Don't wanna be here? Send us removal request.
Text
Strengthening Endpoint Security Through Cloud Computing Security Measures

In today's interconnected world, where digital technology touches nearly every aspect of our lives, protecting our data and devices from cyber threats is more critical than ever. Cloud computing and work-related device use have increased the requirement for comprehensive security. This has brought cloud computing security and endpoint security to the forefront of cybersecurity strategies. Additionally, as we navigate our digital lives, maintaining good cyber hygiene and occasionally practising digital detoxification are essential for security and well-being. This post will discuss these crucial principles and offer practical advice for digital security.
Understanding Cloud Computing Security
Cloud computing has transformed data storage and access for organisations and consumers. However, cloud computing security becomes paramount as more data moves to the cloud. Cloud computing security involves implementing measures to protect cloud-based systems, data, and applications from cyber threats. These measures include encryption, identity and access management (IAM), and regular security audits.
Cloud computing security is complex during data transit and storage. Encryption is essential: it prevents data from being read without the correct key. Moreover, identity and access management controls who can access specific data and applications, reducing the risk of unauthorised access. Regular security audits also play a vital role in identifying vulnerabilities and ensuring current security measures.
The Importance of Endpoint Security
As more employees use personal devices like laptops, smartphones, and tablets for work, endpoint security has become critical to cybersecurity. Endpoint security safeguards these devices from cyberattacks. Since endpoints are often the first entry point for cyberattacks, securing them is essential to prevent data breaches and other security incidents.
Traditional endpoint security measures include antivirus software, firewalls, and intrusion detection systems. However, with cyberattacks becoming increasingly sophisticated, modern endpoint security solutions are leveraging advanced technologies such as artificial intelligence (AI) and machine learning. These technologies help detect and respond to threats in real-time, thereby providing more robust protection against malware, phishing, and other forms of cyberattacks.
The Role of Cyber Hygiene
While advanced security solutions are essential, maintaining basic cyber hygiene is equally important in protecting against cyber threats. Cyber hygiene refers to the routine practices and precautions that individuals and organisations should take to ensure the security and health of their digital systems. These practices include regularly updating software, using strong and unique passwords, and being vigilant against phishing attempts.
Maintaining good cyber hygiene is akin to practising good personal hygiene. Like washing your hands to avoid illness, you should update your software to prevent fraudsters from exploiting flaws. Strong passwords and multi-factor authentication make it more challenging for criminals to access your accounts.
Benefits of Digital Detoxification

In our always-on, hyperconnected world, the constant stream of digital information can lead to stress, burnout, and reduced productivity. Digital detoxification involves taking a deliberate break from digital devices and online activities to recharge and refocus. This practice can have significant benefits for both mental well-being and overall productivity.
Digital detoxification doesn't mean completely disconnecting from the digital world; it can be as simple as setting aside specific times during the day to be device-free. For example, many people find it helpful to disconnect during meals or before bed to avoid the distractions of social media, emails, and other online activities. Reducing digital overload can improve individuals' focus, sleep quality, and overall mental health.
Best Practices for Implementing Cloud Computing Security, Endpoint Security, Cyber Hygiene, and Digital Detoxification
To create a secure and balanced digital environment, it's essential to implement best practices across all areas of cybersecurity:
For cloud computing security, Ensure that your cloud service provider follows strict security protocols, uses strong encryption for data, and regularly reviews and updates its security policies.
For endpoint security: Implement complete endpoint protection, update devices with security patches, and warn users about unprotected networks.
For cyber hygiene: Use strong, unique passwords for each account, update software regularly, and teach personnel to spot and avoid phishing efforts.
For digital detoxification: Set boundaries for device use, take regular breaks from screens, and engage in offline activities to recharge mentally and physically.
Conclusion
Strong security is crucial as the digital landscape evolves. Cloud computing security, endpoint security, and cyber hygiene are essential to a cybersecurity plan that protects data and devices. Practice digital detoxification to balance digital engagement and personal well-being. Businesses and individuals may confidently traverse the digital world with these tactics, knowing they are secure and psychologically refreshed.
0 notes
Text
Online Scams Warning: The Importance of Using Two-Factor Authentication

In today's digital world, the convenience of the internet comes with certain risks. Scammers now use sophisticated online methods to steal personal information, money, and identities. Understanding these threats is crucial to safeguarding yourself against potential losses. This article provides an online scam warning and explores essential security measures, including two-factor and multi-factor authentication and the importance of cyber threat intelligence.
Understanding the Threat: Online Scams Warning
Online scams try to get victims' passwords, credit card numbers, and social security numbers. These frauds include phishing emails, fake websites, and social engineering. Unfortunately, as technology advances, so do the methods used by scammers. According to reports, online frauds are rising, affecting millions of individuals annually. The financial and emotional toll of these scams can be devastating, making it more important than ever to heed online scam warnings and take proactive steps to protect yourself.
