Don't wanna be here? Send us removal request.
Text
Week 08: Security Everywhere 06
https://www.smh.com.au/national/nsw/high-tech-cameras-to-nab-motorists-catch-eye-of-privacy-commissioner-20190718-p528dt.html
I saw this post while browsing reddit /r/sydney a week or so ago, and looking back, it ties in neatly with the week 07 tutorial case study, where we debated whether or not we should have more surveillence. Also, the author of the article Matt O’Sullivan, was the guest speaker who came and spoke in one of the earlier weeks!
So what happened was there were cameras set up along two roads, where it took a photo of every driver that passed, regardless of what they were doing. The plan was to catch people who had their phones else/doing other illegal things, but taking pictures of everybody that passes seems wrong. The people who set up the cameras assured the public that most pictures were deleted “within an hour”. I 100% don’t believe them, and believe that those pictures would be stored a lot longer, either for training the AI or for other data collecting reasons.
0 notes
Text
Week 08: Zero Knowledge Proofs
Zero Knowledge Proofs are really interesting, I watched this video by Adam Smallhorn which went through it with some more details
https://www.youtube.com/watch?v=hVKXIxLb4HM
We also went through an example in class, which I found was the most straight forward to understand. So person A is colourblind and doesn’t believe that the two pool balls in front of him are different colours. So person A holds the two balls out in his hands, person B looks at them, and person A holds the balls behind his back and either shuffles them or doesn’t. Because person B can “see colour”, he will know for a fact whether person A shuffled them or not. But person A will never know what the colours are. Repeat this a million times, and the probability of “guessing” drops to 0, so it’s “proven” that person B can see colour, but person A never finds out what the colours are.
So how does this apply to security: we want to prove that we know the password to someone, without revealing the password! You would repeat a test a million times, and getting it right everytime would essentially “prove” that you know the password.
0 notes
Text
Week 08: plsdonthaq.me Shuffle
This was a fun one, I’m not that familar with python so there was a lot of googling and looking at stackoverflow forum posts. But eventually I wrote some python which went through the shuffle.txt, scanned each line, extracted the number using regular expressions (findall) and placed it in a dictionary (with the corresponding line). Then all it took was to sort the dictionary, and as I printed out each line into a text file, I first took out the “::number::” from each line using another regular expression (replace).
Yay I appeared!

I’ll leave the flag out due to spoilers
0 notes
Text
Week 08: Tutorial Reflection
Most of the tutorial was spent watching everybody’s something awesome presentation, and they were all really cool!. We didn’t end up going over the case study so I had a go at it a copy of days after the tutorial.
I haven’t watched Stargate SG1, but I have seen one and a bit seasons of Stargate Atlantis. It’s a really good show!
So the problem is, I’m Major “M”, who can speak to an alien A, but I can’t see the invisible man X (Jack, from the Youtube clip). Jack can speak to the alien, who can in turn speak to me. This does seem really similar to the Houdini case, and the question was raised in the tutorial. But it does make sense, houdini focused more on authentication, while this case study is focusing more on integrity.
Now... we can’t get Jack to do RSA in his head... if only
So how do we guarantee the integrity of our conversation, so that we know the alien is tampering with our conversation like a man in the middle attack
I remember from the BBC show Sherlock, there was a scene when Sherlock was about to open a safe, which had a trap (gun) rigged inside of it. He looked at Irene and realized it was a trap. He shouted out “Vatican Cameos”, and Holmes immediately knew there was danger. It’s a stretch but I would be hoping I would know Jack well. Maybe Jack could say something which seems innocent/random to the Alien, but to me it would immediately scream “danger, I’m/we’re in danger”. Or better yet, inspired by the Youtube clip listed on the case study page. The way Jack would talk through the alien, could be an indication of who is talking. If Jack had a very peculiar way of speaking/was very rude/worded his sentences in such a way that I knew it was Jack... that would prove integrity I think.
