Text
Job Application - Something Awesome Project.

If there was ONE thing that I wish I had more time to do, it would be this.
Lets get on with it.
So I have had three iterations for my proposal. My first one was not approved. After emailing my tutor for ideas, I made another proposal, which seemed ok. My third proposal was suggested by my tutor later on in the term, which was thankfully similar to my second proposal.
To quote my tutor:
If you wish to make a genuine go of it, I would recommend looking into the DVWA (Damn Vulnerable Web App) which will allow you to test some of the concepts. I reckon you could find a walk through tutorial for the DVWA and you could perhaps research and write up the OWASP top 10 vulnerabilities. This might bring you to a passable, face-saving territory. I would address it in blogging / and or on the project that you had left it to the last two weeks due to overload, but really poured your effort into it in the last few weeks, rather than trying to deceive the marker that you did work all along the semester.
So I have done so, and created a sort of tutorial-like sets of blogs for reference.
The OWASP Top 10 Vulnerabilities
Tutorial #1 - Intro and Installation
Tutorial #2 - Bute Force Attack & Kali on Windows
Tutorial #3 - COmmand Injection
I have already mentioned this in my time management section and made a blog post about it, but I’ll summarize it again: Considering the amount of work that was required, I thought it was rational to minimize the SAP work, since the “mark to work” ratio was simply too low (this section is only 8 marks). Instead I chose to maximize my work and time management done by focusing on all the other sections of my job application (as well as other uni work).
I believe my work done currently puts me in the “face-saving territory” which is hopefully a pass. I just hope that my tutor can see I have sacrificed this section to prioritize all the other sections of my job application.
Unfortunately, this part of my job application remains unfinished. However, in the tutorial, Adam hinted that he wanted us to continue working on it even after we submit our job application. (I should have gotten written proof of this...). So that is what I plan to do. I will update this blog if I manage to complete anything else.
1 note
·
View note
Text
Job Application - Skills
Security Ability
Now this has some overlap my my Analysis section of my Job Application, which is because I believe analysis is an important security skill. In particular, many of the Openlearning activities required use of my security ability, such as the:
Calculating bits of security
Preventing Barbara from doing her evil work by hacking her account
Running a length extension attack. I also made a small C program to help me.
Something Awesome Project
My Something Awesome Project allowed me to utilize a whole range of research and practical skills on the Damn Vulnerable Web Application (DVWA).
Some skills I acquired included:
Setting up an Apache Web Server and Kali Linus
Brute Forcing an application using Hydra
Very Simple Command Injection
Practical Skills
Throughout the course, I spent quite a bit of time solving cryptograms, including the ones showns in this blog and this one.
I also played a very security-featured game where you were a detective which was the same as an attacker trying to break into a house. I blogged about it here.
I also think that communication is a key skill, which I demonstrated by being considerably active online (on Tumblr and Openlearning), and by asking my Tutor for help when I needed it via email.
See my Community and Professionalism Section for more evidence.

I realize that a lightning talk or dumpster diving would have been an amazing skill to put here. But regretably, it is too late, and I have explained why here in this blog.
2 notes
·
View notes
Text
Job Application - Community and Professionalism
Contribution to course environment
I aided in creating material for the course/lecture textbook, and even blogged about it here
Blog
Link to textbook
Teamwork and Community
Now since there we're not too many opportunities to work in a team (except for maybe dumpster diving which I did not have time for), I instead actively participated by replying/blogging on Tumblr and commenting on Openlearning
Tumblr made it fairly easy to follow fellow students and to encourage others by liking and following their content. As shown, I think this shows my interaction with the tumblr community.
Tumblr Reblogs
Response to a post about Russian and the US election
Response to a post regarding emerging biometric technology
Tumblr Replies - I don’t know how to link to a reply, so I took a screenshot instead. I also dont know how to search my previous replies, there were two more...


Openlearning participation in activities
Shredding Excercise
Crown Jewels
Merkle Puzzles
Took the initiative to ask about the Something Awesome Project Proposal Guidelines
Communication and feedback
If there was anything that was addressed to me, I would always try to respond well.
I also exchanged several emails with my tutor (one I initiated, the other was him), which I think shows communication and some level of professionalism?


