#penetration testing
Explore tagged Tumblr posts
Text
15 Best Free Resources for Malicious URLs and Phishing Links for Cybersecurity Testing
In today’s rapidly evolving cybersecurity landscape, having access to reliable sources of malicious URLs, phishing links, and malware samples is essential for security professionals, penetration testers, and IT administrators. Whether you’re validating your security controls, conducting security awareness training, or researching new threat vectors, accessing known malicious content in a…
#cyber threats#cybersecurity#ethical hacking#malicious URLs#malware analysis#malware samples#penetration testing#phishing detection#phishing links#security controls#security testing#security tools#security validation#threat intelligence#web security
2 notes
·
View notes
Text
youtube
A look into security.
2 notes
·
View notes
Text
finding usernames/passwords for testfire.net
background: testfire.net is a "fake" website designed for pentesters to play around with. it is NOT a real bank and no one's information is actually being stolen here. this was an assignment for a class.


first we start by logging into the admin account, username: admin and password: admin. although a general SQL injection works on this site. for the inject, password is irrelevant.
other injects that work (note that's not a quotation, that's two apostrophes):
' or ''='
' or '1' = '1
or any other statement that will always be true
on the left we see we can "Edit users"


our assignment was to find username and password pairs. you'd think you could cheekily change the passwords of existing accounts or add new accounts to fulfill this requirement, but none of these options on the admin page actually work.

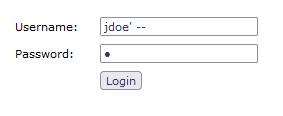
we can see the usernames of several users. since we know the username field is vulnerable to injects, we can now login to any of these without knowing the password.

this field is also vulnerable to injects. inject used:
' --
okay never mind post cancelled
i just checked the solution that my professor wanted and i shit you not its this:

these do technically work as username and password pairs. like, if you use them, you will sign in. in fact, i think you can just put anything other than a blank space for the password and it would count. but man. fuck this.
regardless, here are some actual pairs that i ended up finding. i cant quite remember how i found them, but i saw someone use "demo1234" as a password for both jdoe and jsmith, so i tested sspeed and its the same password. cant find the other ones though.
jdoe | demo1234
jsmith | demo1234
sspeed | demo1234
2 notes
·
View notes
Text



Emile Walker from Penetration Testing is demisexual!
2 notes
·
View notes
Text
Staying Relevant: Balancing Learning and Life as an Ethical Hacker
Have you experienced burnout while trying to develop your skills and you just don't have the time to do everything? Finding balance is the key to improving your skills in a healthy way. In this article, I explore healthy habits to grow without burning out
You’ve heard it before – cybersecurity is a field that evolves at a blindingly fast pace. The tools, techniques, and technologies threatening networks transform rapidly. As an ethical hacker, your skills can become obsolete within months if you aren’t continuously upgrading your knowledge. Point #4 on our hacker roadmap deals with knowing the latest and greatest when it comes to the state of…

View On WordPress
#burnout#certifications#conference#continuous learning#Cyber Security#cybersecurity education#cybersecurity skills#Ethical Hacking#hacker skills#infosec community#leadership#learning plan#maintaining balance#microlearning#Penetration Testing#pentesting methodologies#personal development#podcast#red team operations#security news#security policies#security tools#time management#trends#vulnerability assessments#work-life balance
3 notes
·
View notes
Text

woa. must be legit LOOK at that COVER
The Hacker Playbook 2 at thrift
#software testing#penetration testing#thrift books#playbook#hacker playbook#book covers#book cover#second hand#software#reference books
3 notes
·
View notes
Text
How effective is Red Teaming & Pen Testing?
In today’s digital landscape, ensuring cybersecurity is crucial for organizations of all sizes. One of the key approaches to identifying vulnerabilities in security systems is through Red Teaming and Penetration Testing (Pen Testing). But how effective are these strategies?
Evaluating the Effectiveness of Red Teaming
Through the simulation of real threats, red teaming evaluates an organization's defenses. Here’s how it proves effective:
Comprehensive Security Assessment: It offers an in-depth analysis of security measures and identifies weaknesses.
Realistic Scenarios: By mimicking actual threat actors, it provides a practical understanding of potential risks.
Team Improvement: The exercise fosters collaboration among security teams, enhancing their response strategies.
Assessing the Impact of Penetration Testing
Pen testing focuses on identifying vulnerabilities through controlled attacks. Its effectiveness can be summarized by:
Finding Weak Points: It draws attention to particular weaknesses that an attacker could take advantage of.
Prioritizing Threats: Helps organizations focus on critical areas needing protection.
Regulatory Compliance: Frequently necessary to adhere to rules and industry norms.
Both red teaming and pen testing play vital roles in strengthening an organization’s cybersecurity posture. By proactively identifying vulnerabilities, organizations can better defend against potential threats and ensure a safer digital environment.
0 notes
Text
Penetration testing isn't just about ethical hacking—it's a structured process that helps businesses discover and fix vulnerabilities before real attackers exploit them.
In cybersecurity, the penetration testing lifecycle is typically divided into five essential phases:
Planning & Reconnaissance
Scanning
Gaining Access
Maintaining Access
Analysis & Reporting
Each stage plays a vital role in identifying potential security gaps, especially for businesses in finance, healthcare, and technology sectors.
If you're managing sensitive data or infrastructure, understanding these phases helps you assess risk better and strengthen your defenses.
Dive deeper into the complete breakdown here: Read the Full Guide
1 note
·
View note
Text
What Is CREST Penetration Testing? Benefits & Importance