Looking at it, I think it still comes down to a pre-shared secret of some kind. I was thinking of asking Jack something I knew only he would know, but I guess that falls under authentication instead of integrity. So yeah, I think the best way to guarantee integrity would be to notice the wording of how “Jack” is speaking through the Alien. A very peculiar way of speaking, that screams “I am Jack” would be a viable option.
0 notes
Text
Week 08: Lecture Reflection
In the morning lecture, we started off by covering errors, and the question was, when something goes wrong, what is the root cause? We covered root cause analysis, where we try to work out what was the original reason something went wrong, because if we can work that out, we can prevent future errors from occurring. We went through a cyber disaster example:
We could blame user error (shift the blame)
We could blame the culture
After that we went through how humans focus on what grabs our attention instead of what’s important. We talked about magicians and how the whole trick relies on the magician controlling the audiences attention, drawing them away from where the real trick is happening.
We covered frequency gambling, where we match the current situation with previous situations, and we pick the most common solution we’ve used in the past. We covered a few smaller topics like confirmation bias and satisficing (good enough, not perfect). Admittedly at this point in time my attention was drawn elsewhere and I stopped taking notes on the morning lecture. Hopefully I’ll be able to read through the compiled week 08 notes for what I missed out on.
In the evening lecture, Richard Buckland read us a story! About the 3 mile island nuclear reactor incident. “If you design a system without security in mind, expect normal security breaches” - Richard. He said we have to stop focusing on scapegoats and systems that can’t fail, and design systems so that the impact is limited when things go wrong.
We covered the steps in asset management
Work out your most important assets, and just defend them
Assume you will be breached and set it up so that it won’t be a total disaster (compartmentalize?)
0 notes
Text
Week 08: Buffer Overflow Challenges 1.2 Blind
I tried these in week 07 but struggled, this past week was hectic, especially since I presented on tuesday with the forensics group and on wednesday for my something awesome.
Okay... running ./blind I get “This is almost exactly the same as jump...”
The hint from my tutor was to use objdump, specifically objdump -h (headers)
Okay I get 25 different headers, how do I know which one is the function we want?
I googled gdb show all functions, and found the command info functions
This showed me that there was main function, win function and vuln function
I’m gonna assume that the vuln function gets called when I run ./blind, and I need it to run the win function
disass vuln shows me that its setting up a buffer, and calling gets
From info functions I can see that the win function starts at 0x08048506
But how big is the buffer?
python -c “print(’A’ * 64 + ‘\x06\x85\x04\x08′) | ./blind doesn’t seem to work
python -c “print(’A’ * 72 + ‘\x06\x85\x04\x08′) | ./blind seg faults but also prints out the same message a second time, so something must be happening
Been trying things like ltrace, strace, gdb but no luck so far
Googled some reverse engineering posts
Okay... by stepping through with gdb I can see that once it gets to the part of the program when I input something, afterwards it jumps back from vuln to main
ooo okay... using gdb, I got up to the part when I’m entering something into the buffer, I spammed a billion “A”s and it finally seg faulted, and I could see the memory address was 0x41414141
So 64 “A”s isnt enough, lets find out how many we need ...
70 not enough
Okay wait, 64+12 ‘A’s and it kind loops and asks for more input??
64+14 ‘A’s and we get a seg fault, it’s trying to go to 0x08004141
OK!, we’ve overwritten with 2 “A”’s
So how about 76 “A”s and the address?
Yes!
This level took forever but I got it
python -c “print(’A’ * 76 + ‘\x06\x85\x04\x08′)” | ./blind
This is almost exactly the same as jump...
COMP6841{Ooh_Youre_Good}Segmentation fault
Ooh You’re Good!
Done!
0 notes
Text
Week 08: Google Yourself
Downloaded a 1gb zip file, uncompressed to 2.23gbs. That’s what google is allowing me to see about my own data
Well first off
BrowserHistory.json is 1.45million lines long, that’s a lotta browser history
Reddit and youtube has 19999+ matches in this
Facebook has 12163 matches
My Youtube watch-history.html is 16kb big wow
Location History.json has 4.75million lines (its a 100mb json file), they know everything...
