#setoolkit
Explore tagged Tumblr posts
Text
Danh Sách Các Bài Tập EHACKING + PENTEST Phần 6
Danh Sách Các Bài Tập EHACKING + PENTEST Phần 5 Bài Tập CEH – SEToolkit Với AutoPWN & DNSSpoofing Setoolkit (Social-Engineer Toolkit) là một công cụ mạnh mẽ được tích hợp sẵn trong Kali Linux, chuyên dụng cho các cuộc tấn công kỹ thuật xã hội. Dưới đây là giới thiệu chi tiết về Setoolkit: Tổng quan: Được phát triển bởi TrustedSec Mã nguồn mở, viết bằng Python Tập trung vào các cuộc tấn công…
0 notes
Text
Hacking someone account through Fake Facebook Phishing Page is a thing. Now, there’s a lot of things you can do on Facebook. You can join and even start your own pages and groups, see what posts each member shares, upload your own videos, and more. But, in this post, I’ll be talking about the first, and arguably the most popular, thing you can do: Hacking Facebook accounts. Now, before we get started, let me just mention that this is a very dangerous thing to.
2 notes
·
View notes
Photo
Hack Windows Using HTA Attack The Social-Engineer Toolkit
http://www.techtrick.in/description/3493-hack-windows-using-hta-attack-the-social-engineer-toolkit-set-toolkit
#social engineering#social engineer toolkit#set toolkit#setoolkit#Hta atta k#hta attack#htaattack#Hack Windows Using HTA Attack The Social-Engineer Toolkit
2 notes
·
View notes
Text
QR Malicioso

Como ya hemos hablado hay muchas formas de que te “hackeen” o te roben con un simple clic. Pero también es posible hacerlo con algo tan inocente como es un código QR. Si alguien acaba de despertar del coma o salir de una cueva diré que un código QR no es más que la evolución del código de barras tradicional pero que te redirecciona, como por ejemplo a una web. Esto es inocente, pero a la par peligroso. Imagina que llegas a tu trabajo y ves todo empapelado con códigos QR y nadie sabe que esconden. Seguro que algún compañero o incluso tu tentado por la curiosidad lo compruebas. Este QR puede llevarte a algo tan inocente como un meme o por lo contrario descargar un Exploit automáticamente o llevarte a Facebook escondiendo una herramienta de Phishing detrás para robarte tus credenciales.
Hoy con el fin de APRENDER y sabiendo que la comunidad de PixelMuerto no van a hacer el mal, os enseñare como crear un QR y hacerle phishing mostrando Twitter.
Para esto usaremos una herramienta de Kali Linux llamada Setoolkit.
Para ejecutarla vamos a la terminal en Kali y usado el siguiente comando:
setoolkit
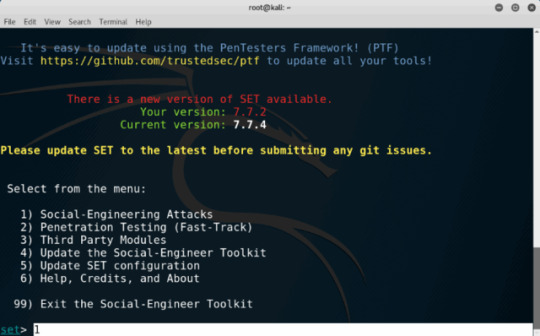
Tras esto nos saldrá el menú para el tipo de ataque que vamos a hacer, marcamos la opcion 1.
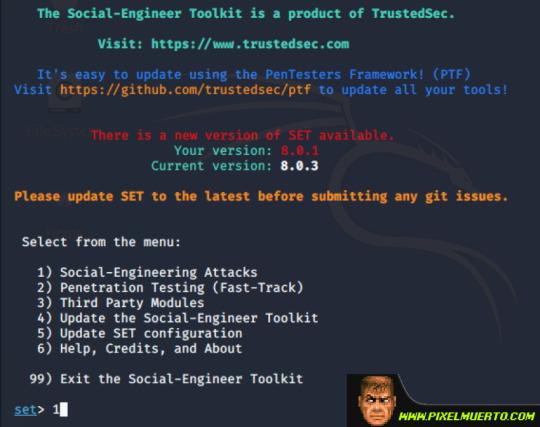
Ahora marcamos la opción 2, Website Attack Vectors.