0 notes
Text
Job Application - Time Management
Weekly Work
Overall, I would try to consistently blog around 3-4 times a week. Now on some weeks, I was overwhelmed with work, so there may be slight delays on the time stamp. BUT what matters is that I eventually covered all the material I wanted to blog about, consisting of the following topics:
Tutorials:
Halifax
Houdini
Doors
Secret Labs
Self Driving Cars
Safer
Snoop
Ghost
Openlearning Activities
Calculating bits of security
Preventing Barbara from doing her evil work by hacking her account
Running a length extension attack
Shredding Excercise
Crown Jewels
Merkle Puzzles
I also found time to blog about other topics (from lectures or security everywhere), as well as reblog and read other peoples blogs, and post some random security news. A full list of my tumblr activity can be found here.
Planning/Work prioritization
Throughout the term I made several blogs planning what had to be done by when. (Unfortunately I did not blog when I had completed my work due to the fact that I thought it was redundant and contributed nothing).
A quick todo list in week 5
My planning after falling extremely behind: This one was a classic example of when things go wrong.
Job Application planning as the deadline drew near.
I knew early on that it would be impossible to complete everything that was required of me. Now looking at the job application, I saw that the mark distribution was quite even, and that the Something Awesome Project (SAP) was only 8 marks. Considering the amount of work that was required, my tutor suggested it was completely rational to minimize the SAP work, since the “mark to work” ratio is of low yield. I came to the same conclusion, and blogged about it in one of my plans.
Instead I chose to prioritize the other areas of this course, which also allowed me to focus on other courses. This did NOT mean I completely neglected my SAP, but rather just pushed it near the end. Unfortunately time management regarding this SAP could have been improved, (so Adam, please just penalize me in the SAP section, not this one). A genuine effort was still made, and can be seen in the Something Awesome Project section of this job application.
Mid-semester Exam
I think my mid-semester exam mark which was not 0 (above average too :D) demonstrates my ability to study and manage my time amid the stressful midsemester assessment period.
1 note
·
View note
Text
Job Application - Analytic
Reflection
After every tutorial and after every other lecture, I would make a detailed blog post regarding a certain topic covered. These are a few that demonstrate a high degree of analysis.
On power and control
On Protecting Australia
On Secret Labs
On Authenticating messages from ghosts
On secret handshakes and Houdini’s protocol
I would also blog about personal reflections on my word and my state of being in the course.
A quick reflection of my job application and why I regret not doing a lightning talk
An analysis of my plans
Application
This courses teaches you to analyze things by viewing the world through "security eyes". And so I kept an eye out around my environment and blogged about anything regarding security or vulnerabilities. Here are some examples of security everywhere
On Microsoft and their memory bugs in C and C+ code
On Huawei and their risk to US national security (via their backdoors)
About a video on the social network Nimses and their privacy invasion
About the benefits and risks of using a password manager
On a escape-room Android game
On Google’s response to leaked voice recordings from their Google home product
Analysis was required when completing the something awesome activities as well as the midsem (including past papers)
Calculating bits of security
Preventing Barbara from doing her evil work by hacking her account
Running a length extension attack
I was able to test and apply the knowledge I learnt in my Something Awesome project where I ran a variety of attacks on the DVWA.
please refer to it here
Research
Sometimes the topics covered in lectures were confusing, and so I would conduct some extra research and blog about it here
On Hash Functions
On TOTP
On Cipher Block Modes
On Buffer Overflows
A large amount of research was also conducted for my Something Awesome Project
Please refer to it here
0 notes
Text
Makes you wonder, is there really a purpose to voting if the outcome is already set? And if so, do the identity of the voters matter anymore? Like in the case of the Russian hackers, they may have rigged the election regardless of who voted for who. If that is the case, then what use is security of the paper ballets if the president has already been chosen? Although I suppose that they could target anyone who didn’t vote for their prefered president (or whosever viewpoints did not align), but that that point in time, the whole country is screwed..
So it probably is important to protect the country first and foremost before any outside country can interfere. Because if another country has any part to play, then the line between whos country is whos becomes very blurred. In something like elections, it just shows that perhaps the US security systems is inadequate.
Security Everywhere 8
I read an article today about Russian hackers targeting election systems in the US. Turns out that all 50 states were actually hacked by hackers linked to the Russian Government and that they were in the position to tamper with them. There is currently to evidence in whether or not they did tamper with it though, which demonstrates the huge security threat it poses.
