#authentication
Explore tagged Tumblr posts
Text
Summary: "I think we should go clubbing again," Buck announces in between Forza races. "We have a Friday in the middle of our 96, it would be perfect." "You guys planning something?" Hen asks, coming over from the kitchen with a bowl of trail mix. "I'm trying to get Eddie to come pick up guys with me," Buck says. Hen's eyebrows arch high above her glasses. "Really," Hen says. "It's more of a wingman situation," Eddie tries to explain. "Yeah, Eddie picks the guys so I don't make stupid decisions," Buck says, flicking through menus to pick a new racetrack. The combination of Hen munching peanuts and looking back and forth between them makes Eddie feel like he's a zoo exhibit. Best Friends, captured in the wild, still feral, exhibiting behaviors heretofore unknown to science. "Well, good luck with - all that," Hen says pointedly to Eddie. She is definitely not talking about the video game.
Author: @vgreysoncellars
#official fic poll#haveyoureadthisfic#pollblr#internet culture#fandom culture#fanfic#fanfiction#tumblr polls#fandom poll#authentication#9 1 1#9 1 1 fanfiction#9 1 1 fic#9 1 1 abc#buddie#9 1 1 buddie#ao3
21 notes
·
View notes
Text
Authenticity isn’t about loyalty to your past self.

It’s not about proving to others that you’ve “never changed.”
That’s just ego, afraid of being misunderstood.
True authenticity?
It’s evolving.
It’s shedding.
It’s waking up today and realizing you no longer agree with the version of you who made those old promises, had those old beliefs, or tolerated those old dynamics.
You don’t owe anyone the performance of consistency.
You owe yourself the freedom to evolve.
True authenticity isn’t about staying the same.
It’s about being braver than you were yesterday.
It’s about being real with the truth that lives in your body right now.
Say it with your chest: I don’t need to stay who I was to prove I’m real.
#authenticity#authenticflavors#authentic self#authentication#authenticliving#ambitious women#beautiful women#beauty#glow society#the glow society#fit beauty#health#self love#self improvement#self care#spiritual awareness#spiritual healing#spiritual warfare#spiritual awakening#spiritual journey#spiritual growth#spirituality#spiritual life#holy spirit#school spirits#sparkle#self growth#personal growth#growth#growing up
10 notes
·
View notes
Text
identifying your principles and values

self-reflection
take some time to reflect on your experiences, beliefs, and priorities. think about moments in your life when you felt most proud, fulfilled, or aligned with your true self. what values were present in those moments? what principles guided your actions and decisions?
make a list
grab a pen and paper and start jotting down words and phrases that resonate with you. think about qualities you admire in others, causes you're passionate about, and behaviors you aspire to embody. these can be anything from honesty and integrity to compassion and creativity.
prioritize
once you have a list of potential values, take some time to prioritize them. consider which values are non-negotiables for you and which ones are less important. remember, there are no right or wrong answers—your values are personal to you.
live your values
now that you've identified your principles and values, it's time to put them into practice. strive to align your actions and decisions with your values on a daily basis. this might mean setting boundaries, making difficult choices, or speaking up for what you believe in.
reflect and adjust
as you navigate life, take time to regularly reflect on your values and how well you're living up to them. be open to adjusting and refining your values as you grow and evolve as a person.

