#hta attack
Text
ICH BIN NICHT MEHR NORMAL,...
DOCH DAS IST MIR EGAL!!..
- kreep in dein System
#Kreep in dein System#horro#creep#666#demon#system stuff#asthetic#drug#dark#darkness#dark side#HTA#hta#HarttoAttack#Hart to Attack
0 notes
Text
Deviæ - Deviæsis - Deviatypal


An adjective to a variation where your physical sex traits are considered unnatural, artificial, or animalistic in nature.
Can be considered this way due to:
HRT or Surgery
Body Modification
Tattoos
Physical Biokinesis/Postfurry Identity
Physical Nonhumanity (Only Physical)
Transhumanist Appendages
Transspecies Transition
Misceverse Transition
Examples:
a transspecies canine getting a knot by use of body modification/beading
disembodied transhuman genitalia that allow for direct stimulation
miscverse scent implants in the skin
tattoos for markings, scales, etc
hormones like HCG, Estrone, DHEA, DHT
animalizing surgery
use of subliminals, exercise, and exposure to nonhumanity
genitalia sleaving
Terminology:
Deviborn/ ANBS - Born with deviatypal traits/ "Assigned Nonhuman By Society"
Cisspecieal - Someone who's species aligns with what was assigned to them by society
HtA/ HtB - Human to Animal/ Human to Beast
Species Dysphoria - Dysphoria that affects the perception of species
Non-dichomy - Those not aligned in the animal/beast or human category
Malspecialia - Affirmation of deviæ identity for the sole purpose of attacking or discrimination
Species expression - The expression of species traits through clothing, terms, names, etc
Vocalization Training - non-surgical method helping with speaking in or around the tone, sounds, or pitch of their species
Tail Creation - The attachment of a tail to the spine permanently or frequently
@radiomogai
@beyond-mogai-pride-flags
@transspeciesculture
#queer#liom#mogai#liom term#mogai term#flag#flag coining#flag making#mogai flag#pride flag#term coining#liom coining#mogai coining#gender coining#xeno coining#coining post#coining terms#mogai blog#coining blog#varioformic#altersex#intersex inclusive#Misceverse#transspecies#alterhuman#nonhuman#transhumanism#physical shifter#physically nonhuman#physical therian
22 notes
·
View notes
Text
Australia challenged on ‘moral failure’ of weapons trade with Israel
Regular protests have been taking place outside Australian firms making crucial components for the F-35 fighter jet.
Melbourne, Australia – Israel’s continued assault on Gaza has highlighted a hidden yet crucial component of the world’s weapons manufacturing industry – suburban Australia.
Tucked away in Melbourne’s industrial north, Heat Treatment Australia (HTA) is an Australian company that plays a vital role in the production of F-35 Joint Strike Fighters; the same model that Israel is using to bomb Gaza.
Weekly protests of about 200 people have been taking place for months outside the nondescript factory, where heat treatment is applied to strengthen components for the fighter jet a product of US military giant Lockheed Martin.
While protesters have sometimes brought production to a halt with their pickets, they remain concerned about what’s going on inside factories like HTA.
“We decided to hold the community picket to disrupt workers, and we were successful in stopping work for the day,” Nathalie Farah, protest organiser with local group Hume for Palestine, told Al Jazeera. “We consider this to be a win.”
“Australia is absolutely complicit in the genocide that is happening,” said 26-year-old Farah, who is of Syrian and Palestinian origin. “Which is contrary to what the government might have us believe.”
More than 32,000 Palestinians have been killed since Israel launched its war in Gaza six months ago after Hamas killed more than 1,000 people in a surprise attack on Israel. The war, being investigated as a genocide by the International Court of Justice (ICJ), has left hundreds of thousands on the brink of starvation, according to the United Nations.

Nathalie Farah has been organising regular protests outside HTA’s factory [Ali MC/Al Jazeera]
According to Lockheed Martin, “Every F-35 built contains some Australian parts and components,” with more than 70 Australian companies having export contracts valued at a total 4.13 billion Australian dollars ($2.69bn).
