Text
Surviving a Ransomware Attack in Healthcare
The rising instances of ransomware attacks is harrowing to say the least. Attackers seek to achieve quick financial gains through the use of this tactic and to be frank, it is working.
Ransomware is a type of malware that is spread through many different avenues. Organizations may run into a situation where an employee was sent a phishing email with a malicious link in it that redirects web traffic and downloads the ransomware to the user’s machine automatically. This is the most common tactic attackers will use to spread their ransomware, coming just ahead of using a spoofed website as seen in the image below:
Source: Ponemon Institute, https://www.ponemon.org/local/upload/file/Ransomware%20Report%20Final%201.pdf
How Does the Ransomware Work?
Once the ransomware is present on a machine, it starts the process of encrypting the hard drive, leaving the user with no access to any of the documents that they were working with, or that were present on the machine at all. The attackers retain access to the encryption keys and are essentially holding the organization’s data hostage until payment is received, or the organization ignores the request because they have full and accurate back-ups of all data. Typically, in these attacks, the storage on the machine is encrypted immediately, leaving the user with a screen that looks much like this:
What is the Attacker Looking to Gain?
In the case of a healthcare environment such as a hospital, this can be extremely challenging because there is no flexibility in the availability of these files. Health care providers must have them. There are times when the ability to access these documents is literally life or death. This forces the hand of the health care organization into paying the fee the attackers request. Many organizations have started to keep intermediary organizations to quickly initiate these payments in Bitcoin (which is what is typically used for these ransomware attacks).
The attackers in this case are extremely knowledgeable about the financial aspect of this type of attack, and they understand that the organizations that are targeted will likely not pay the ransom if it is too high. They have found a sweet spot in the amount of ransom to charge, and according to (Ponemon, 2017), that amount is $2,500. That is the amount that most companies are willing to pay in order to have their data decrypted and returned to the original state. In speaking specifically about health care organizations, this amount is tiny when thinking of the devastating effects that could come from not paying the attackers.
How to Protect your Organization’s Data
The first thing to do to ensure that your organization is protected from ransomware and most other types of attacks is to educate your employees about the importance of computer security and malicious links. Intelligent employees can identify and report suspicious emails to the proper authorities and ensure that there is no initial vector for the ransomware at all. Secondly, preparation is key in this situation. Preparing for the inevitable attack is the best mindset to have, and this can be in the form of mail filtering, proxies, and firewall rules. In the event that something does happen, all organizations should have a plan in place. Who do you call if you log into your computer at work and that ransomware screen pops up? There is nothing wrong with holding a tabletop exercise with your employees and walking through exactly what needs to happen. With an approach that encompasses these important aspects along with your local tactics and techniques, you can sleep well at night knowing that although you can never say that you’ve won the war, your organization has done its due diligence in preparing for the battle.
Author Bio
John Tagita Jr. is a Sr. Cybersecurity Engineer intern with Alpine Security. He holds a variety of industry certifications including CISSP, GIAC, GCFA, and CCFE. John has a passion for forensic investigations and breach response cases, application security, penetration testing, and blockchain technology. He holds degrees in Information Technology, Cyber Security, and Criminal Justice. John is currently active duty in the US Air Force service as a Cyberwarfare Training Chief.
When John is not working in the cyber security arena, you may find him developing Capture the Flag competitions, such as Hacktober or Hack The Arch, or competing himself. He also is passionate about security research and networking with other like-minded hackers. John loves spending the rest of his down-time with his beautiful wife and his four devilishly handsome sons.
Link up with John on social media at https://twitter.com/attackd0gz on Twitter, and https://www.linkedin.com/in/netsecspecialist on LinkedIn.
0 notes
Text
CIS Control 2: Are You Running Software Unaware?

My prior blog on CIS control 1 noted the importance of knowing every hardware device connected to a network. CIS control 2 also speaks to this type of basic security hygiene, only it is software and application specific. Often, attackers will look for unpatched or unsupported software to target, regardless of the system it is running on, or the type of business using it. It is a bootless errand to make sure everything hardware related is hardened as effectively as possible when deprecated or infected applications may be running in the background, allowing the point of attack all the previous hard work was meant to deny.
CIS Control 2: Inventory and Control of Software Assets
Critical Control 2 states: “Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that unauthorized and unmanaged software is found and prevented from installation or execution” (CISv7). This control is intended to prevent such things as zero-day exploits, when a previously unknown vulnerability is exploited, and other attacks through unpatched, known vulnerabilities in software applications. In order to successfully defend the software on a network, it is of vital importance to conduct a thorough and definitive software asset inventory. Like the physical asset inventory, the software asset inventory must be a live document that is constantly maintained and updated, possibly in concurrence with a patch and update list. At minimum this inventory should include the name of software and applications, along with known vulnerabilities and a system for keeping track of updates and patches. Like Control 1, Control 2 is subdivided into sub-controls to make adoption less onerous.
CIS Control 2: Sub-Controls
Sub-control 2.1: Maintain Inventory of Authorized Software.

This sub-control addresses the necessity of maintaining an up-to-date list of all authorized software necessary for an organization to run business systems for business purposes. Machines that have not been searched for all software are more likely to be running applications that may not be for business purposes, introducing an unnecessary risk. Unmonitored machines are more likely to harbor undetected malware. Once a single network foothold has been found, attackers will exfiltrate sensitive data and leverage this infected machine into several infected machines and networks as well. The infected machines may also be used as part of a DoS/DDoS campaign. Sustained and managed software control plays a critical role in executing backup, as well as planning and implementing incidence response and recovery.
Sub-control 2.2: Ensure Software is Supported by Vendor.
When software is supported by the vendor, that means there will be published lists of vulnerabilities and patches, and these will be offered to the users. When software is no longer supported by the vendor, then these patches and updates do not occur, leaving a system at risk. Many attackers will search for outmoded software usage and attack through known vulnerabilities. If any software is running that is unsupported, it should be noted in the inventory, and alternatives considered where possible.
Sub-control 2.3: Utilize Software Inventory Tools.
This will greatly simplify the software documentation process. Offerings run from commercial to open source and encompass a range of prices, so that there is a product for budget.
Sub-control 2.4: Track Software Inventory Information Software.
As previously mentioned, the inventory should record the name, version, publisher and date of installation, as well as state the authorized operating systems.
Sub-control 2.5: Integrate Hardware and Software Asset Inventories.
It is recommended to tie the hardware and software asset inventories to each other so they may be managed from one central location, for ease of management.
Sub-control 2.6: Address Unapproved Software.
This is a good point in the process to address the issue of any unauthorized software that may have been found. It is good if there is a company policy for unauthorized software usage, but for our purposes the software should be either removed or added to the inventory.
Sub-control 2.7: Utilize Application Whitelisting.
Application whitelisting is the creation of an allowable software list. Only software on this list will start and run on the system. Anything not on the list will be prevented from starting and running.
Sub-control 2.8: Implement Application Whitelisting of Libraries.
This is the process of allowing only certain types of software to run, such as “dll.”, “ocx.”, etc. These specifications can help prevent malicious versions of acceptable software from running.
Sub-control 2.9: Implement Application Whitelisting Scripts.
Application whitelisting must also protect the system against any unauthorized scripts.
Sub-Control 2.10: Physically or Logically Separate High-Risk Applications.

Some applications may be needed to conduct business, but are inherently riskier than other applications. These applications should be isolated by segmentation or with a dedicated operating system and workstation.
At this time, whitelisting programs are often being bundled with firewalls and IDS/IPS. Most offer customizable whitelisting, and some allow for “gray” list functions, such as allowing administration to determine what programs can use what resources at what time of day.
CIS Control 2 and Beyond
Of course, implementing the CIS controls is not something that can be accomplished in a short amount of time, and many seek specialized help. Alpine Security offers assistance to businesses of any size to ascertain how far they have already complied, and in what areas they may still need to make changes. If the list seems long and the task ahead daunting, our specialists can help break things down and give your organization a roadmap to completion. Alpine Security always offers a free consultation on our Enterprise Security Audit (ESA) Service. The ESA is based on the Top 20 Critical Controls published by the Center for Internet Security. The ESA is intended to provide a comprehensive picture of where an organization currently falls in Critical Control Implementation, while also delineating a roadmap for full implementation. With the increase in variety and methods of attack on organizations of all sizes and types, running malicious software unaware can become much more costly than the time spent making sure an organization knows everything that should be running on their system, and more easily able to spot when something should not be.
Author Bio

Mary, striking a Yoga Tree Pose
Mary Thierry is a Cybersecurity Analyst and Office Manager with Alpine Security. She is earning her Master’s Degree in Cybersecurity from Maryville University in Missouri. Mary was raised in rural Illinois on a farm, in a town with 500 people in it. If you ask her nicely, Mary will tell you how to start heavy machinery on a cold morning, the best types of fertilizer, and the best places to build a deer stand. Earlier in her career, Mary taught special education, and then worked as a higher education facilitator for disadvantaged teens. Mary has a disabled daughter and is an advocate for persons with disabilities. Outside work, Mary loves to spend time with her family, bake, read Science Fiction/Horror and attend Yoga classes.
0 notes
Text
Vulnerability Assessment With Nessus Home - Part 1
Part One of a Two-Part series
Introduction
If you work in the field of Information Technology, you have probably heard of Vulnerability Assessment (VA). VA is a process of identifying security vulnerabilities in a system. It is recommended that you conduct a VA against your organization's network every quarter, and if your organization follows certain policy and standards, such as PCI DSS, VA is a requirement. However, organizations should not be the only ones conducting VAs against their network; average home users should also conduct vulnerability assessment against their network. In this blog, I will guide you through the process of performing a VA against your network using Nessus Home.
What Is Nessus?
Nessus is a vulnerability scanner developed by Tenable and there are two versions of it: Nessus Home and Nessus Professional. Basically, the major differences between the two are that you can only scan up to 16 IP addresses per scanner, and you won’t be able to perform compliance checks and content audits with Nessus Home. Most average users will not have more than 16 systems, and there is no need to run compliance checks or content audits on your home systems.
Vulnerability assessments are typically done by running authenticated scans, which means the scanner will authenticate against the systems its scanning. The scan will then come back with much more detailed information about a system. With Nessus, you can perform authenticated scans against different operating systems such as Windows, Linux, and Mac OS via different methods such as SMB, SSH, SNMP, Telnet, etc.
Installing and Setting Up Nessus
For demonstration purposes, I will walk you through the process of installing and setting up Nessus and performing an authenticated scan against Windows 10.
To use Nessus, you need to obtain an activation code on Tenable's website, which is (https://www.tenable.com/products/nessus-home). Use your name and email address, and the code will be sent to your email.

Registering for an Activation Code

Emailed Activation Code
Once you receive your code, go to this page (https://www.tenable.com/downloads/nessus) and download Nessus. Choose the appropriate package. In my case, I'm going to download the package for Windows 10 (64-bit).

Downloading Nessus
Install Nessus. During the installation, Nessus will install a tool called WinPcap, which will allow Nessus to capture live network traffic. Check Automatically start the WinPcap driver at boot time option and install WinPcap.

Nessus installer

Nessus Setup Wizard

Select the start the WinPcap driver at boot option
Nessus runs on TCP Port 8834 on your local machine. To access the web console, open a browser and navigate to https://localhost:8834. Once the installation is complete, your default browser will open, and it will ask you to connect via SSL. Click Connect via SSL and your browser will display a warning saying that the certificate cannot be trusted. This is normal since Nessus uses a self-signed certificate. Proceed by clicking Go on to the webpage (Different browsers will have different wording, but they will give you an option to accept the risk and proceed).

Welcome to Nessus!

Certificate Warning, Select Go on to the webpage
Create your account. Make sure you use a strong password! Once you create an account, you will be asked to enter your activation code that was sent to your email. After you enter the code and click Continue, Nessus will start to set up the plugins and other files that it needs to perform a scan. This process will take a while so take a break and come back in an hour or so. After the setup is complete, you’ll be greeted by the web console.
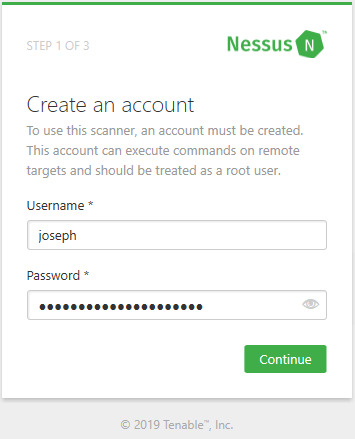
Creating a Nessus account

Registering the scanner

Initializing Nessus

Nessus using Localhost and Port 8834
You can create a new scan by clicking New Scan on the upper right corner. You’ll see that certain templates aren’t available until you upgrade to Nessus Professional, but you still have access to templates such as Advanced Scan, Basic Network Scan, Host Discovery, Malware Scan, Spectre and Meltdown, and WannaCry Ransomware. It is straight forward to use these templates; you give it the IP addresses you want to scan, and credentials if you want to perform the recommended authenticated scan. Setting up a scan and properly performing an authenticated scan will be covered in Part II.