“Confidence”
“IN_ROAD_VEHICLE”, “IN_RAIL_VEHICLE”, “ON_BICYCLE”, “ON_FOOT”
Timestamps, latitude, longitude, activity,
Oh man
Purchases_Reservations
What... it’s saved every online purchase I’ve made into json files
The amount of data that is saved about me, is staggering and scary. Maybe it’s time to move to duckduckgo
0 notes
Text
Week 08: Spot The Fake
The Shed at Dulwich Hill
haha I ended up watching the entire video... it was actually really good
To detect against this kind trickery, I guess the best thing would be for trip advisor to hire staff who’s sole job is to go to business’s, have a chat with the owner, verify that the business exists in the first place
Also... 7 months just declining people and hyping up a restaurant... that’s insane commitment
Also... idk if I’d be comfortable being blindfolded and lead down an alleyway, I guess the host is quite charismatic
Tbh I wouldn’t mind trying “The Shed”
Banksy Fake Currency
idk, seems like fraud to me
Deep Fakes
Ohh deep fakes are so cool, corridor crew has done a few videos on this with Tom Cruise/Keanu Reeves
Activity
I may as well just do The Shed at Dulwich Hill
So the guy spent over 7 months slowly hyping up this fake restaurant on trip advisor
Fake reviews, rejecting bookings
Eventually he let allowed some customers to dine, but he hired a bunch of actors + staff to sell the fake
0 notes
Text
Week 08: Something Awesome Leviathan Game Level 3 - 7
Level 3 -> 4
Running ltrace ./level3 I see this:
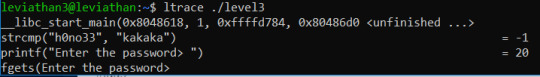
Immediately I try both hono33 and kakaka, until I realised that strcmp was useless! It was a ruse!
It’s the second strcmp that matters
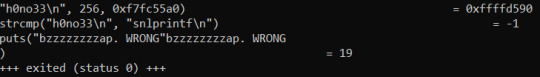
The second strcmp is comparing our input to “snlprintf”
Therefore that’s the password!
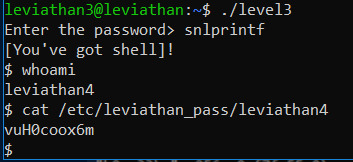
It gave us a shell and running whoami says its leviathan4!
Note that if you run ltrace ./level3 it’ll spit out a leviathan3 shell
So just do ./level3 and you’ll get the leviathan4 shell
Level 4 -> 5
ls -a reveals a hidden folder .trash

Inside .trash was a bin program
Running ./bin spat out some binary
01010100 01101001 01110100 01101000 00110100 01100011 01101111 01101011 01100101 01101001 00001010
I googled a binary to ASCII converter online and got the password out
Level 5 -> 6
Running ./leviathan5 gives
“Cannot find /tmp/file.log”
ltrace ./leviathan5 gives fopen(”tmp/file.log”, “r”)
But it’s doing a puts(”cannot find the file”) ... which means its a fake msg!
No... it doesn’t exist
I tried making a /tmp/file.log file but nothings changed
Oh wait, if I try making the file and running ltrace ./leviathan5 I get
fopen("/tmp/file.log", "r") = 0x804b008 fgetc(0x804b008) = '\377' feof(0x804b008) = 1 fclose(0x804b008) = 0 getuid() = 12005 setuid(12005) = 0 unlink("/tmp/file.log") = 0
Looks like its reading from the file, and then deleting the file?
I tried touch /tmp/file.log
Followed by echo “TEST” >> /tmp/file.log
And then ltrace ./leviathan5
Yep, looks like its reading from the file and printing it out
So how about we make a symbolic link between /tmp/file.log and leviathanpass6?
