All the tricks and tips that TechTrick provides only for educational purpose. If you choose to use the information in TechTrick to break into computer systems maliciously and without authorization, you are on your own. Neither I (TechTrick Admin) nor anyone else associated with TechTrick shall be liable. We are not responsibe for any issues that caused due to informations provided here.
Don't wanna be here? Send us removal request.
Photo
What is consumer cellular reviews plans phones reports login
http://www.techtrick.in/description/4740-what-is-consumer-cellular-reviews-plans-phones-reports-login
0 notes
Photo

Free Online Games Aarp Games Mahjong Dimensions
http://www.techtrick.in/description/4741-free-online-games-aarp-games-mahjongg-dimensions
0 notes
Photo
what is craigslist and how does craigslist work
http://www.techtrick.in/description/4742-what-is-craigslist-and-how-does-craigslist-work
0 notes
Text
Why Is Google Maps So Slow
http://www.techtrick.in/description/4723-why-is-google-maps-so-slow
0 notes
Text
How To Change Business Name On Facebook
http://www.techtrick.in/description/4724-how-to-change-business-name-on-facebook
0 notes
Text
10 Ways To Solve irql_not_less_or_equal windows 10
http://www.techtrick.in/description/4725-10-ways-to-solve-irql-not-less-or-equal-windows-10
0 notes
Text
How To Change Your Name On Facebook
http://www.techtrick.in/description/4726-how-to-change-your-name-on-facebook
0 notes
Text
How to Send a Private Message on Twitter
http://www.techtrick.in/description/4720-how-to-send-a-private-message-on-twitter
0 notes
Link
In the early days of email, companies often relied on users to maintain individual archives outlook emails. The IT department would back up a users email, but searching of messages was not automated. If a specific email needed to be traced, it often took weeks to find it. The emergence of software with specialized email archiving services helps organizations curate data from thousands of mailboxes.
#bestwaytoarchiveoutlookemails#microsoftoutlookarchiveemails#outlookpstfilecreation#retrievearchivedemailoutlook#outlookautoarchive2013#runarchiveoutlook2013#autoarchiveoutlook#outlookautoarchive#backupemailsoutlook2010#automaticallyarchiveoutlook#archiveoutlookemails#setuparchivefolderinoutlook#autoarchivingoutlook2013#archivefolderinoutlook#howtoretrievearchivedemailsinoutlook
0 notes
Link
Figlet display large characters made up of ordinary screen characters. Figlet prints its input using large characters (called "FIGcharacters") made up of ordinary screen characters (called "sub-characters"). Figlet output is generally reminiscent of the sort of "signatures" many people like to put at the end of e-mail and UseNet message. It also reminiscent od the output of some banner programs, although it is oriented normally, not sideways.
#How To Make a Sick Banner For Your Terminal Figlet#figlet online#linux banner generator#linux banner command#linux figlet#cal command in unix with options and examples
0 notes
Link
The dig command is used in network administration that check and lookup domain name server. Dig ( Domain Information Groper ) is a tool in Kali Linux used to gather information about host addresses, mail exchange servers, name servers by sending query to the DNS Name server.
#Hacking Dns Lookup With Dig#dig Linux DNS Lookup#Check your DNS records with dig#Dig Commands#How To Use Dig#Whois#Ping on an Ubuntu VPS to Query DNS Data
0 notes
Link
Transparent Proxy through TOR, I2P, Privoxy, Polipo and modify DNS, for a simple and better privacy and security; Include Anonymizing Relay Monitor (arm), macchanger, hostname and wipe (Cleans ram/cache & swap-space) features. Tested on Debian, Kali, Parrot to use the graphical interface, you will need to install separately GTKdialog and libvte.so.9 and i2p.