Listing of Scan Templates for Nessus
Useful Tips and Tricks
Now, I would like to share how some tips and tricks that I’ve acquired using Nessus for about a year. This is a personal preference, so you do not have to follow my suggestions. It will involve tweaking some settings and if you don’t want to, that’s fine. It won’t affect the performance of the Nessus scans.
By default, Nessus will automatically start and run in the background on boot on Windows. I don’t like how it’s running when I don’t need it (On Linux, Nessus does not start automatically by default and you need to start it manually, which is what I prefer!). In order to prevent Nessus starting on boot, open Services and find Tenable Nessus on the list. You will see that it is set to Automatic. To change this, right click on it and set Startup type to Manual. Nessus won’t start on boot anymore and you’ll have to manually start/stop it. To do so, open a Command Promptor PowerShell and type net stop/start “Tenable Nessus”.

Windows Services

Configuring Nessus to manual start using Windows Services

Net Start/Stop of Nessus
According to Tenable, they release more than 100 plugins weekly. This means that you will have to update Nessus frequently in order to use those new plugins. If there is an update available, Nessus will let you know when you log into the GUI. However, I prefer updating it from the command line. To do this, open a Command Prompt or PowerShell as an administrator and navigate to C:\Program Files\Tenable\Nessus directory. Once you are there, type .\nessuscli.exe update –all (.\ is not needed if you are doing this from the Command Prompt). Nessus will download the updates from nessus.org. Make sure to restart Nessus after you update it.
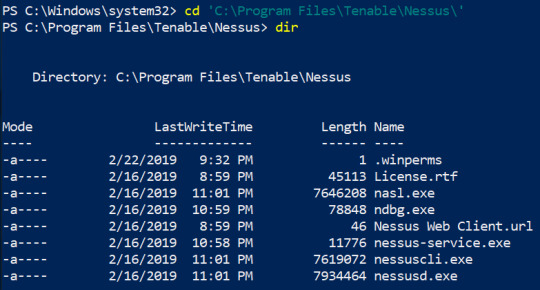
Nessus Directory

Nessus Update from command line
Lastly, Nessus rates the findings with its severity levels: Critical, High, Medium, Low, and Informational. Prior to Nessus v8, it listed the findings by severity but now it “groups” certain findings. I find this feature not very helpful and annoying, so I disabled it right away. To do so, click on Settings next to Scans, go to Advanced, and type groups. This will return two settings: Use Mixed Vulnerability Groups and Use Vulnerability Groups. Set the values to No. You are welcome.

Nessus Groups

Nessus Advanced Settings
Conclusion
Nessus Home is a great vulnerability scanner that everyone should be using, not just cybersecurity professionals. In this blog, I’ve demonstrated installing and setting up Nessus on Windows. In Part II, I will demonstrate how to set up an authenticated scan and tweak some settings on Windows to allow Nessus to perform an authenticated scan.

Author Bio
Joseph Choi is a Cybersecurity Analyst with Alpine Security. He holds several security-related certifications, including Certified Ethical Hacker (CEH), EC-Council Certified Security Analyst (ECSA), CyberSec First Responder (CFR), Security+, and Network+. Joseph is a graduate from Truman State University with a B.S. in Business Administration.
Joseph's cybersecurity experience began at Alpine and includes penetration tests, vulnerability assessments, and wireless penetration tests. He was born and raised in South Korea until the age of 10 when he moved to Mexico. It wasn't until 2007 that his family moved to the States where he completed his high school and college education. He is a fan of Mr. Robot, and in his spare time he enjoys spending time with his girlfriend, taking long walks around the park, and going to the gym.
0 notes
Text
Mr. Robot Walkthrough (Vulnhub)
Anyone who is inspired to partake in a challenging course such as the Offensive Security Certified Professional (OSCP), or Licensed Penetration Tester-Master (LPT (Master)), knows that practice makes you a better hacker. Vulnhub is a great resource to find purpose-built virtual machine images to practice on. This image is based on a popular TV show, and we are going to walk through exploiting it together.
The first step in the hacker’s methodology is enumeration, so that is where we will start, with an Nmap scan of our target’s IP.
Nmap scan performing enumeration of the target
We have found a web service, as well as SSH running. We will look deeper at the web service to see if there is anything there that we can take advantage of.
Mr. Robot based scenario - #fsociety
No typical commands work here, so I choose to run Nikto against the server to see if there are any glaring vulnerabilities.
Alright, we can see the directory contents. There is a file there, so let us grab it.
Captured the dictionary file but still need usernames
We've found a dictionary file for a password attack, but we do not have any usernames yet... let us keep looking.
Running Nikto reveals that a WordPress site is being hosted at that IP, which is obviously a high-value target any time we find it.
Nikto is web server scanner which performs comprehensive tests against web servers.
We can jump right in to the WPSCAN and see what we can come up with.
WPSCAN is a WordPress vulnerability scanner.
There are tons of vulnerabilities and I am not positive any are going to lead anywhere, so I will start a brute force on the user "root" while I do some more enumeration.
Brute force attack against the system administrator account or “root”.
Through our Nikto results, we saw a few more pages to check out. At /readme (grammatical mistake is courtesy of the page).
Based on prior WP knowledge, we know that there should be a login page, so let us check it out at /wp-login:
WordPress login page
Now that we have a login page and a dictionary file, let us try to login. This time, we will use WPScan again, and we will use the file as a user file and a pass file. And... we are in.
Successful credentialed login using the dictionary file.
We can do a lot more to the server now that we have credentialed access.
Since the environment I am in does not lend itself to a reverse shell, and I am unable to upload a php file, I must be a bit more creative.
There is a project called the WordPress Exploit Framework (WPXF) that I have not had a chance to play around with, so this might be a good opportunity. After a brief break for configuration and installation, we have WPXF running on Kali.
WordPress Exploit Framework (WPXF)
This worked well, and I was able to find a new user, "robot", and a password of "abcdefghijklmnopqrstuvwxyz". Now we will jump into ssh and see if we can figure the rest of this challenge out.
SSH using robot as the user name
Since we have found 2 of 3, we know there is one more key out there. Now we will try a search using regex to find the file.
Without root access, we are not going to find it, but luckily Doc Sewell just reminded me that Nmap runs as root during our LPT-M class, and I saw that Nmap is present, so we will try to exploit this.
Found key 3 using Nmap
So, that is all there is to this machine. Using the knowledge that we have from the LPT-M and general hacker’s methodology, we were able to easily exploit the box and find all three keys. If you are interested, check out the VM at https://www.vulnhub.com/entry/mr-robot-1,151/ and give it a shot.
Author Bio
John Tagita Jr. is a Sr. Cybersecurity Engineer intern with Alpine Security. He holds a variety of industry certifications including CISSP, GIAC, GCFA, and CCFE. John has a passion for forensic investigations and breach response cases, application security, penetration testing, and blockchain technology. He holds degrees in Information Technology, Cyber Security, and Criminal Justice. John is currently active duty in the US Air Force service as a Cyberwarfare Training Chief.
When John is not working in the cybersecurity arena, you may find him developing Capture the Flag competitions, such as Hacktober or Hack The Arch, or competing himself. He also is passionate about security research and networking with other like-minded hackers. John loves spending the rest of his down-time with his beautiful wife and his four devilishly handsome sons.
Link up with John on social media at https://twitter.com/attackd0gz on Twitter, and https://www.linkedin.com/in/netsecspecialist on LinkedIn.
0 notes
Text
Incident Response Plan: The Tool You Hope You Never Need
It’s no question that in cybersecurity, defense is the best offense. In the constantly changing threat landscape, the tie often goes to the attacker, and businesses are forced to act like turtles putting up shells of security to ward off threats. That is not always a bad thing; using a well-constructed defense- in- depth plan can greatly limit the likelihood of a successful attack. I would like to believe we can get to a 99.99% level of security. Even if that were true, that extra .01% keeps me up at night. What do we do if the controls fail? How do we respond then? What do we do the other 1% of the time? Once we find out that our emails have been hacked, or our money has been stolen is not the time to ask, “what now?” Even worse, what do you do when you suspect that an insider has embezzled funds and the evidence is located on their computer? Though we invest in and rely on our security controls, it is unfortunately not always enough. We must have a plan for the .01%.
Those Who Fail to Plan, Plan to Fail.
In the world of cybersecurity, one of the biggest reasons companies find themselves becoming victims is because they fail to plan for their IT growth, especially for security. Often small to medium business put little to no thought into cybersecurity until after they have become a victim. As a business grows the need to protect that growth comes with a lot of hard decisions. Many times, a balance must be struck between expanding revenue, generating sources like equipment, and personnel and infrastructures like email servers and IT staff. Many businesses quickly find themselves outgrowing their IT infrastructure before they even realize it has happened. They often don’t realize they have a problem until a compromise or critical failure takes place.
What’s At Stake?
It is imperative to consider what is at stake. The answer is possibly more than you think. Recently a client asked me to give them some case studies to show what the costs of not being properly prepared could be. In one case a small business had $1.5M stolen from their bank accounts over a period of three days using a fairly straightforward cyberattack. Within a few weeks, they were forced to lay off employees and file bankruptcy. Other less obvious risks arise that business may not know how to deal with until it is too late. What happens if an employee uses a personal device on the company network for illegal activity? Is the company protected? What if an employee embezzles funds from a partner corporation and millions in contracts are tied up in litigation? What do you do with that employee’s computers and devices? These are the types of situations that we see on a daily basis and represent that .01 % of cases in which one wrong move could mean the difference between liquidation and salvation. Obviously, we cannot plan for everything, but having a well-laid incident response plan and a trained team in place to execute can prevent a lot of grief in the long run.
What is an Incident Response Plan (IRP)?
The goal of an incident response plan is to have an answer prepared for those “what if” situations. The type of situation can vary from a power outage to a data breach, and the depth of the incident response planning should be based on the likelihood of an event taking place and the severity and level of impact if it does. The incident response plan will outline important information about communications during critical events; it may go as far as to outline authority and decision making matrices to ensure that risk is accepted at the appropriate level.
Key Areas to Cover
Incident response planning can be a daunting task at first glance. There is no end to the number of circumstances that can arise. The real key is to outline how to respond to incidents in a methodical manner, as well as identify who is responsible for acting during a crisis (see Incident Response Team below). The process of incident response is generally broken into 6 areas. Specific checklists and policies can be created for known risks, but these same steps can be used when an event you are unprepared for arises.
1. Preparation – Creating policies and establishing standards for what constitutes an incident. Practicing and conducting drills or exercises to respond to incidents.
2. Identification/ Detection – Tactics techniques and procedures to detect an incident in progress.
3. Containment – Taking steps to prevent the spread or continuation of a breach or incident. This could be as simple as segregating a computer from a network or as complex as removing access to major systems.
4. Eradication – Remove any corrupt or infected files, restore backups, ensure no other systems have been impacted. Restore or replace affected systems.
5. Recovery – Return all systems to full operation.
6. Review Lessons Learned – Identifying what went right or wrong from the incident for future use.
These steps may seem simple at first glance but can quickly become complicated. For example, If an IT staff member determines that a website has been infiltrated does that member then have the authority to take the web server offline while further investigation is conducted? How much revenue will be lost during the outage? Will other system be impacted? What are the risks of operating with a potentially compromised system? Outlining how much risk is acceptable and what level of management is responsible for accepting that risk is critical prior to an incident taking place.
Also of note, the preservation of evidence should be kept at the forefront during all of these stages, especially if there are legal or financial implications for the company or its employees. In some cases, evidence can be destroyed or made useless by something as simple as turning off a computer. Therefore training staff on what to do in these situations is so important. If there are any legal or financial implications, it may be worth bringing in a certified digital forensics team to assist with the protection of evidence. If that is a function that doesn’t exist in-house, bringing in an outside cyber forensics team should be part of the IRP.
Incident Response Team (IRT)
An important aspect of incident response planning is the establishment and training of an IRT. The IRT will be the boots on the ground that will lead the efforts during a cyber incident. While they may not do all the work themselves, these will be the key players who will oversee and coordinate the response to cyber incidents. It may be unrealistic to have all staff trained to handle an incident, so having a team of staff identified and trained ahead of time is key to proper indecent handling. The team should be small enough to be agile, as well as contain multidiscipline employees to allow for perspective and cross-functionality. Ideally, the team will be led by the CISO and contain members of the IT staff. It may also be wise to consider having personnel from other business units, especially legal, HR, and public relations.
Practice, Practice, Practice.
Having an incident response plan sounds good on paper (pun intended), but it is important to test the plan on a regular basis. This will ensure that the team is still current on their responsibilities, able to identify holes in the plan, and give you an opportunity to update for any changes since the last time the IRT was practiced or used. I recommend testing IRP at least semiannually and revisiting it anytime major changes are made to the business or its infrastructures.
It’s Dangerous to Go Alone
It’s ok not to be the expert at everything. You are already great at what you do! If you would like help with security control audits, incident response planning, digital forensics, incident response, or any other cybersecurity service, Alpine Security is just a click away. Often it is more cost effective and less stressful to bring in a consulting team to help whip an organization into shape than try and go it alone.
Author Bio
Isaac (on the left) hiking in Vietnam
Isaac Wright is a Cybersecurity Analyst and Trainer with Alpine Security. A veteran of the US Air Force, Isaac has more than 15 years’ experience in electronics maintenance and security. He holds degrees in Electronics Systems and Education and Training Management as well as a master instructor certification. Isaac has a long history of maintaining, hacking, modding, and using electronics systems from networks and computers to radios and consumer electronics. Isaac has leveraged his expertise to advise CIOs in large multi-site organizations on vulnerability management and risk mitigation.
When not teaching or analyzing network traffic, Isaac loves to play board games with family, fish, camp, and experience everything the world has to offer. An avid traveler, Isaac has been to more than 15 countries and especially enjoys Asia.
0 notes
Text
General Data Protection Regulation (GDPR) Overview