Yep!
ln -s /etc/leviathan_pass/leviathan6 /tmp/file.log
./leviathan5
Gives out the password
Level 6 -> 7
Running ./leviathan6 it says its needs a 4 digit passcode
Running ltrace on it, its doing atoi? and prints out “wrong”
Looking back on this level, I was a bit confused
The game description said that you didn’t need any programming abilities so I assumed you weren’t supposed to brute force the passcode
So I spent hours trying to figure out the trick, maybe the passcode was hidden somewhere?
In the end I peeked at a tutorial, the moment I saw that they were running a script to brute force it... oh man
So I wrote my own bash script that brute forces the 4 digit passcode
And found the passcode to be 7123
At first I tried the range 0 .. 5000 but it kept spitting out error messages like fork ... memory temporary unavailable for something like that
I was worried I was slowing down the server for everyone so I ended up testing small ranges of 1000 at a time
Eventually 7000..8000 range worked for me
Also I kinda forgot bash scripting so I had to google things like bash script for loops, if statements, save output into variable etc...

0 notes
Text
Week 08: Something Awesome Leviathan Game Level 0 - 3
I had difficulty with the first three levels, and looked at walkthroughs.
Level 0 - 1
When I logged in, the folder was empty
So I googled where are the files for leviathan level 0 thinking it was a bug, kinda like the bugs in the bandit game
I saw a guide that said to do ls -a to find the hidden folder, didn’t think of that :/
So I did ls -a revealing a folder called .backup
Inside the folder was a html bookmark?
Full of text, I just used grep to filter for the password
cat bookmarks.html | grep “password”, got the password!
Level 1 - 2
Inside leviathan1, there’s a program called check
It asks for input, checks a “password”
There’s no hints... how do I get the password
I started off by trying out strings to check all the ASCII I got scavenge
I tried them all, no luck
I then spent a long time in gdb, trying to print out variables and see what the strcmp was comparing against
Eventually I looked up a hint..., they said to use ltrace
So I tried ltrace ./check
And there it was! It showed the strcmp and the password
I knew that from gdb there were 3 getchar calls before strcmp, so it had to have been a 3 letter word
whoami gives leviathan2, so I can cat the password out now
Level 2 - 3
This one was hard, I couldn’t get it and I’m still mulling over it now
I ended up looking at a tutorial for this level
You had to make a new directory in tmp
And name a folder inside that directory something like ‘asd; bash -p’
Then run ./printfile ‘asd; bash -p’
Because printfile didn’t check the end of the filename, it ends up running the appended command, opening a bash shell with elevated privileges,
Confusing...
Looking back, I regret peeking at tutorials for the first 2 levels, however this third level was just tricky
0 notes
Text
Week 07: Tutorial Reflection
We started off by going through some of the mid semester answers again. Then we covered Diffie Hellman Key exchange and a bit on certificates. We went through the various types of block ciphers.
ECB - Electronic Code Book
Break a message into blocks
Encipher each block seperately
Patterns persist - which is a problem
CBC - Cipher Block Chaining
Use the previous ciphertext XOR with the block -> put it through the block cipher encryption
Can’t decrypt the second without the first
Makes it more random
Very slow I think?
CTR - Counter Mode
Stream cipher
We went through Caff’s Buffer Overflow Questions!
I had no worries with 1.0 basic
It took me a while to figure out 1.1 whereamI, but that is only because I compiled with gcc instead of using the prescribed make file
Still strugging with 1.2 Blind
Finally we started the case study, which was a debate on whether or not we should have more or less surveillence. We were split into two groups and we had to debate with each other. I was on the side of less surveillence. I remember listening to somebody a long time ago (who did a lot of debating), who said that when you debate, regardless of what your personal beliefs are, when you fight for your side, you begin to believe it, even for just the duration of the debate.
I didn’t really take down notes for this part, as I was too engrossed in listening to the debate. Some of the points below I took down during the debate, others I took from the email sent by Max.
AGAINST
If we collect data now, how do we know what the future holds and how the data will be used in the future? Can we trust the people who hold this data?
Rwanda example
Census on everybodies race, it’s okay, countries relaxed
A couple of years later, that census was used to perform mass genocide
Insider attacks stealing the data
Employees abusing the data to stalk people
Data sold for money?
