#cloud computing security
Explore tagged Tumblr posts
Text
#cloud solutions for growing businesses#cloud computing for growing businesses#iclimb systems india private limited#iclimb website#cloud computing services#cloud computing companies#best cloud service provider#cloud computing security#best cloud computing services
0 notes
Text
Strengthening Endpoint Security Through Cloud Computing Security Measures

In today's interconnected world, where digital technology touches nearly every aspect of our lives, protecting our data and devices from cyber threats is more critical than ever. Cloud computing and work-related device use have increased the requirement for comprehensive security. This has brought cloud computing security and endpoint security to the forefront of cybersecurity strategies. Additionally, as we navigate our digital lives, maintaining good cyber hygiene and occasionally practising digital detoxification are essential for security and well-being. This post will discuss these crucial principles and offer practical advice for digital security.
Understanding Cloud Computing Security
Cloud computing has transformed data storage and access for organisations and consumers. However, cloud computing security becomes paramount as more data moves to the cloud. Cloud computing security involves implementing measures to protect cloud-based systems, data, and applications from cyber threats. These measures include encryption, identity and access management (IAM), and regular security audits.
Cloud computing security is complex during data transit and storage. Encryption is essential: it prevents data from being read without the correct key. Moreover, identity and access management controls who can access specific data and applications, reducing the risk of unauthorised access. Regular security audits also play a vital role in identifying vulnerabilities and ensuring current security measures.
The Importance of Endpoint Security
As more employees use personal devices like laptops, smartphones, and tablets for work, endpoint security has become critical to cybersecurity. Endpoint security safeguards these devices from cyberattacks. Since endpoints are often the first entry point for cyberattacks, securing them is essential to prevent data breaches and other security incidents.
Traditional endpoint security measures include antivirus software, firewalls, and intrusion detection systems. However, with cyberattacks becoming increasingly sophisticated, modern endpoint security solutions are leveraging advanced technologies such as artificial intelligence (AI) and machine learning. These technologies help detect and respond to threats in real-time, thereby providing more robust protection against malware, phishing, and other forms of cyberattacks.
The Role of Cyber Hygiene
While advanced security solutions are essential, maintaining basic cyber hygiene is equally important in protecting against cyber threats. Cyber hygiene refers to the routine practices and precautions that individuals and organisations should take to ensure the security and health of their digital systems. These practices include regularly updating software, using strong and unique passwords, and being vigilant against phishing attempts.
Maintaining good cyber hygiene is akin to practising good personal hygiene. Like washing your hands to avoid illness, you should update your software to prevent fraudsters from exploiting flaws. Strong passwords and multi-factor authentication make it more challenging for criminals to access your accounts.
Benefits of Digital Detoxification

In our always-on, hyperconnected world, the constant stream of digital information can lead to stress, burnout, and reduced productivity. Digital detoxification involves taking a deliberate break from digital devices and online activities to recharge and refocus. This practice can have significant benefits for both mental well-being and overall productivity.
Digital detoxification doesn't mean completely disconnecting from the digital world; it can be as simple as setting aside specific times during the day to be device-free. For example, many people find it helpful to disconnect during meals or before bed to avoid the distractions of social media, emails, and other online activities. Reducing digital overload can improve individuals' focus, sleep quality, and overall mental health.
Best Practices for Implementing Cloud Computing Security, Endpoint Security, Cyber Hygiene, and Digital Detoxification
To create a secure and balanced digital environment, it's essential to implement best practices across all areas of cybersecurity:
For cloud computing security, Ensure that your cloud service provider follows strict security protocols, uses strong encryption for data, and regularly reviews and updates its security policies.
For endpoint security: Implement complete endpoint protection, update devices with security patches, and warn users about unprotected networks.
For cyber hygiene: Use strong, unique passwords for each account, update software regularly, and teach personnel to spot and avoid phishing efforts.
For digital detoxification: Set boundaries for device use, take regular breaks from screens, and engage in offline activities to recharge mentally and physically.
Conclusion
Strong security is crucial as the digital landscape evolves. Cloud computing security, endpoint security, and cyber hygiene are essential to a cybersecurity plan that protects data and devices. Practice digital detoxification to balance digital engagement and personal well-being. Businesses and individuals may confidently traverse the digital world with these tactics, knowing they are secure and psychologically refreshed.
0 notes
Text
Top 10 Effective Practices To Secure Application Modernization On AWS
This is where AWS Cloud steps in, helping businesses upgrade their application portfolios for the future. At every level of the organization, it necessitates careful planning, effective implementation, and readiness to embrace change. Let’s discover the best 10 practices for effective application modernization on the AWS cloud.