The new European Union (EU) Regulation 2016/679 GDPR (General Data Protection Regulation) have gone into effect May 25, 2018. This will have a far-reaching effect and identify many possible repercussions for any organization collecting, processing, and/or storing any EU citizen’s information. Your company need not be located in any of the EU countries; rather if your company collects any EU citizen’s information, your company must adhere to and be complaint to the new regulation.
The essential characteristics of the regulation are to protect personal data as a fundamental right and that privacy is to be respected as an expectation of the GDPR. The GDPR creates a greater level of harmonization across the EU for the sharing and exchange of data. Implementation of the GDPR requirements necessitates a greater level of protection of a person’s digital identity. The reason for such an increased worldwide emphasis on compliance is due to the imposed fines that can be applied if you fail to manage the privacy data appropriately. Fines are set at 4% of the noncompliant organization’s global revenue
Who is Responsible for GDPR?
There are two specific roles that are defined in the regulations, the first is the data controller and the other position is the data processor. A data controller is the collector of the data for internal or outsourced processing. The expectation is that an individual’s consent is required to collect the information. This role is responsible for documenting the format of how the data is to be utilized throughout its lifecycle within the organization, privacy policies, and the ability to process requests for data portability, rectification, objection, etc. The duties that are required for this role include compliance to protect the data subject’s rights. Examples of data controllers include social media organizations, education institutions, health organizations, banks, etc. If your organization determines how the data is to be processed and the purpose of that processing, this indicates a data controller.
A data processor is a natural or legal person, public authority, agency or other body responsible for managing and storing data on behalf of the controller. Specific clauses within the regulation require the same technical and organizational measures to be applied to the controller as well as the processor. An example would be an outsourced payroll company; the data controller tells the payroll organization who to pay and what amount. If you are not making these decisions and just acting on a request, this indicates a data processor. The required liability flows through the chain of data processing. Specifically, the data controller has liability if a data processor fails to fulfill his obligations.
What data is in scope?
Article 4(1) states: “‘personal data means any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person;” Elements of data types could include IP addresses, cookie data, or a photograph associated to an account. In many cases, personal customer data will be in multiple formats and forms in CRMs (Customer Relationship Management systems), contracts, sales contact databases, etc.
How CIS can help
Specific to the data controller and the data processor roles, responsibilities are to “implement appropriate technical and organizational measures to ensure and be able to demonstrate that processing is performed in accordance with the regulation.” CIS offers a multitude of best practices and cybersecurity solutions to help organizations on the path to GDPR compliance.
A strong starting point is to utilize a CIS SecureSuite Membership, which includes access to tools such as CIS-CAT Pro and remediation kits, to assess and harden systems. “Hardening” is the process of limiting vulnerabilities in a system to reduce cyber threats. Hardening systems to the CIS Benchmarks™, secure configuration guidelines for over 150 technologies, provides a platform for compliance and is a recognized foundation to build your remaining data infrastructure. Measure system conformance to the CIS Benchmarks with CIS-CAT Pro Assessor, our configuration assessment tool which provides assurance that the target system is hardened to the standard. It is not sufficient to simply state compliance to a particular benchmark – measure and prove it with the dynamic reporting features of CIS-CAT Pro Dashboard.

If you are working in the cloud, the CIS controls offer pre-hardened virtual machines on the Microsoft Azure Marketplace and Google Cloud Platform (GCP), and Amazon Machine Images (AMIs) on Amazon Web Services in the AWS Marketplace, including the AWS GovCloud (US) region and IC region. CIS Hardened Images conform to the applicable security standards of the CIS Benchmarks, bringing on-demand security to cloud computing environments.
The CIS Controls are a prioritized set of cybersecurity best practices to help organizations improve their security posture. Version 7 of the CIS Controls was released in March 2018 and contains following guidance that can be applied to GDPR compliance. The CIS Controls can serve both as a measurement process to encourage compliance as well as for implementing a security control framework within your organization. In many cases, the entire CIS Controls can be applicable to implement a structured and measured approach to compliance and security for the organization. GDPR will require a complete understanding and visualization of the data flows for personal information throughout your enterprise. The regulation extends to data controllers and processors. It may seem challenging at first, but with due diligence, documented plans, and help from the cybersecurity resources available from CIS, the road to compliance is achievable.
Why is this applicable to companies in the United States?
Why is this applicable to companies in the United States if your company is not doing any business with EU countries? California will soon be implementing the California Consumer Protection Act (CCPA) in July of 2020. California’s CCPA mirrors the EU Regulation 2016/679 for GDPR. Companies in New York doing business with companies in California and collecting consumer data will be required to meet the CCPA. Companies need to move forward and begin the process on GDPR compliance. Here are three key areas in which to move ahead with compliance readiness:
Analyze, develop, and execute GDPR programs across your organization’s systems, processes, people, and policies
Make it a team effort - Get all of your relevant teams working together
Ensure buy-in from your management to stay on top of GDPR compliance
GDPR will ultimately lead to companies gathering just enough data from individuals in order to complete any type of conversion, transaction, or order agreement. But the optimistic viewpoint is that with greater clarity of data protection and privacy controls, consumers will become more comfortable with emerging digital practices, and when working with companies, will be able to form trust with these companies to hold their personal information in high regard.
Author Bio

Doug, shredding a solo.
Doug Stewart is a Senior Sales Manager. Doug brings a wealth of experience and is focused on sales and business development activities. Doug strives to help businesses meet the demands of their on-going cybersecurity requirements and helps them be adequately protected against cyber intrusions.
Doug is located in Colorado where he majored in Music and played hockey at Denver University. He played in a highly competitive hockey league for 24 years post college, and coached his children’s soccer and hockey teams for 12 years. Music is still a strong passion which he pursues professionally with his band. He and his wife are the proud grandparents to three grand kids.
0 notes
Text
Alpine Security Launches Cyber Infinity Training Program
O’Fallon, IL - Alpine Security (“Alpine”), a leading cybersecurity training, penetration testing, and audit firm, announces the launch of their Cyber Infinity Training Program.


The Alpine Security Cyber Infinity Programs consists of 12 months of unlimited certification training for $9,995. Included in the fee for the Cyber Infinity program are all course materials, remote labs, one exam voucher per class, and the Alpine Security exam pass guarantee. The Alpine Security Exam Pass guarantee allows students to retake a class free of charge if they do not feel ready for the exam after going through the training, or if they do not pass the exam in their first attempt. All Alpine Security’s certification training course offerings are included in the program.
“We are excited to introduce this new addition to our training programs,” says Cecilie Kreiner, Alpine Security’s Director of Training. “Whether new to the field or validating current skills via credentials, we encourage our students to map out their career path. The unlimited training in the Cyber Infinity Program allows you to customize your certification track with your personal career goals in mind. Whether you want to specialize in the offensive or defensive tracks, focus on cybersecurity management or cyber forensics, or create a well-rounded package with a variety of cybersecurity certifications, our wide selection of certification training classes can help you reach your goals.“
Alpine Security offers certification training courses from CompTIA, EC-Council, and (ISC)2, as well as hands-on, technical training in a variety of topics such as Wireshark training and malware analysis. Alpine is a CompTIA Authorized partner and EC-Council Accredited Training Center, and was awarded the EC-Council Best Newcomer of the Year in 2017.
Alpine offers the complete CompTIA Cybersecurity Track, starting with the Core Skills Certification Security+. The CompTIA cybersecurity track provides a clear path for those starting a career in cybersecurity and for seasoned cybersecurity professionals looking to advance their career by proving their knowledge, skills, and abilities through certifications. Alpine’s EC-Council offerings include Computer Hacking Forensic Investigator (CHFI), Certified CISO, as well as the complete EC-Council Penetration Testing Track, from Certified Ethical Hacker (CEHv10) to LPT Master. Alpine Security’s (ISC)2 course offerings include CISSP and CAP.
For more information on the Cyber Infinity Training Program, please visit: https://www.alpinesecurity.com/training/cyber-infinity-program
ABOUT ALPINE SECURITY
Alpine Security, a Service Disabled Veteran Owned Small Business, offers a comprehensive suite of cybersecurity services and cybersecurity training. Alpine Security’s instructors are all practitioners who work as penetration testers, incident response handlers, forensic analysts, auditors, and more. This allows them to bring practical, real-world, and up-to-date experience into the classroom. Alpine Security mandates continuous training and certifications for everyone on their team, and all trainers have had to pass their rigorous Train-the-Trainer course as well as recurring courses on effective training and communication.
0 notes
Text
Protecting Internet Communications
Introduction
Today we all communicate constantly over the internet. Some people say we spend too much time on our mobile devices, and we do not interact enough with the world, and with the people around us. However, that is a discussion for another time. In this blog post we want to discuss how we keep our internet communications secure from eavesdropping.

E-Mail
Let us start with the granddaddy of internet communications protocols: E-Mail. Almost before there was any other way of communicating over the internet, there was E-Mail. It ran over a protocol called Post Office Protocol, or POP. The final version of the protocol is POP3. There was only one way to access our email, and that was using an E-Mail client such as Microsoft’s Outlook or Netscape Communicator (old school!) or Eudora (double old school!).
Back in the day there were only a couple of ways to keep your email secure, and that was through encryption. There were a couple of different ways to encrypt email using either a digital certificate or a software suite such as Pretty Good Privacy (PGP). There was also an open source version called Gnu Privacy Guard (GPG).
Both methods are still around and are still effective, although PGP has evolved a bit. It is now owned by Symantec and is part of their Endpoint Security suite solution. Even though the methods for protecting our email communications have evolved, they are still there, and still important. We still send a variety of sensitive information via E-Mail, and we need to protect it.
The easiest way to encrypt our email is to use a digital certificate, also known as a Public Key Certificate . There are a range of options available to obtain an E-Mail digital certificate which is then installed into your E-Mail client and allows you to sign and encrypt email. The drawbacks are that you must be using a dedicated E-Mail client such as Outlook, Apple Mail, or Mozilla Thunderbird , and the people you are communicating with must also have a digital certificate. The same applies if you are using PGP/GPG. Everyone must be using it for it to be effective.
Fortunately, our E-Mail providers are also looking out for us. Companies like Google and Microsoft that provide E-Mail services use end-to-end transport encryption to help make our communications more secure.
Messaging
All the proceeding brings us to the new kid on the block of internet communications: instant messaging. Or just “messaging” as it’s called now.
Messaging started out on our early mobile phones as text messages, which are not and never were secure. However, today we have a variety of ways we can message each other securely from the Messages app in iOS to Whatsapp to Signal to Slack, etc.
“How are these mobile apps secure?”, I can hear you asking. It is a good question. They all use encryption to make sure no one else can eavesdrop on your messages with your friends, family, and business contacts. Apple was one of the first to do this for its customers when it started encrypting the messages between iCloud users. The drawback is, (and you knew one must be coming), the encryption only works between iCloud users. When you send a message, using the Messages app in iOS, to your friend who uses a smart phone that runs a different mobile operating system, such as Android, the message is a plain, unencrypted text message.
Which brings us to the other mobile apps that will help us communicate securely. There are a lot of them out there, but two that we would like to mention are Signal and Whatsapp. Many, many people use these apps daily to communicate securely and if you communicate with people who use a variety of mobile devices you should too. Some of these apps will even let you make encrypted phone calls, which is a big plus. There is also another kind of solution.
VPNs