I found this quite interesting, as elections are actually a huge issue, which can affect the whole political climate of a country, especially in a country such as the US. The Russian hackers being able to hack it and have the ability to tamper votes without leaving any evidence behind is quite scary, as it means that it is hard to detect if anything changed. At the minimum, they would’ve obtained all the data from the voters and probably the info inside the databases. This is the reason why voting is still mostly done in paper on ballots, as there is not secure enough security to prevent these kind of problems currently.
1 note
·
View note
Text
job application
i swear i have too much evidence but not enough claims
0 notes
Text
TOTP
A TOTP is a time-based one-time password generated by an algorithm that takes in the current time as the unique, distintinguishing factor. It is an extension of the HOTP (HMAC-based one-time password) algorithm, which also provides a method of authentication, but does not expire after a certain time interval like TOTP. TOTPs are often used with 2FA systems.
To create a password, the a user TOTP takes in the current unix time and hashes it with a shared secret. This is to locally generated TOTP value. Meanwhile the server does the same thing to generate the authenticator TOTP value. If the authenticator matches the generated value, then the password is valid.

Barbara works for Evil Crop. Most of her evil work is done via email - logging into her Gmail account. In an attempt to increase her security she has used [TOTP]. She uses 2-step verification for her email account using Google Authenticator, and she signs up with new websites by using 'Sign in With Google', and for when she is at a computer she doesn't trust, she has generated a set of 10 one-use only passwords for her Gmail account.
Come up with attacks against Barbara using the technologies above that would compromise her account. Describe it in a comment below. Include explanations of the technology where necessary.
Now TOTPs are not without their weaknesses. Some of them are (cred. wikipedia):
Still susceptible to phishing, but more difficult since attackers need to work on real time
Still susceptible to brute force
Still relies on a shared secret (which can be stolen)
TOTP are valid for longer than the amount of time they show to accound for the server and local clocks not being perfectly synchronised and latency in networks.
0 notes
Text
quick reflection
So my job application is almost due, and as I wrote it, I had a couple of more thoughts that I would like to blog about in this post.
At the beginning of the term, Adam (my tutor) was fairly passionate about trying to get everyone to do a lightning talk. However, not that many people took up that challenge. Sadly, I was one of those people, and now that I am in the middle of writing my job application, I low-key regret not doing one. Now that I am almost at the end, I can see how a lightning presentation could address so many sections of my job application. It fits into the skills, analytics, AND the professionalism section, which I think would have spiced up my application by a lot.
Why did I not do one? Well the reasons were mainly because (a) I thought I had no time to prepare one since I was busy with other things, (b) it was optional and so I thought it would contribute nothing in the end, and (c) noone else did one. But man, was I wrong on (b).
The only other thing I wish I had done better was my Something Awesome Project (SAP). Throughout the term, I really had no clear direction or goal. The ones I set myself could have been too difficult or too easy, and yet I still struggled to bring myself to do it. Since my project was so self directed, I could neither see my goal nor my path, and so I had to reach out to Adam. Even then, I was not sure of the difficulty of his suggestion, and so it became slightly stagnant... And since these past few weeks have been hectic, I hope to actually complete my SAP properly after I submit everything else. Yes the deadline was last thuesday, but Adam said that he would let us continue working until we present it (otherwise, we’d be doing nothing)
Anyway that’s it for now.
0 notes
Text
im contributing
So even though I didn’t actually go to the lecture where I was supposed to take notes, I still went back to the week 5 notes and watched the ABYSMAL echo 360 recording (dont check out the sound quality here, you’ll suffer like me) so I could do my part as a diligent and dedicated student :)
So a lot of the content that Richard covered was already there. BUT there were also quite a lot of mistakes and badly phrased sentences. I don’t know how I’m supposed to prove this, but I went through the whole document fixing the presentation and fixed some things that didn’t quite make sense. I suppose if you go through the document, you’ll see everything is nicely formatted with consistent layoutsUnfortunately this also made me realise that there were things I didn’t quite understand so I had to do a bit on research on things like the Merkle Damgard contruction.
0 notes
Text
With regards to your “emerging” biometric identification technologies, a quite a lot of them aren’t practical or as secure as one would think. Let me address some possible weaknesses for each:
Voice recognition: It’s not safe against (fabricated) recordings of your voice. Also not very private or secure physically - what if someone close by hears you say your password?