Five years from now, cybersecurity will face greater challenges and even higher risks. Currently, the global cybersecurity penetration testing market is worth $4.1 billion, and experts predict it will increase at a strong annual rate of 13.1% until 2033, due to more challenging cyber attacks, broader cloud use, and stronger data privacy rules. Commonly seen in Singapore but happening elsewhere in the Asia-Pacific region as well is a strong increase in the need for advanced testing like CREST penetration testing due to government support, increased digitalization, and the Smart Nation goal.
1 note
·
View note
Text
Comprehensive Guide on Network Reconnaissance using NmapAutomator
When conducting network reconnaissance or penetration testing, efficiency is key. NmapAutomator is a powerful tool that automates and streamlines the process of network scanning, allowing security professionals to focus on actual penetration testing rather than spending time on repetitive scanning tasks. This comprehensive guide on Network Reconnaissance explores what NmapAutomator is, how to set…
#cybersecurity tools#network reconnaissance#network scanning#network security#nmap#penetration testing#reconnaissance tools#security automation#vulnerability scanning
0 notes
Text
Why Cybersecurity Certifications Like ISO 27001 & SOC 2 Matter Today
Cybersecurity threats are growing—fast. Whether you're a startup or an enterprise, frameworks like ISO 27001 and SOC 2 can be the difference between peace of mind and panic.
At Cyber Guardians, we help businesses navigate: 🔐 What VAPT actually involves 💰 VAPT cost in India and what to expect ✅ How to get SOC 2 certification 📈 Getting ISO 27001 certified — minus the confusion
We’ve been there. Let us help you get compliant with confidence.
#VAPT companies in India#SOC 2 certification#ISO 27001 cost#cybersecurity#penetration testing#data compliance#infosec
0 notes
Text
Ethical Hacking Tools: What’s Legal and Free?
Curious about ethical hacking but worried you might trip over legal lines or blow your budget? You’re not alone. With cybersecurity threats rising every day, ethical hackers—also known as white-hat hackers—are becoming heroes in hoodies. But to do it right, you need the proper tools: ones that are legal, effective, and preferably free. Let’s dive into the best ethical hacking tools you can use…
#ethical hacking#free cybersecurity tools#legal hacking software#penetration testing#white-hat hacking
0 notes
Text
Penetration Testing Service in India
Penetration Testing, also known as pen-testing, is a proactive cybersecurity approach aimed at evaluating the security posture of digital systems, networks, and applications. Unlike traditional security measures that focus on prevention and detection, penetration testing adopts an offensive strategy, simulating real-world cyberattacks to identify vulnerabilities before malicious actors exploit them.
0 notes
Text
Protecting Yourself from Cyber Stalking Threats
With the rapid advancement of technology, it has completely changed the way we connect, share, and communicate in this digital age. But with this advancement comes the increase in cyber stalking, defined as the use of the internet or other electronic means to stalk or harass an individual, a serious issue that affects millions worldwide. It can lead to severe emotional, psychological, and even physical harm to the victims, making it crucial to raise awareness about the dangers and preventative measures.
This article provides an in-depth look into cyber stalking, highlighting its threats, legal implications, and preventive measures. Through understanding these dangers, individuals can better protect themselves from becoming victims of cyber stalking.

