Wonderful website designing service at an affordable cost. Website designers are expert of everything right from dynamic website to corporate website.
Don't wanna be here? Send us removal request.
Text
Transmission Control Protocol (TCP) Socket Connection
What is Transmission Control Protocol (TCP)?
Our android development team was working on one mobile app project when TCP came into picture. Basically, Transmission Control Protocol generally recognizes as TCP is a standard that allows establishment and maintenance of within network communication. It functions on the Internet Protocol (IP) to exchange application programs through a shared network. TCP and IP work hand in hand to define the mechanism of how computers interact with each other via data pockets. Our android development team was working on one mobile app project when TCP came into picture.
IP and TCP together are the basic ruling elements of internet protocol suite yet the Internet Engineering Task Force (IETF) specifies TCP as Request for Comments (RFC) standards of documentation. TCP originated as an individual protocol but further, it complimented IP, therefore, they are together referred to as TCP/IP. In network communication, TCP offers a reliable, error-tested, quality delivery stream of octets via an IP network. Major internet entities like World Wide Web, File transfer; Remote Administration, etc are under function based on TCP itself.
For example: In a real organizational context, Transmission Control Protocol (TCP) is utilized for peer to peer communication. As in this case, in order to consider an example, Transmission Control Protocol (TCP) Socket Connection that works as the source of inter-organizational conversation and file share. It is also called an IP messenger. This TCP socket connection is a computer application that functions on a shared LAN or Wi-Fi network. The basic functionality of the TCP socket connection is that it performs secured and reliable data transfer from the company server to the client or multiple clients as well. Organization and management of conversations are handed to the server host, as every message from the client or employee arrives at the server as well. It is a very simple protocol that requires only time configuration and then it allows multi-directional data transmission without any hiccups in the process.
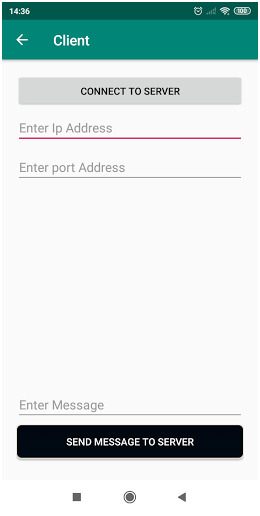
TCP socket connection offers the following features:
TCP socket connection allows sending text messages to the individual who is linked by the same shared network. It can be a shared LAN or Wi-Fi connection.
TCP socket connection allows broadcasting the messages from any user or the server, under the range of common IP.
It allows verification of the sent message and received status to the server destination.
What Does Transmission Control Protocol (TCP) Work On?
Transmission Control Protocol (TCP) is a network-oriented protocol that pronounces that it first establishes a network and then manages a communication via data packets sharing between the devices under the same hosted network. It basically begins the function by breaking the data into data packets so that the network is capable to transfer it. It manages the flow of data packets being shared as it keeps track of data packets sent to and data packets received from inside the network. It means if in case the data packet or message is sent from one device then the admin or server would get the notification along with the device address of the sender. As TCP has a function of transmitting error-free data, it also manages the flow of retransmission of missed or out dropped data packages. Being an Open System Interaction (OSI) communication protocol, TCP works on parts of the layers such as the transport layer and the session layer.
Process of Transmission Control Protocol (TCP) functioning:
There are basically steps in the Transmission Control Protocol (TCP) function, namely, segmentation, multiplexing, three-way handshake, data sequencing and acknowledgment, and flow control. These functions that TCP deploys can be discussed as follows:
1. Segmentation : Segmentation is the process to bifurcate the big stream of data into smaller segments or sections. This basically allows the server or the host to send or receive any bulk of information over the shared network. While working in the transmission layer the act of segmentation is performed in order to develop small-sized data packets that a shared network can transmit from one device to another. For example: If in case the bandwidth of the shared network is 2MBPS and the size of the data file is 100Mb then the segmentation is performed to divide the data file into 50 small-sized data packets. Once the data packets of reduced size are created then they can be transmitted through available bandwidth with quite an ease. This segmentation takes place at the sender’s end but when the data reaches the server’s end then the destination host reconstructs the data file by connecting those small data packets.
In terms of segmentation only, TCP is all time pitted against User Datagram Protocol (UDP) as they both work on the transmission layer. Yet TCP stands well tall here as TCP supports data segmentation but UDP does not. The standout feature of TCP is that it performs the segmentation process on its own before setting it for via-bandwidth transmission.
2. Connection Establishment Or Multiplexing : As mentioned earlier Transmission Control Protocol (TCP) is a connection-oriented protocol, as it requires sending data only through a well-established network connection. Therefore, connection establishment is the second step of TCP function. Once the network between server and sub-devices is established then the transmission begins. This is ensured that TCP would not transmit any data without establishing a strong network.
3. Three-way Handshake : The data transmission via TCP is required to be secured and authorized therefore, there is the provision of the third step of TCP functioning. The three-way handshake is the methods of authentication which allows the data to be synchronized and acknowledged. In this activity, at first, the source or server sends a synchronization (SYN) segment to the other end of the sub-device or receiver. If the terms are acknowledged by the user then it responds back with synchronization/acknowledgment (SYN/ACK) segment. This ensures that the source and destination both have received the terms and then finally the primary source will send the Acknowledged (ACK) segment so that the handshake is completed. This three-way handshake signifies that a reliable and authentic connection is well established.