Ear recognition: Makeup artists and their fancy moulds
Typing: this is an interesting one, but are there really enough nuances in someone’s typing to distinguish between people? And I think’s its too much of a hassle to type out a letter everytime you want to unlock something.
Gait: This is probably the most secure, save for some really skilled actors that can mimic everything?
I suppose this is why we don’t hear of these forms of biometrics as much as the others.
Current State of Biometrics
We already know the issues we face with passwords and other single-factor authentication protocols. They are often ‘weak’, reused and can be easily forgotten given the number of passwords some people have to remember. This is where the idea of biometrics comes in - it aims to alleviate these concerns by mapping the concept of authentication to physical aspects of our bodies. The question is how good are biometrics right now and where are they vulnerable?

I want to go over the main types that are in use today which are:
Iris / retina scanning - uses unique patterns in the iris or vein patterns in the retina
Facial recognition - extract features of the face (i.e. distance between eyes) and match against a database
Fingerprint scanning - identification via the ridges and valleys on your fingers
Finger dimensions & palm veins - not as common as fingerprints but beginning to gain popularity
DNA - copying and splitting of genetic markers in our genes (very accurate)
There are some other interesting emerging ones too:
Voice recognition - can recognise an individual in as few as 100 datapoints in your speech
Ear recognition - shape of human ear is unique to every individual; remains pretty much the same from birth to death
Typing - identification of individuals through habits of using a keyboard (i.e. rhythm & key pressure)
Gait - mainly used in analysing athletes at present, but could be expanded to identify individuals (unique ways in which joints move)
All these methods of identifying individuals via biometrics are ‘good and well’, however we have one main issue with them all. In order for an organisation to use these as authentication, these elements need to be converted into data and stored. If the data was compromised then you have permanently lost your biometric authentication (for that aspect) - there are only so many physical aspects you can use for biometrics, where as you aren’t limited in password choice. There have already been proven methods today to forge facial recognition, fingerprints and iris scans from this data. Honestly, I don’t think biometrics alone can provide great security at this stage - although, I think as part of a multi-factor authentication, they definitely add to the overall security. (it’s just another pain in the ‘butt’ for an attacker)
The other big issue with systems implementing biometrics is the ‘type I / type II error tradeoff’. Being able to recognise the physical features in sufficient detail such that it recognises the individual most of the time, without leading to a significant increase in false positives, is difficult. I’m pretty sure Richard already mentioned in the lectures the example of going through the airport - the systems are tilted towards approving identities, otherwise we would have huge queues and lots of manual intervention required.
TransportNSW - Facial Recognition Replace Opal Cards? (article)
The transport minister, Andrew Constance, basically discussed the idea of using facial recognition in the not-too-distant future instead of Opal Cards. Now I don’t actually see any issues regarding forging authentication in this case - since the costs are so minimal for a single transaction, it wouldn’t be worth the effort for an attacker to try and forge it. My problem revolves around the fact I don’t think our facial recognition technology is good enough to do this yet; we can barely recognise people with lined up passport photos at the airport.
My other major concern relates to privacy - the government will be investing billions of dollars if they were to try and develop this system, so who says that would just limit it to transport? I think they would try and expand the system to law enforcement and every other area of government, if they manage to get the authentication working well. Remember a lot of image recognition systems rely on being able to ‘train against data’; if millions of people are using the systems every day then you can collect a lot of data in a short period of time. They would be able to get so good at recognising your face in every shade of light and every angle; to the point where they could use this on every camera in their control. This is the point we become a ‘surveillance state’.
China - Facial Recognition (article)
Some of the things China has been doing with regards to facial recognition are definitely starting to feel like an Orwellian dystopia. According to the article, here are the main things they’ve been doing in 2018:
Police facial recognition glasses - almost like ‘Google Glass’, they can be used to identify individuals and flag criminals
Drones in class - used to scan student’s faces to track attendance and how closely they followed lectures
“Smart” uniforms - microchipped school uniforms to give location and link up with on-school facial recognition
AI news anchors - used to ‘effectively replace’ an anchor when breaking news needs to be broadcast
Facial recognition near rivers - recognition used to detect children near river to give them warnings and alert parents
Checking up on animals - facial recognition to identify pigs and track well-being
San Francisco Biometric Ban (article)
The ban was essentially enacted due to people being concerned about violation of their privacy and civil rights - it prevents “the use of facial recognition software by the police and other agencies”. A number of organisations have spoken out against the ban citing the numerous benefits of biometrics in identification - missing children, fraudulent documents and identity theft. Honestly I think this ban is a bit silly; I think a more balanced approach (i.e. restriction to where surveillance can occur) would be more appropriate.