One of the other ways to secure your communications is to use a Virtual Private Network (VPN). Many of us, like me, are used to being able to take our laptops down to the local coffee shop, or with us when we travel, connect to any ‘ole Wi-Fi, and then keep doing what we always do on the internet. What you may not be aware of however, is that unlike our home Wi-Fi networks which are encrypted, open, public Wi-Fi that we get at coffee shops, libraries, airports, etc., are not encrypted. Anything done on those wireless networks can be intercepted by nefarious people. A good rule of thumb is, if you don’t have to enter a passphrase to connect to the wireless, it is not secure.
So how do you secure wireless? I’m glad you asked! It is secured by using a VPN. As with the encryption methods for E-Mail and messaging, there are a variety of VPN providers out there that do not cost a lot of money. An individual or organization should research and decide which one is best for their respective needs. It is not recommended to use a free VPN provider. Free VPN providers can be iffy because they get much of their funding via pushing ads to their users. One way they do that is by tracking what you do, which kind of defeats the purpose of using a VPN in the first place.
Returning to how a VPN can protect your communications, we could go into a lot of detail about what a VPN does, but we will keep it simple instead. Unlike the secure solutions above, which are very specific, a VPN works by creating a tunnel between you and a remote server. This tunnel is encrypted, which means that everything you send through it is protected from eavesdropping. This can be especially useful if you are working at the aforementioned coffee shop or airport.
Summary
All the information included in this blog is really our way of getting you to think about how, and who, you are communicating with on the internet, and what data you are sending. The bad guys are out there, and they are always watching and trying to get anything they can. If you are planning a birthday party for your best friend or sending your bank information to your CPA at tax time, do it securely. Do not make it easy for the bad guys!
Author Bio

Michael with his foster pit bull, Toby.
Michael Allbritton is a Cybersecurity Analyst and Trainer with Alpine Security. He holds several security-related certifications, including Certified Information Systems Security Professional (CISSP), Network+, Security+ and CyberSec First Responder (CFR). Michael has many years of experience in software testing, professional services, and project management. He is equally comfortable working with software engineers on testing and design and with sales to meet and manage customer expectations. Michael’s cybersecurity experience with Alpine includes penetration testing, vulnerability assessments, and social engineering engagements for various clients as well as teaching courses for the above-mentioned certifications.
In his spare time Michael is an enthusiastic amateur photographer, diver, and world traveler. He has photographed wildlife and landscapes in the United States, Africa, Central America, West, and East Europe and has amassed several hundred dives as a PADI Divemaster.
0 notes
Text
sqlmap: Sucking Your Whole Database Through a Tiny Little Straw

Before getting into cybersecurity, I was a software developer for many years. Although I had heard about security vulnerabilities introduced to software via poor coding practices, I, like many of my colleagues, did not take security all that seriously. Hacking seemed like an arcane art, only mastered by those willing to spend years pouring over dusty tomes of x86 assembly language manuals and protocol RFCs. It did not occur to us that many of the vulnerabilities could be exploited by anyone with basic web development coding skills and the willingness to spend a few hours on research.
One of these mysterious incantations was the dreaded “SQL Injection” attack. What exactly could one do with a SQL Injection attack, anyway? No one was quite sure, but since our software was going into a secure military installation, we were pretty sure that the perimeter defenses would prevent anyone from harming it.
SQL Injection is a vulnerability that is introduced when software developers do not check data entered by users for validity and suitability to purpose. A malicious user can enter unexpected special characters to modify the structure of a SQL query. This can happen when the developer pastes together pieces of a query with “unsanitized” user input. The unsanitized input contains special characters that modify the structure of the query before it is passed to the query parser.
For example, consider a query in a PHP snippet that tests whether a user entering credentials at a login page is a valid user in the database:
$username = $_GET[‘username’];
$password = $_GET[‘password’];
$sql = “select USER_ID from USERS where USERNAME=’$username’ and PASSWORD=’$password’;”;
In this example, the variables username and password are retrieved from the HTTP POST that was submitted by the user. The strings are taken as-is and inserted, via string interpolation, into the query string. Since no validation is done on the input, the user can enter characters that will modify the structure of the query. For example, if the user enters ‘ or 1=1; # for the username, and nothing for the password, the variable sql will now equal:
$sql = “select USER_ID from USERS where USERNAME=’’ or 1=1; #’ and PASSWORD=’$password’;”
In the MySQL database engine, the “#” sign is a comment, so everything that comes after it is ignored in the query. There are no users with a blank username, but the condition “1=1” is always true, so the query will always succeed, returning all user IDs in the database. The subsequent code will likely only check that at least one record was returned, and it will likely grab just the first ID, which in most cases, will be that of the administrative user.
Doing SQL injection manually requires a fair bit of knowledge of how SQL works. On top of that, there are many different SQL engines, each with slight variations in syntax, such as PostgreSQL, MySQL, Microsoft SQL Server, Oracle, IBM DB2, and others. SQL Injection “cheat sheets” can help pentesters figure out the required syntax for testing a web application, but SQL Injection is still a very time-consuming attack to carry out.
Enter sqlmap. sqlmap is a program that automates tests for SQL Injection. Not only does it work with many different SQL engines, when used against vulnerable applications, it can:
Determine the schema of the database: database, table, and column names
Dump data from tables
Potentially upload or download files to the database server machine
Perform out-of-band tests
Dump usernames, password hashes, privileges, and roles
Pass hashes off to a password cracker for a dictionary attack
Perform “Blind” and “Boolean-based” SQL injection attacks, when the web application does not return error messages (this is probably sqlmap’s best time-saving feature. Performing these attacks by hand is almost completely untenable)
Potentially even launch a remote shell on the database server
Let’s perform a demo attack against the Mutillidae intentionally-vulnerable web application as it is hosted on the OWASP Broken Web Application virtual machine. We will launch an attack against Mutillidae’s login page.

Multillidae Login Page
sqlmap has many command line parameters, but we are going to set up the attack the easy way. The first thing we must do is to set FireFox’s proxy to run through Burp Community Edition running on localhost on port 8080. Then, we are going to enter a bogus login and password, such as admin / canary. We capture the request in Burp before it goes to the server, as shown below.

Capturing the HTTP POST Request for the Mutillidae Login (Bottom Pane)
Copying the POST request from the bottom pane, we save the request to a text file. In this case, the file is called mutillidae-req.txt, as shown below.

Saving the POST request
We can then run sqlmap using the text file by passing it with the “-r” command line parameter. We also pass “-p username” to give it the name of the parameter we would like to attack.
sqlmap -r mutillidae-req.txt -p username
The first command will do some enumeration of the database to tell us that the database engine is MySQL 5.0 or above.

sqlmap Running

Database Identified as MySQL
Once we have the database engine, we can run sqlmap again, telling it what the engine is, so it does not have to guess again. Also, we will ask sqlmap to get a list of databases on the server by using the following command:
sqlmap -r mutillidae-req.txt -p username --dbms mysql --dbs

Enumerating the Databases on the Database Server
Looking at the results, we notice that there is a database called wordpress that we would like to attack. The WordPress blogging platform can be abused to allow an attacker to install malicious PHP code, as long as the attacker has the administrative credentials. Running sqlmap again, we ask it to enumerate the tables in the wordpress database using the following command:
sqlmap -r mutillide-req.txt -p username --dbms mysql -D wordpress --tables
Below, we can see the results of the WordPress database’s table enumeration.

WordPress Database Table Enumeration
The most interesting table appears to be the wp_users table. We will ask sqlmap to dump the contents of the table with the following command:
sqlmap -r mutillidae-req.txt -p username --dbms mysql -D wordpress -T wp_users --dump

sqlmap Dumps the wp_user Table
sqlmap runs, and as a bonus, it asks us if we want to save credentials that we have found, and if we would like to attempt to crack any password hashes with a dictionary attack. Why YES, please DO! :D

sqlmap Asks if We’d Like to Crack Passwords
When we take the defaults, sqlmap runs a dictionary attack with its default dictionary of about 1.4 million passwords. We could also have chosen our own dictionary. In short order, sqlmap recovers passwords for two WordPress users: admin (daniel1984) and user (zealot777).

sqlmap Cracks the WordPress Passwords
Once we have the admin password, we login to the WordPress admin page using the credentials admin / daniel1984.

Logging in to the WordPress Admin Page

Logged in to the WordPress Admin Page
Once logged in as admin, we can modify the searchform.php page for the default theme, as shown in the screenshots below.

Editing the searchform.php File in the WordPress Default Theme
We replace the searchform.php code with that of the excellent b374k Web Shell.

searchform.php Page Code Replaced by Malicious b374k Web Shell Code
Once we have replaced the searchform.php code with the web shell code, we can simply browse to the searchform.php file directly with the following URL:
http://192.168.115.128/wordpress/wp-content/themes/default/searchform.php
The b374k web shell page is displayed, and we login with the password provided when we created the b374k PHP file.

Logging in to the b374k Web Shell
Once logged in, we are presented with the File Explorer page. We can browse to any page that the web server has permissions to read, and we can inspect its contents.

b374K Web Shell File Explorer
Here, we view the /etc/passwd file.

Using B374k to View the /etc/passwd File
We can do many other things with b374k, such as create a remote shell from the victim web server back to our attacking computer, as shown in the following screenshot:

Using b374k to Create a Remote Shell
As you can see, sqlmap is an incredibly useful tool to demonstrate to web developers and project managers alike that SQL Injection is indeed a serious vulnerability, one that deserves their full attention. SQL Injection can lead to complete system compromise. I am often told after a demo of sqlmap that it is “the scariest thing you have shown us yet”.
Learn more about sqlmap and other hacking tools in one of our Penetration Testing Courses.

Doc Sewell in Dandong, China, across the Yalu River from Shinuiju, North Korea
Author Bio
Daniel "Doc" Sewell is CTO and Trainer for Alpine Security. He currently holds many security-related certifications, including EC-Council Certified Security Analyst (ECSA), Licensed Penetration Tester (Master), Offensive Security Certified Professional (OSCP), Certified Information Systems Security Professional (CISSP) and Certified Secure Software Lifecycle Professional (CSSLP). Doc has many years of experience in software development, working on web interfaces, database applications, thick-client GUIs, battlefield simulation software, automated aircraft scheduling systems, embedded systems, and multi-threaded CPU and GPU applications. Doc's cybersecurity experience includes penetration testing a fighter jet embedded system, penetration testing medical lab devices, creating phishing emails and fake web sites for social engineering engagements, and teaching security courses to world-renowned organizations such as Lockheed Martin and the Hong Kong Police Department. Doc's hobbies and interests include home networking, operating systems, computer gaming, reading, movie watching, and traveling.
0 notes
Text
CIS Control 1: The Beginning of Basic Cybersecurity

The CIS Critical Controls were developed as a framework to not only ensure the successful realization of basic cybersecurity hygiene, but to lead to the planning and implementation of a robust security protocol. To build any cybersecurity protection schemata, it is necessary to know the extent of what it is you are protecting. This is the stated purpose of Control 1.
CIS Control 1 Overview: Inventory of Authorized and Unauthorized Devices
Critical Control 1 states: “Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access” (CISv.7). This control is not so much intended to prevent unauthorized access, although a complete inventory with attendant policy enforcement will do just that. Instead, it is devised so an organization may be certain of what devices are on the network, so they may be effectively defended. Then these devices will not be the unknown gap in the defensive perimeter that allows a devastating attack to execute on an unsuspecting network. Compiling a detailed asset inventory may seem like an intimidating task for an organization of any size, especially if this is a first-time endeavor. However, Control 1 is segmented into eight subcontrols designed to give form to the mission at hand.