Protesters have also picketed Rosebank Engineering, in Melbourne’s southeast, the world’s only producer of the F-35’s “uplock actuator system”, a crucial component of the aircraft’s bomb bay doors.
Defence industry push
In recent years, the Australian government has sought to increase defence exports to boost the country’s flagging manufacturing industry.
In 2018, former Prime Minister Malcolm Turnbull announced Australia aimed to become one of the world’s top 10 defence exporters within a decade. It is currently 30th in global arms production, according to the Stockholm International Peace Institute.
It is an aspiration that appears set to continue under the government of Anthony Albanese after it concluded a more than one-billion-Australian-dollar deal with Germany to supply more than 100 Boxer Heavy Weapon Carrier vehicles in 2023 – Australia’s single biggest defence industry deal.
Since the Gaza war began, the industry and its business relationship with Israel have come increasingly under the spotlight.
Last month, Deputy Prime Minister Richard Marles insisted that there were “no exports of weapons from Australia to Israel and there haven’t been for many, many years”.
However, between 2016 and 2023 the Australian government approved some 322 export permits for military and dual-use equipment to Israel.
The Department of Foreign Affairs and Trade’s own data – available to the public online – shows that Australian exports of “arms and ammunition” to Israel totalled $15.5 million Australian dollars ($10.1m) over the same period of time.
Officials now appear to be slowing the export of military equipment to Israel.
In a recent interview with Australia’s national broadcaster ABC, the Minister for International Development and the Pacific Pat Conroy insisted the country was “not exporting military equipment to Israel” and clarified this meant “military weapons, things like bombs”.
However, defence exports from Australia fall into two categories, items specifically for military use – such as Boxer Heavy Weapons vehicles for Germany – and so-called ‘dual use’ products, such as radar or communications systems, that can have both civilian and military uses.
[See the video embedded in the article]
Australia’s Department of Defence did not respond to Al Jazeera’s requests about whether the halt to defence exports to Israel also included dual-use items.
What is certain is that companies such as HTA and Rosebank Engineering are continuing to manufacture components for the F-35, despite the risk of deployment in what South Africa told the International Court of Justice in December amounted to “genocidal acts“.
In the Netherlands – where parts for the jet are also manufactured – an appeal court last month ordered the Dutch government to block such exports to Israel citing the risk of breaching international law.
The Australian government has also come under scrutiny for its lax “end-use controls” on the weapons and components it exports.
As such, while the F-35 components are exported to US parent company Lockheed Martin, their ultimate use is largely outside Australia’s legal purview.
Lauren Sanders, senior research fellow on law and the future of war at the University of Queensland, told Al Jazeera that the “on-selling of components and military equipment through third party states is a challenge to global export controls.
“Once something is out of a state’s control, it becomes more difficult to trace, and to prevent it being passed on to another country,” she said.
Sanders said Australia’s “end use controls” were deficient in comparison with other exporters such as the United States.
“The US has hundreds of dedicated staff – with appropriate legal authority to investigate – to chase down potential end-use breaches,” she said.
“Australia does not have the same kind of end-use controls in place in its legislation, nor does it have the same enforcement resources that the US does.”

The protesters say they will continue their action until manufacturing of F-35 components is stopped [Ali MC/Al Jazeera]
In fact, under legislation passed in November 2023, permits for defence goods are no longer required for exports to the United Kingdom and the US under the AUKUS security agreement.
In a statement, the government argued the exemption would “deliver 614 million [Australian dollars; $401m] in value to the Australian economy over 10 years, by reducing costs to local businesses and unlocking investment opportunities with our AUKUS partners”.
International law
This new legislation may provide more opportunities for Australian weapons manufacturers, such as NIOA, a privately owned munitions company that makes bullets at a factory in Benalla, a small rural town in Australia’s southeast.
The largest supplier of munitions to the Australian Defence Force, NIOA – which did not respond to Al Jazeera for comment – also has aspirations to break into the US weapons market.
At a recent business conference, CEO Robert Nioa said that “the goal is to establish greater production capabilities in both countries so that Australia can be an alternative source of supply of weapons in times of conflict for the Australian and US militaries”.
