#cybersecurity risk management
Text
Intelligent Automated Risk Management (IARM): Enhancing Risk Identification and Decision-Making
Unlock the future of risk management with Intelligent Automation: smarter, faster, and more proactive. #RiskManagement #AI #MachineLearning #Automation #BigData #Fintech #Healthcare #CyberSecurity
Introduction
In an era where businesses face a myriad of risks—from financial uncertainties to cyber threats—traditional risk management approaches often struggle to keep up with the pace and complexity of emerging risks. Intelligent Automated Risk Management (IARM) offers a transformative approach by integrating cutting-edge technologies to enhance risk identification, assessment, and…
#Advanced Risk Modeling#AI in Risk Management#AI Risk Prediction#Anomaly Detection Technology#Automated Risk Management Solutions#Automation in Risk Assessment#big data analytics#Blockchain in Risk Management#Continuous Risk Monitoring#Cybersecurity Risk Management#Financial Risk Management#Intelligent Automated Risk Management#Machine Learning Risk Assessment#Operational Risk Management#Predictive Analytics for Risk#Real-Time Risk Monitoring#Risk Management Automation#Risk Management Best Practices#Risk Management Technologies#Risk Management Trends
5 notes
·
View notes
Text
Since I need to distract myself a bit let me talk about
~✨Risk Management ✨~
So, y'all have read the interview of the CEO or something like that of the company that owned the submarine, yeah? He said something like "at a certain point security is useless".
I work in security (ok, cybersecurity but) so I'd like to get on the occasion to explain to everyone what risk is and how it works.
PSA: I'm not defending the guy, i don't care. This is just me taking the ball to explain something. Idk what he meant, I didn't read the whole interview and this is not about the submarine incident.
So, let me define risk first as:
Likehood * Impact
Likehood is the probability that something could happen.
Impact is the damage you get if that thing happens.
Risk is generally classified according to tables similar to this one.
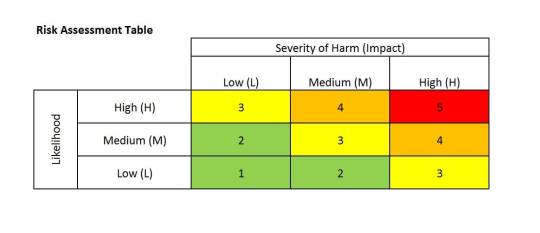
If you're doing a good job you are probably going to create one of this personalised for each "thing" you need to assess.
The thing is: when we assess a risk we need to consider a few things:
What's the worst case scenario?
Do we have a "back-up" plan if things go wrong (-> limits the impact)
What are the most important asset for this thing we want to assess? (Helps identify the impact)
What is the probability that a villain could access the assets? What kind of tools would they need?(likehood)
Is there something we can do about this?
And other things. I'm trying to keep it very generic.
Then we proceed. After we evaluated the risk(s) we could face, we have four choices:
Avoid the risk -> obvious right? We take the steps to eliminate the risk completely;
Mitigate the risk -> reducing the likehood or the impact by taking several measures
Transfer the risk -> you hire someone that takes the risk for you (insurance, anyone?)
Accept the risk.
I know this sounds counterintuitive, but think about it for a second.
You own a car. You did all the controls you could do and consider yourself a moderate and careful driver(mitigation), have a insurance (transference), leave the phone in the backseat (avoidance... kinda)but there is still a residual risk of having an incident, despite all the countermeasures you took.
You can decide to not drive at all, that would land the risk to 0, but you need to go to work, right?
Is reasonable at this point for you to... Not drive entirely? Some of you might say no, for various reasons: it's irrational, need to go to work, you can't use a bike because it's too far...
Companies do the same when evaluating risks. They might decide that, to them, action X doesn't represent a threat (small impact or extremely low likehood).
Consider also that in cybersecurity every layer of defense you create it's literally making someone's job more difficult. Sometimes it's worth it (consider the case of assets that handle personal data or credit card information), sometimes after you did all the assesment you find out that the level of sophistication an attack would require is such improbable, expensive, impractical that you don't take any measure to fix it.
(I recommend the Darknet Diaries "Jeremy from Marketing" episode - it's a really interesting example of what I'm talking about specifically)
Most of the time risks are being mitigated - avoiding a risk entirely is often impossible or would require too much resources. I have a post on "accessibility for the users and security" to write for my cybersecurity portfolio since last year but ok I guess.
Thanks for coming to my ted talk about something no one cares about but I found incredibly interesting.
34 notes
·
View notes
Text
Enhancing Security and Mitigating Risks: Unveiling the Power of Century Solutions Group