6 notes
·
View notes
Text
Random question
The bank has invented a new way of turning a message into a number - called a CDC code, and uses this as part of a procress to verify messages with so called VERIFY codes. The bank authenticates and protects the integrity of its messages by computing a VERIFY CODE which is the CDC code of {password,message} I.E. The CDC code of a secret password with the message appended to then end of it. The Bank sends the resultant VERIFY CODE along with the message (but does not send the password of course!) All messages each day use the same password. Below is how a CDC code is computed: Start with the first character of the message, convert it into a code using the following table (only some values shown) {{{ A->23
B->47
I->397
L->507
O->581
P->635
R->687
U->763
Y->901
0->405
1->73
}}} Then multiply this by 521, mod it by 10,000, add 450, mod it by 967, then add in the code for the next character, and repeat... For example the CDC code for the message "AU" is 216. Working: {{{ 'A' 23x521 = 11983
mod 10,000 = 1983
+450 = 2433
mod 967 = 499
+763 'U' = 1262
x521 = 657502
mod 10,000 = 7502
+450 = 7952
mod 967 = 216
}}} You have intercepted the following messages and VERIFY CODES: {{{ "PAYBOB100" has VERIFY CODE of 481
"BILLBOB1000" has VERIFY CODE of 573
"PAYROB1000" has VERIFY CODE of 301
}}} What is the VERIFY code for "PAYBOB1000" ? (enter digits only in your answer) Notice this question is asking for the VERIFY code not the CDC code.
Initially I thought that you had to find the password, or the CDC of the password by working backwards from the verify code. So I made a program that tried to find this password by calculating the CDC of the messages first and then comparing it to the VERIFY CODE.

But after runnning the above, it resulted in a CDC of 809 for PAYBOB100:
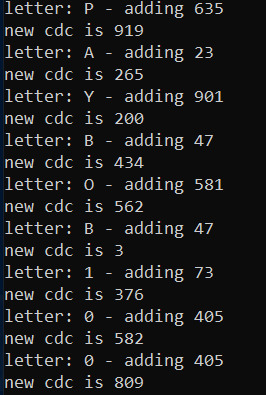
Similarly for the message BILLBOB1000, the verify code was 460. I quickly realized that this led nowhere as the CDC code I found had almost no correlation with the given VERIFY CODE.
But then I realized that this was an exam question, and that they probably would’t have time to do all this coding. So the only other possible method was to use a length extension attack since PAYBOB1000 is the same as PAYBOB100 with an additional 0. So all we had to do was to take the VERIFY CODE from PAYBOB100 and then calculate the new CDC using the method provided. So all I had to change from my previous code was the initial starting CDC (which was the given VERIFY CODE) and the letter we appended.

And the final VERIFY CODE was 122!
0 notes
Text
security and authentication
The idea of authentication has been around for centuries. Originally, authentication was used to spot fakes ranging from counterfeit products to currency to paintings.
Today, the list of things that can be faked has only increased. A small list of common things that people fake is:
money (duh)
jewellery
news
emails
pictures and videos
conspiracies
quotes
technology (im looking at you china)
id (or online accounts)
love (lol)
A subset of faked objects are edited objects . Now these are often more subtle and like counterfeits, are hard to spot. Depending on the case, it may be akin to someone tampering with evidence. I’m just thinking of the case where security footage is edited to remove a hacker’s face...
So how can we check an object’s authenticity? How do we know if something is a counterfeit? How can we know if an original has been tampered with? Unfortunately these things depend on the object. There is no universal answer to these questions.
Some of these things boil down to experience. For some other, there is software that can help identify whether or not something is edited like this tool. Identity can be checked by using biometrics. However, nothing is failsafe unfortunately.
0 notes
Text
the duck is doomed
This week has not been fun at all. I realise that the job application is due in a week, and there are a million things I still want to include in the application. So far, the only thing I am on top of for this course is the tutorial blogs. I regret to say, I am completely behind on lecture materials not only for this course but for another course as well.