#How to Hide IP and MAC Address using Anonym8#how to hide ip address and access any blocked site using anonym8#How to Install and Use Anonym8#how to hide ip address
0 notes
Link
Lynis is an open source and much powerful auditing tool for Unix/Linux like operating systems. It scans system for security information, general system information, installed and available software information, configuration mistakes, security issues, user accounts without password, wrong file permissions, firewall auditing, etc.
#Security Auditing and Scanning Tool for Linux Systems Lynis#linux security audit tool#lynis remote scan#linux security audit checklist#lynis github
0 notes
Photo
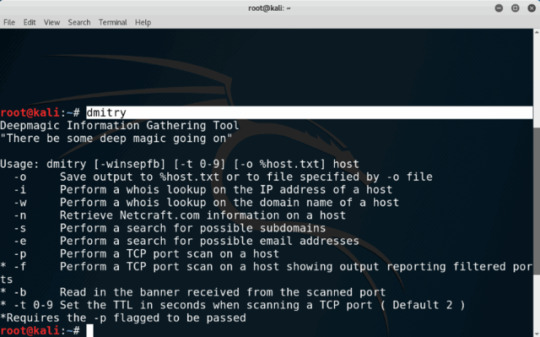
How to use Dmitry Information Gathering Tool
DMitry has the ability to gather as much information as possible about a host. Base functionality is able to gather possible subdomains, email addresses, uptime information, tcp port scan, whois lookups, and more.
http://www.techtrick.in/description/3496-how-to-use-dmitry-information-gathering-tool
#HowtouseDmitryInformationGatheringTool#maltego#HowtouseDmitryinKaliLinux#HowtoUseDmitryEffectively#HowToUseDmitry#dnmapclient#netdiscover
0 notes
Photo
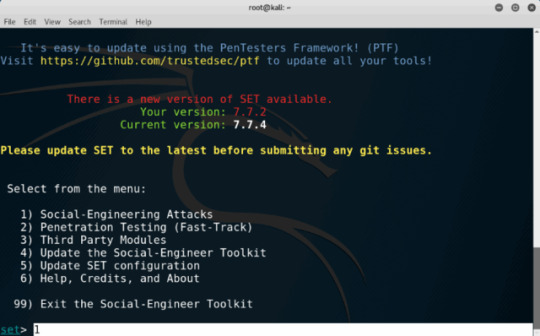
Hack Windows Using HTA Attack The Social-Engineer Toolkit
http://www.techtrick.in/description/3493-hack-windows-using-hta-attack-the-social-engineer-toolkit-set-toolkit
#social engineering#social engineer toolkit#set toolkit#setoolkit#Hta atta k#hta attack#htaattack#Hack Windows Using HTA Attack The Social-Engineer Toolkit
2 notes
·
View notes
Photo
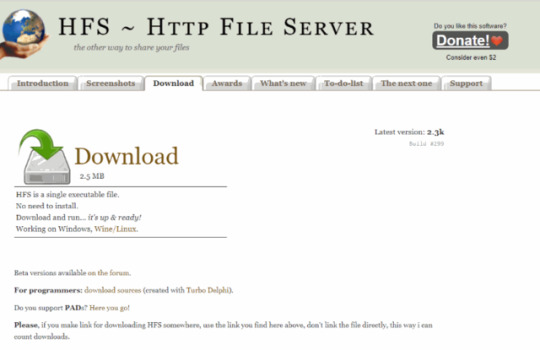
How to send or receive files in Kali Linux - Using HFS(HTTP File Server)
http://www.techtrick.in/description/3477-how-to-send-or-receive-files-in-kali-linux-using-hfs
#sendfileskalilinux#share files in linux#how to share files in kali linux#HTTP File server#hfs#hfs ftp server
0 notes
Photo

Spoofing and "Man in Middle" attack in Kali Linux - Using Ettercap
http://www.techtrick.in/description/3476-spoofing-and-man-in-middle-attack-in-kali-linux-using-ettercap
#spoofing#emailspoofing#maninthemiddleattack#MIMTMAttack#man in the middle#spoofing attack#ettercap kali linux
0 notes