Greens Senator David Shoebridge told Al Jazeera that the government needed to “publicly and immediately refute the plan to become a top 10 global arms dealer and then to provide full transparency on all Australian arms exports including end users.
“While governments in the Netherlands and the UK are facing legal challenges because of their role in the global supply chain, the Australian Labor government just keeps handing over weapons parts as though no genocide was happening,” he said. “It’s an appalling moral failure, and it is almost certainly a gross breach of international law.”

The Dutch government has faced legal action over the export of F-35 fighter jet parts to Israel [File: Piroschka van de Wouw/Reuters]
Elbit has come under fire for its sale of defence equipment to the Myanmar military regime, continuing sales even after the military, which seized power in a 2021 coup, was accused of gross human rights violations – including attacks on civilians – by the United Nations and others.
Despite a recent joint announcement between the Australian and UK governments for an “immediate cessation of fighting” in Gaza, some say Australia needs to go further and cut defence ties with Israel altogether.
“The Australian government must listen to the growing public calls for peace and end Australia’s two-way arms trade with Israel,” Shoebridge said. “The Albanese government is rewarding and financing the Israeli arms industry just at the moment they are arming a genocide.”
Protests have continued both at the HTA factory in Melbourne and their premises in Brisbane, with organisers pledging to continue until the company stops manufacturing components for the F-35.
#palestine#free palestine#save palestine#gaza#free gaza#save gaza#world news#current events#war on gaza#gaza genocide#gaza strip#israel#gazaunderattack#israeli apartheid#israel palestine conflict#boycott israel#palestinian genocide#palestine genocide#stop the genocide#genocide#human rights#arms trade#weapons manufacturing#weapons technology
26 notes
·
View notes
Text
Civilians Killed By Burma Army Jets and Mortars: Over 8,000 Displaced by Fighting in Ler Doh and Hsa Hti Townships, Western Karen State, Burma
Ler Doh and Hsa Hti Townships, Western Karen State, Burma
Fighting continues in Ler Doh and Hsa Hti townships of western Karen State, displacing over 8,315 villagers from more than nine villages in the last two months. The car road between Kyauk Kyi and Shwe Gyin has become a war zone for civilians living in the area. Over the past two months, November in particular, more than 8,000 people have fled their homes to escape bombings, mortars, drones, beatings, abductions and death by attacking Burma Army jets, artillery and ground troops. On November 12, local resistance groups captured three Burma Army camps within the area, Baw Ga Hta, Toe Tah Dah and Tha Seik camps. Significant fighting increased as Burma Army reinforcements from Shwe Gyin were intercepted by resistance groups along the car road. Civilians suffered as Burma Army jets, mortars, and drones bombed the country side and soldiers burned house after house. FBR teams in the area report that three civilians have been killed and five injured by Burma Army munitions during October and November. The camps were eventually reclaimed and reinforced by the Burma Army. Burma Army troops spreading from these camps are forcing villagers out of their homes to make room for Burma Army infrastructure such as additional camps and airstrips.
On October 22, Burma Army troops shot and killed Naw Day Nyaw Paw, a 48-year-old woman working at her farm. The troops then looted and burned some of the surrounding structures. Four days later, a Burma Army unit from Na Tha Gwen camp injured two villagers after dropping bombs from a drone. On 2 November, the Burma Army fired mortars into Ta Ray Se Village, killing one man and injuring two others. In Pa Den Gow Village, the Burma Army troops began burning homes; seven were completely destroyed. On 28 November, Burma Army troops from Yin Oh Sein fired mortars into Zaw Wei Village, killing a young father. FBR medics tried to help but were unable to save his life.
Throughout these two months, FBR teams, in conjunction with local community leaders have been delivering what aid they can in the form of food and shelter to those displaced. The fighting continues into December with families digging shelters next to their homes to protect themselves from jet fighter, mortar and drone attacks. Below are photos of the aforementioned events within Ler Doh and Hsa Hti townships in western Karen State, followed by a detailed incident log.
