#ModuleActivity
Explore tagged Tumblr posts
Text
Week 08: Google Yourself
Downloaded a 1gb zip file, uncompressed to 2.23gbs. That’s what google is allowing me to see about my own data
Well first off
BrowserHistory.json is 1.45million lines long, that’s a lotta browser history
Reddit and youtube has 19999+ matches in this
Facebook has 12163 matches
My Youtube watch-history.html is 16kb big wow
Location History.json has 4.75million lines (its a 100mb json file), they know everything...
“Confidence”
“IN_ROAD_VEHICLE”, “IN_RAIL_VEHICLE”, “ON_BICYCLE”, “ON_FOOT”
Timestamps, latitude, longitude, activity,
Oh man
Purchases_Reservations
What... it’s saved every online purchase I’ve made into json files
The amount of data that is saved about me, is staggering and scary. Maybe it’s time to move to duckduckgo
0 notes
Text
Week 08: Spot The Fake
The Shed at Dulwich Hill
haha I ended up watching the entire video... it was actually really good
To detect against this kind trickery, I guess the best thing would be for trip advisor to hire staff who’s sole job is to go to business’s, have a chat with the owner, verify that the business exists in the first place
Also... 7 months just declining people and hyping up a restaurant... that’s insane commitment
Also... idk if I’d be comfortable being blindfolded and lead down an alleyway, I guess the host is quite charismatic
Tbh I wouldn’t mind trying “The Shed”
Banksy Fake Currency
idk, seems like fraud to me
Deep Fakes
Ohh deep fakes are so cool, corridor crew has done a few videos on this with Tom Cruise/Keanu Reeves
Activity
I may as well just do The Shed at Dulwich Hill
So the guy spent over 7 months slowly hyping up this fake restaurant on trip advisor
Fake reviews, rejecting bookings
Eventually he let allowed some customers to dine, but he hired a bunch of actors + staff to sell the fake
0 notes
Text
Week 07: Email Phising CTF Part 02

Yikes, FLAG: COMP6441{MakeSureYouSetUpTwoFactorAuthToPreventThis!!}
0 notes
Text
Week 07: Email Phising CTF Part 01
Ooo an interactive social enginerering CTF?!
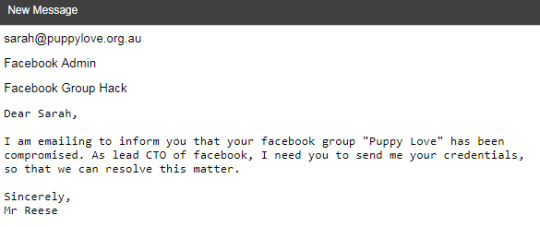
So we need to obtain the facebook login details for the Puppy Love facebook page and organise payment of $1200 to be made to my fake account from the Puppy Love accounts team.
I’m a bit confused on how this is gonna work though...
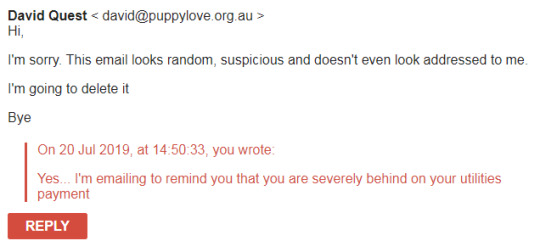
Oops, let’s try again.
Maybe this is better?

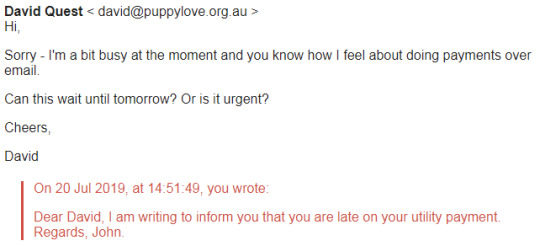
I know it’s a bot but still, lets have some fun!

Okay, it sent me the same email back, I think I need to include the word “urgent” in the email?
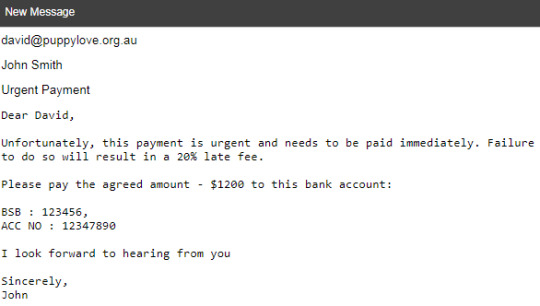
Cool!, got the payment:

FLAG: COMP6441{paymentfraudisreal!}
0 notes
Text
Week 05: Hash Question
I was confused about how to do the week 04 hash activity until Richard explained length extension attacks in this weeks lecture. So I went back and gave it another attempt, and I think I’ve got it.