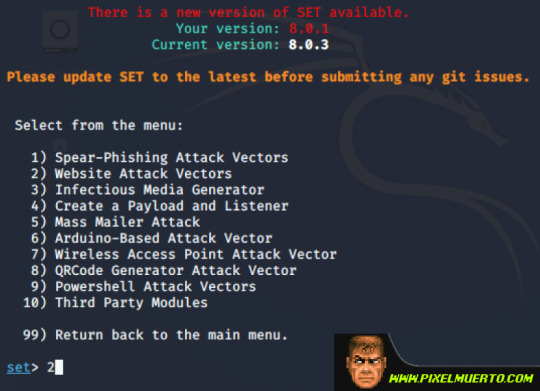
Tras esto marcaremos la opción de Credenciales ya que es lo que nos interesa, opción 3.
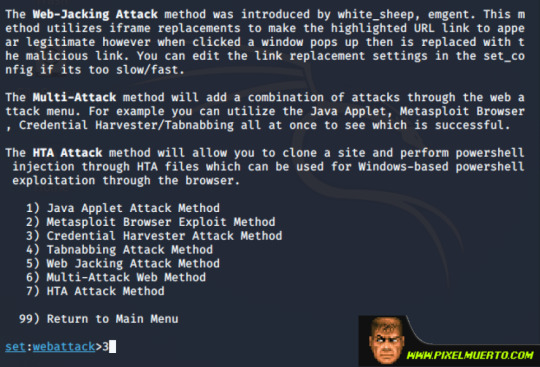
Ya tenemos definido qué tipo de ataque será. A continuación, vamos a clonar la web para el phising, opción 2.
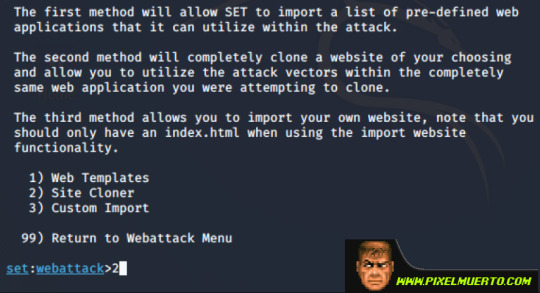
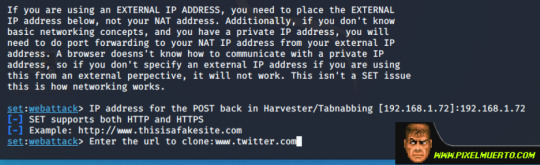
Ahora nos pide la IP donde levantaremos el falso Twitter, yo como lo voy a hacer en un entorno controlado pondré mi propia IP.
Tras esto nos pedirá que URL es la que vamos a clonar, en mi caso twitter.com.
Y con esto ya tendríamos levantado el falso twitter en mi IP, ya solo nos queda asociarlo con el QR. Para esto retrocedemos en el menú hasta llegar al inicio usando varias veces “99”.
Una vez en el inicio volvemos a marcar la opción 1.
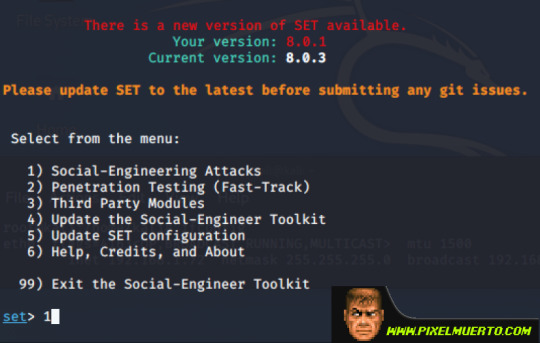
Ahora indicaremos que vamos a generar un QR, opción 8.