Warning: Graphic image below that some readers may find disturbing.
https://www.freeburmarangers.org/2022/12/14/civilians-killed-by-burma-army-jets-and-mortars-over-8000-displaced%EF%BF%BC-by-fighting-in-ler-doh-and-hsa-hti-townships-western-karen-state-burma/
CRD. Free Burma Rangers










crd. Free Burma Rangers
#rejectmilitarycoup#savemyanmar#hearthevoiceofmyanmar#whathappeninmyanmar#justiceformyanmar#human rights violations#crimes against humanity
5 notes
·
View notes
Text
How Malvertisers are Exploiting Google Ads
A malvertising campaign that manipulates Google Ads to divert users seeking popular software to fraudulent landing pages and deliver subsequent-stage payloads has come to light. Malwarebytes, the firm that unearthed this activity, described it as “distinctive in its methodology of fingerprinting users and distributing time-sensitive payloads.”
This attack specifically targets users looking for Notepad++ and PDF converters to display counterfeit ads on Google’s search results page. When these ads are clicked, the system weeds out bots and other unintended IP addresses by presenting a decoy website. If the visitor is considered valuable to the threat actor, they are rerouted to a cloned website promoting the software, while the system quietly fingerprints the system to ascertain if the request is coming from a virtual machine.
The Intricacies of the Malvertising Campaign
Users who fail the verification are directed to the official Notepad++ website, while a potential target is given a unique ID for “tracking purposes and also to make each download unique and time-sensitive.” The terminal-stage malware is an HTA payload that establishes a connection to a remote domain (“mybigeye[.]icu”) on a custom port and delivers subsequent malware.
Jérôme Segura, Director of Threat Intelligence, stated, “Threat actors are successfully employing evasion strategies that circumvent ad verification checks and enable them to target specific victim types.” He added, “With a dependable malware delivery chain at their disposal, malicious actors can concentrate on enhancing their decoy pages and creating custom malware payloads.”
Overlap with Similar Campaigns and the Use of Punycode
This revelation coincides with a similar campaign that targets users searching for the KeePass password manager with harmful ads that direct victims to a domain using Punycode (keepass[.]info vs. ķeepass[.]info), a unique encoding used to convert Unicode characters to ASCII.
The Role of Decoy Sites and Malicious Installers
Users who arrive at the decoy site are duped into downloading a malicious installer that ultimately triggers the execution of FakeBat (also known as EugenLoader), a loader designed to download other malicious code.
The misuse of Punycode is not entirely new, but its combination with rogue Google Ads indicates that malvertising via search engines is becoming increasingly sophisticated. The objective is to execute a homograph attack and entice victims into installing malware by using Punycode to register domain names similar to a legitimate site.
The Constant Evolution of Threats
Multiple threat actors such as TA569 (also known as SocGholish), RogueRaticate (FakeSG), ZPHP (SmartApeSG), ClearFake, and EtherHiding have been noticed exploiting themes related to fake browser updates to disseminate Cobalt Strike, loaders, stealers, and remote access trojans, indicating that these attacks are a persistent, evolving threat.
Dusty Miller, a researcher at Proofpoint, stated in an analysis published this week, “Fake browser updates exploit end user trust with compromised websites and a lure customized to the user’s browser to legitimize the update and fool users into clicking.” He warned, “The threat is only in the browser and can be initiated by a click from a legitimate and expected email, social media site, search engine query, or even just navigating to the compromised site.”
https://www.infradapt.com/news/how-malvertisers-are-exploiting-google-ads/
0 notes
Text
Cyberspionage: Fileless Malware DownEX entdeckt

Die Experten der Bitdefender Labs haben eine neue Malware-Familie entdeckt. Die anspruchsvolle und sehr gezielt ausgespielte Attacke unter dem Namen DownEx zielt aktuell noch auf Regierungsbehörden in Zentralasien ab. In diesen Regionen aktive Unternehmen können ebenso zu Opfern werden.
Das Hauptziel der Angreifer ist die Spionage und Exfiltration von Informationen. Der Schadcode der Fileless-Attacke wird zu großen Teilen nur im Arbeitsspeicher ausgeführt und ist daher nur schwer zu erkennen. Über die Analyse des Python-Scripts und ein Reverse Engineering der Kommunikation mit dem Command-and-Control (C2C)-Server konnten die Experten vier Hauptfunktionen der Malware identifizieren: Sie ermöglicht es Hackern, gezielt nach Dateien zu scannen, sie zu exfiltrieren, zu löschen oder Screenshots von Bildschirminhalten betroffener Systeme anzufertigen.