Common Types of Online Scams
Phishing Attacks: Phishing is a prevalent online scam where attackers send fake emails or messages. These messages often connect to bogus websites that steal login credentials or personal information.
Fake Online Stores: Scammers create bogus web stores that sell popular products cheaply. These sites gather payment information without delivering goods.
Social Engineering: Social engineering manipulates people into disclosing confidential information. Scammers pose as reputable people or companies in phone calls, emails, or in-person interactions.
Tech Support Scams: In these scams, fraudsters pretend to be tech support representatives from well-known companies like Microsoft or Apple. They pretend your computer has a virus and offer to remedy it for a cost, installing malware or stealing your data.
Strengthening Your Security with Two-Factor Authentication
Two-factor authentication (2FA) is one of the best techniques for securing online accounts. By requiring two forms of verification, it significantly reduces the chances of a scammer gaining access to your personal information, even if they have your password.
What is Two-Factor Authentication?
Two-factor authentication requires two types of identification to authenticate identity. This usually requires a password and a smartphone or security token. Even if cybercriminals obtain your password, they need the second factor to access your account.
How to Enable Two-Factor Authentication
Check Your Accounts: Many online services, including social media, email, and financial platforms, offer two-factor authentication as an option. Check your account security settings for 2FA.
Set Up Two-Factor Authentication: Follow the service's instructions to enable two-factor authentication. This usually requires connecting your account to a mobile device or using Google Authenticator.
Use 2FA Consistently: Once 2FA is enabled, make it a habit to use it every time you log in to your accounts. While it may add an extra step, the enhanced security is worth the effort.
Enhancing Protection with Multi-Factor Authentication

While two-factor authentication is vital, multi-factor authentication (MFA) takes protection further. Multi-factor authentication adds security to online accounts by verifying users with two or more independent factors.
The Importance of Multi-Factor Authentication
Multi-factor authentication provides additional security by combining multiple types of verification, such as something you know (password), something you have (security token), and something you are (biometric data like fingerprints). This multi-layered method makes it challenging for scammers to breach your protection, even if they compromise one factor.
Implementing Multi-Factor Authentication
Choose the Right MFA Methods: Depending on the service, you may have several options for multi-factor authentication, including SMS codes, email verification, security tokens, and biometric verification. Select the most suitable methods.
Enable MFA on All Sensitive Accounts: Ensure that multi-factor authentication is enabled on all accounts that store sensitive information, such as banking, healthcare, and email accounts.
Regularly Review and Update Your MFA Settings: Technology and cyber threats are evolving rapidly. Periodically review your multi-factor authentication settings and update them to maintain maximum security.
Staying Informed with Cyber Threat Intelligence
Cyber threat intelligence collects, analyses, and comprehends cyber threats. By staying current on scams and cyber risks, you can protect yourself and your data.
How Cyber Threat Intelligence Can Help
Cyber threat intelligence involves monitoring various sources of information, including open-source intelligence, social media, and specialised cybersecurity platforms. This information is then analysed to identify patterns and emerging threats. By staying updated with cyber threat intelligence, you can recognise potential dangers and adjust your security practices accordingly.
Applying Cyber Threat Intelligence in Daily Life
Stay Informed: Regularly read cybersecurity news, blogs, and reports to stay informed about the latest online scams and threats.
Use Cyber Threat Intelligence Tools: Consider using tools and services that provide real-time cyber threat intelligence, alerting you to potential risks as they arise.
Adapt Your Security Practices: Use the insights from cyber threat intelligence to improve your security practices. This might include changing passwords frequently, enabling new security features, or avoiding certain websites or services.
Conclusion
In today's increasingly connected world, the threat of online scams is ever-present. By heeding this online scam warning and taking proactive steps, such as enabling two-factor and multi-factor authentication, you can significantly reduce your risk of falling victim to these scams. Additionally, staying informed with cyber threat intelligence will help you stay ahead of emerging threats. Remember, the best defence against online scams combines awareness, strong security measures, and continuous vigilance. Protect yourself and your information by implementing these essential security practices today.
#Cyber Threat Intelligence#Multi-factor authentication#Two-Factor Authentication#Online Scams Warning
0 notes
Text
Top Tips for Effective Theft Monitoring in the Digital Age
In today's rapidly evolving digital landscape, staying secure online is more important than ever. Businesses and individuals must secure their data and digital activities from rising cyber threats. This article will delve into four critical aspects of digital security: Email Whitelisting, the emerging threat of the Tesla Botnet, the importance of Theft Monitoring, and the growing concerns around Ad Fraud & Click Fraud. Understanding these concepts and using effective tactics helps protect your online presence and prevent costly security breaches.