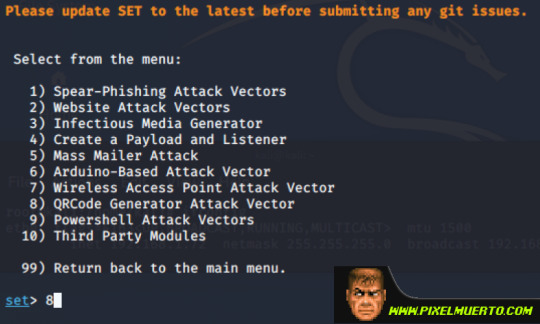
Para terminar, nos pedirá la URL donde nos llevará ese código QR, en mi caso pongo de nuevo mi propia IP.
Tras esto nos indica la ruta donde se cuenta el código QR.
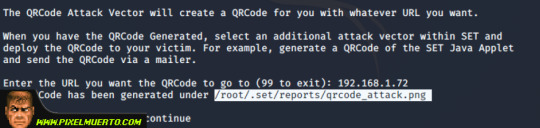
Si vamos a la ruta y abrimos la imagen .png podemos ver que efectivamente tenemos ya nuestro QR Malicioso.
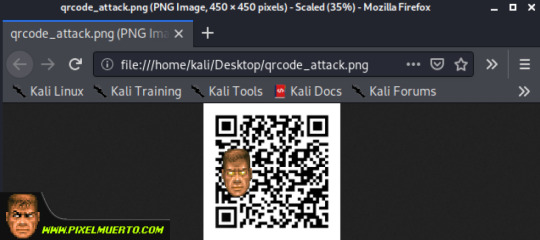
Ahora simplemente tendríamos que pasarle este código QR a la víctima. Si la victima cayera en la trampa ver la contraseña sería tan fácil como ir a la ruta “/var/www”. En esta ruta se generará un .txt con el user y la pass de la víctima.
Y esto sería el QR Malicioso. Como ya dije puedes hacer que se redireccione a un Exploit simplemente poniendo la URL o podrías hacer que se descargue alguna imagen con un troyano oculto, esto ya es al gusto del consumidor.
Esto sería como ir a un buffet libre teniendo gastroenteritis y solo tener un paquete de clínex mentolados.
Un pixel saludo.
0 notes
Text
Fsociety Hacking Tools Pack
Paquete de herramientas de hacking de Fsociety: un marco de prueba de penetración.
Fsociety es un sistema de prueba de penetración hermoso que comprende todos los dispositivos de prueba de penetración que necesita un programador. Incorpora todos los dispositivos asociados a la serie Mr. Robot. Esta herramienta consta de una inmensa lista de dispositivos que comienza con la estructura de la información del evento social para después de la explotación.
Menu
Information Gathering
Password Attacks
Wireless Testing
Exploitation Tools
Sniffing & Spoofing
Web Hacking
Private Web Hacking
Post Exploitation
Contributors
Install & Update
Information Gathering:
Nmap
Setoolkit
Host To IP
WPScan
CMS Scanner
XSStrike
Dork - Google Dorks Passive Vulnerability Auditor
Scan A server's Users
Crips
Password Attacks:
Cupp
Ncrack
Wireless Testing:
Reaver
Pixiewps
Bluetooth Honeypot
Exploitation Tools:
ATSCAN
sqlmap
Shellnoob
Commix
FTP Auto Bypass
JBoss Autopwn
Sniffing & Spoofing:
Setoolkit
SSLtrip
pyPISHER
SMTP Mailer
Web Hacking:
Drupal Hacking
Inurlbr
WordPress & Joomla Scanner
Gravity Form Scanner
File Upload Checker
WordPress Exploit Scanner
WordPress Plugins Scanner
Shell and Directory Finder
Joomla! 1.5 - 3.4.5 remote code execution
Vbulletin 5.X remote code execution
BruteX - Automatically brute force all services running on a target
Arachni - Web Application Security Scanner Framework
Private Web Hacking:
Get all websites
Get joomla websites
Get wordpress websites
Control Panel Finder
Zip Files Finder
Upload File Finder
Get server users
SQli Scanner
Ports Scan (range of ports)
Ports Scan (common ports)
Get server Info
Bypass Cloudflare
Post Exploitation:
Shell Checker
POET
Weeman
Installation
Installation Linux
bash <(wget -qO- https://git.io/vAtmB)
Installation
Download Termux
bash <(wget -qO- https://git.io/vAtmB)
33 notes
·
View notes
Text
Hacktronian. Otra herramienta all-in-one para Pentesters
Hacktronian quiere hacernos la vida más fácil a los Pentesters ofreciendo un conjunto de herramientas de hacking accesibles a través de un menú.