Spionage: Auf der Suche nach vertraulichen Daten
Die Urheber der Kampagne interessieren sich dabei besonders für vertrauliche Daten, wie etwa mit der Erweiterung .pgp (Pretty Good Privacy) oder .pem (Privacy Enhanced Mail). Ebenso suchen die Hacker nach Finanzdaten, wie etwa den QuickBooks-Logfiles (.tlg-Erweiterung).
Die Domain und die IP-Adressen im Zusammenhang mit der Kampagne sind neu. Der Schadcode weist keine Ähnlichkeiten mit bisher bekannter Malware auf. Die Bitdefender Labs haben die neue Malware-Kampagne als erste entdeckt und ihr den Namen DownEx gegeben.
Gezielte Attacken auf Unternehmen
Die Hacker wenden sich gezielt an ausgesuchte Opfer. Der ursprüngliche Angriffsvektor ist nicht klar, Spear Phishing und Social Engineering stehen aber wohl am Anfang jeder Attacke. Für das Ausspielen des Payloads nutzen die Cyberkriminellen recht klassisch und einfach ein Icon mit einer .docx-Datei, die eine ausführbare Datei als Schad-Payload tarnt. Zweiter Payload ist eine .hta-Datei – allerdings ohne diese Dateierweiterung) mit eingebettetem bösartigen VBScript-Code, der das angegriffene System mit dem C2C-Server verbindet. Eine .hta-Datei (HTML Application) enthält VBScript-, HTML-, CSS- oder JavaScript-Code, der als Standalone-Applikation in Windows-Betriebssystemumgebungen ausführbar ist. Die anschließende, schwer zu entdeckende Kommunikation zwischen Server und Opfersystem läuft über die Python-basierte Backdoor help.py.
Russischer Hintergrund? – Staatlicher Hintergrund!
Indikatoren und verwendete Techniken können auf einen russischen Hintergrund der Akteure hinweisen. Allerdings lassen sich dazu keine endgültigen Aussagen treffen. Die Metadaten des verwendeten Dokuments mit vorgegebener Identität eines Diplomaten könnte ein Indiz sein.
Ebenso verwendet die Malware eine gecrackte Version von Microsoft 2016, die vor allem in russischsprechenden Ländern verbreitet ist („SPecialisST RePack“ oder „Russian RePack by SPecialiST“). Die Backdoor ist zudem in zwei Sprachen verfasst. Diese Praxis ist von der Russland-basierten APT28-Gruppe und ihrer Hintertür Zebrocy bekannt. Diese Hinweise sind aber nicht hinreichend. Offensichtlich ist der staatliche Hintergrund der äußerst gezielten Attacke. Die Metadaten des Word-Dokuments weisen auf einen tatsächlichen Diplomaten als vermeintlichen Absender hin.