FOR
Help improve safety/ prevent crimes
Stop terrorist attacks
Perform better background checks
There was a point made from the FOR side which was something along the lines of we’ll get world peace. Dunno if it was serious but it got me thinking. World peace through mass surveillence sounds like a totalitarian state akin to 1984. I’d be terrified to live in one of those countries.
Personally though, obviously there’s no right answer here. I would lean slightly towards having more surveillence. But this kind of surveillence is guaranteed to draw bad people in who will abuse it for their own purposes.
0 notes
Text
Week 07: Something Awesome Krypton Game Level 5 -> 6
Okay, this is a long one as well
So we’re given a password, encoded with a vignere cipher. We’re also given two more “discovered”, encoded messages (which are a lot longer)
We’re not given the length of the key
So the game plan is to:
Find the length of the key using the index of coincidence
Given the key length, use frequency analysis to find the key
I wrote some python which finds the index of coincidence for key lengths between 2 and 10
Take a key length of two for example
found1 = "SXULWGNXIOWRZJGOFLCMRHEFZALGS.....
ABABABABAB......
We form two new strings, one that looks like
SUWNI... (All these letters were shifted by the key “A”)
XLWGX... (All these letters were shifted by the key “B”)
Now for these two strings, we count the number of times each letter appears (inside of a python dictionary)
Now we iterate through this dictionary, with this formula (Index of Coincidence formula)
total = total + (val*(val - 1)) / (sum1*(sum1-1))
here total ends up being our index of coincidence
val is the variable that represents the number of times (A, B, C etc..) appears in the string
sum1 represents the total number of letters counted
And we do this for each string we have (and add them all up), in this case 2, and we divide it by 2 to get the average Index of Coincidence which happens to be 0.0419...
Now we think, what if the key length was 3?
found1 = "SXULWGNXIOWRZJGOFLCMRHEFZALGS.....
ABCABCABC...
So we split the string into 3 new strings, one that looks like
SLN...
XWX...
UGI...
And we do the same thing as before, all the way up to an arbitary number
Because this is a CTF game, the keylength can’t be ridiculously long, so I’ve chosen to check up to length 10
Eventually we get these results:
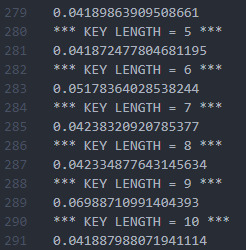
Now the index of coincidence for plain english text is approximately 0.0667
Source: https://www.dcode.fr/index-coincidence
So, this closest number here is key length 9
Therefore, we can make a safe assumption that our key length is 9
Knowing this, we do frequency analysis again
We collect all letters in position 1, 10 etc... because they were all shifted by the same letter (The first letter of our vignere cipher key)
We collect all letters in position 2, 11 etc...
In the end we have 9 strings
We perform frequency analysis, by counting the number of appearances of each letter in the string, and divide it by the total count
From there, you would shift the letters until they matched the frequency that which you would find in plaintext english
Now I found a website that does the same thing as what I’m doing, but they have a nice bar graph to help us when we are trying to align the two frequency charts, as well as a smooth animation (you just click on shift left/shift right), instead of having a text editor open, and spamming space bar and having to move whatever part of the alphabet has spilled over the edge back onto the front)
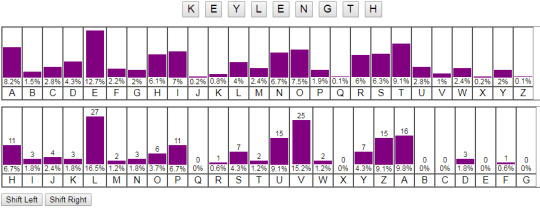
Source: http://www.brianveitch.com/maze-runner/frequency-analysis-vigenere/index.html
So the key was KEYLENGTH, and the password was RANDOM!
Now I decided not to do the next level, because I decided that the amount of time it would take to solve that level (the last level in the krypton game), I could probably do quite a bit of another game!