Lo bueno es que se puede instalar tanto en Linux como en Android (mediante Termux y siendo root)
Esto es lo que contiene la herramienta
HACKTRONIAN Menu :
Information Gathering
Password Attacks
Wireless Testing
Exploitation Tools
Sniffing & Spoofing
Web Hacking
Private Web Hacking
Post Exploitation
Install The HACKTRONIAN
Information Gathering:
Nmap
Setoolkit
Port Scanning
Host To IP
wordpress user
CMS scanner
XSStrike
Dork - Google Dorks Passive Vulnerability Auditor
Scan A server's Users
Crips
Password Attacks:
Cupp
Ncrack
Wireless Testing:
reaver
pixiewps
Fluxion
Exploitation Tools:
ATSCAN
sqlmap
Shellnoob
commix
FTP Auto Bypass
jboss-autopwn
Sniffing & Spoofing:
Setoolkit
SSLtrip
pyPISHER
SMTP Mailer
Web Hacking:
Drupal Hacking
Inurlbr
Wordpress & Joomla Scanner
Gravity Form Scanner
File Upload Checker
Wordpress Exploit Scanner
Wordpress Plugins Scanner
Shell and Directory Finder
Joomla! 1.5 - 3.4.5 remote code execution
Vbulletin 5.X remote code execution
BruteX - Automatically brute force all services running on a target
Arachni - Web Application Security Scanner Framework
Private Web Hacking:
Get all websites
Get joomla websites
Get wordpress websites
Control Panel Finder
Zip Files Finder
Upload File Finder
Get server users
SQli Scanner
Ports Scan (range of ports)
ports Scan (common ports)
Get server Info
Bypass Cloudflare
Post Exploitation:
Shell Checker
POET
Weeman
Instalación en Linux :
(la herramienta hay que ejecutarla como ROOT)
git clone https://github.com/thehackingsage/hacktronian.git
cd hacktronian
chmod +x install.sh
./install.sh
Lanzarla escribiendo hacktronian
Instalación en Android :
Abrir Termux
pkg install git
pkg install python
git clone https://github.com/thehackingsage/hacktronian.git
cd hacktronian
chmod +x hacktronian.py
python2 hacktronian.py
Más info en su repositorio de GitHub
2 notes
·
View notes
Text
Something Awesome Update
Week 4 Update
I have finished my researches on the man in the middle attack, and I will be moving onto trying the actual hack soon. Here’s a quick summary of what I need to do.
Pre-attempt:
- Download and install Kali Linux as that will be where I perform the attack.
- Install all necessary tools and programs that will assist me, such as arpspoof, apache2, setoolkit.
Attempt:
- Connect myself in-between my test-machines and their router.
- Make/clone a fake website.
- Enter in login credentials on the fake website on the test-machines and capture the data in a file.
- Test on different machines to test the reusability of this method of hacking.
1 note
·
View note
Text
Darkarmy
DARKARMY Hacking Tools Pack – A Penetration Testing Framework . DARKARMY MENU : Information Gathering Password Attacks Wireless Testing Exploitation Tools Social Engineering Web Hacking DDOS Tools Remote Administrator Tools (RAT) Bug Bounty Tools DarkArmy Tools 1ucif3r’s Tools Update The DARKARMY Information Gathering : Nmap Setoolkit Port Scanning Host To IP wordpress…

View On WordPress
0 notes
Text
SOCIAL ENGINEERING The Most Powerful Hack
SOCIAL ENGINEERING The Most Powerful Hack
Social Engineering was mentioned a few times here on Spyboy, but not very many explained what it is, or how to do it. I love this quote because it’s true:

Social Engineering is the key to carrying out client-side attacks, and all you need is a little creativity!