#AWS Cloud#Application Modernization#application modernization services#aws security#aws security services#cloud security#cloud computing security#AWS Managed Services Providers#AWS Services#migrate to AWS
0 notes
Text

Cloud computing has one of the fastest adoption rates globally. Most organizations are using the power of cloud computing to access and manage data efficiently as well as for scalability. Currently, the global market size of cloud computing is $679 billion in 2024, and it is expected to surpass $1 trillion by 2027. It clearly shows how fast the world is adapting to cloud computing technology. And that increases the chances of cyber attacks and data breaches as well. It is a big concern that every organization is focusing on resolving by improving cloud computing security.
#cloud computing#cloud security#cloud computing security#cloud security solutions#software development security#cloud computing technologies
0 notes
Link
Cyber Security Services in UAE and other Gulf countries
#cyber security services#cybersecurity services#network security in networking#network and network security#cloud computing security#cyber security companies#computer security companies#top cyber security companies#Cyber security solutions#Cybersecurity solutions
0 notes
Text
Evolve Cloud Labs: Revolutionizing Businesses with Cloud Native Services
Introduction
In the fast-paced digital era, businesses are increasingly embracing cloud technology to enhance agility, scalability, and innovation. Cloud native services have emerged as a key enabler in this transformation, empowering companies to build, deploy, and manage applications efficiently. Among the pioneers in the USA, Evolve Cloud Labs has been at the forefront, revolutionizing the cloud native landscape with its cutting-edge solutions. This article delves into the world of Evolve Cloud Labs, exploring its services and contributions to the ever-evolving cloud industry.
A Glimpse into Evolve Cloud Labs
Evolve Cloud Labs is a premier cloud native services company based in the USA. With a strong focus on innovation and client-centricity, the company has been a trailblazer in helping businesses harness the true potential of cloud technology. Established by visionary entrepreneurs, Evolve Cloud Labs quickly gained prominence for its technical expertise, unwavering commitment, and remarkable problem-solving capabilities.
Cloud Native Services Offered
Cloud Strategy and Consultation: Evolve Cloud Labs takes pride in delivering tailor-made cloud strategies aligned with each client's unique business objectives. Their team of experienced cloud architects collaborates closely with clients to understand their requirements and designs efficient cloud solutions.
Cloud-Native Application Development: Embracing the best practices of cloud-native architecture, the company develops applications that are highly scalable, resilient, and cost-effective. By leveraging cutting-edge technologies, such as containers and microservices, Evolve Cloud Labs empowers clients to adapt to changing business needs swiftly.
Cloud Migration Services: Migrating legacy systems to the cloud requires careful planning and execution. Evolve Cloud Labs simplifies this process by utilizing well-established migration methodologies, minimizing disruptions, and ensuring a seamless transition to the cloud environment.
DevOps and Automation: The company emphasizes DevOps practices to accelerate application development and deployment. Through automation, continuous integration, and continuous delivery (CI/CD), clients can experience enhanced efficiency and reduced time-to-market.
Cloud Security Solutions: Recognizing the criticality of data security, Evolve Cloud Labs implements robust security measures to protect clients' sensitive information and ensure compliance with industry standards.
Managed Cloud Services: Post-implementation, the company offers comprehensive managed services to maintain and optimize cloud infrastructure. This enables clients to focus on their core business while leaving the technical complexities to the experts at Evolve Cloud Labs.
Contributions to the Cloud Native Community
Beyond their exceptional services, Evolve Cloud Labs actively contributes to the growth and development of the cloud native community. They frequently organize workshops, webinars, and seminars to share knowledge, best practices, and emerging trends in the cloud industry. Their contributions to open-source projects and engagement in collaborative forums demonstrate their commitment to advancing the field.
Client Success Stories
Evolve Cloud Labs' success can be measured by the accomplishments of their clients. Numerous businesses, ranging from startups to Fortune 500 companies, have experienced significant transformations with the implementation of cloud native services. Improved application performance, cost savings, and increased agility are just a few of the benefits clients have reported.
Conclusion
Evolve Cloud Labs stands tall as a trailblazer in the cloud native services domain, empowering businesses to thrive in the digital era. With a relentless pursuit of excellence, a customer-centric approach, and a passion for innovation, the company continues to lead the charge in transforming businesses across the USA. As the cloud landscape evolves, Evolve Cloud Labs remains dedicated to driving the adoption of cutting-edge technologies, ensuring their clients stay ahead of the curve. To learn more about Evolve Cloud Labs and its services, visit their website.