So after hashing, “PAYBOB100″ and the key, we got 481
We can just add on another 0 at the end of the hash, to get “PAYBOB1000″ without having to figure out what the key is, because it’s already embedded into 481.
So:
481 + 405 = 886 (Add the code for “0″ to the hash)
886 x 521 = 461606
461606 mod 10000 = 1606
1606 + 450 = 2056
2056 mod 967 = 122
So the verify code for “PAYBOB1000″ is 122 !
0 notes
Text
Week 05: Dropping the Bomb
Nuclear Weapons Storage Facilities
Minutemen-III operated and controlled by old 1980′s tech
8 inch floppy disks, low KB/MB of storage/ram, slow processors
Upsides is no WIFI/ Bluetooth, lowered chance of being compromised but like any system, not 100% safe
Podcast Analysis Question - For the US Government, what were the most important assets that required protecting?
The Titan II Missile itself
Oxidizer and Fuel were both very volatile
Toxic to humans
“Bomb on top of a bomb”
Mental/Physical health of workers
Can’t get them to slack off
Protect the workers from harm
Overworked, too tired - can make mistakes
Too young - took risks
Didn’t use torque wrench, broke protocols
They should have more workers, less shifts per worker
Access into the facility
From external threats
Insider attacks
Missile Command Center
Have to protect the only way to control/ monitor the missiles
What would you do differently?
Perform regular maintenance on the aging facility
There’s a gap between the missile and the platform?
Fix it ASAP
Hire more workers, less shifts for the workers so they’re not overworked and making poor decisions
Better communication between the command center and the workers so that the knowledge gap in the podcast scenario didn’t happen
Workers knew there was a hole in the missile vs Command center told there was smoke
Podcast Source: https://www.thisamericanlife.org/634/human-error-in-volatile-situations/act-one-1
0 notes
Text
Week 04: Magic Tricks
Penn & Teller - Jean-Pierre Parent
I assume the presenter is in on the trick and is playing along. Her body has to be contorted in some way, maybe the back of the board is bigger than it seems, and shes sort of kneeling into a cubby space, the shoes at the bottom are 100% fake.
0 notes
Text
Week 04: Hashs and MACs
Bit confused about this question
So for "PAYBOB100" has VERIFY CODE of 481 it’s like:
481 = hash( “key” | ”PAYBOB100″ ) ?
573 = hash( “key” | ”BILLBOB1000″ )
301 = hash( “key” | ”PAYROB1000″ )
I think we’re supposed to use a length extension attack?
So we need to find
VERIFYCODE = hash( “key” | “PAYBOB1000″ )
I’m not sure, I’ll have to get back to this later
0 notes
Text
Week 03: ATM Attacks and defenses
Attacks:
Card skimmers, I’ve seen videos of atm skimmers where there was an entire fake card reader/keypad, put ontop of the real one.
Little camera put above the keypad, not sure how it’s useful without the card itself though ‘
Defenses:
Tug at the card reader, sometimes the fake one will pop off
Cover the keypad with your hand when you enter the code in
0 notes
Text
Week 03: Examples of low probability high impact events
The week 01 case study on the deepwater horizon incident is a good example of a low probabilty high impact event, a lot had to go wrong, many failsafes failed for the accident to happen.
A rocket launch failing somehow, even though billions of dollars were pumped in, rooms filled with the smartest people, accidents could still occur
Asteriods crashing onto earth, solar flares frying satellites
0 notes
Text
Week 03: How to steal a penguin
During the day, on a public holiday so there will be a ton of people at the aquarium. Workers/guards will be working overtime, exhausted and annoyed. So we’d dress up as aquarium workers, and “act like we belong”.
There’s a bunch of youtube videos of people just acting like they belong, and gaining access to all sorts of places that they don’t belong. So we’d wear the proper worker outfit, and make our own fake id cards.
To get past security, just nod at them and pretend like you work there. We’ll remain undetected by hiding in plain sight. We’ll literally bring a little penguin portable enclosure, kinda like a dog cage but for a penguin. We’ll just let ourselves into the enclosure and put the penguin in the cage.
If anyone asks, we’re taking it away for mandatory health checkup or something. We could wear hats, sunglasses to cover our faces. Maybe we could walk out of the aquarium with the cage, no one would stop us because they assume we’re working.
0 notes
Text
Week 02: Type 1/ Type 2 Errors
In the lecture we covered 2 examples of type 1/type 2 errors
Airport security face scanning
Type 1 - It really was the right person but the system thought the picture didn’t match the face
Type 2 - It wasn’t the right person but security let them through
Disease testing
Type 1 - They didn’t have the disease but doctors thought they did
Type 2 - They did but doctors thought they didn’t
Others:
Alcohol breath testing?