Once the three-way handshake is processed, then both of the parties, source and destination can transmit data. This can be a two-way data transfer or unidirectional, it only depends on the requirements of the shared network conversation. Yet TCP only requires the authentication of header data, as the first step of authentication is already performed in segmentation.
4. Sequencing and acknowledgment : This is the next step of Transmission Control Protocol (TCP) functioning, it can be considered as an intermediate step but a whole process in itself. It involves 4 sub-processes as detailed below:
Identification of lost data packets and recognition of information
Detection and removal of duplicate data packets
Recognition and sequencing of the dropped or off orderly arrived data packets.
Control and management of the dataflow or overflow of the data packets.
Sequencing and acknowledgment are the strong reliability check process of TCP as it involves recognition of authentic data packets, dropping of duplicate data packets and sequencing of the data packets as well.
To offer reliability, TCP assigns the numeric system or sequence numbering to ease transmitted segments or data packets. This helps the destination host in rearranging the order of data packets and detect if all the sent data packets are received. Only on the based on sequence numbers, the data file is reconstructed at the destination host. Once the sequencing part is over then the acknowledgment part begins.
It also works on the numeric system only but the order of acknowledgment numbers is in the opposite direction to the sequencing numbers. These acknowledgment numbers are sent to the source-destination as verification of received data. After all the verification a final acknowledgment number is sent from the destination host to the server which is one numeric higher than the actual number of data packets. If any sequencing or acknowledgment number is missing then it is an indication that a data packet is only missing. Once the source and host interchange the sequence numbers then the process of data exchange can be used anytime or they can interchange themselves in functions.
5. Flow Control : Transmission Control Protocol (TCP) performs the flow control process through windowing. Basically, windowing is the process of flow control itself. It is required when one source uploads bulky data files and the data packets are overloaded in the transmission signal then the flow control technique though windowing comes into play. It secures the system from problems like buffering and malfunctioning. In this process, the receiver device updates the sender device about its window size during the three-way handshake only. This way the destination host gives a precision of data load to be transmitted by the sender. Window size is basically a number of data packets that can be stored and processed in the receiver’s system. As the sender computer has a precision of the receiver’s window size therefore the flow of data packets is controlled by the sender itself.
For example: If the window size of the destination host is 10 then the source will only transmit 10 data packets, once these data packets are received by the destination host then the sender will get the confirmation notification. Then only the source will release further 10 numbers of data packets to the destination host. This is how the flow control in TCP is performed to prevent the transmission from buffering.
To enhance the performance of TCP, there is another brownie step performed. This step is called packet dropping and sequencing. In this step, duplicate data packets are dropped from the transmission and then the order of data packets that arrived off the order is set.
What Is Transmission Control Protocol (TCP) Used For?
TCP is used for inter-organizational or internal shared server to client communication purposes. It is used for such organizational conversations because it is authentic as well as a reliable source of communication and data transmission. It is utilized for ensuring the security of the sensitive information shared between the organization and clients. Irrespective of the amount of information being transmitted, TCP maintains the integrity of the data over the shared network. TCP is used as a higher priority when the total amount of data is required to be transmitted without any leakage from the higher-level protocols.
TCP/IP is used in the application layer in three different functions, mentioned as follows:
Inter-organizational peer to peer communication of file transfers; TCP/IP is used as, File transfer Protocol Secure Shell (SSH), and Telnet.
For e-mail transmissions, Post Office Protocol (POP), Simple Mail Transfer Protocol (SMTP), Internet Message Access Protocol (IMAP), etc are used as TCP/IP integrated functions.
In the web, access HTTP is a form of TCP/IP.
TCP/IP Stack:
All of these applications of TCP are only available in the application layer of the TCP/IP stack. Where TCP/IP stack is the virtual destination or model that represents the organization and transmission of data that have taken place over a shared IP. It represents the layers of information, based on how the data is stored, organized, handled and transmitted. It is basically a series of protocols traced over the data transmission from the server to the destination host and vice versa.
Parting Words:
Transmission Control Protocol (TCP) is a standard set protocol that allows inter-organizational communication over the shared IP. It shall be concluded that TCP and IP both individually make statement importance in Internet Protocol Suit but once they go hand in hand as TCP/IP, the applications like TCP socket connection can be developed. TCP deploys five stages of data transmission process such as segmentation, multiplexing, three-way handshake, data sequencing and acknowledgment, and flow control which makes it stand as a reliable, authentic and professional communication standard in the industries. TCP socket connection is an important application because it only allows data transfer inside the organization, and it reduces the hazards of data leakage outside the shared IP.
#tcp/ip#tcp#transmission control protocol#internet protocol#internet#networking#communication protocol
0 notes
Text
Ways To Secure Your Magento Website From Getting Hacked
Check out our new article on securing Magento website.
Click here to check the article
We provide Web development related services.