The Importance of Email Allowlisting
A simple but effective email list ensures that critical emails enter your inbox without being sent to spam. In a world where phishing attempts and unsolicited emails are commonplace, it's easy for legitimate messages to get lost in the clutter.
How Email Whitelisting Works
Email Allowlisting involves adding specific email addresses or domains to a "safe list." When an email from an allowed sender arrives, it bypasses the spam filter and lands directly in your inbox. This would benefit businesses that need fast, secure communication with clients, partners, and assistance providers.
Benefits of Email Whitelisting
By using Email Whitelisting, you ensure that crucial communications are not missed. This can be vital for businesses that need to respond promptly to client inquiries or receive essential updates from service providers. Whitelisting also reduces phishing assaults by allowing only trusted emails into your inbox. It also improves the efficiency of your email management by filtering out irrelevant messages.
Understanding the Tesla Botnet
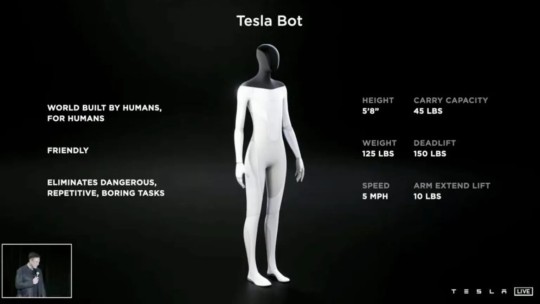
As cyber threats evolve, the Tesla Botnet has become a significant concern. Cybercriminals remotely control a botnet of infected machines without the owners' knowledge. The Tesla Botnet is one such network, and it has gained notoriety for its ability to carry out a range of malicious activities.
What is the Tesla Botnet?
Infected machines in the Tesla Botnet are used for DDoS assaults, data breaches, and Bitcoin mining. The botnet primarily targets IoT (Internet of Things) devices, exploiting vulnerabilities in these systems to gain control and carry out its operations.
How to Protect Against the Tesla Botnet
Multifaceted protection against the Tesla Botnet is needed. Ensure all devices, especially IoT ones, have the latest security patches and firmware. Use strong, unique passwords for each device and two-factor authentication whenever possible. Additionally, monitor your network for any unusual activity that could indicate a botnet infection, and consider using security software that can detect and neutralise such threats.
The Role of Theft Monitoring in Digital Security
As more personal and financial information is stored online, Theft Monitoring has become a critical component of digital security. Theft Monitoring involves actively tracking your data to detect unauthorised use, which can help prevent identity theft and financial fraud.
How Theft Monitoring Works
Theft monitoring services investigate the dark web for unlawful use of your Social Security number, bank account, or credit card information. If suspicious activity is detected, the service alerts you immediately, allowing you to take swift action to protect your identity and finances.
Why You Need Theft Monitoring
Theft Monitoring provides peace of mind by offering a proactive approach to identity protection. With the increasing number of data breaches and cyberattacks, having a system to monitor and protect your information is more critical than ever. Early identification via Theft Monitoring can avert financial loss and a lengthy identity restoration process.
Combating Ad Fraud & Click Fraud
In the digital marketing world, Ad Fraud and click Fraud pose serious challenges to businesses that rely on online advertising. Ad Fraud refers to the generation of fake impressions, clicks, or conversions, which leads to wasted ad spend and skewed performance metrics. Click fraud, which uses fake clicks to drain advertising budgets or mislead competition, also includes ad fraud.
The Impact of Ad Fraud & Click Fraud on Businesses
Ad Fraud & Click Fraud can have devastating effects on businesses. When companies pay for fraudulent clicks or impressions, they waste valuable resources that could have been used for genuine customer engagement. This not only distorts the effectiveness of ad campaigns but also inflates advertising costs. Moreover, the data from fraudulent activities can mislead marketing strategies, leading to poor business decisions.
Strategies to Prevent Ad Fraud & Click Fraud
To protect your business from Ad Fraud and click Fraud, it's essential to implement robust detection and prevention strategies. Utilise advanced analytics tools to identify abnormal patterns in ad interactions, such as sudden spikes in click rates or traffic from suspicious IP addresses. Partner with reputable ad networks with strict fraud detection protocols. Regularly audit your ad campaigns to ensure that the clicks and impressions you pay for are genuine. You may avoid these frauds by being cautious and using the correct tools.
Conclusion
In conclusion, the digital landscape presents numerous challenges, from managing email security through Email Whitelisting to protecting against sophisticated threats like the Tesla Botnet. Theft Monitoring plays a crucial role in safeguarding personal information, while businesses must remain vigilant against Ad Fraud and click Fraud to protect their advertising investments. Understanding these dangers and executing effective measures can improve your digital security and keep your online presence safe.