remember, identifying your principles and values is an ongoing process. it's okay if it takes time, and it's okay if your values change over time too. what's important is that you stay true to yourself and live a life that's in alignment with what matters most to you.
#principles#values#purpose#beliefs#understanding#resilience#meaning#authentic#authenticity#authentication#authentic self#effort
20 notes
·
View notes
Text
Public Assistance Delays: Ration Card Digital Issues
Grievance Status for registration number : PMOPG/E/2025/0043367 Grievance Concerns To Name Of Complainant Yogi M. P. Singh Date of Receipt 29/03/2025 Received By Ministry/Department Prime Minister’s Office Grievance Description Most respected Sir if the government has prepared modified Ration cards of the Ration card holders then why this new ration card is not showing on the Internet as…
3 notes
·
View notes
Text
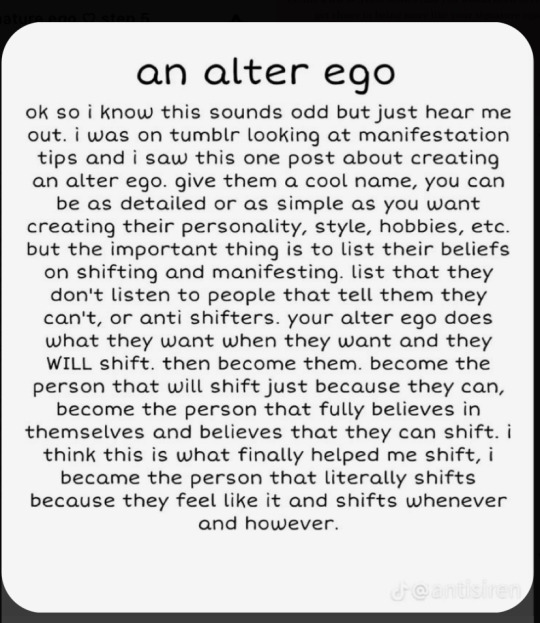
Yes !!!!!!
#manifesting#alter ego#express yourself#perspective#create mod#alterhuman#beyourbestself#findyourself#youroneofakind#beautiful#language#who are you#learn about me#self discovery#imagination#aesthetic attraction#authenticity#authentic self#authenticliving#authentication#leadership
14 notes
·
View notes
Text
Facial Recognition Application - Future of Work
Are you feeling irritated waiting in long lines for check-ins? Don't worry, we are here with an interesting application called Face Recognition. Say goodbye to the stone age. Welcome effortless check-ins with Face Recognition. Upgrade now and step into the future!
👉🌐 https://www.pranathiss.com 👉📧 [email protected] 👉📲 +1 732 333 3037
#futureofwork#SecureCheckIns#security#techinnovation#biometric security#authentication#Digitaltransformation#godigital#Facialrecognitionsoftware#FacialRecognitionTech#Facialrecognitionsystem#fraudprevention#ai security#aiinnovation#advancedsecurity#techrevolution#smartsecurity#FacialRecognitionAI#frauddetection#nextgensecurity#securetech#face recognition#futuretech#EffortlessCheckIns
10 notes
·
View notes
Text
Don't forget your Mothers, baby's mother and aunts this Easter or Mother's day ✨️💕
#valentino#mario#handbag#soft girl#queen#beige#chainlink#easter#gift#totebag#soft aesthetic#brand new#authentication
9 notes
·
View notes
Link
3 notes
·
View notes
Text


#spotify#home & lifestyle#welcome home#nature#flowers#music#pink#lifestyle#like#landscape#amazing beauty#authentication#lifestyle blog#beautiful#blogger#vintage#vtuber#cottagecore#angel core#cutecore#inspiration#scene inspo#soundcloud
4 notes
·
View notes
Text
Weekly output: FCC updates broadband map, Meta vs. California link-tax bill, passkeys, Mark Vena podcast
A holiday-shortened week got a little shorter with an overnight trip to New York for a press-preview event put on by the people behind the IFA trade show that’s brought me to Berlin since 2012. In addition to the posts below, Patreon readers got a bonus: my thoughts on note-taking alternatives to a significantly more expensive Evernote. 5/30/2023: FCC Updates Broadband Map With New ISP Data,…

View On WordPress
#1Password#account security#apple#authentication#California Journalism Protection Act#link tax#login#Mark Vena#passkey#passkeys#Patreon#wwdc
2 notes
·
View notes
Text

Shrek’s lesbian daughter and donkey’s gay son at the fantasy thrift.
#as a former teenage lesbian dirtbag who had a gay best friend in high school this is in fact authentic to my experience#my art#art#comics#sketch dump#digital sketch#shrek 5#shrek fanart#shrek franchise#shrek#illustration#artists on tumblr#digital illustration#illustrators on tumblr#character design#character fanart#queer artists#fantasy character#fan comic#digital sketchbook
28K notes
·
View notes
Link
PAY3DS ACS – SecurePay 3DS: Enhanced Authentication Solution for Secure Online Transactions
0 notes
Text
Laravel 12 Multi-Auth System: Admin & User Login
#Laravel12#MultiAuth#AdminLogin#UserAuthentication#Laravel#WebDevelopment#LaravelApp#MultiAuthSystem#Authentication#LaravelDevelopment#LaravelTutorial#UserLogin#AdminPanel#PHP#LaravelSecurity#LaravelProjects#LoginSystem#WebAppDevelopment#LaravelBestPractices#LaravelAuth#AdminUserLogin#PHPFramework#UserRoles#LaravelMultiAuth#BackendDevelopment#WebAppFeatures
0 notes
Text
6 Ways to Make Authentication Systems More User-friendly