In an increasingly interconnected world, businesses face a myriad of security challenges and risks. From cyber threats and data breaches to physical vulnerabilities, organizations must adopt comprehensive strategies to safeguard their assets, customers, and reputation. This blog will explore the critical role played by Century Solutions Group in providing top-tier security and risk management services.
Read Blog: https://centurygroup.net/enhancing-security-and-mitigating-risks/
#Security and Risk Management#security breach ruin#cybersecurity as a service#cyberattack#cybersecurity#managed it services
3 notes
·
View notes
Text
Mastering IT Management: Strategies for Success in the Digital Age

#Information Technology Management#IT Strategy#PGDM Specialization#Emerging Technologies#Business Technology#Cybersecurity Management#Risk Management#Colleges for IT Management#Colleges in India#Data Analytics#Master’s in IT Management
1 note
·
View note
Text
White Paper: The Urgent Need for Migrating from Dynamics AX 2012 R3 to Dynamics 365 Finance and Supply Chain
Executive Summary
As of January 10, 2023, Microsoft officially ended extended support for Dynamics AX 2012 R3, a widely used ERP system. Despite this, many organizations around the world continue to rely on Dynamics AX 2012, exposing themselves to significant risks. This white paper explores the threats, vulnerabilities, and dangers associated with the continued use of an unsupported ERP system.…
#change management#compliance#cybersecurity risks#data migration#Dynamics 365 Finance#Dynamics 365 Supply Chain#Dynamics AX 2012 R3#end of support#ERP migration#ERP support#ERP upgrade#legacy system migration#Microsoft Dynamics#operational efficiency#Routeget Technologies#upgrade to Dynamics 365
0 notes
Text
Not For Just the Big Boys
The Importance of Cybersecurity for Small Businesses: Protecting Your Digital Assets
In today’s digital age, where technology plays a vital role in business operations, cybersecurity has become a critical concern for companies of all sizes. While large corporations often make headlines for cyber attacks, small businesses are not immune to the threats posed by cyber criminals. In fact, small…
0 notes
Text
Why Privileged Access Management is Crucial for Modern Cybersecurity Strategies?
Privileged Access Management (PAM) allows enterprises to control access to business systems for people with certain access privileges, such as domain or account administrators, network equipment account managers, help desk workers, HR, and so on. PAM can monitor access to prevent security risks with these high-end computers.
Whatever report you read, the main points of entry are phishing emails,…
#Compliance#Cyber Threats#cybersecurity#Endpoint Security#IT Security#Multi-factor Authentication#PAM#pam privileged access management#pam security#pam solution#Privileged Access Management#privileged access management tools#privileged identity management#risk mitigation
0 notes
Text
Learn essential strategies for securing and protecting your big data in this comprehensive blog post. It covers best practices for data encryption, access control, and threat detection to ensure your valuable information remains safe from breaches and cyber threats. Equip yourself with the knowledge to implement robust data protection measures effectively.
#Big Data Security#Data Protection#Cybersecurity#Data Encryption#Access Control#Threat Detection#IT Security#Data Management#Risk Mitigation#Data Privacy
0 notes
Text
Techniques for Strategic Growth in IT Management: Navigating the Future with a PGDM Specialization

#Information Technology Management#IT Strategy#PGDM Specialization#Emerging Technologies#Business Technology#Cybersecurity Management#Risk Management#Colleges for IT Management#Colleges in India#Data Analytics#Master’s in IT Management
1 note
·
View note
Text

GRC Strategies for Retail: Strengthening Compliance and Security
0 notes
Text
Advanced Persistent Threats: Understanding the Characteristics, Tactics, and Strategies for Prevention and Mitigation in Today's Cyber Landscape
A detailed read on Cyber security in today's digital landscape. Happy Sunday everyone!
Advanced Persistent Threats (APTs) are a type of cyber attack that is specifically targeted at organizations or individuals to steal sensitive information or disrupt operations. These attacks are carried out by highly skilled and organized hackers who use sophisticated techniques to gain access to networks and systems. In this paper, we will discuss APTs in detail, including their…