0 notes
Text
Captchas Demystified: How They Secure Your Online Activities
The internet is a powerful tool that has revolutionized how we live, work, and communicate. However, it also presents numerous security challenges. From malicious websites to phishing emails, online frauds are becoming increasingly sophisticated. Protecting yourself requires knowledge and tools to navigate these risks. This article will explore essential online security topics, including web filtering, Amazon email scams, reporting online frauds, and captchas demystified. Understanding these areas can help you stay safe online and avoid cyberattacks.
Understanding Web Filtering
Web filtering is a crucial component of online security. It involves controlling access to websites and online content based on specific criteria. Whether you are an individual user, a parent, or a business owner, web filtering can help protect you from harmful content and maintain a safe browsing environment.
How Web Filtering Works
Web filtering operates by blocking or allowing website access based on rules set by the user or administrator. These rules can be based on categories, such as adult content, gambling, or social media, or they can target specific URLs or keywords. Web filtering software analyzes a webpage's content and determines whether it should be accessible.
Benefits of Web Filtering
Enhanced Security: Web filtering protects against malicious websites that may host viruses, phishing attempts, or other harmful content. Web filtering helps prevent malware infections and data breaches by blocking these sites.
Increased Productivity: In workplaces and schools, web filtering can prevent access to distracting websites, helping users focus on tasks.
Parental Controls: Web filtering lets parents restrict their kids' online access for safety and age-appropriate content.
Identifying and Avoiding Amazon Email Scams
Amazon is one of the world's largest and most trusted online retailers. Unfortunately, this makes it a prime target for scammers. Amazon email scams are fraudulent emails that appear from Amazon but are designed to steal personal information or money.
Common Types of Amazon Email Scams
Phishing Emails: These emails seem like Amazon and ask you to click a link to authenticate your account, update payment information, or monitor a shipment. The link takes you to a bogus Amazon page that steals login and financial information.
Order Confirmation Scams: You might receive an email confirming an order you didn't place. The email includes a link to cancel the order, but clicking it can install malware on your device.
Gift Card Scams: Scammers may send emails claiming you've won an Amazon gift card. They ask for your personal information to claim the prize, which is used for fraud.
How to Avoid Amazon Email Scams
Verify the Sender: Always check the sender's email address. Legitimate emails from Amazon will come from an official Amazon domain, such as @amazon.com.
Don't Click Suspicious Links: If you receive an unexpected email, don't click any links. Instead, go directly to Amazon's website and log in to check your account.
Report Suspicious Emails: Report questionable emails to Amazon at [email protected] to assist others avoid these scams.
The Importance of Reporting Online Frauds
Online fraud is a growing problem; reporting it is essential to combating cybercrime. Whether you've encountered a phishing email, a fake website, or any other online scam, reporting online fraud can help protect others and contribute to law enforcement efforts.
How to Report Online Frauds
Report to the Website or Service: If fraud occurs on a specific platform, report it directly to that site. Most companies have procedures for handling fraud reports.
Complain to the FTC: The FTC is vital to combating US online fraud. On its website, it provides scam data for complaints.
Notify Your Financial Institution: If you've provided financial information to a scammer, immediately contact your bank or credit card company to protect your accounts.
Why Reporting Online Frauds Matters
Reporting online fraud is vital for several reasons:
Preventing Further Harm: Reporting fraud protects others from similar scams.
Supporting Law Enforcement: Your report helps law enforcement catch cybercriminals.
Raising Awareness: When fraud is reported, it helps spread awareness of the scam, making it less likely that others will fall for it.
Captchas Demystified: What They Are and Why They Matter

Captchas demystified are a standard feature on many websites, often appearing when trying to log in, create an account, or make a purchase. But what exactly are captchas, and why are they important?
What Are Captchas?
Captcha is a "Completely Automated Public Turing test to tell Computers and Humans Apart." This challenge-response test determines whether the user is a human or a bot. Captchas can take various forms, including distorted text that you must type in, image recognition tasks, or simple checkboxes.
Why Captchas Are Important
Preventing Automated Attacks: Captchas are designed to prevent bots from creating fake accounts, sending spam, or conducting brute-force attacks.
Securing Online Transactions: By ensuring that a human is completing the transaction, captchas help protect against fraudulent purchases and account breaches.
Improving Web Security: Captchas contribute to the broader security ecosystem by making it more difficult for automated programs to exploit online services.
Conclusion
In the ever-evolving landscape of online security, understanding key concepts like web filtering, Amazon email scams, reporting online frauds, and captchas is essential. By implementing web filtering, you can protect yourself from harmful content. Recognizing and avoiding Amazon email scams helps you safeguard your personal information. Reporting online fraud is a critical step in combating cybercrime, and understanding captchas demystified enables you to appreciate their role in keeping the internet secure. Stay informed and vigilant to enhance online safety and enjoy a safer browsing experience.
2 notes
·
View notes