CIS Control 1 Subcontrols 1.1 - 1.5 (Click to Enlarge)
CIS Control 1 Subcontrols
Subcontrols 1.1 and 1.2 recommend the use of both active and passive automated tools to identify device assets so they may be updated as needed and added to the hardware asset inventory. Anything with an IP address must be counted. This includes printers, copy machines, and even automated vending machines if they connect to the network. This asset inventory is also not limited to what is always attached to the network. Virtual Private Networks (VPNs) and mobile devices must also be inventoried, and these types of connections typically come and go on a network. Whether physical or virtual, if it has an IP address and ever connects to the network, it should be included as an asset. There are many such tools at varying price points, so that an organization will typically be able to devise a method that both works within their current framework and is financially feasible as well.
Subcontrol 1.3 advises Dynamic Host Configuration Protocol (DHCP) to be used to assign IP addresses. This automates IP allocation and is no small part of an IP address management system that aids in updating the hardware asset inventory and helps keep it updated. Subcontrols 1.4 and 1.5 focus on the maintenance of a detailed hardware asset inventory, whether or not the device is connected and whether or not the device is authorized to be connected. An inventory should at least indicate if an asset is portable, the name of the device, and the IP number. Including MAC addresses and serial numbers is a good practice to start with and maintain and can also be used to prove ownership for insurance purposes. Whatever information an organization deems necessary to keep in the asset inventory, it must be noted that this procedure is dynamic and ongoing for the lifecycle of any device. Records must also be kept of devices as they are deprecated and removed from the network or recommissioned and returned to the network. This is a priority on par with keeping updated blueprints and maintenance information for an organization’s physical and logical topology.

CIS Control 1 Subcontrols 1.6 - 1.8 (Click to Enlarge)
Subcontrol 1.6 suggests steps to take in dealing with unauthorized devices. When an organization obtains the actual number of unauthorized devices currently connected to their network, they may also discover the need to update current policies and procedures for IoT (Internet of Things) devices. Such policies and procedures may take the form of employee education of various types, as well as clearly delineated employee agreements as to what is, and is not allowed on the network. ATP (Advanced Persistent Threats) and other hackers wait on the internet for such unauthorized devices to gain an entry point into a network, or to use as a pivot point if the network is already compromised. It is unfortunate but true that attack avenues are always evolving, and one of the most commonly used avenues of malware delivery is via email spear-phishing campaigns aimed at the unwary employee, or through the connection of an unauthorized and unprotected device such as a smart phone or laptop.
Once this inventory is complete, subcontrols 1.7 and 1.8 mention steps to take towards ensuring company control of which devices are authorized to connect to the network. Port-level controls are a necessity, along with proper switch configurations, and both should be tied to the device asset inventory. This should help ensure only authorized devices may connect to the network.
Certainly this is a task that requires time, attention to detail, and commitment. It is not as exciting as other defensive processes, but proper implementation will lead to the best execution of the other 19 Controls, as well as add to the overall improvement of an organization’s defense posture by increasing efficiency and response time and reducing the network attack surface.
Conclusion and Next Steps
The CIS Critical Controls are not rigid, but may be implemented in the ways that best suit an organization’s needs and acceptable risk. Neither are the CIS Critical Controls weighted equally. Critical Control 1 is as important and essential to the support of any cybersecurity posture as a foundation is to the support of a house. A variety of studies show that CIS Control implementation is proven to prevent around 90% of network attacks. That renders the return on investment undeniable, and the importance cannot be overstated to management and board members.
Alpine Security remains committed to fostering cybersecurity awareness globally and locally while providing our specialized services to organizations and individuals alike. Pursuant to that commitment, Alpine Security offers a free consultation on our Enterprise Security Audit (ESA) Service.
The ESA is based on the Top 20 Critical Controls published by the Center for Internet Security. The ESA is intended to provide a comprehensive picture of where an organization currently falls in Critical Control Implementation, while also delineating a roadmap for full implementation. With the increase in variety and methods of attack on organizations of all sizes and types, defensive uncertainty is a luxury no security-conscious entity can afford.
0 notes
Text
Institutional Safeguards and the Human Element

Phishing emails from a CEO to an Executive Assistant with urgent tasks (scams) are on the rise
Does your organization welcome questions from employees? Would an employee feel comfortable questioning their supervisor about a task? How often do you push a job down the chain and expect it to “just get done?” The urgency of business demands that employees be able to carry out tasks without question. Unfortunately, that same urgency can lead to the exact conditions that cybercriminals exploit daily to the tune of billions of dollars. These exploits and a lack of focus on institutional safeguards to prevent them mostly go unnoticed within organizations until they become the target of a cyber-attack.
When discussing the method of how cybercriminals operate, it is often easy to take the “that could never happen to me” mentality. We’ve all heard the story of someone’s uncle who was catfished out of his life savings by someone from another country whom he never met, but is the love of his life. While the need for human connection may not be every individual’s weak point, everyone has at least one. In the business environment, humans are invariably the weak link in the security chain. Cybercriminals are particularly adept at manipulating the human element to extort money, intellectual property, and resources.
Here we will explore a case study involving a recent incident response that Alpine Security performed. In this incident, the company in question was targeted using email spoofing and phishing attacks resulting in losses of over $20k. This particular scam is noteworthy because it highlights a technique that is on the rise in recent months and illustrates how cybercriminals often use human and institutional weaknesses to fulfill their goals.

Initial Phishing Email to Elicit a Response
In the first phase of this attack, the criminal used a Gmail account designed to look like it was coming from the supervisor of the targeted employee, e.g., [email protected]. Seeing the name in the email address, the employee did not suspect that the email did not originate from their actual boss. The email explained that the supervisor wanted to give away some eBay gift cards to a vendor but was tied up and would like the employee to go and pick them up quickly. The employee responded and followed instructions to purchase $2,000 in eBay gift cards. She was then instructed to scratch off the back of the cards and send images of the codes to the email account. As luck would have it, she sent the codes via text rather than email, enabling her company to catch the scam before the codes were leaked, but it was a very close call.

2nd Phishing Email. Attacker sent this email after they received a response to the first email.
At first glance, it is easy to assume that we, in the same position, would have noticed one of the several red flags that this story illustrates. However, understanding the physiology of this kind of attack allows us to fully grasp how easy it is to fall victim to this type of scam. In this case, the criminal had two factors to their advantage; the first of which is the appeal to authority. Many employees are not going to question their boss when asked to perform a task as long as the job seems somewhat reasonable. If this is a task the employee has performed before, they may not think twice about doing it at all. If you work in a marketing or sales department picking up some gift cards might not be an out of the ordinary request. The appeal to authority can be just enough to make the employee second guess their suspicion and take an action they otherwise may not have. Furthermore, company cultures often do not promote open communication and freedom to question. Therefore, the employee may not feel empowered to raise concerns if they suspect something is amiss. Couple that with the second advantage the criminal is exploiting - urgency, and you have a recipe for social engineering. The “supervisor” is in a hurry and needs their assistant to perform a task quickly. If the employee has doubts, this may be the nudge they need to forget those doubts, get the job done, and “just be a team player.”
Employers should not underestimate physiological factors that play into these types of scams. It is human nature to want to be helpful and do your job well. It is often an institutional weakness to expect employees to carry out tasks without question or to put too little safeguards in place to prevent the compromise of one employee from costing the company money. It is natural to want to blame the employee for being careless, but the truth is that her actions were precisely what her boss would have expected had he been the one who sent the request.
If the attack had stopped here, it would have been merely a lesson learned for the company to be more careful. Unfortunately, it didn’t.
In phase two of the attack, the criminal sent an executive in the same company an email that appeared to come from another person within the company. The executive clicked a link in the email which prompted them to input their Office 365 username and password. Thinking this was merely a standard password prompt the employee complied and completed their work.
Unbeknownst to them, the login page they had input their credentials to was fake (spoofed), allowing the hacker to capture their credentials. The attacker quietly logged into the account and remotely set up a rule to automatically mark any emails from the finance department as read and send them to a hidden folder. They then sent an email to the finance department asking why an invoice to a company had not been paid. Over the next several days they were able to pose as the company executive and trick the finance department into fraudulently processing over $20K in fake invoices.
Both of these cases have human error as a common element, but stronger institutional safeguards are the only real tool to defeat human error. What would happen if we put a straightforward safeguard in place in either of these cases? What if a phone call and passphrase, or digitally signed email were required to initiate a wire transfer? What if the employees had training on how to detect spoofed emails?
In a third case, a client of Alpine Security received the same email requesting that they purchase iTunes gift cards. This was particularly interesting because the employee had recently bought gift cards for a similar giveaway. However, in this case, the company had a safeguard in place that a transaction like this needed to be approved verbally by the employee's supervisor. When she contacted them, they quickly detected the email was a hoax and were able to move on with no loss of money and little lost time.
How well would your organization handle an event like this? In the fast-paced world of cybercrime, no company is too small or too big to be a target. Stories like this happen every day. For the unprepared, they can bankrupt an organization or cause severe operational impacts. For a prepared company, they are a blip on the radar and something to talk about after you hit your next team milestone.
Does your institution have the training and safeguards in place to weather a cyber attack? Alpine Security has the tools to help. We offer a full range of private training for organizations to assist in cybercrime prevention as well as penetration testing, vulnerability assessment, and social engineering campaigns. Want to see how ready your company is for a cyber attack? Do not wait for the bad guys to test you. Let us help!
Author Bio

Isaac (on the left) hiking in Vietnam
Isaac Wright is a Cybersecurity Analyst and Trainer with Alpine Security. A veteran of the US Air Force, Isaac has more than 15 years’ experience in electronics maintenance and security. He holds degrees in Electronics Systems and Education and Training Management as well as a master instructor certification. Isaac has a long history of maintaining, hacking, modding, and using electronics systems from networks and computers to radios and consumer electronics. Isaac has leveraged his expertise to advise CIOs in large multi-site organizations on vulnerability management and risk mitigation.
When not teaching or analyzing network traffic, Isaac loves to play board games with family, fish, camp, and experience everything the world has to offer. An avid traveler, Isaac has been to more than 15 countries and especially enjoys Asia.
0 notes
Text
Comprehensive Guide to IoMT Cybersecurity – Risks, Safeguards, and What We Protect

The Internet of Medical Things, also known as the IoMT, is one of the most revolutionary developments in healthcare today. It empowers physicians to monitor patients remotely by providing the patient with network-enabled devices. These devices can track a wide variety of processes, from medication compliance to blood glucose level.
IoMT has become an extremely profitable industry. Let's look at the statistics:
87 percent of healthcare companies are using or preparing to use IoT technologies
63 percent of IoT technologies in use today are used for patient monitoring
71 percent of researchers believe that IoMT technologies are developing faster than the clinical world is ready to use them
By 2020, as many as 30 billion IoMT devices will be in use worldwide. By 2022, the market for IoMT will hit $158 billion.
The time is come to get very serious about IoMT cybersecurity.
Why IoMT Cybersecurity Is Worth the Trouble
IoMT devices offer benefits in every value metric of health care - patient outcomes, patient satisfaction, scientific advancement, and financial viability.
Lower Cost of Care
With the percentage of elderly persons rapidly increasing worldwide, experts are anticipating a potentially overwhelming rise in health care costs. The IoMT can make it possible for doctors to monitor patients remotely and send automatic recommendations when data exceeds the normal range. With this resource, doctors can lower costs by scheduling fewer in-person visits.
Additionally, because IoMT devices report data automatically, they reduce the need for nurses and support staff to verify data. This makes for more efficient use of staffing resources and focuses more attention on patient care.
Better Outcomes
Today, IoMT is most helpful in ensuring patient compliance with doctors' instructions. An enabled device communicates data regarding outcome-related behaviors such as medication adherence or exercise habits. The same devices can track whether a patient's condition improves or declines, thus providing key information that physicians can use to adjust care recommendations.
Customized Treatment
The pharmaceutical and medical device industries are already using IoMT to innovate around patient-centered treatment. Patients with Parkinson's disease, for example, now have access to wearable sensors that monitor and optimize medication use to improve patients' quality of life.
Additionally, there are numerous possibilities to add IoMT technology to pre-existing devices. For example, for patients with diabetes who use insulin pens, the IoMT could gather blood sugar data or record self-treatment schedules. The resulting data could help doctors better refine patients' treatment plans.
Access to Research
IoMT devices allow researchers to gather vast amounts of data conveniently, thus allowing them to more easily recruit and monitor study participants. Optimizing this process benefits not only the researcher, who can spend more time with participants and evaluating results, but also the many patients who can benefit from experimental treatments.
Innovations in IoMT Technology
IoMT is going places - down a patient's esophagus, to the grocery store, and even in a diabetic's eye, all thanks to technology's ability to get smaller, faster, and smarter.