Social Engineering Toolkit
OTW did a general tutorial on using SEToolkit, which by the way is a fantastic tool, so I…
View On WordPress
0 notes
Text
Week4 - Something awesome
Website Clone and data analysis
The lecture this week mentioned about social engineering and phishing which give me a big picture of what I should do. After the research, I would like to create a fake website and then analyze the username and password through a python program I wrote this week.
The target website is Facebook and clones this site can be easily done by The Social-Engineer Toolkit (SET)[1]. The SET had already installed in Kali so I don’t need to install it. The site clone can be achieved below:
1. Run the program through command “setoolkit”
2. Select 1 ->“Social-Engineering Attacks”
3. Select 2 ->” Website Attack Vectors”
4. Select 3 -> “Credential Harvester Attack Method”
5. Select 2 -> “Site Cloner”
6. Enter my IP address. I just use my local The IP address which is “192.168.0.105”
7. Enter the target URL of the target website. www.facebook.com
Then, the clone is done. I can visit my fake website through visiting my local IP address which is “192.168.0.105”
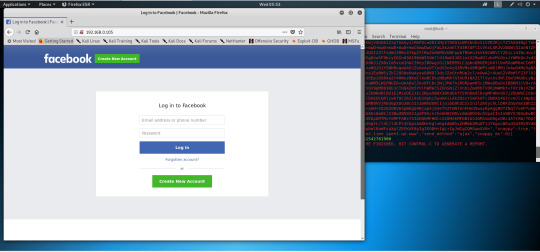
Enter the fake Email and password in the fake website for testing.
I enter “[email protected]” and “somethingawesome” and then click log in.
The SET should record the communications and then I would like to find out those messages from the log.
Press”Ctrl+c” for suspend the SET process and then the SET inform us that the report has been saved in the path “/root/.set//reports/2019-06-26 06:00:05.808897.html”.
Then I write a short python script named ‘get_email_password.py’ to analyze this log file and print the possible username and password. It takes one argument to let the script know where the log is. To invoke the program in this case, just call:
“python get_email_password.py "/root/.set//reports/2019-06-26 06:00:05.808897.html"”
Then the script generates the result and print in the terminal like this:
Find possible username: [email protected]
Find possible password: somethingawesome
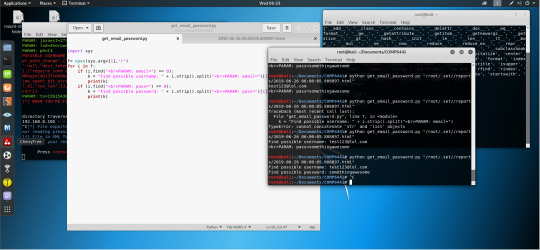
All done. That’s what I achieved this week. I plan to have a research on how to send email through python next week, hope everything goes well.
Source
[1] https://github.com/trustedsec/social-engineer-toolkit
0 notes
Text
Metasploit Master : Setoolkit
Metasploit Master : Setoolkit
Now, I hope you remember how to navigate SEToolkit, as it is very simple. Let’s start by opening the attacks menu. Step 1Open the Attacks Menu
Open SEToolkit by opening a terminal and typing setoolkit.