This’ll probably be one of the levels I’ll demo in my presentation in week 08
0 notes
Text
Week 07: Something Awesome Pwnable.kr Level 1
pwnable.kr fd level
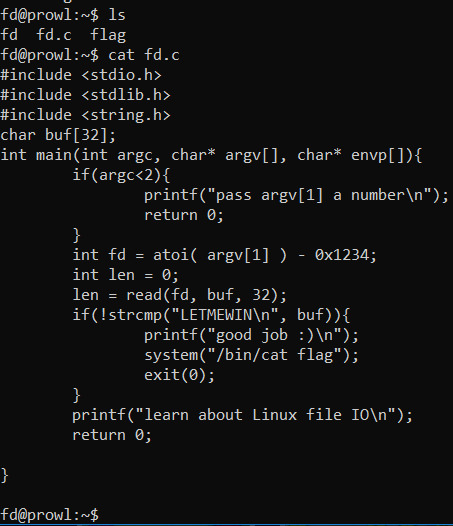
Here is a snippet of the code
So working backwards, you can see that strcmp is comparing “LETMEWIN” to a char array called buf
strcmp returns 0 if true, the ! reverses that into a 1 which is true in an if statement, which would allow us to see what is in the flag file
So we need buf to contain the string “LETMEWIN”
Working upwards, len = read(fd, buf, 32)
In this, len doesn’t matter too much, what matters is that read is a c function that reads 32 bytes from the file descriptor “fd” into the buffer “buf”
Looking up further, we can see that fd is set in this line;
int fd = atoi( argv[1] ) - 0x1234;
It took me a while, but I realised that a file descriptor = 0, is standard input
1 is standard ouput and 2 is standard error
So, if we can set the variable to be 0, the program will read from standard input and put the contents into the array buf
Now atoi just converts string to int, it’s very commonplace when reading int input from arg
Converting 0x1234 to decimals we get 4660
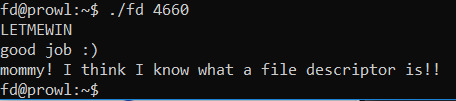
So... here’s what we do
We run ./fd 4660
int fd = atoi (argv[1]) - 0x1234
Will become int fd = atoi (4660) - 0x1234
Which will be fd = 4660 - 4660 = 0
So fd is set to 0
Now we can type in LETMEWIN, which will be read by the c function (read), into the array buf
The strcmp will return true, the if statement returns true, and we get the sytem call system(”/bin/cat flag”) which shows us our flag
“mommy! I think I know what a file descriptor is!!”
Yikes
0 notes
Text
Week 07: Lecture Reflection
We started off the morning lecture by going over some of the mid sem questions. I’m pretty sure I chose integrity for the question where they ask if you were the commander of an army and only the president knows the 10 digit nuclear launch code, what would you be worried about? I get that it’s Type 1 / Type 2 error in retrospect, at the time I was just thinking like what if the message was tampered with or something. The other question we covered, Q10 had no right solution! Full marks for everyone!
We covered Proof of liveness quickly - proof that there is somebody behind the message. Followed by going over Diffie Hellman again. I remember we went through this in an earlier lecture. Diffie Hellman is to set up a shared key.
So Allison and Bob both agree on a base and a modulus and they both pick their own secret. They each calculate base^(their own secret) mod modulus and they send that to each other. Then they get the other persons message and do secret = (other persons message)^(their own secret) mod modulus. In the end they both get the same shared secret. The diffie hellman exchange relies on the discrete log problem, where it is really hard to reverse the calculation base^(their own secret) ,mod modulus.
https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange
We covered some definitions
(From the lecture slides)
Vulnerability - a potential weakness in something
Exploit - attack a vulnerability
Software bug - vulnerability in software
Stack and the Heap
Stack - First In First Out
When functions are called, their temporary information is stored on the stack
Heap - when space is known at compile time - store on heap
Malloc -> put data on heap
We covered types of software bugs
Memory corruption - attacker changes the memory, attack can control what the program does
Format String Attack
C uses printf, 1st argument is format string telling it what to do with the remaining arguments, but if it’s not a control variable, it just prints it out
printf(”Richard %s”) works fine, since there is no next argument in the function call, printf will just look lower into the stack and print it out
Doing printf(”%x%x%x%x”); will just dump out the stack (cool!)