Wearable medical device examples. Image source: https://www.researchgate.net/figure/Three-types-of-wearable-sensor-nodes-powered-by-thermoelectric-energy-harvesters-The_fig1_279634036
Wearable Medical Devices
As sensors become more advanced, device manufacturers have found ways to integrate them into wearable fabrics. This has led to advancements such as:
“smart” wound dressing that automates the delivery of painkillers, antibiotics, and tissue regenerating medicines
clothing and bedding that can alert caregivers to the needs of bedridden patients
bluetooth-enabled gloves that help stroke patients recover function faster
EEG-enhanced earbuds and headbands that improve pain management
All of these advancements help patients to get better care and take control of their health outcomes.
Ingestible Sensors
In order to increase the number of patients who take their medication according to doctor's orders – a number calculated by the World Health Organization at just 50 percent – Proteus Digital Health has developed ingestible sensors that track when a patient has taken his or her prescribed pill. This information travels to a smartphone app so that patients and their doctors can monitor adherence.

Glucose Tracking Contact Lens. Image source: https://www.engadget.com/2014/01/17/google-health-smart-contact-lenses-diabetes/
Glucose Monitoring
The Eversense XL system, distributed by Roche, uses an implanted sensor and rechargeable transmitter to send information about blood glucose levels to patients' smartphones. Patients receive vibration alerts when glucose levels drop or rise to unhealthy levels, as well as phone notifications when levels appear to be approaching those levels. Users can also track their daily habits to understand what affects their blood sugar.
Glucose-Tracking Contact Lenses
Yes, you read that right. Google and Novartis have teamed up to create a network-enabled contact lens that measures the blood sugar in patients' tears. The patient can view his or her data through a smartphone app and adjust insulin delivery based on results.

Ingestible sensor - camera. Image source: https://www.marsdd.com/news-and-insights/ingestibles-smart-pills-revolutionize-healthcare/
Swallowable Cameras
Doctors can now view the interior of a patient's digestive system without uncomfortable endoscopy procedures. It happens thanks to PillCam™, a swallowable camera that provides internal views of the small bowel. As the camera travels through the patient's system, advanced visualization technologies enable the physician to track speed of movement through the bowel and view images of potential abnormalities.
IoMT Out in the World
Not all IoMT devices are found in hospitals and laboratories. Many, like the consumer health wearables that have pervaded the consumer market, allow patients and their doctors to track health information on a day-to-day basis.
Fitness Trackers
Fitness trackers, like the well-known FitBit, are convenient wearable devices that track the body systems associated with exercise. They use:
bioimpedance sensors to track heart rate, respiration rate, and blood flow
thermometers to track increases in skin temperature
skin response sensors to detect sweat
optical heart rate monitor to measure cardiac exertion
accelerometers to count steps
These devices include software that can this information into health advice that the patient can use, but that's as far as it goes. They don't send data to doctors or recommend medications, but they do collect and store user information.
If not properly encrypted, that information could fall into the hands of hackers who might sell or alter it. There is even the possibility that a hacker could attempt to ransom a patient's own health data back to him or her.

Smartwatch Apps
Many smartwatches now have health tracking systems that monitor the wearer's health data. The recently-released Apple Watch Series 4, for example, tracks the wearer's cardiac rhythm and notifies him or her if it detects any irregular heartbeats.
The watch's Health app, meanwhile, tracks your stress levels, physical activity, sleep habits, and nutrition. These trackers can connect to a number of other third-party apps, which increases the number of companies that have access to your data.
Remote Patient Monitoring
Remote patient monitoring, also known as RPM, is one of the highest-profile trends in the health care industry.The current shift toward value-based care is making a distinct space for RPM technologies, which have the potential to reduce health care costs while improving patient outcomes and the overall patient experience.

Steps to Hack a Pacemaker
The Downside – IoMT Cybersecurity Concerns
Medical information is very valuable to hackers – up to 10 times more valuable than a credit card number. But it isn't just data that cybersecurity experts fear may be at risk.
In 2012, the Showtime television series Homeland aired an episode in which a character hacked into the software that controlled the pacemaker of the US vice president. The hacker then used that access to take control of the pacemaker's programming and caused a fatal heart attack. Shortly thereafter, then-vice president Dick Cheney's medical team disabled the wireless feature on his pacemaker, fearing that the television program would inspire a terrorist to take similar action.
Pacemakers and cybersecurity soon dropped from the news, but they came back again just four years later.
The Pacemaker Recall
In August of 2017, the Food and Drug Administration publicized a recall of 465,000 radiofrequency-enabled implantable pacemakers after a review identified security vulnerabilities. The FDA found that a hacker could use equipment at distributed on the commercial market to gain access to the device. With this access, a hacker could change the device's programming and harm the patient by depleting the battery or order dangerous pacing.
Fortunately, the FDA recall and development of firmware update occurred before any malicious access could occur.

Hacking Owlet infant heart rate monitors
Infant Health at Risk
In 2016 in the UK, the media reported a security vulnerability in the Owlet infant heart monitor sensor. Cybersecurity researchers found that while data sent between parent smartphones and base servers was secure, the networking between the sensor and the base server had no encryption whatsoever and could be accessed without so much as a login.
That means that anyone within range could monitor the infant's data, interfere with alert systems, or otherwise interfere with monitoring. The media deemed the situation to be the year's worst IoT security risk.

Hacking insulin pumps. Image source: https://www.extremetech.com/extreme/92054-black-hat-hacker-details-wireless-attack-on-insulin-pumps
Insulin Delivery Made Vulnerable
All of those IoMT enabled glucose monitors? Those are vulnerable to hackers too.
In 2011, a security researcher who is also a diabetic conducted an independent investigation. He found that a hacker could intercept the signals from a glucose monitor and change the readout, which would likely cause the wearer to adjust the dosage. If the attacker repeated the process, it could prove fatal. More frighteningly, this could happen from up to half a mile's distance.
Hackable Medication Pumps
Research has also identified vulnerabilities in a particular brand of infusion pump, a type of technology that delivers medication into patients' bloodstreams. In 2014, an independent professional reported that he had written a program that could instruct pumps to deliver lethal doses of medicine. The researcher found these vulnerabilities in at least five pump models.
Whole Systems at Risk
IoMT devices also put the hospital at risk of what is known as a backdoor attack. In one well-publicized example, hackers used malware to infect blood gas analyzers, which are important for the monitoring of critical care and surgical patients. The infected devices allowed attackers to infiltrate hospital networks and extract confidential data, which was then sent to an undisclosed European location.
A simulation of the attack revealed that the blood gas analyzers were routinely sending unencrypted data. That meant that the hackers could make any changes that they wished within the hospital system - to patient data, to treatment and diagnostic requests, and even to key administrative information.
Identifying Key Vulnerabilities
The IoMT would be a vulnerable situation even with adequate safeguards in place, simply because it sends and receives extremely personal information. Unfortunately, most of today's systems are not set up to protect such private data.
Outdated Software
Some working medical devices, such as CT scanners and even pacemakers, are upwards of 20 years old. These devices are capable of connecting to hospital systems but feature software systems that have not been conscientiously updated. Such systems are not set up to defend against today's advanced threats, which can disable an entire hospital network through a single device.
Departments Working in Isolation
In order for medical devices to be truly secure, all stakeholders must participate in screening for and responding to threats. This can be a difficult task in a complex healthcare organization where the primary focus is typically the immediate health of the patient.
The clinicians who use these devices often have so many pressing patient care tasks that they can easily overlook cybersecurity updates Meanwhile, facility IT staff and device manufacturers become involved with their own team's tasks.
This isolated way of working does not stand up to the complex and interlocking demands of medical device cybersecurity. In order to defend systems and devices from intruders, stakeholders must come together to create a unified security strategy.
Unclear Regulations and Poor Compliance
Manufacturers and healthcare delivery organizations (HDOs) have traditionally lacked clear mandates regarding the security of medical devices. A 2017 survey revealed that just 44 percent of HDOs and 51 percent of device manufacturers followed FDA guidelines to make devices more secure, despite the fact that approximately 33 percent of both groups were aware of potential harm to patients if a security breach did occur.
Improving Security and Protecting Patients
In one of the first major steps toward improved monitoring of cybersecurity, the FDA recognized the UL 2900 standard for medical device cybersecurity in August of 2017. Officially published as UL 2900-1, the standard offers a series of checks designed to identify vulnerabilities.
By recognizing the standard, the FDA enables manufacturers to indicate UL 2900-1 compliance as a response to cybersecurity concerns.
Regulatory Updates
In late 2018, the FDA published draft guidelines that bring medical device cybersecurity requirements up to date with today's risk set. Changes include:
A two-tier risk assessment system that prioritizes devices with the ability to connect with other products, a network, or the Web
Mandated documentation specific to a device's or system's risk tier
A Cybersecurity Bill of Materials (CBOM) that lists software and hardware with potential vulnerability to hackers
Greater alignment with the National Institute of Standards Technology's globally acknowledged Cybersecurity Framework
The FDA hopes that aligning with the Framework will improve UL 2009-1 compliance.
Recommendations, Not Mandates
The released documentation is geared toward premarket submissions and “contains nonbinding recommendations.” It is yet to be seen whether these recommendations are compelling enough to increase the percentage of manufacturers and HDOs that are actively trying to prevent attacks, a percentage most recently measured at 17 percent and 15 percent respectively.
Recommendations for HDOs
In 2018, the FDA collaborated with government research contractor MITRE Corp. to develop a cybersecurity guide for medical devices. The guide provides recommendations for healthcare providers and other involved organizations to prevent and respond to cybersecurity incidents involving medical devices. It features such recommendations as:
Creating a threat detection standard for all of an enterprise's devices and networks
Investment in firewalls and other prevention technologies
Inventorying of an enterprise's full range of medical devices, with attention to those with connectivity capabilities
The latter plays a particularly important role in uncovering security vulnerabilities. Only by identifying areas of potential risk can a provider screen for and correct vulnerabilities.
Next Steps for Attack Prevention
Technology never stays still and neither do hackers. The new developments in protecting patient data and patients themselves will not be the end of healthcare cybersecurity, nor will they guard against every possible way of hacking IoMT devices.
It is vitally important for all HDO's to develop and implement medical device security and IoMT security strategies. These strategies need to include not only a screening and threat mitigation standard for current devices but also a plan for maintaining security on a continuing basis.
Simplify Clinician Processes
Clinicians, both doctors and nurses, have their hands full with patient care. Any cybersecurity tasks, such as authentication checks, must be minimal on their part and automated as much as possible. Software updating and other processes must not disrupt workflow.
Threat Mitigation Training
The concept of keeping the clinician involved but uninterrupted also applies to threat intervention strategies. All personnel involved with a device or network must know what to do if a data compromise occurs.
Network Segmentation
Many security experts are now advocating for increased segmentation of enterprise systems. By segmenting their networks, organizations can more effectively implement security checks and isolate any threats before they pose a widespread risk.
Encryption of Patient Information
Because IoMT devices expose more patient information to enterprise networks, it is important for electronic health records (EHRs) to be as secure as possible. Technology such as homomorphic encryption, which secures data even as it is being used, can keep patient information safe from unwanted access. Protection can even be applied to personally identifiable information (PII), which is particularly valuable to cybercriminals.
Investing in Prevention
An ounce of prevention is still worth a pound of cure, both in patient care and in IoMT cybersecurity. As much as possible, security analytics and software updating should be automatic. The most critical and complex tasks can be passed on to a third-party provider with expertise in medical device security and the hacking of IoMT devices.
The FDA has placed the burden of IoMT cybersecurity on the people who develop and use them. This adds a set of high-urgency tasks for companies that are already tasked with the safety and well-being of patients. It is unsurprising that experts urge companies to outsource high-level tasks to a company with the expertise to handle them.
Alpine Security provides penetration testing services with a focus on IoMT devices. Through extensive experience in ethical hacking and identification of cybersecurity risk, we can relieve HDOs and manufacturers of the necessary burden to review and test all enabled devices, freeing those organizations to focus on patient outcomes.
0 notes
Text
Alpine Security Demonstrates Commitment to Medical Device Security by Sponsoring the Archimedes Medical Device Security Conference