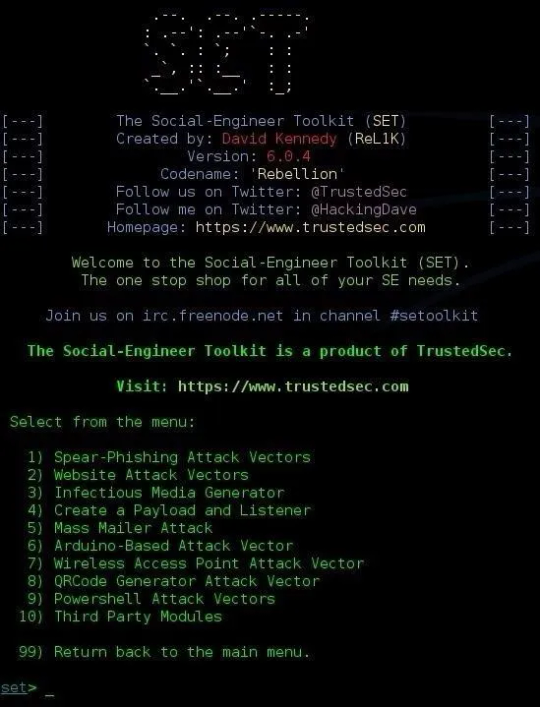
https://tpc.googlesyndication.com/safeframe/1-0-6/html/container.html
Open up the Website Attack Vectors menu by pressing 2:
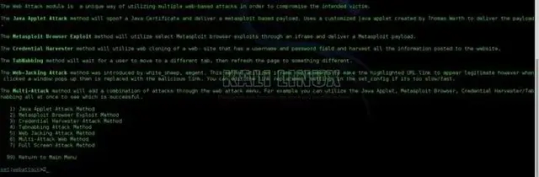
Step 2Choose Your Attack
For this…
View On WordPress
0 notes
Text
March 03, 2020 at 10:00PM - The Complete Linux System Administrator Bundle (96% discount) Ashraf
The Complete Linux System Administrator Bundle (96% discount) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
Red Hat Linux is a popular Linux based operating system used by more than 90% of Fortune Global 500 companies due to its extremely stable and secure platform, and flexibility to engage with a massive ecosystem of businesses. Through this course, you’ll learn everything about how to construct and manage a Red Hat Linux system. Before you know it, you’ll be qualified to administrate Linux systems at any company, big or small!
Access 61 lectures & 11 hours of content 24/7
Learn how to install Red Hat & Fedora Linux
Understand online information services, video & monitor information, hardware requirements & network configuration
Discover RAID & logical volumes
Execute commands, navigate the file system, create new users, modify permissions & more administrative tasks
Learn about laughing programs, Cinnamon, bundle applications & useful models w/ system setting
Manage files w/ Nemo
Beginning with a quick crash course in Linux, this course will dive into using a Virtual Machine to code apps in Linux. From a module on the advantages of Bash to writing and debugging scripts, this course is ideal for anybody who would like to work with Linux on a daily basis. Considering many leading tech and data-driven companies use Linux, this is an excellent foundation for any aspiring professional programmer.
Access 93 lectures & 17 hours of content 24/7
Learn how to manipulate the Bash environment
Understand Regexes
Use the Stream Editor to perform basic text transformations
Discover AWK programming to extract & report on data
Master interactive scripts, conditions & loops
You very likely know Windows or Mac OS X–you’re probably visiting us from one of them now. However, Linux and UNIX are two operating systems that any self-respecting programmer needs to know. Both are powerful, flexible operating systems in use by many big companies, and are common OS choices for programmers. This comprehensive course will give you the lowdown on how to optimize both.
Access 237 lectures & 43 hours of content 24/7
Study operating system concepts like concurrency, asynchronous processes, disk scheduling & more
Learn how operating systems are designed & constructed
Understand the boot process & basic configuration of Linux
Discover file, user & group management
Differentiate between Linux & UNIX & how each is useful
Learn Kernel & its features in Linux & UNIX
Kali Linux is one of the premiere distros for penetration testing: the infiltration of networks in a practical environment to test the reliability and security of systems. It is extremely portable–able to run on hardware devices like Raspberry Pi and USB Armory as well as desktops and laptops–and specifically designed for pentesting. Given that pentesters are in enormous demand these days, this course will give you an outstanding foundation in this lucrative profession.