#cloud native services company#cloud native application development#cloud migration#cloud modernization#cloud data engineering#cloud computing security
1 note
·
View note
Text
On Personal InfoSec
Been awhile since I've had one of these posts but I figure with all that's going on in the world it's time to make another one of these posts and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides.
Browsers:
There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out.
Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN:
Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Proton VPN: Has easily the most amount of countries serviced, can take cash payments, and does offer port forwarding.
Email Provider:
Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Outlook.com you'll need to pay.
Proton Mail: Secure, end-to-end encrypted, and fairly easy to setup and use. Offers a free option up to 1gb
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Email Client:
Thunderbird if you're on Windows or Linux
Apple Mail if you're on macOS
Cloud Storage:
Proton Drive: Encrypted cloud storage from the same people as Proton Mail.
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free, and open source.
Chat Clients:
Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode.
If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help.
I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#information security#infosec#computer security#computer infosec#personal infosec#browsers#internet browser#email#instant messaging#cloud storage#linux#pop os#linux mint#ubuntu#firefox#firefox extensions#long post
56 notes
·
View notes
Text
Secure and Scalable Cloud Server Management at Atcuality
For businesses seeking to enhance scalability and maintain top-tier security, Atcuality provides unparalleled cloud server management services. Our solutions cover all aspects of cloud server maintenance, including load balancing, patch management, data backups, and disaster recovery planning. Our experienced professionals work with cutting-edge tools to ensure that your servers are secure, efficient, and scalable to meet changing business needs. Whether you operate in e-commerce, finance, or technology, we tailor our services to align with your operational goals. With Atcuality as your trusted partner, you can focus on driving growth while we handle the technical complexities of cloud management.
#seo marketing#seo services#artificial intelligence#azure cloud services#seo agency#digital marketing#seo company#iot applications#ai powered application#amazon web services#ai applications#virtual reality#augmented reality agency#augmented human c4 621#augmented and virtual reality market#augmented intelligence#augmented reality#cloud security services#cloud computing#cloud services#cloud service provider#cloud server hosting#software#devops#information technology#cash collection application#task management#blockchain#web developing company#web development
2 notes
·
View notes
Text
youtube
Top 5 Cloud Computing Skills for 2025 (Salaries Included)
In this video, he share the top 5 Cloud Computing Skills for 2025, and he included all the salaries for these skills as well as the Cloud Computing Jobs you can apply for.
#education#Cloud Computing Skills#cloudcomputing#educate yourself#educate yourselves#security#technology#awscloud#aws cloud#ai machine learning#Top 5 Cloud Computing Skills for 2025#education for all#youtube#Youtube
2 notes
·
View notes
Text

The Comprehensive Guide to Web Development, Data Management, and More
Introduction
Everything today is technology driven in this digital world. There's a lot happening behind the scenes when you use your favorite apps, go to websites, and do other things with all of those zeroes and ones — or binary data. In this blog, I will be explaining what all these terminologies really means and other basics of web development, data management etc. We will be discussing them in the simplest way so that this becomes easy to understand for beginners or people who are even remotely interested about technology. JOIN US
What is Web Development?
Web development refers to the work and process of developing a website or web application that can run in a web browser. From laying out individual web page designs before we ever start coding, to how the layout will be implemented through HTML/CSS. There are two major fields of web development — front-end and back-end.
Front-End Development
Front-end development, also known as client-side development, is the part of web development that deals with what users see and interact with on their screens. It involves using languages like HTML, CSS, and JavaScript to create the visual elements of a website, such as buttons, forms, and images. JOIN US
HTML (HyperText Markup Language):
HTML is the foundation of all website, it helps one to organize their content on web platform. It provides the default style to basic elements such as headings, paragraphs and links.
CSS (Cascading Style Sheets):
styles and formats HTML elements. It makes an attractive and user-friendly look of webpage as it controls the colors, fonts, layout.
JavaScript :
A language for adding interactivity to a website Users interact with items, like clicking a button to send in a form or viewing images within the slideshow. JOIN US
Back-End Development
The difference while front-end development is all about what the user sees, back end involves everything that happens behind. The back-end consists of a server, database and application logic that runs on the web.
Server:
A server is a computer that holds website files and provides them to the user browser when they request it. Server-Side: These are populated by back-end developers who build and maintain servers using languages like Python, PHP or Ruby.
Database:
The place where a website keeps its data, from user details to content and settings The database is maintained with services like MySQL, PostgreSQL, or MongoDB. JOIN US
Application Logic —
the code that links front-end and back-end It takes user input, gets data from the database and returns right informations to front-end area.

