?
We offer white-label cybersecurity services so you can resell pentesting to your clients without hiring a full team.
📦 Get the full service suite here: 🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
💌 Stay Ahead of Threats—Subscribe Now!
Don’t miss future posts, case studies, and cybersecurity tips.
📬 Subscribe to our LinkedIn Newsletter
🔁 Final Thoughts
Command injection remains one of the most dangerous web application vulnerabilities. Symfony gives you the tools to secure your app—but only if you use them correctly.
Don’t wait until you’re hacked. Take 2 minutes to scan your website with our free Website Security Scanner tool.
📝 Originally written by the Pentest Testing Corp. team 📌 Visit our blog for more: https://www.pentesttesting.com/blog/
2 notes
·
View notes
Link
Tonight we’re talking about Juice Shop. It’s an example web application built for hackers to practice on. If you’re familiar with the older Damn Vulnerable Web App (DVWA), it’s a similar tool.
Tonight’s ArkanSec will be livestreamed on Discord from our meeting at Grub’s. Hope to see you there!
0 notes