Access 120 lectures & 22 hours of content 24/7
Become aware of the multitude of malicious attacks perforated by Black Hat Hackers
Break into or DDOS your own infrastructure to test its security
Use essential Kali Linux tools like Setoolkit, Android Malware App, Aircrack-ng & John the Ripper
Develop trojans & backdoors for Windows using Metasploit
A Bash script is a plain text file which contains a series of commands that allows a programmer to combine multiple simple tools to solve a more complex problem on Linux or UNIX servers. Learning how to write Bash script is essential for system administrators as it dramatically reduces the time needed to solve a problem. Considering most IT companies use Linux or UNIX, this course will give you a leg up on the competition to become a well-paid system administrator.
Access 25 lectures & 5 hours of content 24/7
Learn to take input from USER or FILE & output it on screen
Create your own commands using Bash script
Automate tasks for more streamlined programming
Discover essential uses of Linux
OpenSUSE is a general purpose operating system built on top of Linux Kernel, and the best open-source tool from the Linux community. Over this course, you’ll cover general Linux concepts, learn openSUSE system administration and delve into computer networking concepts and HP-UX administration tasks. If you’ve ever considered Linux system administration, this course is calling your name!
Access 11 lectures & 2 hours of content 24/7
Discuss basic principles of Linux openSUSE & learn its applications
Use command-line utilities & YaST in openSUSE Linux
Understand hard disk partitioning
Discover system setup, RPM package management, online updates, network & firewall configuration, user administration & more in an integrated interface
Prepare for the openSUSE certification exam
Python is a server-side interpreted, open-source, non-compiled scripting language that offers an extremely efficient way of scripting in Linux. It’s widely regarded as one of the easiest programming languages to learn and can accomplish complicated tasks with minimal coding, making it an excellent tool for Linux system administration. If you are, or are aspiring to be, a system administrator, network engineer or pentester, then this course is right up your alley.
Access 98 lectures & 18 hours of content 24/7
Go from basics to advanced in Python
Discover OS Soup & its uses
Build GUIs w/ Python
Learn about security related tasks, performing network scanning & open port scanning
Gain the skills you need to be a Linux system administrator
from Active Sales – SharewareOnSale https://ift.tt/3arROkU https://ift.tt/eA8V8J via Blogger https://ift.tt/2TjgIxb #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Video
Kali Linux Create a Payload and Listner SEToolkit exe File
This Video is Only For Educational Purpose we are not responsible for illegal activities.
0 notes
Video
Setoolkit in android ~~~~~~~~~~~~~~~~~ Follow us: @648.hrk @648.hrk ~~~~~~~~~~~~~~~~~ . #webdesign #code #computer #hacker #hacking #webdeveloper #coding #computerscience #hackers #hackingout #webdevelopment #coder #art #hackerpschorr #programming #computers #hackerman #hack #javascript #coders #technology #hackerstayaway #hackingthecity #codemasters #design #growthhacker #hackingaround #html https://www.instagram.com/p/BzE2YEYAeM5/?igshid=dhmu7r4zngrm
#webdesign#code#computer#hacker#hacking#webdeveloper#coding#computerscience#hackers#hackingout#webdevelopment#coder#art#hackerpschorr#programming#computers#hackerman#hack#javascript#coders#technology#hackerstayaway#hackingthecity#codemasters#design#growthhacker#hackingaround#html
0 notes
Text
I added a video to a @YouTube playlist https://t.co/tPR9AzJFOw Learn Kali Linux Episode #51: Website Cloning Using SEToolkit
I added a video to a @YouTube playlist https://t.co/tPR9AzJFOw Learn Kali Linux Episode #51: Website Cloning Using SEToolkit
— Nathan Sandy (@nathansandy2020) October 20, 2018
from Twitter https://twitter.com/nathansandy2020
0 notes
Text
SEToolkit – Credential Harvester Attack [Tutorial]
SEToolkit – Credential Harvester Attack [Tutorial]
As a penetration tester, there will be times that the client requirements will be to perform social engineering attacks against their own employees in order to test if they follow the policies and the security controls of the company. After all, if an attacker fails to gain access to a system then it might try alternative ways like social engineering attacks.
In this article, we will see how we…
View On WordPress
0 notes