Why Proper Data Management is Absolutely Critical
Data management — Besides web development this is the most important a part of our Digital World. What Is Data Management? It includes practices, policies and procedures that are used to collect store secure data in controlled way.
Data Storage –
data after being collected needs to be stored securely such data can be stored in relational databases or cloud storage solutions. The most important aspect here is that the data should never be accessed by an unauthorized source or breached. JOIN US
Data processing:
Right from storing the data, with Big Data you further move on to process it in order to make sense out of hordes of raw information. This includes cleansing the data (removing errors or redundancies), finding patterns among it, and producing ideas that could be useful for decision-making.
Data Security:
Another important part of data management is the security of it. It refers to defending data against unauthorized access, breaches or other potential vulnerabilities. You can do this with some basic security methods, mostly encryption and access controls as well as regular auditing of your systems.
Other Critical Tech Landmarks
There are a lot of disciplines in the tech world that go beyond web development and data management. Here are a few of them:
Cloud Computing
Leading by example, AWS had established cloud computing as the on-demand delivery of IT resources and applications via web services/Internet over a decade considering all layers to make it easy from servers up to top most layer. This will enable organizations to consume technology resources in the form of pay-as-you-go model without having to purchase, own and feed that infrastructure. JOIN US
Cloud Computing Advantages:
Main advantages are cost savings, scalability, flexibility and disaster recovery. Resources can be scaled based on usage, which means companies only pay for what they are using and have the data backed up in case of an emergency.
Examples of Cloud Services:
Few popular cloud services are Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. These provide a plethora of services that helps to Develop and Manage App, Store Data etc.
Cybersecurity
As the world continues to rely more heavily on digital technologies, cybersecurity has never been a bigger issue. Protecting computer systems, networks and data from cyber attacks is called Cyber security.
Phishing attacks, Malware, Ransomware and Data breaches:
This is common cybersecurity threats. These threats can bear substantial ramifications, from financial damages to reputation harm for any corporation.
Cybersecurity Best Practices:
In order to safeguard against cybersecurity threats, it is necessary to follow best-practices including using strong passwords and two-factor authorization, updating software as required, training employees on security risks.
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) represent the fastest-growing fields of creating systems that learn from data, identifying patterns in them. These are applied to several use-cases like self driving cars, personalization in Netflix.
AI vs ML —
AI is the broader concept of machines being able to carry out tasks in a way we would consider “smart”. Machine learning is a type of Artificial Intelligence (AI) that provides computers with the ability to learn without being explicitly programmed. JOIN US
Applications of Artificial Intelligence and Machine Learning: some common applications include Image recognition, Speech to text, Natural language processing, Predictive analytics Robotics.
Web Development meets Data Management etc.
We need so many things like web development, data management and cloud computing plus cybersecurity etc.. but some of them are most important aspects i.e. AI/ML yet more fascinating is where these fields converge or play off each other.
Web Development and Data Management
Web Development and Data Management goes hand in hand. The large number of websites and web-based applications in the world generate enormous amounts of data — from user interactions, to transaction records. Being able to manage this data is key in providing a fantastic user experience and enabling you to make decisions based on the right kind of information.
E.g. E-commerce Website, products data need to be saved on server also customers data should save in a database loosely coupled with orders and payments. This data is necessary for customization of the shopping experience as well as inventory management and fraud prevention.
Cloud Computing and Web Development
The development of the web has been revolutionized by cloud computing which gives developers a way to allocate, deploy and scale applications more or less without service friction. Developers now can host applications and data in cloud services instead of investing for physical servers.
E.g. A start-up company can use cloud services to roll out the web application globally in order for all users worldwide could browse it without waiting due unavailability of geolocation prohibited access.
The Future of Cybersecurity and Data Management
Which makes Cybersecurity a very important part of the Data management. The more data collected and stored by an organization, the greater a target it becomes for cyber threats. It is important to secure this data using robust cybersecurity measures, so that sensitive information remains intact and customer trust does not weaken. JOIN US
Ex: A healthcare provider would have to protect patient data in order to be compliant with regulations such as HIPAA (Health Insurance Portability and Accountability Act) that is also responsible for ensuring a degree of confidentiality between a provider and their patients.
Conclusion
Well, in a nutshell web-developer or Data manager etc are some of the integral parts for digital world.
As a Business Owner, Tech Enthusiast or even if you are just planning to make your Career in tech — it is important that you understand these. With the progress of technology never slowing down, these intersections are perhaps only going to come together more strongly and develop into cornerstones that define how we live in a digital world tomorrow.