Type 1 - They didn’t have any alcohol in their system but breathalyzer said they did
Type 2 - They did have alcohol in their systems but breathalyzer said they didn’t
Code testing
Type 1 - The code was written perfectly but failed the autotests
Type 2 - The code had bugs but passed all the autotests
0 notes
Text
Week 02 Dumpster Diving Activity
His name is Adam S and he was in Melbourne at some point (myki card)
He once stayed at the nunnery accommodation in Melbourne
I’m going to assume that he once went on holiday to Melbourne, or maybe it was a business trip/ to a convention?
He is associated with Telstra and works/studies at UNSW?
He’s interested in hacking and also went to startcon, a convention for new companies and entrepreneurs
He loves eating fastfood, maccas/chargrill charlies and snacking
He likes to drink coke zero, and seems to buy a lot of bottled water
He wears contact lenses
He drives a car
His phone number is 0412345678 :)
His address is No Street St :)
He has an apple computer/laptop or maybe its the iPad Pro he bought
It was somebodies birthday, maybe his?
He has some old newspapers?
The analysis got progressively worse haha
0 notes
Text
Week 02 Shredding Activity
We have to rearrange the shredded document to reconstruct it.
The pictures of the faces is a great starting point to get some connected, I can see Trump and one other person
I’m also just focusing on one word at a time, so if i see like pres I know i’m looking for -ident to complete the word president
I found it!:
Trump Requests All Security Briefings Be Kept To 140 Characters Or Less
To safely dispose of a document I would just burn the document until they were ashes, and then dump the ashes into water, and pour it down the drain
0 notes
Text
Week 02 Warmup Crypto Challenge
COMP3441{""}
I can see 3 4 4 1 scattered throughout the text The number is always the 3rd of the block of text I can see the two { } and theres 3 "_" I got it, its one letter from each block of text so the first letter of each block makes THEFLA the second letter of each block makes GISCOM THEFLAGISCOM, yea thats it
TGPR GWTA DEKI HI3O YNOD ONAT ES4L OCII NTB} FC4L URSD THO_ LO1I RYAE EIU_ AM{N OPBA VNT_
Breaking it down like this makes it a lot easier to read for me, I can just read the letters downwards
THEFLA GISCOM P3441{ ROLLIN GYOURO WNCRYP TOISAB ADIDEA DONTEV ENTHIN KABOUT IT}___
The flag is COMP3441{Rolling your own crypto is a bad idea don't even think about it}___
Success!
0 notes
Text
Week 08: Buffer Overflow Challenges 1.2 Blind
I tried these in week 07 but struggled, this past week was hectic, especially since I presented on tuesday with the forensics group and on wednesday for my something awesome.
Okay... running ./blind I get “This is almost exactly the same as jump...”
The hint from my tutor was to use objdump, specifically objdump -h (headers)
Okay I get 25 different headers, how do I know which one is the function we want?
I googled gdb show all functions, and found the command info functions
This showed me that there was main function, win function and vuln function
I’m gonna assume that the vuln function gets called when I run ./blind, and I need it to run the win function
disass vuln shows me that its setting up a buffer, and calling gets
From info functions I can see that the win function starts at 0x08048506
But how big is the buffer?
python -c “print(’A’ * 64 + ‘\x06\x85\x04\x08′) | ./blind doesn’t seem to work
python -c “print(’A’ * 72 + ‘\x06\x85\x04\x08′) | ./blind seg faults but also prints out the same message a second time, so something must be happening
Been trying things like ltrace, strace, gdb but no luck so far
Googled some reverse engineering posts
Okay... by stepping through with gdb I can see that once it gets to the part of the program when I input something, afterwards it jumps back from vuln to main
ooo okay... using gdb, I got up to the part when I’m entering something into the buffer, I spammed a billion “A”s and it finally seg faulted, and I could see the memory address was 0x41414141
So 64 “A”s isnt enough, lets find out how many we need ...
70 not enough
Okay wait, 64+12 ‘A’s and it kind loops and asks for more input??
64+14 ‘A’s and we get a seg fault, it’s trying to go to 0x08004141
OK!, we’ve overwritten with 2 “A”’s
So how about 76 “A”s and the address?
Yes!
This level took forever but I got it
python -c “print(’A’ * 76 + ‘\x06\x85\x04\x08′)” | ./blind
This is almost exactly the same as jump...
COMP6841{Ooh_Youre_Good}Segmentation fault
Ooh You’re Good!
Done!
0 notes