Passende Artikel zum Thema
Lesen Sie den ganzen Artikel
0 notes
Photo
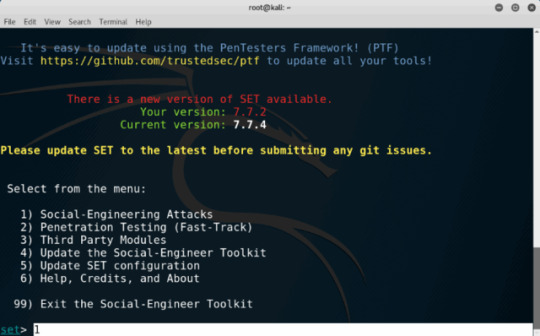
Hack Windows Using HTA Attack The Social-Engineer Toolkit
http://www.techtrick.in/description/3493-hack-windows-using-hta-attack-the-social-engineer-toolkit-set-toolkit
#social engineering#social engineer toolkit#set toolkit#setoolkit#Hta atta k#hta attack#htaattack#Hack Windows Using HTA Attack The Social-Engineer Toolkit
2 notes
·
View notes
Text
Junta has lost 11 outposts in Karen State after coup
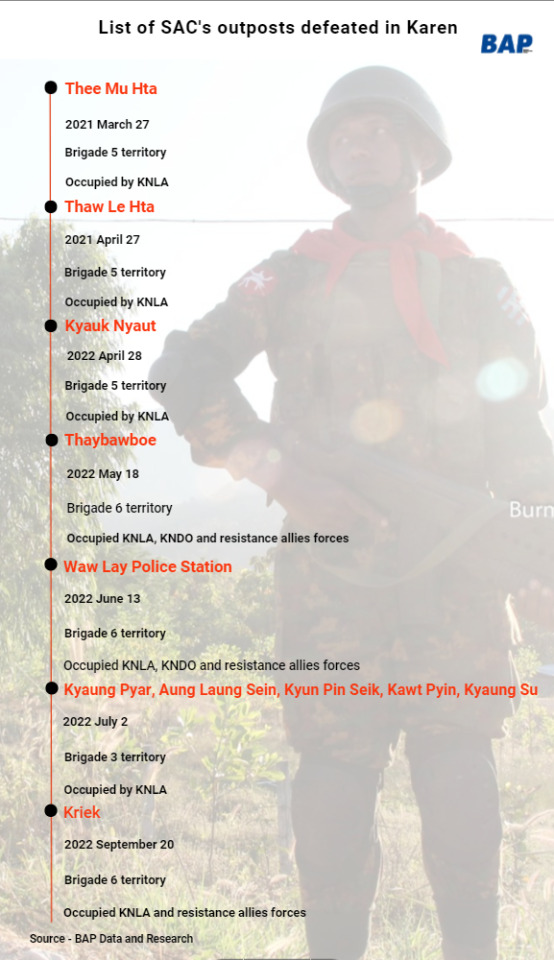
Kawthoolei, September 22
According to data collected by Burma Associated Press, the military has lost a total of 11 bases in KNU-controlled areas, including Waw Lay police station, located in southern Myawaddy Township.
The military base named Kriek, located in Kawkareik Township, Karen State seized last Tuesday. It took only 17 minutes to defeat the outpost, then the Karen National Liberation Army (KNLA) and its allied forces PDF occupied the military outpost, and it was the eleventh outpost that has seized by the KNLA.
That outpost was taken by KNLA on 21 August 2021 once after the SAC’s troops have run and left their base, however, they re-based there later.
Junta keeps losing its outposts from Karen State after taking control of power in 2021. The military has lost only two outposts in 2021 but up to nine outposts have been lost including Waw Lay police station till 20 September 2022.
After the first three months of the coup of 2021, the junta lost strategic point outposts named Thee Mu Hta and Thaw Le Hta which are in Brigade 5 of the Karen National Union controlled area. After exactly one month of Thee Mu Hta being seized, the KNLA occupied SAC’s Thaw Le Hta outpost again.
The military troops based in Kriek and Khar Li Khee outposts from Brigade 6 were run and left their bases in August 2021 then KNU seized the outposts. Later, KNU allowed SAC troops to back and re-based in those outposts after reclaiming according to the NCA agreement.
One year later of Thaw Le Hta seizure, SAC lost Kyauk Nayut and Thaybowboe outposts from Brigade 5 of KNU controlled area. There is only three weeks difference between the Kyauk Nyaut and Thaybowboe seizures. Thaybawboe is one of the strategic outposts where the Myanmar military had been based since the 1990s.
Less than a month after being occupied the Thaybawboe, the Karen ethnic armed organizations and its allies raided Waw Lay police station from Myawaddy Township, weapons were seized and nine members of the local defense forces who were arrested in the station were also rescued as a bonus.
About two weeks after the Waw Lay incident, on June 26, Karen ethnic armed organisations and its allied forces tried to occupy Ukaritha outpost from Brigade 6. The battle has been intense for a week, both SAC and KNU didn’t release the details of death and injury information.