0 notes
Text
Top Benefits of Using Salesforce CRM
Check out our new article on dev.to to find out the benefits of using Salesforce CRM in your business.
We are Salesforce development company based in US.

#salesforce#Salesforce Development#crm development services#crm development company#web developers#web developing company#web development
0 notes
Text
Things You Should Know before Using Magento E-commerce
If you are planning to run a new eCommerce website based on Magento platform, then there are few things one should consider & should be aware of before going for it. Check this article to know more.

#magento#magento development#magento developers#magento development services#Ecommerce#webstore#onlinestore#business
0 notes
Text
Magento Hosting Requirement via Hosting Calculator
Check out our article on Magento hosting calculator.
Click here to read - https://webdesignanddevelopment.site123.me/blog/magento-hosting-requirement-via-hosting-calculator
We , Best Websites Designer, strive to provide best magento development services.
0 notes
Photo

We are leading dating website development company based in Miami, US.
If you are looking to grab the business opportunity in online dating field, then you would like to have a look at our services.
#dating#online dating#web design#web developing company#web development#web developers#dating website development
0 notes
Link
If you are looking for business opportunities then you might want to have a look on this article on business opportunities in dating sites.
#dating#dating websites#dating sites#web design#web development#web developing company#web developers#online dating
0 notes
Link
Drupal development services by Best Websites Designer based in Miami, US
#drupal development services#drupal#drupal development#drupal developer#miami#drupal website development
0 notes
Link
Upcoming trends in CRM Salesforce development
0 notes
Link
Check out what are the benefits that make Magento ecommerce one of the best option
0 notes
Link
Latest trends we can expect in 2020 in magento development.
0 notes
Link
Salesforce CRM development services by Best Websites Designer
0 notes
Link
Magento Development Services By Best Websites Designer.
0 notes
Link
Check out why magento based ecommerce is an better option for your business growth. Plus, find out the comparision of Magento with its competitors.
0 notes
Link
Sales CRM Development
0 notes
Link
We are WordPress Developer Miami of Best Website Designer. We provide one of the best WordPress Development Services in Miami. It includes other web development services.
#wordpress#wordpressdeveloper#wordpressdevelopermiami#wordpressdevelopment#wordpressdevelopmentservice
0 notes
Link
Check out why wordpress is important for your business.
Find out one of the best wordpress developer miami.
0 notes