O’Fallon, IL, January 2, 2019 - Alpine Security is proud to announce its support for the 2019 Archimedes Medical Device Security 101 Conference. As one of the conference's top sponsors, Alpine Security hopes to boost awareness of the cybersecurity vulnerabilities currently present within the medical community — and the many opportunities for improving healthcare cybersecurity.
Hosted by the University of Michigan’s Archimedes Center for Medical Device Security, this year's conference will take place in Orlando on January 21st and 22nd. A variety of key industry players are expected to attend, including product engineering directors, clinical facilities engineers, IT security managers, and more. This year's speakers include Norton Healthcare's AJ Aspinwall, Royal Philips Healthcare's Jonathan Bagnall, and Edward Brennan from the Health Information Sharing and Analysis Center (H-ISAC). Support from Alpine Security and other sponsors has been instrumental in allowing these speakers and a variety of other panelists to share their expertise.
The team at Alpine Security is well aware of the threats that hacked medical devices pose, both in the medical community and in a variety of other industries and settings. Patients, in particular, are at risk — each United States hospital bed currently possesses between 10 and 15 devices, many of which are connected to the facility's network. Just one malfunction can prove deadly, especially for high-risk patients for whom every second is of grave importance.
As Alpine Security CEO, Christian Espinosa, points out, hospitals are uniquely vulnerable because they are open to the public.
"Because of the nature of hospitals and their openness...it's easy for an attacker to walk into a hospital and perform nefarious activities. Nobody is going to question them." - Christian Espinosa, Alpine Security CEO
Espinosa warns that hackers can easily find exposed ethernet connections or even hack into the facility's wireless network while hanging out in the hospital cafeteria.
Unfortunately, medical device security remains shockingly minimal at most healthcare facilities. This is where Alpine Security comes into play.
In addition to supporting the Archimedes Medical Device Security 101 Conference, Alpine Security does its part to improve healthcare security by providing risk assessment and penetration testing services tailored for medical devices and healthcare environments. Using Alpine Security's arsenal of penetration testing services, Healthcare Delivery Organizations (HDOs) and medical device manufacturers can more effectively address the risks brought about by modern medical device connectivity.
About Alpine Security
Alpine Security appreciates that every person and organization face an increasing risk of cyber attacks. They aim to use their resources to do something about it. Alpine Security offers a variety of cybersecurity services, including risk assessments, penetration testing, training, audits, and incident response. The company's team is committed to always remaining a step ahead of today's tech-savvy hackers.
About Archimedes Center for Medical Device Security
The Archimedes Center for Medical Device Security was established to help manufacturers and industry experts navigate the operational hazards of cybersecurity implementation and prepare them for future challenges of FDA requirements. Archimedes is an independent, pioneering center focused on the education and advancement of medical device security where key industry players come together for learning in a safe place.
0 notes
Text
CIS Controls: A Cybersecurity Blueprint to Prevent Cyber Attacks

Data breaches arguably constitute the gravest risk modern businesses face. According to an alarming report from the insurance company Hiscox, 70 percent of organizations are inadequately prepared for cyberattacks. This is particularly concerning in light of the multi-million, even billion dollar damages that can result from breaches. Already, far too many businesses have suffered devastating attacks; 45 percent of Hiscox's poll respondents admitted to suffering at least one cyberattack in the past year, with many suffering two or more attacks.
At the small to midsize business level, cyberattacks aren't merely annoying — they can spell certain doom for those already struggling to get by. Hence the need for robust security protocol. That's exactly what the Center for Internet Security provides with its Top 20 list of Critical Security Controls. While these controls have been in the making for well over a decade, they've recently gained greater prominence at the federal and state level — and among private entities. Below, we offer an in-depth overview of this critical security tool, as well as suggestions for implementation:
What Are the CIS Top 20 Critical Security Controls?
The Center for Internet Security maintains detailed guidelines outlining prioritized actions known as critical security controls (CSCs). The goal is to proactively and effectively address security threats, thereby minimizing the potential for future data breaches. While any organization can benefit from implementing these controls, they are particularly valuable for those that currently lack robust security protocol. The CSC provide an accessible means of implementing security features while paving the path to a fully-fleshed compliance framework.
A Brief History of the CIS Top 20 CSC

Before diving in to explore specific controls, it helps to gain a broader understanding of how they came to be. They were initially developed in response to a 2008 request from the Office of the Secretary of Defense, in which assistance was sought from the National Security Agency. At the time, the NSA best understood the nature of cyber attacks — and how to combat them. Then, the White House maintained the following cybersecurity mantra: "Offense must inform defense."
By the time the aforementioned request was made of the NSA, the agency had already compiled and refined a list of effective security controls dating back to the early 2000s. These controls were originally prompted by military requests. While the initial list was limited to official use, the NSA eventually agreed to share its compiled cybersecurity information in hopes of helping other government agencies improve their security protocol.
Upon validation by the U.S. State Department, the CIS Top 20 was found to align closely with thousands of documented attacks suffered at the federal level. In an effort to address significant security weaknesses, the State Department made integration of the CIS standards a clear priority. The effort was an undeniable success; the State Department achieved an impressive 88 percent reduction in risk across tens of thousands of systems. As a result, the CIS standards quickly became the blueprint of choice not only for other federal organizations, but also in the private sector.
Today, the CIS Top 20 controls are maintained and updated by a vast team of volunteers, including experts from every segment of the cyber ecosystem. Expert volunteers include auditors, threat analysts, policy-makers, users, and more. They come from a wide array of sectors, including everything from transportation to defense. Their feedback ensures that the controls remain not only effective for protecting against a range of security threats, but also accessible, scalable, and easy to implement for a broad spectrum of businesses and organizations.
Defining the Basic Controls (Top 6)

Basic CIS Controls (click to enlarge)
The first six controls outlined by the CIS are often referred to as the 'basic controls.' While all of the outlined controls in the Top 20 are valuable, the basic CIS controls would ideally be implemented by all organizations seeking to ready themselves for future cyber attacks. Basic controls include the following:
#1 Inventory of Authorized and Unauthorized Hardware
It is imperative that organizations track all network devices — without a detailed inventory, it is virtually impossible to provide adequate protection. Successful application of the CIS first control is the foundation on which all other CIS controls rely. Putting this control into practice means identifying all relevant devices and maintaining a current inventory. This can be a huge undertaking; experts at CIS recommend using active scanning tools and other automated procedures.
#2 Inventory of Authorized and Unauthorized Software
This control references the need for active management of all network software to ensure that only authorized software is installed — and to quickly detect and deal with any unauthorized software that finds its way into managed networks. Cybercriminals regard organizations with vulnerable software as easy targets. Organizations that identify all existing software and develop approved whitelists improve visibility and may even see considerable savings as they discard unnecessary programs.
#3 Continuous Vulnerability Management
From software updates and patches to threat bulletins, ample opportunities exist for attackers to take advantage of new vulnerabilities — even among systems initially designed to be secure. As new vulnerabilities are reported, would-be attackers race to exploit these gaps. Without continuous scanning, organizations risk falling behind — a huge threat given the common knowledge that time is of the essence in the event of an attack.
#4 Controlled Use of Administrative Privileges
Attackers commonly rely on administrative privileges to carry out harmful actions within targeted enterprises. While most employees are aware of such efforts, even notoriously vigilant individuals can fall victim to scams. Common examples include opening files from malicious sites, downloading problematic attachments, or even merely visiting websites capable of exploiting users. One of the easiest to implement — and yet most effective — controls available, this step involves separating administrative accounts from personal internet activity. Additionally, systems should be configured for log entries and alerts.
#5 Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
Accessibility often plays a key role in modern software adoption — sometimes to the detriment of security. Default accounts and open services can leave organizations and their key players vulnerable. Hence, the need for this basic control, which is especially important in an increasingly BYOD (bring your own device) oriented workplace. Rigorous configuration management is essential if organizations are to keep attackers at bay.
#6 Maintenance, Monitoring, and Analysis of Audit Logs
While the cliche 'an ounce of prevention is worth a pound of cure' certainly applies to modern cybersecurity efforts, it's foolish to assume that breaches will never occur. Unfortunately, even organizations with exceptional security protocol sometimes fall victim to cyberattacks. When the worst-case scenario arrives, it's important to be prepared — not only in the interest of responding quickly and effectively, but also because a detailed understanding of one attack could potentially lead to new protocol to prevent future issues.

Foundational and Organizational CIS Controls (click to enlarge)
Foundational and Organizational Controls
The other control categories include foundational controls and organizational controls. These areas can help enterprises shore up their security after they have mastered the basic controls. Without mastery of the basics, however, these additional controls are not likely to serve as a viable security solution. Controls referred to as foundational or organizational include:
Foundational CIS Controls
7. Email and Web Browser Protections
8. Malware Defenses
9. Limitation and Control of Network Ports, Protocols, and Services
10. Data Recovery Capabilities
11. Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches
12. Boundary Defenses
13. Data Protection
14. Controlled Access Based on the Need to Know
15. Wireless Access Control
16. Account Monitoring and Control
Organizational CIS Controls
17. Implement a Security Awareness and Training Program
18. Application Security Software
19. Incident Response and Management
20. Penetration Tests and Red Team Exercises
While there is clear value in all of the controls included on the Top 20 list, not all controls will prove accessible or applicable in all situations. Nearly all organizations, however, can benefit from implementing the controls identified as 'basic' by the CIS.
Comparing CIS to Other Frameworks
The CIS Top 20 is just one of several security frameworks relied upon by government and private enterprises alike. Other top framework providers include National Institute of Standards and Technology (NIST) and Payment Card Industry (PCI) Security Standards Council. While these hold clear value, they can be difficult for small businesses to adopt. The CIS Top 20 serves as an essential stepping stone for those who may feel intimidated by other frameworks or otherwise incapable of implementing them. CIS controls can also be used alongside other frameworks; some companies even use CIS standards to prioritize alternate frameworks.
Mandating Controls
Presently, the CIS Top 20 serves as a standard of care for the state of California, where the Attorney General has partnered with CIS to help local businesses follow the protocol outlined in the state's Data Breach Report.

While CIS became a key California framework in early 2016, recent changes in the state's privacy laws have further underscored the importance of adopting CIS controls. Signed into law in 2018 and expected to go into effect in 2020, the California Consumer Privacy Act now supplements the state's data breach legislation, granting consumers the right to sue if breaches of data occur and businesses do not provide appropriate protection via 'reasonable' procedures. While the state fails to adequately define 'reasonable' in the context of the Consumer Privacy Act, it is clear based on previous efforts with the CIS that implementation of, at minimum, the basic six CSCs is expected.
While California has clearly set the bar high in terms of mandated internet security protocol, other state and local government entities are beginning to follow suit with similar legislation. Michigan, in particular, has made great strides in terms of encouraging implementation of prominent security frameworks. The 2018 Performance Audit Report from the Michigan Office of the Auditor General referenced NIST Special Publication 800-53 as the bare minimum regarding security controls.
In Ohio, the CIS controls are highlighted as one of a few available frameworks with which business cybersecurity practices would ideally conform. While the Ohio Attorney General maintains that the state's recent adoption of the Data Protection Act does not serve as a minimum cybersecurity standard, it does create a valuable incentive for the local business community to amp up security efforts.
In some states, CIS controls are not yet mandated — but they are used heavily by government entities. Success at this level may eventually lead to broader mandates for government organizations and private businesses alike. As CIS experts point out, top users of the CSCs include the states of Arizona, Colorado, and Idaho. In addition to making its mark at the state level, the CIS controls are increasingly utilized in major metropolitan areas, including Oklahoma City, San Diego, and Portland, among others.
Success Stories
The Center for Internet Security offers numerous case studies that demonstrate the ability of various controls to protect against a broad range of security threats. For example, CIS highlights a top banking institution as relying on these controls for gap analysis. The banking institution's Chief Information Security Officer explains, "If we are not quite meeting the intent of a particular CIS Control, we can identify areas to focus on and improve." This valuable baseline has allowed the bank to maintain its status as one of the nation's most secure financial institutions.
While the value of the CIS controls is clear in banking and finance, many retailers have yet to adopt appropriate security measures to protect their customers and suppliers. One outdoor retailer, however, is leading the way by engaging in CIS analysis not just once, but twice every year. While the retailer also uses such familiar frameworks as NIST and PCI, a top security analyst for the company explains that the CIS controls provide, by far, the biggest bang for the buck by assisting in prioritization of other frameworks. "We see the real value is in the CIS controls because they are more user-friendly and are a practical, prioritized framework."
In another case study, CIS reveals that Corden Pharma has adopted the CSCs in hopes of meeting diverse security requirements for the company's range of customers. Manager of IT and Business Systems John Nord explains, "[Corden Pharma] needed a more standardized security program for our company to be able to provide to our customers. The CIS controls fit that need." Nord adds that, while initially daunting, implementation for the CSCs is not nearly as arduous as NIST framework adoption can be.
What Lies Ahead for the CIS Controls?
The CIS Top 20 are constantly evolving as new threats arise — and as new technologies become available for keeping these threats at bay. In early 2018, CIS released Version 7, which, as CIS executive Tony Sager explains, "sets the stage for future improvements in measurement, implementation, and alignment with other security frameworks."
Although pleased thus far with the rollout of Version 7, companies are already looking ahead to Version 8. With new editions of the CSC released approximately once every three years, Version 8 can most likely be expected in 2021 or 2022. Until then, experts anticipate that states and municipalities will continue to follow California's lead in prioritizing these security measures and working closely with CIS to ensure the adoption of robust cybersecurity controls.
Next Steps for Adopting CIS Controls
Regardless of how the CIS controls evolve in the future, it is important to get a handle on security protocol today. The widely trusted security controls from the CIS can provide a valuable blueprint. Not sure where to start? Alpine Security's Enterprise Security Audit (ESA) service provides valuable insight into your organization's current security protocol. Closely aligned with the CIS Top 20, this comprehensive assessment offers a holistic approach involving effective controls for cyber defense. Reach out today to discover how Alpine Security can assist your organization in adopting and abiding by the Center for Internet Security's Top 20 Controls.
0 notes
Text
The Greatness of Being Uncomfortable