The military mainly used airstrikes to protect Ukaritha outpost, which is near the Thai-Myanmar borderline. Subsequently, there was an incident where a bomb dropped and exploded in the Thailand area and then the Myanmar military apologized for it.
Myanmar military counter-attacked with heavy airstrikes - a total of 94 airstrikes have launched within 4 days: June 27 to 30, according to the KNU statement released on July 5.
Despite SAC save Ukaritha, another five outposts from Brigade 3 of the Karen National Union-controlled area were lost. They are Kyaung Pyar, Aung Laung Sein, Kyun Pin Seik, Kawt Pyin, and Kyaung Su outposts and KNU occupied all of them simultaneously, according to the KNU statement released on July 3.
After the military coup, clashes have been spotted every day in Karen State. According to the Karen National Union (KNU) released on September 13, between January 2021 to the end of August 2022, over 6,000 clashes had happened within the KNU-controlled areas. The clashes have claimed more than 5,000 lives of SAC and its allies Border Guard Force (BGF), and another 4,000 were also injured.
Burma Associated Press
2 notes
·
View notes
Note
hey, sorry but my dislexya has been attacking me for a bit and i cant tell what your username is supposed to be (also my brain is off sorry for incomprehensible)
oh yeah, I don't mind explaining it at all! One of us was going for something edgy but simple, and decided to write forever-death but backwards, to become htaed-reverof
(also I hope bolding and coloring those helped make it easier to read?)
1 note
·
View note
Text
Week 8 Security Everywhere
Australia Post told to improve cyber security practices
Article - https://www.itnews.com.au/news/australia-post-told-to-improve-cyber-security-practices-527738
The national auditor found gaps in the security of two of Australia Post’s critical systems! Australia Post was called out for “not effectively managing cyber security risks” and not undertaking “detailed risk management assessment” on the systems for the past two years. This means that the ability for Australia post to withstand a cyber attack is pretty bad, as their evaluations would only be accurate 2 years ago. Any new developments in cyber security, such as a new attack, would make the Australia Post system vulnerable.
The audit found only half of the ten sampled controls were designed and implemented as specified in the framework, with others only partially implemented or not in place at all.
I find it interesting that a government controlled entity is audited by itself and found to be fully of security holes. Similar government entities such as the Reserve Back underwent a similar audit and they didn’t have such risks.
One of the things Australia Post didn’t do was application whitelisting for “blocking unauthorised applications from executing on its corporate desktop and server environments”. This makes it possible for a Stuxnet like situation to occur - an attacker could simply plug in their USB and infect the system. Especially if the malware is a worm which spreads it across the network, the system is susceptible to single point of failure.
The auditor says that “risk aren’t being managed effectively”. This links back to what Richard usually says. It is about the risk not the outcome. People like to see that if there is no bad outcome, then the security is good! Perhaps Australia Post saw that they have not been hacked for a while and became complacent. This leaves them open for future attacks. So the fact that Australia Post didn’t have proper procedures in place to manage risk is already a failure, even if nothing bad has happened.
The Australian Cyber Security Centre has listed strategies that businesses should follow to mitigate cyber security incidents. https://www.cyber.gov.au/publications/strategies-to-mitigate-cyber-security-incidents.
Here are some from the page that we can all follow!
Configure Microsoft Office macro settings to block macros from the Internet, and only allow vetted macros either in 'trusted locations' with limited write access or digitally signed with a trusted certificate.
Application whitelisting of approved/trusted programs to prevent execution of unapproved/malicious programs including .exe, DLL, scripts (e.g. Windows Script Host, PowerShell and HTA) and installers.
Patch applications e.g. Flash, web browsers, Microsoft Office, Java and PDF viewers. Patch/mitigate computers with 'extreme risk' vulnerabilities within 48 hours. Use the latest version of applications.
1 note
·
View note
Text
New 'Quantum' Builder Lets Attackers Easily Create Malicious Windows Shortcuts
New ‘Quantum’ Builder Lets Attackers Easily Create Malicious Windows Shortcuts
A new malicious tool that allows cybercriminals to create malicious Windows Shortcuts (.LNK) files has been put up for sale on cybercrime forums.