View On WordPress
#Advanced Persistent Threats (APTs)#Cyber attack mitigation#Cyber attack prevention#Cyber risk management#cyber threats#Cybersecurity#Data protection#Employee education#Endpoint protection#Incident response#Least privilege#Network segmentation#Security assessments#Security audits#Threat intelligence
2 notes
·
View notes
Text
When Cyber Attacks Are the Least of Our Worries: 5 Shocking Threats to Critical Infrastructure
Introduction paragraph explaining the significance of the list. Use key phrases related to the topic for SEO optimization.
Imagine a world where the things we rely on every day suddenly vanish. No power, no water, no internet—sounds like a bad sci-fi movie, right? But it’s more real than you might think. The importance of critical infrastructure can’t be overstated. These systems are the backbone…
#Critical Infrastructure#Cybersecurity#Emerging Threats#Infrastructure Protection#Infrastructure Vulnerabilities#National Security#Public Safety#Risk Management#Security Events#Technological Threats
0 notes
Text
Premier IT Risk Management Services In India | Tech Triad
Safeguard your enterprise with Tech Triad's advanced cybersecurity and IT risk management services. To know more information, visit the website.
0 notes
Text
Safeguarding Supply Chains: Guiding Cybersecurity Risks in Transportation and Logistics
Technology twists deeply with logistics operations, and cybersecurity has emerged as a critical concern for Immensity Logistics and the entire transportation and logistics industry. Here’s an exploration of the cybersecurity risks specific to supply chains in this sector, along with strategies to mitigate these risks effectively:
Understanding Cybersecurity Risks in Transportation and Logistics
Data Breaches and Theft: The vast amount of sensitive data handled in logistics operations, including shipment details, customer information, and financial records, makes logistics companies prime targets for data breaches.
Ransomware and Malware Attacks: Malicious software such as ransomware can infiltrate systems, encrypt critical data, and demand ransom for decryption, causing severe disruptions and financial losses.
Phishing and Social Engineering: Employees are often targeted through deceptive emails or messages to gain unauthorized access to systems or sensitive information, exploiting human vulnerabilities.
Supply Chain Disruptions: Attacks on logistics partners or subcontractors can disrupt the entire supply chain, leading to delays, operational downtime, and significant financial repercussions

Impact of Cybersecurity Incidents
Operational Disruption: Cyber incidents can halt transportation services, delay shipments, and disrupt supply chain operations, impacting customer satisfaction and business continuity.
Financial Losses: Remediation costs, regulatory fines, legal fees, and revenue loss due to interrupted processes can affect profitability and growth.
Reputational Damage: A cybersecurity breach can tarnish a logistics company’s reputation, eroding client trust and confidence in its ability to protect sensitive information and maintain operational integrity.
Mitigating Cybersecurity Risks: Strategies by Immensity Logistics
Risk Assessment and Management: Regularly assess vulnerabilities across systems, networks, and third-party partnerships to prioritize security investments and mitigation efforts.
Employee Awareness and Training: Educate employees on cybersecurity best practices, phishing awareness, and incident response protocols to strengthen the human firewall against cyber threats.
Secure Network Infrastructure: Implement robust cybersecurity measures such as firewalls, intrusion detection systems, encryption protocols, and access controls to safeguard data and prevent unauthorized access.
Patch and Update Management: Maintain up-to-date software and firmware to mitigate vulnerabilities and protect against known cyber threats targeting outdated systems.
Incident Response Planning: Develop and regularly test an incident response plan to ensure swift and effective response to cyber incidents, minimizing operational downtime and financial impact.
Partnership and Compliance: Collaborate with cybersecurity experts, industry associations, and regulatory bodies to stay abreast of evolving threats, adhere to industry standards, and maintain compliance with data protection regulations.
Conclusion
At Immensity Logistics, safeguarding supply chains against cybersecurity risks is not just a priority but a commitment to ensuring secure, efficient, and resilient logistics operations. By adopting proactive cybersecurity measures, leveraging technology responsibly, and fostering a culture of vigilance and preparedness, Immensity Logistics aims to mitigate risks effectively and uphold the dynamic landscape of transportation and logistics.
#Cybersecurity#immensity logistics#freight logistics#Update Management#Reputational Damage#Supply Chains#Risk Assessment
0 notes
Text
Cybersecurity and Risk Management
The virtual age has delivered sizeable blessings, however it has additionally uncovered agencies to a growing landscape of cyber threats. records breaches, malware assaults, and phishing scams can cripple operations, erode client believe, and inflict good sized monetary damage.
what is Cybersecurity and threat control?
Cybersecurity is the practice of defensive your structures, networks, and facts from unauthorized get admission to, use, disclosure, disruption, amendment, or destruction. danger management makes a speciality of identifying, assessing, and mitigating capability threats for your cybersecurity posture.
Cybersecurity and Risk Management
Why is it important?
Cyberattacks are getting an increasing number of sophisticated and common. A strong cybersecurity and risk control software is vital for any business, no matter size or enterprise. here's why:
Protects touchy facts: shield purchaser records, financial facts, and highbrow property from robbery or misuse.
Guarantees business continuity: reduce downtime and disruption as a result of cyberattacks.
Continues customer believe: reveal your dedication to data safety and construct more potent client relationships.
Reduces monetary losses: prevent the tremendous costs related to records breaches and cyberattacks.
Complies with guidelines: Meet enterprise standards and felony necessities for facts safety.
0 notes
Text
ManageEngine Announces Integration with Constella Intelligence for Proactive Supply Chain Risk Management
Spots and notifies leaked credentials in the dark web before attackers exploit them, preventing breaches
Provides the first point of defense against supply chain risks and helps perform advanced analytics on the threat to determine the extent of the attacker’s steps
Download and explore the 30-day, free-trial now: https://mnge.it/Ftc
Metro Manila — ManageEngine, a division of Zoho Corp. and a…

View On WordPress
0 notes