There is no denying that most people in this world want to avoid feeling uncomfortable as much as possible. The problem with this mindset is that those who fear discomfort and uncertainty are always going to be stuck in the same place. The best way to fail to succeed is to stay in one place for relative comfort.
Fear of failure ruins our lives
If you think about it, you will come to the conclusion that our biggest fear is not failure itself. What we truly fear is that other people will see us fail. This is a very common problem and it has no logic behind it. When you fail, you feel like others are going to ridicule you or laugh at you, but no one ever laughs at failure, they may feel bad for you, but they fear failure more than you do, they are completely frozen by fear and they never even try anything new because they would rather stay in their comfort zone.
Just imagine how ridiculous it would be for you to give up your goals and dreams because you are afraid of what others will say if you fail. The simple thought of this makes you cringe and it should be more than enough to motivate you to take action.
Good things will never happen to you
People are usually expecting god things to happen to them in life. They say “I’m a good person, I deserve good things, I know things will change” but the problem is that they are just standing on the road of life, while others are standing there with them waiting for good things to come to them. This is a huge problem for many people because they feel entitled to happiness and to success just because they are nice, or because they are honest and decent. Those are not qualities and virtues that give you a free pass to success. The sad truth is that no one has ever achieved success in life by thinking this way.
Imagine that you are standing on the road and you see a pot of gold a few miles away, but there are traps and pits all the way through. You are going to be waiting forever if you expect someone else to carry that gold to your location. Anyone that reaches that gold is going to keep it for themselves. They would be willing to share if you also walked towards that gold and took your chances with those traps.
The exact same thing happens with everything we want in life. If we don’t start heading in the direction of what we want, there is always going to be someone else willing to take the risk. The point here is that anything you want in like is going to require that you move forward and step out of your comfort zone.
Adding value to your journey
The greatest thing a person can do in life is to add value in their journey to the goals they set for themselves. If your goals include being a competitive and highly valuable asset to any modern business, you will find that cybersecurity training is going to be essential for that purpose. We have classes with official certifications in cybersecurity that will add thousands of dollars of value to your paychecks.
Step out of your comfort zone and invest in your future. Take action and move forward on the road to your dreams. Find out how to enroll in our awesome courses to add massive value to your journey to success!
0 notes
Text
Cyber Extortion: Ransomware vs Extortionware

Cyber crime is not just the plotline of bad TV movies. It's a $600 billion global business that accounts for 0.8% of the world's GDP. Anyone on the internet - and there are 3.2 billion of us - is a potential victim.
While phishing scams and identity theft are old news, the more serious threats to organizations are ransomware and extortionware. In fact at Europol's 2018 Internet Organized Crime Threat Assessment, the European crime prevention agency stated, "In a few short years, ransomware has become a staple attack tool for cybercriminals, rapidly accommodating aspects common to other successful malware such as affiliate programs and as-a-service business models."
Ransomware's sister threats are a different form of cyber crime called cyber blackmail or cyber extortion. Blackmail doesn't necessarily involve sophisticated technology. But ransomware and cyber extortion typically do. While these two types of malware share common themes, they also differ in key respects. What's the difference between ransomware and extortionware? And what can you do to prevent your company from becoming a victim of cyber crime?
What is ransomware?
Ransomware is a type of malware that locks a computer system down until the victim pays the extortioner for the key code to unlock the device. It's an obvious form of cyber crime. While some internet criminals try to fly below the surface, stealing data without you realizing it, ransomware is overt. The hacker is telling you in plain language, "We've encrypted your system. The key is in our lockbox. If you want your data or computer to work again, you'll pay us." Usually, the victim has to pay in Bitcoin or through another hard-to-trace method.
It's the most common form of cybercrime and perhaps the most effective. Who wouldn't pay a few hundred dollars to a criminal instead of a few thousand to a break-fix IT service, which might not be able to unlock the system anyway? The trouble is, there's nothing to stop the criminal from coming back again ... and again. Ransomware can cost a lot more than the initial payment; it also costs time, productivity, and reputation.
Examples of ransomware
The first ransomware appeared in 1989. Hackers mailed floppy disks (remember those?) to unsuspecting victims who inadvertently installed the malware on their computers. To get the key, the victim had to mail either $189 or $378 to Panama. Today's cyber criminals operate a similar racket but with greater technical prowess. The WannaCry ransomware attack in 2017, which was linked to the North Korean government, infected about 200,000 computers in 150 countries.

Bad Rabbit Example
Bad Rabbit was a ransomware that affected European and Russian users. Unlike WannaCry, which spread randomly, Bad Rabbit targeted its victims, which included the Odessa airport and Kiev's mass transit system.
A relatively new and irritating form of ransomware is called "police-themed demands." In this, the criminals claim to be the police who are shutting down your computer due to its use in a terrorist act or a child pornography ring. By paying a few hundred dollars in fines, the "police" claim, you can unlock your computer. Of course, the whole thing is bogus, and you're the victim of ransomware.
What is cyber extortion?
Extortion is simply demanding a good, service, or payment to prevent violence or destruction of property. Some cyber criminals get ahead of the competition by demanding money before they hurt you. Much like the mobsters of yore who wanted payment for "security services," these cyber extortionists basically tell you to pay them or they will lock up your system. According to Insureon, "Cyber extortionists may threaten to harm you, your reputation, or your property if you do not comply with their demands. Cyber extortion can take many forms." For instance, a hacker may send malicious traffic using a bot, overwhelm the site with more requests than it can handle, or simply shut it down.
What is cyber blackmail?
Blackmailers employ the psychology of fear and shame to motivate victims. In these cases, the cyber criminal will claim that he's been inside your computer, snapped screenshots of embarrassing photos or searches, and recorded sketchy video using your camera. He will threaten to send the screenshots and pics to everyone in your address book or post them on social media unless you pay up. It's basically cyber blackmail.
"Cyber-blackmail is the act of threatening to share information about a person to the public, their friends or family, unless a demand is met or money is paid," according to the BBC. It is a particularly insidious kind of crime. In fact, some hackers are even targeting children.
Cyber blackmail doesn't only affect individuals, but it also harms companies. Hackers claim they have stolen sensitive data from a company's storage and threaten to expose it unless paid off. Many times, the hacker has no evidence at all and is simply bluffing. The really dangerous part is that emails from hackers often reveal they have secured your password, and while that may be all they have, it's often enough to do some serious damage.

Cyber Extortion Example (click to enlarge)
Am I a victim of ransomware, extortionware, or cyber blackmail?
Because these are forthright kinds of crime, you'll likely know if you're a victim. The hackers will tell you when they demand the ransom, threaten you for money, or want blackmail payoff. One handy way to assess the credibility of an extortion scheme or blackmail threat is at HaveIBeenPwned. This site lets you see what breaches your email address has been associated with, so you can determine if the password that is supposedly compromised and used for the cyber extortion is simply from a previous breach or if the hacker really has broken through your security system.
In no case should you pay off a cybercriminal even if you think they have something on you. A qualified managed services provider or IT professional can help protect you against ransomware and can reverse most of it easily. Cyber blackmailers almost never have the goods on you they say they have, and extortionists are probably no match for your IT managed service provider or cybersecurity squad. Report cybercriminals to the police. Your company doesn't need to be a victim.
How penetration testing and training can prevent cyber crime
At Alpine Security, our penetration testing services and training can help prevent both ransomware and extortionware. We can also help you know what to do if a hacker uses ransomware to lock down your system. Penetration testing can help identify gaps in systems and networks, and our user awareness training, including our phishing services, can identify gaps in user training. To learn more about protecting your organization from ransomware and cyber extortion, contact us today.
0 notes
Text
The Ultimate Guide to Cyber Threat Maps

A cyber threat map, also known as a cyber attack map, is a real-time map of the computer security attacks that are going on at any given time. One of the most famous was released by the company Norse and went so viral, even among non-hackers, that it got its own story in Newsweek in 2015.
The map itself looks like a global game of laser tag. Beams of light, represented by different colors, shoot across a darkened screen showing where an attack comes from and where it is going. When it first caught the public eye, captivated audiences watched hackers wage cyber-war across hundreds and thousands of miles.
How Does A Cyber Threat Map Work?
If cyber attacks are sneaky mice – or, more appropriately, giant rats – then cyber attack maps work like the mousetrap.
Norse, for example, maintained a global threat intelligence network of more than 8 million sensors and “honeypots” in 47 countries across the world. These tools impersonated thousands of applications and devices that are common targets of hackers.
When a hacker hits a Norse sensor, the hacker believed that it had breached a system. Instead, Norse collected information about the hacker's toolkit, including his or her IP address. This information then manifested as data on the cyber attack map.
This model has continued past the demise of Norse to power live maps like Cyberthreat, ThreatCloud, and Fortinet. Some companies claim that these are real-time cyber attacks, but most are more like selections of recent attacks.
What Are They Good For?
First of all, anyone can look at a cyber threat map and understand something about current attacks. For laypeople, it might just be an understanding of how prevalent these attacks are.
For pros, a cyber threat map can provide data that can lead to the discovery of a potential new attack. Even though these maps don't really show cyber attacks in real-time, they give you information, and a cybersecurity pro can never have too much of that.
The Best of the Best in Cyber Threat Maps
Not all cyber threat maps are created equal. Some are great eye candy for pen test companies, but others do offer good functionality. A few even let you manipulate the map to focus on its most useful information.
#1 Cyberthreat by Kaspersky Lab
Kaspersky's cyber threat map may be the best in the business in terms of interactivity and visual appeal. It's also mobile optimized so you can show it to clients or colleagues from anywhere. And if you want particular data, the site offers you the option to find it.
Narrowing It Down
Kaspersky's Cyberthreat also offers useful statistics about current cyber attacks. Through its website, you can learn about:
Vulnerabilities identified
Most widespread threats
Botnet activity trends
Prevalence of infected mail and spam
You can find this data for a specific country or look at it on a worldwide level.
The Widget
Kaspersky Lab has figured out that cybersecurity professionals often use threat maps to visually represent their work to clients. To make it easier, they have created a Cyberthreat map widget, which you can embed in your website, as shown below, so that clients can see a representation of the latest threats.

Fortinet Threat Map (click to enlarge)
#2 Fortinet by Fortiguard
This one isn't quite as customizable as Cyberthreat, but it's informative enough to warrant runner-up honors. The main map color codes its attacks by severity to make it easier to focus on the most critical situations, coded in red. The details of these attacks scroll quickly along the bottom of the map, where the viewer can identify the threat type and location.
Fortiguard clients have a bit more freedom in terms of map design. By placing a tool known as the ThreatGate, users can monitor the threats approaching a particular location.

Check Point Threatcloud (click to enlarge)
The Best of the Rest
In addition to Fortinet and Cyberthreat, there are a few other cyber attack maps that repeatedly appear on “Best of” lists. They are:
#3 ThreatCloud by Check Point
#4 FireEye
#5 Trend Micro
#6 Deteque
#7 Arbor Networks
#8 Akamai
Each of these maps presents its data in a slightly different format and with a slightly different emphasis. Take a look, try them out, and find out which one will work best for you.
The Take-Away
If you find these maps intriguing, know that they're not enough to make you an expert. You'll need to learn more about cybersecurity and take some training, like the penetration testing courses available through Alpine Security. There are tests available for all levels of pen testers – check it out today.
0 notes