With the fundamental knowledge of web development, data management, automation and ML you will manage to catch up with digital movements. Whether you have a site to build, ideas data to manage or simply interested in what’s hot these days, skills and knowledge around the above will stand good for changing tech world. JOIN US
#Technology#Web Development#Front-End Development#Back-End Development#HTML#CSS#JavaScript#Data Management#Data Security#Cloud Computing#AWS (Amazon Web Services)#Cybersecurity#Artificial Intelligence (AI)#Machine Learning (ML)#Digital World#Tech Trends#IT Basics#Beginners Guide#Web Development Basics#Tech Enthusiast#Tech Career#america
4 notes
·
View notes
Text
#web development service#e commerce website development service#web development company#web app development services#web and mobile app development services#it management service#it management solutions#it infrastructure management services#it service management consulting#it service operations management#cyber security service#cyber security company#cyber security solution#cyber security service provider#cyber security consultation#cloud computing services#cloud computing companies#best cloud service provider#cloud computing security#best cloud computing services#iot services#iot solutions#iot development services#iot software development#iot network solutions#hr services#staffing service provider#hr recruitment solutions#hr services company#staffing solutions provider
0 notes
Text
Broadcom's AI surge challenges Nvidia's dominance
New Post has been published on https://thedigitalinsider.com/broadcoms-ai-surge-challenges-nvidias-dominance/
Broadcom's AI surge challenges Nvidia's dominance
.pp-multiple-authors-boxes-wrapper display:none; img width:100%;
Riding the AI wave, semiconductor giant Broadcom has joined the stampede of companies chasing Nvidia for a piece of the lucrative AI chip market. The computing and software conglomerate is up more than 66% in the past year, as it makes power moves to establish itself as one of the most dominant players in AI today. Broadcom has been making aggressive moves that have piqued the interest of analysts and investors, from buying VMware in a $61 billion deal to strengthen its data centre and cloud chops, to investments in AI chip R&D.
Central to Broadcom’s AI aspirations now is its fast-growing AI-connected chip business, which the company said it now forecasts will bring in an astounding $11 billion in revenue for fiscal 2024, up from a previous forecast of $10 billion. Combined with a 15% jump in Broadcom Inc shares recently, the upward revision reinforces the strong appetite for chips driving the rise of generative AI.
Morningstar analysts agreed in a note to Reuters that Broadcom remains “we continue to see Broadcom as incredibly well-positioned to benefit from rising generative AI investment in the long term,” — a view widely held on Wall Street. A second explanation for the upswing in AI for Broadcom is essentially through buying or investing very well over the years.
They come as one of three planned spinoffs in Dell’s drive to become a full-fledged cloud computing firm with the $61 billion acquisition of VMware next year, which also added $50 billion to its market capitalisation, per FactSet data. In addition, Broadcom has been ramping up its own custom AI chip business, inking deals with tech giants including Alphabet’s Google and Meta Platforms.
In March, the company revealed that a third unidentified customer was using its custom AI chips, which gave its business credibility in this high-stakes industry. According to Reuters, “At an investor conference on Wednesday, Broadcom said it will produce the new custom AI chips for ‘hyperscaler’ buyers that are mostly Alphabet’s Google and Meta Platforms.”
Diversified revenue streams and investor optimism
Broadcom’s software division, bolstered by the VMware acquisition, added $2.7 billion to its second-quarter revenue, further diversifying the company’s revenue streams and positioning it as a formidable force in the AI ecosystem. The company’s stock performance reflects this optimism, with shares surging 76% over the past 12 months and closing at a staggering $1,495.5 on Wednesday.
Broadcom’s recent announcement of a 10-for-1 stock split, a move reminiscent of Nvidia’s strategy, is expected to further fuel investor enthusiasm. “It’s a sure-fire way to send your stock soaring,” Triple D Trading analyst Dennis Dick told Reuters, commenting on the stock split, adding that the move was “right out of Nvidia’s book.”
Nvidia’s dominance and competitive pressure
Broadcom is progressing, but Nvidia is still the leader in this space. For years, Nvidia has benefited from the first-mover advantage of producing AI chips that cater to a long tail of applications while favoring innovation over turning in big volume. While that balance appears to be in flux, Broadcom’s recent wins shed light on how the writing may be on the wall for a boom in AI now benefiting more than just one company.
This new contender has even forced Nvidia’s CEO Jensen Huang to admit that ‘a resurgent Broadcom (and other start-ups) have planners at Nvidia nervous. Huang, for his part, stressed how the company must continue to innovate to ensure that it remains ahead of its peers. Nevertheless, competition has yet to make a dent on Nvidia’s enviable lead in the AI chip market as the company busily cranks out its top-performing AI tech.