In today's digital landscape, strong authentication is paramount for security. However, complex and cumbersome login processes can lead to user frustration, abandoned accounts, and ultimately, a negative user experience. Striking the right balance between robust security and user convenience is crucial. Luckily, there are several ways to enhance authentication systems without compromising safety. Let's explore six key strategies to make logging in a smoother, more user-friendly experience.
1. Embrace Social Login: The Power of Familiarity
Let's face it, most users already have accounts with major platforms like Google, Facebook, Apple, or Twitter. Implementing social login allows users to authenticate using these existing credentials, eliminating the need to create and remember yet another unique username and password.
Benefits: Reduces friction, speeds up the registration and login process, leverages users' existing trust in established platforms, and can improve conversion rates.
Implementation: Offer multiple social login options to cater to a wider user base. Clearly indicate the data being shared with your platform during the authorization process.
2. Passwordless Authentication: Beyond the Traditional String
The password, while a cornerstone of security, is also a major source of user pain. Passwordless authentication methods offer secure alternatives that are often more convenient.
Magic Links: A unique, time-sensitive link is sent to the user's email address or phone number. Clicking the link logs them in directly.
One-Time Passwords (OTPs): Generated via SMS, authenticator apps, or email, OTPs provide a secure, temporary login credential without the need to remember a complex password.
Biometric Authentication: Leveraging fingerprint scanning, facial recognition, or voice recognition offers a secure and highly user-friendly way to authenticate, especially on mobile devices.
Security Keys: Physical USB or Bluetooth keys provide a strong form of two-factor authentication that is resistant to phishing attacks but can be less convenient for some users.
3. Streamline the Registration Process: Keep it Lean
A lengthy and demanding registration form can be a significant barrier to entry. Minimize the required information to the absolute essentials.
Ask for Only What's Necessary: Collect only the data you truly need upfront. Additional information can be gathered later as the user interacts with your platform.
Offer Progressive Profiling: Gradually collect user details over time, rather than bombarding them with a long form during registration.
Provide Clear Instructions and Feedback: Ensure the registration process is intuitive with clear labels, helpful tooltips, and immediate feedback on input errors.
4. Intelligent Password Management Assistance: Empowering Users