Printf(%n) can write to the stack -> wow
Integer Overflow
Integers have fixed amount of space
If you know there’s a counter in memory, type in a big enough password so the counter wraps around
Let’s it pass some test or trick it in some way
We also covered shell code
Old hackers would try to make a remote shell pop up w/ privileges
We covered the national vulnerabiltity database, if you found a new vulnerability, it was numbered and added to the list. Plus we went through some cool bug exercises, we were shown c code and we had to find the flaw. After that we started covering assets, security is there to protect your assets, but sometimes we protect the wrong assets. We need to first brainstorm, what is it we are trying to protect? Ask a lot of people, from different backgrounds on what they think need protecting, and do this every month or so.
In the evening lecture, the bug bounty group presented. Then we started talking about authentication on the internet, how do we know we are trying to access the correct website? We looked at PKI
PKI
Public Key Infrastructure
A “passport” that links your public key with a domain name
Certified by “trusted” companies
Web browser will authenticate the certificate to make sure you’re accessing the right website
0 notes
Text
Week 07: Security Everywhere 05
Another headline, posted yesterday: NSA contractor sentenced to prison for huge theft of classified U.S Data. I’m surprised he only got 9 years for it. I thought that insiders got life in those supermax prisons.
Ah, they could never prove that he sold that data to anyone.
“He pleaded guilty to “willful retention of national defense information”. Martin is being accused of stealing from the NSA, CIA, U.S Cyber Command starting from 1996. When his home was raided they found stacks of documents and harddrives worth 50 terabytes of data.” - From the link below
From a glance, I think he wanted to sell the secrets out, but either he was too scared or he hid it really well and nobody could prove it. I guess this is just another example of an insider attack. Like always, humans will always be the weakest link in security.
Newsarticle Source: https://www.reuters.com/article/us-usa-cyber/nsa-contractor-sentenced-to-prison-for-huge-theft-of-classified-us-data-idUSKCN1UE2NV
0 notes
Text
Week 07: Security Everywhere 04
“Russian Secret Intelligence Agency Hacked”
Ouch, this wasn’t my “Bold Prediction” (That was a valve hack), but still wow.
Hackers targeted FSB (Federal Security Service) and stole 7.5 terabytes of data, exposing FSB secret projects:
de-anonymize tor browsing
scrape social media & split off russian internet from rest of the world (russian intranet??)
Mmm supposedly nothing of importance was leaked (these projects were known already), but it was the fact that they were compromised to begin with which was newsworthy.
Newsarticle Source: https://www.forbes.com/sites/zakdoffman/2019/07/20/russian-intelligence-has-been-hacked-with-social-media-and-tor-projects-exposed/#57d83f636b11
0 notes
Text
Week 07: Instagram Oopsie

I took this screenshot a few weeks ago, forgot to post it. My instagram account was compromised, shame lol. I changed the password to a stronger one, (one that I haven’t used before).
I tried using haveibeenpwned.com with a couple of my email addresses and:
Main Email Address:
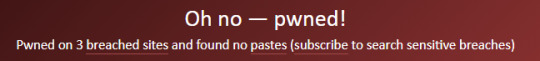
2844 Seperate Data Breaches? (80 million records)
Collection #1 (2.7 billion records)
MPGH (Don’t judge lol)
Secondary Email Address:

Adobe
Town of Salem
CrackingForum
Edmodo
MPGH
MyFitnessPal
Just to name a few were all compromised and my details were leaked
Very old email address I only use because I have some old accounts that still use this email:

Not looking good for me, luckily I’ve changed the passwords to all my important accounts already, to stronger ones (quite a while ago)
0 notes