Broadcom vs Nvidia: The battle for AI chip supremacy
Unlike Nvidia’s graphics processing units which have long dominated the industry, Broadcom’s custom AI chips – or application-specific integrated circuits – might offer a great business opportunity for tech giants with massive and steady-state AI workloads. These bespoke chips require considerable initial capital investment but they can offer large cost savings in both CapEx and power consumption, which sets them up as a more cost-effective (if less general purpose) option to Nvidia’s.
Also bullish on Broadcom is Piper Sandler analyst Harsh Kumar, who writes, “We continue to see [Broadcom] as the best AI play [excluding Nvidia] due to its strong positioning in the custom ASIC business along with its strong software portfolio.”
Broadcom’s multi-pronged strategy of pumping cash into buyouts, offering bespoke chips and expanding into a software business has established it as a strong rival, as the AI revolution shows few signs of abating. Nvidia is still the undisputed leader in the industry, but Broadcom’s bold AI play here was enough to light a fire under investors and analysts both, sowing the seeds of what could become an epic showdown in the market for AI chips.
(Photo by Kenny Eliason)
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
Tags: ai, artificial intelligence, broadcom, Nvidia
#2024#ai#ai & big data expo#AI chip#AI chips#amp#applications#Art#artificial#Artificial Intelligence#automation#Big Data#billion#book#broadcom#Business#CEO#chips#Cloud#cloud computing#Companies#competition#comprehensive#computing#conference#cost savings#Custom AI Chip#cyber#cyber security#data
2 notes
·
View notes
Text
A Complete Guide to Mastering Microsoft Azure for Tech Enthusiasts
With this rapid advancement, businesses around the world are shifting towards cloud computing to enhance their operations and stay ahead of the competition. Microsoft Azure, a powerful cloud computing platform, offers a wide range of services and solutions for various industries. This comprehensive guide aims to provide tech enthusiasts with an in-depth understanding of Microsoft Azure, its features, and how to leverage its capabilities to drive innovation and success.
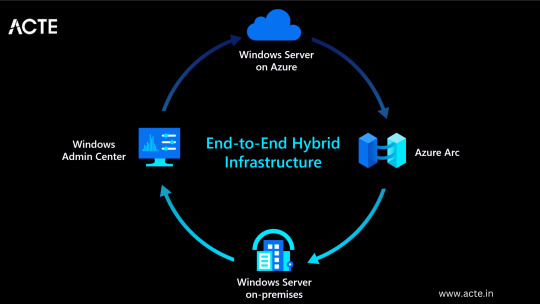
Understanding Microsoft Azure
A platform for cloud computing and service offered through Microsoft is called Azure. It provides reliable and scalable solutions for businesses to build, deploy, and manage applications and services through Microsoft-managed data centers. Azure offers a vast array of services, including virtual machines, storage, databases, networking, and more, enabling businesses to optimize their IT infrastructure and accelerate their digital transformation.
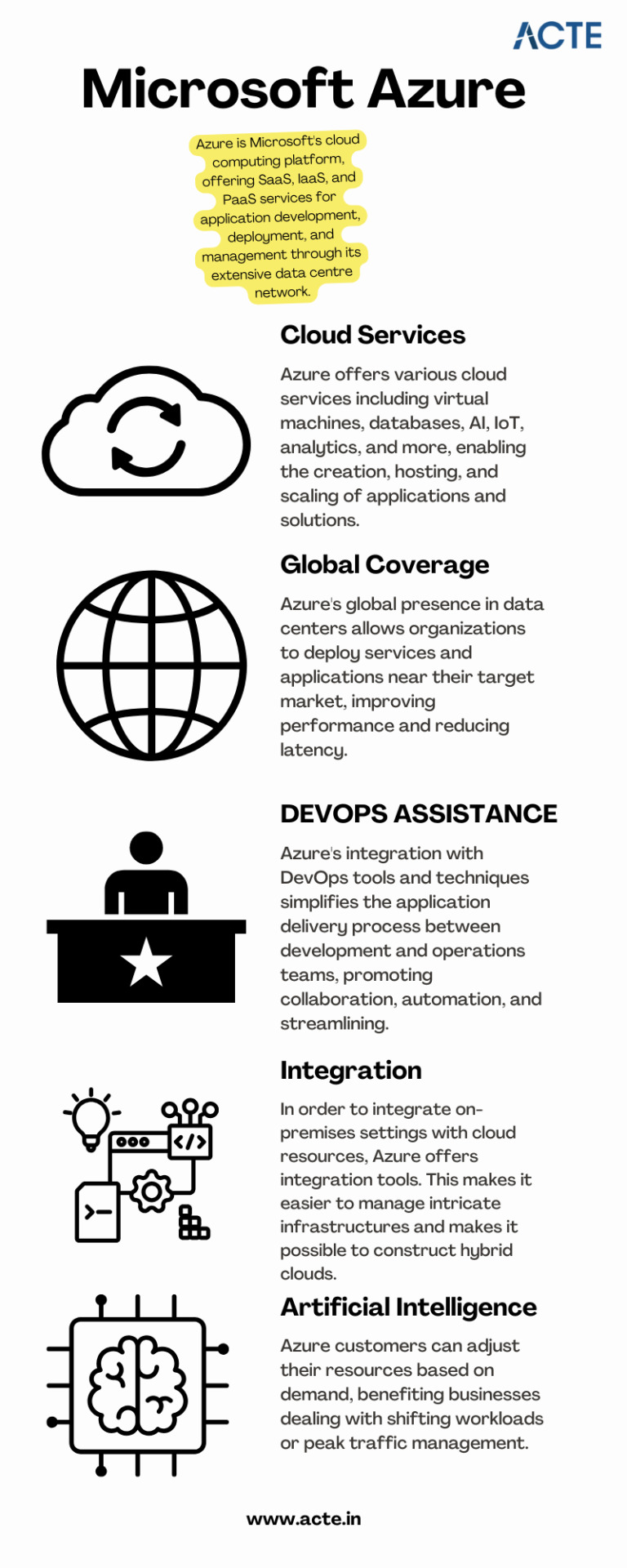
Cloud Computing and its Significance
Cloud computing has revolutionized the IT industry by providing on-demand access to a shared pool of computing resources over the internet. It eliminates the need for businesses to maintain physical hardware and infrastructure, reducing costs and improving scalability. Microsoft Azure embraces cloud computing principles to enable businesses to focus on innovation rather than infrastructure management.