The Rising Threat of Cyber Stalking
Cyber stalking is a pervasive threat that often starts innocuously but can escalate rapidly, affecting individuals in various aspects of their lives. The growth of social media platforms, online communities, and messaging apps has increased the exposure of personal information, making individuals vulnerable to exploitation. Unlike traditional stalking, which occurs in physical spaces, cyber stalking can happen remotely, and it can affect people regardless of their location.
Cyber stalkers use a variety of methods to harass their victims, such as sending threatening messages, posting private information online, or engaging in defamation campaigns. The anonymity of the internet often emboldens stalkers, as they can hide behind fake profiles, and victims may not always know who is behind the attacks. This sense of anonymity and the widespread access to personal data make cyber stalking a growing concern for individuals, families, and businesses alike.
How Cyber Stalking Works
Cyber stalkers can engage in several practices to monitor, intimidate, or harm their victims. Among the most common practices of cyber stalking includes:
Social Media Harassment: A very common portal for cyber stalking is social media. The abuser may be creating a different profile to harass the victim through impersonation, or following excessively. They could also post any defamatory comments or even private information just to harm one's reputation and invade their personal space.
Email and Instant Messaging Threats: Stalkers can send harassing, threatening, or intimidating emails, messages, or even make phone calls. These threats may be aimed at instilling fear in the victim, and often, the messages contain explicit language or images designed to intimidate.
Identity Theft and Data Breaches: In some cases, cyber stalkers may use information that they stole through data breaches or other methods to impersonate their victims or continue manipulating their lives. For example, cyber stalkers might access private accounts, steal financial information, or engage in identity fraud.
With the proliferation of smart phones and other devices, stalking may be possible through spyware or GPS tracking apps to trace the victim's movements and activities. These spyware and tracking apps enable stalking to trace the real-time location, conversations, and other personal data.
Online Defamation: Cyber stalkers can publish false information or defamatory content about their victims online to tarnish their reputations. This can cause them emotional distress and potentially harm their social or professional life.
Impact of Cyber Stalking
The psychological and emotional impact of cyber stalking is indeed deep. Most victims of cyber stalking are likely to feel anxiety, fear, and helplessness. Such stalking can lead to depression, insomnia, and, in extreme cases, suicidal thoughts. The sense of violation from the inability to escape harassment at home makes victims feel unsafe in their own abode.
In addition to the emotional impact, there is the financial loss and reputational damage to one's profession. Such victims may face missed chances at employment, strained relationships, and extreme stress that comes with the continuous harassment. Cyber stalking has long-lasting effects that can even affect an individual's sense of trust in digital spaces.
Legal Framework and Cyber Stalking
There have been various legislations by several countries regarding cyber stalking and its related crimes. For instance, in the United States, some of the enactments are Violence Against Women Act (VAWA) and the Cyberstalking Law. While these enactments provide a victim with a legal recourse for his or her own protection, they are sometimes enforced and implemented irregularly. Further, the enforcement of the said enactments in all jurisdictions may not be explicit.
Legal action may be taken in cases where the personal information of a victim is being used for malicious purposes through privacy laws, harassment laws, and anti-cyberbullying regulations. Victims are advised to report such incidents of cyber stalking to the law enforcement agencies that can assist in gathering evidence and pursuing legal action against perpetrators.
It is worth noting that building a case against cyber stalkers often proves to be difficult because the anonymity of the Internet does not lend itself well to follow identification, and in some respects, the laws are not developed well enough to grapple with the overall issue of cyber stalking. For this reason, prevention is still the best medicine in dealing with cyber stalking.
Prevention of Cyber Stalking: Proactive Measures
The best way to handle cyber stalking is by avoiding it in the first place. Here are several ways in which one can keep oneself safe:
Online Privacy Settings: Many online services and social media platforms provide privacy settings through which one can control what other people view about oneself. Control of access to personal information and being aware of what one posts online minimizes the chances of falling prey to a cyber stalker.
Use Strong Passwords and Two-Factor Authentication: Securing online accounts with strong, unique passwords and enabling two-factor authentication (2FA) can prevent cyber stalkers from gaining unauthorized access to personal accounts.
Be Careful with Personal Information: Do not over-post personal details on the internet. This includes not sharing your full name, address, phone number, or any other sensitive information that may be used by a stalker.
Report Suspicious Activity: If you see unusual activity online, like unwanted messages, fake accounts, or threatening content, report it right away to the administrators of the platform and, if needed, to the law enforcement agencies.
Seek Legal Protection: If you feel threatened, you may want to pursue legal protection like a restraining order or cyber harassment lawsuit. Most states and countries have laws in place to protect victims of cyber stalking.
Take Control of Your Digital Footprint: Conduct regular audits of your online presence and remove outdated or unnecessary information. Monitor search engine results for your name to ensure your information is not being used maliciously.
Conclusion: Empowering Yourself to Stay Safe Online
Cyber stalking poses a significant danger to the future of online security in a significantly interconnected world. Understanding the characteristics of cyber stalking, the types of potential results, and techniques used by the stalkers makes it possible to take steps and protect oneself in advance. If it is upgrading privacy settings or using safe passwords, one always has the legal right to prosecute the stalkers and ensure security.
A cyber security course will be beneficial for those seeking further knowledge and better security practices in protecting themselves against the ever-growing threats of the digital world. Being well-informed and watchful, individuals can prevent cyber stalking and ensure their digital lives are free from malicious actors.
0 notes
Text
Coding and Scripting for Beginner Hackers
Learning to code and write scripts is a crucial skill for getting into ethical hacking and cybersecurity. Scripting allows you to automate repetitive tasks, develop your own custom tools, analyze data, and program everything from small hacking tools to machine learning models. Understanding and knowing how to code in different languages can be extremely useful when doing deep dives into malware…

View On WordPress
#Cyber Security#cybersecurity careers#Ethical Hacking#hacer certifications#hacking for beginners#hacking guide#hacking homelab#infosec#learn to code#learn to hack#Penetration Testing#Pentesting
4 notes
·
View notes