I have no excuse but to say that my time management has difficult. I have been forced to prioritize other courses first due to the unending deadlines one after the other. This course, however has been extremely lax in explaining what is actually required. I really have no idea how much is needed to pass or for credit or for distinction or for high distinction.
Looking at the sample job applications, I can only aim for the top, and I find that impossible to do since I have my thesis and other subjects to look out for. So I have, in essence, chosen to sacrifice my job application and a bit of my sanity to save my other courses.
At this point in time, the only thing I am really satisfied with is my Analytical Skill and Security Skills section. I think that my community and professionalism could be improved on, so I plan to focus on that soon. And at this point in time, I am willing to forsake my Something Awesome Project.
BUT I believe my tutor(Adam) STRONGLY hinted that he encouraged us to continue working on our something awesome project even after we submit the job application. I have no idea if this means that I will be losing marks on time management or the something awesome project itself… All I hope is that it is not both :')
Thankfully, today and tomorrow is relatively free for me, so time for me to get blogging :D

0 notes
Text
security and ghosts
For this week’s tutorial exercise, the question was this:
Suppose you are the friendly Major M from the base who can see the alien A but who cannot see the invisible man X. Only A can see and hear X.
Q: What would you M do to get from X his report on the Alien's (A's) planet?
Now the problem with this scenario is whether or not Alien A is a good or bad guy. If A is evil, then for all we know, he could have killed X already, and is just infiltrating our group for his own purposes. And since X is invisible (a ghost), we have no way of telling if X really is where A says he is.
Now if A is allegedly good, then he needs to prove that somehow. So first, we must check that X really is there and... not dead. And so we need some way of authenicating X’s existence. This can be done by asking A something only X will know, such as his mother’s maiden name.
Now that we know X really is not dead or made up, then we can at the very least trust A to transfer our message. But we now run into the issue of whether or not A will tamper with X’s words, since X’s report may include information regarding the aliens. Although if A really hasn’t killed X yet, then we can hopefully trust that A will continue to communicate with X for us.
Therefore, we need a method of authenticating the integrity of our message so that we can know whether or not A tampered with the message. The other solution is to create a method that is tamper proof, or encrypted in a way that A does not know X and our shared key. That is, something that we and X know, but is oblivious to A. Now this can be as simple as using some military-specific protocol protocol that uses a word substitution cipher, or even just a simple monoalphabetic cipher like morse code.
Now a more interesting solution that was raised in class was create a barrier between what A and us. However, we can still ask X a question, and then he can tell his answer to A, and then A can relay that answer back to us in writing. The idea is that we remove the context from A, so A cannot know what questions we are asking, and so can not understand the what his answers mean. If he does not know what the answers mean, then he can not tamper with the answers.

If we want to increase the security or our communication even further, we can ask our questions where the answer is either yes or no, or maybe even some form of multiple choice. With this method, we can authenticate that the message is not being tampered with by randomly asking X really obvious questions amid secret ones. And if we recieve the correct answer from X, then we know that the A can be trusted and that the method works. However, if we recieve a wrong answer, then A must be guessing the questions, and of course, that makes things more difficult. So I suppose we can just repeat the questions and collate the most repeated answer from A (since A cannot be guessing correctly every single time).
0 notes
Text
security and buffer overflows
So recently I found an article about how the Microsoft Security Response Center (MSRC) was considering the shift from “unsafe legacy languages” to more modern, safer ones.
The reason? Their security engineering manager said this:
The majority of vulnerabilities fixed and with a CVE assigned are caused by developers inadvertently inserting memory corruption bugs into their C and C++ code.
It turns out C and C++ may be unsafe compared to other programming languages that use automatic memory management, like C# and .NET.
So why is memory an issue in security? It’s mainly due to something called buffer overflow.
Buffer overflow occurs when data is written to memory outside of a memory buffer or array. It is similar to corruption of the memory, and is reliant on the code or compiler failing to check the end of the array. Attackers will usually try to trick the program into executing their own code by using this overflow method to overwrite return addresses to point to another part of the memory that they modified.
Buffer overflows can be protected against by using a canary. A canary is a set value that is placed on the stack to monitor buffer overflows. If a buffer overflows, the value of the canary will be corrupted/changed, and so when the canary is verified, it will fail and alert the program that there has been a buffer overflow.
0 notes