Key Features and Benefits of Microsoft Azure
Scalability: Azure provides the flexibility to scale resources up or down based on workload demands, ensuring optimal performance and cost efficiency.
Vertical Scaling: Increase or decrease the size of resources (e.g., virtual machines) within Azure.
Horizontal Scaling: Expand or reduce the number of instances across Azure services to meet changing workload requirements.
Reliability and Availability: Microsoft Azure ensures high availability through its globally distributed data centers, redundant infrastructure, and automatic failover capabilities.
Service Level Agreements (SLAs): Guarantees high availability, with SLAs covering different services.
Availability Zones: Distributes resources across multiple data centers within a region to ensure fault tolerance.
Security and Compliance: Azure incorporates robust security measures, including encryption, identity and access management, threat detection, and regulatory compliance adherence.
Azure Security Center: Provides centralized security monitoring, threat detection, and compliance management.
Compliance Certifications: Azure complies with various industry-specific security standards and regulations.
Hybrid Capability: Azure seamlessly integrates with on-premises infrastructure, allowing businesses to extend their existing investments and create hybrid cloud environments.
Azure Stack: Enables organizations to build and run Azure services on their premises.
Virtual Network Connectivity: Establish secure connections between on-premises infrastructure and Azure services.
Cost Optimization: Azure provides cost-effective solutions, offering pricing models based on consumption, reserved instances, and cost management tools.
Azure Cost Management: Helps businesses track and optimize their cloud spending, providing insights and recommendations.
Azure Reserved Instances: Allows for significant cost savings by committing to long-term usage of specific Azure services.
Extensive Service Catalog: Azure offers a wide range of services and tools, including app services, AI and machine learning, Internet of Things (IoT), analytics, and more, empowering businesses to innovate and transform digitally.
Learning Path for Microsoft Azure
To master Microsoft Azure, tech enthusiasts can follow a structured learning path that covers the fundamental concepts, hands-on experience, and specialized skills required to work with Azure effectively. I advise looking at the ACTE Institute, which offers a comprehensive Microsoft Azure Course.

Foundational Knowledge
Familiarize yourself with cloud computing concepts, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Understand the core components of Azure, such as Azure Resource Manager, Azure Virtual Machines, Azure Storage, and Azure Networking.
Explore Azure architecture and the various deployment models available.
Hands-on Experience
Create a free Azure account to access the Azure portal and start experimenting with the platform.
Practice creating and managing virtual machines, storage accounts, and networking resources within the Azure portal.
Deploy sample applications and services using Azure App Services, Azure Functions, and Azure Containers.