Double Quantum Link Builderthe software allows you to spoof any extension and choose from over 300 icons, not to mention UAC support and bypass Windows Smart Screen as well as “multiple payloads per .LNK” file. .HTA payload and disk image (.ISO)…

View On WordPress
0 notes
Text
PayGen Tool To generate Stable Undetected Payload Features: ▫️ Create Payload With...
PayGen
Tool To generate Stable Undetected Payload
Features:
▫️ Create Payload With MsfVenom Automated
▫️ Creates a handler.rc file
▫️ Undetectable
▫️ Stop Sec Services And Kill Av Process
▫️ AutoPortForwarding(Ngrok)
▫️ Obfuscate Payload
▫️ Can Make VBS Dropper
▫️ Can Make HTA Attack
▫️ Auto Exe signing
▫️ Generate Android Payloads
▫️ shellcode injection with python
▫️ shellcode injection with powershell
https://github.com/youhacker55/PayGen

-
0 notes
Photo

Hiring. My Meeting in Dec with Film commish office and Jan with HTA again 2011and 2022 …lead to hui meeting—new law “ commercial #photographypermitrequired hawaii in effect”- anybody not kanaka ohana or aupuni moi kii, and cashing income needs a permit (used to be only film), #Weohana kanaka and maoli hawaii practitioners was and (will bel) holding it down this whole time. New transplants work-for-hire especially wedders needed a wake up call. Elopers, engage, events, influencesrs, journalists, marketers, advertising from Anywea. Make these suckers pay the taxes they never pay since 1800s. X 365 days x 300 pp photographers…You ain’t family and you aint paying for tax to education or sleeping at my wahipana (waikiki only pay to Priv and Bishop) . #iwashea2022 #futuresfuture #gettingouttahand #haoleperspective #homeofthemakaainana #makespacehawaiiancomingthrough To and For and From the Tutu Wahine- “educate the visitors, “ she (they) said. #wahipanawednesday #wilmahealaniholi #stellasilvaburgess #tedpuakinikiniblake Cutting the other ones a break before heart attacks @auntylouisetutu @memanine62 @maliaandcompany can coach you through it https://www.instagram.com/p/CbcJzgUu5I6R9vnodOG6t8qkG-Ajunaw9o1V4M0/?utm_medium=tumblr
#photographypermitrequired#weohana#iwashea2022#futuresfuture#gettingouttahand#haoleperspective#homeofthemakaainana#makespacehawaiiancomingthrough#wahipanawednesday#wilmahealaniholi#stellasilvaburgess#tedpuakinikiniblake
0 notes
Text
12.12.2020
Okay, it’s actually already 5 Mar 2021. Just back tracking as it was pretty much an eventful end of the year and start of the year for me. :)
03.10.2020 - Officially turned 30 during the pandemic.
12.12.2020 - Got married to the love of my life! Bawl on my wedding day as it rained soooooo heavily, had my first ever anxiety panic attack. What a memorable day! Never knew my emotions could get the better of me.
25.01.2021 - Career switched and came out from my comfort zone. Did something unimaginable by going into the unknown, joining the ‘dark’ force. Dropped my economical progression lifestyle of 9 years. Excited yet 80% of me is nervous as.. wait when was the last time I marched under the hot sun? Exercised and getting a GOLD on my NAPFA test? Living the regimental lifestyle? At least a good 12 years ago. Shizzz. I’ve enjoyed the stressful but fulfilling corporate world, helming good salary enough for me to travel, eat, shop luxury, buy a house, good CPF contribution and enjoy some of the good things in life. But, definitely not a meaningful/purposeful career in my opinion. So yes, into the unknown. Mixing with kids more then 4 years younger and fitter than me. Just 5 weeks into my attachment and I feel..... old yet... wiser. And I feel great that I’m joining the force at the right time, after I’m married! I can’t deal with the... ‘It’s good to be young!’ (IMO, dumb and stupid) phase. At your age boy, my ex-boyfriend (now husband) is so much more mature. :P
In exactly 10 days time, I will officially start my regimental lifestyle for a good 9 months in HTA. Gahhhhhh.... I’m scared. :’)
0 notes