While moving beyond passwords is ideal, they remain a reality for many systems. Make password management less painful.
Strong Password Generators: Offer a built-in tool to suggest strong and unique passwords, encouraging better security habits.
Password Strength Indicators: Provide visual feedback on password complexity as the user types, guiding them towards stronger options.
"Show Password" Option: Allow users to temporarily reveal their password during entry to reduce typos and frustration.
Clear Password Reset Mechanisms: Make the password reset process straightforward and secure, with clear instructions and multiple recovery options (e.g., email, security questions).
5. Context-Aware Authentication: Smart Security
Authentication doesn't always need to be a rigid, one-size-fits-all process. Context-aware authentication adapts the level of security based on the user's behavior, location, device, and the sensitivity of the action they are trying to perform.
Risk-Based Authentication: Trigger stronger authentication methods (like 2FA) only when suspicious activity is detected or when accessing sensitive data.
Location-Based Authentication: Allow seamless login from trusted locations but require additional verification from unfamiliar networks.
Device Recognition: Remember trusted devices to avoid repeatedly prompting for authentication.
6. Consistent and Intuitive User Interface:
A well-designed and consistent authentication interface across all platforms (web, mobile app) can significantly improve user experience.
Clear Visual Hierarchy: Make login fields and buttons easily identifiable.
Mobile-First Design: Ensure the authentication process is seamless and responsive on mobile devices.
Consistent Branding: Maintain a consistent look and feel with your overall brand to build trust and familiarity.
Minimize Distractions: Keep the login/registration page clean and focused on the task at hand.
Finding the Right Balance:
Implementing user-friendly authentication doesn't mean sacrificing security. The key is to adopt a layered approach, combining strong security measures with intuitive design and user-centric features. By focusing on convenience and reducing friction, you can create authentication systems that are both secure and a pleasure to use, ultimately leading to happier and more engaged users.
0 notes
Text
Power Your Apps with Twilio SMS Messaging Solutions
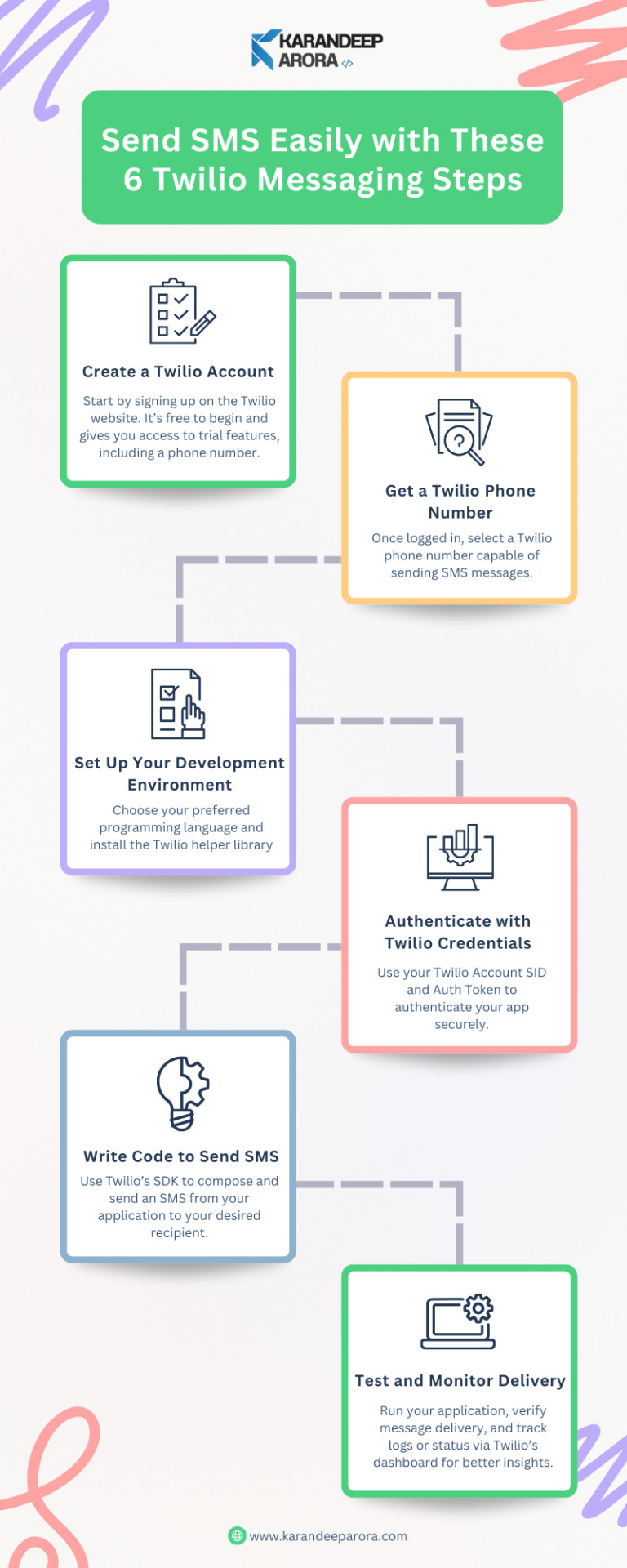
Twilio SMS Messaging enables developers to send fast, secure, and scalable text messages globally. From customer alerts to two-factor authentication, integrate SMS into your apps effortlessly using Twilio’s robust API. Enhance user engagement with reliable and real-time communication tools.
#twilio sms#twilio development services#authentication#sms#api integration#twilio messaging services
0 notes