Certification and Specializations
Pursue Azure certifications to validate your expertise in Azure technologies. Microsoft offers role-based certifications, including Azure Administrator, Azure Developer, and Azure Solutions Architect.
Gain specialization in specific Azure services or domains, such as Azure AI Engineer, Azure Data Engineer, or Azure Security Engineer. These specializations demonstrate a deeper understanding of specific technologies and scenarios.
Best Practices for Azure Deployment and Management
Deploying and managing resources effectively in Microsoft Azure requires adherence to best practices to ensure optimal performance, security, and cost efficiency. Consider the following guidelines:
Resource Group and Azure Subscription Organization
Organize resources within logical resource groups to manage and govern them efficiently.
Leverage Azure Management Groups to establish hierarchical structures for managing multiple subscriptions.
Security and Compliance Considerations
Implement robust identity and access management mechanisms, such as Azure Active Directory.
Enable encryption at rest and in transit to protect data stored in Azure services.
Regularly monitor and audit Azure resources for security vulnerabilities.
Ensure compliance with industry-specific standards, such as ISO 27001, HIPAA, or GDPR.
Scalability and Performance Optimization
Design applications to take advantage of Azure’s scalability features, such as autoscaling and load balancing.
Leverage Azure CDN (Content Delivery Network) for efficient content delivery and improved performance worldwide.
Optimize resource configurations based on workload patterns and requirements.
Monitoring and Alerting
Utilize Azure Monitor and Azure Log Analytics to gain insights into the performance and health of Azure resources.
Configure alert rules to notify you about critical events or performance thresholds.
Backup and Disaster Recovery
Implement appropriate backup strategies and disaster recovery plans for essential data and applications.
Leverage Azure Site Recovery to replicate and recover workloads in case of outages.
Mastering Microsoft Azure empowers tech enthusiasts to harness the full potential of cloud computing and revolutionize their organizations. By understanding the core concepts, leveraging hands-on practice, and adopting best practices for deployment and management, individuals become equipped to drive innovation, enhance security, and optimize costs in a rapidly evolving digital landscape. Microsoft Azure’s comprehensive service catalog ensures businesses have the tools they need to stay ahead and thrive in the digital era. So, embrace the power of Azure and embark on a journey toward success in the ever-expanding world of information technology.
#microsoft azure#cloud computing#cloud services#data storage#tech#information technology#information security
6 notes
·
View notes
Photo
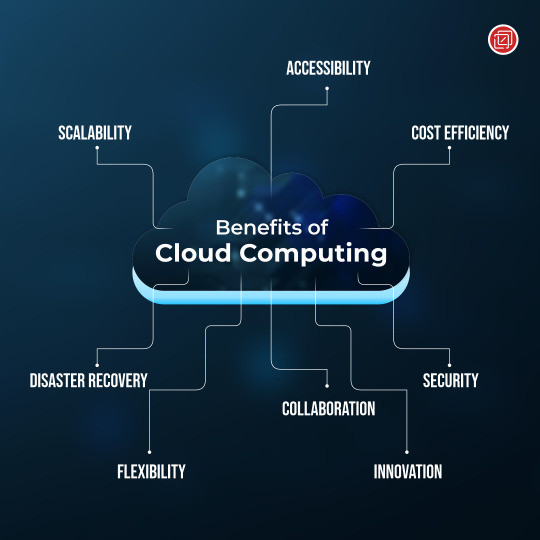






Embrace the cloud for scalability, cost efficiency, accessibility, disaster recovery, security, collaboration, flexibility, and innovation.
Remember to evaluate providers and implement security measures for successful cloud adoption.
Ready to unlock the power of the cloud? Consult with cloud experts and start harnessing these benefits for your business today!
Happy cloud computing! ☁️💪
6 notes
·
View notes
Text
But I’m sure they’re being totally responsible with AI.
4 notes
·
View notes
Text
Best Final Year Project Ideas for Students
Discover innovative and high-scoring project ideas for engineering, IT, and science final year students.
#cyber security projects for final year students#cyber security projects for final year#web development projects for final year#final year projects for cse#python projects for final year students#network security projects for final year students#cyber security final year project#data science final year projects#app development projects for final year#cloud computing projects for final year students#best web development projects for final year students#web development project for final year#final year project for cyber security#cloud computing final year project#aws projects for final year github#best computer science projects for final year#best computer science final year projects#best final year projects for it students#best major project for cse#best project for computer science final year#best projects for it final year#best python projects for final year students#cloud based final year projects#cloud computing based projects for final year#cloud computing projects final year#cloud projects for final year students
0 notes